Intelligent Mesh Cluster Algorithm for Device-Free Localization in Wireless Sensor Networks
Abstract
1. Introduction
- We propose the IMC method, a geometric method built with an object-oriented programming technique by abstracting the geometric elements in WSN, such as nodes, links, segments on links, intersecting points among links, meshes formed by links, and seeds, into different classes. The instances of the built classes are organically combined to realize adaptively wireless link control and target location estimation.
- The proposed scheme utilizes the mesh cluster to narrow the scope of monitoring by scanning only the mesh cluster-related wireless links and inactive remaining links, and the estimation of the target’s position is calculated by the weighted centroid coordinates of triggered meshes in the mesh cluster, which reduces energy consumption while ensuring positioning accuracy and noise interference.
- The performance of the proposed scheme is evaluated with groups of simulations under different parameters. Results demonstrate the accuracy and effectiveness of the method.
2. Related Works
3. Proposed IMC Algorithm
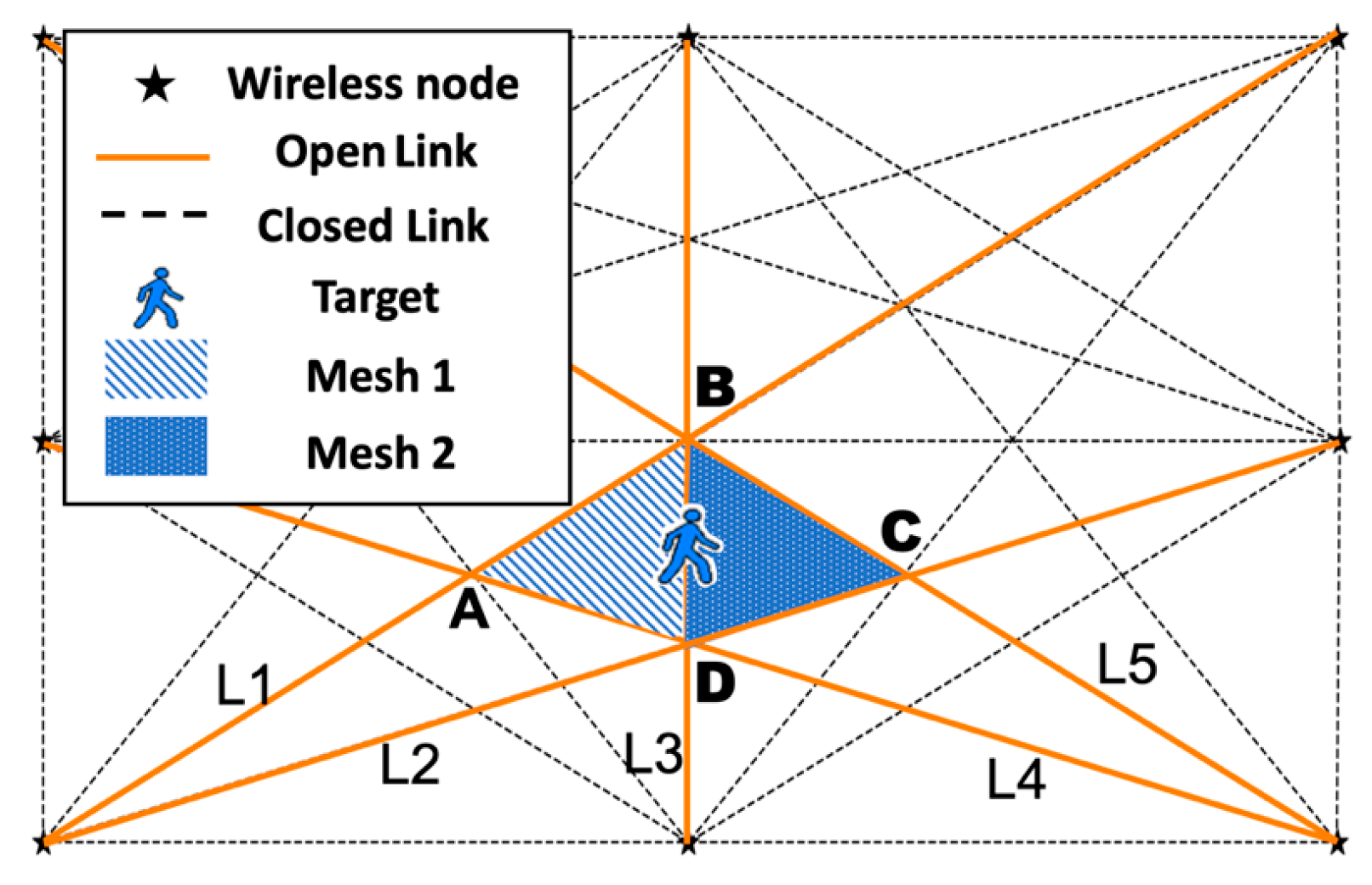
3.1. System Description
3.2. Geometric Elements Abstract
| Algorithm 1 The method of creating Ip and Segment instances |
| Input: The list L including all Link instances in network. |
| Output: Intersecting point list Ip and Segments list Seg for each link in . 1. for all links in L do 2. for all links in L, do 3. Compute intersecting point using Intersection-Point algorithm. 4. if then 5. 6. 7. for all links in L do 8. Sort the intersecting points in including two endpoints in ascending order of x-axis coordinates. 9. Create Segment instances with sequenced intersecting points and endpoints and , then stored in Seg list. |
