Abstract
In this paper, a security framework based on cellular automata is proposed, which is composed of three parts: entity authentication, data encryption, and decryption. Authentication is based on a zero-knowledge protocol, and its robustness is supported by the fact that the shared secret is not only an NP-complete problem but also dynamically transformed by a two-dimensional cellular automaton into a more complex secret. Thus, the authentication’s output is the key to data encryption/decryption in the following steps. One more strength of this system is the sensibility of the cellular automata to initial conditions—which is why we must know the initial configuration in order to obtain the key and the times that cellular automata evolved. All those characteristics give the system both robustness and security.
1. Introduction
Cryptography is an ancient discipline. It is concerned with constructing robust schemes against malicious attempts to make these schemes deviate from their prescribed functionality [1]. For a long time, in order to preserve our information, cryptographic protocols, schemes and mechanisms have been created. Nowadays, it is necessary to prevent the information disclosure and ensure that an unauthorized entity cannot access the transmitted messages. Due to the development of cryptography and cryptanalysis at the same time, there is a need to create robust methods as preventive measures. The protection of data is essential, not only with cryptographic schemes but also with authentication methods. The objective of this paper was to design a security framework based on cellular automata. First, an authentication test was developed based on zero-knowledge interactive proofs using an NP-complete problem as a shared secret due to the naturalness of these problems. Then, these are connected with a stream cipher using a 2-D cellular automaton. These tools were selected due their mathematical and computational properties.
2. Related Work
There are several methods to develop cryptography such as elliptic curves [2,3,4], genetic algorithms [5,6,7], chaotic maps [8,9,10] and cellular automaton. The last mentioned is the method proposed in this paper, which is a subset of dynamic systems that have been effectively and chiefly used to construct strong cryptosystems by taking advantage of not only their randomness but also their dynamical properties [11]. There are some cryptography applications with cellular automata: an evolutionary computation approach was proposed [12] to design a fast and secure block cipher using non-uniform second-order cellular automata. Image encryption techniques aim to protect the image’s content with higher efficiency and security than conventional cryptographic methods using an image’s unique properties. An image encryption model based on two-dimensional partitioned cellular automaton was proposed [13]. This model has the same topology as a digital image and is flexible to images with different color depths.
Image encryption is an efficient and vital way to protect classified and secret images. With the advancement of the computer’s processing power, AES, DES, or chaotic series type, just like image encryption schemes are not as secure as before [14]. For that reason, those authors [14] presented a new hybrid image encryption method for protecting secret and imperative images by employing logistic sine system (LSS) together with two-dimensional cellular automata and finite-state machine-based DNA rule generator, other authors [15] presented an authenticated image encryption algorithm based on cellular automata.
In the same fashion, a novel image encryption scheme was proposed based on permutation–diffusion architecture using cellular automata [16]. Similarly, Xingyuan Wang and Dapeng Luan [17] proposed a novel image encryption scheme based on reversible cellular automaton (RCA) combining chaos. An intertwining logistic map with complex behavior and periodic boundary reversible cellular automata was used in that algorithm.
There was another image encryption algorithm proposed in [18], in which a special kind of periodic boundary cellular automata with unity attractors was used. Furthermore, there are other applications such as a chaotic encryption algorithm based on the “Life-like” cellular automata [19], which act as a pseudo-random generator (PRNG). In [20], a non-uniform cellular automata framework is proposed.
The aim of this work was to design a cellular automata security framework. As the first step, an authentication test was developed based on zero-knowledge interactive proofs, using as a shared secret an NP-complete problem. Then, a stream cipher developed with cellular automata (CA) must be joined to it because both constitute simple formal models for complex and chaotic systems; also, all the cells synchronously update their states by applying a local rule [21,22]. In contrast to some encryption techniques such as DES, AES, RC4 and VEST [23,24], our algorithm offers an authentication service, which must be approved in order to obtain a key and the access to encrypt or decrypt a file.
