Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions through Machine Learning Tools in Cloud Computing Environment
Abstract
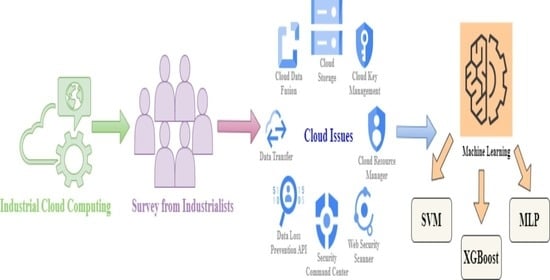
:1. Introduction
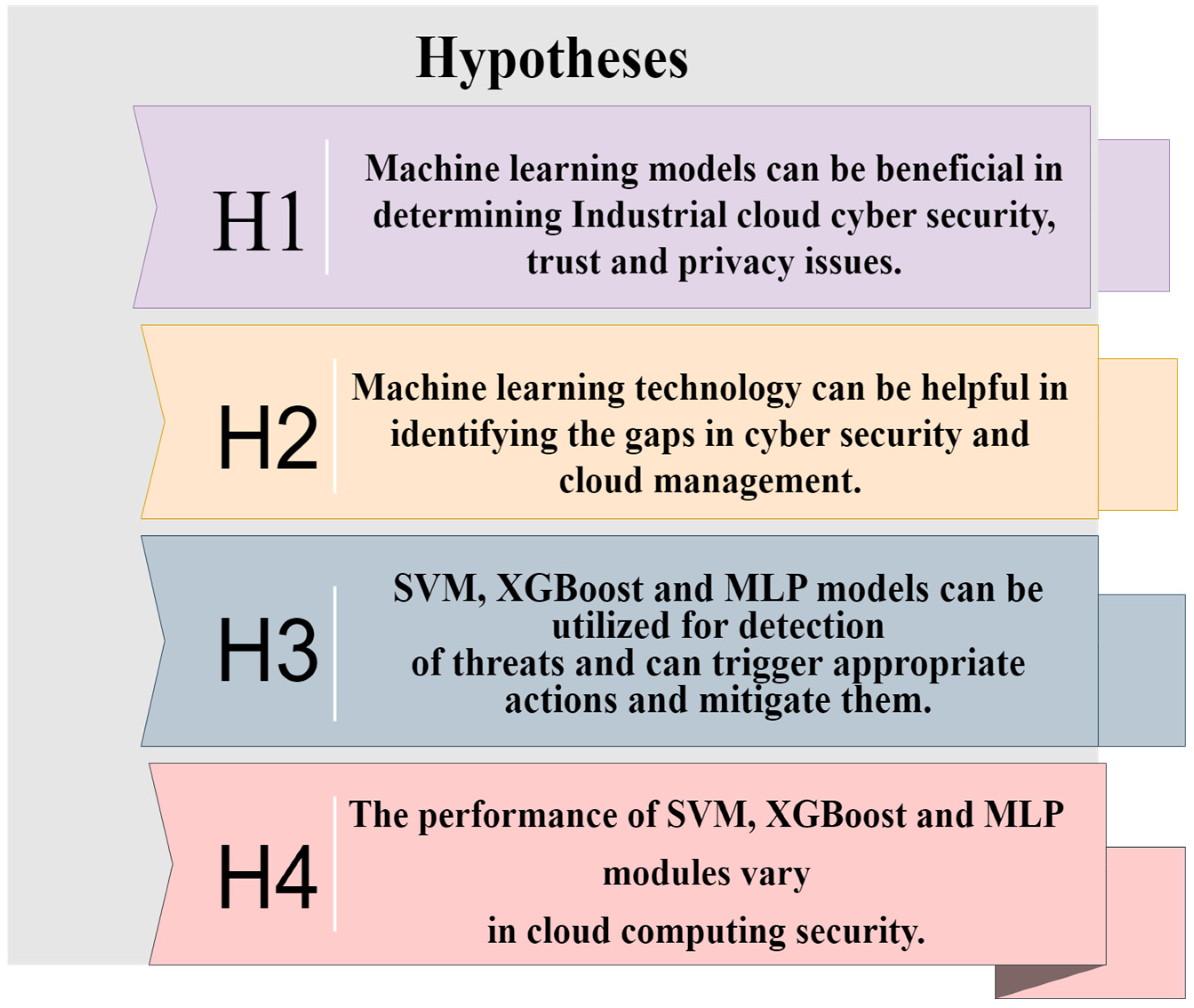
2. Literature Review
- Use ML models to sermonize industrial cloud cyber security, trust, and privacy issues.
- Identification of gaps in utilizing the ML approaches for cloud security.
- Detection and mitigation of security threats.
- Triggering appropriate security actions.
- Comparison of the performance of SVM, X.G.B., and ANN models in cloud computing security.
