Abstract
Sparse Code Multiple Access (SCMA) is capable of ameliorating the performance of wireless communication systems for massive connectivity. The sparsity of the codeword allows SCMA to employ the message-passing algorithm (MPA) at the receiver to address the connection overload. The detection complexity of traditional MPA, on the other hand, is exponentially exploding with the increasing number of connected devices. In this paper, a low-complexity MPA scheme is developed with the threshold and dynamical user removal algorithm (TB-RMPA) based on shuffled MPA (SMPA). By introducing the concept of Iterative Elimination of Dominated Strategies (IEDS) in game theory, a novel method of assigning different dominance levels to users is proposed hereby, and a threshold criterion is discussed to judge the reliability of user decoding. Inspired by this, users with reliable decoding in the iterative process will be dynamically eliminated in each iteration. The numerical analysis revealed that the new TB-RMPA detector’s implementation complexity decreases significantly compared with SMPA, while the symbol error ratio performance degrades unnoticeably.
1. Introduction
Communication resources have become scarce treasures due to the unprecedented expansion of access users. Multiple access technology is regarded as a critical technology to circumvent the problem. However, orthogonal multiple access technology (OMA) normally cannot meet the requirements of massive connection, ultra-high data transmission rate, and low latency for future mobile communications. A new multiple access technology, namely non-orthogonal multiple access (NOMA), has been developed for providing high spectrum utilization and massive connections [1,2]. By overlapping user data information to increase the system capacity, NOMA supports the non-orthogonal transmission of signals, albeit with increasing the computational complexity.
Sparse Code Multiple Access (SCMA) is an emerging NOMA technology based on multidimensional codebooks that is theoretically derived from low-density signature code division multiple access (LDS-CDMA) [3,4,5]. CDMA applies spread spectrum technology and distinguishes different users by assigning different code sequences. The transmitter in the CDMA system performs quadrature amplitude modulation (QAM) on the bit data stream after forwarding error correction. Thereafter, the wide-bandwidth spreading sequence generated by the spreading sequence generator will spread the modulated signal. After adding the inverse fast Fourier transform (IFFT), the user information is superimposed and sent through the channel. SCMA integrates the QAM modulator and the spread spectrum part of the LDS-CDMA system at the transmitting end, directly mapping the incoming bits to the complex multidimensional codeword after channel coding. Different users hold dedicated codebooks, and the spreading coding part selects a codeword from each codebook for transmission according to user data.
For SCMA, the received signal is a mixed superposition of codewords of each user, and there is a certain degree of interference among different users. Ordinary orthogonal separation methods cannot distinguish user information, and joint multi-user detection is required for data separation. The key challenges for multi-user detection (MUD) are serious multiple access interference and considerable processing complexity. To tackle this, sophisticated methods have been designed to save computing resources [6,7,8]. An improved MUD scheme is advocated by employing maximum joint posterior probability (MAP) detection and over-searching. However, this algorithm incurs significant additional complexity. By leveraging the sparse structure, theoretically, SCMA can obtain multi-user detection with close to maximum likelihood (ML) performance by utilizing a less complex message-passing algorithm (MPA) detector.
Multiple compelling decoders modified from MPA have been proposed to approximate the optimal performance [9,10,11]. Unfortunately, the detection complexity of traditional MPA grows exponentially as the the number of access devices grows. Hence, some plausible approaches are developed to simplify the MPA calculation. By removing all exponential operations, MAX-Log-MPA and Log-MPA have reasonably low complexity, albeit with slightly sacrificed performance [12,13,14]. In [15], MPA and the compressed sensing (CS) technique are combined, and a compressive sampling matching algorithm is introduced to correct the error code. Additionally, refs. [16,17] reclassify the information transmitted in factor graphs as strong edges and interference. The unselected edges are processed by Gaussian approximation (ESGA). In reference [18], a modified ESGA scheme is proposed, and a threshold selection method is introduced to define a strong neighbor edge group. The method devised in [19] adopts the expectation propagation algorithm (EPA) in a massive MU-MIMO SCMA system. QR decomposition and decentralized function nodes are employed to improve the performance. Codebook optimization methods are also applied to reduce the complexity by utilizing different codebook structures and design approaches [20,21,22,23]. Moreover, a partial marginalization (PM) MPA algorithm is investigated to further simplify the iterative processing [24]. However, the parallel technique is ineffective in terms of convergence rate. To address this issue, shuffled MPA (SMPA), a novel multi-user detection approach for uplink SCMA systems that employs a dissimilar message update method, has been developed [25].
Specifically, the essence of the MPA algorithm is to utilize the iterative update of the information between the factor nodes to obtain the optimal solution. Unfortunately, reducing the algorithm’s computing complexity remains a challenging task due to the iterative process’s intricacy. Recent studies demonstrate that game theory is capable of studying the act of association and interaction of different autonomous nodes thanks to its excellent processing and optimization capabilities for mathematical problems [26,27]. In recent years, game theory models have been widely used as an analysis tool to circumvent problems such as congestion control, power control, decoding, and algorithm optimization [28,29,30,31]. In the game process, participants always hope to continuously eliminate inferior strategies, and they finally obtain a dominant strategy to maximize their own benefits, which is the definition of Iterative Elimination of Dominated Strategies (IEDS). From the game theory perspective, each iteration process in the MPA algorithm can be regarded as a game, and each user can be regarded as a strategy in the game.
Inspired by [25], we amalgamate IEDS in game theory with an SMPA detection scheme to conceive a low-complexity MUD for uplink SCMA. Specifically, we develop a novel threshold-based SCMA detection scheme with a dynamical user removal algorithm (TB-RMPA). We provide substantial analysis and numerical simulations to study the decoding performance of the proposed algorithm. The main contributions of this paper are summarized as follows.
