Research on Secure Communication on In-Vehicle Ethernet Based on Post-Quantum Algorithm NTRUEncrypt
Abstract
:1. Introduction
1.1. Related Research
1.2. The Work in This Paper
2. In-Vehicle Secure Communication
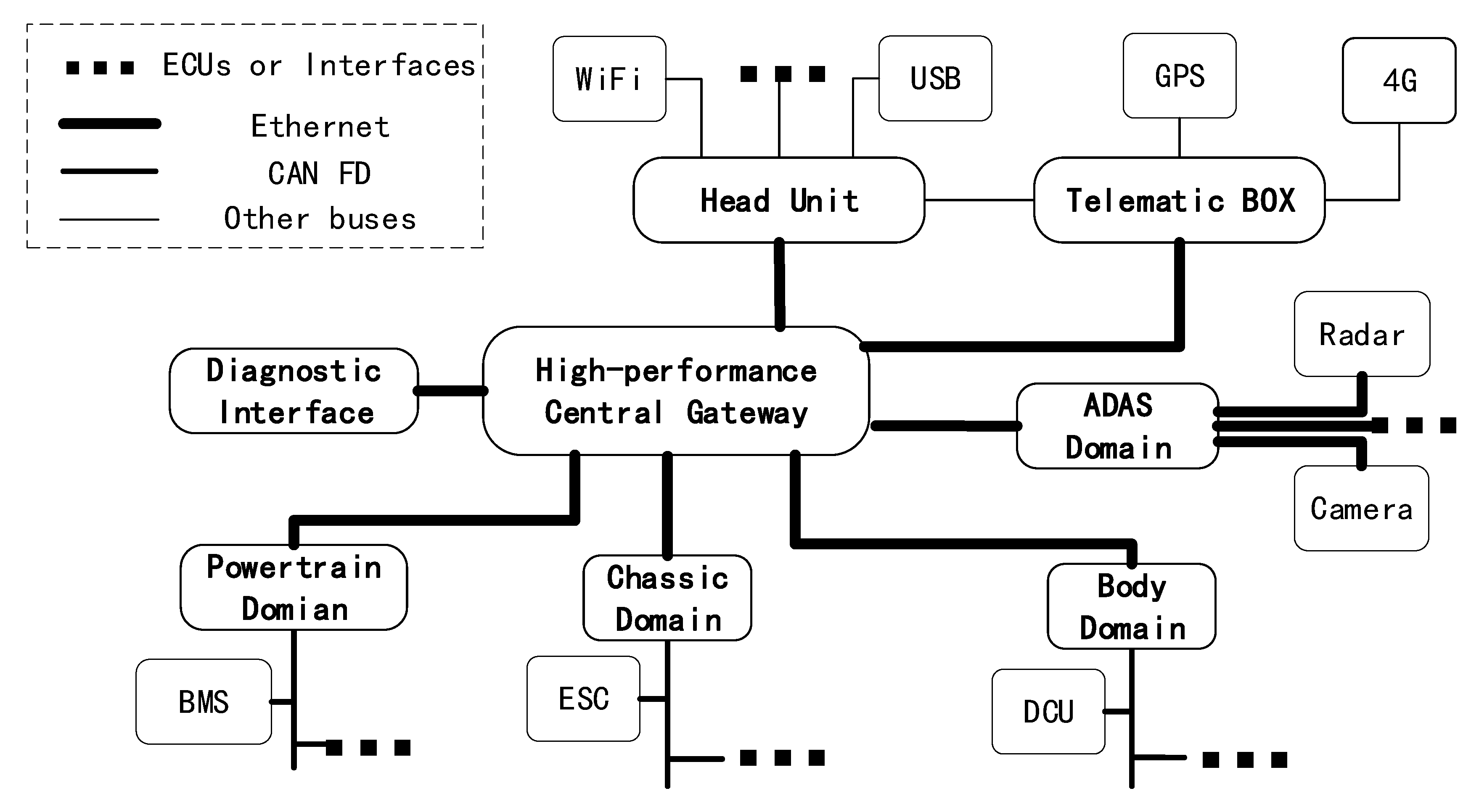
2.1. Research on In-Vehicle Ethernet Communication
2.2. Choosing NTRU Variation Algorithm
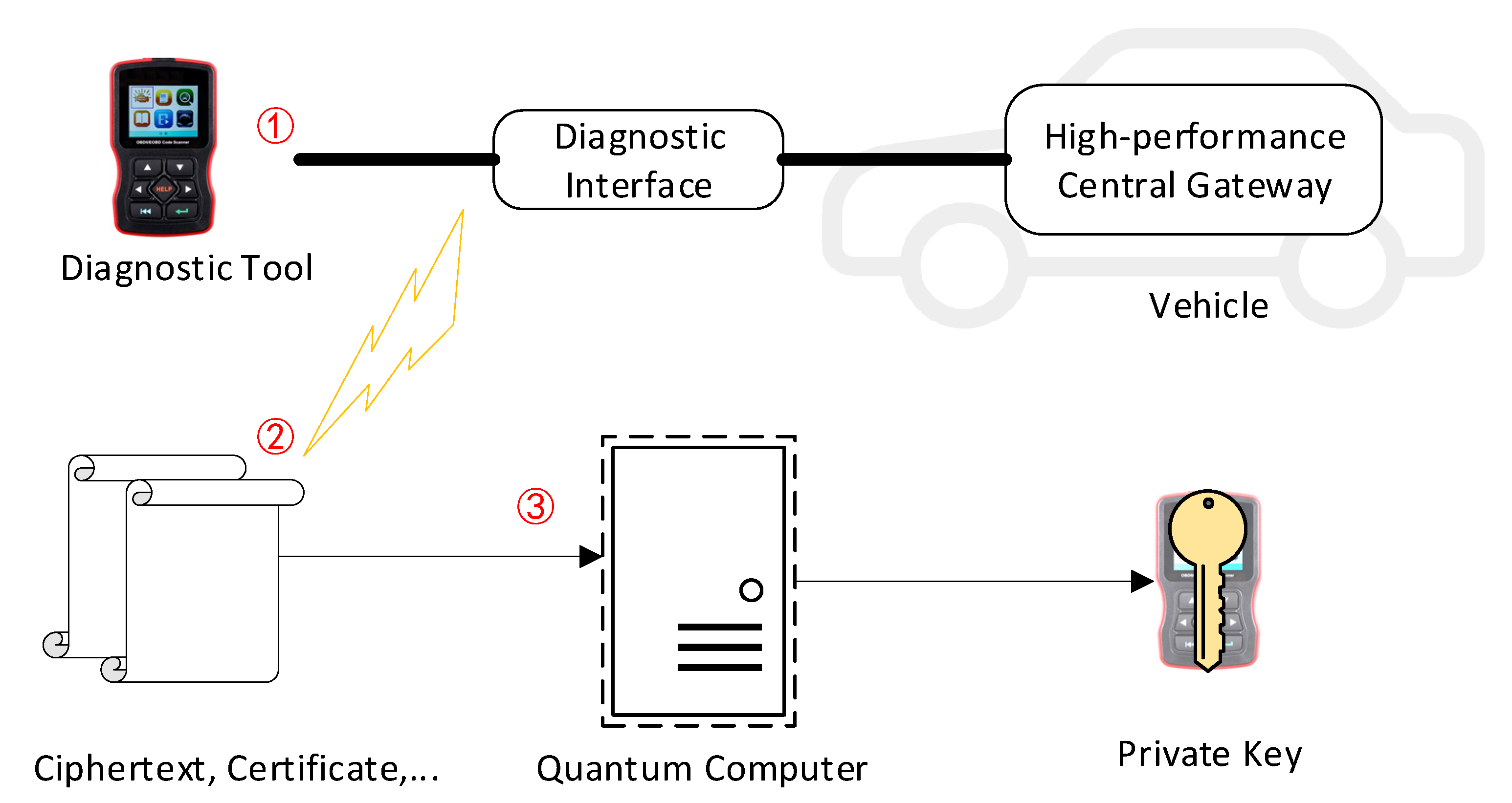
2.3. Use Cases of NTRUEncrypt of In-Vehicle Ethernet Communication
2.4. Function of NTRUEncrypt Algorithm in TLS
3. Mathematical Background of NTRU
3.1. Mathematical Principle
3.1.1. Public Parameters