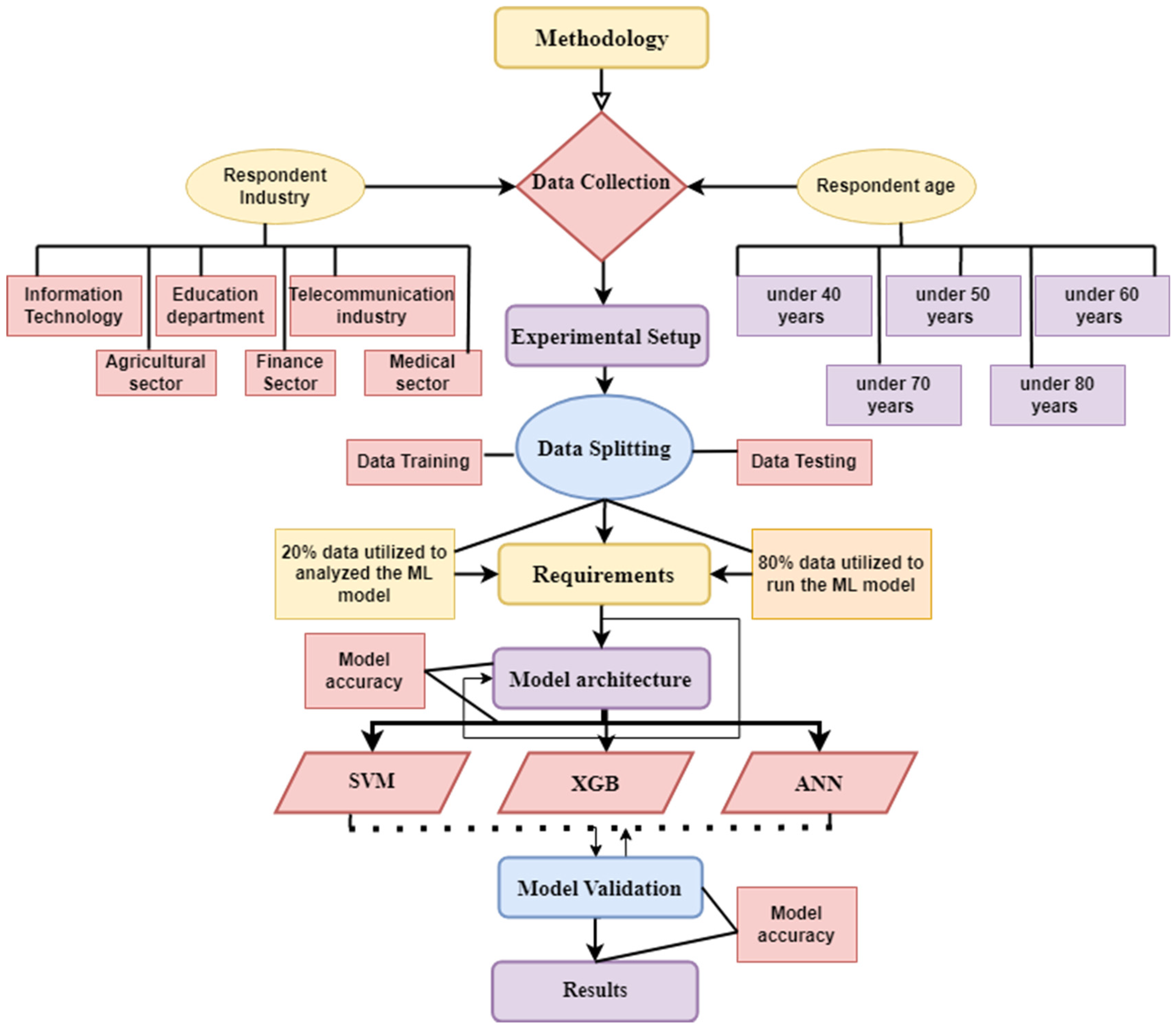
3. Methodology
3.1. Data Collection
3.2. Experimental Setup
3.3. Data Splitting
3.4. Requirements
3.5. Model’s Architecture
3.5.1. Support Vector Machine (SVM)
3.5.2. Gradient Boosting Model
3.5.3. Artificial Neural Networks
3.6. Evaluation Matrices
4. Results and Discussion
4.1. Features Selection
4.2. ML Analysis
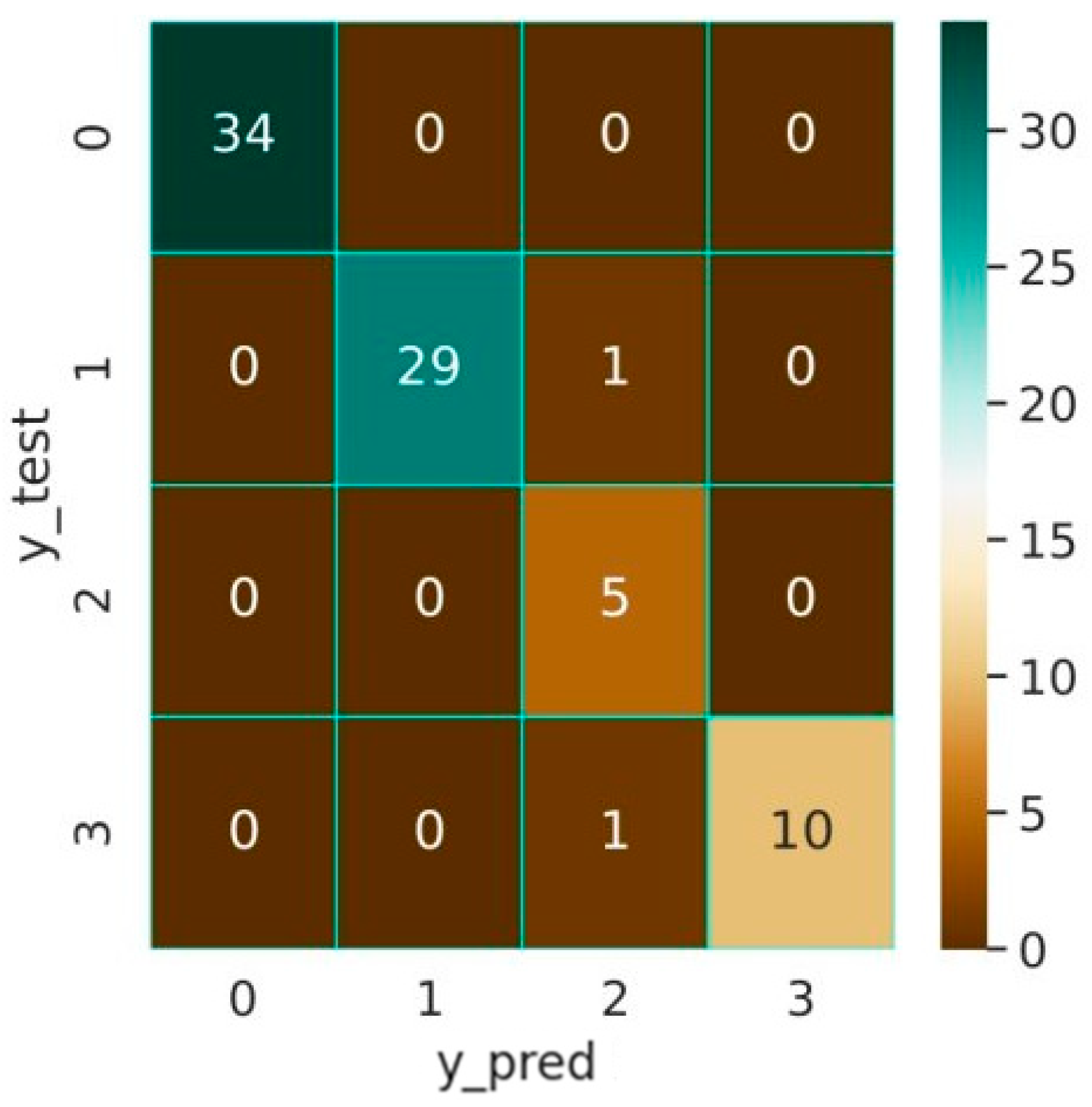
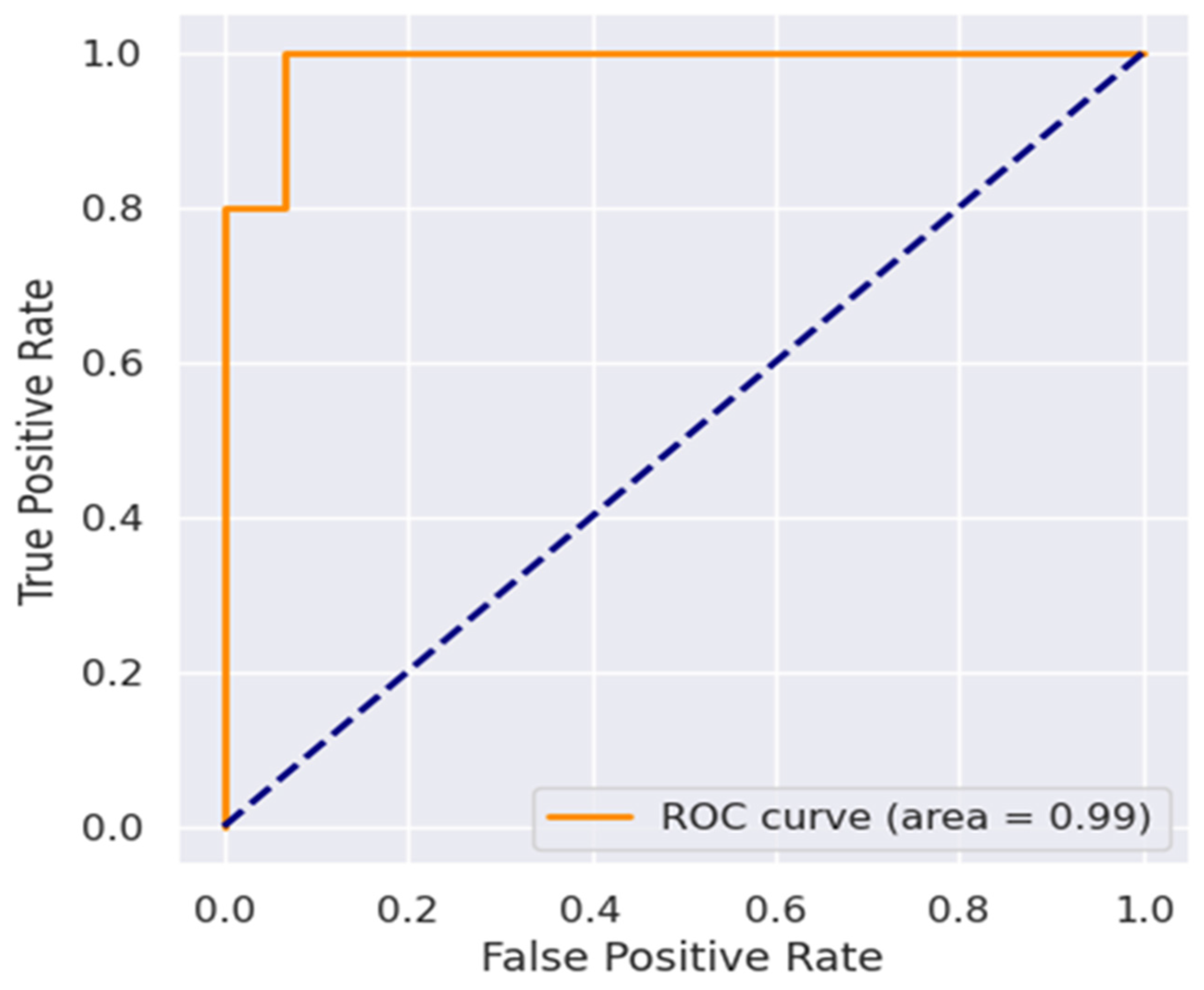
4.2.1. XGB Model
4.2.2. SVM Model
4.2.3. MLP Model
5. Conclusions and Suggestions
Supplementary Materials
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nassif, A.B.; Abu Talib, M.; Nasir, Q.; Albadani, H.; Dakalbab, F.M. Machine learning for cloud security: A systematic review. IEEE Access 2021, 9, 20717–20735. [Google Scholar] [CrossRef]
- Aljumah, A.; Ahanger, T.A. Cyber security threats, challenges and defense mechanisms in cloud computing. IET Commun. 2020, 14, 1185–1191. [Google Scholar] [CrossRef]
- Sandesh, A. Cloud Computing Security for Multi-Cloud Service Providers: Controls and Techniques in our Modern Threat Landscape. Int. J. Comput. Syst. Eng. 2022, 16, 379–384. [Google Scholar]
- Brandao, P.R. Bases, Challenges, and Main Dangers for Deploying Cybersecurity in Industry 4.0. Adv. Wirel. Commun. Netw. 2019, 5, 33. [Google Scholar] [CrossRef]
- Butt, U.A.; Mehmood, M.; Shah, S.B.H.; Amin, R.; Shaukat, M.W.; Raza, S.M.; Suh, D.Y.; Piran, J. A review of machine learning algorithms for cloud computing security. Electronics 2020, 9, 1379. [Google Scholar] [CrossRef]
- Jupalle, H.; Kouser, S.; Bhatia, A.B.; Alam, N.; Nadikattu, R.R.; Whig, P. Automation of human behaviors and its prediction using machine learning. Microsyst. Technol. 2022, 28, 1879–1887. [Google Scholar] [CrossRef]
- Qayyum, A.; Ijaz, A.; Usama, M.; Iqbal, W.; Qadir, J.; Elkhatib, Y.; Al-Fuqaha, A. Securing machine learning in the cloud: A systematic review of cloud machine learning security. Front. Big Data 2020, 3, 587139. [Google Scholar] [CrossRef]
- Bhamare, D.; Salman, T.; Samaka, M.; Erbad, A.; Jain, R. Feasibility of supervised machine learning for cloud security. In Proceedings of the 2016 International Conference on Information Science and Security (ICISS), IEEE, Jaipur, India, 19–22 December 2016. [Google Scholar]
- O’donovan, P.; Gallagher, C.; Leahy, K.; O’sullivan, D.T. A comparison of fog and cloud computing cyber-physical interfaces for Industry 4.0 real-time embedded machine learning engineering applications. Comput. Ind. 2019, 110, 12–35. [Google Scholar] [CrossRef]
- Behl, A. Emerging security challenges in cloud computing: An insight into cloud security challenges and their mitigation. In Proceedings of the 2011 World Congress on Information and Communication Technologies, IEEE, Innsbruck, Austria, 11–14 December 2011. [Google Scholar]
