Abstract
In this paper, a dual-hop underlay cognitive relay network (CRN) with a best-relay selection (BRS) scheme under spectrum-sharing constraints from the primary user (PU) is investigated. The system model in this work consists of one PU, one secondary user (SU) and a few SU relays. Both users exchange the information using a half-duplex mode through amplify-and-forward (AF) SU relays. Moreover, all channels are modelled using the Nakagami-m fading model. In this work, the outage probabilities (OPs) are derived for the proposed system model under several scenarios to investigate the network performance under interference power constraint at the PU receiver. In addition, the impacts of the number of relays and the channel fading severity parameters are investigated as well. Furthermore, the system performance is investigated for several PU locations. The various numerical results are verified using a Monte Carlo simulation. Overall, the obtained results show that several factors such as the number of relays, channel fading severity parameters and PU location have a major impact on the outage performance of the SU. The simulation and analytical results are perfectly matched, confirming the accuracy of the analytical derivations.
1. Introduction
Due to the exponential increase in demand for mobile communication and the shortage of licensed bands, network providers and researchers have been continuously working over the last decade on different techniques to find a solution for these challenging problems. One of the obtained solutions is to exploit the unlicensed spectrum bands for mobile communication [1,2,3]. Therefore, different algorithms and techniques were proposed to allow mobile networks to access a few unlicensed spectrum bands such as the 2.4 GHz and 5 GHz bands, which are essentially occupied by Wi-Fi technology [4,5,6,7]. The key goal of the proposed algorithms was to guarantee a fair coexistence for the coexisting networks over the unlicensed bands achieving more spectrum, which can be used for wireless data and services [8,9,10,11,12,13,14,15]. In addition, this mechanism is expected to be adopted in the 3GPP standards for 5G New Radio Unlicensed (5G NR-U) and beyond [16,17,18].
Cognitive relay networks (CRNs), the scope of this context, have inspired researchers over the past few years as a key solution due to their potential in addressing spectrum shortage in the new generations of mobile communications. The dynamic spectrum sharing of cognitive radio (CR) networks allows the secondary users (SUs) to use the licensed radio spectrum of the primary users (PUs), improving the quality of service (QoS) and spectrum efficiency [19,20,21]. On the other hand, cooperative communication is widely used in wireless communications as a novel technique that provides a better system throughput using relay nodes [22,23]. Therefore, merging both techniques together, i.e., CR and cooperative communication, would provide more reliable communication, capacity and spectrum utilisation [24,25].
The unlicensed SUs are permitted to acquire the licensed spectrum in CR given that the data transmission of the licensed PUs is protected leading to the spectrum utilisation. This spectrum access is achieved by using spectrum underlay, overlay or interweave approaches [26]. In the underlay approach, the SU can transmit over the licensed spectrum, which is allocated for the PU, under interference constraints. In particular, the SU can use the PU spectrum only when the interference from the SU is below a certain threshold of interference at the PU receiver [27,28]. In the overlay approach, the SU can share simultaneously the spectrum band with the PU. In particular, the SU assists the PU in allocating some frequency bands and these vacant bands can be used for SU transmissions. On the other hand, the SU can only transmit simultaneously with the PU when a busy spectral slot was wrongly detected as a free band in the interweave approach [29]. In [30], a quantized soft-decision (QSD)-based scheme was proposed using a hybrid underlay and overlay CRN. The soft decision of the spectrum usage was quantized in this work, and a compressive polarized method was proposed. In particular, the local sensing results were regarded as bits and the SUs could transmit their parameters based on the reporting channel quality.
The use of relays in mobile networks was discussed in several works. The obtained results of these various works showed that using the relays in spectrum-sharing networks could improve spectrum utilisation and therefore the overall performance. In particular, the relays act as virtual antenna arrays in such system configurations [31,32]. Decode-and-forward (DF) and amplify-and-forward (AF) relaying schemes are broadly used in wireless networks. The relay decodes the signal and discards the noise from the original signal in the DF technique. After that, the message is encoded and forwarded to the destination [33,34,35,36]. On the contrary, in the AF technique, the relay forwards the signal to the destination after the amplification process. However, regardless of the noise amplification that is impeded in the AF technique, it requires simpler relay nodes [37,38]. A comprehensive study was performed in [39] to compare AF, DF and compress-and-forward (CF) cooperative strategies for slow Rayleigh fading channels. The obtained results showed that all strategies outperformed the direct transmission (i.e., without relaying). In addition, CP outperformed DF when the relay was close to the receiver while DF outperformed CP when the relay was close to the transmitter.
The best-relay selection (BRS) paradigm is extensively deployed in CRNs. In such scheme, the multiple relays are equipped with the CR user and the destination selects the relay with the best-received signal-to-noise ratio (SNR). A BRS scheme is commonly deployed in mobile networks due to its key benefits compared with other relaying schemes, where it can improve the diversity order related to the outage probability. Therefore, a BRS scheme can provide better cooperative gains, spectrum utilisation and cost efficiency compared with the repetitive transmission scheme [40,41,42]. The BRS strategy was deployed to investigate the energy harvesting relays in [43], where all nodes were supposed to follow a Rayleigh fading model considering a perfect knowledge of the channel state statistics. The obtained results verified that the use of this scheme could increase the lifetime of the network and the spectral efficiency. Moreover, the energy efficiency could be improved by increasing the number of relays. On the other hand, instead of using the BRS strategy, the relays in [44] were selected based on analytical hierarchy process (AHP) techniques. Specifically, the work suggested exploiting AHP techniques, which require a low latency time to select reliable relay nodes preventing unsuccessful transmissions. A new cooperative scheme assisted with artificial noise for the underlay DF CRNs was proposed in [45], where the SU transmitter exchanged secure information confidentially with the SU destination via multiple DF relays. Two schemes were investigated in that work: BRS and conventional relay selection (CRS). All links were modelled using a Rayleigh fading model. The simulation results confirmed that the secrecy outage could be improved by considering the proposed BRS model.
