Towards Transparent and Secure IoT: Improving the Security and Privacy through a User-Centric Rules-Based System
Abstract
:1. Introduction
2. Related Work
3. System Design
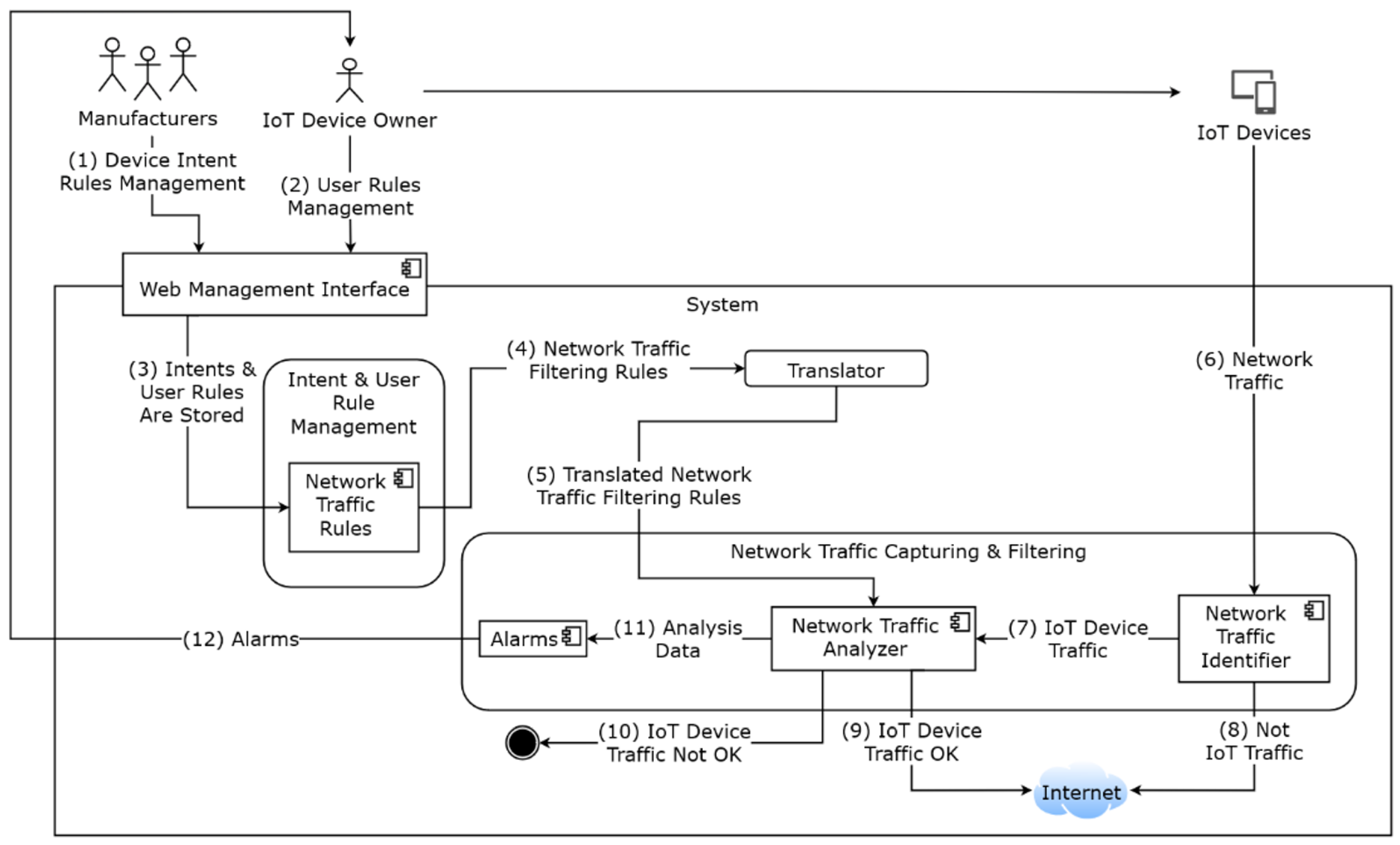
3.1. Architecture
- The “IoT Device Manufacturer” specifies and definies their own intentions that are translated to simple rules (“Intent Rules”);
- The “IoT Device Owner” specifies and definies their own rules (“User Rules”);
- Both the “Intent Rules” and the “User Rules” are stored on the “Intent and User Rules Management” service;
- Rules are sent to the “Translator” service that is responsible for conducting the rules translation to the appropriate network filtering service (in this case, it will be Snort);
- “Translator” service sends the translated rules to the “Network Traffic Capturing and Filtering” service through the “Network Traffic Analyser” component;
- “IoT Devices” produce network traffic. This network traffic is captured by the “Network Traffic Capturing and Filtering” service, through the “Network Traffic Identifier” component;
- If the “Network Traffic Identifier” identifies the traffic as having origin in an IoT device, the traffic is redirected to the “Network Traffic Analyser”;
- If it is not IoT device traffic, it is redirected to the Internet;
- If the “Network Traffic Analyser” verifies that the traffic is compliant with the rules, then the traffic is routed to the internet;
- If not, traffic is blocked;
- “Network Traffic Analyser” component produces a set of analytical data that will be used to generate alarms or simply collect information about the system usage;
- Alarm information is sent by the “Alarms” component of the system to the “IoT Device Owner”.
3.1.1. Intents and User Rule Management REST API
3.1.2. Translator (Integration Layer with Filtering Tool)
- Rule Action—specifies what action the Snort rule performs on the packet it received, such as alert, drop, log, pass, reject, or drop.