- Hassan, W.; Chou, T.-S.; Tamer, O.; Pickard, J.; Appiah-Kubi, P.; Pagliari, L. Cloud computing survey on services, enhancements, and challenges in the era of machine learning and data science. Int. J. Inform. Commun. Technol. 2020, 9, 117–139. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities, and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Ige, T.; Sikiru, A. Implementation of data mining on secure cloud computing over a web API using a supervised machine learning algorithm. In Proceedings of the Artificial Intelligence Trends in Systems: Proceedings of 11th Computer Science On-Line Conference 2022; Springer: Berlin/Heidelberg, Germany, 2022; Volume 2. [Google Scholar]
- Mozumder, D.P.; Mahi, M.J.N.; Whaiduzzaman, M. Cloud computing security breaches and threats analysis. Int. J. Sci. Eng. Res. 2017, 8, 1287–1297. [Google Scholar]
- Kazim, M.; Zhu, S.Y. A survey on top security threats in cloud computing. Int. J. Adv. Comput. Sci. Appl. 2015, 6, 109–113. [Google Scholar] [CrossRef] [Green Version]
- Tandon, R. A survey of distributed denial of service attacks and defenses. arXiv 2020, arXiv:2008.01345. [Google Scholar]
- Khalid, A.; Khan, Z.H.; Idrees, M.; Kirisci, P.; Ghrairi, Z.; Thoben, K.-D.; Pannek, J. Understanding vulnerabilities in cyber-physical production systems. Int. J. Comput. Integr. Manuf. 2022, 35, 569–582. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.A.; Noura, H.N.; Salman, O.; Chehab, A. Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. Int. J. Inf. Secur. 2022, 21, 115–158. [Google Scholar] [CrossRef] [PubMed]
- Vinoth, S.; Vemula, H.L.; Haralayya, B.; Mamgain, P.; Hasan, M.F.; Naved, M. Application of cloud computing in banking and e-commerce and related security threats. Mater. Today Proc. 2022, 51, 2172–2175. [Google Scholar] [CrossRef]
- Alsmadi, I.; Dwekat, Z.; Cantu, R.; Al-Ahmad, B. Vulnerability assessment of industrial systems using Shodan. Clust. Comput. 2022, 25, 1563–1573. [Google Scholar] [CrossRef]
- Zahariev, P.; Hristov, G.; Kinaneva, D.; Chaisricharoen, R.; Georgiev, G.; Stoilov, P. A review of the main characteristics and security vulnerabilities of the wireless communication technologies in the Industry 4.0 domain. In Proceedings of the 2022 Joint International Conference on Digital Arts, Media, and Technology with ECTI Northern Section Conference on Electrical, Electronics, Computer and Telecommunications Engineering (ECTI DAMT & NCON), IEEE, online. 26–28 January 2022. [Google Scholar]
- Karunasingha, D.S.K. Root mean square error or mean absolute error? Use their ratio as well. Inf. Sci. 2022, 585, 609–629. [Google Scholar] [CrossRef]
- Xing, J.; Zhang, Z. Hierarchical network security measurement and optimal proactive defense in cloud computing environments. Secur. Commun. Netw. 2022, 2022, 6783223. [Google Scholar] [CrossRef]
- Ukwandu, E.; Ben-Farah, M.A.; Hindy, H.; Bures, M.; Atkinson, R.; Tachtatzis, C.; Andonovic, I.; Bellekens, X. Cyber-security challenges in the aviation industry: A review of current and future trends. Information 2022, 13, 146. [Google Scholar] [CrossRef]
- Takabi, H.; Joshi, J.B.; Ahn, G.-J. Security and privacy challenges in cloud computing environments. IEEE Secur. Priv. 2010, 8, 24–31. [Google Scholar] [CrossRef]
- Subramanian, E.; Tamilselvan, L. A focus on the future cloud: Machine learning-based cloud security. Serv. Oriented Comput. Appl. 2019, 13, 237–249. [Google Scholar] [CrossRef]