Two relaying schemes for spectrum-sharing cooperative networks were analysed in [46]; the first scheme used an opportunistic decode-and-forward (ODF) relay and the other scheme used an uncoded decode-and-forward (UDF) relay. In the UDF scheme, the relay can transmit or not or it can generate some information of the received signal with the help of a maximum-likelihood (ML) detection process. On the other hand, due to the severe shadowing and deterioration of the line-of-sight link in satellite communication, relay nodes have been used to forward the satellite signals to the destinations. Therefore, the reconfigurable intelligent surface (RIS) has received much attention from researchers as a promising technique to meet the requirements of 5G networks and beyond, such as low power communication and huge connectivity demands. The authors in [47] proposed a novel strategy to reconfigure the radio environments of the propagation medium by increasing the strength of the received signal and minimizing the total transmit power of the satellite and base station. This strategy, which was based on regulating the phases of the passive components at the RIS, focused on a joint beam-forming design and optimization for RIS-aided hybrid satellite–terrestrial relay networks, where the links between the satellite and base station to the users were blocked. Several works have recently been conducted to improve the energy efficiency of communication networks. For instance, the authors in [48] proposed an optimization scheme with a low complexity to reduce the power consumption under the constraint of the total transmit power in multibeam cognitive satellite systems using an iterative algorithm. A joint beam-forming and power allocation for nonorthogonal multiple-access (NOMA)-based satellite–terrestrial networks were investigated in [49]. In particular, multicast communication was used to serve the earth base stations, which served multiple users through NOMA. A constrained optimization problem was formulated maximizing the sum rate. The authors in [50] investigated a satellite and aerial integrated network consisting of a satellite and an unmanned aerial vehicle (UAV). Multicast transmission was employed in the satellite, while the UAV used rate-splitting multiple access (RSMA) to improve spectral efficiency. An optimization problem was formulated maximizing the sum rate of the proposed system with respect to some constraints.
Several statistical models have been used to describe the fading in wireless channels. In particular, the Nakagami-m distribution has been considered in wireless networks since it is known as the best-fit distribution for empirical path strength of data [51], while Suzuki’s distribution is considered a mixed distribution of short-term Rayleigh and lognormal distributions taking into account both small- and large-scale fading components. The authors in [51] derived the average rate and coverage probability for composite fading channel consisting of shadowing and Nakagami-m fading based on stochastic geometry. In addition, closed-form expressions for the outage probability of device-to-device (D2D) communications were obtained in [52] considering additive white Gaussian noise (AWGN) and a Suzuki fading channel. Nonanalytic integrals were solved for that scenario based on the Gauss–Laguerre quadrature and Gauss–Legendre quadrature methods. The results showed that a low-complexity approximation was associated with the three-point Gauss–Legendre based formula.
The performance of DF multiple-relay CRN under interference from the PU and eavesdropper was investigated in [53]. In that work, all channels experienced a Nakagami-m fading model. Furthermore, the selection-combining (SC) scheme was deployed in the destination. The variation of secrecy outage probability for several parameters was observed. On the other hand, the performance of dual-hop AF multiple-relay CRN under the interference from the PU was investigated in [54]. All channels experienced a Nakagami-m fading model. In addition, the communication between the source and destination of the SU network was not available through a direct link due to sever shadowing. On the other hand, an enhanced CRN model with a direct link was considered in [55]. An SC scheme was deployed at the destination. For both scenarios, the outage probability (OP) was evaluated and the obtained results showed that the second system model (i.e., using the SC scheme) achieved better performance compared with the regular AF relaying transmission [56]. In addition, the performance of CRNs using DF relays using the maximal-ratio combining (MRC), which provides the maximum output SNR, was investigated in [57]. The total sum rate was maximized for AF wireless networks under the total relay transmit power or individual relay powers in [58]. A low-complex technique was proposed in this work to obtain a closed-form formula. In addition, two algorithms were proposed to evaluate the average sum rate and energy efficiency. The obtained results showed that increasing the number of relays and quality uplink/downlink channels could provide a higher sum rate. A novel cooperative model was proposed in [45] aided by artificial noise to enhance the physical layer security of underlay DF CRNs. Best-relay selection (BRS) and conventional-relay selection (CRS) schemes were proposed in this work to provide security for SUs’ transmissions.
OP and secrecy outage probability (SOP) with independent but not necessarily identically distributed (i.n.i.d) Rayleigh channels were obtained in [59] to investigate the security of the physical layer for a multihop spectrum-sharing network with a PU constraint. In particular, an novel method was proposed to cope with the balance of security and network performance. On the other hand, the performance of dual-hop AF CRNs over lognormal channels was investigated in [60] using time-switching-based relaying (TSR) and power-splitting-based relaying (PSR) techniques. The simulation results showed that the PSR scheme had an insensitive impact on the overall throughput.