3. Materials and Methods
This section is devoted to introducing the preliminaries related to information security systems and a discrete model of computation to be discussed in this paper. We explicitly define the basics of cryptography, cellular automaton, complexity, and a well-knowing np-problem called three graph coloring.
3.1. Preliminary
3.1.1. Cellular Automata
One of our model’s parts are cellular automata (CA), which are defined by four characteristics [25]. The first is a discrete cellular state space ℓ which is the discrete lattice of cells or sites upon which CAs “live” and their dynamics unfold; the second element is the local space value , each cell of ℓ indexed by the elements of the ℓ’s symmetry group. Although CAs are assumed to live on infinitely large lattices, computer simulations must necessarily be run on finite sets; for this reason, boundary conditions are important. Finally, there is a dynamical rule ; state transitions are therefore local in both space and time, individual cells evolve iteratively according to a fixed and usually deterministic function of the current state of that cell and its neighboring cells.
3.1.2. Cellular Automata in Cryptography
The use of cellular automata in cryptography is done to best confront the ability of dynamical systems to generate complexity with the cryptanalyst’s tools for cutting through such complexity [26]. Moreover, they are attractive candidates for cryptosystems since they are naturally adapted to massively parallel computation. The approach to using CA in cryptography involves applying both reversible and irreversible rules. Using that tool to build cryptosystems is flexible and powerful; it can be used to solve a wide variety of practical cryptographic problems. These applications motivate the careful investigation of the security properties of such systems.
3.1.3. Some Features of Cryptography
Let A be a finite set, which we will call alphabet, and let m be the message (a text from ) that Alice wants to transmit in secrecy to Bob; it is usually called the plaintext. Alice will first transform the plaintext into , the so-called ciphertext. It will be the ciphertext that she will transmit to Bob. Let A and B be two finite alphabets. Any one-to-one mapping E of to is called a cryptographic transformation [27].
Cryptography itself splits into three main branches: symmetric algorithms, asymmetric algorithms and cryptographic protocols. We will focus on symmetric cryptography, which is divided into block ciphers and stream ciphers.
3.1.4. Perfectly Secret Encryption
We imagine that an adversary who knows the probability distribution over m also knows the likelihood of sending different messages. Subsequently, he observes some ciphertext being sent by one entity to another. Ideally, keeping this ciphertext should not affect the knowledge of the adversary; in other words, the a posteriori likelihood that some message m was sent should be no different from the a priori probability that m would be sent.
3.1.5. Zero-Knowledge Proofs
Zero-knowledge proofs are interactive protocols that enable one entity (called the prover) to convince another entity (called the verifier) of the validity of a mathematical statement without revealing anything beyond the statement’s assertion [28]; that is to say, is a pair of interactive Turing machines, which satisfy two properties—namely completeness and soundness [29].
- Completeness can be expressed as
- Soundness can be expressed for every interactive Turing machine as
In the first place, completeness means that the verifier (V) accepts the proof if the statement is true. In the second place, soundness implies that V rejecting the proof of the fact is false. A cheating prover can convince an honest verifier that some false statement is true with only a very small probability [30].
3.1.6. NP Complexity
The class consists of all sets S: where a verifier exists, there is ordinarily a Turing machine V such that if and only if there exists a string y of polynomial length in the size of x, such that accepts in polynomial time the span of x [31].
3.1.7. Graph Coloring
The graph coloring problem is a NP-hard problem and can be defined as follows: given an undirected graph with being the set of nodes and any edge between and is the set of edges. The graph coloring problem is: to determine a partition of V in a minimum number (the chromatic number) of color classes such that for each edge, , and are not in the same color class [32].
3.2. Cryptography with Cellular Automata and Zero Knowledge Model
This project was divided into two parts, each part refers to different pillars of information assurance, the first one describe the authentication and the second one describing the confidentiality and integrity.