3.1.2. Key Generation
3.1.3. Encryption
3.1.4. Decryption
3.2. Choosing Parameters of NTRUEncrypt
4. Experiment Process and Analysis
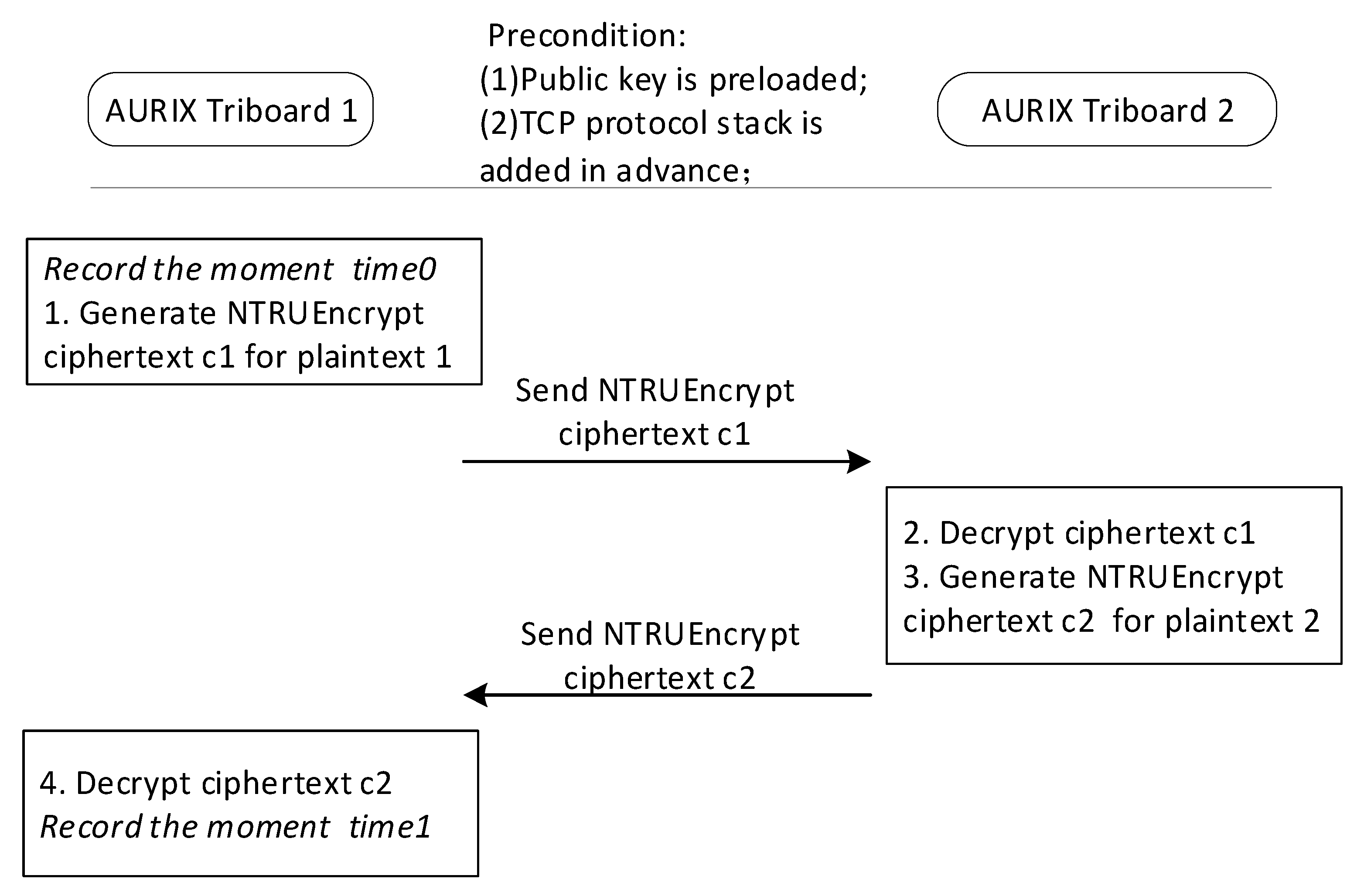
4.1. Experiment Principle
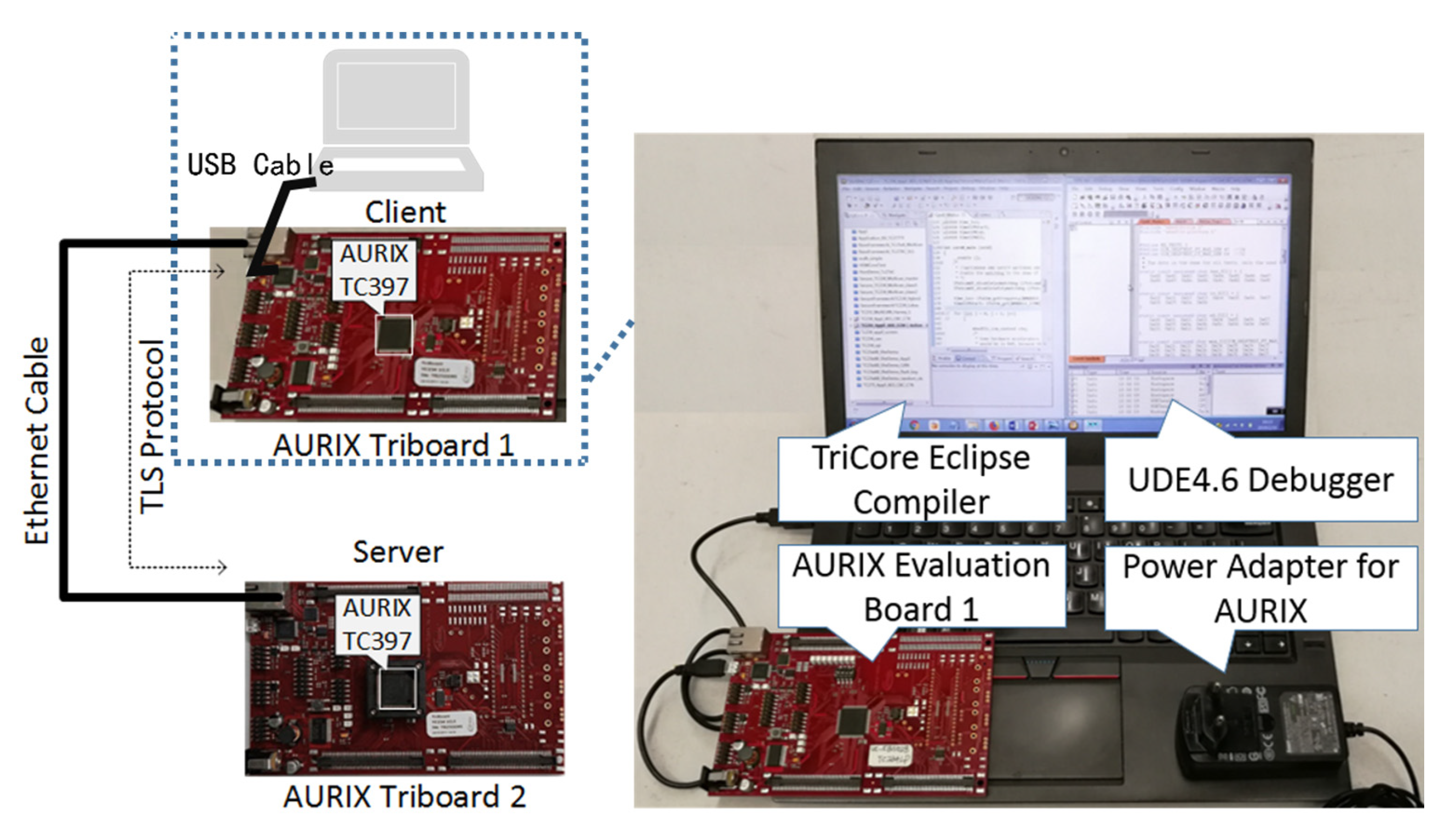
4.2. Experiment Equipment and Settings
4.3. Experiment Results and Analysis
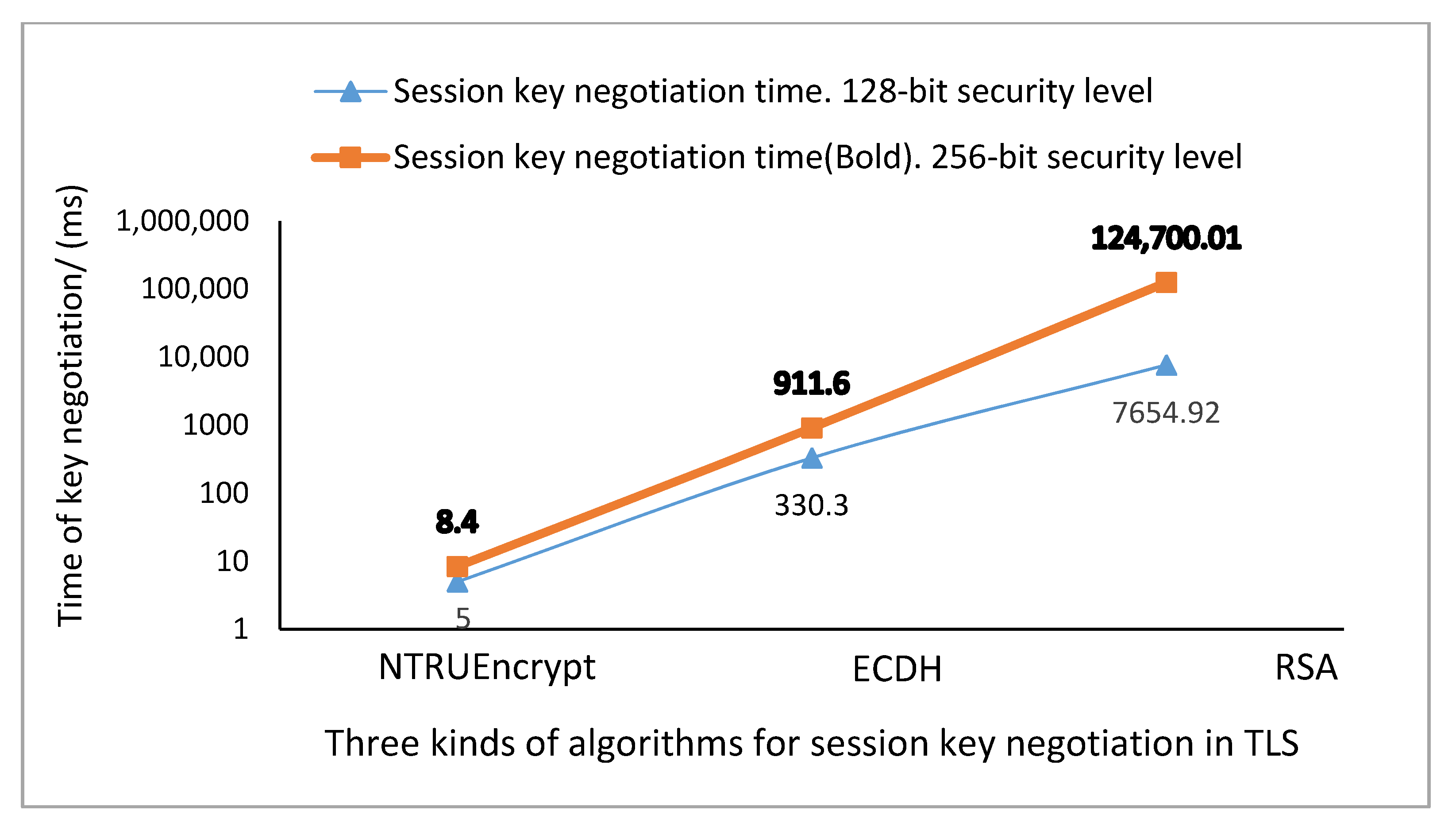
4.3.1. Execution Time of Algorithms
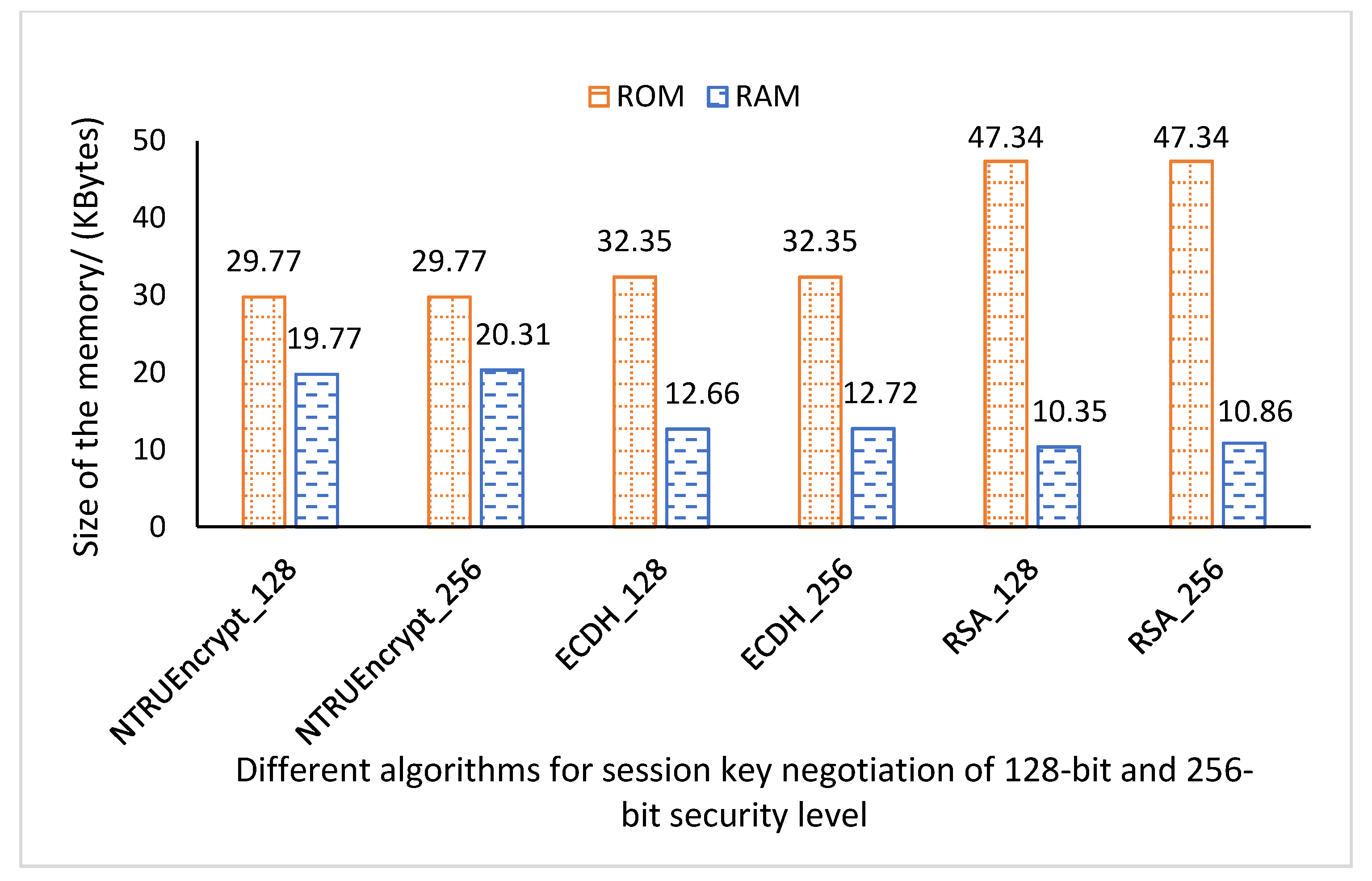
4.3.2. Memory Occupation of Algorithms
5. Conclusions
- NTRUEncrypt based session key negotiation for in-vehicle TLS has a prominent speed advantage over