2. Motivations and Contributions
In this work, we focus on the best-relay selection scheme for cognitive relay networks given that it represents a promising approach to improve the performance of cooperative wireless networks because it can generally achieve a cooperative diversity gain without deploying multiple antennas at the source or destination. In particular, a relay node is selected from a set of relays with optimization criteria as the outage probability. This mechanism offers reasonable costs in terms of network complexity. The main novelties of the model proposed and analysed in this work are combining cooperative communication with spectrum-sharing networks and exploiting the BRS scheme in CRNs over Nakagami-m fading channels. The fading model was selected as Nakagami-m because it was the most appropriate model for indoor multipath propagation [61,62].
The main contributions of this work are as follows:
- (1)
- A system model for a cognitive underlay network with multiple AF relays using a BRS scheme is proposed to enhance the network performance.
- (2)
- The OP, which is one of the essential metrics to investigate the performance of mobile networks, is evaluated under interference power constraints over i.n.i.d Nakagami-m fading channels.
- (3)
- The impact of several factors that may affect the system performance, such as the number of relays, the fading severity parameters and the PU location, is investigated.
The rest of this work is organised as follows. First, Section 3 provides the system and channel models. In addition, the CRN structure is introduced. The outage probability analysis is presented in Section 4 using the BRS strategy. The considered methodology, simulation environment and obtained results are provided in Section 5. The conclusions are summarised in Section 6. Finally, a few ideas are presented as future work in Section 7.
3. System Model and Preliminaries
As depicted in Figure 1 below, a dual-hop cognitive relaying network is considered. The network consists of one PU, one SU and a few relays. In particular, the SU comprises a source node S, multiple AF relays () and a destination D. The interference from the PU receiver P is considered as well. Moreover, it is supposed that the path loss and severe shadowing prevents the existence of a direct link between S and D. The SU source S transmits the signal in the first hop into N relays under interference power constraint . After that, the received signal is amplified using the relay with a variable gain , and it is forwarded to the SU destination D, where can be expressed as follows
where is the transmit power at S, is the transmit power at , is the power of the AWGN term at , and is the channel coefficient of the link i→j, where and . A single antenna is deployed in all nodes, and the SU relays operate in channel state information (CSI) using AF relays. The PU source is located far away from the receiving nodes (i.e., and D) leading to no real interference [63,64]. The BRS scheme is considered here where the best relay is selected based on the highest instantaneous SNR . For the kth relay, the received signal at after the first hop transmission is expressed as
where x is the transmitted signal, is the channel fading coefficient of the link S→, and is the AWGN at , with the power of . The received signal at the SU destination D after the second hop transmission can be expressed as
where is the AWGN at D, with the power of .
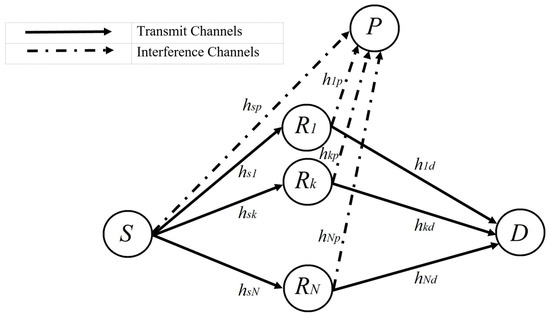
Figure 1.
A cognitive underlay network with multiple AF relays.
All links are assumed to be i.n.i.d. flat Nakagami-m channels where m is an integer fading severity parameter. Moreover, the channel power gains follow the gamma distribution. The means power of the channel power gains are , , and , respectively. Therefore, the cumulative distribution function (CDF) of the channel power gains is given as
and the probability distribution function (PDF) of the channel power gains is given as
where is the corresponding fading severity parameter m, and is the incomplete gamma function given by Equation (8.350.2) [65].
4. Performance Analysis
Evaluating the OP of the considered system model using the BRS scheme requires analysing the instantaneous end-to-end SNR of the link S→→D. This can be obtained using Equation (2) in [66] and therefore can be expressed as follows
where is the instantaneous SNRs for the first hop given by
where is the instantaneous SNRs for the second hop given by
where . Hence, can be expressed as follows
A tighter upper-bound approximation suggested in [67] can be used to obtain a tractable form of Equation (9). Therefore, is used instead of , where can be expressed as follows
The destination D is equipped with a selection combiner (SC) to select the best path for transmission. Hence, the instantaneous SNR at the destination can be expressed as follows
Conditional statistics are applied on the channel coefficient of the link S→P due to the common random variable . On the other hand, the other random variables, , are independent variables. It can be noticed that is the maximum of multiple dependent random variables. Thus, the conditional CDF of the SNR for each path is required and it can be obtained as follows
where . On the other hand, is the minimum of two random variables and its conditional CDF can be expressed as
In order to obtain the conditional CDFs for the two hops, a few notations are assumed for simplicity where , and . Therefore, the instantaneous SNR of the first hop can be rewritten as
In addition, can be expressed as
Then, the first hop’s conditional CDF on Y can be written as
The same procedure is followed to obtain the second hop’s conditional CDF conditioned on Y (i.e., ). Therefore, the instantaneous SNR of the second hop can be rewritten as
Therefore, can be expressed as
Following a few mathematical manipulations which are shown in detail in Appendix A, the conditional CDF of the SNR for the second hop conditioned on Y can be expressed as follows
where is a function of given in Equation (A11). is the Beta function given by Equation (8.384.1) [65] and is the Gauss hypergeometric function given by Equation (9.100) [65].
