A Survey on Citizens Broadband Radio Service (CBRS)
Abstract
1. Introduction
- We provide a complete overview of the CBRS architecture describing the entities and their functionalities and highlighting different CBRS stakeholders and the regulation and standardization process in CBRS.
- An in-depth discussion of several schemes proposed in the literature for spectrum sharing and resource allocation in CBRS is provided.
- We provide a comprehensive discussion of the contributions and weaknesses of the schemes proposed in the literature for preserving the privacy of incumbents, PAL devices, and GAA devices in CBRS.
- The open issues requiring further research are presented.
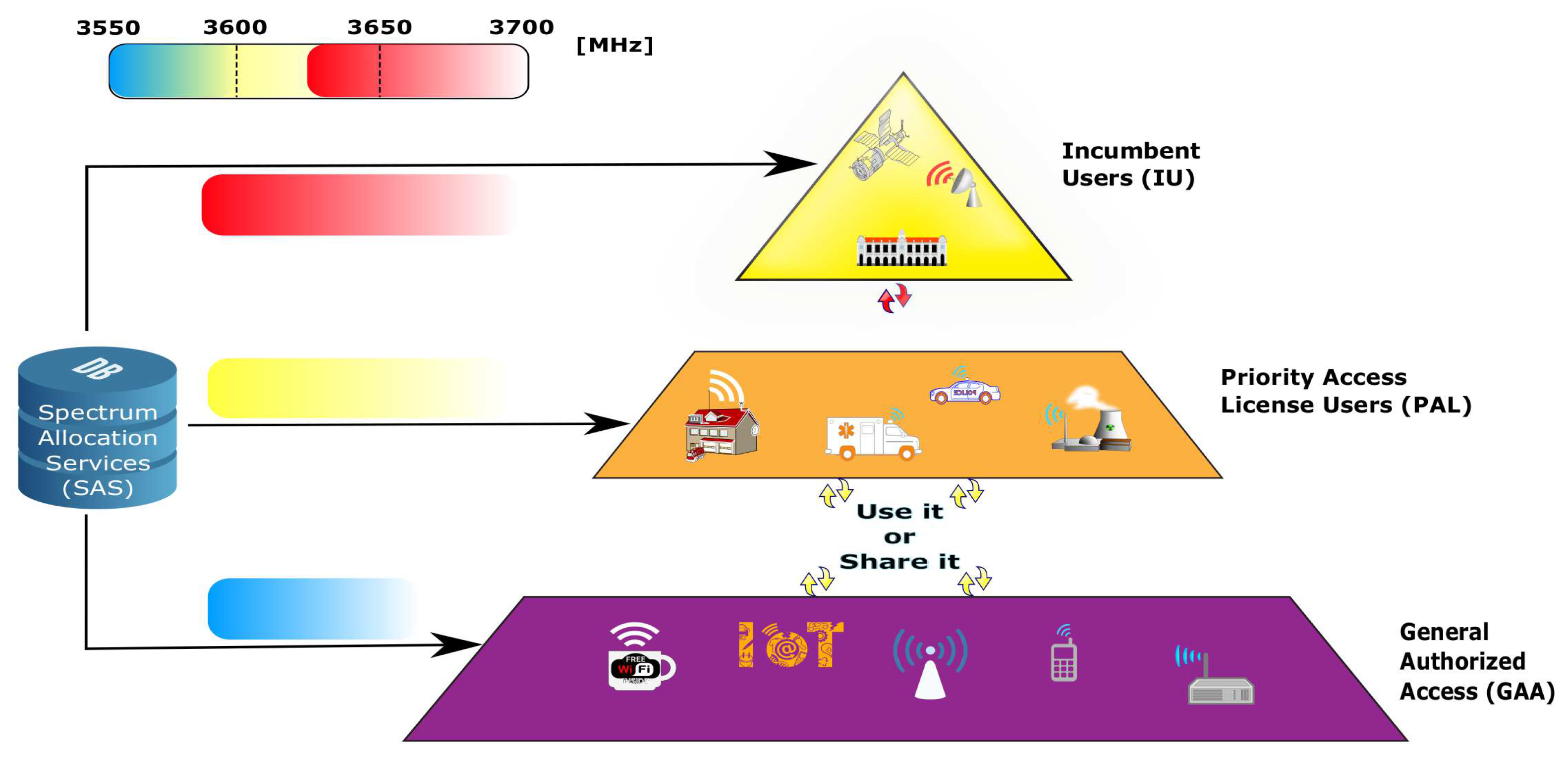
2. CBRS—An Overview
2.1. Three-Tier Hierarchical Architecture
- Each license is valid for a period of ten years;
- Each license is valid for only a single license area consisting of a county, where counties are defined based on the data of the United States Census Bureau;
- Each license authorizes the licensee to transmit on a 10 MHz channel in a license area;
- A licensee can aggregate up to four licenses in the service area consisting of its multiple contiguous license areas;
- More than 7 licenses cannot be given in any license area at any given time [13].
2.2. Regulations for Frequency Assignment
- The PAL CBSDs can only operate within the former 100 MHz spectrum, i.e., 3550–3650 MHz.
- The minimum bandwidth of the channel that can be allocated to the priority access licensee is 10 MHz.
- A priority access licensee can aggregate up to 4 licenses in a license area at any given time, which implies the PAL CBSDs under a licensee can operate on a maximum bandwidth of 40 MHz.
- The total number of channels assigned for the operations of the PAL CBSDs cannot exceed 7, as the total number of licenses in a license area is limited to 7. This implies that the PAL CBSDs cannot access more than 70 MHz of the spectrum at any given time.
- Geographic Contiguity: If a priority access licensee holds multiple licenses belonging to contiguous license areas, it should be assigned the same channels in each license area, to the extent feasible.
- Channel Contiguity: If a priority access licensee holds multiple licenses all belonging to a license area, it should be assigned multiple contiguous channels, to the extent feasible.