- Rule Protocol—specifies which protocol should be parsed for suspicious behaviour, such as TCP, UDP, ICMP, or IP.
- Source IP—specifies the packet’s source IP(s) address(es).
- Source Port—specifies which source port(s) of the packet.
- Flow Direction—specifies which direction of the packet flow, unidirectional (->) or bidirectional (<>).
- Destination IP—specifies the destination address(es) of the packet.
- Destination Port—specifies the destination port(s) of the packet.
- Rule Options—specify what content the rule should analyse, where it is located within the packet, the packet size, the message shown when the alert is triggered, and the rule ID.
3.1.3. Snort IPS
- -A console: this argument configures Snort so that the alerts it generates are sent to the console.
- -c /etc/snort/snort.conf: this argument allows you to choose the configuration file of the Snort settings that should be executed.
- -i ens33: ens34: this argument chooses the interfaces to listen for traffic.
- -Q: this argument allows you to run Snort in inline mode.
3.1.4. Web Management Interface
3.2. Snort Implementation Workflow
4. System Validation and Testing
4.1. Test System Deployment
4.2. Functional Tests
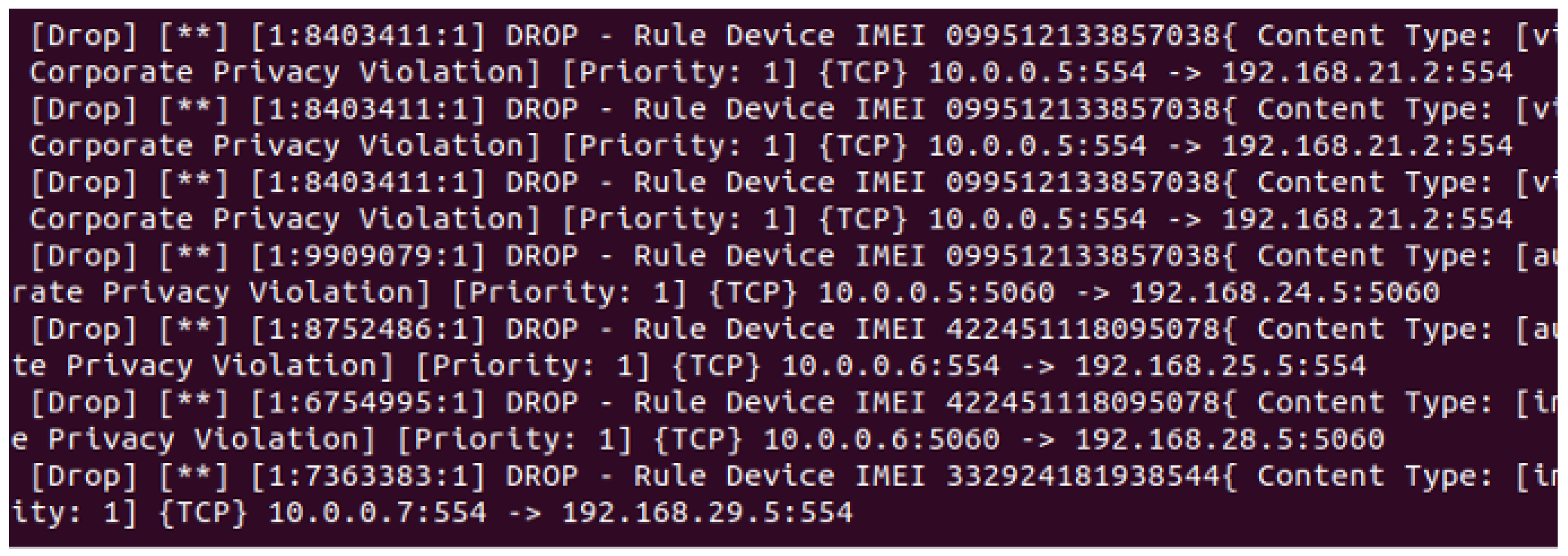
4.2.1. Test Scenario I—Violations of the Manifest of Intents
4.2.2. Test Scenario II—Violations of the User Rules
4.3. System Performance
- Packets Received—represents the number of packets that were captured for inspection.
- Packets Analysed—represents the number of packets parsed from packets received.
- Dropped Packets—represents the number of packets not found and therefore not analysed by the analysis component.
- Packets Whitelisted/Blacklisted—represents the number of packets whose content and destination address violated the manufacturer’s specifications or IoT device owner rules.
- Analysis Runtime—represents the time taken to analyse and classify packets received by the traffic capture component.