The conditional CDF for the instantaneous SNR at the destination can be expressed as
Following a few mathematical manipulations which are shown in detail in Appendix B, the conditional CDF can be expressed as follows
where
and
Hence, the OP of the considered system model can be obtained using the following equation
Finally, the outage probability of the considered underlay CRN with BRS with interference constraints using Nakagami-m fading channels can be expressed as
5. Numerical Results and Discussion
In this section, the analytical and simulation results for the OPs of the considered system model are provided and compared for several scenarios. In particular, to capture the effect of the number of relays on the performance of the considered system model, the outages for various number of relays were compared. In addition, to investigate the impact of the channel severity parameters of the SU links, the outages for different severity parameters under a fixed PU location were compared. Furthermore, the impact of the PU location on the outage performance was investigated for different PU locations.
All nodes followed a collinear topology in the considered cognitive relaying network model to study the impact of the path loss on the system outage. The source–destination distance was normalised to one; this means the SU source S and SU destination D were assumed to be located at points with coordinates (0, 0) and (1, 0), respectively. In addition, the SU relay was assumed to be located at a point with coordinates (0.5, 0) at the middle distance between S and D. Each link experienced an exponential decay model for the path loss with a path-loss exponent equal to four. Moreover, the threshold for the outage was assumed to be a 1 dB power.
The outages for the considered spectrum-sharing network under different settings for the number of secondary relays are depicted in Figure 2. It is noteworthy that the diversity order increased by increasing the number of SU relays. The figure shows that the performance of the CRN improved as the number of the SU increased. On the other hand, increasing the number of SU relays would improve the performance but would consume more power and make the network more complex. Moreover, it is worth noting that the BRS scheme selected the best relay from several relays. Therefore, it was not necessarily the case that more improvement would be achieved when we changed the number of relays from two to three compared with the case when we changed the number of relays from one to two. Overall, the simulation results coincided with the derived analytical results and there was an improvement by using more relays within the SU.
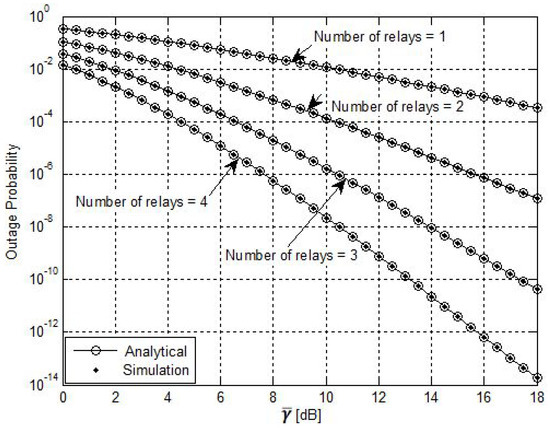
Figure 2.
Impact of number of relays on the system performance, (, and the PU was at (0.6, 0.6)).
The OPs for several fading severity parameters of the SU channels are depicted in Figure 3. In particular, the PU was assumed to be at (0.6, 0.6). The interference links were assumed to have a unity fading severity parameter (i.e., ). Under this assumption, three scenarios with distinct fading severity parameters were investigated; scenario 1: the first hop was less severe compared with the second hop (); scenario 2: both hops had the same severity parameters (); and scenario 3: the second hop was less severe compared with the first hop (). It can be seen that the third scenario outperformed the other scenarios. This is because the minimum severity parameter for both hops in this scenario was two. The simulation results matched the analytical results as well.
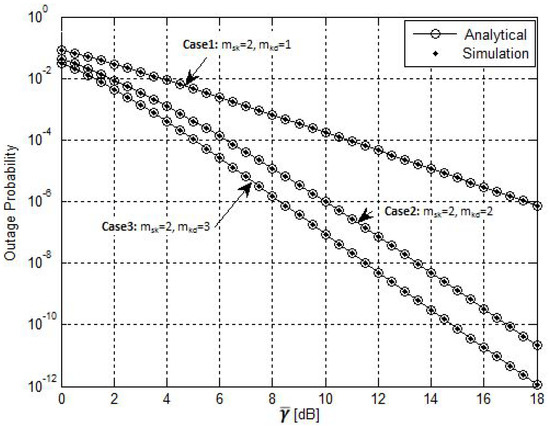
Figure 3.
Impact of severity parameters on the system performance, ().
The impact of the PU location on the OP of the considered system model for several locations of the PU is shown in Figure 4. In particular, the outages for three distinct locations for the PU are provided. The figure shows that as the PU moved away from the SU network, better performance could be achieved, and the interference threshold of the PU could be tolerated. Hence, the best case among the various considered PU locations was achieved when the PU was at the (0.8, 0.8) coordinates. Moreover, the simulation results coincided with the derived analytical results for the various PU locations.