2.3. SAS
- Registering the CBSDs, authenticating their location and identity, and authorizing them for spectrum access;
- Communicating with the ESC sensors regarding the activity of the incumbents and enforcing the exclusion/ protection zones to protect the incumbents from any harmful interference from the PAL and GAA CBSDs;
- Confirming the relocation or suspension of the CBSDs from a channel within 300 s once the activity of incumbents are detected on the channel;
- Allocating the channels to the PAL and GAA CBSDs while protecting the PAL CBSDs against any harmful interference from other PAL CBSDs and GAA CBSDs;
- Determining the maximum transmission power of the CBSDs at their location;
- Responding to the queries of the PAL and GAA CBSDs regarding the availability of the spectrum.
- SAS Discovery Procedure: Each SAS administrator provides a URL to the registered CBSDs. The registered CBSDs can use the list of URLs to connect to a server. The SAS and CBSDs mutually authenticate each other using the transport layer security protocol.
- CBSD Registration Procedure: A CBSD in the Unregistered state can send the registration request to the SAS after the mutual authentication procedure is completed successfully. The registration request message contains the identity, location, equipment capabilities, and measurement reporting capabilities of the CBSD. The SAS can either accept or reject the registration request. The CBSD transits to the Registered state once the SAS accepts the registration request. However, the CBSD remains in the Unregistered state if the SAS rejects the registration request. Figure 3 presents the registration state diagram of the CBSD.
- CBSD Spectrum Enquiry Procedure: A registered CBSD can send the spectrum enquiry request to the SAS to determine the availability of the spectrum. The CBSD can specify one or more channels it plans to use and determine their availability. The SAS can respond with the list of available channels. The CBSD can use this procedure to determine the operational parameters, such as channel, transmission power, etc., that it can use for transmission.
- CBSD Grant Procedure: A CBSD can start the grant procedure once it has successfully completed the registration procedure. Here, a grant can be seen as a contract between the SAS and CBSD through which the SAS authorizes a CBSD to transmit on the band only using the operational parameters specified in the grant. A CBSD in the Idle state can send a grant request to the SAS, which contains the operational parameters it plans to use for transmission. The SAS can accept the grant request if the operational parameters mentioned in the grant do not create any interference and reject the request otherwise. The CBSD transits to the Granted state if the SAS accepts the request and sends the grant expiry time and heartbeat interval time. The CBSD remains in the Idle state if the grant request is rejected. The CBSD in the Granted state cannot transmit on the band until it successfully completes the heartbeat procedure and moves to the Authorized state. Figure 4 presents the grant state diagram of the CBSD.
- CBSD Heartbeat Procedure: The CBSD sends the first heartbeat request after it has successfully completed the grant procedure and entered into the Granted state. The CBSD can transmit on the band using the operational parameters specified in the approved grant only after the SAS accepts its heartbeat request. The heartbeat interval, grant expiry timer, and transmit expiry timer are specified in the heartbeat response message by the SAS. The CBSD has to send heartbeat requests after the heartbeat interval timer elapses. The CBSD has to stop its transmissions within 60 s once the transmit expiry timer has elapsed. The SAS uses the heartbeat procedure to interact with CBSDs and dynamically control their transmissions on the band with respect to the activity of the incumbents by renewing, suspending, and terminating the associated grants.
- CBSD Grant Relinquishment Procedure: The CBSD can send the relinquishment request to the SAS for terminating any existing grant. The SAS can accept the request and terminate the grant. The CBSD is then not authorized to transmit on the band using the operational parameters specified in the terminated grant.
- CBSD Deregistration Procedure: The CBSD uses this procedure to de-register itself from the SAS. The SAS deletes all the grants associated with the CBSD. The CBSD enters into the Unregistered state, as shown in the Figure 3.
2.4. ESC
3. Spectrum Sharing (Resource Allocation)
3.1. Power
3.2. Delay Time
3.3. Bandwidth
3.4. Distance
3.5. Traffic
3.6. User
4. Privacy
- Obfuscation-based schemes relying on the addition of the noise or dummy information to create ambiguity in the estimation of the adversary, and
- Cryptography-based schemes employing the cryptographic tools to limit the adversary’s access to the incumbents’ private details.
4.1. Obfuscation-Based Schemes
- Add random non-positive noise to the transmit power to be allocated to the CBSDs;
- Change the shape of their protection contours;
- Enlarge the protection contours by combining the protection contours of other incumbents.
- A random adversary querying from multiple locations selected randomly;
- A strategic adversary querying from multiple locations selected optimally by minimizing the performance metric.
- Have access to the information exchange between the incumbents and SAS either by hacking the SAS or by eavesdropping on the link between SAS and incumbents;
- Have access to the communication between the SAS and all CBSDs;
- Have access to the allocations made to a subset of CBSDs in the network.
- Insertion of false entries of incumbents into the database;
- Perturbation of resources to be allocated to the CBSDs;
- Addition of uncertainty to the adversary’s a priori distribution by making the incumbents’ behavior more dynamic.
- The ESC sensors obtain the parameters by performing the local machine learning models;
- The ESC sensors then aggregate the parameters using the compressed sensing and transmit the aggregated signals to the SAS;
- The SAS then optimizes the global parameters and transmits them to the ESC sensors;
- The ESC sensors perform incumbent detection using the global detection method and report the decision to the SAS.
- The SAS selects a channel randomly from the set of idle channels available;
- The SAS orders the channel and selects the lowest available idle channel.
- The adversary compromises the CBSDs and observes the assignments made to the CBSDs by the SAS;
- The adversary hacks the SAS and eavesdrops on the communications between the SAS, ESC, and incumbents.
- The inherent noise in the readings of the ESC sensors;
- The false entries of incumbents injected by the military forces;
- The perturbation in the resources allocated by the SAS to the CBSDs.
4.2. Cryptography-Based Schemes
- FCC, which is responsible for generating system keys, authorizing the CBSDs, and ensuring compliance with the regulations;
- Multiple synchronized databases containing smart contracts in each record, which defines the rules of channel usage;
- Multiple CBSDs, which query the SAS for channel allocation.