ECDH and RSA. The speed advantage of NTRUEncrypt compared to ECDH and RSA is more prominent when the security level becomes higher. On the 128-bit security level, the speed of the session key negotiation using NTRUEncrypt is 66.06 times faster than ECDH, and 1530.98 times faster than RSA. Meanwhile, on the 256-bit security level, the speed of the session key negotiation using NTRUEncrypt is 108.52 times faster than ECDH, and 14,845.24 times faster than RSA.
- Memory occupation of NTRUEncrypt is at the same order of magnitude compared to that of ECDH and RSA. However, memory occupation is not as crucial an impact factor as the ROM and RAM occupation ratio for a single algorithm is no more than 0.30% and 0.29% of TC397′s ROM and RAM.
- As TLS can fulfill most performance requirements of the automotive industry, considering the above two conclusions, post-quantum enhanced session key negotiation will probably be widely used for in-vehicle Ethernet communication.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ECDH | Elliptic Curve Diffie–Hellman |
| RSA | Rivest–Shamir–Adleman |
| TLS | Transport Layer Security |
| ECC | Elliptic Curve Cryptography |
| LB-PKC | Lattice-Based Public-Key Cryptographic algorithms |
| NTRU | Number Theory Research Unit |
| WSN | Wireless Sensor Network |
| EPON | Ethernet Passive Optical Network |
| CAN | Controller Area Network |
| E/E | Electronic and Electrical |
| DTLS | Datagram Transport Layer Security |
| ECU | Electronic Control Unit |
| MPU | Micro Processor Unit |
| SVP | Shortest Vector Problem |
| gcd | Greatest Common Divisor |
| ROM | Read-only Memory |
| RAM | Random Access Memory |
| LwIP | lightweight IP |
| DoIP | Diagnostic over IP |
| SOME/IP | Scalable Service-Oriented MiddlewarE over IP |
Appendix A. Polynomial Ring
Appendix B. Ternary Polynomial
Appendix C. Operations on R and Rp or Rq
Appendix D. The Inverse of a Polynomial
References
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the IEEE 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Zhang, Z.; Chen, C.; Hoffstein, J.; Whyte, W.; Schanck, J.M.; Hulsing, A.; Rijneveld, J.; Schwabe, P.; Danba, O. NTRUEncrypt. Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019. Available online: https://csrc.nist.gov/projects/post-quantum-cryptography/round-2-submissions (accessed on 22 June 2021).