- An improved low-complexity MPA receiver for SCMA is proposed. This scheme, of sequential nature, was further generalized to the SMPA scheme imposing a threshold-based criterion for dynamically weeding out users.
- An advantage user-ranking method is introduced based on the factor graph, and users are sorted in descending order before searching so that reliable nodes can be pruned in subsequent iterations. Additionally, we combine the idea of repeatedly eliminating disadvantages in game theory with the iterative serial message algorithm, and we treat every user whose information has been reliably decoded as a strict inferior strategy that can be eliminated.
- The threshold is set to determine the reliability and stability of the signal. In the iterative process, the current optimal user will be judged in each iteration. Once the threshold condition is met, the current optimal user will be deleted. Meanwhile, we use the parameter to balance the system error performance and complexity.
The remainder of this paper is structured as follows. We first elaborate on the system model of SCMA in Section 2. Furthermore, the original MPA detection algorithm and SMPA scheme are presented. In Section 3, we put forward the concept of superior users, and the proposed TB-RMPA scheme is presented. The decoding complexity and performance comparison are discussed in Section 4. Finally, our conclusions are provided in Section 5.
The notations in this paper are as follows. The uppercase boldface letter stands for matrices, the lowercase boldface letter denotes vectors, and normal letters are scalar quantities. denotes the absolute value of scalar x. The n-th unit of the vector is expressed as . denotes the transpose of .
Especially, the abbreviations employed in this paper are illustrated in Table 1 for ease of access.

Table 1.
Summary of abbreviations.
2. System Model
2.1. Principle of SCMA
In the SCMA system, J and K denote the number of access users and physical resources orthogonal to each other, respectively. In a non-orthogonal system, the channel can be overloaded, and the number of J is usually greater than K. The overloading factor is defined as the ratio of users to physical resources. Table 2 presents the definitions and key points of the parameters in the uplink SCMA system [32,33].

Table 2.
The parameters in the uplink SCMA system.
Figure 1 illustrated an uplink SCMA system. The initial information bits are coded into in the channel encoding section by utilizing a Low-Density Parity Check Code (LDPC) represented by a check matrix [34]. Thereafter, the system users select corresponding codewords from the codebook at the transmitter, and the coded bitstreams are directly mapped to the K-dimensional plural codewords . The K-dimensional codewords comprise N non-zero elements, and each codebook contains M codewords. The mapped codeword will be superimposed and sent on each physical resource. The mapping relationship can be expressed as , for user j, where .
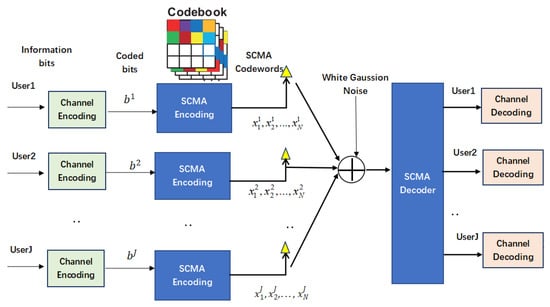
Figure 1.
SCMA multiplexing scheme.
The transmitted signal at the receiver can be expressed as
where represents the SCMA codeword sent by the j-th user, and stands for the channel coefficient vector between the base station and user j. In this paper, the channels are modeled as an independent Rayleigh channel and Rician channel. is the white noise vector, which obeys the Gaussian distribution of . indicates the variance of each element of , and is the identity matrix. The factor graph matrix reflects the user’s usage of transmission resources. The total number of “1” in each row and column of are denoted by and , respectively. The received signal is subjected to multi-user detection in the SCMA decoder, and the detected LDPC signal is decoded by a belief propogation algorithm [35].
2.2. Original MPA Multi-User Detection for Uplink SCMA
Assuming that the receiving signal and the user channel gain are all known conditions, we can use the MAP algorithm to detect the user’s codeword combination. The joint optimal MAP detection will estimate the joint posterior probability function that maximizes the transmitted symbols, which can be expressed as
Although MAP is the optimal multi-user detection algorithm, its complexity is too high. Therefore, MPA, a message-passing algorithm with close performance but low computational complexity, has become the focus of research in the industry at this stage. MPA uses the idea of iteration based on bipartite factor graph modeling. Function nodes (FNs) and variable nodes (VNs) represent the transmission layers and users, respectively [36]. Iteration is repeated feedback, and the result obtained each time will become the initial value of the next iteration. The MPA algorithm obtains a performance close to the maximum likelihood through continuous iterative updates of the information transmitted between the nodes. When the number of iterations meets the maximum number of iterations set initially, the user codeword is judged and output. The following optimal detection criterion is admitted.
The posterior probabilities are calculable with the factor graph known. For ease of notation, we define as the probability that user node transfers codeword information to resource node during the t-th iteration. denotes the probability that resource node transfers codeword information to user node during the t-th iteration, and t represents the number of the current iteration. The update of information is divided into two steps. (1) Resource nodes use external information from user nodes to update information. (2) User nodes use external information from resource nodes to update information [37,38]. The two processes are expressed by mathematical formulas as
where represents all elements in except j, and represents all elements in except k. The algorithm will continue to repeat the two steps of the iterative process until the maximum number of iteration is reached and then execute the decision output. A posterior probability for the corresponding codeword can be represented as
The binary log-likelihood ratios (LLRs) to decide the bits are
2.3. SMPA Multi-User Detection Scheme
In the traditional MPA algorithm, the new messages generated in the current iteration will not be used until the next iteration. The SMPA algorithm does not update the function node and the variable node sequentially. It updates a function node and then updates the related variable node, so that the function node information updated in the current iteration can be used for other function node updates in the same round [25]. Different from the traditional MPA algorithm, the update of the variable node in the SMPA algorithm is immediately after the update of each function node. The update of information iteration in the SMPA algorithm can be modified as
It can be seen from Equation (9) that the message of the variable node updated in this round of iteration has been used when some function nodes are updated in this round of iterations. Obviously, the updated variable node messages in this round are more reliable than the previous round variable node messages; that is, the message propagation in the SMPA algorithm is more timely, which makes the convergence speed faster.