5. Regulation and Standardization
- 2010 [101]: The Presidential Memorandum of June 2010 titled “Unleashing the Wireless Broadband Revolution” calls for the National Telecommunications and Information Administration (NTIA), in collaboration with the Federal Communications Commission (FCC), to re-purpose 500 MHz of spectrum from existing Federal and non-Federal uses to wireless broadband use within ten years. The idea was to improve America’s economic competitiveness, create jobs, and help maintain America’s leadership role in technological innovation. In this context, the US President’s Council of Advisors on Science and Technology also released a report titled “Realizing the Full Potential of government-held Spectrum to Spur Economic Growth” on spectrum sharing.
- 2012 [102]: The US President directs the Federal Government to establish a new Federal Spectrum Access System (SAS) using industry partners that will serve as an information and control clearinghouse for band-by-band spectrum registrations and conditions of use and allow non-Federal users to access underutilized spectrum in Federal bands. The SAS will practice the fundamental principle that underutilized spectrum capacity should be used or shared to the greatest extent.
- 2013 [103]: The Presidential Memorandum of June 2013, “Expanding America’s Leadership in Wireless Innovation,” calls for continued efforts to make more spectra available for wireless broadband applications. The memorandum advocates spectra sharing as an essential means of making more spectra available. In doing so, it sustains the momentum of [2], which made a case for advanced spectrum sharing and called for identifying 1000 MHz of Federal spectra dedicated to pilot projects.
- 2014 [104,105]: FCC proposed the baseline technical standards for the operation of Citizens Broadband Radio Service Devices (CBSDs) and End User Devices in the 3.5 GHz band and general rules for the operation of the SAS and approval of SAS Administrators. The WInnForum created a Spectrum Sharing Committee focused on implementing the US Federal Communications Commission’s regulations for three-tiered spectrum sharing in the 3550–3700 MHz Citizens Broadband Radio Service (CBRS) band. The Committee presently has broad participation from over 60 organizational stakeholders in the new 3.5 GHz band, including wireless operators, Spectrum Access System developers, equipment manufacturers, satellite operators, Wireless Internet Service Providers (WISPs), utilities, the US government, and others.
- 2015 [106]: In April 2015, the FCC formally established a three-tier framework to support making the federal band comprising 3550–3700 MHz, available for shared broadband commercial use under the title the Citizens Broadband Radio Service (CBRS), utilizing the SAS model. The Commission adopted service and technical rules governing the 3.5 GHz band as the new Part 96 of its rules.
- 2016 [104] The FCC completed the regulatory framework and finalized the rules governing the use of the CBRS band, including the finalized specific licensing, technical, and service rules for dynamic sharing between the three tiers of users. Furthermore, the formation of CRBS Alliance initiatives with participation from Access Technologies (Alphabet), Federated Wireless, Intel, Nokia, Qualcomm, and Ruckus Wireless.
- 2017 [107]: To promote additional investment to facilitate 5G network deployment in the CBRS band, the industrial stakeholders (such as CTIA and T-Mobile) filed petitions for rulemaking, which asked the Commission to reexamine several of the Part 96 rules related to PALs. They also proposed several changes to the PAL licensing rules, including much larger license areas, longer license terms, and renewability. The Commission carefully considered input from the various stakeholders to develop an approach that strikes an improved balance among the different use cases for the band.
- 2018 [107]: With the release of the FCC’s third Report and Order, the FCC increased PAL license areas to county size and lengthened PAL license terms to 10 years. It is anticipated that adopting similar rules in this band will help promote additional investment in the next generation of wireless services. FCC also adopted changes to the technical rules to facilitate transmissions over wider bandwidth channels without significant power reduction and changes to the information security requirements to safeguard commercially sensitive information better and protect critical infrastructure. It was anticipated that the targeted changes described herein would spur additional investment and broader deployment in the band, promote robust and efficient spectrum use, and help ensure the rapid deployment of advanced wireless technologies (including 5G) in the United States. The FCC and NTIA started the Spectrum Access System (SAS) and Environmental Sensing Capability (ESC) certification process and SAS testing for Amdocs, CommScope, Google, Federated Wireless, and Sony. The FCC announced the establishment of the initial commercial deployments (ICD) process and ESC registration process, and SAS administrators submitted ICD proposals to the FCC. It also issued the first CBSD certifications to Ericsson, Nokia, Sercomm, and Ruckus Networks and the first End-User Device (EUD) certification to Sierra Wireless. The CBRS Alliance published Release 1 of the Network and Coexistence Baseline Specifications and launched the OnGo brand and certification program. WInnForum released the final code for CBSD protocol testing and approved the first six test labs for CBRS standards compliance.
- 2019 [108,109,110]: The CBRS Baseline Standards Release 1 was created by the WInnForum to address the requirements of 47 CFR (Code for Federal Regulation) Part 96 and develop an ecosystem of interoperable Spectrum Access System and CBRS device technologies. WinnForum approved Nokia, CommScope, Federated Wireless, and Google as CBRS Certified Professional Installer (CPI) Training Program Administrators and Insta, Kyrio, and CommScope as CBRS Root CA Operators. Similarly, FCC approved five SAS administrators: Amdocs, CommScope, Google, Sony, and Federated Wireless.
- 2020 [111,112,113]: This release 2 of CBRS Baseline Standards by WInnForum is the beginning of bringing new functionality to the CBRS ecosystem, moving beyond the features required for regulatory compliance to the features users, operators, and suppliers desire to make CBRS more effective for their missions. Throughout 2020, the Forum has continued to expand Release 2 specification enhancements to the baseline CBRS Operational and Functional Requirements. The resulting optional features and functionality can be incorporated at any time, with a special focus on supporting specific vertical markets and their deployments. To address backward compatibility with the WinnForum Release 1 Baseline Standards, the only mandatory feature in Release 2 for a SAS or CBSD is to support the feature-capability exchange between SASs and CBSDs. After 76 rounds, the FCC auction of PAL licenses in the 3550–3650 MHz band was completed on August 25th, 2020, raising more than USD billion in bids. The auction made the greatest number of spectrum licenses available in a single FCC auction.