- Dump Runtime—represents the time taken to generate and send packets to the network.
- Delay—represents the additional expense required to analyse the generated packets.
4.3.1. Intent Scenario Results
4.3.2. Rules Scenario Results
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bhosale, D.A.; Mane, V.M. Comparative study and analysis of network intrusion detection tools. In Proceedings of the 2015 International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Davangere, India, 29–31 October 2015; pp. 312–315. [Google Scholar]
- Nest Home Security Devices Have a Hidden Microphone. Google Calls It an “Error”. Section: Security. Available online: https://www.popularmechanics.com/technology/security/a26448907/google-nest-hidden-microphone/ (accessed on 3 April 2023).
- Calado, J.P.d.C. Open Source IDS/IPS in a Production Environment: Comparing, Assessing and Implementing. Master’s Thesis, Universidade de Lisboa, Lisbon, Portugal, 2018. [Google Scholar]
- Chakraborty, S. When Smart Gadgets Spy on You: Your Home Life Is Less Private Than You Think. Available online: https://economictimes.indiatimes.com/tech/internet/when-smart-gadgets-spy-on-you-your-home-life-is-less-private-than-you-think/articleshow/60984623.cms?from=mdr (accessed on 3 April 2023).
- Coble, S. Xiaomi Security Camera Shows User Wrong Video Feed. Available online: https://www.infosecurity-magazine.com/news/xiaomi-camera-shows-wrong-video/ (accessed on 3 April 2023).
- Google Nest Guard Has Microphone That Wasn’t Disclosed. Available online: https://www.mercurynews.com/2019/02/20/google-nest-guard-has-a-microphone-but-it-didnt-say-that-on-the-box/ (accessed on 3 April 2023).
- Statt, N. Amazon’s Alexa Isn’t just AI—Thousands of Humans Are Listening. Available online: https://www.theverge.com/2019/4/10/18305378/amazon-alexa-ai-voice-assistant-annotation-listen-private-recordings (accessed on 3 April 2023).