In order to further simplify the complexity of the algorithm, we give priority to preprocessing the algorithm by moving the iterative process into the logarithmic domain, which follows the Jacobian logarithm formula.
3. Proposed Detection Schemes for UPLINK SCMA
The traditional MPA algorithm and the S-MPA algorithm both detect the user signals uniformly after the algorithm is executed to the maximum number of iterations, and each user will participate in the process of each iteration, so the execution complexity of the algorithm is very high. In this section, we propose a new low-complexity decoder based on confidence stability and dynamic user culling, called TB-RMPA, to reach equilibrium between error rate performance and complexity.
3.1. Iterative Elimination of Dominated Strategies
In game theory, the ideal goal is to obtain the maximum benefit at the minimum cost [26,27]. Participants in each game are independent decision-makers, and their benefits depend on the actions of other participants. Convergence of the game to a steady state is the Nash equilibrium. The usual way to identify a game Nash equilibrium is to do an exhaustive search, but this is very complicated, and we hope to reduce the search process as much as possible.
There is a definition of a disadvantageous strategy in game theory, where it shows that participants can always recognize bad strategies based on rational assumptions, and these strategies definitely can be avoided. If holds for all , and for a certain , , then the strategy is inferior to .
If all participants actually understand the strict bad strategies that every participant will not adopt, then they can effectively ignore the strict bad strategies that their opponents will not adopt. If the initial game has some players with strict inferior strategies, then all the players know that they are facing a small-scale restricted game because the number of total strategies is reduced.
We introduce this idea into the decoding algorithm to further reduce the algorithm complexity. Each iteration process can be regarded as a game, and each user can be regarded as a strategy in the game. When the user’s decoding reaches the optimal level, it becomes an inferior strategy that can be eliminated in the restricted game. After removing the strictly inferior strategy, the new game will not include the strictly inferior strategy that has been removed.
Inspired by this, we can continuously detect and eliminate users with reliable decoding in the iterative process. At this time, we need to deal with two new key issues: first, how to define the user’s decoding reliability to ensure that the elimination of users will not increase the bit error rate and reduce the system performance; second, whether the sequence of multi-user elimination has an impact on the system performance and complexity. Moreover, we also need to determine a good elimination strategy.
3.2. User Ranking
In the traditional parallel message passing algorithm, each VN node is an independent unit. During the iterative update, each VN node searches for the FN node connected to it in the factor graph to update the message. Take the SCMA system whose factor matrix is Equation (14) as an example. Among them, the rows of the sparse matrix represent the number of physical resources, and the columns of the matrix represent the number of users. The content of the matrix contains two elements: ‘0’ and ‘1’; ‘0’ means that the user does not occupy this physical resource, and ‘1’ means that user data occupies this orthogonal resource for transmission.
Figure 2 shows the information iteration update factor graph structure of the traditional parallel message passing algorithm. The user node VN1 uses the resource nodes FN2 and FN4 connected to it to update information, and then, the new VN1 is used as external information to update the information values of FN2 and FN4. According to this rule, each iteration will be updated in the order of the user nodes. The information value of FN will not be calculated until all the messages from FN to VN have been propagated, so that the external information of FN that can be used in time is not fully utilized.
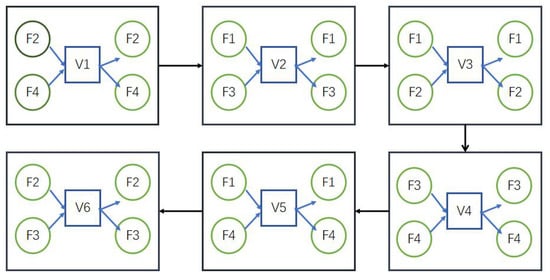
Figure 2.
Information iteration update factor graph structure of traditional parallel message passing algorithm for an SCMA system with , .
Figure 3 displays the information iteration update factor graph structure of the serial message passing algorithm. In an iteration process, we can use the updated VN1 information value as external information to indirectly update VN4 and then use the updated information from VN4 to indirectly update VN2. Once the order of VN nodes is reasonably chosen, an update to the current user node can be synchronously transmitted to other user nodes, so that users can receive more external information and converge faster.
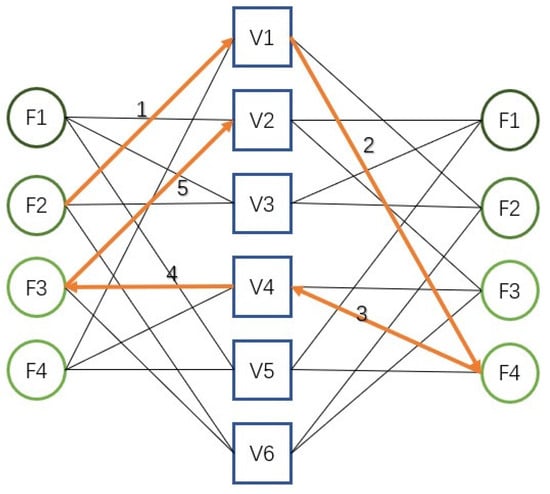
Figure 3.
Information iteration update factor graph structure of the serial message passing algorithm.
In the iterative process, the convergence speed of different user nodes is different. The nodes that converge slowly need more iterations to get a sufficiently reliable decoding. We reasonably choose the order of the VN nodes and sort the user nodes; then, the convergent nodes can be eliminated from the original factor graph, effectively reducing the complexity of the algorithm.