- 2021 [114]: The issuance of PAL Licenses, i.e., SAS support for PAL, is expected by the FCC in 2021. FCC-approved SAS Administrators (Amdocs, CommScope, Federated Wireless, Google, and Sony) have notified the WInnForum that they are working to implement PAL support based on the current FCC rules and established WInnForum standards.
- 2022: The National Advanced Spectrum and Communications Test Network (NASCTN) is hosting a public meeting (https://www.federalregister.gov/documents/2022/07/01/2022-14164/national-advanced-spectrum-and-communications-test-network-citizens-broadband-radio-service-sharing (accessed on 29 November 2022)) on NASCTN’s next project, the Citizens Broadband Radio Service (CBRS) Sharing Ecosystem Assessment. This meeting aims to bring together federal, industry, and academic stakeholders to disseminate information about NASCTN’s next project. NASCTN’s next project, the CBRS Sharing Ecosystem Assessment, seeks to provide data-driven insight into the CBRS sharing ecosystem’s effectiveness between commercial and DoD radar systems and to track changes in the spectrum environment over time.
6. Discussion
6.1. Resource Allocation
6.2. Privacy
7. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Xie, X.; Rong, B.; Kadoch, M. Explaining 6G Spectrum THz, MmWave, Sub 6, and Low-Band. In 6G Wireless Communications and Mobile Networking; Xie, X., Rong, B., Kadoch, M., Eds.; Bentham Science Publishers: Sharjah, United Arab Emirates, 2021; pp. 1–22. ISBN 978-1-68-108796-2. [Google Scholar]
- Xiao, M.; Mumtaz, S.; Huang, Y.; Dai, L.; Li, Y.; Matthaiou, M.; Karagiannidis, G.K.; Björnson, E.; Yang, K.; Chih-Lin, I.; et al. Millimeter Wave Communications for Future Mobile Networks. IEEE J. Sel. Areas Commun. 2017, 35, 1909–1935. [Google Scholar] [CrossRef]
- Zhang, Z.; Xiao, Y.; Ma, Z.; Xiao, M.; Ding, Z.; Lei, X.; Karagiannidis, G.K.; Fan, P. 6G Wireless Networks: Vision, Requirements, Architecture, and Key Technologies. IEEE Veh. Technol. Mag. 2019, 14, 28–41. [Google Scholar] [CrossRef]
- Hassan, M.R.; Karmakar, G.C.; Kamruzzaman, J.; Srinivasan, B. Exclusive Use Spectrum Access Trading Models in Cognitive Radio Networks: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2192–2231. [Google Scholar] [CrossRef]
- In the Matter of Unlicensed Operation in the TV Broadcast Bands, Additional Spectrum for Unlicensed Devices Below 900 MHz and in the 3 GHz Band. Available online: https://www.fcc.gov/document/matter-unlicensed-operation-tv-broadcast-bands-additional (accessed on 19 November 2022).
- FCC Releases Rules for Innovative Spectrum Sharing in 3.5 GHz Band. Available online: https://www.fcc.gov/document/fcc-releases-rules-innovative-spectrum-sharing-35-ghz-band (accessed on 19 November 2022).
- 47 CFR Part 96—Citizens Broadband Radio Service. Available online: https://www.ecfr.gov/current/title-47/chapter-I/subchapter-D/part-96 (accessed on 19 November 2022).
- Private LTE Networks. Available online: https://www.qualcomm.com/media/documents/files/private-lte-networks.pdf (accessed on 19 November 2022).
- CBRS Operational Security. WINNF-TS-0071. Wireless Innovation Forum. Available online: https://cbrs.wirelessinnovation.org/release-1-standards-specifications (accessed on 19 November 2022).
- Bhattarai, S.; Vaka, P.R.; Park, J.-M. Thwarting Location Inference Attacks in Database-Driven Spectrum Sharing. IEEE Trans. Cogn. Commun. Netw. 2018, 4, 314–327. [Google Scholar] [CrossRef]
- Agarwal, P.; Kumar, A.; Yamaguchi, R.S. Privacy Preserving Scheme for Operating Frequency of Incumbents in Citizens Broadband Radio Service. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11–14 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–10. [Google Scholar]
- Wang, J.; Errapotu, S.M.; Gong, Y.; Qian, L.; Jantti, R.; Pan, M.; Han, Z. Data-Driven Optimization Based Primary Users’ Operational Privacy Preservation. IEEE Trans. Cogn. Commun. Netw. 2018, 4, 357–367. [Google Scholar] [CrossRef]
- Requirements for Commercial Operation in the U.S. 3550–3700 MHz Citizens Broadband Radio Service Band. WINNF-TS-0112. Wireless Innovation Forum. Available online: https://cbrs.wirelessinnovation.org/release-1-standards-specifications (accessed on 19 November 2022).
- Signaling Protocols and Procedures for Citizens Broadband Radio Service (CBRS): Spectrum Access System (SAS)—Citizens Broadband Radio Service Device (CBSD) Interface Technical Specification. WINNF-TS-0016. Wireless Innovation Forum. Available online: https://cbrs.wirelessinnovation.org/release-1-standards-specifications (accessed on 19 November 2022).