- Amazon Alexa Heard and Sent Private Chat. Available online: https://www.bbc.com/news/technology-44248122 (accessed on 3 April 2023).
- 10 Fascinating Things We Learned When We Asked The World ’How Connected Are You?’ | The Mozilla Blog. Available online: https://blog.mozilla.org/en/mozilla/10-fascinating-things-we-learned-when-we-asked-the-world-how-connected-are-you/ (accessed on 3 April 2023).
- What the Internet of Things Means for Consumer Privacy. Available online: https://impact.economist.com/perspectives/technology-innovation/what-internet-things-means-consumer-privacy-0/white-paper/what-internet-things-means-consumer-privacy (accessed on 3 April 2023).
- Atlam, H.F.; Wills, G.B. IoT Security, Privacy, Safety and Ethics. In Digital Twin Technologies and Smart Cities; Internet of Things; Farsi, M., Daneshkhah, A., Hosseinian-Far, A., Jahankhani, H., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 123–149. [Google Scholar] [CrossRef]
- Assiri, A.; Almagwashi, H. IoT Security and Privacy Issues. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Chanal, P.M.; Kakkasageri, M.S. Security and Privacy in IoT: A Survey. Wirel. Pers. Commun. 2020, 115, 1667–1693. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Khowaja, S.A.; Khuwaja, P.; Dev, K.; Lee, I.H.; Khan, W.U.; Wang, W.; Qureshi, N.M.F.; Magarini, M. A secure data sharing scheme in Community Segmented Vehicular Social Networks for 6G. IEEE Trans. Ind. Inform. 2022, 19, 890–899. [Google Scholar] [CrossRef]
- Zhang, L.; Li, Y.; Jin, T.; Wang, W.; Jin, Z.; Zhao, C.; Cai, Z.; Chen, H. SPCBIG-EC: A robust serial hybrid model for smart contract vulnerability detection. Sensors 2022, 22, 4621. [Google Scholar] [CrossRef] [PubMed]
- Zhang, L.; Wang, J.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Smart contract vulnerability detection combined with multi-objective detection. Comput. Netw. 2022, 217, 109289. [Google Scholar] [CrossRef]
- Ren, Y.; Zhu, F.; Sharma, P.K.; Wang, T.; Wang, J.; Alfarraj, O.; Tolba, A. Data query mechanism based on hash computing power of blockchain in internet of things. Sensors 2019, 20, 207. [Google Scholar] [CrossRef] [Green Version]
- Abdul-Ghani, H.A.; Konstantas, D. A Comprehensive Study of Security and Privacy Guidelines, Threats, and Countermeasures: An IoT Perspective. J. Sens. Actuator Netw. 2019, 8, 22. [Google Scholar] [CrossRef] [Green Version]
- Shen, Y.; Vervier, P.A. IoT Security and Privacy Labels. In Proceedings of the Privacy Technologies and Policy; Lecture Notes in Computer Science; Naldi, M., Italiano, G.F., Rannenberg, K., Medina, M., Bourka, A., Eds.; Springer: Cham, Switzerland, 2019; pp. 136–147. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A.H. Addressing Security and Privacy Issues of IoT Using Blockchain Technology. IEEE Internet Things J. 2021, 8, 881–888. [Google Scholar] [CrossRef]
- Bettayeb, M.; Nasir, Q.; Talib, M.A. Firmware Update Attacks and Security for IoT Devices: Survey. In Proceedings of the ArabWIC 6th Annual International Conference Research Track, Rabat, Morocco, 7–9 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sun, P.; Garcia, L.; Salles-Loustau, G.; Zonouz, S. Hybrid Firmware Analysis for Known Mobile and IoT Security Vulnerabilities. In Proceedings of the 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Valencia, Spain, 29 June–2 July 2020; pp. 373–384. [Google Scholar] [CrossRef]
- Srivastava, P.; Peng, H.; Li, J.; Okhravi, H.; Shrobe, H.; Payer, M. FirmFuzz: Automated IoT Firmware Introspection and Analysis. In Proceedings of the 2nd International ACM Workshop on Security and Privacy for the Internet-of-Things, London, UK, 15 November 2019; pp. 15–21. [Google Scholar] [CrossRef]
- Government Efforts toward Promoting IoT Security Awareness for end Users: A Study of Existing Initiatives—ProQuest. Available online: https://www.proquest.com/openview/e8826900b7596e3720cbc3c9c8786ec0/1?pq-origsite=gscholar&cbl=396497 (accessed on 3 April 2023).