In the process of iterative update of information, the more external information a user iteratively generates, the more reliable his decoding is after this iteration. In other words, this user enjoys a high level of advantage. Since the threshold condition is met, the effect of eliminating the user in the next iteration process on the signal decoding recovery will become minor.
According to the order in which the time-frequency resources are processed, we can assign different initial coefficients to the time-frequency resources. Information decoding on post-processing physical resources is more reliable. Under this principle, for the SCMA system with J = 6 and K = 4, the coefficient of the time-frequency resource can be set to . User ranking level can be jointly expressed by sparse matrix and resource coefficient .
For the SCMA system whose sparse matrix is Formula (15), the order of the dominant users is
3.3. Confidence Stability Based on a Threshold
The algorithm dynamically removes users based on the confidence stability judgment. In each iteration process, the current user with the highest level is judged. We develop a residual-based threshold criterion, which includes two parts: initial threshold and parameter . The threshold is initially set to one-twentieth of the updated information in this iteration, and the final criterion is adjusted by parameter . If the user satisfies Formula (17), the user signal judgment is determined to be sufficiently reliable. The user will be eliminated from the next iteration, and the eliminated user will no longer participate in subsequent iterations processes.
where and coefficient have a value range of (0, 1) .
3.4. TB-RMPA Multiuser Detection Scheme
To address the problem of excessive complexity of the algorithm, we transfer the SMPA algorithm to the logarithmic domain initially and apply the above-mentioned advantageous user dynamic elimination strategy to this algorithm, which is named the TB-RMPA algorithm. Equations (12) and (13) are modified to
The value of the coefficient will affect the overall result of the threshold, which determines the range of signal reliability judgment. We can find the best parameter suitable for the current system through a dynamically selected procedure. Initialize = 1; in this case, the complexity of the system is the lowest. Set an appropriate step size S and target SER to simulate a system over a fixed signal-to-noise ratio. If the simulation performance fails to reach the target, reduce the value of by the step size and repeat the above process until the simulation results meet the expected requirements. If the value is reduced to 0 and SER is still greater than the target, it means that the current signal-to-noise ratio is not suitable. Repeat the process after increasing the signal-to-noise ratio appropriately.
If before the arrival of the maximum number of iterations , then all users have been decoded and eliminated, indicating that the algorithm does not require so many iterations. If the operation reaches the maximum number of iterations , then all remaining undecoded users will be decoded uniformly. It is foreseeable that the more users are eliminated after each iteration, the lower the overall complexity of the decoding algorithm. When = 0, the proposed TB-RMPA scheme is the original serial logSMPA scheme. According to this idea, users are dynamically identified in iterations, and factor graphs are deleted.
Table 3 illustrates the key notations and descriptions of the TB-RMPA algorithm while Algorithm 1 demonstrates the detailed procedure including threshold selection and user dynamic elimination.
| Algorithm 1 TB-RMPA |
| Input:,,,,, S |
| Output: |
|

Table 3.
The notation list of the TB-RMPA algorithm.
For the SCMA system in the previous example with = 0.4, the number of eliminated users is 3 after T iterations. User nodes VN4, VN1, and VN6 are judged to be trusted nodes, and the factor graph is updated as shown in Figure 4.
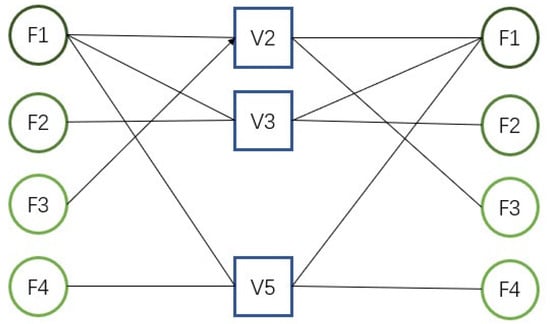
Figure 4.
Updated factor graph structure using TB-RMPA.
3.5. Computational Complexity Analysis
In this subsection, the computational complexities of TB-RMPA are analyzed in detail. SMPA, log-SMPA, edge-selected MPA (ES-MPA) [17], and discretized message passing algorithm (DMPA) [39] are also compared as baselines. The detailed calculation complexity comparison of different detection schemes is shown in Table 4, where the symbol set size for each user is M, the number of physical resources is K, the user number is J, and the maximum iteration number is T. and denote the amount of users hosted by a physical resource and amount of resources occupied by a user. S stands for the number of users that have been eliminated until this iteration. Since the proposed TB-RMPA scheme eliminates users in the iterative process, it is obvious that the number of real-time users and the values corresponding to different resources in FN-to-VN are dynamically changing during each iteration. The proposed scheme can immediately add message propagation in the current iteration and timely eliminate user signals whose decoding is sufficiently reliable to speed up the convergence speed. Therefore, the overall computational complexity can be greatly reduced.

Table 4.
Simulation scenarios with fixed parameters.
4. Simulations
In this section, numerical simulations are presented to validate the analytical results as well as the proposed TB-RMPA scheme. In order to investigate the proposed scheme under different configurations, the computational complexity, SER, and the convergence performances are taken into consideration. In the SCMA system, the number of transmitted stream is J = 6, and the number of resources is K = 4. The channel coding adopts LDPC codes with rate and length . In all simulations, the coded two-dimensional data flow of each user is modulated by a group of four-dimensional complex constellation points, and the channel settings are modeled as independent Rayleigh channel and Rician channel [40].
