A Blockchain-Based Method for Optimizing the Routing of High-Frequency Carbon-Trading Payment Channels
Abstract
:1. Introduction
- The Multi-Factor Routing Payment Scheme (MFPS)-based algorithm is proposed. The path selection takes into account the transaction fees, node reputation, and distance to select the optimal path for the transaction. In order to reduce channel congestion and avoid the problem of channel capacity imbalances, the channel balance is adjusted by applying different charging percentages based on the channel balance difference. In order to improve the transaction success ratio, when there is no path in the payment channel network to fulfill the amount required for the transaction, the transaction amount is split according to the largest channel balance, employing a greedy transaction splitting approach to minimize the number of splits.
- The Asymmetric Encryption-Based Time-Locked Contract payment protocol (ATLC) is proposed. This protocol uses a combination of asymmetric encryption algorithms and data signing algorithms for encryption, decryption, and verification. It ensures the atomicity of the transaction process, data consistency, balance security, and value privacy.
- Extensive experimental simulations are conducted, demonstrating that the MFPS algorithm achieves higher transaction payment success ratios with lower average handling expenses. The proposed solutions also provide security and privacy protection against wormhole attacks, double-flower attacks, and false-transaction attacks, demonstrating improved performance in terms of computational verification and message overhead.
2. Related Works
3. Related Knowledge
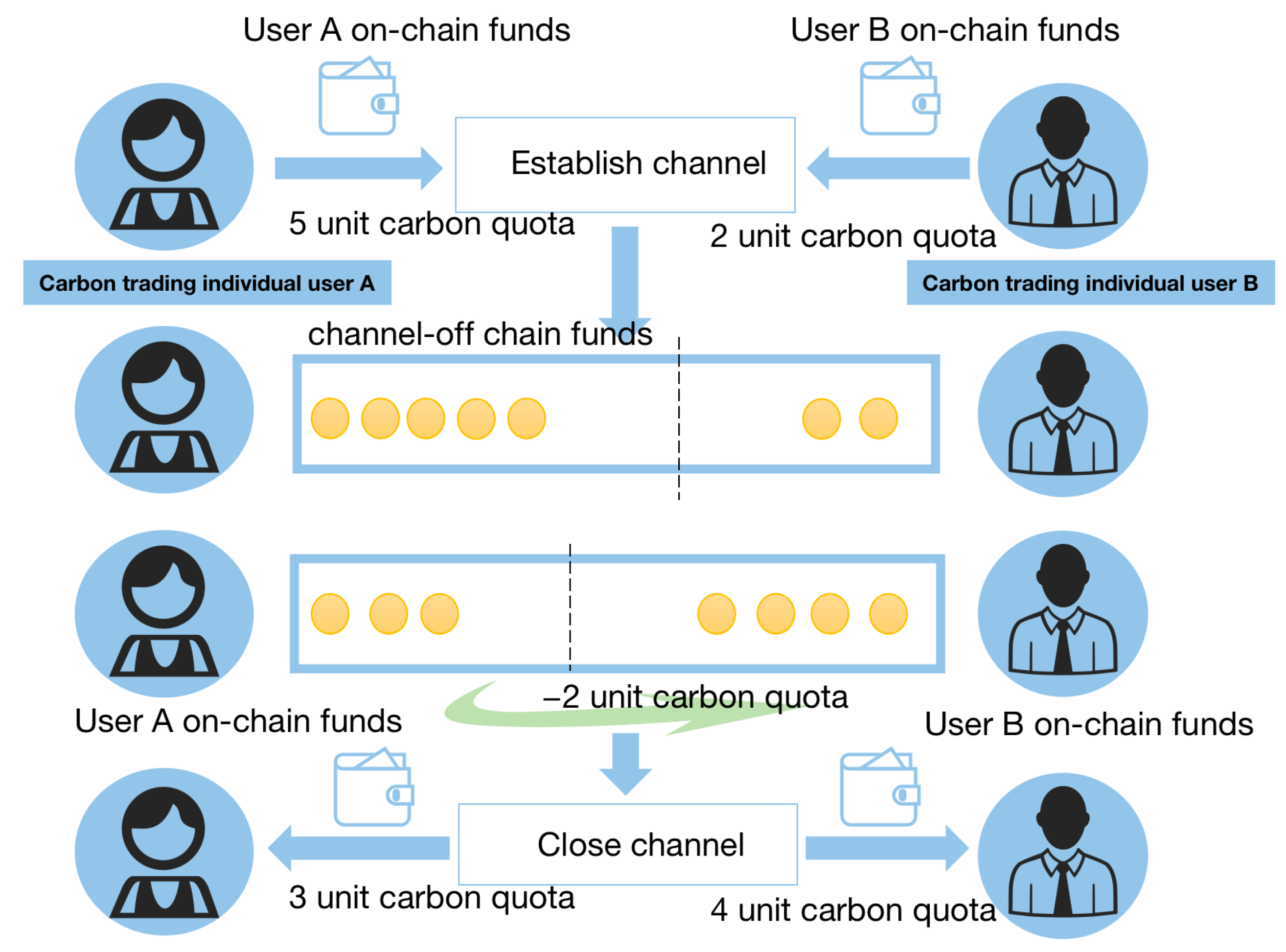
3.1. Off-Chain Payment Channels
3.2. Off-Chain Payment Channels
4. System Model
4.1. Network Model
- Set each edge to have a transaction fee , which is the fee charged by node when transferring the transaction amount from to .
- Set each edge to have a channel balance , which represents the maximum transaction amount that can be transferred from to .
- Set each edge to have an HTLC tolerance time , which is the longest time for to wait for to provide the secret R.
- Set the total balance of each edge channel as , which denotes the sum of the channel balances on both sides. Therefore, and the balance is always .
4.2. Payment Model
- Timing constraint: To complete the payment request R, the next route must be forwarded within the time-lock tolerance time of the HTLC in each payment channel, as shown in Equation (2). Timeliness is achieved through the HTLC’s time lock, which guarantees the integrity of transactions in intermediate payment channels.