3.2.1. Authentication
For the authentication system, a zero-knowledge interactive proof (ZKIP) is proposed, which has two graphs three-coloring and as a shared secret. This means the graphs are only known by the prover (P) and the verifier (V). Firstly, P generates a commit message indicating that it knows about the shared graphs. Secondly, V returns a challenge; in this case, it asks P for an edge of the chosen graph in a pseudo-random way, and P returns an answer to V. Finally, the process can be repeated several times to ensure verification. Two graphs were used: to make the authentication process difficult for a eavesdropper; so if this entity wants to obtain information, it would need to know both graphs and the way both graphs are colored.
A prover (P) chooses one graph, then changes the value of the vertexes’ color. During a loop, a pseudo-string is created and is processed with the new value of the graph; the result is sent to the verifier (V), who computes the vertexes’ value as well as choose an edge in the graph. If the edge is in the graph, the prove continues—and if the test does not fail in iterations, then it finishes correctly. This algorithm’s output will be a vector, which will be used as a key for the encryption–decryption of files.
P and V have access to the cipher function ; and , where the variables are represented by:
- R—binary vectors set of cardinality 8;
- C—colors set;
- —cipher colors set;
- ⊕—operator XOR;
- —one-dimensional cellular automata defined as a 4-tuple (S,N,f,d);
- S—;
- N—it is considered radius one;
- —rule 30;
- —one dimensional;
- —binary vectors of cardinality 8;
The steps in the Algorithm 1 are executed times where and if , else , the aim is to enable one entity to convince another entity of the validity of the mathematical statement without revealing anything beyond the assertion of the statement.
3.2.2. Encryption/Decryption
In the data encryption and decryption, a matrix has as data the value of the vector obtained in the authentication repeated n-times, one cellular automaton of 2-D, and the file to be encrypted–decrypted. The output of the Algorithms 2 and 3 will be the encrypted–decrypted file, respectively. The headers of the files are encrypted which provokes the loss of the original file.
The output of the authentication process is called , where: and Vector of cardinality 16.
The cipher will be an cellular automaton P, defined as a 4-tuple (S,N,f,d) where:
- ⋄
- S—
- ⋄
- N—Moore neighborhood, it is considered radius one.
- ⋄
- —two dimensional.
- ⋄
- —variant of Conway’s life:
- Any live cell with one, three, five or eight live neighbors survives;
- Any dead cell with three, five or seven live neighbors becomes a live cell;
- All other live cells die in the next generation. Similarly, all other dead cells stay dead.
The frontier states of the cellular automaton P will be toroidal. For the extremes, the neighbors will be taken from the upper, lower or extreme sides, respectively, to shape a neighborhood of the adjacent cells. Moreover, the lattice of this one will be represented as eight times the file’s size to encrypt (D); it is multiplied by eight because a flow cipher will be performed and it is necessary to represent the data in bytes.
| Algorithm 1: Authentication test using interactive zero-knowledge. |
 |
In order to correctly decode the files, it is necessary for both the cellular automaton encoder and decoder to have the same input and the same configuration. This is the key , which is an essential part because this one contains the number of times that the automaton will evolve. Moreover, it contains the data which will be replicated in a matrix; this matrix will be the input of the decoder CA.
4. Results
On top of that, the implementation of the algorithm and different types of analysis were performed using Python 3 on a computer with Intel CORE i5 processor having 4 GB RAM. First of all, we simulated the authentication algorithm and after the encryption/decryption algorithm, the Appendix A shows the app developed. Figure 1 shows us the software design.
| Algorithm 2: Files encoder using cellular automaton. |
 |
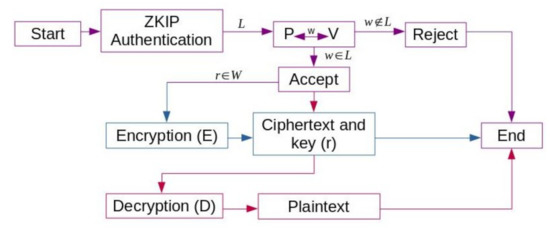
Figure 1.