Figure 5 depicts the computational complexity comparison of the detection schemes with six iterations. To facilitate observation, we have normalized the mathematical operations of the complexity derived in Table 4. Addition is normalized by a ratio of one to one, while multiplication and comparison are normalized by a ratio of one to ten and one to twenty, respectively. Here, we set = 0.2, 0.5, and 0.8 in the TB-RMPA algorithm.
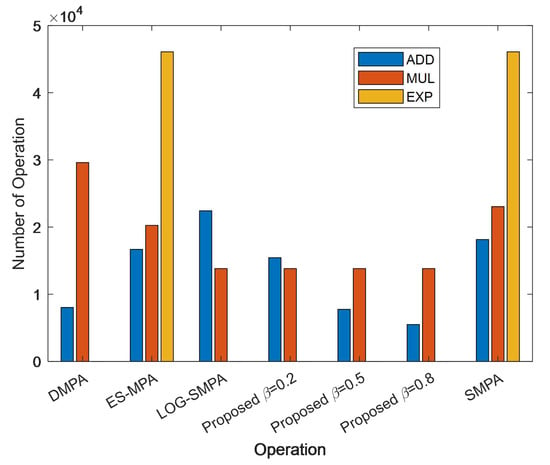
Figure 5.
Complexity comparison of different detection schemes.
As shown, the proposed TB-RMPA has significantly lower computational complexity than the SMPA, Log-SMPA, DMPA, and ES-MPA algorithms. After the iterative user elimination scheme is applied, the TB-RMPA algorithm can save varying degrees of the computational complexity (with different apllied) compared to that of the Log-SMPA receiver. This result demonstrates the superiority of the proposed TB-RMPA scheme.
In Figure 6, we present the result of numerical evaluation complexity of the proposed TB-RMPA for the scenarios in Table 5. From the complexity order prediction above, the value of can be chosen to reduce the average complexity with respect to TB-RMPA. It is inspired that the larger the value of is, the greater complexity reduction ratio can be achieved, which is meaningful for high-efficiency transmission.
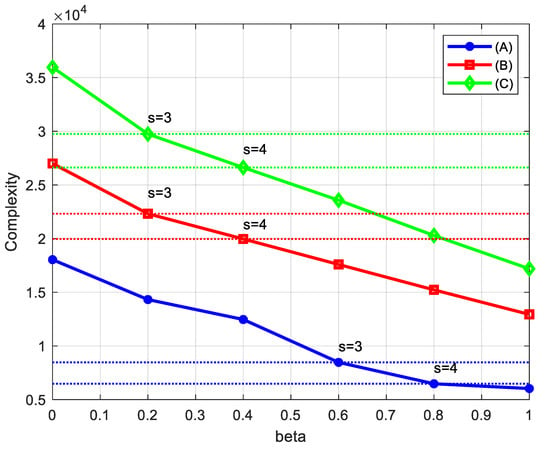
Figure 6.
Complexity of proposed TB-RMPA scheme for scenarios in Table 5. Markers stand for the results of excluded users s = 3 and s = 4 in numerical simulation.

Table 5.
Parameters of different simulation scenarios.
To evaluate the convergence performance of the TB-RMPA detector more intuitively, we demonstrate the SER vs. SNRs at different numbers of outer loop iterations in Figure 7. In our simulation, the basic parameters are set as follows: the number of users is J = 6, the number of subcarriers is , the degrees of the factor graph are = 3 and = 2, and the threshold is = 0.5. As shown, the performance of the receivers improves as iterations increase. After several iterations, the performance gains become marginal. It can be seen that the proposed scheme converges after four outer iterations. The BER curves of the algorithm suffer only negligible BER performance degradation and almost coincide with the optimal curve. Similar results can be obtained for other scenarios, which demonstrate the good convergence of the TB-RMPA receiver.
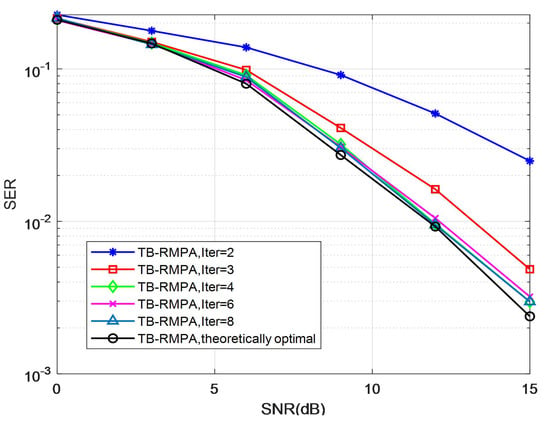
Figure 7.
Convergence performance of TB-RMPA with = 0.5 in the Rayleigh channel.
Figure 8 compares the SER performance versus SNR for the proposed TB-RMPA, SMPA, classic MPA, ES-MPA, and PM-MPA schemes on the Rayleigh channel, respectively. The TB-RMPA decoder has nearly the same SER as the SMPA method, which has a nearly 3 dB performance loss compared to the classic MPA method when iteration = 3. This can be explained that a sufficient number of users cannot be eliminated and the decoding is not reliable enough due to the insufficient iteration of information. The figure illustrates that the proposed scheme has about 3 dB gain over PM-MPA (iteration = 6) and suffers only negligible BER performance degradation compared with the SMPA schemes at SNR = 15. It can be explained that the proposed TB-RMPA can utilize more effective messages to achieve convergence. Compared with other detection algorithms, TB-RMPA achieves similar bit error performance while maintaining low complexity.