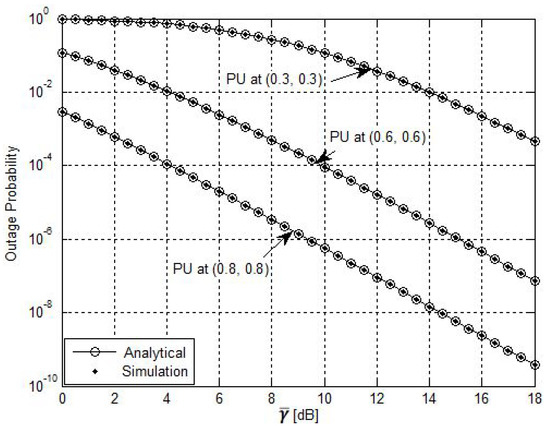
Figure 4.
Impact of primary user location on the system performance, ( and ).
6. Conclusions
In this paper, we studied the outage performance of a cognitive multiple-AF-relay network with a best-relay selection (BRS) strategy under primary user constraints. For this study, we proposed a system model that merged cooperative communication and spectrum-sharing techniques together, in which all channels were modelled using a Nakagami-m fading model. The proposed system model was studied in terms of SNR and OP under different scenarios. In particular, the impacts of increasing the number of SU relays, the fading severity parameters and the primary user location were investigated. The OPs for these different scenarios were evaluated mathematically using the BRS scheme. Thereafter, the theoretical results were verified using a Monte Carlo simulation. The obtained results demonstrated that the OP of the spectrum-sharing network could be improved using cooperative diversity. In addition, the outage performance also depended on the minimum fading severity parameters of the SU hops. Moreover, the PU location took part in the performance of the cognitive relay network. These key results are significant for network providers in order to design a mobile network.
7. Future Work
As future work, the work in this paper can be extended considering other relaying techniques such as decode-and-forward (DF) and compress-and-forward (CF) to investigate the impact of the relaying technique on the network performance. In addition, it can be extended by deploying more primary and secondary users to investigate the impact and constraints of increasing the number of users. Moreover, the impact of several parameters such as the number of relays and fading severity parameters on the outage performance and the total sum rate can be explored for higher number of users.
Author Contributions
The authors contributed equally to this work and the individual contributions are as follows: conceptualization, M.A. and M.F.A.-M.; methodology, M.A. and M.M.S.; software, M.A.; validation, M.F.A.-M. and M.M.S.; writing—original draft, M.A.; supervision, M.F.A.-M. and M.M.S.; writing—review and editing, M.F.A.-M. and M.M.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Applied Science Private University, Amman, Jordan.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Derivation of Fγ2k(γ/Y)
Considering the notations that previously assumed and taking into account that the instantaneous SNR of the second hop is independent of Y, can be rewritten as
Therefore, can be expressed as
Then,
However, and can be represented, respectively, as follows,
and
Hence, Equation (A3) can be written as
The integral can be obtained using Equation (6.455.1) in [65] and therefore, it can be expressed as
where is a function of and it is given by
where is the Beta function given by Equation (8.384.1) [65] and is the Gauss hypergeometric function given by Equation (9.100) [65].
Substituting and in Equation (A7) yields
Appendix B. Derivation of FγSC(γ/Y)
The conditional CDF for the instantaneous SNR at the destination conditioned on Y (i.e., ) can be expressed as
Equation (8.352.4) [65] can be used here and therefore, can be represented as follows
Therefore, can be rewritten as
However, the binomial theorem leads to
Using Equation (A16), can be represented as follows
Thus, the binomial theorem can be exploited here as follows:
On the other hand, the multinomial theorem yields
where the multinomial coefficient, for any integer positive m and any non-negative integer n, is given by
Therefore, the multinomial theorem can be exploited here as follows:
However,
Equation (A22) can be represented as
Thus, can be expressed as follows
For notational simplicity, the following assumption is considered
Thus, can be expressed as
References
- 3GPP. Study on licensed-assisted access to unlicensed spectrum. 3rd Generation Partnership Project (3GPP) 2015, 6, TR 36.889. [Google Scholar]
- Alhulayil, M.; López-Benítez, M. Novel LAA waiting and transmission time configuration methods for improved LTE-LAA/Wi-Fi coexistence over unlicensed bands. IEEE Access 2020, 8, 162373–162393. [Google Scholar] [CrossRef]
- Saleem, R.; Alvi, S.A.; Durrani, S. Performance-fairness trade-off for Wi-Fi and LTE-LAA coexistence. IEEE Access 2021, 9, 62446–62459. [Google Scholar] [CrossRef]
- Alhulayil, M.; López-Benítez, M. Coexistence mechanisms for LTE and Wi-Fi networks over unlicensed frequency bands. In Proceedings of the 2018 11th International Symposium on Communication Systems, Networks & Digital Signal Processing (CSNDSP), Budapest, Hungary, 18–20 July 2018; pp. 1–6. [Google Scholar]
