A Study on the Security of Online Judge System Applied Sandbox Technology
Abstract
:1. Introduction
2. Related Work
2.1. Sandbox
2.2. Research on Known Attack Methods
2.3. MITRE ATT&CK
- Tactics represent the “why” of the ATT&CK technique or subtechnique. Adversarial tactics indicate the attacker’s objective or rationale for acting. An adversary, for example, may wish to obtain credential access.
- Techniques represent “how” an adversary accomplishes a tactical goal by completing an action. For example, an adversary may release credentials in order to obtain credential access.
- Procedures are the exact implementations of techniques or subtechniques used by adversaries. To illustrate, a procedure may be an adversary injecting PowerShell into lsass.exe to dump credentials by scraping LSASS memory on a target.
2.4. Threat Modeling
3. Research Method
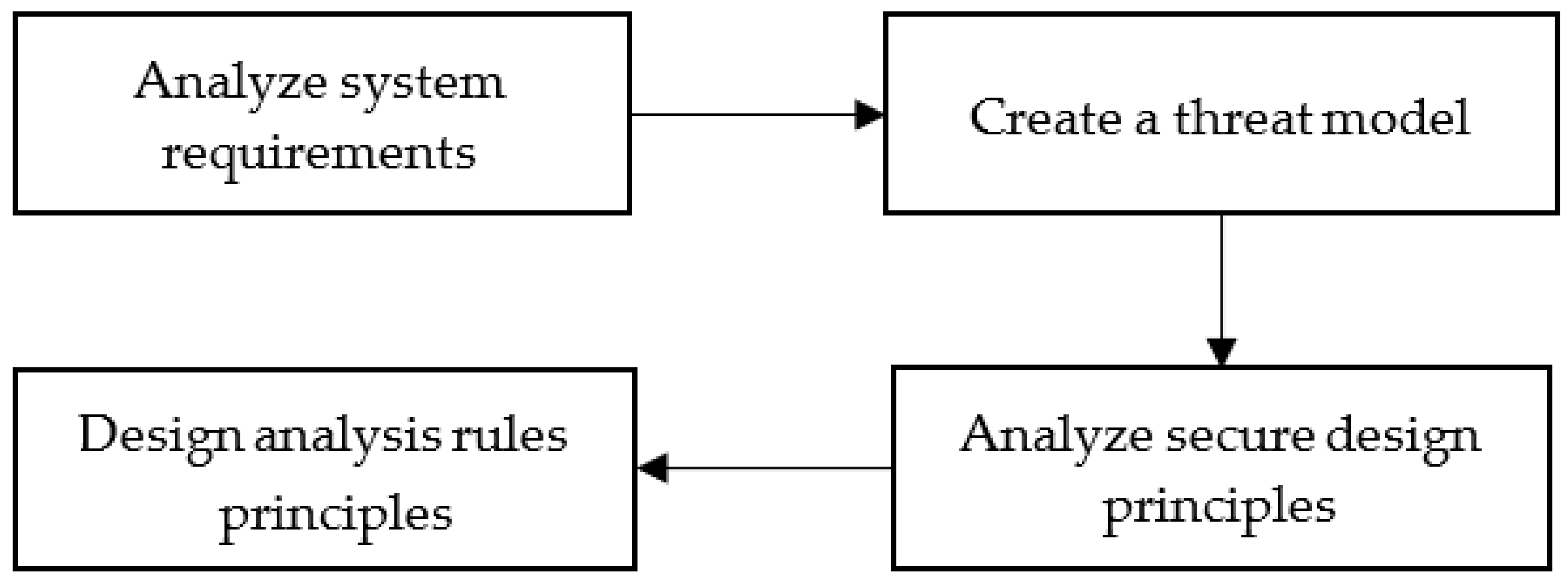
3.1. Research Process
3.2. System Requirements Analysis
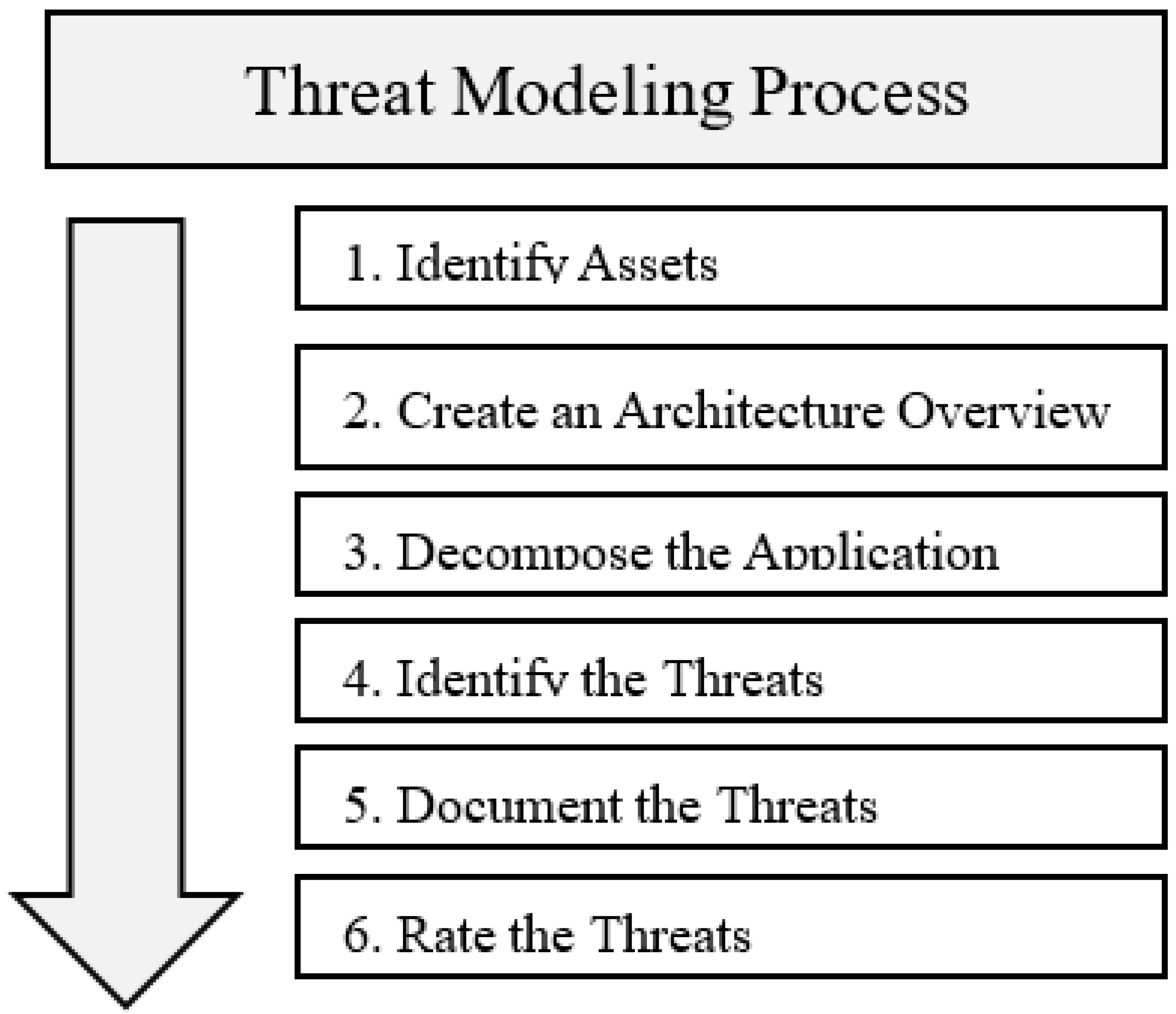
3.3. Threat Modeling Process
3.4. Analysis of Security Design Principles
- Consume System Resources: Programs uploaded by users may consume many system resources.
- Injection Attack: Injection attacks may occur at all places in the system where users can input, and user login pages are often vulnerable to SQL injection attacks.
- Disrupt System Operation: The program uploaded by the user may disrupt the operation of the system.
- Brute Force Attacks: The place in the system needed to verify the identity may be subject to brute force attacks.
- Cross-Site Scripting: Cross-site scripting attacks may occur in all system places displaying user input information.
- Disclosure of Confidential Data: The system should avoid the leakage of test data, e.g., the program compilation and judge results, the execution environment, and the communication method of the program.
- Over-Privileged Application and Service Accounts: The principle of least privilege should be followed for the permission design of each user and service in the system to prevent attackers from compromising the system through users or services with excessive permissions.
- User Denies Performing an Operation: The system should record the user’s various operations to avoid the difficulty of checking the affected range and finding the attack method after the system is attacked. It can make the attacker deny its operation.
- Attacker Reveals Implementation Details: If exceptions occur during system operation, detailed error information should be avoided from being sent back to the user. Additionally, when an error occurs when the system compiles and executes the program uploaded by the user, the information returned to the user should also avoid very detailed information, such as system environment information.