Block diagram of Algorithms 1–3. It shows the security framework’s flow.
| Algorithm 3: Files decoder using cellular automaton. |
| input: Encrypted file E,. output: Decrypted file D. The key is taken and replicated A times, this matrix will be the lattice of P. P evolves n-times, where n is represented with the first four digits of converted from binary to decimal. A vector V is created and transformation of the output from P to V is performed. E is read as a bits array.  |
In the second place, a general diagram to represent the functional mechanism of the proposed method is presented in Figure 2. Moreover, the diagram is divided into authentication, encryption, and decryption mechanisms. In Figure 3, the ZKIP authentication is shown and it explains how the communication is between the entities. Secondly, Figure 4 represents the block diagram of the encryption part; it is essential that the user approves the first step in order to obtain a key, whereas in the decryption part, the user must have the correct one to obtain the plaintext as shown in Figure 5.
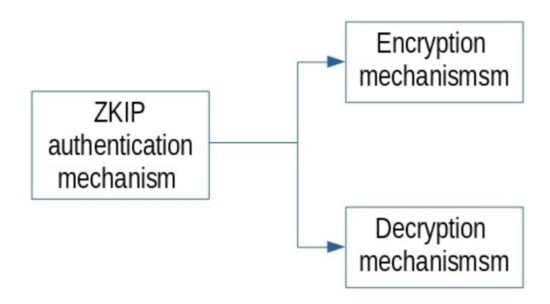
Figure 2.
The functional mechanism of the general proposed method.
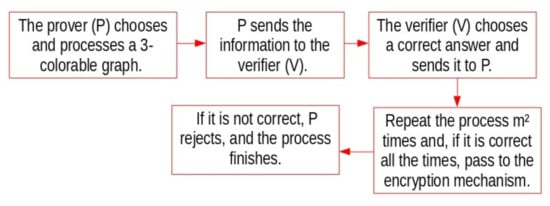
Figure 3.
The functional mechanism of the ZKIP authentication proposed method.
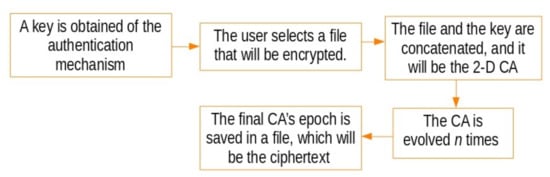
Figure 4.
The functional mechanism of the encryption proposed method.
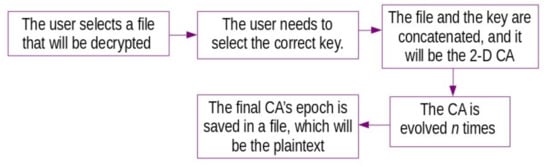
Figure 5.
The functional mechanism of the decryption proposed method.
4.1. Authentication
The ZKP algorithm satisfies three properties.:
- Completeness—if the graph is three colorable, then any pair of edges will undoubtedly be differently colored. Therefore, an honest verifier will complete all iterations and accept with a probability of 1;
- Soundness—if the graph is not three colorable and the verifier follows the protocol, then no matter how the prover plays and at each round, the verifier will reject with a probability of at least ;
- Zero-knowledge—the only information received by the verifier at each round is a pair of randomly selected elements, and the prover only answers cipher colors.
Isomorphic graphs are used when the algorithm does a nodes permutation before encrypting them to display the information at the verifier.
4.2. Encryption and Decryption
This section presents the results for the files of different categories, namely .JPG, .PDF, .MP3, .ZIP, .XLS, and .DOC. Files were chosen at random, comprising various file sizes and file types. Here, we present an analysis of 12 files, varying file sizes from 330 bytes to 8,649,167 bytes. The analysis compares encryption and decryption times, chi-square values, entropy, and avalanche achieved (%). The algorithm works for any file because conversion to byte-map is performed. In the encryption process, the header file is also modified to the cipher file which does not exhibit information about the plain file.
Table 1 shows the file’s size, type, as well as the time of encryption and decryption for each one.

Table 1.
File size, decryption, and encryption time.
The entropy is described as the measurement of the unpredictability of data in the information source. In other words, this means the measurement of randomness in data which is calculated through Equation (1):
where:
- x: discrete random variable;
- P(x): probability density function of x.