| Algorithm 2 The method of creating Seed and Mesh instances |
| Input: All nodes N, intersecting points Ip, and links L. |
| Output: Seeds list P and meshes list Q. 1. for all nodes in N do 2. Create seeds around nodes . 3. for all intersecting points in Ip do 4. Create seeds around intersecting points . 5. 6. for all seeds in do 7. Calculate the position relationship with all links in L using Equation (2). 8. Classify the seeds based on , infer the vertexes and sides, then create meshes Q. |
3.3. Mesh Cluster (MC) and Mesh Expansion Index (MEI)
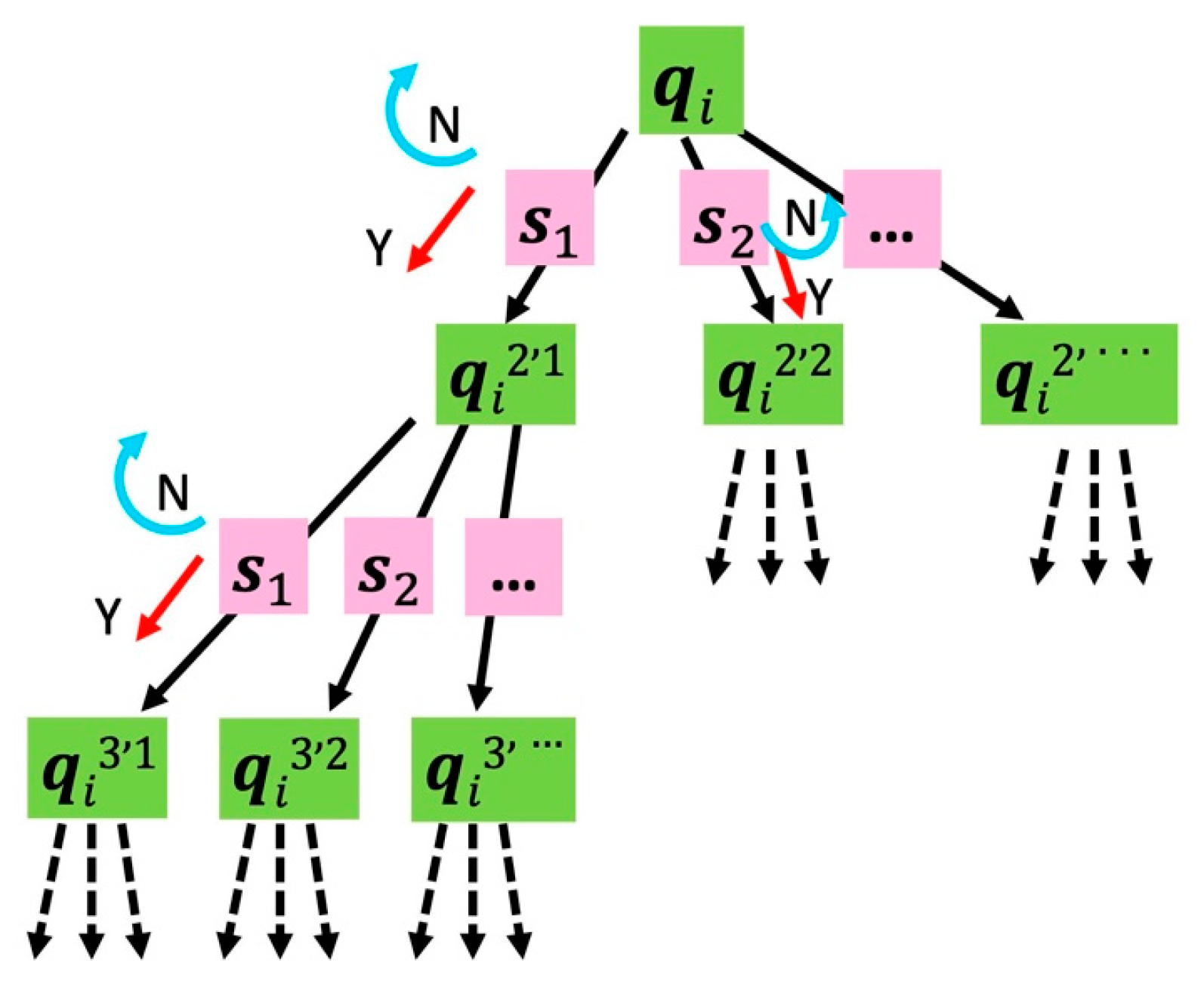
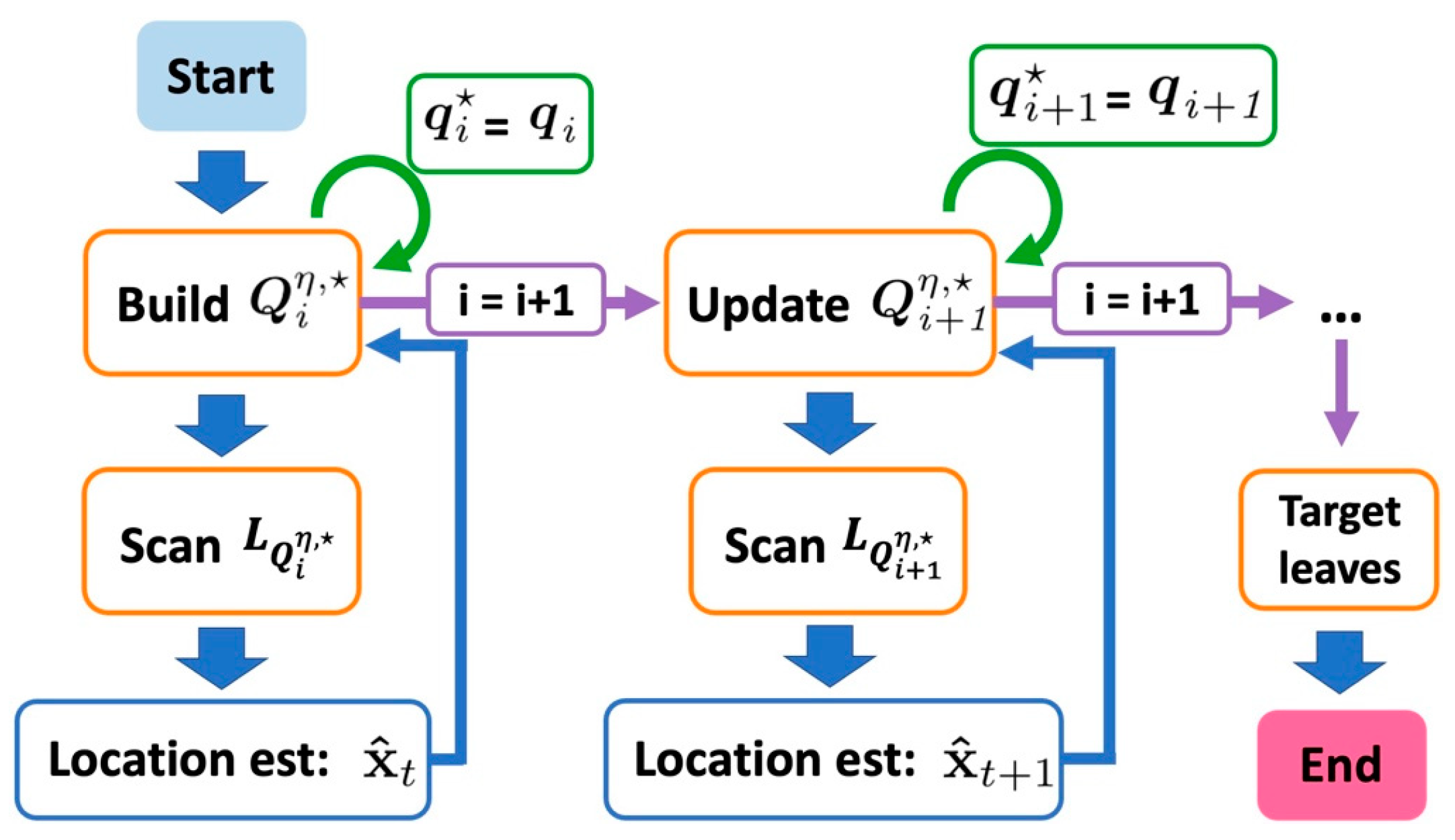
3.4. Location Estimation
- Phase 1: Initialize mesh cluster.
| Algorithm 3 A n-Ary Tree Traversal Algorithm |
| Input: The mesh cluster and triggered links |
| Output: The set of triggered links related meshes 1. Add the first item to 2. for all mesh in do 3. for all segment in Seg do 4. if then 5. Add the neighbor mesh of segment into without duplicate. |
- Phase 2: Update mesh cluster.
| Algorithm 4 Intelligent Mesh Cluster Algorithm |
| 1. Network initialization: Build Nodes N, and Links L. 2. Build Ips Ip and Segments Seg for each link using Algorithm 1. 3. Build Seeds P for each intersecting points and nodes, Meshes Q using Algorithm 2. 4. Scan the edge links of the network and build the first mesh cluster . 5. Scan the links in and calculate the location estimate using Equation (9). 6. Find the nearest mesh using Equation (10). 7. if is then 8. Go back to step (7). 9. else 10. Update the next mesh cluster and go back to step (7). |