- Hoffstein, J.; Pipher, J.; Silverman, J.H. NTRU: A ring-based public key cryptosystem. In International Algorithmic Number Theory Symposium; Springer: Berlin/Heidelberg, Germany, 1998; pp. 267–288. [Google Scholar]
- Chaudhary, R.; Aujla, G.S.; Kumar, N.; Zeadally, S. Lattice-based public key cryptosystem for internet of things environment: Challenges and solutions. IEEE Internet Things J. 2018, 6, 4897–4909. [Google Scholar] [CrossRef]
- Dierks, T.; Rescorla, E. The Transport Layer Security (TLS) Protocol, Version 1.2; RFC 5246: Cincinnati, OH, USA, 2008; pp. 1–104. [Google Scholar]
- Nguyen, H.B. An Overview of the NTRU Cryptographic System; San Diego State University: San Diego, CA, USA, 2014. [Google Scholar]
- Yin, A.; Chen, D.; Ding, Y. An efficient and secure authentication scheme based on NTRU for 10G ethernet passive optical. Optik 2014, 125, 7207–7210. [Google Scholar] [CrossRef]
- Shaheen, S.H.; Yousaf, M.; Jalil, M. A smart card oriented secure electronic voting machine built on NTRU. Int. Arab J. Inf. Technol. 2020, 17, 386–393. [Google Scholar] [CrossRef]
- Sepúlveda, J.; Liu, S.; Mera, J.M.B. Post-quantum enabled cyber physical systems. IEEE Embed. Syst. Lett. 2019, 11, 106–110. [Google Scholar] [CrossRef]
- Bi, B.; Huang, D.; Mi, B.; Deng, Z.; Pan, H.J.W.P.C. Efficient LBS Security-Preserving Based on NTRU Oblivious Transfer. Wirel. Pers. Commun. 2019, 108, 2663–2674. [Google Scholar] [CrossRef]
- Mi, B.; Huang, D.; Wan, S. NTRU implementation of efficient privacy-preserving location-based querying in VANET. Wirel. Commun. Mob. Comput. 2018, 2018, 7823979. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.-W.; Sangiovanni-Vincentelli, A. Cyber-Security for the Controller Area Network (CAN) Communication Protocol. In Proceedings of the 2012 International Conference on Cyber Security, Alexandria, VA, USA, 14–16 December 2012; pp. 1–7. [Google Scholar]
- Woo, S.; Jo, H.J.; Kim, I.S.; Lee, D.H. A Practical Security Architecture for In-Vehicle CAN-FD. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2248–2261. [Google Scholar] [CrossRef]
- Zelle, D.; Krauß, C.; Strauß, H.; Schmidt, K. On Using TLS to Secure In-Vehicle Networks. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Association for Computing Machinery, Reggio, Calabria, Italy, 29 August–2 September 2017; pp. 1–10. [Google Scholar]
- PQC-Forum. Available online: https://groups.google.com/a/list.nist.gov/g/pqc-forum/c/Mb5ZKpnO57I/m/S8yaURFYCwAJ (accessed on 20 February 2022).
- Prest, T.; Fouque, P.-A.; Hoffstein, J.; Kirchner, P.; Lyubashevsky, V.; Pornin, T.; Ricosset, T.; Seiler, G.; Whyte, W.; Zhang, Z. FALCON. Post-Quantum Cryptography Project of NIST; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2017.
- Hoffstein, J.; Silverman, J. Optimizations for NTRU. Public-Key Cryptography and Computational Number Theory. In Proceedings of the De Gruyter Proceedings in Mathematics, Vienna, Austria, 18 June–13 July 2001; pp. 77–88. [Google Scholar]
- IEEE P1363.1 Draft 10: Draft Standard for Public Key Cryptographic Techniques Based on Hard Problems over Lattices. Available online: https://eprint.iacr.org/eprint-bin/print.pl (accessed on 22 June 2021).