A completely random stream would thus have high entropy. For a stream with a highly random distribution of characters, the entropy should be close to 8 [33].
Another commonly used test to check for randomness in a stream of data is the chi-square test which calculates the degree to which two given samples of data differ from each other. The test tells the degree of confidence with which one can reject or accept a hypothesis:
where:
- the frequency of a character in the encrypted file;
- the frequency of a character in a uniform distribution.
The chi-2 test in this paper is used to measure the histogram uniformity. Furthermore, the avalanche effect is measured using a statistical analysis of data. When an input is slightly changed, the output changes drastically. If a bit in the plain text is flipped or changed, then for an evident avalanche effect, almost half of the ciphertext bits are changed in the ciphertext. A good encryption algorithm should always satisfy the following relation:
Table 2 shows the results obtained by using our system and RC4 algorithm. Most of the entropy values are close to 8 and this means that, even if the previous symbols are known, it is still impossible to predict the next character in the sequence. However, the entropy decreases if the number of bytes to be encrypted is small. The avalanche values obtained were greater than 0.5, which indicates that the output has drastic changes when the input is slightly changed. Finally, the execution time is high when there is an extensive input file or a big amount of evolution times of the CA.

Table 2.
Entropy, chi-square value, and avalanche achieved.
Decrypt
As a consequence of encrypting, we obtain a key file and an encrypted file. However, if we want to decrypt, it is necessary to solve the authentication process, and subsequently, with the key and the encrypted file, we can obtain the plain text. In Figure 6, a decrypt diagram is shown.
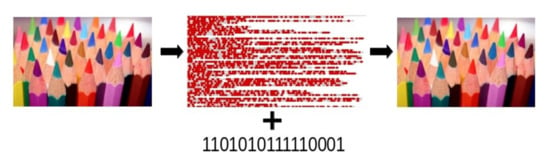
Figure 6.
Decryption diagram which shows the visual flow of the process.
5. Discussion
In this paper, a security system with good cryptographic properties because of the tools used was developed. The amount of computer time it takes to run this algorithm is ; this makes it computationally efficient. It has a high-security level because the authentication problems are NP-complete (in this case, graph 3 coloring); it is, we can verify the solution in polynomial time, while for finding a solution an exponential time is necessary.
All the algorithms are linked; if an eavesdropper wanted to obtain the plain text, they would need to have the ciphertext, the key, and pass the zero-knowledge proof. Moreover, they would need to know the evolution rules and the number of times that the cellular automata evolve; for this reason, the algorithm is better than some stream algorithms [34,35,36].
Some applications for this work can be as a captcha; in another case, it can be used when someone forgets their password and the person needs to prove that whoever is not an impostor. In addition, if we wanted to send a private message, we only cipher the text, and a correct entity could obtain the decrypted text; also, it can be a secure channel for sharing information.
The algorithm works for any file because conversion to byte-map is performed. In the encryption process, the header file is also modified to the cipher file which does not exhibit information about the plain file; should we want to decrypt it, it is also necessary to solve the authentication process, and subsequently, with the key and the encrypted file, we can obtain the plain text.
6. Conclusions
In this paper, a novel framework was presented, in which the key to solving an NP-complete problem is obtained; this provides not only authentication but also confidentiality in security services. Another point is that, as shown in Table 1, the framework encrypts different types of files, unlike in [13,37], but similarly, it works with cellular automata. Moreover, the encryption time depends on the file size; in comparison with, [38] is faster and has better avalanche achieved percentages (Table 2), so it is better because of the efficiency of the diffusion mechanism. In other words, the encryption algorithm possesses good diffusion characteristics. In the future, this concept may be extended to introduce other services such as integrity and non-repudiation to build a complete network security software service that helps provide absolute security for data transmission.