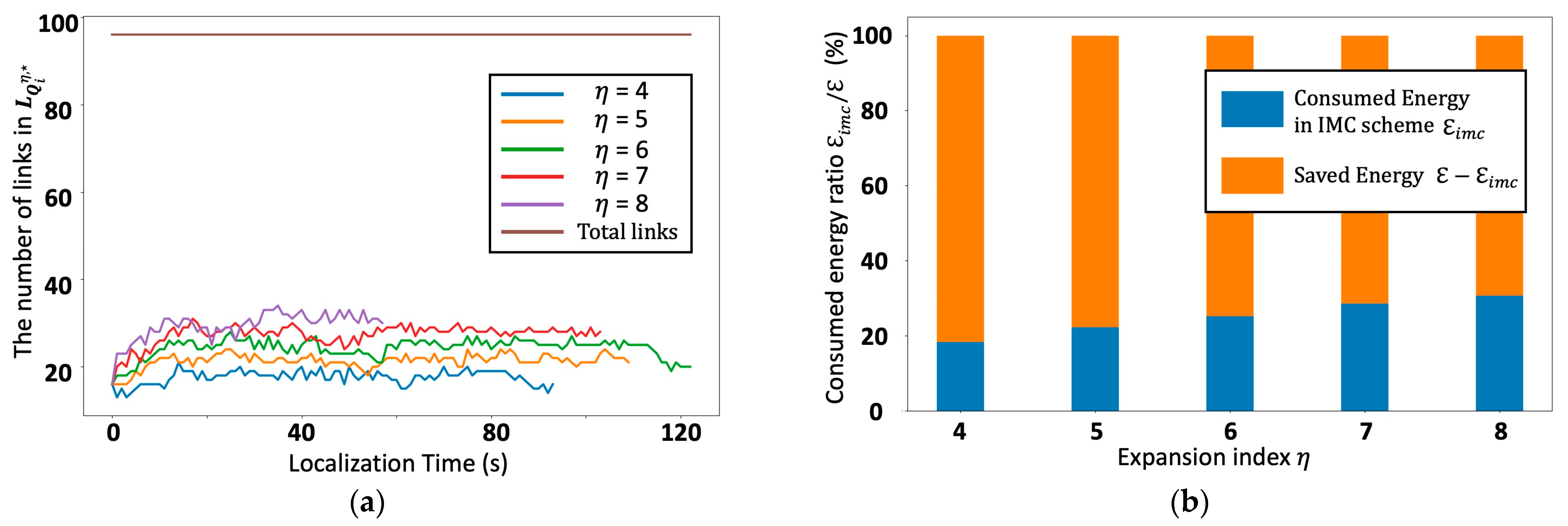
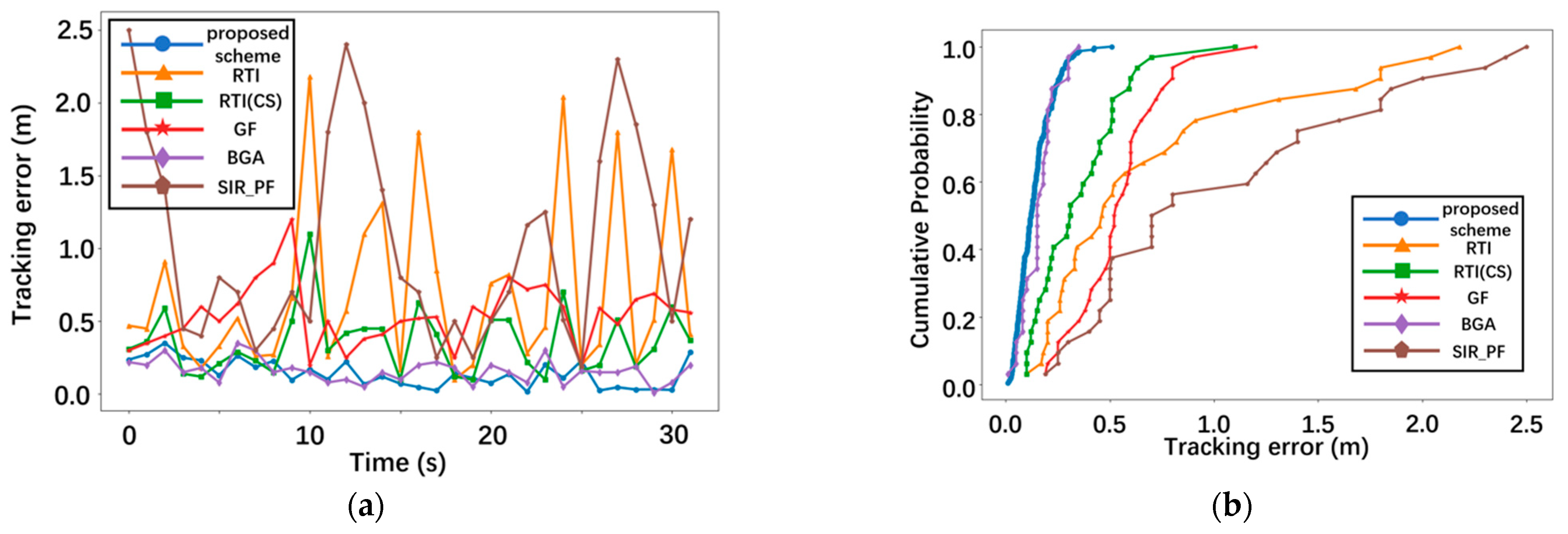
4. Performance Analysis and Evaluation
5. Computational Complexity Analysis
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yang, J.; Wang, M.; Yang, Y.; Wang, J. A device-free localization and size prediction system for road vehicle surveillance via UWB networks. IEEE Trans. Instrum. Meas. 2022, 71, 1–11. [Google Scholar] [CrossRef]
- Feng, Y.S.; Liu, H.Y.; Hsieh, M.H.; Fung, H.C.; Chang, C.Y.; Yu, C.C.; Huang, C.W. An RSSI-based device-free localization system for smart wards. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Penghu, Taiwan, 15–17 September 2021; pp. 1–2. [Google Scholar]
- Ma, L.; Liu, M.; Wang, H.; Yang, Y.; Wang, N.; Zhang, Y. WallSense: Device-free indoor Localization using wall-mounted UHF RFID tags. Sensors 2019, 19, 68. [Google Scholar] [CrossRef]
- Cimdins, M.; Schmidt, S.O.; Hellbrück, H. MAMPI-UWB—Multipath-assisted device-free localization with magnitude and phase information with UWB transceivers. Sensors 2020, 20, 7090. [Google Scholar] [CrossRef]
- Lee, J.; Park, K.; Kim, Y. Deep learning-based device-free localization scheme for simultaneous estimation of indoor location and posture using FMCW radars. Sensors 2022, 22, 4447. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Kim, Y. Deep learning-based indoor two-dimensional localization scheme using a frequency-modulated continuous wave radar. Electronics 2021, 10, 2166. [Google Scholar] [CrossRef]