- Hoffstein, J.; Pipher, J.; Schanck, J.M.; Silverman, J.H.; Whyte, W.; Zhang, Z. Choosing parameters for NTRUEncrypt. In Cryptographers’ Track at the RSA Conference; Springer: Berlin/Heidelberg, Germany, 2017; pp. 3–18. [Google Scholar]
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- AURIX Family TC39X. Available online: https://www.infineon.com/cms/en/product/microcontroller/32-bit-tricore-microcontroller/32-bit-tricore-aurix-tc3xx/aurix-family-tc39xxx/ (accessed on 15 November 2020).
- AURIX Triboard. Available online: https://www.infineon.com/cms/en/product/evaluation-boards/kit_a2g_tc375_5v_trb/ (accessed on 16 November 2020).
- The NTRU Project. Available online: http://tbuktu.github.io/ntru/ (accessed on 25 May 2020).
- Lim, H.-T.; Weckemann, K.; Herrscher, D. Performance study of an in-car switched ethernet network without prioritization. In International Workshop on Communication Technologies for Vehicles; Springer: Berlin/Heidelberg, Germany, 2011; pp. 165–175. [Google Scholar]

| Security Demands | Commonly Used Basic Cryptographic Algorithms |
|---|---|
| Confidentiality | Symmetric Cryptography, Public Key Cryptography |
| Integrity | Hash Algorithm |
| Availability | Hash Algorithm, Public Key Cryptography |
| Authenticity | Public Key Cryptography |
| Non-repudiation | Public Key Cryptography |
| Variations of NTRU Algorithm | NIST Level | Security Level | Public Key/(Bit) | CPU Cycles in Key Generation | CPU Cycles in Key Encapsulation/Decapsulation |
|---|---|---|---|---|---|
| NTRUEncrypt-443 | 1 | 128-bit | 611 | 4,818,993 | 788,041/1,111,005 |
| NTRUEncrypt-743 | 1–5 | 128-bit– 512-bit | 1023 | 12,947,474 | 1,607,275/2,661,836 |
| NTRU HRSS | 1 | 128-bit | 1138 | 112,743,476 | 3,614,922/10,691,695 |
| Algorithms Derived from NTRU | NIST Level | Public Key/(Bit) | CPU Cycles in Verification for the Signature or Key Encapsulation/Decapsulation |
|---|---|---|---|
| Falcon-512 | 1 | 897 | 439,446 |
| Falcon-1024 | 4–5 | 1793 | 882,054 |
| NTRUEncrypt-443 | 1 | 611 | 788,041/1,111,005 |
| NTRUEncrypt-743 | 1–5 | 1023 | 1,607,275/2,661,836 |
| Cryptographic Algorithms for Session Key Negotiation | Security Level | Length of Public Key (Bit) |
|---|---|---|
| NTRUEncrypt EES443EP1 | 128-bit | L(Pk) = 611 |
| RSA 3072 | 128-bit | L(Pk) = 3072 |
| ECDH (ECC256) | 128-bit | L(Pk) = 256 |
| NTRUEncrypt EES743EP1 | 256-bit | L(Pk) = 1023 |
| RSA 15360 | 256-bit | L(Pk) = 15,360 |
| ECDH (ECC521) | 256-bit | L(Pk) = 521 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, Y.; Liu, Y.; Wu, M.; Li, J.; Liu, S.; Zhao, J. Research on Secure Communication on In-Vehicle Ethernet Based on Post-Quantum Algorithm NTRUEncrypt. Electronics 2022, 11, 856. https://doi.org/10.3390/electronics11060856
Zhu Y, Liu Y, Wu M, Li J, Liu S, Zhao J. Research on Secure Communication on In-Vehicle Ethernet Based on Post-Quantum Algorithm NTRUEncrypt. Electronics. 2022; 11(6):856. https://doi.org/10.3390/electronics11060856
Chicago/Turabian StyleZhu, Yuan, Yipeng Liu, Mingzhi Wu, Jinzhao Li, Shiyang Liu, and Jianning Zhao. 2022. "Research on Secure Communication on In-Vehicle Ethernet Based on Post-Quantum Algorithm NTRUEncrypt" Electronics 11, no. 6: 856. https://doi.org/10.3390/electronics11060856
APA StyleZhu, Y., Liu, Y., Wu, M., Li, J., Liu, S., & Zhao, J. (2022). Research on Secure Communication on In-Vehicle Ethernet Based on Post-Quantum Algorithm NTRUEncrypt. Electronics, 11(6), 856. https://doi.org/10.3390/electronics11060856