Compared to the RC4 algorithm (Table 2), we obtained better results in avalanche values; i.e., diffusion efficiency is better. The proposed system has better results in chi-square values when the file size is small because the bytes are more uniformly distributed by the CA. The advantage of this framework is that the user must authenticate with a secret, and the key is dynamically created for all files. If someone obtains the key of a previous cipher file, they will only be able to decrypt the file if they pass the authentication test, and the key will only work for that file. Entities that want to encrypt/decrypt similar files must know the secret in order to be authenticated. In the case that multiple entities are required to be present to perform the encryption process, the secret can be shared; each user has a part necessary to do this.
Author Contributions
Conceptualization, E.C.-B.; methodology, G.T.-C.; software, E.C.-B.; validation, J.C.C.-E. and G.T.-C.; formal analysis, J.C.C.-E. and G.T.-C.; investigation, E.C.-B.; writing—original draft preparation, E.C.-B.; writing—review and editing, G.T.-C. and J.C.C.-E. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
We gratefully thank CONACyT for financial support, and we also thank the simulation and modeling laboratory for providing the equipment and knowledge for developing this research.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
This section shows the steps with the images of the algorithms developed into an app.
First of all, the instructions are given to the user at the beginning. The user can perform the authentication process or exit. This step is shown in Figure A1.
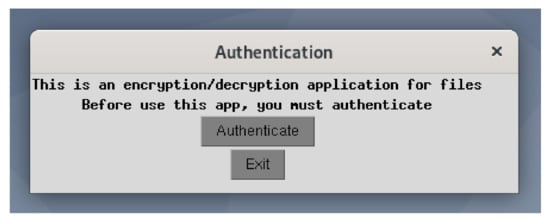
Figure A1.
Starting application.
After the authentication process begins, the encrypted values of the vertex are shown to the user. The user must give an existing edge of the graph as an answer. If the edge is not in the graph, the system rejects the process and it finishes as shown in Figure A2.
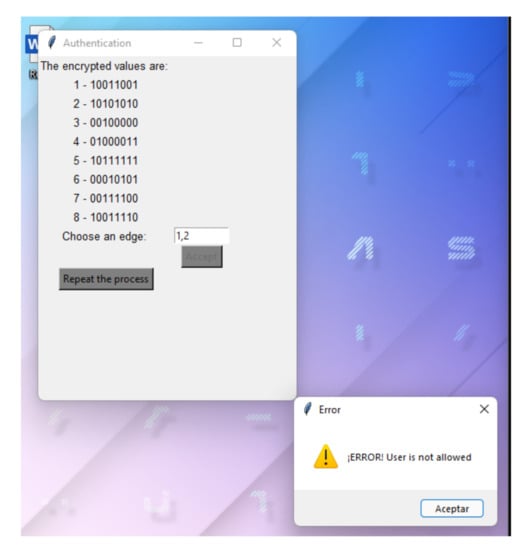
Figure A2.
Incorrect authentication.
If the user’s answer is correct (the edge is in the graph), the vector values which were encrypted in the vertex are shown and the user must decide whether the values are correct or not. This step is implemented in order to verify whether somebody has modified the app to obtain some information from the user. It is shown in Figure A3.
Figure A4 shows the next step: if the test is approved, the encryption/decryption process continues. The user selects the file and the action to perform. To decrypt, the user needs to give the key to the process; otherwise, the key is obtained from the authentication process.
Finally, the encrypted or decrypted file is obtained and the user selects the directory to save it. Some samples are obtained and saved, and the result is shown in Figure A5 and Figure A6.
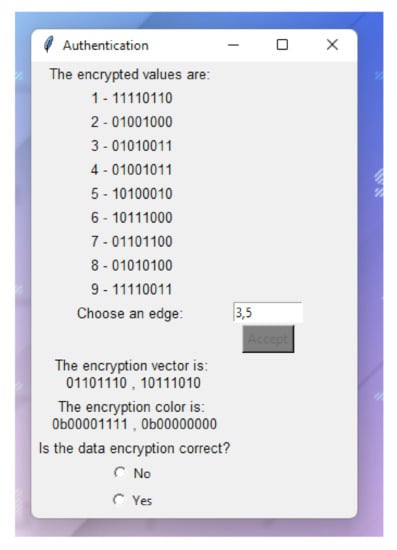
Figure A3.