- Yang, S.; Kim, Y. Single 24-GHz FMCW radar-based indoor device-free human localization and posture sensing with CNN. IEEE Sens. J. 2023, 23, 3059–3068. [Google Scholar] [CrossRef]
- Yang, S.; Sun, C.; Kim, Y. Indoor 3D localization scheme based on BLE signal fingerprinting and 1D convolutional neural network. Electronics 2021, 10, 1758. [Google Scholar] [CrossRef]
- Konings, D.; Faulkner, N.; Alam, F.; Lai, E.M.-K.; Demidenko, S. FieldLight: Device-free indoor human localization using passive visible light positioning and artificial potential fields. IEEE Sens. J. 2020, 20, 1054–1066. [Google Scholar] [CrossRef]
- Youssef, M.; Mah, M.; Agrawala, A. Challenges: Device-free passive localization for wireless environments. In Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking (MobiCom’07), Montreal, QC, Canada, 9–14 September 2007; pp. 222–229. [Google Scholar]
- Moussa, M.; Youssef, M. Smart devices for smart environments: Device-free passive detection in real environments. In Proceedings of the 2009 IEEE International Conference on Pervasive Computing and Communications, Galveston, TX, USA, 9–13 March 2009; pp. 1–6. [Google Scholar]
- Seifeldin, M.; Saeed, A.; Kosba, A.E.; El-Keyi, A.; Youssef, M. Nuzzer: A large-scale device-free passive localization system for wireless environments. IEEE Trans. Mob. Comput. 2013, 12, 1321–1334. [Google Scholar] [CrossRef]
- Zhang, D.; Liu, Y.; Guo, X.; Ni, L.M. RASS: A real-time, accurate, and scalable system for tracking transceiver-free objects. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 996–1008. [Google Scholar] [CrossRef]
- Wilson, J.; Patwari, N. A fade-level skew-laplace signal strength model for device-free localization with wireless networks. IEEE Trans. Mob. Comput. 2012, 11, 947–958. [Google Scholar] [CrossRef]