- Saha, R.K. Coexistence of cellular and IEEE 802.11 technologies in unlicensed spectrum bands-a survey. IEEE Open J. Commun. Soc. 2021, 2, 1996–2028. [Google Scholar] [CrossRef]
- Zhang, H.; Leng, S.; Wei, Y.; He, J. A Blockchain Enhanced Coexistence of Heterogeneous Networks on Unlicensed Spectrum. IEEE Trans. Veh. Technol. 2022, 71, 7613–7624. [Google Scholar] [CrossRef]
- Kosek-Szott, K.; Valvo, A.L.; Szott, S.; Gallo, P.; Tinnirello, I. Downlink channel access performance of NR-U: Impact of numerology and mini-slots on coexistence with Wi-Fi in the 5 GHz band. Comput. Netw. 2021, 195, 108188. [Google Scholar] [CrossRef]
- Alhulayil, M.; López-Benítez, M. Methods for the allocation of almost blank subframes with fixed duty cycle for improved LTE-U/Wi-Fi coexistence. In Proceedings of the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 29 October–1 November 2019; pp. 1–6. [Google Scholar]
- Chen, B.; Chen, J.; Gao, Y.; Zhang, J. Coexistence of LTE-LAA and Wi-Fi on 5 GHz with corresponding deployment scenarios: A survey. IEEE Commun. Surv. Tutorials 2017, 19, 7–32. [Google Scholar] [CrossRef]
- Lin, Y. Genetic Algorithm for LTE and WiFi Networks in 5G Heterogeneous Environment. In Proceedings of the 2021 7th International Conference on Computer and Communications (ICCC), Chengdu, China, 10–13 December 2021; pp. 2254–2258. [Google Scholar]
- Alhulayil, M.; López-Benítez, M. Dynamic contention window methods for improved coexistence between LTE and Wi-Fi in unlicensed bands. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference Workshop (WCNCW), Marrakech, Morocco, 15–18 April 2019; pp. 1–6. [Google Scholar]
- Ahmed, M.; Gabr, B.; Afify, L.H.; El-Sherif, A.; Seddik, K.G.; Elattar, M. Machine Learning-based Module for Monitoring LTE/WiFi Coexistence Networks Dynamics. In Proceedings of the 2021 IEEE International Conference on Communications Workshops (ICC Workshops), Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Daraseliya, A.; Korshykov, M.; Sopin, E.; Moltchanov, D.; Andreev, S.; Samouylov, K. Coexistence Analysis of 5G NR Unlicensed and WiGig in Millimeter-Wave Spectrum. IEEE Trans. Veh. Technol. 2021, 70, 11721–11735. [Google Scholar] [CrossRef]
- Alhulayil, M.; López-Benítez, M. Static contention window method for improved LTE-LAA/Wi-Fi coexistence in unlicensed bands. In Proceedings of the 2019 International Conference on Wireless Networks and Mobile Communications (WINCOM), Fez, Morocco, 29 October–1 November 2019; pp. 1–6. [Google Scholar]
- Alhulayil, M.; López-Benítez, M. LTE/Wi-Fi coexistence in unlicensed bands based on dynamic transmission opportunity. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Seoul, Republic of Korea, 6–9 April 2020; pp. 1–6. [Google Scholar]
- Loginov, V.; Troegubov, A.; Lyakhov, A.; Khorov, E. Enhanced Collision Resolution Methods with Mini-Slot Support for 5G NR-U. IEEE Access 2021, 9, 146137–146152. [Google Scholar] [CrossRef]
- Patriciello, N.; Lagén, S.; Bojović, B.; Giupponi, L. NR-U and IEEE 802.11 technologies coexistence in unlicensed mmWave spectrum: Models and evaluation. IEEE Access 2020, 8, 71254–71271. [Google Scholar] [CrossRef]
- Girmay, M.; Shahid, A.; Maglogiannis, V.; Naudts, D.; Moerman, I. Machine learning enabled Wi-Fi saturation sensing for fair coexistence in unlicensed spectrum. IEEE Access 2021, 9, 42959–42974. [Google Scholar] [CrossRef]
- Chakraborty, P.; Prakriya, S. Secrecy outage performance of a cooperative cognitive relay network. IEEE Commun. Lett. 2017, 21, 326–329. [Google Scholar] [CrossRef]
- Wang, D.; Liang, W.; Hu, X.; Zhai, D.; Zhang, D. Cooperative privacy provisioning for energy harvesting based cognitive multi-relay networks. China Commun. 2020, 17, 125–137. [Google Scholar] [CrossRef]
- Fan, Y.; Liao, X.; Yao, R.; Zuo, X.; Zhu, Z. Secure Precoding Scheme for Full-Duplex MIMO Untrusted Relay Network with Energy Harvesting. In Proceedings of the 2020 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Macau, China, 21–24 August 2020; pp. 1–5. [Google Scholar]
- Zhang, Y.; Zhao, Y.; Zhou, Y. User-Centered Cooperative Communication Strategy for 5G Internet of Vehicles. IEEE Internet Things J. 2022, 9, 13486–13497. [Google Scholar] [CrossRef]
- Jingjing, B.; Junjie, W.; Chunliang, H. The Study of Cooperative Diversity Scheme for Indoor Visible Light Communication. In Proceedings of the 2019 IEEE International Conference on Computation, Communication and Engineering (ICCCE), Fujian, China, 8–10 November 2019; pp. 253–255. [Google Scholar]
- Wang, Z.; Guo, J.; Chen, Z.; Yu, L.; Wang, Y.; Rao, H. Robust secure UAV relay-assisted cognitive communications with resource allocation and cooperative jamming. J. Commun. Netw. 2022, 24, 139–153. [Google Scholar] [CrossRef]
