Variable Delayed Dual-Core Lockstep (VDCLS) Processor for Safety and Security Applications
Abstract
1. Introduction
2. Related Work
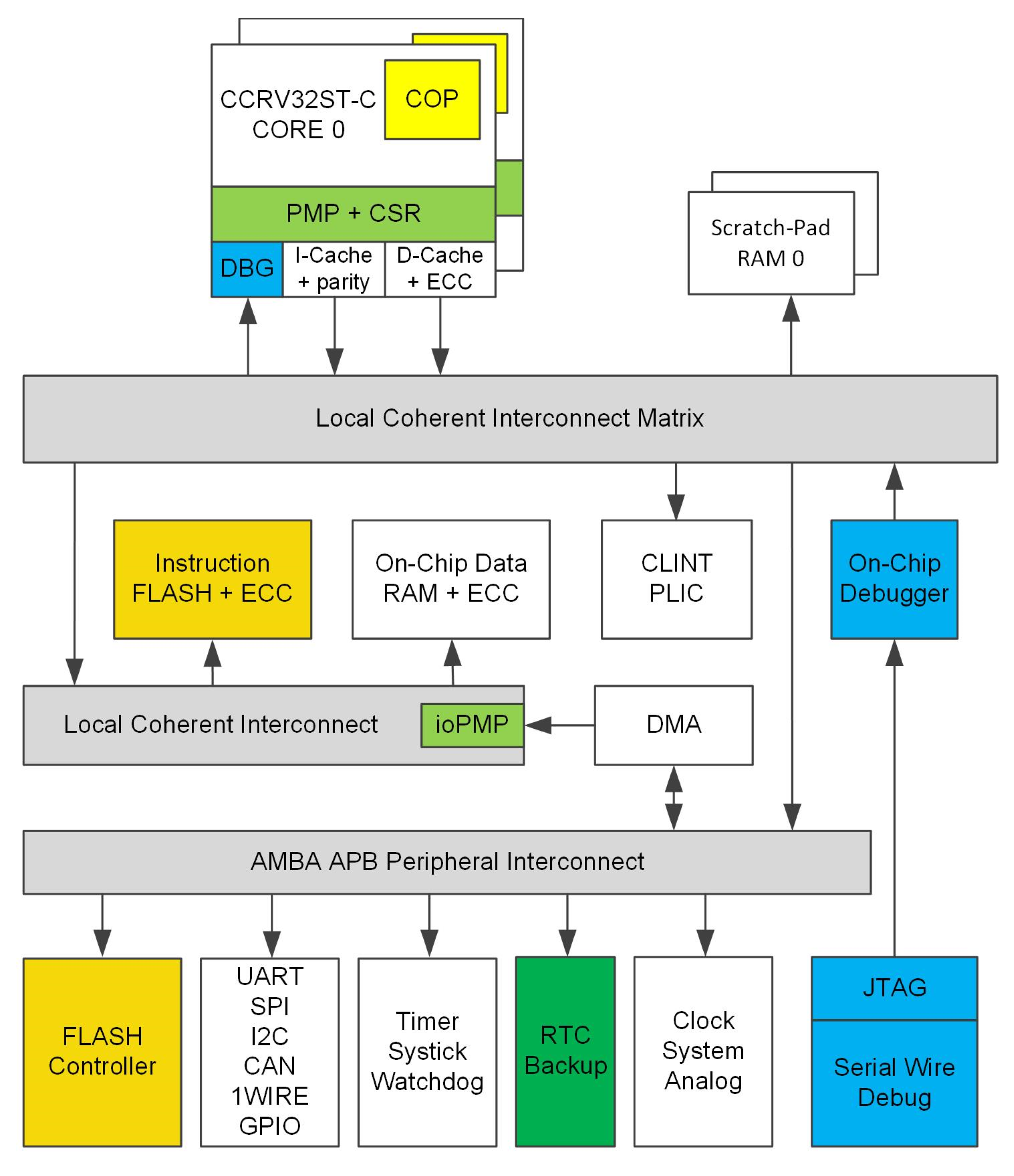
3. Design Architecture
- RV32GCX instruction set;
- Six-stage integer pipeline;
- Single-issue, in-order design;
- Gshare branch prediction;