- Kim, H.; Kim, J.; Kim, Y.; Kim, I.; Kim, K.J. Design of network threat detection and classification based on machine learning on cloud computing. Clust. Comput. 2019, 22, 2341–2350. [Google Scholar] [CrossRef]
- Kwabena, O.-A.; Qin, Z.; Zhuang, T.; Qin, Z. Mscryptonet: Multi-scheme privacy-preserving deep learning in cloud computing. IEEE Access 2019, 7, 29344–29354. [Google Scholar] [CrossRef]
- Gupta, I.; Gupta, R.; Singh, A.K.; Buyya, R. MLPAM: A machine learning and probabilistic analysis based model for preserving security and privacy in a cloud environment. IEEE Syst. J. 2020, 15, 4248–4259. [Google Scholar] [CrossRef]
- Abbas, Z.; Myeong, S. Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions Through Machine Learning Tools in Cloud Computing Environment. Preprints 2023. [Google Scholar] [CrossRef]
- Thakkar, A.; Lohiya, R. A review on machine learning and deep learning perspectives of IDS for IoT: Recent updates, security issues, and challenges. Arch. Comput. Methods Eng. 2021, 28, 3211–3243. [Google Scholar] [CrossRef]
- Kuwajima, H.; Yasuoka, H.; Nakae, T. Engineering problems in machine learning systems. Mach. Learn. 2020, 109, 1103–1126. [Google Scholar] [CrossRef] [Green Version]
- Kumar, R.S.S.; Wicker, A.; Swann, M. Practical machine learning for cloud intrusion detection: Challenges and the way forward. In Proceedings of the 10th ACM Workshop on Artificial Intelligence and Security; Association for Computing Machinery: New York, NY, USA, 2017. [Google Scholar]
- Chkirbene, Z.; Erbad, A.; Hamila, R.; Gouissem, A.; Mohamed, A.; Hamdi, M. Machine learning based cloud computing anomalies detection. IEEE Netw. 2020, 34, 178–183. [Google Scholar] [CrossRef]
- Kumar, B.; Roy, S.; Singh, K.U.; Pandey, S.K.; Kumar, A.; Sinha, A.; Shukla, S.; Shah, M.A.; Rasool, A. A Static Machine Learning Based Evaluation Method for Usability and Security Analysis in E-Commerce website. IEEE Access 2023, 40488–40510. [Google Scholar] [CrossRef]
- Kandi, P.; Tarapatla, S.R.; Kumar, S.; Kadiyam, H.; Chowdary, D.; Moparthi, N.R. A Review: Data Security in Cloud Computing Using Machine Learning. In Proceedings of the 2022 5th International Conference on Contemporary Computing and Informatics (IC3I), IEEE, Cairo, Egypt, 14–16 December 2022. [Google Scholar]
- Mohammad, A.S.; Pradhan, M.R. Machine learning with big data analytics for cloud security. Comput. Electr. Eng. 2021, 96, 107527. [Google Scholar] [CrossRef]
- Bandari, V. Enterprise Data Security Measures: A Comparative Review of Effectiveness and Risks Across Different Industries and Organization Types. Int. J. Bus. Intell. Big Data Anal. 2023, 6, 1–11. [Google Scholar]
- Harmon, R.L.; Psaltis, A. The future of cloud computing in financial services: A machine learning and artificial intelligence perspective. In The Essentials of Machine Learning in Finance and Accounting; Routledge: Abingdon, UK, 2021; pp. 123–138. [Google Scholar]