Authentication process.
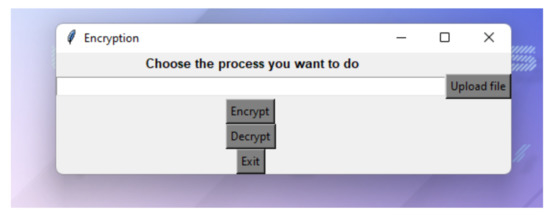
Figure A4.
Encryption/decryption process.

Figure A5.
Results obtained during the encryption process of the .mp3 file.

Figure A6.
Results obtained during the encryption process of the .jpg file.
References
- Goldreich, O. Modern Cryptography, Probabilistic Proofs and Pseudorandomness; Springer Science & Business Media: New York, NY, USA, 1998; pp. 154–196. [Google Scholar]
- Miller, V.S. Use of Elliptic Curves in Cryptography; Conference on the theory and application of cryptographic techniques, Springer: Berlin/Heidelberg, Germany, 1985; pp. 154–196. [Google Scholar]
- Hankerson, D.; Menezes, A.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Jurišic, A.; Menezes, A. Elliptic curves and cryptography. Dr. Dobb’s J. 1997, 265, 26–36. [Google Scholar]
- Delman, B. Genetic Algorithms in Cryptography; RIT’s Digital Media Library: Rochester, NY, USA, 2004. [Google Scholar]
- Khan, F.; Bhatia, S. A novel approach to genetic algorithm based cryptography. Int. J. Res. Comput. Sci. 2012, 2, 7–10. [Google Scholar] [CrossRef][Green Version]
- Mishra, S.; Bali, S. Public key cryptography using genetic algorithm. Int. J. Recent Technol. Eng. 2013, 2, 150–154. [Google Scholar]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Cryptography using multiple one-dimensional chaotic maps. Commun. Nonlinear Sci. Numer. Simul. 2005, 10, 715–723. [Google Scholar] [CrossRef]
- Pisarchik, A.; Zanin, M. Chaotic map cryptography and security. Encryption Methods Softw. Secur. 2010, 19, 1–28. [Google Scholar]
- Mazloom, S.; Eftekhari-Moghadam, A. Color image encryption based on coupled nonlinear chaotic map. Chaos Solitons Fractals 2009, 42, 1745–1754. [Google Scholar] [CrossRef]
- Hamed, Y.; Ali, N. Enhanced RC5 Key Schedule Using One-Dimensional Cellular Automata for Audio File Encryption. Iraqi J. Sci. 2019, 60, 388–401. [Google Scholar]
- Kamel, M. A genetic strategy to design cellular automata based block ciphers. Expert Syst. Appl. 2014, 17, 7958–7967. [Google Scholar]
- Yong, W.; Yi, Z.; Qing, Z.; Zehui, L. Image encryption using partitioned cellular automata. Neurocomputing 2018, 275, 1318–1332. [Google Scholar]
- Khan, S.; Han, L.; Lu, H.; Butt, K.; Bachira, G.; Khan, N. A New Hybrid Image Encryption Algorithm Based on 2D-CA, FSM-DNA Rule Generator, and FSBI. IEEE Access 2019, 7, 81333–81350. [Google Scholar] [CrossRef]
- Eslami, Z.; Kabirirad, S. A Block-Based Image Encryption Scheme Using Cellular Automata with Authentication Capability; AIP Conference Proceedings; AIP Publishing LLC: Melville, NY, USA, 2019. [Google Scholar]
- Jeyaram, B.; Radha, R.; Raghavan, R. New cellular automata-based image cryptosystem and a novel non-parametric pixel randomness test: New cellular automata-based image cryptosystem and a novel non-parametric pixel randomness test. Secur. Commun. Netw. 2016, 9, 3365–3377. [Google Scholar] [CrossRef]
- Xingyuan, W.; Dapeng, L. A novel image encryption algorithm using chaos and reversible cellular automata. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 3075–3085. [Google Scholar]
- Abdo, A.; Shiguo, L.; Ismail, I.A.; Amin, M.; Diab, H. A cryptosystem based on elementary cellular automata. Commun. Nonlinear Sci. Numer. Simul. 2013, 18, 136–147. [Google Scholar] [CrossRef]