- Feasibility constraint: To successfully complete the payment request R by passing through each channel in the path p , it is necessary for the channel balance to be at least equal to the sum of the payment amount and all the handling fees incurred after passing through node , as shown in Equation (3).
- Timeliness constraint: To successfully complete the payment request R, the payment must be finalized within the specified completion time of the payment request and reach the intended recipient. Therefore, it is necessary to ensure that the sum of the payment start time st and the time needed to complete the transaction transfer in each link along the path does not exceed the transaction deadline dl specified in the payment request. indicates the transaction transfer time required in channel link e, as shown in Equation (4).
5. PCN Routing Optimization Algorithm
5.1. MFPS: Multi-Factor Routing Payment Scheme
5.1.1. Transaction Fees
5.1.2. Node Reputation Value
- Correct behavior: The node successfully transfers the transaction amount and required secret within the specified time lock.
- Malicious behavior: The node fails to transfer the amount of the transaction within the prescribed time lock, fails to provide the required secret, or provides a forged secret.
5.1.3. Distance
5.2. ATLC: Time-Locked Contract Payment Protocol Based on Asymmetric Encryption
5.2.1. Introduction to ATLC Protocol
- 1.
- The sender generates a random numeric identifier and using the asymmetric encryption algorithm RSA . The sender node transmits through the anonymous secure communication channel to each intermediate node and the receiver.
- 2.
- Transaction lock phase: The sender transmits transaction-related information to the next hop node . The intermediate node receives the transaction information from the previous hop and verifies the correctness of the conditions of the incoming contract using the RSA algorithm for decryption and verification. It checks if If the match is successful, provides funds to the next hop node and locks them in the channel. If the match is unsuccessful, the transaction is terminated and the funds locked in the channel are unlocked and returned to the original section.
- 3.
- Transaction release phase: After receiving the transaction information, the receiver determines whether the current time is less than dl. If it is satisfied, it proceeds to the verification phase and enters the fund release phase upon successful verification of the match. uses the digital signature algorithm RSA for signature generation and sends to the previous hop stage . When the intermediate node receives from the next hop node of the transaction, it uses the DSA algorithm to verify and determine if . If the verification is successful, the funds locked in the channel are released to . If the verification is unsuccessful, the transaction is terminated and the funds locked in the channel are unlocked and returned to the original node.