- Single or multicore implementation;
- Up to 1.38 DMIPS/MHz/Core;
- Up to 2.10 CoreMark/MHz/Core;
- Custom instruction set extension;
- On-chip debug support.
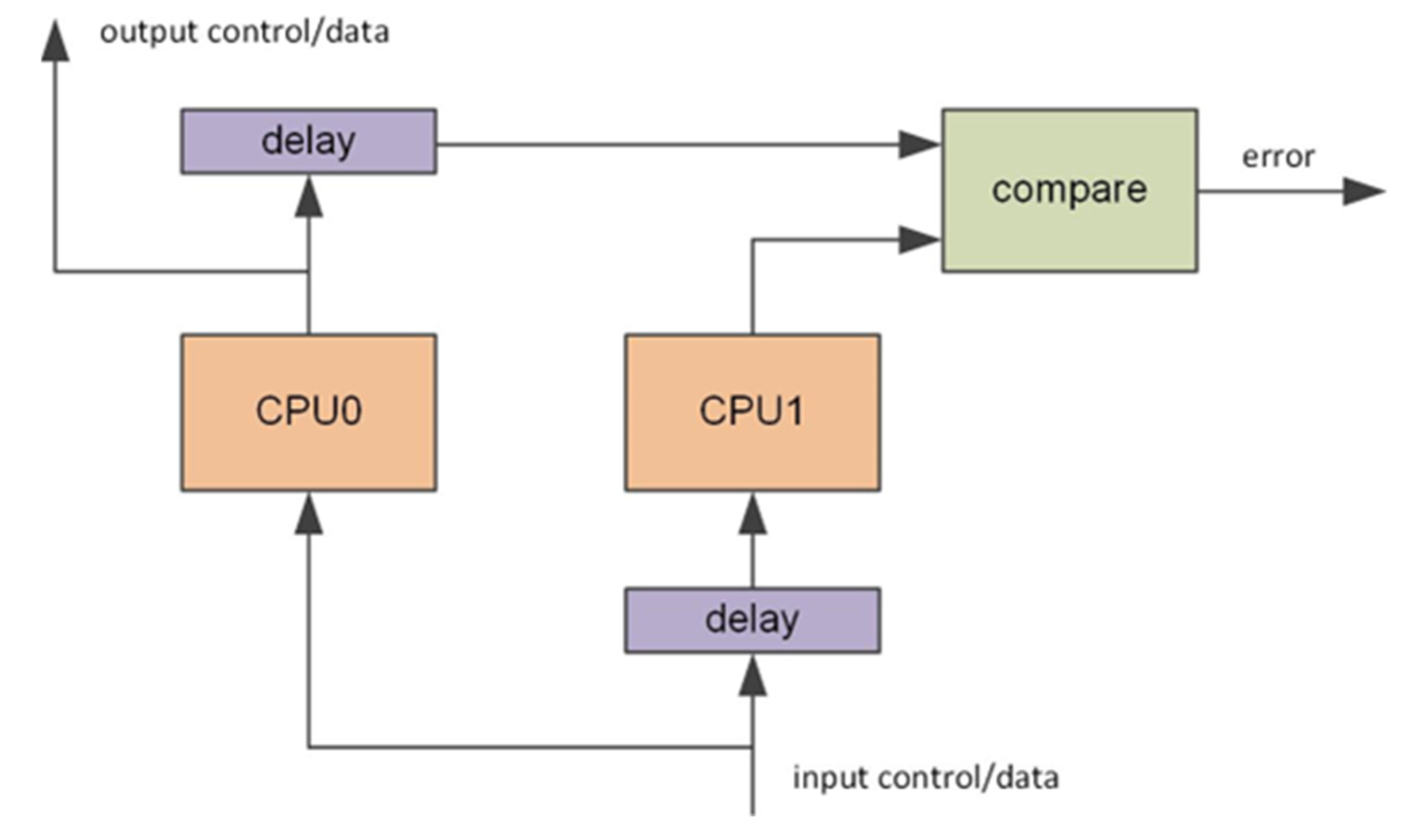
3.1. Checker Module
3.2. VDCLS Controller Module
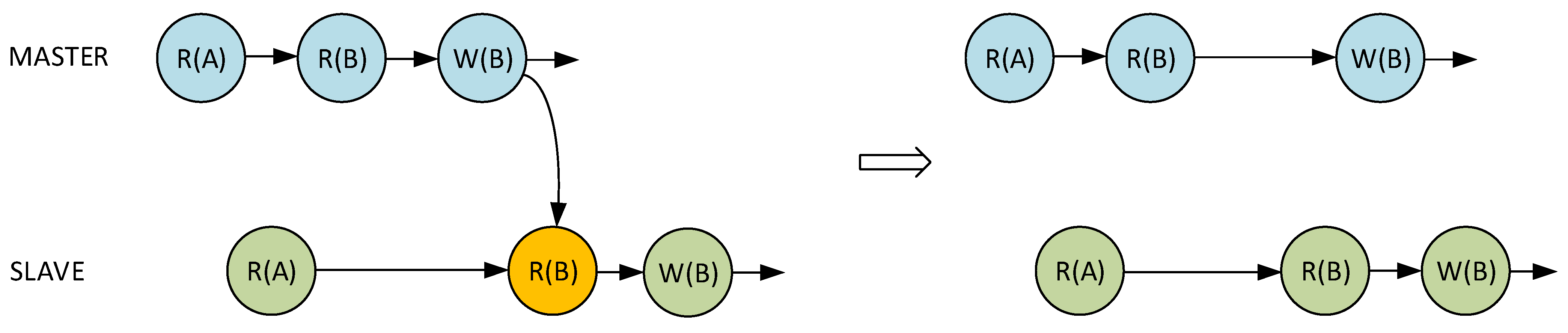