- Liu, J.; Wang, X.; Shen, S.; Yue, G.; Yu, S.; Li, M. A Bayesian Q-learning game for dependable task offloading against DDoS attacks in sensor edge cloud. IEEE Internet Things J. 2020, 8, 7546–7561. [Google Scholar] [CrossRef]
- Yu, Z.; Hu, J.; Min, G.; Wang, Z.; Miao, W.; Li, S. Privacy-preserving federated deep learning for cooperative hierarchical caching in fog computing. IEEE Internet Things J. 2021, 9, 22246–22255. [Google Scholar] [CrossRef]
- Marwan, M.; Kartit, A.; Ouahmane, H. Security enhancement in healthcare cloud using machine learning. Procedia Comput. Sci. 2018, 127, 388–397. [Google Scholar] [CrossRef]
- Praveena, D.; Rangarajan, P. A machine learning application for reducing the security risks in hybrid cloud networks. Multimed. Tools Appl. 2020, 79, 5161–5173. [Google Scholar] [CrossRef]
- Tabassum, N.; Alyas, T.; Hamid, M.; Saleem, M.; Malik, S.; Zahra, S.B. Qos-based cloud security evaluation using the neuro-fuzzy model. Comput. Mater. Contin. 2022, 70, 1127–1140. [Google Scholar] [CrossRef]
- Salman, T.; Bhamare, D.; Erbad, A.; Jain, R.; Samaka, M. Machine learning for anomaly detection and categorization in multi-cloud environments. In Proceedings of the 2017 IEEE 4th International Conference on Cyber Security and Cloud Computing (CSCloud), IEEE, New York, NY, USA, 26–28 June 2017. [Google Scholar]
- Mishra, S.; Tyagi, A.K. The role of machine learning techniques in the Internet of things-based cloud applications. In Artificial Intelligence-Based Internet of Things Systems; Springer: Cham, Switzerland, 2022; pp. 105–135. [Google Scholar]
- Friesen, M.; Wisniewski, L.; Jasperneite, J. Machine Learning for Zero-Touch Management in Heterogeneous Industrial Networks-A Review. In Proceedings of the 2022 IEEE 18th International Conference on Factory Communication Systems (WFCS), IEEE, online. 27–29 April 2022. [Google Scholar]
- Arzo, S.T.; Naiga, C.; Granelli, F.; Bassoli, R.; Devetsikiotis, M.; Fitzek, F.H.P. A theoretical discussion and survey of network automation for IoT: Challenges and opportunity. IEEE Internet Things J. 2021, 8, 12021–12045. [Google Scholar] [CrossRef]
- Jose, J.; Jose, D.V.; Rao, K.S.; Janz, J. Impact of Machine Learning Algorithms in Intrusion Detection Systems for Internet of Things. In Proceedings of the 2021 International Conference on Advances in Computing and Communications (ICACC), IEEE, Kochi, India, 21–23 October 2021. [Google Scholar]
- Alsharif, M.; Rawat, D.B. Study of machine learning for cloud-assisted iot security as a service. Sensors 2021, 21, 1034. [Google Scholar] [CrossRef]
- Masetic, Z.; Hajdarevic, K.; Dogru, N. Cloud computing threats classification model based on the detection feasibility of machine learning algorithms. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), IEEE, Opatija, Croatia, 22–26 May 2017. [Google Scholar]
- Vora, U.; Mahato, J.; Dasgupta, H.; Kumar, A.; Ghosh, S.K. Machine Learning–Based Security in Cloud Database—A Survey. In Machine Learning Techniques and Analytics for Cloud Security; Wiley: Hoboken, NJ, USA, 2021; pp. 239–269. [Google Scholar]