- 4.
- When the transaction release phase is successfully verified at sender , the channel funds are released to node , the transaction is closed, and sender successfully transfers the funds to receiver .
5.2.2. Privacy Protection Analysis
- Atomicity: Transactions are executed or aborted. Atomicity is a necessary property in the proposed multi-hop payment mechanism. During the transaction process, if there is a node verification mismatch, the transaction will terminate, and the transaction amount in the channel will be released back to the original node, ensuring the atomicity of the transaction.
- Data consistency: During transactions, the balances in the payment phase and release phase are changed and transferred to the node channel. If the verification does not match at any stage of the transaction process, the transaction amount will be returned to the original node, and the channel balance of each node will remain unchanged. The consistency of the balance throughout the channel is ensured.
- Balance security: If there is a malicious node, any intermediate node participating in the transaction does not lose its balance or the transaction fee obtained by participating in the transaction. If an honest node is in the transaction lock phase and encounters a situation where is a malicious node and the decryption received by using the private key does not match , the transaction terminates and does not lose any fees. In the transaction release phase, if node directly sends to , uses the public key of node to verify and sign. If it does not match , the channel transaction balance of user will remain locked, and the amount will be returned to the original node after the transaction is terminated. In this case, the node will not lose any fees, which ensures the balance security of the node.
- Value privacy: In addition to the sender and receiver intermediate nodes not knowing the transaction amount information of the transaction, the intermediate nodes in the payment path can only see the payment value transmitted by the previous hop node and the payment value paid to the next hop node.
5.3. Design of Routing Algorithm
| Algorithm 1: Route-Init |
 |
| Algorithm 2: PaySplit |
 |
| Algorithm 3: PaymentRoute |
 |
| Algorithm 4: Recipient |
 |
6. Simulation Experiments
6.1. Environments and Parameter Setting
6.2. Security Analysis
- Anti-wormhole attack: In the path , if is an honest node, and are malicious nodes. If and collude to obtain the transaction fee of , the malicious attack is a wormhole attack. In this paper, we propose an ATLC that can effectively prevent wormhole attacks. If node directly sends the transaction information to node for the digital signature verification phase, and node does not have the identifier of node , the verification result cannot be matched. As a result, the channel balance will not be released or unlocked and the honest node will not lose any funds.
- Anti-double-flower attack: A double-flower attack is when an attacker repeatedly uses the same funds to make payments. In the asymmetric encryption and digital signature used by the ATLC, each transaction node has a unique digital signature and public key for verification, and an attacker cannot forge the digital signature. Therefore, the attacker cannot perform a double-flower attack.
- Anti-fraudulent trading attack: A fake transaction attack is when an attacker sends fake transactions to deceive the trading node and obtain the fee. In the ATLC protocol, each transaction has a unique identification called TsId, and nodes need to sign and verify the transaction. Only through the verification of the node can the transaction be completed, thereby preventing attackers from sending false transactions.
- Anti-replay attack: This is when an attacker retransmits the transmitted data during the data transmission between two communication parties. The ATLC uses the digital signature algorithm (DSA) and encryption algorithm to protect against replay attacks.
- Denial-of-service attack: This is when an attacker sends a large number of invalid requests by forging identities. As a result, communication between two parties cannot proceed as normal. The ATLC uses the DSA to protect against denial-of-service attacks.