- Radi, W.; Abdel-Hadi, R.H.; El-Badawy, H.M.; El-Ramly, S.H. Performance assessment for cognitive cooperative multiple relays network (CCMRN) with imperfect channel state information. IEEE Access 2018, 6, 44607–44615. [Google Scholar] [CrossRef]
- Sharmila, A.; Dananjayan, P. Spectrum sharing techniques in cognitive radio networks–A survey. In Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 29–30 March 2019; pp. 1–4. [Google Scholar]
- Sun, C.; Jiao, R. Discrete exclusion zone for dynamic spectrum access wireless networks. IEEE Access 2020, 8, 49551–49561. [Google Scholar] [CrossRef]
- Kachroo, A.; Ekin, S.; Imran, A. Statistical modelling of dynamic interference threshold and its effect on network capacity. IEEE Trans. Veh. Technol. 2020, 69, 5102–5114. [Google Scholar] [CrossRef]
- Liang, W.; Xin Ng, S.; Hanzo, L. Cooperative Overlay Spectrum Access in Cognitive Radio Networks. IEEE Commun. Surv. & Tutor. 2017, 19, 1924–1944. [Google Scholar]
- Wu, X.; Zhang, L.; Wu, Z. Quantized soft-decision-based compressive reporting design for underlay/overlay cooperative cognitive radio networks. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 1044–1055. [Google Scholar] [CrossRef]
- Viswanathan, H.; Mogensen, P.E. Communications in the 6G era. IEEE Access 2020, 8, 57063–57074. [Google Scholar] [CrossRef]
- Li, Q.; Wen, M.; Dang, S.; Basar, E.; Poor, H.V.; Chen, F. Opportunistic spectrum sharing based on OFDM with index modulation. IEEE Trans. Wirel. Commun. 2020, 19, 192–204. [Google Scholar] [CrossRef]
- Qian, S.; He, X.; Zhou, X. Physical Layer Security in Untrusted Diamond Relay Networks with Imperfect Source-Relay Links. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022; pp. 1–6. [Google Scholar]
- Al-Mistarihi, M.F.; Mohaisen, R.; Darabkh, K.A. Closed-form expression for BER in relay-based df cooperative diversity systems over Nakagami-m fading channels with non-identical interferers. In Internet of Things, Smart Spaces, and Next Generation Networks and Systems. NEW2AN ruSMART 2019; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11660, pp. 700–709. [Google Scholar]
- Al-Mistarihi, M.F.; Mohaisen, R.; Darabkh, K.A. BER analysis in relay-based DF cooperative diversity systems over Rayleigh fading channels with non-identical interferers near the destination. In Proceedings of the 2019 International Conference on Advanced Communication Technologies and Networking (CommNet), Rabat, Morocco, 12–14 April 2019; pp. 1–5. [Google Scholar]
- Pan, X.; Ge, S.; Zhou, X.; Wang, Z. Physical Layer Security in Untrusted Decode-and-Forward Relay Networks Allowing Intra-Link Errors. In Proceedings of the 2019 15th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), Shenzhen, China, 11–13 December 2019; pp. 119–124. [Google Scholar]
- Alghorani, Y.; Chekkouri, A.S.; Chekired, D.A.; Pierre, S. Improved S-AF and S-DF relaying schemes using machine learning based power allocation over cascaded Rayleigh fading channels. IEEE Trans. Intell. Transp. Syst. 2020, 22, 7508–7520. [Google Scholar] [CrossRef]
- Ai, Y.; Mathur, A.; Cheffena, M.; Bhatnagar, M.R.; Lei, H. Physical layer security of hybrid satellite-FSO cooperative systems. IEEE Photonics J. 2019, 11, 1–14. [Google Scholar] [CrossRef]
- Rizinski, M.; Kafedziski, V. Outage probability of AF, DF and CF cooperative strategies for the slow fading relay channel. In Proceedings of the 2013 11th International Conference on Telecommunications in Modern Satellite, Cable and Broadcasting Services (TELSIKS), Nis, Serbia, 16–19 October 2013; pp. 609–612. [Google Scholar]
- Sultan, K. Best relay selection schemes for NOMA based cognitive relay networks in underlay spectrum sharing. IEEE Access 2020, 8, 190160–190172. [Google Scholar] [CrossRef]
- Jia, S.; Zhang, J.; Zhao, H.; Xu, Y. Relay selection for improved security in cognitive relay networks with artificial noise. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018; pp. 1–5. [Google Scholar]
- Chopra, K.; Bose, R.; Joshi, A. Secrecy performance of threshold-based cognitive relay network with diversity combining. J. Commun. Netw. 2018, 20, 383–395. [Google Scholar] [CrossRef]
- Andrawes, A.; Nordin, R.; Ismail, M. Wireless energy harvesting with cooperative relaying under the best relay selection scheme. Energies 2019, 12, 892. [Google Scholar] [CrossRef]
- Banerjee, J.S.; Chakraborty, A.; Chattopadhyay, A. A decision model for selecting best reliable relay queue for cooperative relaying in cooperative cognitive radio networks: The extent analysis based fuzzy AHP solution. Wirel. Netw. 2021, 27, 2909–2930. [Google Scholar] [CrossRef]
- Jia, S.; Zhang, J.; Zhao, H.; Lou, Y.; Xu, Y. Relay selection for improved physical layer security in cognitive relay networks using artificial noise. IEEE Access 2018, 6, 64836–64846. [Google Scholar] [CrossRef]