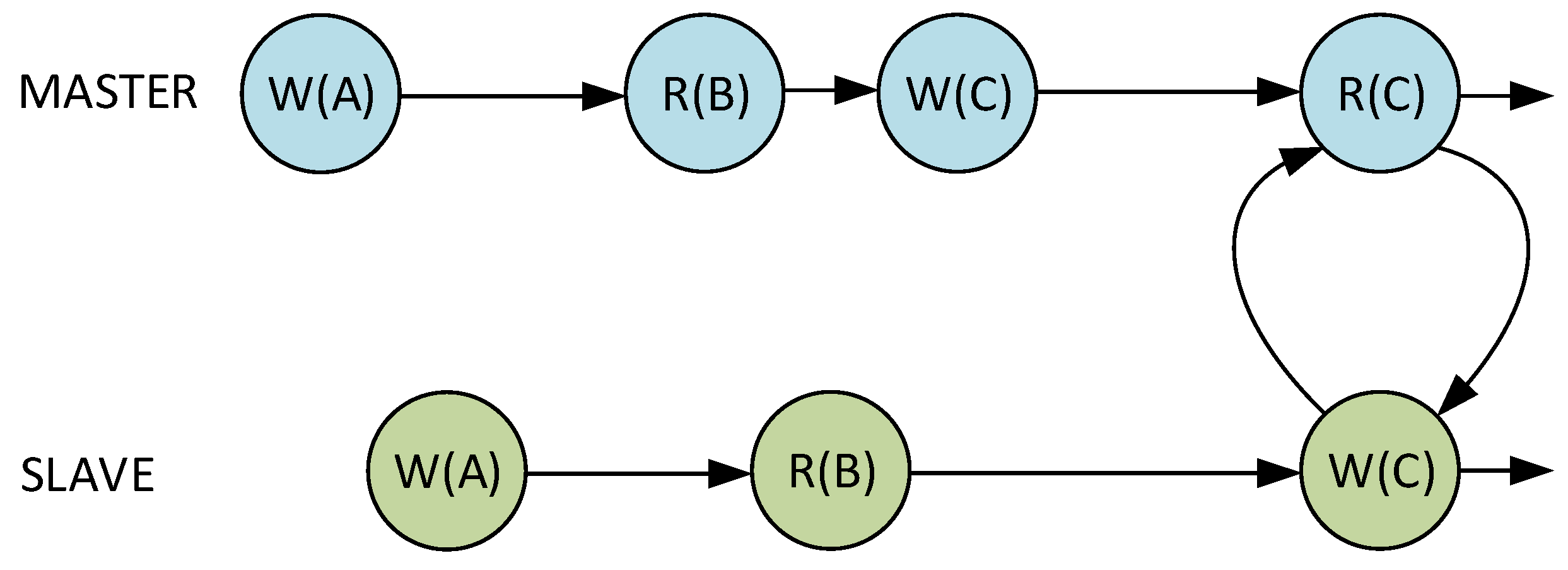
3.3. Cache Synchronization
3.4. Interrupt Injection
3.5. Peripheral Bus
4. Results
4.1. FPGA Results
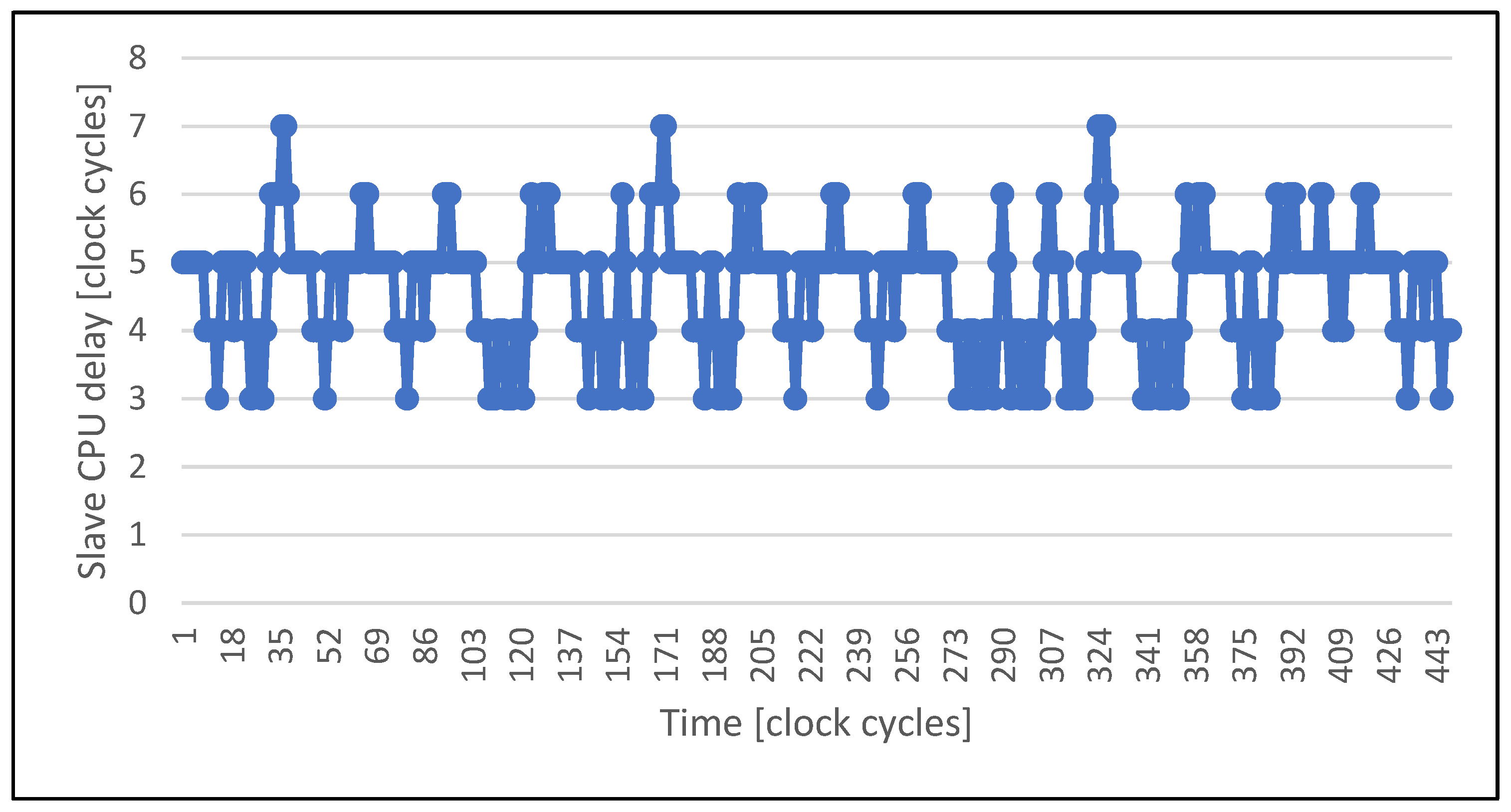
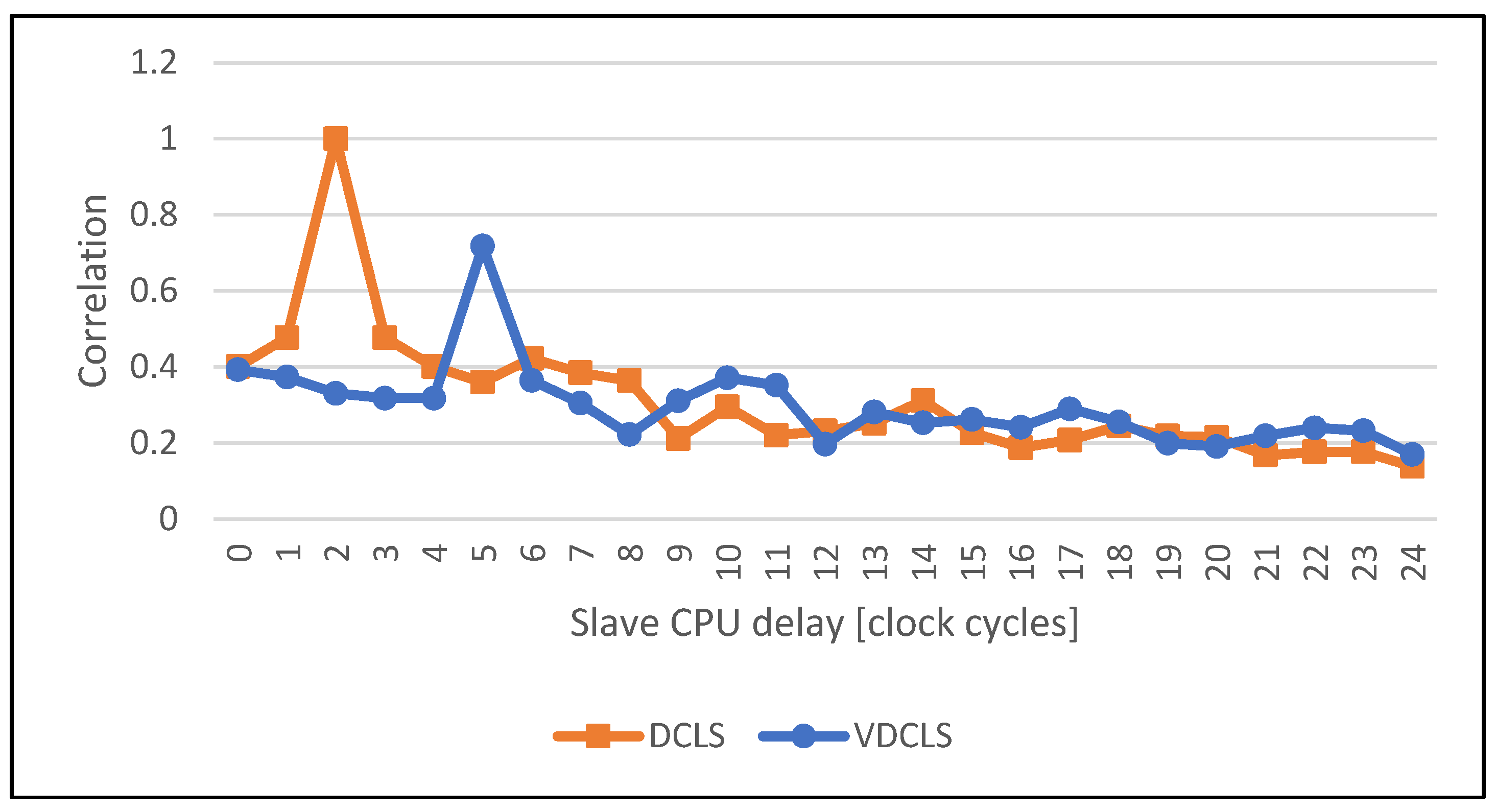
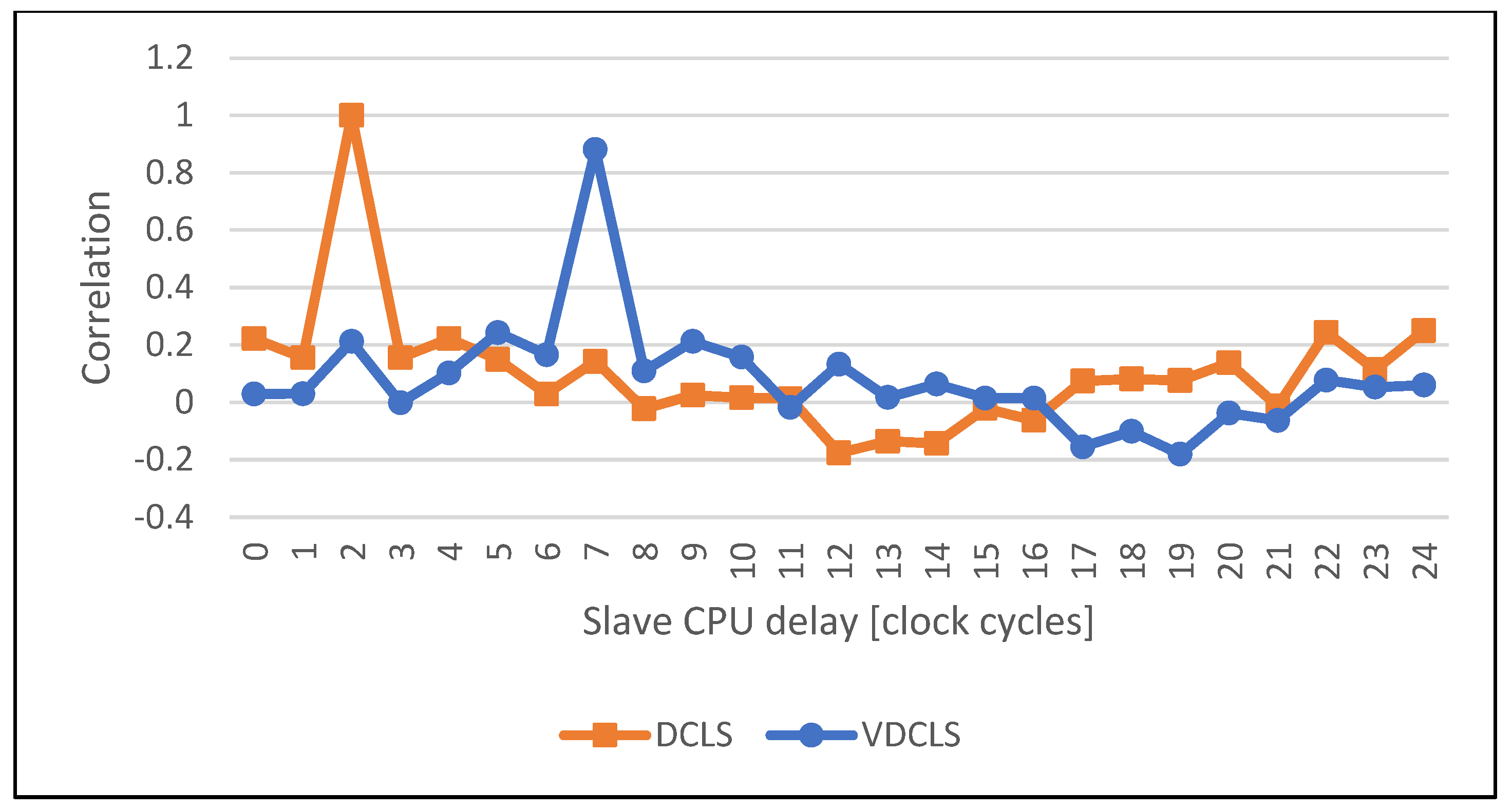
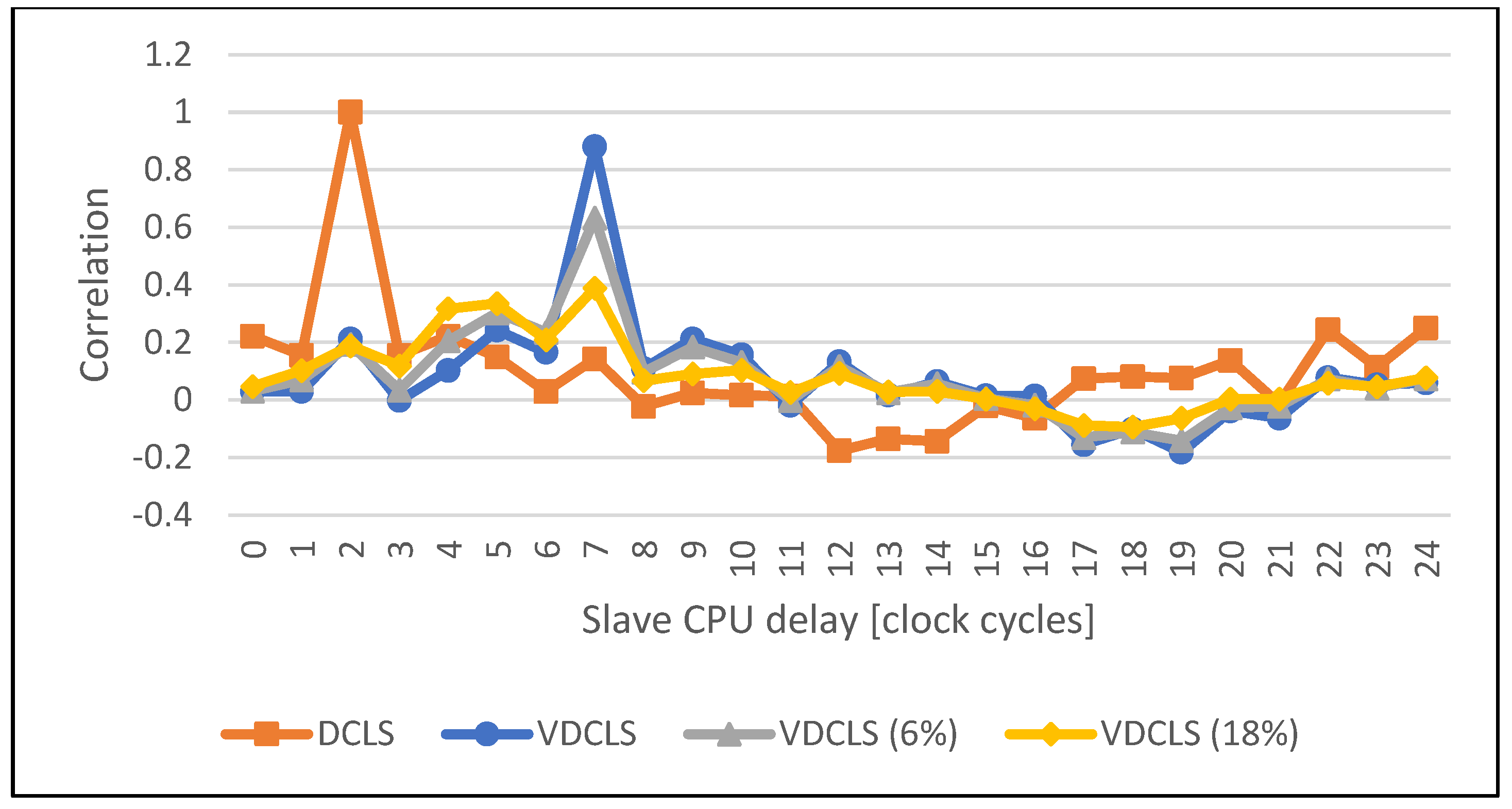
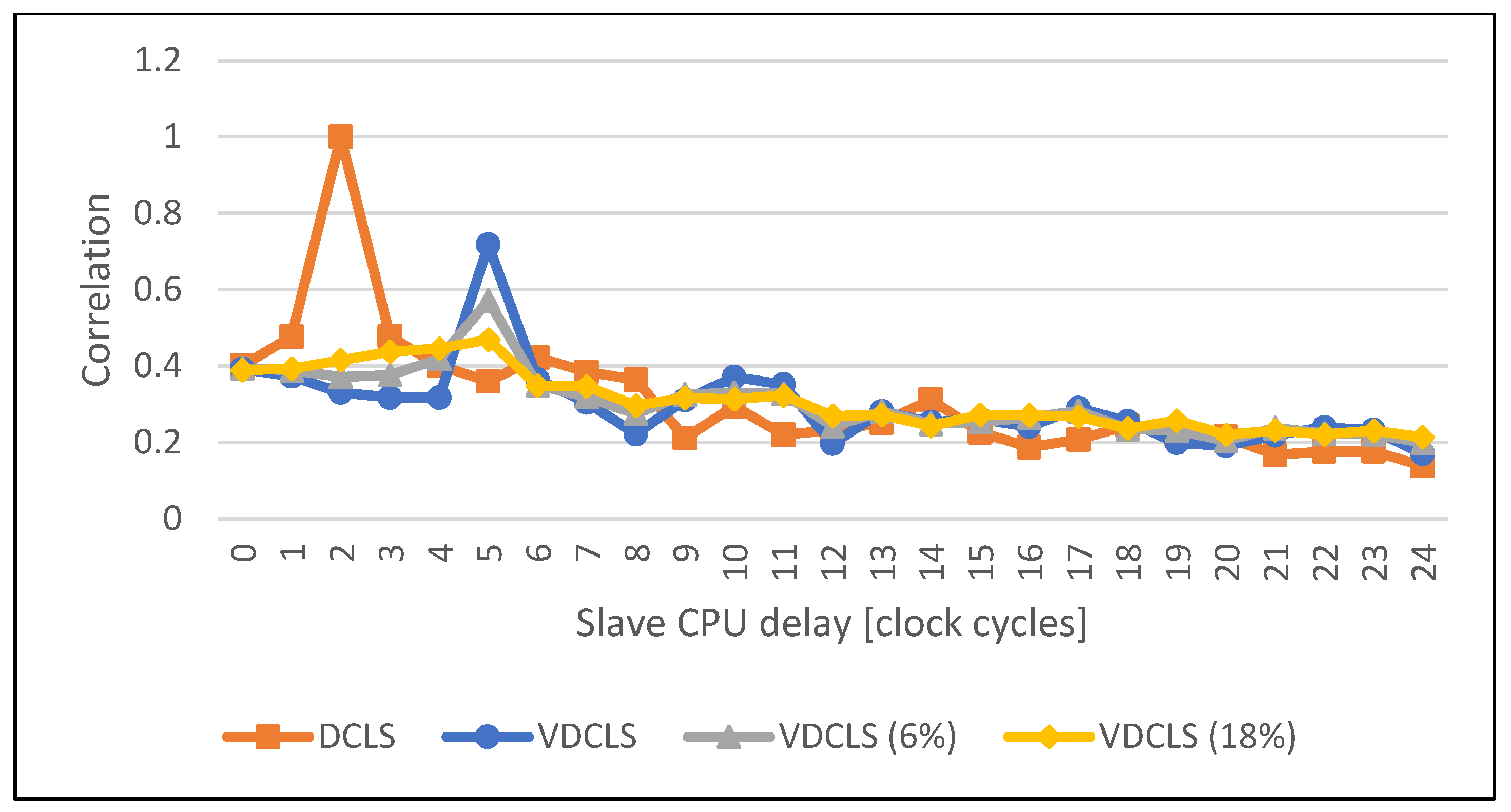