- Ye, Y.; Wu, D.; Shu, Z.; Qian, Y. Overview of LTE Spectrum Sharing Technologies. IEEE Access 2016, 4, 8105–8115. [Google Scholar] [CrossRef]
- Parida, P.; Dhillon, H.S.; Nuggehalli, P. Stochastic Geometry-Based Modeling and Analysis of Citizens Broadband Radio Service System. IEEE Access 2017, 5, 7326–7349. [Google Scholar] [CrossRef]
- Krishnan, N.N.; Kumbhkar, R.; Mandayam, N.B.; Seskar, I.; Kompella, S. Coexistence of Radar and Communication Systems in CBRS Bands through Downlink Power Control. In Proceedings of the MILCOM 2017, 2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 713–718. [Google Scholar]
- Manosha, K.B.S.; Matinmikko-Blue, M.; Latva-aho, M. Framework for Spectrum Authorization Elements and Its Application to 5G Micro-Operators. In Proceedings of the 2017 Internet of Things Business Models, Users, and Networks, Copenhagen, Denmark, 23–24 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–8. [Google Scholar]
- Basnet, S.; Jayawickrama, B.A.; He, Y.; Dutkiewicz, E. Considering Switching Overhead for Transmit Power Allocation for GAA in Spectrum Access System. In Proceedings of the 2017 17th International Symposium on Communications and Information Technologies (ISCIT), Cairns, Australia, 25–27 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–5. [Google Scholar]
- Yin, L.; Li, S.; Zhu, H.; Ma, Y.; Teng, Y.; Liu, H. Reduced-Power Almost Black Subframe Based Pulse Radar Spectrum Sharing for LTE System. IEEE Trans. Electromagn. Compat. 2018, 60, 1223–1230. [Google Scholar] [CrossRef]
- Achatz, R.J. Interference Protection Criteria Simulation. In Proceedings of the 2018 IEEE Radar Conference (RadarConf18), Oklahoma City, OK, USA, 23–27 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 473–477. [Google Scholar]
- Krishnan, N.N.; Mandayam, N.; Seskar, I.; Kompella, S. Experiment: Investigating Feasibility of Coexistence of LTE-U with a Rotating Radar in CBRS Bands. In Proceedings of the 2018 IEEE 5G World Forum (5GWF), Silicon Valley, CA, USA, 8–11 July 2018; pp. 65–70. [Google Scholar]
- Kliks, A.; Kryszkiewicz, P.; Kulacz, L.; Kowalik, K.; Kolodziejski, M.; Kokkinen, H.; Ojaniemi, J.; Kivinen, A. Spectrum Management Application for Virtualized Wireless Vehicular Networks: A Step Toward Programmable Spectrum Management in Future Wireless Networks. IEEE Veh. Technol. Mag. 2018, 13, 94–105. [Google Scholar] [CrossRef]
- Kang, D.H.; Balachandran, K.; Buchmayer, M. Coexistence Performance of GAA Use Cases Using LTE-TDD Technologies in 3.5GHz CBRS Spectrum. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–7. [Google Scholar]
- Basnet, S.; Jayawickrama, B.A.; He, Y.; Dutkiewicz, E. Transmit Power Allocation for General Authorized Access in Spectrum Access System Using Carrier Sensing Range. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Lees, W.M.; Wunderlich, A.; Jeavons, P.J.; Hale, P.D.; Souryal, M.R. Deep Learning Classification of 3.5-GHz Band Spectrograms with Applications to Spectrum Sensing. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 224–236. [Google Scholar] [CrossRef]
- Tarver, C.; Tonnemacher, M.; Chandrasekhar, V.; Chen, H.; Ng, B.L.; Zhang, J.; Cavallaro, J.R.; Camp, J. Enabling a “Use-or-Share” Framework for PAL–GAA Sharing in CBRS Networks via Reinforcement Learning. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 716–729. [Google Scholar] [CrossRef]
- Basnet, S.; He, Y.; Dutkiewicz, E.; Jayawickrama, B.A. Resource Allocation in Moving and Fixed General Authorized Access Users in Spectrum Access System. IEEE Access 2019, 7, 107863–107873. [Google Scholar] [CrossRef]
- Kulacz, L.; Kryszkiewicz, P.; Kliks, A.; Bogucka, H.; Ojaniemi, J.; Paavola, J.; Kalliovaara, J.; Kokkinen, H. Coordinated Spectrum Allocation and Coexistence Management in CBRS-SAS Wireless Networks. IEEE Access 2019, 7, 139294–139316. [Google Scholar] [CrossRef]
- Troglia, M.; Melcher, J.; Zheng, Y.; Anthony, D.; Yang, A.; Yang, T. FaIR: Federated Incumbent Detection in CBRS Band. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Gao, W.; Sahoo, A. Performance Study of a GAA-GAA Coexistence Scheme in the CBRS Band. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–10. [Google Scholar]
- Cui, P.; Chen, S.; Camp, J. GreenLoading: Using the Citizens Band Radio for Energy-Efficient Offloading of Shared Interests. Comput. Commun. 2019, 144, 66–75. [Google Scholar] [CrossRef]
- Jeon, J.; Ford, R.D.; Ratnam, V.V.; Cho, J.; Zhang, J. Coordinated Dynamic Spectrum Sharing for 5G and Beyond Cellular Networks. IEEE Access 2019, 7, 111592–111604. [Google Scholar] [CrossRef]
- Sahoo, A. Fair Resource Allocation in the Citizens Broadband Radio Service Band. In Proceedings of the 2017 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Piscataway, NJ, USA, 6–9 March 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–2. [Google Scholar]
- Gao, W.; Sahoo, A. Performance Impact of Coexistence Groups in a GAA-GAA Coexistence Scheme in the CBRS Band. IEEE Trans. Cogn. Commun. Netw. 2021, 7, 184–196. [Google Scholar] [CrossRef] [PubMed]
- Cai, M.; Laneman, J.N. Wideband Distributed Spectrum Sharing with Multichannel Immediate Multiple Access. Analog. Integr. Circ. Sig. Process 2017, 91, 239–255. [Google Scholar] [CrossRef][Green Version]
- Parida, P.; Dhillon, H.S.; Nuggehalli, P. Stochastic Geometry Perspective of Unlicensed Operator in a CBRS System. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), San Francisco, CA, USA, 19–22 March 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–7. [Google Scholar]