- Nannuru, S.; Li, Y.; Zeng, Y.; Coates, M.; Yang, B. Radio-frequency tomography for passive indoor multitarget tracking. IEEE Trans. Mob Comput. 2013, 12, 2322–2333. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Q.; Yu, Y.; Cheng, P.; Wu, L.; Wang, H. Robust device-free wireless localization based on differential RSS measurements. IEEE Trans. Ind. Electron. 2013, 60, 5943–5952. [Google Scholar] [CrossRef]
- Guo, Y.; Huang, K.; Jiang, N.; Guo, X.; Li, Y.; Wang, G. An exponential-rayleigh model for RSS-based device-free localization and tracking. IEEE Trans. Mob. Comput. 2015, 14, 484–494. [Google Scholar] [CrossRef]
- Li, Y.; Chen, X.; Coates, M.; Yang, B. Sequential monte carlo radio-frequency tomographic tracking. In Proceedings of the 2011 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Prague, Czech Republic, 22–27 May 2011; pp. 3976–3979. [Google Scholar]
- Kaltiokallio, O.J.; Hostettler, R.; Patwari, N. A novel bayesian filter for RSS-based device-free localization and tracking. IEEE Trans. Mob. Comput. 2021, 20, 780–795. [Google Scholar] [CrossRef]
- Wilson, J.; Patwari, N. Radio tomographic imaging with wireless networks. IEEE Trans. Mob. Comput. 2010, 9, 621–632. [Google Scholar] [CrossRef]
- Wilson, J.; Patwari, N. See-through walls: Motion tracking using variance-based radio tomography networks. IEEE Trans. Mob. Comput. 2011, 10, 612–621. [Google Scholar] [CrossRef]
- Kaltiokallio, O.; Bocca, M.; Patwari, N. A fade level-based spatial model for radio tomographic imaging. IEEE Trans. Mob. Comput. 2014, 13, 1159–1172. [Google Scholar]