6.3. Experimental Results
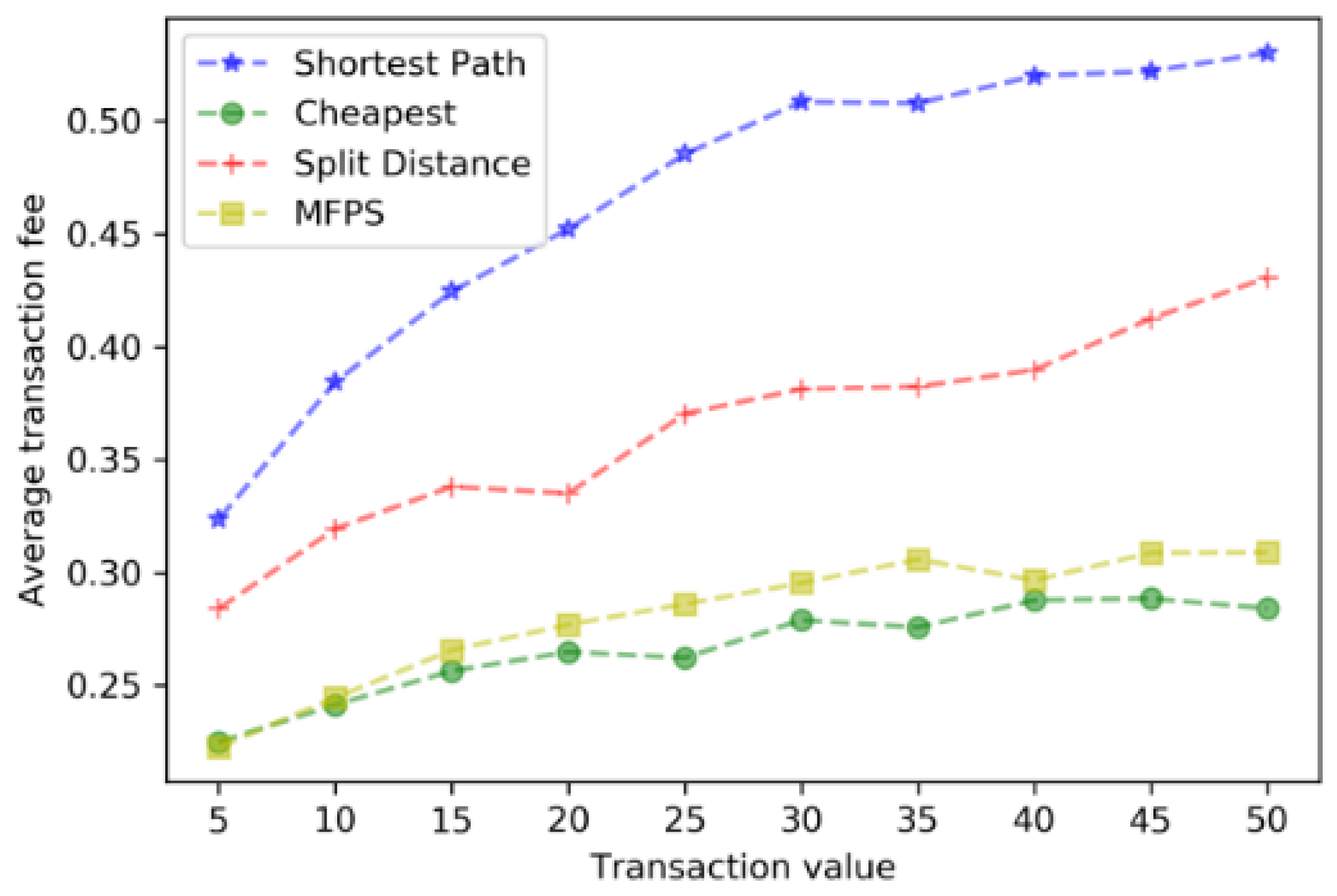
- ShortestPath: The algorithm chooses the shortest path for trading under the trade constraints;
- Cheapest: In the transaction path selection, this algorithm selects the path with the lowest transaction fee;
- SplitDistance: If the channel balance does not meet the amount needed for the transaction, this algorithm splits the transaction amount along the shortest path.