- Palola, M.; Hoyhtya, M.; Aho, P.; Mustonen, M.; Kippola, T.; Heikkila, M.; Yrjola, S.; Hartikainen, V.; Tudose, L.; Kivinen, A.; et al. Field Trial of the 3.5 GHz Citizens Broadband Radio Service Governed by a Spectrum Access System (SAS). In Proceedings of the 2017 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Piscataway, NJ, USA, 6–9 March 2017; IEEE: Piscataway, NJ, USA, 2019; pp. 1–9. [Google Scholar]
- Parvez, I.; Khan, T.; Sarwat, A.I.; Parvez, Z. LAA-LTE and WiFi Based Smart Grid Metering Infrastructure in 3.5 GHz Band. In Proceedings of the 2017 IEEE Region 10 Humanitarian Technology Conference (R10-HTC), Dhaka, Bangladesh, 21–23 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 151–155. [Google Scholar]
- Youssef, Z.; Majeed, E.; Mueck, M.D.; Karls, I.; Drewes, C.; Bruck, G.; Jung, P. Performance Enhancement of the CSMA/CA MAC Mechanisms Using a Reject Request to Send (RRTS) Message for 3.5 GHz Shared Spectrum Systems. In Proceedings of the 2018 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–8. [Google Scholar]
- Youssef, Z.; Majeed, E.; Mueck, M.D.; Karls, I.; Drewes, C.; Bruck, G.; Jung, P. Concept Design of Medium Access Control for Spectrum Access Systems in 3.5 GHz. In Proceedings of the 2018 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2018; pp. 1–8. [Google Scholar]
- Foukas, X.; Marina, M.K.; Kontovasilis, K. Iris: Deep Reinforcement Learning Driven Shared Spectrum Access Architecture for Indoor Neutral-Host Small Cells. IEEE J. Select. Areas Commun. 2019, 37, 1820–1837. [Google Scholar] [CrossRef]
- Sahoo, A.; El Ouni, N.; Shenoy, V. A Study of Timing Constraints and SAS Overload of SAS-CBSD Protocol in the CBRS Band. In Proceedings of the 2019 IEEE Globecom Workshops (GC Wkshps), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Clark, M.A.; Psounis, K. Trading Utility for Privacy in Shared Spectrum Access Systems. IEEE/ACM Trans. Networking 2018, 26, 259–273. [Google Scholar] [CrossRef]
- Sohul, M.M.; Yao, M.; Yang, T.; Reed, J.H. Spectrum Access System for the Citizen Broadband Radio Service. IEEE Commun. Mag. 2015, 53, 18–25. [Google Scholar] [CrossRef]
- Kuester, D.G.; Jacobs, R.T.; Ma, Y.; Coder, J.B. Testing Spectrum Sensing Networks by UAV. In Proceedings of the 2016 United States National Committee of URSI National Radio Science Meeting (USNC-URSI NRSM), Boulder, CO, USA, 6–9 January 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–2. [Google Scholar]
- Ghosh, A.; Berry, R.A.; Aggarwal, V. Spectrum Measurement Markets for Tiered Spectrum Access. IEEE Trans. Cogn. Commun. Netw. 2018, 4, 929–941. [Google Scholar] [CrossRef]
- Ghosh, A.; Aggarwal, V.; Chakraborty, P. Tiered Spectrum Measurement Markets for Joint Licensed and Unlicensed Secondary Access. IEEE Trans. Netw. Sci. Eng. 2020, 7, 1295–1309. [Google Scholar] [CrossRef]
- Jo, M.; Chen, X.; Kim, K.S. OP-Map Based Next Generation Frequency Sharing System. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar]
- Hasan, C.; Marina, M.K. Communication-Free Inter-Operator Interference Management in Shared Spectrum Small Cell Networks. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–10. [Google Scholar]
- Butt, M.M.; Macaluso, I.; Galiotto, C.; Marchetti, N. Fair Dynamic Spectrum Management in Licensed Shared Access Systems. IEEE Syst. J. 2019, 13, 2363–2374. [Google Scholar] [CrossRef]
- Souryal, M.R.; Nguyen, T.T. Independent Calculation of Move Lists for Incumbent Protection in a Multi-SAS Shared Spectrum Environment. IEEE Wireless Commun. Lett. 2021, 10, 38–42. [Google Scholar] [CrossRef]
- Manosha, K.B.S.; Joshi, S.; Hanninen, T.; Jokinen, M.; Pirinen, P.; Posti, H.; Horneman, K.; Yrjola, S.; Latva-aho, M. A Channel Allocation Algorithm for Citizens Broadband Radio Service/Spectrum Access System. In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Findland, 12–15 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Ying, X.; Buddhikot, M.M.; Roy, S. SAS-Assisted Coexistence-Aware Dynamic Channel Assignment in CBRS Band. IEEE Trans. Wirel. Commun. 2018, 17, 6307–6320. [Google Scholar] [CrossRef]
- Hiltunen, K.; Matinmikko-Blue, M.; Latva-aho, M. Impact of Interference Between Neighbouring 5G Micro Operators. Wirel. Pers. Commun. 2018, 100, 127–144. [Google Scholar] [CrossRef]
- Souryal, M.R.; Nguyen, T.T. Effect of Federal Incumbent Activity on CBRS Commercial Service. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–5. [Google Scholar]
- Karaki, R.; Mukherjee, A. Coexistence of Contention-Based General Authorized Access Networks in 3.5 GHz CBRS Band. In Proceedings of the 2018 IEEE 87th Vehicular Technology Conference (VTC Spring), Porto, Portugal, 3–6 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Tonnemacher, M.; Tarver, C.; Chandrasekhar, V.; Chen, H.; Huang, P.; Ng, B.L.; Charlie Zhang, J.; Cavallaro, J.R.; Camp, J. Opportunistic Channel Access Using Reinforcement Learning in Tiered CBRS Networks. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; pp. 1–10. [Google Scholar]
- Dong, X.; Gong, Y.; Ma, J.; Guo, Y. Protecting Operation-Time Privacy of Primary Users in Downlink Cognitive Two-Tier Networks. IEEE Trans. Veh. Technol. 2018, 67, 6561–6572. [Google Scholar] [CrossRef]
- Tuukkanen, T.; Yrjola, S.; Matinmikko, M.; Ahokangas, P.; Mustonen, M. Armed Forces’ Views on Shared Spectrum Access. In Proceedings of the 2017 International Conference on Military Communications and Information Systems (ICMCIS), Oulu, Finland, 15–16 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–8. [Google Scholar]