- Wang, J.; Gao, Q.; Cheng, P.; Yu, Y.; Xin, K.; Wang, H. Lightweight robust device-free localization in wireless networks. IEEE Trans. Ind. Electron. 2014, 61, 5681–5689. [Google Scholar] [CrossRef]
- Feng, C.; Au, W.S.A.; Valaee, S.; Tan, Z. Received-signal-strength-based indoor positioning using compressive sensing. IEEE Trans. Mob. Comput. 2012, 11, 1983–1993. [Google Scholar] [CrossRef]
- Wang, J.; Gao, Q.; Wang, H.; Cheng, P.; Xin, K. Device-free localization with multidimensional wireless link information. IEEE Trans. Veh. Technol. 2015, 64, 356–366. [Google Scholar] [CrossRef]
- Wang, J.; Chen, X.; Fang, D.; Wu, C.Q.; Yang, Z.; Xing, T. Transferring compressive-sensing-based device-free localization across target diversity. IEEE Trans. Ind. Electron. 2015, 62, 2397–2409. [Google Scholar] [CrossRef]
- Zhang, D.; Ma, J.; Chen, Q.; Ni, L. An RF-based system for tracking transceiver-free objects. In Proceedings of the 5th Annual IEEE International Conference on Pervasive Computing and Communications (PerCom’07), White Plains, NY, USA, 19–23 March 2007; pp. 135–144. [Google Scholar]
- Zhang, D.; Lu, K.; Mao, R.; Feng, Y.; Liu, Y.; Ming, Z.; Ni, L. Fine-grained localization for multiple transceiver-free objects by using RF-based technologies. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1464–1475. [Google Scholar] [CrossRef]
- Talampas, M.; Low, K. Geometry-based algorithms for device-free localization with wireless sensor networks. In Proceedings of the 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 21–24 April 2014; pp. 1–6. [Google Scholar]