- Cookie Manipulation: The system should set the attributes of cookies to HttpOnly and Secure and require the user to re-enter the password when performing sensitive operations to prevent attackers from easily obtaining other people’s cookies.
- Session Hijacking: The system should avoid transmitting the session ID through the URL and avoid cookie leakage to prevent attackers from obtaining the session ID and pretending to be other users.
- Man In the Middle: The system should use HTTPS to transmit data to prevent attackers from intercepting packets.
3.5. Analysis of Code Analysis Rules
4. Practice and Case Study
4.1. System Architecture Diagram
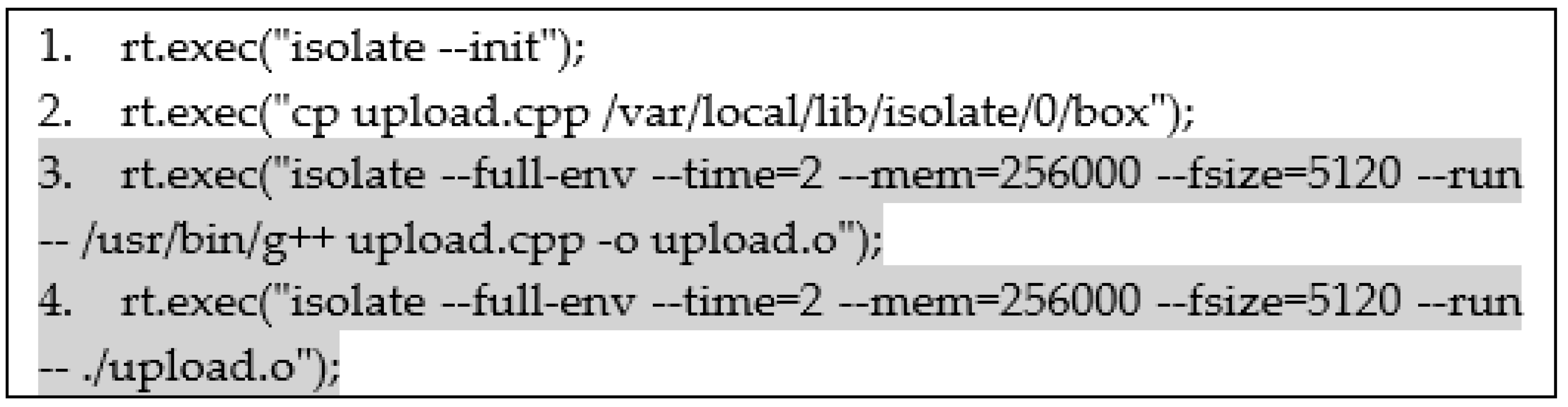
4.2. Sandbox Execution Command Acquisition
- STRING_LITERAL: When the parameter type is STRING_LITERAL, the tree node is directly parsed as a string constant. The processing code fragment is shown in Figure 4.
- 2.
- PLUS: When the parameter type is PLUS, the processing code fragment is as shown in Figure 5, and the details are as follows.
- 3.
- IDENTIFIER: When the parameter type is IDENTIFIER, the processing code fragment is as shown in Figure 6, and the details are as follows.
- 4.
- NEW_ARRAY: When the parameter type is NEW_ARRAY, the processing code fragment is as shown in Figure 7, and the details are as follows.
- 5.
- METHOD_INVOCATION: When the parameter type is METHOD_INVOCATION, the processing code fragment is as shown in Figure 8, and the details are as follows.
4.3. Implementation of Analysis Rules
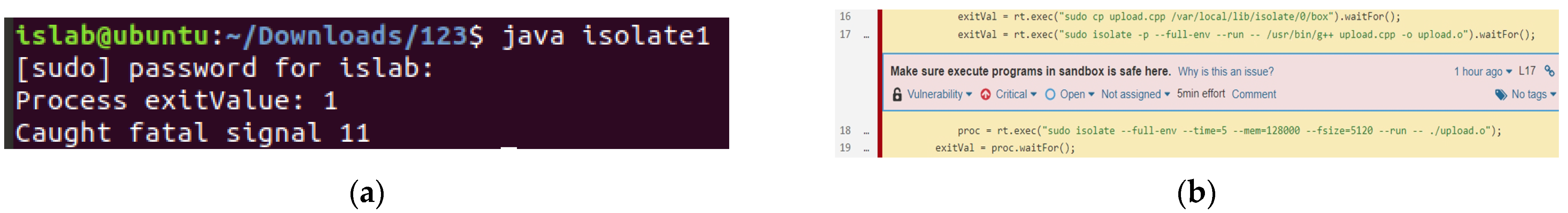
- Control groups are not enabled, and multiple processes are not allowed: In this case, the judge system should limit the execution time, memory usage, and hard disk space of the sandbox. Figure 9 shows the code fragment violating this rule.