- Jeaneth, M.; Anderson, G.; Odemir, B. Chaotic encryption method based on life-like cellular automata. Expert Syst. Appl. 2012, 39, 12626–12635. [Google Scholar]
- Abolfazl, Y.; Mohammad, H.; Masood, N. Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt. Lasers Eng. 2017, 90, 225–237. [Google Scholar]
- Ulam, S. Random Processes and Transformations. Proc. Int. Congr. Math. 1952, 2, 264–275. [Google Scholar]
- Von Neumann, J. Theory of Self-Reproducing Automata; University of Illinois Press: Champaign, IL, USA, 1966. [Google Scholar]
- Thambiraja, E.; Ramesh, G.; Umarani, D.R. A survey on various most common encryption techniques. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2012, 2, 226–233. [Google Scholar]
- Agrawal, M.; Mishra, P. A comparative survey on symmetric key encryption techniques. Int. J. Comput. Sci. Eng. 2012, 5, 877. [Google Scholar]
- Ilachinski, A. Cellular Automata a Discrete Universe, 1st ed.; World Scientific: New York, NY, USA, 2001. [Google Scholar]
- Gutowitz, H. Cryptography with Dynamical Systems. In Laboratoire d’Electronique; Springer: Dordrecht, The Netherlands, 1996. [Google Scholar]
- Henk, C.A. Fundamentals of Cryptology, 1st ed.; Kluwer Academic Publishers: New York, NY, USA, 2002; pp. 2–25. [Google Scholar]
- Pass, R. Alternative Variants of Zero-Knowledge Proofs. Ph.D. Thesis, Universitets Service US AB, Stockholm, Sweden, 2004. Available online: https://www.diva-portal.org/smash/get/diva2:9472/FULLTEXT01.pdf (accessed on 20 December 2021).
- Feng, L.; McMillin, B. A Survey on Zero-Knowledge Proofs. Adv. Comput. 2014, 94, 25–69. [Google Scholar]
- Goldreich, O. Zero-Knowledge twenty years after its invention. IACR Cryptol. ePrint Arch. 2002, 2002, 186. [Google Scholar]
- Steven, R.; Avi, W. Computational Complexity Theory; American Mathematical Society: Providence, RI, USA, 2004. [Google Scholar]
- Dorne, R.; Hao, J. A new genetic local search algorithm for graph coloring. In International Conference on Parallel Problem Solving from Nature; Springer: New York, NY, USA, 1998; p. 754. [Google Scholar]
- Malhotra, P. Detection of Encrypted Streams for Egress Monitoring; Iowa State University: Ames, IA, USA, 2007. [Google Scholar]
- Klein, A. Attacks on the RC4 stream cipher. Des. Codes Cryptogr. 2008, 48, 142–149. [Google Scholar] [CrossRef][Green Version]
- Akhyar, F.; Nasution, S.; Surya, M.; Purboyo, T. Rabbit algorithm for video on demand. In Proceedings of the 2015 IEEE Asia Pacific Conference on Wireless and Mobile (APWiMob), Bandung, Indonesia, 27–29 August 2015; pp. 208–213. [Google Scholar]
- De Canniere, C.; Preneel, B. New Stream Cipher Designs; Springer: Berlin, Germany, 2008; pp. 244–266. [Google Scholar]
- Contreras, J.; Ramírez, M.; Aboytes, M. Image Encryption System Based on Cellular Automata and S-Box. Res. Comput. Sci. 2019, 10, 153–161. [Google Scholar] [CrossRef]
- Manna, S.; Dutta, S. A Stream Cipher based Bit-Level Symmetric Key Cryptographic Technique using Chen Prime Number. Int. J. Comput. Appl. 2014, 12, 975–8887. [Google Scholar] [CrossRef][Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).