- Li, D. Cognitive relay networks: Opportunistic or uncoded decode-and-forward relaying? IEEE Trans. Veh. Technol. 2014, 63, 1486–1491. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS aided hybrid satellite-terrestrial relay networks: Joint beamforming design and optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-based secure energy efficient beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 1–4. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Wang, J.B.; De Cola, T.; Wang, J. Joint beamforming and power allocation for satellite-terrestrial integrated networks with non-orthogonal multiple access. IEEE J. Sel. Top. Signal Process. 2019, 13, 657–670. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; De Cola, T.; Wang, J.B.; Zhu, W.P.; Cheng, J. Supporting IoT with rate-splitting multiple access in satellite and aerial-integrated networks. IEEE Internet Things J. 2021, 8, 11123–11134. [Google Scholar] [CrossRef]
- Cho, K.; Lee, J.; Kang, C.G. Stochastic geometry-based coverage and rate analysis under Nakagami & log-normal composite fading channel for downlink cellular networks. IEEE Commun. Lett. 2017, 21, 1437–1440. [Google Scholar]
- Ghavami, H.; Moghaddam, S.S. Outage probability of device to device communications underlaying cellular network in Suzuki fading channel. IEEE Commun. Lett. 2017, 21, 1203–1206. [Google Scholar] [CrossRef]
- Yang, Q.; Zhu, L.; Xie, M.; Zhu, M.; Zhao, H. Performance Analysis in Multi-Relay DF Cognitive Relay Networks under Nakagami–m fading channels. In Proceedings of the 2020 IEEE Computing, Communications and IoT Applications (ComComAp), Beijing, China, 20–22 December 2020; pp. 1–6. [Google Scholar]
- Shurman, M.; Al-Mistarihi, M.F.; Alhulayil, M. Outage probability of dual-hop amplify-and-forward cognitive relay networks under interference power constraints over Nakagami-m fading channels. In Proceedings of the 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 25–29 May 2015; pp. 516–520. [Google Scholar]
- Alhulayil, M.; Al-Mistarihi, M.F.; Shurman, M. Outage probability of amplify-and-forward underlay cognitive relay networks with selection diversity over Nakagami-m fading channels. In Proceedings of the 2015 38th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 25–29 May 2015; pp. 521–525. [Google Scholar]
- Shurman, M.M.; Al-Mistarihi, M.F.; Alhulayil, M.M. Performance analysis of amplify-and-forward cognitive relay networks with interference power constraints over Nakagami-m fading channels. IET Commun. 2016, 10, 594–605. [Google Scholar] [CrossRef]
- Ding, J.; Yang, Q.; Xie, Y. Performance analysis of MRC technique in DF cognitive relay networks. In Communications, Signal Processing, and Systems. CSPS 2017; Lecture Notes in Electrical Engineering; Springer: Singapore, 2017; Volume 463, pp. 1040–1048. [Google Scholar]
- Shirvani Moghaddam, S.; Alibeigi, M. Sum-rate maximization based on power constraints for cooperative AF relay networks. J. Commun. Eng. 2017, 6, 1–25. [Google Scholar]
- Pham, M.N. On the secrecy outage probability and performance trade-off of the multi-hop cognitive relay networks. Telecommun. Syst. 2020, 73, 349–358. [Google Scholar] [CrossRef]
- Liu, Y.; Shen, J.; Pan, Z.; Xiao, R.; Yang, H.; Yan, C. Performance analysis of dual-hop AF relaying networks over log-normal fading channels with interferences. In Proceedings of the 2019 IEEE/CIC International Conference on Communications Workshops in China (ICCC Workshops), 11–13 August 2019; pp. 130–135. [Google Scholar]
- Yura, H.; Beck, S. Multipath scintillation statistics obtained from RF measurements near the earth’s surface. IEEE Trans. Antennas Propag. 2019, 67, 400–414. [Google Scholar] [CrossRef]
- Yan, C.; Fu, L.; Zhang, J.; Wang, J. A comprehensive survey on UAV communication channel modeling. IEEE Access 2019, 7, 107769–107792. [Google Scholar]
- Liu, Z.; Liang, C.; Yuan, Y.; Guan, X. Energy efficient resource allocation based on relay selection and subcarrier pairing with channel uncertainty in cognitive radio network. Comput. Netw. 2019, 161, 82–92. [Google Scholar] [CrossRef]
- Hu, Z.; Cheng, J.; Zhang, Z.; Liang, Y.C. Performance analysis of collaborative beamforming with outdated CSI for multi-relay spectrum sharing networks. IEEE Trans. Veh. Technol. 2018, 67, 11627–11641. [Google Scholar] [CrossRef]
- Gradshteyn, I.; Ryzhik, I. Tables of Integrals, Series and Products, 7th ed.; Academic Press (Elsevier): Burlington, MA, USA; London, UK, 2007. [Google Scholar]
- Hasna, M.O.; Alouini, M.S. Outage probability of multihop transmission over Nakagami fading channels. IEEE Commun. Lett. 2003, 7, 216–218. [Google Scholar] [CrossRef]
- Ikki, S.; Ahmed, M.H. Performance analysis of cooperative diversity wireless networks over Nakagami-m fading channel. IEEE Commun. Lett. 2007, 11, 334–336. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).