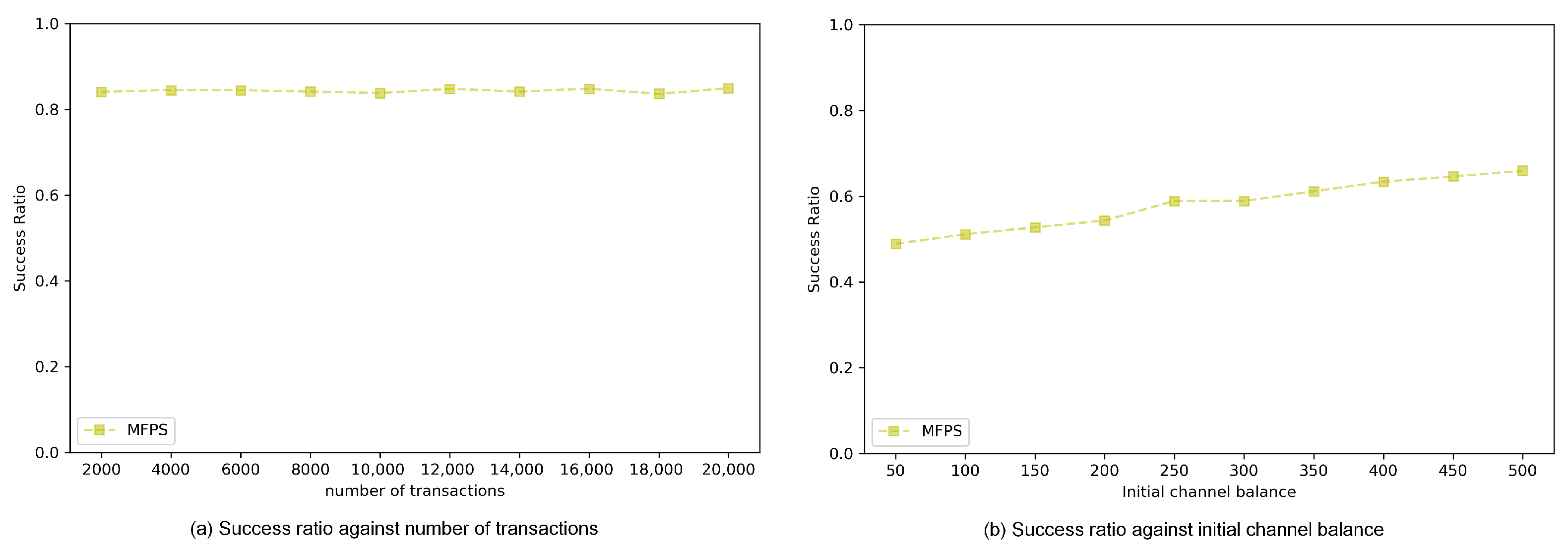
- Success ratio: This refers to the percentage of total transactions successfully received by the recipient;
- Average transaction fee: This refers to the average transaction fee paid in successfully completed transactions;
- Average message spending: This refers to the overhead in terms of the average number of messages involved in a successful transaction request;
- Delay: This refers to the time required to complete a transaction (in mesc).
- Number of transactions: This refers to the total number of transactions performed in the off-chain payment channel network;
- Initial channel balance: This refers to the initial balance in the channel of the node that establishes the off-chain payment channel network;
- Transaction value: This refers to setting the transaction amount for each transaction in the off-chain payment channel network;
- TNumber of nodes: This refers to the total number of nodes present in the off-chain payment channel network.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fang, G.; Tian, L.; Liu, M. How to optimize the development of carbon trading in China—Enlightenment from evolution rules of the EU carbon price. Appl. Energy 2018, 211, 1039–1049. [Google Scholar] [CrossRef]
- Almer, C.; Winkler, R. Analyzing the effectiveness of international environmental policies: The case of the Kyoto Protocol. J. Environ. Econ. Manag. 2017, 82, 125–151. [Google Scholar] [CrossRef] [Green Version]
- Kim, S.K.; Huh, J.H. Blockchain of carbon trading for UN sustainable development goals. Sustainability 2020, 12, 4021. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Abou Jaoude, J.; Saade, R.G. Blockchain applications–usage in different domains. IEEE Access 2019, 7, 45360–45381. [Google Scholar] [CrossRef]
- Richardson, A.; Xu, J. Carbon Trading with Blockchain. In Mathematical Research for Blockchain Economy; Pardalos, P., Kotsireas, I., Guo, Y., Knottenbelt, W., Eds.; Springer: Cham, Switzerland, 2020; pp. 105–124. [Google Scholar]
- Pan, Y.; Zhang, X.; Wang, Y.; Yan, J.; Zhou, S.; Li, G.; Bao, J. Application of blockchain in carbon trading. Energy Procedia 2019, 158, 4286–4291. [Google Scholar] [CrossRef]
- Vaig, l.K.K.; Karne, R.; Siluveru, M.; Kesoju, M. Review on Blockchain Technology: Architecture, Characteristics, Benefits, Algorithms, Challenges and Applications. Mesopotamian J. Cybersecur. 2023, 2023, 73–85. [Google Scholar]
- Yaseen, M.; Bahari, M.; Hammood, O.A. Blockchain technology applications, concerns and recommendations for public sector. Mesopotamian J. Comput. Sci. 2021, 2021, 1–6. [Google Scholar] [CrossRef] [PubMed]