- Fontaine, J.; Kappler, J.; Shahid, A.; De Poorter, E. Log-based intrusion detection for cloud web applications using machine learning. In Advances on P2P, Parallel, Grid, Cloud and Internet Computing: Proceedings of the 14th International Conference on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC-2019); Springer: Berlin/Heidelberg, Germany, 2020; Volume 14. [Google Scholar]
- Kaur, K.; Zandu, V. Computing, A secure data classification model in cloud computing using machine learning approach. Int. J. Grid Distrib. Comput. 2016, 9, 13–22. [Google Scholar] [CrossRef]
- Auria, L.; Moro, R.A. Support Vector Machines (SVM) as a Technique for Solvency Analysis; DeutschesInstitut für Wirtschaftsforschung: Berlin, Germany, 2008. [Google Scholar]
- Xinfeng, Z.; Yan, Z. Application of support vector machine to reliability analysis of engine systems. TELKOMNIKA Indones. J. Electr. Eng. 2013, 11, 3552–3560. [Google Scholar] [CrossRef]
- Michalski, R.S.; Carbonell, J.G.; Mitchell, T.M. Machine Learning an Artificial Intelligence Approach; Springer: Berlin/Heidelberg, Germany, 1984. [Google Scholar]
- Singh, K.J.; De, T. MLP-GA based algorithm to detect application layer DDoS attack. J. Inf. Secur. Appl. 2017, 36, 145–153. [Google Scholar] [CrossRef]
- Ahakonye, L.A.C.; Nwakanma, C.I.; Lee, J.-M.; Kim, D.-S. Efficient classification of enciphered SCADA network traffic in a smart factory using decision tree algorithm. IEEE Access 2021, 9, 154892–154901. [Google Scholar] [CrossRef]
- Shon, T.; Moon, J. A hybrid machine learning approach to network anomaly detection. Inf. Sci. 2007, 177, 3799–3821. [Google Scholar] [CrossRef]
- Rabbani, M.; Wang, Y.L.; Khoshkangini, R.; Jelodar, H.; Zhao, R.; Hu, P. A hybrid machine learning approach for malicious behavior detection and recognition in cloud computing. J. Netw. Comput. Appl. 2020, 151, 102507. [Google Scholar] [CrossRef]
- Peddabachigari, S.; Abraham, A.; Thomas, J.P. Intrusion detection systems using decision trees and support vector machines. Int. J. Appl. Sci. Comput. 2004, 11, 118–134. [Google Scholar]
- Zimba, A.; Chen, H.; Wang, Z. Bayesian network-based weighted APT attack paths modeling in cloud computing. Future Gener. Comput. Syst. 2019, 96, 525–537. [Google Scholar] [CrossRef]
- Nie, L.; Jiang, D.; Lv, Z. Modeling network traffic for traffic matrix estimation and anomaly detection based on Bayesian network in cloud computing networks. Ann. Telecommun. 2017, 72, 297–305. [Google Scholar] [CrossRef]
- Kachavimath, A.V.; Narayan, D. A deep learning-based framework for distributed denial-of-service attacks detection in a cloud environment. In Advances in Computing and Network Communications: Proceedings of CoCoNet 2020; Springer: Berlin/Heidelberg, Germany, 2021; Volume 1. [Google Scholar]
- Meyer, D.; Leisch, F.; Hornik, K. The support vector machine under test. Neurocomputing 2003, 55, 169–186. [Google Scholar] [CrossRef]
- Jussila, S. Worksite Data Analysis Using Cloud Services for Machine Learning. Master’s Thesis, Tampere University, Tampere, Finland, 2019. [Google Scholar]