- 2.
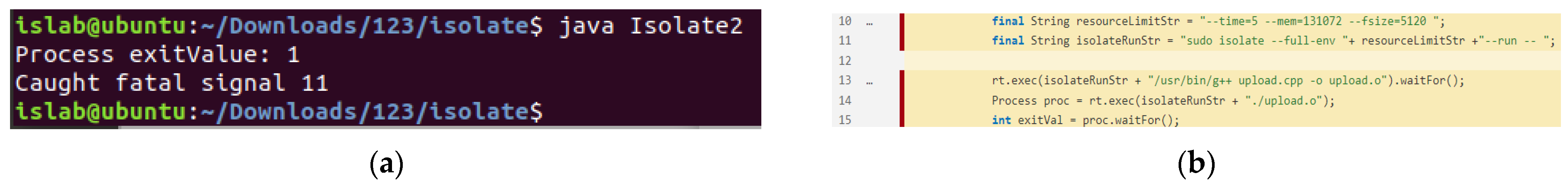
- Control groups are not enabled, and multiple processes are allowed: When the Control Group is not enabled, the sandbox can only limit the use of resources for each process and cannot limit the resources used by the sum of multiple processes. In this case, if multiple processes are allowed to execute, an attacker can circumvent the sandbox resource limitation by creating multiple processes in the program execution.
- 3.
- Control groups are enabled and multiple processes are not allowed: In this case, the point to note is the same as in the first case. The judge system should limit the sandbox execution time, memory usage, or hard disk space.
- 4.
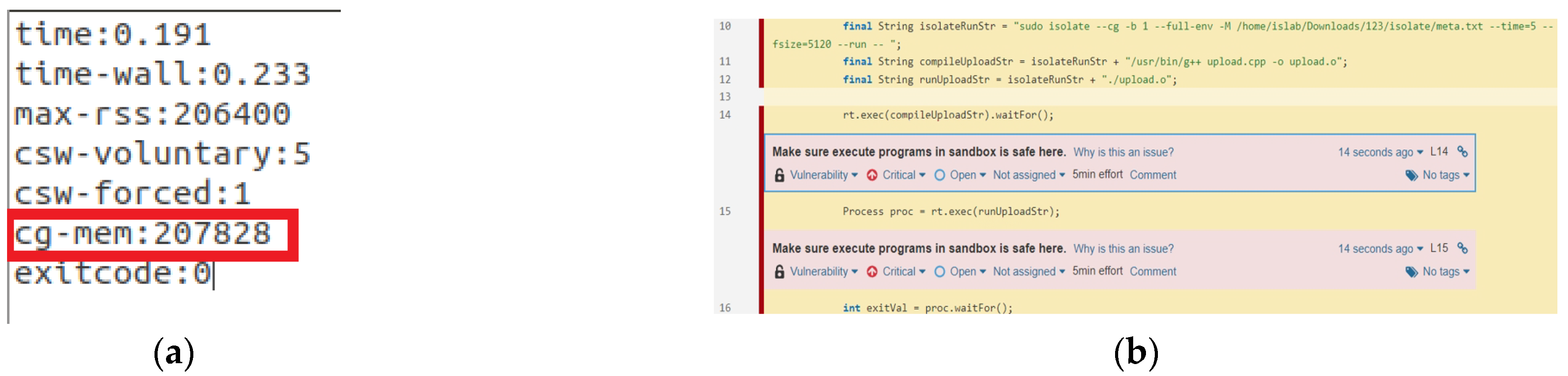
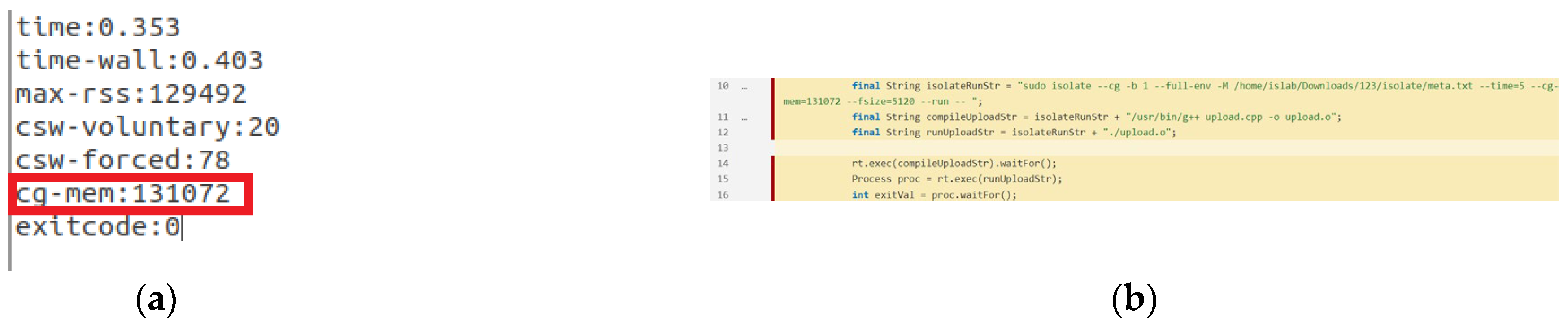
- Control groups are enabled and multiple processes are allowed: In this case, the use of resources by the sandbox should also be limited. Special attention should be paid to the memory limit. It is necessary to limit the memory usage of the entire control group. Figure 11 presents a code fragment that violates the rules.