- Bugeja, J.; Vogel, B.; Jacobsson, A.; Varshney, R. IoTSM: An End-to-End Security Model for IoT Ecosystems. In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 1–15 March 2019; pp. 267–272. [Google Scholar] [CrossRef]
- Jaigirdar, F.T.; Rudolph, C.; Bain, C. Prov-IoT: A Security-Aware IoT Provenance Model. In Proceedings of the 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Guangzhou, China, 29 December 2020–1 January 2021; pp. 1360–1367. [Google Scholar] [CrossRef]
- Irshad, M. A Systematic Review of Information Security Frameworks in the Internet of Things (IoT). In Proceedings of the 2016 IEEE 18th International Conference on High Performance Computing and Communications; IEEE 14th International Conference on Smart City; IEEE 2nd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Sydney, NSW, Australia, 12–14 December 2016; pp. 1270–1275. [Google Scholar] [CrossRef]
- Amar, Y.; Haddadi, H.; Mortier, R.; Brown, A.; Colley, J.; Crabtree, A. An Analysis of Home IoT Network Traffic and Behaviour. arXiv 2018, arXiv:1803.0536. [Google Scholar] [CrossRef]
- Mazhar, M.H.; Shafiq, Z. Characterizing Smart Home IoT Traffic in the Wild. In Proceedings of the 2020 IEEE/ACM Fifth International Conference on Internet-of-Things Design and Implementation (IoTDI), Sydney, NSW, Australia, 21–24 April 2020; pp. 203–215. [Google Scholar] [CrossRef]
- Ostinato Traffic Generator for Network Engineers. Available online: https://ostinato.org/ (accessed on 3 April 2023).
- Snort—Network Intrusion Detection & Prevention System. Available online: https://www.snort.org/ (accessed on 3 April 2023).
- Hafeez, S.; Eng, B. Deep Packet Inspection Using Snort. Master’s Thesis, University of Victoria, Victoria, Canada, 2016. [Google Scholar]








| Device | Device Type (TAC) | Declared Content-Type | Declared Communication Protocol | Declared Destination Addresses |
|---|---|---|---|---|
| Samsung Android Tablet | 09951213 | [video/mp4, audio/mpeg] [video/x-msvideo, audio/ogg] | [HTTP, RTSP] [HTTP, RTSP] | [192.168.21.0/24, 192.168.22.0/24] [192.168.23.0/24, 192.168.24.0/24] |
| Apple iOS Smartphone | 42245111 | [audio/basic, video/h264] [image/jpeg, text/plain] | [HTTP, RTSP] [HTTP, RTSP] | [192.168.25.0/24, 192.168.26.0/24] [192.168.27.0/24, 192.168.28.0/24] |
| Huawei Android Smartphone | 33292418 | [audio/mpeg, video/mp4] | [SIP, RTSP] | [192.168.29.0/24, 192.168.30.0/24] |
| Protocol Data | |
|---|---|
| Source IP: 10.0.0.10 | Destination IP: 192.168.21.10 |
| Text Protocol | |
| TAC:09951213 | |
| Content-Type: [text/plain, video/h264] | |
| Protocol Data | |
|---|---|
| Source IP: 10.0.0.10 | Destination IP: 192.168.30.10 |
| Text Protocol | |
| TAC:09951213 | |
| Content-Type: [video/mp4, audio/mpeg] | |
| Device | Device ID (IMEI) | Content-Type Allowed by Device Owner | Communication Protocol Allowed by Device Owner | Destination Address Allowed by Device Owner |