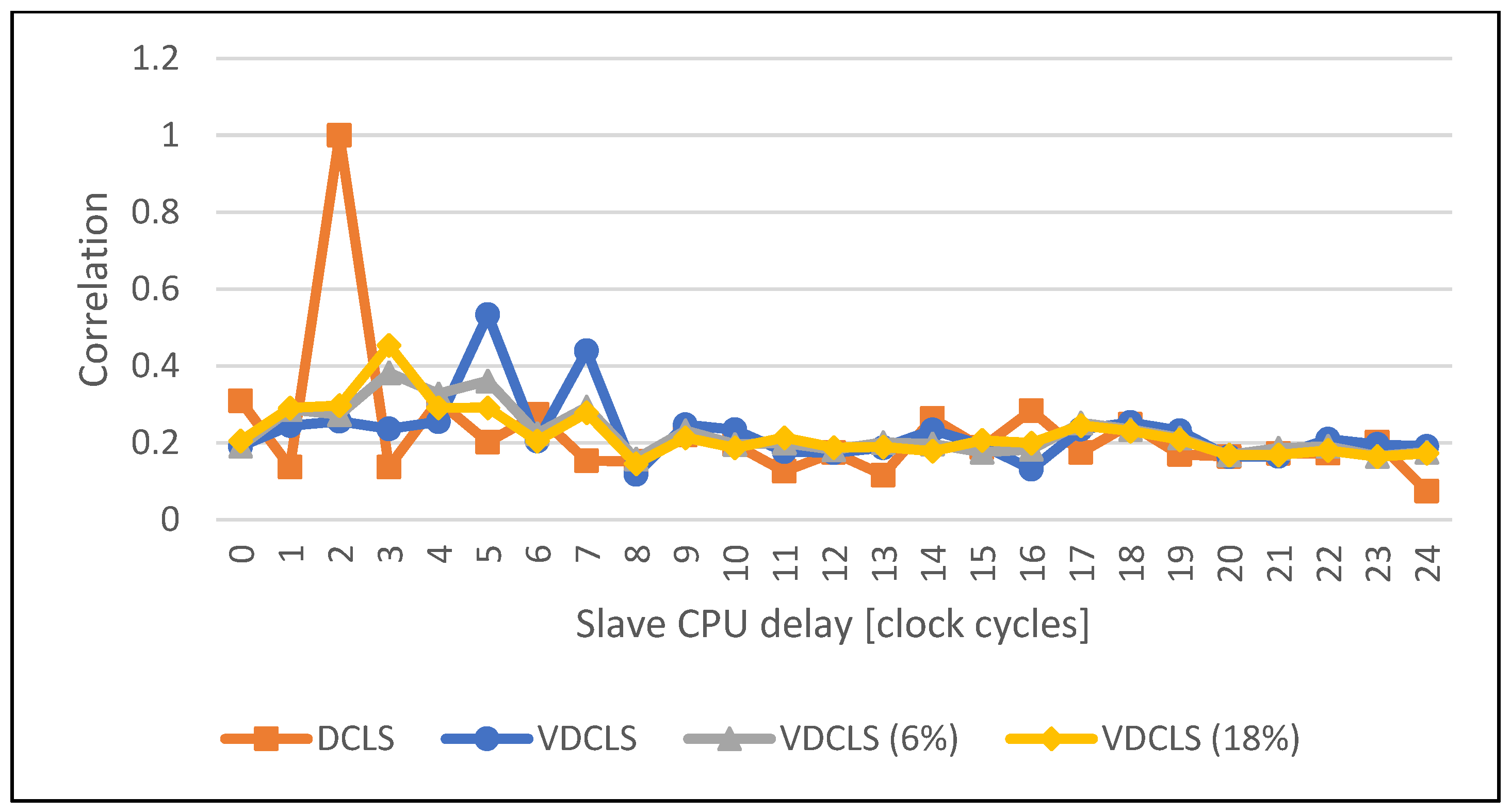
4.2. Execution Correlation Results
- r(d):
- correlation coefficient;
- xi:
- values of first variable;
- yi:
- values of second variable;
- n:
- number of samples;
- d:
- the second variable offset.
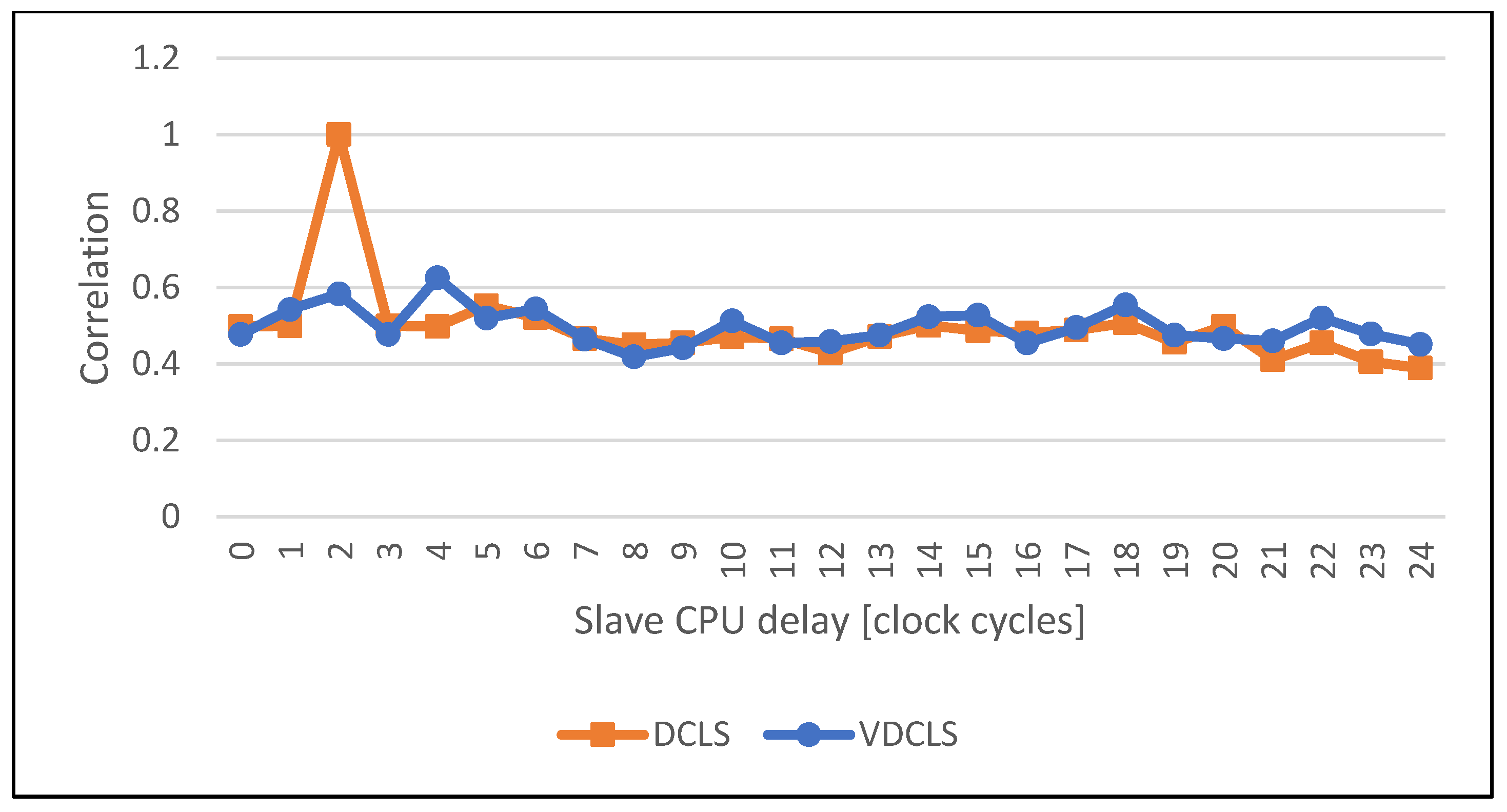
4.3. Dummy Cycles Injection Results
5. Failure Analysis
5.1. Single Event Effects
5.2. Common Mode Failures
5.3. Single Point of Failure
5.4. Fault Coverage
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Sierawski, B.D.; Reed, R.A.; Mendenhall, M.; Weller, R.A.; Schrimpf, R.D.; Wen, S.-J.; Wong, R.; Tam, N.; Baumann, R.C. Effects of scaling on muon-induced soft errors. In Proceedings of the 2011 International Reliability Physics Symposium, Monterey, CA, USA, 10–14 April 2011; pp. 3C.3.1–3C.3.6. [Google Scholar]
- ECSS-E-ST-70-11C; Space Engineering—Space Segment Operability. ESA-ESTEC: Noordwijk, The Netherlands, 2008.