- Rai, A.K.; Dwivedi, R.K. Fraud detection in credit card data using machine learning techniques. In Machine Learning, Image Processing, Network Security and Data Sciences: Second International Conference, MIND 2020, Silchar, India, 30–31 July 2020; Proceedings, Part II 2; Springer: Singapore, 2020; pp. 369–382. [Google Scholar]





| Year | Study | Focus | Key Findings and Limitations |
|---|---|---|---|
| 2016 | Kaur et al. [32] | Data classification in cloud | Analysis of the security issues at authentication and storage. Development of data classification model. The author does not suggest any framework to solve the security concerns. |
| 2017 | Salman et al. [33] | Anomaly detection and classification | Detection of attacks and their classification by LR and RF. 99% detection and 93.6% classification accuracy by RF. It fails to categorize some attacks. |
| 2018 | Marwan et al. [34] | Healthcare cloud data security | Prevent unauthorized access to healthcare cloud data. Use of SVM and FCM for image pixel classification to ensure security. It only focuses on image segmentation for security and privacy and does not mention future challenges. |
| 2019 | Subramanian et al. [35] | Cloud cyber security | Avoidance of static nature for security verification of the cloud. Use of CNN model for automatic response to threats and saving enterprise data. It does not mention the type of threats, privacy, trust issues, and future challenges for the cyber cloud. |
| 2020 | Praveena et al. [36] | Hybrid cloud security | Reduction in security risks to hybrid cloud by enhanced C4.5 algorithm. Determination of the level of security during storing and authorizing data. The author does not discuss threats, trust issues, or future concerns for the hybrid cloud. |
| 2020 | Wang et al. [37] | DDOS attack detection | MLP-based model to detect DDOS attacks. Detection based on the feature selection and feedback mechanism to detect errors. The model is not able to find a globally optimized feature. The feedback mechanism can generate a false response. |
| 2020 | Chkirbene et al. [27] | Anomaly detection | Classification of scheme to protect the network from unwanted nodes. Reduction of incorrect data issues and differentiation of attacks. The author must discuss trust concerns, industrial cyber issues, and insufficient model comparison. |
| 2021 | Haseeb et al. [38] | Health industrial IoT security | Avoidance of uncertainty in data management of the health sector. Data protection by the EDM-ML approach ensures trust between networks. It does not compare the performance of models and does not mention prospects. |
| 2021 | Alsharif et al. [39] | IoT security | Use of ML-IDS to take account of traffic defects. The offloading of heavy tasks from the cloud. It does not study industrial cyber cloud concerns or issues regarding the use of the ML approach for the cloud. |
| 2022 | Tabassum et al. [33] | QoS security | Neuro-fuzzy approach to studying cloud security, reliability, and efficiency. Discussion of threats, security, and trust issues. No comparison of the model’s performance. |