|---|---|---|---|---|
| Samsung Android Tablet | 099512133857038 | [video/quicktime, audio/x-aiff] [audio/basic, video/h264] | [RTSP, SIP] [SIP, RTSP] | [192.168.21.0/24, 192.168.22.0/24] [192.168.23.0/24, 192.168.24.0/24] |
| Apple iOS Smartphone | 422451118095078 | [audio/ogg, video/h265] [image/jpeg, text/csv] | [SIP, RTSP] [RTSP, SIP] | [192.168.25.0/24, 192.168.26.0/24] [192.168.27.0/24, 192.168.28.0/24] |
| Huawei Android Smartphone | 332924181938544 | [image/jpeg] | [RTSP] | [192.168.29.0/24, 192.168.30.0/24] |
| Protocol Data | |
|---|---|
| Source IP: 10.0.0.5 | Destination IP: 192.168.21.2 |
| Text Protocol | |
| IMEI: 099512133857038 | |
| Content-Type: [text/plain, video/h264] | |
| Packets/s Throughput | Packets Captured | Packets Analysed | Packets Dropped | Packets Blacklisted |
|---|---|---|---|---|
| 100 | 113,019 | 100% | 0% | 88.48% |
| 500 | 102,240 | 100% | 0% | 97.62% |
| 1000 | 101,391 | 100% | 0% | 98.62% |
| 3000 | 105,846 | 100% | 0% | 94.25% |
| 5000 | 100,941 | 100% | 0% | 98.71% |
| 7000 | 102,817 | 100% | 0% | 94.81% |
| 9000 | 101,165 | 100% | 0% | 96.37% |
| 10,000 Packets/s | |
|---|---|
| Analysis Runtime High/Low | 16 min 45 s / 1 min 36 s |
| Dump Runtime High/Low | 16 min 39 s/10 s |
| Delay Runtime High/Low | 1 min 48 s/6 s |
| Average Analysis Runtime | 4 min 23 s |
| Average Dump Runtime | 3 min 17 s |
| Average Delay Runtime | 1 min 06 s |
| Packets/s Throughput | Packets Captured | Packets Analysed | Packets Dropped | Packets Blacklisted |
|---|---|---|---|---|
| 100 | 247,000 | 100% | 0% | 40.44% |
| 500 | 121,334 | 100% | 0% | 82.40% |
| 1000 | 106,842 | 100% | 0% | 93.39% |
| 3000 | 102,444 | 100% | 0% | 97.19% |
| 5000 | 101,960 | 100% | 0% | 97.72% |
| 7000 | 102,255 | 100% | 0% | 97.33% |
| 9000 | 104,410 | 100% | 0% | 95.75% |
| 10,000 Packets/s | |
|---|---|
| Analysis Runtime High/Low | 19 min 03 s/2 min 50 s |
| Dump Runtime High/Low | 16 min 40 s/10 s |
| Delay Runtime High/Low | 3 min 15 s/1 min 57 s |
| Average Analysis Runtime | 5 min 53 s |
| Average Dump Runtime | 3 min 17 s |
| Average Delay Runtime | 2 min 36 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lola, J.; Serrão, C.; Casal, J. Towards Transparent and Secure IoT: Improving the Security and Privacy through a User-Centric Rules-Based System. Electronics 2023, 12, 2589. https://doi.org/10.3390/electronics12122589
Lola J, Serrão C, Casal J. Towards Transparent and Secure IoT: Improving the Security and Privacy through a User-Centric Rules-Based System. Electronics. 2023; 12(12):2589. https://doi.org/10.3390/electronics12122589
Chicago/Turabian StyleLola, João, Carlos Serrão, and João Casal. 2023. "Towards Transparent and Secure IoT: Improving the Security and Privacy through a User-Centric Rules-Based System" Electronics 12, no. 12: 2589. https://doi.org/10.3390/electronics12122589