- Talampas, M.; Low, K. A geometric filter algorithm for robust device-free localization in wireless networks. IEEE Trans. Ind. Inform. 2016, 12, 1670–1678. [Google Scholar] [CrossRef]
- Talampas, M.C.R.; Low, K.S. An enhanced geometric filter algorithm with channel diversity for device-free localization. IEEE Trans. Instrum. Meas. 2016, 65, 378–387. [Google Scholar] [CrossRef]
- Sun, C.; Zhou, B.; Yang, S.; Kim, Y. Geometric midpoint algorithm for device-free localization in low-density wireless sensor networks. Electronics 2021, 10, 2924. [Google Scholar] [CrossRef]
- Abdullah, O.A.; Al-Hraishawi, H.; Chatzinotas, S. Deep learning-based device-free localization in wireless sensor networks. In Proceedings of the 2023 IEEE Wireless Communications and Networking Conference (WCNC), Glasgow, UK, 26–29 March 2023. [Google Scholar]
- Zhou, R.; Hou, H.; Gong, Z.; Chen, Z.; Tang, K.; Zhou, B. Adaptive device-free localization in dynamic environments through adaptive neural networks. IEEE Sens. J. 2021, 21, 548–559. [Google Scholar] [CrossRef]
- Zhao, L.; Huang, H.; Li, X.; Ding, S.; Zhao, H.; Han, Z. An accurate and robust approach of device-free localization with convolutional autoencoder. IEEE Internet Things J. 2019, 6, 5825–5840. [Google Scholar] [CrossRef]
- Abdull Sukor, A.S.; Kamarudin, L.M.; Zakaria, A.; Abdul Rahim, N.; Sudin, S.; Nishizaki, H. RSSI-based for device-free localization using deep learning technique. Smart Cities 2020, 3, 444–455. [Google Scholar] [CrossRef]
- Koutris, A.; Siozos, T.; Kopsinis, Y.; Pikrakis, A.; Merk, T.; Mahlig, M.; Papaharalabos, S.; Karlsson, P. Deep learning-based indoor localization using multi-view BLE signal. Sensors 2022, 22, 2759. [Google Scholar] [CrossRef]