| 2022 | Bangui et al. [40] | Threat detection in Vehicular Ad-hoc Networks (VANET) | Detection and prevention of intrusion in VANET. Use of RF and core set detection for increasing detection efficacy. It does not provide proper solutions to the different types of threats. It lacks performance comparison and trust or privacy factors. |
| Sr No. | Survey Questions |
|---|---|
| 1. | How familiar are you with cloud computing security and machine learning? |
| 2. | Have you or your organization implemented any cloud computing security measures in your operations? |
| 3. | What are the biggest security concerns you have about cloud computing? |
| 4. | How do you think ML can be used to improve cloud computing security? |
| 5. | How confident are you in the effectiveness of current cloud computing security measures? |
| 6. | In your opinion, what are the biggest challenges in implementing effective cloud computing security? |
| 7. | How often do you or your organization conduct security assessments or audits for cloud computing systems? |
| 8. | What role do you think human factors play in cloud computing security? |
| 9. | What measures should cloud service providers take to improve the security of their offerings? |
| 10. | How do you think regulations and compliance requirements affect cloud computing security? |
| 11. | How can organizations ensure their cloud service providers comply with security standards and regulations? |
| 12. | How do you think increasing Internet of Things (IoT) devices affects cloud computing security? |
| 13. | How effectively do you believe machine learning has improved the security of your industry’s cloud computing operations? |
| 14. | How important is security in your industry’s cloud computing operations? |
| 15. | What are your future plans for using machine learning in cloud computing security in your industry? |
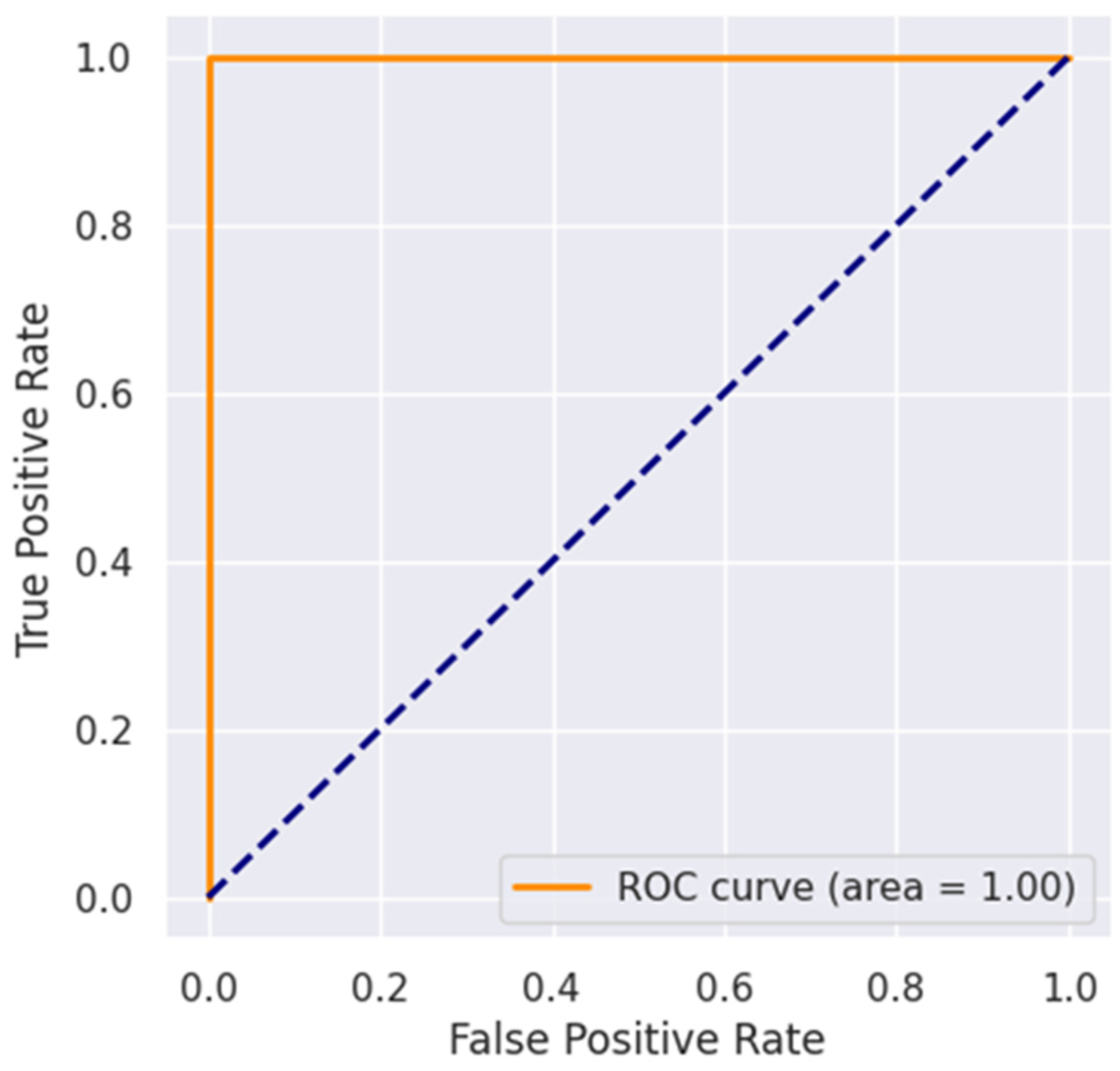
| Model | Accuracy | Precision | Recall | F1-Score | ROC-AUC |
|---|---|---|---|---|---|
| XGB | 97.50 | 97.60 | 97.60 | 97.50 | 1 |
| SVM | 97.35 | 97.30 | 97.30 | 97.30 | 1 |
| MLP | 96.20 | 96.21 | 96.20 | 96.20 | 99 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abbas, Z.; Myeong, S. Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions through Machine Learning Tools in Cloud Computing Environment. Electronics 2023, 12, 2650. https://doi.org/10.3390/electronics12122650
Abbas Z, Myeong S. Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions through Machine Learning Tools in Cloud Computing Environment. Electronics. 2023; 12(12):2650. https://doi.org/10.3390/electronics12122650
Chicago/Turabian StyleAbbas, Zaheer, and Seunghwan Myeong. 2023. "Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions through Machine Learning Tools in Cloud Computing Environment" Electronics 12, no. 12: 2650. https://doi.org/10.3390/electronics12122650
APA StyleAbbas, Z., & Myeong, S. (2023). Enhancing Industrial Cyber Security, Focusing on Formulating a Practical Strategy for Making Predictions through Machine Learning Tools in Cloud Computing Environment. Electronics, 12(12), 2650. https://doi.org/10.3390/electronics12122650