4.4. Case Study
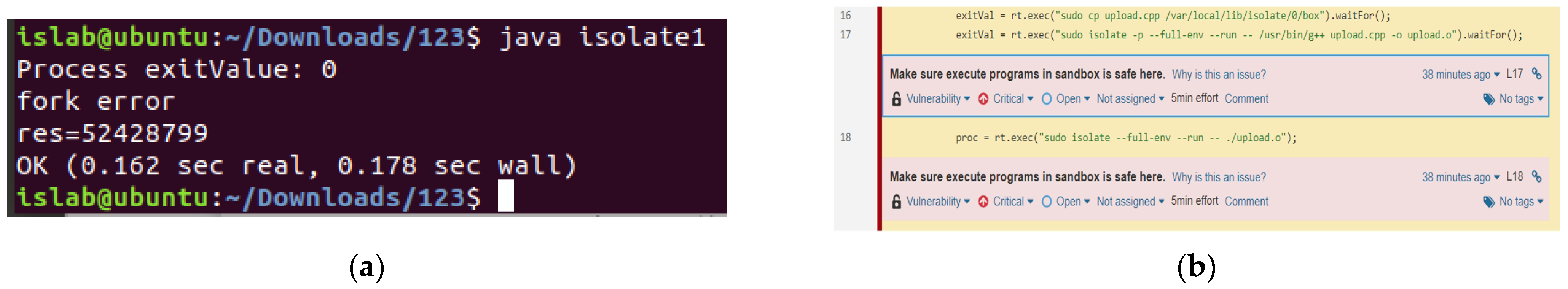
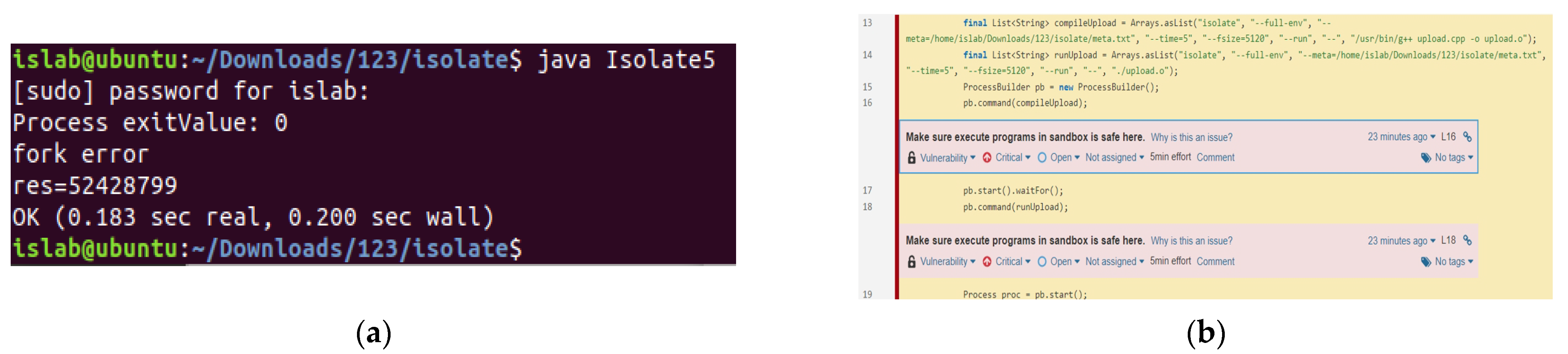
- Version 1: When the control group is disabled, multiple processes are not permitted, and system resources are not regulated; the execution result is depicted in Figure 14. The program runs the experimental C++ program in the sandbox successfully. This version is evaluated using the code analysis tool, and the argument type provided in lines 16–18 is a single string. Lines 17–18 of this program do not limit the sandbox’s resource use while building and running a C++ application in the sandbox.