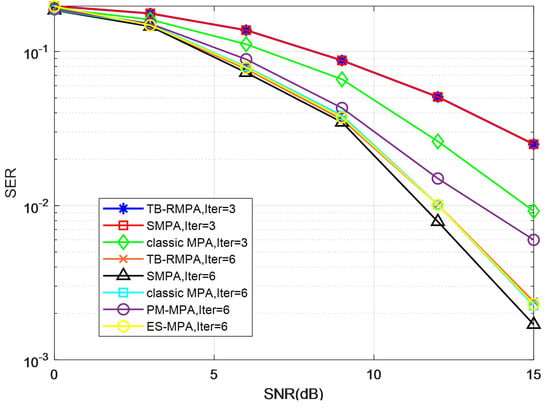
Figure 8.
SER performance comparison of different detection schemes in the Rayleigh channel.
Figure 9 illustrates the SER performance of the proposed TB-RMPA decoder for various numbers of on the Rayleigh channel. It demonstrates that there is a slight performance loss when beta changes. Hence, a comprehensive consideration is supposed to be made between the computational complexity and system performance. Furthermore, the threshold must be revised for different scenarios. Applying the proper threshold to the algorithm allows the system to achieve the desired performance at the lowest accomplishable complexity.
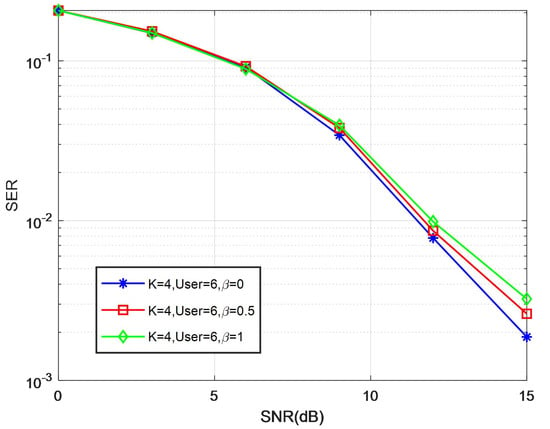
Figure 9.
SER performance comparison of different on the Rayleigh channel.
To illustrate the superior performance of the proposed algorithm, the above simulations are also performed on the Rician channel. Rayleigh distribution is a specific scenario of Rician distribution. Multipath transmission occurs during the transmission of the transmitted signal, which leads to amplitude degradation of the received signal due to the superposition of multiple signals. The distribution of the received signal amplitude can be Rayleigh distribution or Rician distribution. When a path does not have a dominant scattering path, we term it a Rayleigh fading channel. If a path in the multipath is dominant (with only a line-of-sight (LOS) component), that is a Rician fading channel.
In a Rician channel, parameter k is the essential parameter. The link-level simulations adopt k = 10 with other settings same as the preliminary. Figure 10, Figure 11 and Figure 12 show the SER performance on a Rician channel for the TB-RMPA scheme. As Rayleigh fading has a greater impact on the signal, the overall bit error rate of the simulation results in the Rician channel has dropped significantly, but the trend of the curve remains basically unchanged. We can get the same conclusion as the previous simulation.
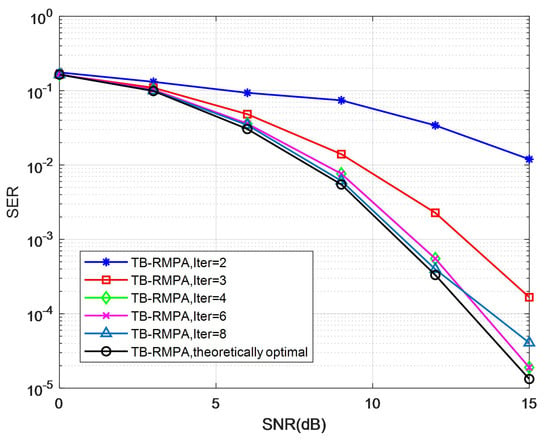
Figure 10.
Convergence performance of TB-RMPA with = 0.5 in a Rician channel.
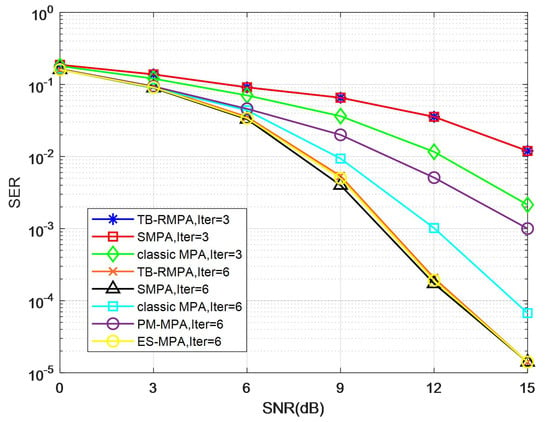
Figure 11.
Comparisonof different detection schemes in a Rician channel.
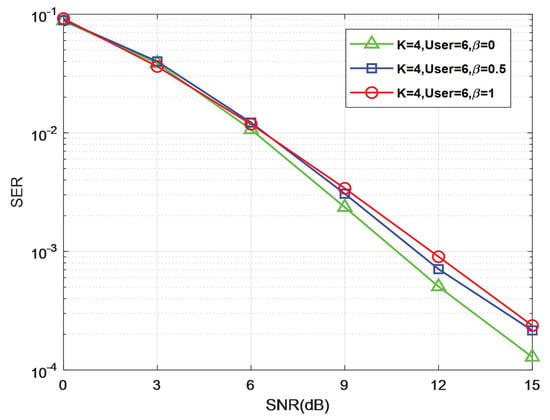
Figure 12.
SER performance comparison of different in a Rician channel.
5. Conclusions
In this paper, we propose a novel low-complexity detection scheme derived from SMPA, and we term our approach TB-RMPA. The modification to SMPA considers a threshold-based confidence stability criterion to weed out users. Specifically, we combine the idea of IEDS in game theory with the SMPA algorithm, assigning different dominance levels to system users based on the factor matrix, and dynamically eliminating the dominant users, which has met the threshold standard in the iterative process. Threshold , as a parameter that can be dynamically adjusted, becomes an effective means to balance the system complexity and bit error rate. Numerical analysis revealed that the proposed algorithm can achieve a significant reduction in computational complexity with a small compromise on BER performance loss.