- ISO 26262:2018 Road Vehicles—Functional Safety. 2018. Available online: https://www.iso.org/standard/68383.html (accessed on 24 November 2022).
- Oh, N.; Shirvani, P.P.; McCluskey, E.J. Control-flow checking by software signatures. IEEE Trans. Reliab. 2002, 51, 111–122. [Google Scholar] [CrossRef]
- Bashiri, M.; Miremadi, S.G.; Fazeli, M. A Checkpointing Technique for Rollback Error Recovery in Embedded Systems. In Proceedings of the 2006 International Conference on Microelectronics, Dhahran, Saudi Arabia, 16–19 December 2006; pp. 174–177. [Google Scholar]
- Mukherjee, S. Architecture Design for Soft Errors; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 2008. [Google Scholar]
- Iturbe, X.; Venu, B.; Ozer, E.; Das, S. A Triple Core Lock-Step (TCLS) ARM® Cortex®-R5 Processor for Safety-Critical and Ultra-Reliable Applications. In Proceedings of the 2016 46th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Workshop (DSN-W), Toulouse, France, 28 June 2016–01 July 2016; pp. 246–249. [Google Scholar]
- RISC-V International. Available online: https://riscv.org/ (accessed on 20 November 2022).
- Ozer, E.; Venu, B.; Iturbe, X.; Das, S.; Lyberis, S.; Biggs, J.; Harrod, P.; Penton, J. Error Correlation Prediction in Lockstep Processors for Safety-Critical Systems. In Proceedings of the 2018 51st Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), Fukuoka, Japan, 20–24 October 2018; pp. 737–748. [Google Scholar]
- NEC Corporation. Fault Tolerant Server. White Paper, 2017. Available online: https://www.nec.com/en/global/prod/express/collateral/whitepaper/ft_WhitePaper_E.pdf (accessed on 24 November 2022).
- Stratus. FtServer Architecture. Available online: https://www.stratus.com/solutions/platforms/ftserver/ftserver-architecture/ (accessed on 19 November 2022).
- STMicroelectronics. SPC574K72/SPC57EM80 Getting Started. Revision 2. Application Note. 2014. Available online: https://www.st.com/resource/en/application_note/an4389-spc574k72spc57em80-getting-started-stmicroelectronics.pdf (accessed on 23 November 2022).
- NXP Semiconductors. MPC5643L Microcontroller Reference Manual. Rev. 10. 2012. Available online: https://www.nxp.com/files-static/32bit/doc/ref_manual/MPC5643LRM.pdf (accessed on 23 November 2022).
- NXP Semiconductors. e200z4 Power Architecture™ Core Reference Manual. Rev. 0. 2009. Available online: https://www.nxp.com/files-static/32bit/doc/ref_manual/e200z4RM.pdf (accessed on 23 November 2022).
- Texas Instruments. TMS570LC4357 Hercules™ Microcontroller Based on the ARM® Cortex®-R Core. 2017. Available online: https://www.ti.com/lit/ds/spns195c/spns195c.pdf (accessed on 23 November 2022).
- ARM Ltd. Cortex™-R5 Revision: r1p2. Technical Reference Manual. 2011. Available online: https://developer.arm.com/documentation/ddi0460/d/ (accessed on 23 November 2022).
- ARM Ltd. Cortex-M33 Dual Core Lockstep. Version 1.0. Application Note. 2017. Available online: https://developer.arm.com/documentation/ecm0690721/latest (accessed on 23 November 2022).
- Synopsys, Inc. DesignWare ARC Functional Safety Processor IP. Available online: https://www.synopsys.com/designware-ip/processor-solutions/arc-functional-safety-processors.html (accessed on 24 November 2022).
- UltraSoC Technologies Ltd. Cybersecurity and functional safety: The case for embedded analytics. White paper. Available online: https://hc32.hotchips.org/assets/sponsors/UltraSoC/UltraSoC_Safety%20and%20Security%20white%20paper.pdf (accessed on 24 November 2022).
- Sondon, S.; Mandolesi, P.; Masson, F.; Julián, P.; Palumbo, F. A dual core low power microcontroller with openMSP430 architecture for high reliability lockstep applications using a 180 nm high voltage technology node. In Proceedings of the 2013 IEEE 4th Latin American Symposium on Circuits and Systems (LASCAS), Cusco, Peru, 27 February–1 March 2013; pp. 1–4. [Google Scholar]
- Hanafi, A.; Karim, M.; Hammami, A.E. Dual-lockstep microblaze-based embedded system for error detection and recovery with reconfiguration technique. In Proceedings of the 2015 Third World Conference on Complex Systems (WCCS), Marrakech, Morocco, 23–25 November 2015; pp. 1–6. [Google Scholar]
- de Oliveira, Á.B.; Rodrigues, G.S.; Kastensmidt, F.L.; Added, N.; Macchione, E.L.A.; Aguiar, V.A.P.; Medina, N.H.; Silveira, M.A.G. Lockstep Dual-Core ARM A9: Implementation and Resilience Analysis Under Heavy Ion-Induced Soft Errors. IEEE Trans. Nucl. Sci. 2018, 65, 1783–1790. [Google Scholar] [CrossRef]
- Sim, M.T.; Zhuang, Y. A Dual Lockstep Processor System-on-a-Chip for Fast Error Recovery in Safety-Critical Applications. In Proceeding of the 46th Annual Conference of the IEEE Industrial Electronics Society (IECON), Singapore, 18–21 October 2020; pp. 2231–2238. [Google Scholar]
- Doran, H.D.; Lang, T. Dynamic Lockstep Processors for Applications with Functional Safety Relevance. In Proceedings of the 26th IEEE International Conference on Emerging Technologies and Factory Automation (ETFA), Västerås, Sweden, 7–10 September 2021; pp. 1–4. [Google Scholar]
- Kempf, F.; Hartmann, T.; Baehr, S.; Becker, J. An Adaptive Lockstep Architecture for Mixed-Criticality Systems. In Proceedings of the 2021 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), Tampa, FL, USA, 7–9 July 2021; pp. 7–12. [Google Scholar]