- 2.
- Version 2: Figure 16 depicts the execution outcome without activating control groups, allowing numerous processes to execute, and not restricting the usage of system resources. The program was able to successfully run the experimental C++ program in the sandbox. This version is evaluated using the code analysis tool; the string on line 12 is the concatenation of the string variable; and the arguments passed on lines 13 and 14 are the strings on line 12.
- 3.
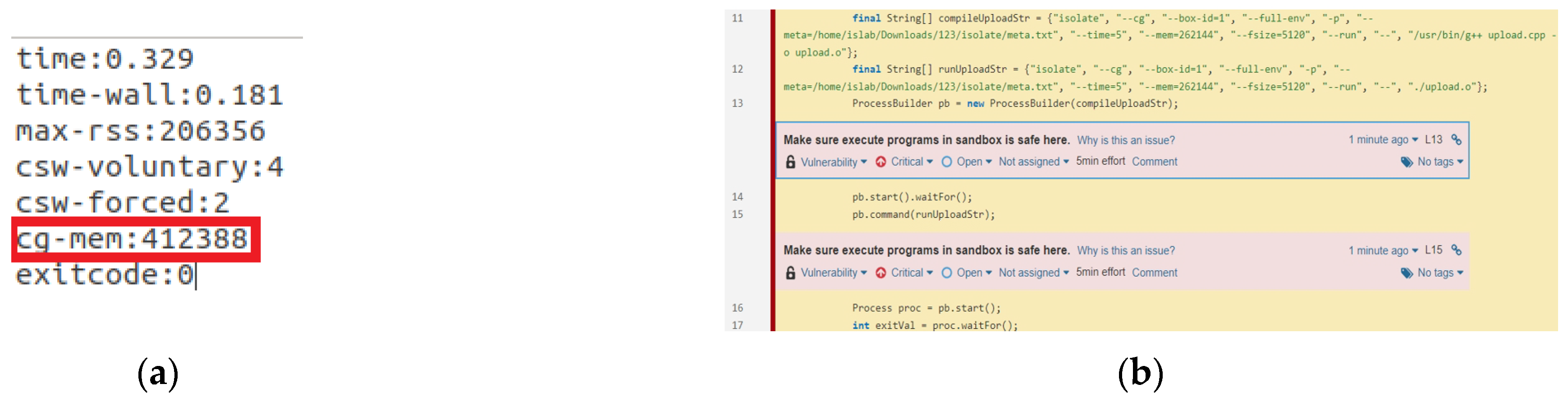
- Version 3: The control group is activated, many processes cannot run at the same time, and memory use is not limited. Figure 18 depicts the execution outcome. The program execution status given by the sandbox is examined once it has been executed. The control group’s memory use has reached about 203 MB, as shown in Figure 18a, marked by a red border. Finally, the updated code is examined and lines 14–15 remain unaffected.
- 4.