Author Contributions
Conceptualization, S.L. and Y.F.; methodology, S.L. and Y.F.; software, S.L. and Y.F.; resources, S.L. and Y.F.; data curation, S.L. and Y.F.; writing—original draft preparation, Y.F.; writing—review and editing, Y.S.; supervision, Y.S. and Z.X. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Central University Basic Research Fund of China under Grant CUC210B032.
Conflicts of Interest
The authors declared that we do not have any commercial or associative interest that represents a conflict of interest in connection with the work submitted.
References
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; I, C.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Ding, Z.; Peng, M.; Poor, H.V. Cooperative Non-Orthogonal Multiple Access in 5G Systems. IEEE Commun. Lett. 2015, 19, 1462–1465. [Google Scholar] [CrossRef] [Green Version]
- Nikopour, H.; Baligh, H. Sparse code multiple access. In Proceedings of the 2013 IEEE 24th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), London, UK, 8–11 September 2013; pp. 332–336. [Google Scholar] [CrossRef]
- Au, K.; Zhang, L.; Nikopour, H.; Yi, E.; Bayesteh, A.; Vilaipornsawai, U.; Ma, J.; Zhu, P. Uplink contention based SCMA for 5G radio access. In Proceedings of the 2014 IEEE Globecom Workshops (GC Wkshps), Austin, TX, USA, 8–12 December 2014; pp. 900–905. [Google Scholar] [CrossRef] [Green Version]
- Hoshyar, R.; Wathan, F.P.; Tafazolli, R. Novel Low-Density Signature for Synchronous CDMA Systems Over AWGN Channel. IEEE Trans. Signal Process. 2008, 56, 1616–1626. [Google Scholar] [CrossRef] [Green Version]
- Han, Y.; Zhou, W.; Zhao, M.; Zhou, S. Enabling High Order SCMA Systems in Downlink Scenarios With a Serial Coding Scheme. IEEE Access 2018, 6, 33796–33809. [Google Scholar] [CrossRef]
- Ghaffari, A.; Leonardon, M.; Savaria, Y.; Jego, C.; Leroux, C. Improving performance of SCMA MPA decoders using estimation of conditional probabilities. In Proceedings of the 2017 15th IEEE International New Circuits and Systems Conference (NEWCAS), Strasbourg, France, 25–28 June 2017; pp. 21–24. [Google Scholar] [CrossRef]
- Deepshikha; Vanidevi, M. Modified SCMA Decoder for 5G Uplink System. In Proceedings of the 2018 15th IEEE India Council International Conference (INDICON), Coimbatore, India, 16–18 December 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Sfeir, E.; Mitra, R.; Kaddoum, G.; Bhatia, V. RFF Based Detection for SCMA in Presence of PA Nonlinearity. IEEE Commun. Lett. 2020, 24, 2604–2608. [Google Scholar] [CrossRef]
- Yuan, W.; Wu, N.; Yan, C.; Li, Y.; Huang, X.; Hanzo, L. A Low-Complexity Energy-Minimization-Based SCMA Detector and Its Convergence Analysis. IEEE Trans. Veh. Technol. 2018, 67, 12398–12403. [Google Scholar] [CrossRef]
- Wu, Y.; Zhang, S.; Chen, Y. Iterative multiuser receiver in sparse code multiple access systems. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 2918–2923. [Google Scholar] [CrossRef]
- Zhang, C.; Yang, C.; Pang, X.; Song, W.; Xu, W.; Zhang, S.; Zhang, Z.; You, X. Efficient Sparse Code Multiple Access Decoder Based on Deterministic Message Passing Algorithm. IEEE Trans. Veh. Technol. 2020, 69, 3562–3574. [Google Scholar] [CrossRef]
- Zhang, S.; Xu, X.; Lu, L.; Wu, Y.; He, G.; Chen, Y. Sparse code multiple access: An energy efficient uplink approach for 5G wireless systems. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 4782–4787. [Google Scholar] [CrossRef]
- Wei, F.; Chen, W. Low Complexity Iterative Receiver Design for Sparse Code Multiple Access. IEEE Trans. Commun. 2017, 65, 621–634. [Google Scholar] [CrossRef]
- Durak, M.H.; Ertuğ, Ö. CS-Based Multiuser Detector for SCMA Systems. In Proceedings of the 2019 International Symposium on Networks, Computers and Communications (ISNCC), Istanbul, Turkey, 18–20 June 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Du, Y.; Dong, B.; Chen, Z.; Fang, J.; Gao, P.; Liu, Z. Low-Complexity Detector in Sparse Code Multiple Access Systems. IEEE Commun. Lett. 2016, 20, 1812–1815. [Google Scholar] [CrossRef]
- Wang, Y.; Qiu, L. Edge Selection-Based Low Complexity Detection Scheme for SCMA System. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Silva, B.F.d.; le Ruyet, D.; Uchôa-Filho, B.F. Threshold-Based Edge Selection MPA for SCMA. IEEE Trans. Veh. Technol. 2020, 69, 2957–2966. [Google Scholar] [CrossRef]
- Wang, P.; Liu, L.; Zhou, S.; Peng, G.; Yin, S.; Wei, S. Near-Optimal MIMO-SCMA Uplink Detection With Low-Complexity Expectation Propagation. IEEE Trans. Wirel. Commun. 2020, 19, 1025–1037. [Google Scholar] [CrossRef]