- Zhou, B.; Ahn, D.; Lee, J.; Sun, C.; Ahmed, S.; Kim, Y. A passive tracking system based on geometric constraints in adaptive wireless sensor networks. Sensors 2018, 18, 3276. [Google Scholar] [CrossRef] [PubMed]
- Stark, H.; Woods, J.W. Probability, Statistics, and Random Processes for Engineers, 4th ed.; Pearson Education: London, UK, 2011. [Google Scholar]






| Link | |||||||||
|---|---|---|---|---|---|---|---|---|---|
| Seed | |||||||||
| 1 | 1 | −1 | 1 | 1 | −1 | −1 | −1 | ||
| 1 | 1 | 1 | 1 | 1 | −1 | −1 | −1 | ||
| 1 | 1 | −1 | 1 | 1 | −1 | −1 | −1 | ||
| −1 | 1 | 1 | 1 | 1 | −1 | −1 | −1 | ||
| 1 | 1 | −1 | 1 | 1 | −1 | −1 | −1 | ||
| −1 | 1 | −1 | 1 | 1 | −1 | −1 | −1 | ||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, C.; Zhou, J.; Jang, K.-S.; Kim, Y. Intelligent Mesh Cluster Algorithm for Device-Free Localization in Wireless Sensor Networks. Electronics 2023, 12, 3426. https://doi.org/10.3390/electronics12163426
Sun C, Zhou J, Jang K-S, Kim Y. Intelligent Mesh Cluster Algorithm for Device-Free Localization in Wireless Sensor Networks. Electronics. 2023; 12(16):3426. https://doi.org/10.3390/electronics12163426
Chicago/Turabian StyleSun, Chao, Junhao Zhou, Kyong-Seok Jang, and Youngok Kim. 2023. "Intelligent Mesh Cluster Algorithm for Device-Free Localization in Wireless Sensor Networks" Electronics 12, no. 16: 3426. https://doi.org/10.3390/electronics12163426
APA StyleSun, C., Zhou, J., Jang, K.-S., & Kim, Y. (2023). Intelligent Mesh Cluster Algorithm for Device-Free Localization in Wireless Sensor Networks. Electronics, 12(16), 3426. https://doi.org/10.3390/electronics12163426