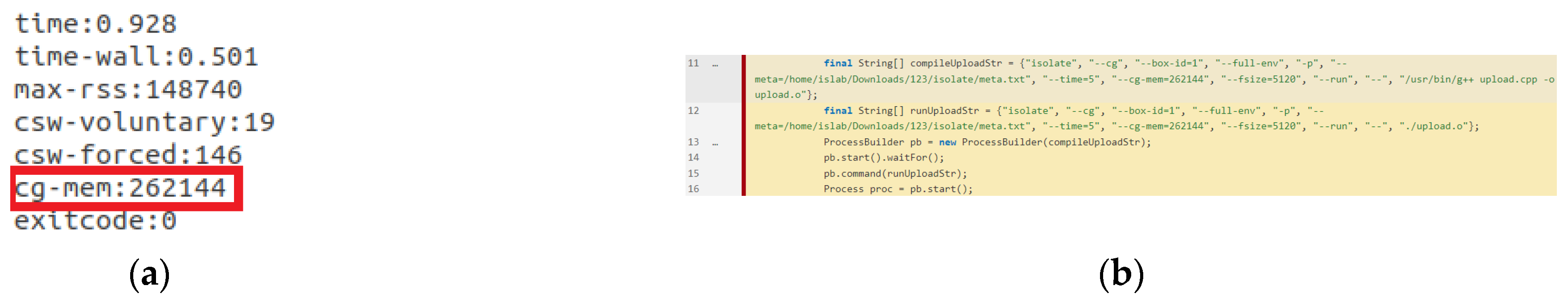
- Version 4: The control group is activated, enabling many processes to run and not restricting memory use via the control group. The execution result is displayed in Figure 20. The program execution status reported by the sandbox is examined after it has been executed. The control group’s memory use reaches about 403 MB, as shown in Figure 20a marked by a red border. The code analysis tool is used to examine this version. The arguments passed on lines 13 and 15 are the string arrays on lines 11 and 12, respectively. Memory is only limited for each process when the sandbox is utilized in lines 13 and 15 of this program, and no control group is used to restrict it.
- 5.
- Version 5: Figure 22 depicts the execution outcome when the control group is disabled, numerous processes are not permitted to run, and memory use is not regulated. The execution is successful when the program employs the sandbox to run the experimental C++ program. The code analysis tool is used to examine this version, and the arguments passed on lines 16 and 18 are the string lists on lines 13 and 14, respectively. When utilizing the sandbox, lines 16 and 18 of these programs do not limit memory utilization.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kurnia, A.; Lim, A.; Cheang, B. Online judge. Comput. Educ. 2001, 36, 299–315. [Google Scholar] [CrossRef]
- Hong, H.; Sun, Z. TS-ABOS-CMS: Time-bounded secure attribute-based online/offline signature with constant message size for IoT systems. J. Syst. Archit. 2022, 123, 102388. [Google Scholar] [CrossRef]
- Mustafa, M.; Buttar, A.M.; Sajja, G.S.; Gour, S.; Naved, M.; William, P. Multitask Learning for Security and Privacy in IoV (Internet of Vehicles). In Autonomous Vehicles Volume 1: Using Machine Intelligence; IGI Global: Hershey, PA, USA, 2022; pp. 217–233. [Google Scholar]
- Mustafa, M.; Alshare, M.; Bhargava, D.; Neware, R.; Singh, B.; Ngulube, P. Perceived security risk based on moderating factors for blockchain technology applications in cloud storage to achieve secure healthcare systems. Comput. Math. Methods Med. 2022, 2022, 6112815. [Google Scholar] [CrossRef] [PubMed]
- Forišek, M. Security of programming contest systems. Inf. Technol. Sch. 2006, 553–563. Available online: https://www.google.com.hk/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&ved=2ahUKEwj8g_fg_oKAAxWI0GEKHRArB-kQFnoECAsQAQ&url=https%3A%2F%2Fpeople.ksp.sk%2F~misof%2Fpublications%2Fcopy%2F2006attacks.pdf&usg=AOvVaw0n9T9092mp0Rl25bdHy8oC&opi=89978449 (accessed on 2 July 2023).
- Sims, R.W. Secure Execution of Student Code. In Technical Report of Department of Computer Science; University of Maryland: College Park, MD, USA, 2012. [Google Scholar]
- Mareš, M. Security of Grading Systems. Olymp. Inform. 2021, 15, 37–52. [Google Scholar] [CrossRef]
- Yi, C.; Feng, S.; Gong, Z. A comparison of sandbox technologies used in online judge systems. Appl. Mech. Mater. 2014, 490–491, 1201–1204. [Google Scholar] [CrossRef]
- Gong, L.; Mueller, M.; Prafullchandra, H.; Schemers, R. Going Beyond the Sandbox: An Overview of the New Security Architecture in the Java Development Kit™ 1.2. In Proceedings of the USENIX Symposium on Internet Technologies and Systems, Monterey, CA, USA, 8–11 December 1997; pp. 102–112. [Google Scholar]
- Mareš, M.; Blackham, B. A New Contest Sandbox. Olymp. Inform. 2012, 6, 100–109. [Google Scholar]
- National Cyber Awareness System. Security Tip (ST04-015): Understanding Denial-of-Service Attacks. 2009. Available online: https://www.cisa.gov/uscert/ncas/tips/ST04-015 (accessed on 15 March 2022).