- Xiao, B.; Xiao, K.; Zhang, S.; Chen, Z.; Xia, B.; Liu, H. Iterative detection and decoding for SCMA systems with LDPC codes. In Proceedings of the 2015 International Conference on Wireless Communications & Signal Processing (WCSP), Nanjing, China, 15–17 October 2015; pp. 1–5. [Google Scholar] [CrossRef] [Green Version]
- Miao, J.; Hu, X.; Zhao, Z. A Low Complexity Multiuser Detection Scheme with Dynamic Factor Graph for Uplink SCMA Systems. In Proceedings of the 2019 IEEE/CIC International Conference on Communications in China (ICCC), Changchun, China, 11–13 August 2019; pp. 846–851. [Google Scholar] [CrossRef]
- Hao, Y.; Xiao, K.; Chen, Z.; Xia, B. Density evolution analysis of LDPC-coded SCMA systems. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 11–13 October 2017; pp. 1–6. [Google Scholar] [CrossRef]
- He, Q.; Bai, B.; Feng, D.; Xu, H.; Zhu, M. A Nonbinary LDPC-Coded SCMA System with Optimized Codebook Design. In Proceedings of the 2017 IEEE 86th Vehicular Technology Conference (VTC-Fall), Toronto, ON, Canada, 24–27 September 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Mu, H.; Ma, Z.; Alhaji, M.; Fan, P.; Chen, D. A Fixed Low Complexity Message Pass Algorithm Detector for Up-Link SCMA System. IEEE Wirel. Commun. Lett. 2015, 4, 585–588. [Google Scholar] [CrossRef]
- Du, Y.; Dong, B.; Chen, Z.; Fang, J.; Yang, L. Shuffled Multiuser Detection Schemes for Uplink Sparse Code Multiple Access Systems. IEEE Commun. Lett. 2016, 20, 1231–1234. [Google Scholar] [CrossRef]
- Xu, X.; Wang, Y.; Liu, J.; Zhang, X. Analysis on the achievement milestones and limitations of Game Theory. In Proceedings of the 2008 Chinese Control and Decision Conference, Yantai, China, 2–4 July 2008; pp. 1214–1219. [Google Scholar] [CrossRef]
- Wooldridge, M. Does Game Theory Work? IEEE Intell. Syst. 2012, 27, 76–80. [Google Scholar] [CrossRef]
- Junhui, Z.; Tao, Y.; Yi, G.; Jiao, W.; Lei, F. Power control algorithm of cognitive radio based on non-cooperative game theory. China Commun. 2013, 10, 143–154. [Google Scholar] [CrossRef]
- Wang, B.; Han, Z.; Liu, K.J.R. Distributed Relay Selection and Power Control for Multiuser Cooperative Communication Networks Using Stackelberg Game. IEEE Trans. Mob. Comput. 2009, 8, 975–990. [Google Scholar] [CrossRef] [Green Version]
- Xiao, M.; Shroff, N.B.; Chong, E.K.P. Utility-based power control in cellular wireless systems. In Proceedings of the IEEE INFOCOM 2001, Conference on Computer Communications, Twentieth Annual Joint Conference of the IEEE Computer and Communications Society (Cat. No.01CH37213), Anchorage, AK, USA, 22–26 April 2001; Volume 1, pp. 412–421. [Google Scholar] [CrossRef]
- La, R.J.; Anantharam, V. Optimal routing control: Game theoretic approach. In Proceedings of the 36th IEEE Conference on Decision and Control, San Diego, CA, USA, 12 December 1997; Volume 3, pp. 2910–2915. [Google Scholar] [CrossRef] [Green Version]
- Hou, Z.; Xiang, Z.; Ren, P.; Cao, B. SCMA Codebook Design Based on Divided Extended Mother Codebook. IEEE Access 2021, 9, 71563–71576. [Google Scholar] [CrossRef]
- Liu, Z.; Yang, L.-L. Sparse or Dense: A Comparative Study of Code-Domain NOMA Systems. IEEE Trans. Wirel. Commun. 2021, 20, 4768–4780. [Google Scholar] [CrossRef]
- MacKay, D.I.C.; Neal, R.M. Near Shannon limit performance of low density parity check codes. Electron. Lett. 1996, 32, 1645–1646. [Google Scholar]
- Sun, W.-C.; Su, Y.-C.; Ueng, Y.-L.; Yang, C.-H. An LDPC-Coded SCMA Receiver with Multi-User Iterative Detection and Decoding. IEEE Trans. Circuits Syst. Regul. Pap. 2019, 66, 3571–3584. [Google Scholar] [CrossRef]
- Wu, X.; Wang, Y.; Li, C. Low-Complexity CRC Aided Joint Iterative Detection and SCL Decoding Receiver of Polar Coded SCMA System. IEEE Access 2020, 8, 220108–220120. [Google Scholar] [CrossRef]
- Xiang, L.; Liu, Y.; Xu, C.; Maunder, R.G.; Yang, L.-L.; Hanzo, L. Iterative Receiver Design for Polar-Coded SCMA Systems. IEEE Trans. Commun. 2021, 69, 4235–4246. [Google Scholar] [CrossRef]
- Li, D.; Jia, M.; Wang, X.; Guo, Q.; Gu, X. Iterative Multiuser Detection and Decoding for Sparse Code Multiple Access Combined with Spectrally Efficient Frequency Division Multiplexing. IEEE Access 2020, 8, 24887–24895. [Google Scholar] [CrossRef]
- Zhang, C.; Luo, Y.; Chen, Y. A Low-Complexity SCMA Detector Based on Discretization. IEEE Trans. Wirel. Commun. 2018, 17, 2333–2345. [Google Scholar] [CrossRef]
- Kaplan, G.; Shamai, S. Achievable performance over the correlated Rician channel. IEEE Trans. Commun. 1994, 42, 2967–2978. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).