- Helliar, C.V.; Crawford, L.; Rocca, L.; Teodori, C.; Veneziani, M. Permissionless and permissioned blockchain diffusion. Int. J. Inf. Manag. 2020, 54, 102136. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Talib, M.A.; Nassif, A.B. Performance analysis of hyperledger fabric platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef] [Green Version]
- Li, W.; He, M. Comparative analysis of bitcoin, Ethereum, and libra. In Proceedings of the 2020 IEEE 11th International Conference on Software Engineering and Service Science, Beijing, China, 21 September 2020; pp. 545–550. [Google Scholar]
- Pan, C.; Liu, Z.; Liu, Z.; Long, Y. Research on Scalability of blockchain: Issues and methods. J. Comput. Res. Dev. 2018, 55, 2099–2110. [Google Scholar]
- Lee, J.; Long, A.; McRae, M.; Steiner, J.; Handler, S.G. Bitcoin basics: A primer on virtual currencies. Bus. Law Int. 2015, 16, 21. [Google Scholar]
- Zhou, Q. Research on Blockchain Scalability Based on State Channel and Cross-Chain Protocol. Master’s Thesis, Shanghai Jiaotong University, Shanghai, China, 2020. [Google Scholar]
- Yang, D.; Long, C.; Xu, H. A review on scalability of blockchain. In Proceedings of the 2020 the 2nd International Conference on Blockchain Technology, Hilo, HI, USA, 12 March 2020; pp. 1–6. [Google Scholar]
- Yang, D.; Narayanan, V.; Zheng, C.D. A Secure Sharding Protocol for Open Blockchains. In Proceedings of the 23rd ACM Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 17–30. [Google Scholar]
- Huang, J.; Kong, L.; Chen, G.; Wu, M.-Y.; Liu, X.; Zeng, P. Towards Secure Industrial IoT: Blockchain System with Credit-Based Consensus Mechanism. IEEE Trans. Ind. Inform. 2019, 15, 3680–3689. [Google Scholar] [CrossRef]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. 2016. Available online: https://coinrivet.com/research/papers/the-bitcoin-lightning-network-scalable-off-chain-instant-payments/ (accessed on 14 January 2016).
- Raiden Network. Available online: https://raiden.network/ (accessed on 1 September 2019).
- Herlihy, M. Atomic cross-chain swaps. In Proceedings of the 2018 ACM Symposium on Principles of Distributed Computing, Egham, UK, 23–27 July 2018; pp. 245–254. [Google Scholar]
- Papadis, N.; Tassiulas, L. Blockchain-based payment channel networks: Challenges and recent advances. IEEE Access 2020, 8, 227596–227609. [Google Scholar] [CrossRef]
- Jia, L.; Pei, Q.; Wang, X.; Zhang, H.; Yu, L.; Zhang, J.; Sun, Y. Overview of off-chain Channel Routing Algorithms. J. Softw. 2022, 22, 233–253. [Google Scholar]
- Grunspan, C.; Pérez-Marco, R. Ant routing algorithm for the lightning network. arXiv 2018, arXiv:1807.00151. [Google Scholar]
- Malavolta, G.; Moreno-Sanchez, P.; Kate, A.; Maffei, M. Silentwhispers: Enforcing Security and Privacy in Decentralized Credit Networks. Cryptology ePrint Archive. 2016. Available online: https://eprint.iacr.org/2016/1054 (accessed on 15 November 2016).