- Palola, M.; Hartikainen, V.; Mäkeläinen, M.; Kippola, T.; Aho, P.; Lähetkangas, K.; Tudose, L.; Kivinen, A.; Joshi, S.; Hallio, J. The first end-to-end live trial of CBRS with carrier aggregation using 3.5 GHz LTE equipment. In Proceedings of the IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Baltimore, MD, USA, 6–9 March 2017; pp. 1–2. [Google Scholar]
- Saha, G.; Abouzeid, A.A.; Matinmikko-Blue, M. Online Algorithm for Leasing Wireless Channels in a Three-Tier Spectrum Sharing Framework. IEEE/ACM Trans. Netw. 2018, 26, 2623–2636. [Google Scholar] [CrossRef]
- Xin, C.; Song, M. Analysis of the On-Demand Spectrum Access Architecture for CBRS Cognitive Radio Networks. IEEE Trans. Wirel. Commun. 2020, 19, 970–978. [Google Scholar] [CrossRef]
- Saha, G.; Abouzeid, A.A. Optimal Joint Partitioning and Licensing of Spectrum Bands in Tiered Spectrum Access under Stochastic Market Models. In Proceedings of the 2020 18th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOPT), Volos, Greece, 15–19 June 2020; pp. 1–8. [Google Scholar]
- Xing, L.; Ma, Q.; Gao, J.; Chen, S. An Optimized Algorithm for Protecting Privacy Based on Coordinates Mean Value for Cognitive Radio Networks. IEEE Access 2018, 6, 21971–21979. [Google Scholar] [CrossRef]
- Mao, Y.; Chen, T.; Zhang, Y.; Wang, T.; Zhong, S. Towards Privacy-Preserving Aggregation for Collaborative Spectrum Sensing. IEEE Trans. Inform. Forensic Secur. 2017, 12, 1483–1493. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhang, H.; He, S.; Cheng, P. Bilateral Privacy-Preserving Utility Maximization Protocol in Database-Driven Cognitive Radio Networks. IEEE Trans. Dependable Secur. Comput. 2020, 17, 236–247. [Google Scholar] [CrossRef]
- Grissa, M.; Hamdaoui, B.; Yavuz, A.A. Location Privacy in Cognitive Radio Networks: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 1726–1760. [Google Scholar] [CrossRef]
- CBRS Communications Security Technical Specification. WINNF-TS-0065. Wireless Innovation Forum. Available online: https://cbrs.wirelessinnovation.org/release-1-standards-specifications (accessed on 19 November 2022).
- Shi, S.; Xiao, Y.; Lou, W.; Wang, C.; Li, X.; Hou, Y.T.; Reed, J.H. Challenges and New Directions in Securing Spectrum Access Systems. IEEE Internet Things J. 2021, 8, 6498–6518. [Google Scholar] [CrossRef]
- An, K.; Lin, M.; Ouyang, J.; Zhu, W.-P. Secure Transmission in Cognitive Satellite Terrestrial Networks. IEEE J. Select. Areas Commun. 2016, 34, 3025–3037. [Google Scholar] [CrossRef]
- Vaka, P.R.; Bhattarai, S.; Park, J.-M. Location Privacy of Non-Stationary Incumbent Systems in Spectrum Sharing. In Proceedings of the 2016 IEEE Global Communications Conference (GLOBECOM), Washington, DC, USA, 4–8 December 2016; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Grissa, M.; Yavuz, A.A.; Hamdaoui, B. Location Privacy in Cognitive Radios With Multi-Server Private Information Retrieval. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 949–962. [Google Scholar] [CrossRef]
- Grissa, M.; Yavuz, A.A.; Hamdaoui, B. When the Hammer Meets the Nail: Multi-Server PIR for Database-Driven CRN with Location Privacy Assurance. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; IEEE: Piscataway, NJ, USA; pp. 1–9. [Google Scholar]
- Dou, Y.; Zeng, K.; Yang, Y.; Ren, K. Preserving Incumbent Users’ Privacy in Exclusion-Zone-Based Spectrum Access Systems: Poster. In Proceedings of the 22nd Annual International Conference on Mobile Computing and Networking, New York City, NY, USA, 3 October 2016; ACM: New York, NY, USA, 2016; pp. 473–474. [Google Scholar]
- Dou, Y.; Zeng, K.; Li, H.; Yang, Y.; Gao, B.; Ren, K.; Li, S. P2-SAS: Privacy-Preserving Centralized Dynamic Spectrum Access System. IEEE J. Sel. Areas Commun. 2017, 35, 173–187. [Google Scholar] [CrossRef]
- Dou, Y.; Zeng, K.; Li, H.; Yang, Y.; Gao, B.; Guan, C.; Ren, K.; Li, S. P2-SAS: Preserving Users’ Privacy in Centralized Dynamic Spectrum Access Systems. In Proceedings of the 17th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Paderborn, Germany, 5 July 2016; ACM: New York, NY, USA, 2016; pp. 321–330. [Google Scholar]
- Li, H.; Dou, Y.; Lu, C.; Zabransky, D.; Yang, Y.; Park, J.-M.J. Preserving the Incumbent Users’ Location Privacy in the 3.5 GHz Band. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–10. [Google Scholar]
- Bahrak, B.; Bhattarai, S.; Ullah, A.; Park, J.-M.J.; Reed, J.; Gurney, D. Protecting the Primary Users’ Operational Privacy in Spectrum Sharing. In Proceedings of the 2014 IEEE International Symposium on Dynamic Spectrum Access Networks (DYSPAN), McLean, VA, USA, 1–4 April 2014; pp. 236–247. [Google Scholar]
- Liu, J.; Zhang, C.; Lorenzo, B.; Fang, Y. DPavatar: A Real-Time Location Protection Framework for Incumbent Users in Cognitive Radio Networks. IEEE Trans. Mobile Comput. 2020, 19, 552–565. [Google Scholar] [CrossRef]
- Salama, A.M.; Li, M.; Lazos, L.; Xiao, Y.; Krunz, M. On the Privacy and Utility Tradeoff in Database-Assisted Dynamic Spectrum Access. In Proceedings of the 2018 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Seoul, Republic of Korea, 22–25 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–10. [Google Scholar]
- Salama, A.M.; Li, M.; Lazos, L.; Xiao, Y.; Krunz, M. Trading Privacy for Utility in Database-Assisted Dynamic Spectrum Access. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 611–624. [Google Scholar] [CrossRef]