- Abate, F.; Sterpone, L.; Lisboa, C.A.; Carro, L.; Violante, M. New Techniques for Improving the Performance of the Lockstep Architecture for SEEs Mitigation in FPGA Embedded Processors. IEEE Trans. Nucl. Sci. 2009, 56, 1992–2000. [Google Scholar] [CrossRef]
- Kasap, S.; Wächter, E.W.; Zhai, X.; Ehsan, S.; McDonald-Maier, K.D. Novel lockstep-based fault mitigation approach for SoCs with roll-back and roll-forward recovery. Microelectron. Reliab. 2021, 124, 114297. [Google Scholar] [CrossRef]
- Rodrigues, C.; Marques, I.; Pinto, S.; Gomes, T.; Tavares, A. Towards a Heterogeneous Fault-Tolerance Architecture based on Arm and RISC-V Processors. In Proceedings of the 45th Annual Conference of the IEEE Industrial Electronics Society (IECON), Lisbon, Portugal, 14–17 October 2019; pp. 3112–3117. [Google Scholar]
- Oleksiak, A.; Cieślak, S.; Marcinek, K.; Pleskacz, W.A. Design and Verification Environment for RISC-V Processor Cores. In Proceedings of the 26th International Conference Mixed Design of Integrated Circuits and Systems (MIXDES), Rzeszow, Poland, 27–29 June 2019; pp. 206–209. [Google Scholar]
- Cieślak, S.; Oleksiak, A.; Marcinek, K.; Pleskacz, W.A. Retargeting the MIPS-II CPU Core to the RISC-V Architecture. In Proceedings of the 26th International Conference Mixed Design of Integrated Circuits and Systems (MIXDES), Rzeszow, Poland, 27–29 June 2019; pp. 261–264. [Google Scholar]
- ChipCraft Sp z o.o. CCRV32ST-C Processor Core Template. Datasheet. 2019. Available online: http://chipcraft-ic.com/download/CCRV32ST-C_template.pdf (accessed on 24 November 2022).
- Randolph, M.; Diehl, W. Power Side-Channel Attack Analysis: A Review of 20 Years of Study for the Layman. Cryptography 2020, 4, 15. [Google Scholar] [CrossRef]
- Clavier, C.; Coron, J.-S.; Dabbous, N. Differential Power Analysis in the Presence of Hardware Countermeasures. In Proceedings of the Second International Workshop, Worcester, MA, USA, 17–18 August 2000; pp. 252–263. [Google Scholar]
- Ostrowski, Ł.; Marcinek, K.; Pleskacz, W.A. Implementation and Comparison of SPA and DPA Countermeasures for Elliptic Curve Point Multiplication. In Proceedings of the 26th International Conference Mixed Design of Integrated Circuits and Systems (MIXDES), Rzeszow, Poland, 27–29 June 2019; pp. 227–230. [Google Scholar]
- Danger, J.-L.; Guilley, S.; Bhasin, S.; Nassar, M. Overview of Dual rail with Precharge logic styles to thwart implementation-level attacks on hardware cryptoprocessors. In Proceedings of the 3rd International Conference on Signals, Circuits and Systems (SCS), Medenine, Tunisia, 6–8 November 2009; pp. 1–8. [Google Scholar]
- Mitra, S.; Saxena, N.R.; McCluskey, E.J. Common-mode failures in redundant VLSI systems: A survey. IEEE Trans. Reliab. 2000, 49, 285–295. [Google Scholar] [CrossRef]
- Peña-Fernández, M.; Serrano-Cases, A.; Lindoso, A.; García-Valderas, M.; Entrena, L.; Martínez-Álvarez, A.; Cuenca-Asensi, S. Dual-Core Lockstep enhanced with redundant multithread support and control-flow error detection. Microelectron. Reliab. 2019, 100–101, 113447. [Google Scholar] [CrossRef]
- Aviles, P.M.; Lindoso, A.; Belloch, J.A.; Garcia-Valderas, M.; Morilla, Y.; Entrena, L. Radiation Testing of a Multiprocessor Macrosynchronized Lockstep Architecture With FreeRTOS. IEEE Trans. Nucl. Sci. 2022, 69, 462–469. [Google Scholar] [CrossRef]









| Dhrystone [DMIPS/Hz] | CoreMark [CoreMark/MHz] | |
|---|---|---|
| Multicore (2 cores) | 1.38 | 2.10 |
| VDCLS | 1.24 | 2.04 |
| Multicore (2 Cores) | VDCLS | |||||
|---|---|---|---|---|---|---|
| LUTs | FFs | LUTs | FFs | % LUTs | % FFs | |
| processor system | 38842 | 27583 | 39460 | 28693 | +1.59 | +4.02 |
| processor coreplex | 28796 | 20932 | 29425 | 22042 | +2.18 | +5.30 |
| core 0 | 3102 | 2165 | 3162 | 2169 | +1.93 | +0.18 |
| core 1 | 3105 | 2165 | 3149 | 2169 | +1.42 | +0.18 |
| d-cache 0 | 902 | 1275 | 975 | 1333 | +8.09 | +4.55 |
| d-cache 1 | 963 | 1272 | 885 | 1296 | −8.09 | +1.87 |
| i-cache 0/1 | 725 | 826 | 734 | 850 | +1.24 | +2.90 |
| interrupt | 1184 | 1636 | 1467 | 1842 | +23.90 | +12.59 |
| multicore | 119 | 352 | 356 | 786 | +199.16 | +123.30 |
| # Errors | % Errors | |
|---|---|---|
| Activated errors | 7233 | 100% |
| Detected errors | 7233 | 100% |
| Undetected errors | 0 | 0% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marcinek, K.; Pleskacz, W.A. Variable Delayed Dual-Core Lockstep (VDCLS) Processor for Safety and Security Applications. Electronics 2023, 12, 464. https://doi.org/10.3390/electronics12020464
Marcinek K, Pleskacz WA. Variable Delayed Dual-Core Lockstep (VDCLS) Processor for Safety and Security Applications. Electronics. 2023; 12(2):464. https://doi.org/10.3390/electronics12020464
Chicago/Turabian StyleMarcinek, Krzysztof, and Witold A. Pleskacz. 2023. "Variable Delayed Dual-Core Lockstep (VDCLS) Processor for Safety and Security Applications" Electronics 12, no. 2: 464. https://doi.org/10.3390/electronics12020464
APA StyleMarcinek, K., & Pleskacz, W. A. (2023). Variable Delayed Dual-Core Lockstep (VDCLS) Processor for Safety and Security Applications. Electronics, 12(2), 464. https://doi.org/10.3390/electronics12020464