- Roos, S.; Moreno-Sanchez, P.; Kate, A.; Goldberg, I. Settling payments fast and private: Efficient decentralized routing for path-based transactions. arXiv 2017, arXiv:1709.05748. [Google Scholar]
- Yu, R.; Xue, G.; Kilari, V.T.; Yang, D.; Tang, T. Coinexpress: A fast payment routing mechanism in blockchain-based payment channel networks. In Proceedings of the 27th International Conference on Computer Communication and Networks, Hangzhou, China, 30 July–2 August 2018; pp. 1–9. [Google Scholar]
- Wang, P.; Xu, H.; Jin, X.; Wang, T. Flash: Efficient dynamic routing for offchain networks. In Proceedings of the 15th International Conference on Emerging Networking Experiments and Technologies, Orlando, FL, USA, 9–12 December 2019; pp. 370–381. [Google Scholar]
- Sivaraman, V.; Venkatakrishnan, S.B.; Ruan, K.; Negi, P.; Yang, L.; Mittal, R.; Fanti, G.; Alizadeh, M. High throughput cryptocurrency routing in payment channel networks. In Proceedings of the 17th USENIX Symposium on Networked Systems Design and Implementation (NSDI 20), Santa Clara, CA, USA, 25–27 February 2020; pp. 777–796. [Google Scholar]
- Malavolta, G.; Moreno-Sanchez, P.; Kate, A.; Maffei, M.; Ravi, S. Concurrency and privacy with payment-channel networks. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 455–471. [Google Scholar]
- Mohanty, S.K. Tripathy S.n-htlc: Neo hashed time-lock commitment to defend against wormhole attack in payment channel networks. Comput. Secur. 2021, 106, 102291. [Google Scholar] [CrossRef]
- Mizrahi, A.; Zohar, A. Congestion Attacks in Payment Channel Networks. In Proceedings of the Financial Cryptography and Data Security, Virtual Event, 1–5 March 2021; pp. 170–188. [Google Scholar]
- Li, P.; Miyazaki, T.; Zhou, W. Secure Balance Planning of Off-blockchain Payment Channel Networks. In Proceedings of the IEEE INFOCOM 2020—IEEE Conference on Computer Communications, Toronto, ON, Canada, 6–9 July 2020; pp. 1728–1737. [Google Scholar]
- Zhang, Y.; Yang, D.; Xue, G. Cheapay: An optimal algorithm for fee minimization in blockchain-based payment channel networks. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Zhang, Q.; Cao, S.; Zhang, X. Cross-chain payment routing scheme based on multi-factor reverse auction. J. Comput. Res. Dev. 2022, 59, 2233–2246. [Google Scholar]
- Eckey, L.; Faust, S.; Hostáková, K.; Roos, S. Splitting Payments Locally While Routing Interdimensionally. Cryptology ePrint Archive. Paper 2020/555. 2020. Available online: https://eprint.iacr.org/2020/555 (accessed on 15 May 2020).






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, Y.; Xiong, A.; Qiu, X.; Guo, S.; Wang, D.; Li, D.; Zhang, X.; Kuang, Y. A Blockchain-Based Method for Optimizing the Routing of High-Frequency Carbon-Trading Payment Channels. Electronics 2023, 12, 2586. https://doi.org/10.3390/electronics12122586
Song Y, Xiong A, Qiu X, Guo S, Wang D, Li D, Zhang X, Kuang Y. A Blockchain-Based Method for Optimizing the Routing of High-Frequency Carbon-Trading Payment Channels. Electronics. 2023; 12(12):2586. https://doi.org/10.3390/electronics12122586
Chicago/Turabian StyleSong, Yu, Ao Xiong, Xuesong Qiu, Shaoyong Guo, Dong Wang, Da Li, Xin Zhang, and Yue Kuang. 2023. "A Blockchain-Based Method for Optimizing the Routing of High-Frequency Carbon-Trading Payment Channels" Electronics 12, no. 12: 2586. https://doi.org/10.3390/electronics12122586
APA StyleSong, Y., Xiong, A., Qiu, X., Guo, S., Wang, D., Li, D., Zhang, X., & Kuang, Y. (2023). A Blockchain-Based Method for Optimizing the Routing of High-Frequency Carbon-Trading Payment Channels. Electronics, 12(12), 2586. https://doi.org/10.3390/electronics12122586