- Wei, J.; Pu, C. TOCTTOU Vulnerabilities in UNIX-Style File Systems: An Anatomical Study. In Proceedings of the FAST ′05 Conference on File and Storage Technologies, San Francisco, CA, USA, 13–16 December 2005. [Google Scholar]
- Lampson, B. A note on the confinement problem. Commun. ACM 1973, 16, 613–615. [Google Scholar] [CrossRef]
- Tsafrir, D.; Etsion, Y.; Feitelson, D.G. Secretly monopolizing the CPU without superuser privileges. In Proceedings of the USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007; pp. 239–256. [Google Scholar]
- Ishkov, N. A Complete Guide to Linux Process Scheduling. Master’s Thesis, Tampere University, Tampere, Finland, 2015. [Google Scholar]
- MITRE ATT&CK. Available online: https://attack.mitre.org/ (accessed on 27 May 2023).
- OWASP. Threat Modeling. Available online: https://owasp.org/www-community/Application_Threat_Modeling (accessed on 19 June 2022).
- Meier, J.D.; Mackman, A.; Vasireddy, S.; Dunner, M.; Escamilla, R.; Murukan, A. Introduction to Threats and Countermeasures. In Improving Web Application Security: Threats and Countermeasures; Microsoft: Redmond, WA, USA, 2003; pp. 3–66. [Google Scholar]
- Microsoft. The STRIDE Threat Model. Available online: https://docs.microsoft.com/en-us/previous-versions/commerce-server/ee823878(v=cs.20) (accessed on 10 June 2022).
- Kohnfelder, L.; Garg, P. The Threats to Our Products; Microsoft: Redmond, WA, USA, 1999. [Google Scholar]
- Signal (7)—Linux Manual Page. Available online: https://man7.org/linux/man-pages/man7/signal.7.html (accessed on 19 June 2022).












| Functional Requirements | Description |
|---|---|
| Post questions | Teachers may create questions and write question descriptions based on their needs, as well as specify the programming language, program execution time restriction, and upload period. |
| Design test data | Teachers can produce numerous sets of data to examine the questions they create. Input data and predicted output outcomes are included in the test data. |
| Upload program | After students develop a program in response to the question requirements, they can submit the program code to the system, and the system judges the program’s validity. |
| Verify program correctness | The system can verify the correctness of the programs supplied by students based on the test data. |
| Query program correctness | Students can check the verified results of the uploaded programs. |
| Threat | Attacks |
|---|---|
| Consume System Resources | Denial-of-Service attack |
| Disrupt System Operation | Denial-of-Service attack |
| Over-Privileged Application and Service Accounts | Cross-language attack |
| Sensitive Information Leakage | Covert channel |
| TOCTTOU |
| Class | Constructor or Method |
|---|---|
| java.lang.Runtime | Exec () |
| java.lang.ProcessBuilder | Constructor |
| Command () |
| Ver. | Input Command Method | Command Parameter Type | Sandbox Usage Scenarios | |
|---|---|---|---|---|
| Enable CG | Allow Multi-Process | |||
| 1 | Runtime.getRuntime(). exec | STRING_LITERAL | no | no |
| 2 | Runtime.getRuntime(). exec | PLUS | no | yes |
| 3 | Runtime.getRuntime(). exec | IDENTIFIER | yes | no |
| 4 | ProcessBuilder () | NEW_ARRAY | yes | yes |
| 5 | ProcessBuilder.command() | METHOD_INVOCATION | no | no |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kuo, J.-Y.; Wen, Z.-J.; Hsieh, T.-F.; Huang, H.-X. A Study on the Security of Online Judge System Applied Sandbox Technology. Electronics 2023, 12, 3018. https://doi.org/10.3390/electronics12143018
Kuo J-Y, Wen Z-J, Hsieh T-F, Huang H-X. A Study on the Security of Online Judge System Applied Sandbox Technology. Electronics. 2023; 12(14):3018. https://doi.org/10.3390/electronics12143018
Chicago/Turabian StyleKuo, Jong-Yih, Zhi-Jia Wen, Ti-Feng Hsieh, and Han-Xuan Huang. 2023. "A Study on the Security of Online Judge System Applied Sandbox Technology" Electronics 12, no. 14: 3018. https://doi.org/10.3390/electronics12143018
APA StyleKuo, J.-Y., Wen, Z.-J., Hsieh, T.-F., & Huang, H.-X. (2023). A Study on the Security of Online Judge System Applied Sandbox Technology. Electronics, 12(14), 3018. https://doi.org/10.3390/electronics12143018