- Clark, M.; Psounis, K. Can the Privacy of Primary Networks in Shared Spectrum Be Protected? In Proceedings of the IEEE INFOCOM 2016—The 35th Annual IEEE International Conference on Computer Communications, San Francisco, CA, USA, 10–14 April 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–9. [Google Scholar]
- He, X.; Jin, R.; Dai, H. Camouflaging Mobile Primary Users in Database-Driven Cognitive Radio Networks. IEEE Wirel. Commun. Lett. 2019, 8, 21–24. [Google Scholar] [CrossRef]
- Li, H.; Yang, Y.; Dou, Y.; Park, J.-M.J.; Ren, K. PeDSS: Privacy Enhanced and Database-Driven Dynamic Spectrum Sharing. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1477–1485. [Google Scholar]
- Cheng, Q.; Nguyen, D.N.; Dutkiewicz, E.; Mueck, M. Preserving Honest/Dishonest Users’ Operational Privacy with Blind Interference Calculation in Spectrum Sharing System. IEEE Trans. Mob. Comput. 2020, 19, 2874–2890. [Google Scholar] [CrossRef]
- Cheng, Q.; Nguyen, D.N.; Dutkiewicz, E.; Mueck, M.D. Preserving Operational Information in Spectrum Access System with Dishonest Users. In Proceedings of the 2017 17th International Symposium on Communications and Information Technologies (ISCIT), Cairns, Australia, 25–27 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Zhang, H.; Leng, S.; Chai, H. A Blockchain Enhanced Dynamic Spectrum Sharing Model Based on Proof-of-Strategy. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Grissa, M.; Yavuz, A.A.; Hamdaoui, B. TrustSAS: A Trustworthy Spectrum Access System for the 3.5 GHz CBRS Band. In Proceedings of the IEEE INFOCOM 2019—IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1495–1503. [Google Scholar]
- Grissa, M.; Yavuz, A.A.; Hamdaoui, B.; Tirupathi, C. Anonymous Dynamic Spectrum Access and Sharing Mechanisms for the CBRS Band. IEEE Access 2021, 9, 33860–33879. [Google Scholar] [CrossRef]
- Lin, Y.; Ye, Y.; Yang, Y. Preserving Incumbent User’s Location Privacy Against Environmental Sensing Capability. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–10. [Google Scholar]
- Clark, M.; Psounis, K. Designing Sensor Networks to Protect Primary Users in Spectrum Access Systems. In Proceedings of the 2017 13th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Jackson, WY, USA, 21–24 February 2017; pp. 112–119. [Google Scholar]
- Wang, N.; Le, J.; Li, W.; Jiao, L.; Li, Z.; Zeng, K. Privacy Protection and Efficient Incumbent Detection in Spectrum Sharing Based on Federated Learning. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 29 June–1 July 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–9. [Google Scholar]
- Ben Mosbah, A.; Hall, T.A.; Souryal, M.; Afifi, H. Analysis of the Vulnerability of the Incumbent Frequency to Inference Attacks in Spectrum Sharing. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 640–642. [Google Scholar]
- Ben Mosbah, A.; Hall, T.A.; Souryal, M.; Afifi, H. An Analytical Model for Inference Attacks on the Incumbent’s Frequency in Spectrum Sharing. In Proceedings of the 2017 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Piscataway, NJ, USA, 6–9 March 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–2. [Google Scholar]
- Clark, M.; Psounis, K. Optimizing Primary User Privacy in Spectrum Sharing Systems. IEEE/ACM Trans. Netw. 2020, 28, 533–546. [Google Scholar] [CrossRef]
- Zhang, R.; Wang, N.; Zhang, N.; Yan, Z.; Lou, W.; Thomas Hou, Y. PriRoster: Privacy-Preserving Radio Context Attestation in Cognitive Radio Networks. In Proceedings of the 2019 IEEE International Symposium on Dynamic Spectrum Access Networks (DySPAN), Newark, NJ, USA, 11 November 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–10. [Google Scholar]
- Agarwal, P.; Kumar, A.; Yamaguchi, R.S. Preserving Operation Frequency Privacy of Incumbents in CBRS. IEEE Access 2022, 10, 111022–111041. [Google Scholar] [CrossRef]
- Interdepartment Radio Advisory Committee (IRAC). National Telecommunications and Information Administration. Available online: https://www.ntia.doc.gov/page/interdepartment-radio-advisory-committee-irac (accessed on 20 November 2022).
- CFR 47 CFR 96. Available online: https://ecfr.io/Title-47/Part-96 (accessed on 20 November 2022).
- The CBRS Commercial Launch, Senza Fili. Available online: https://senzafili.com/reports/cbrs_launch/ (accessed on 13 August 2022).
- Presidential Memorandum: Unleashing the Wireless Broadband Revolution. Available online: https://obamawhitehouse.archives.gov/the-press-office/presidential-memorandum-unleashing-wireless-broadband-revolution (accessed on 20 November 2022).
- Report to the President: Realizing the Full Potential of Government-Held Spectrum to Spur Economic Growth. Available online: https://apps.dtic.mil/sti/citations/ADA565091 (accessed on 20 November 2022).
- Amendment of the Commission’s Rules with Regard to Commercial Operations in the 3550–3650 MHz Band. Available online: https://www.federalregister.gov/documents/2016/07/26/2016-14505/amendment-of-the-commissions-rules-with-regard-to-commercial-operations-in-the-3550-3650-mhz-band (accessed on 20 November 2022).
- FCC Announces NOTICE of Proposed Rulemaking for 3.5 GHz Band Auction, Federal Communications Commission, 23 April 2014. Available online: https://transition.fcc.gov/Daily_Releases/Daily_Business/2014/db0425/FCC-14-49A1.pdf (accessed on 20 November 2022).
- Shared Commercial Operations in the 3550–3650 MHz Band. Available online: https://www.federalregister.gov/documents/2015/06/23/2015-14494/shared-commercial-operations-in-the-3550-3650-mhz-band (accessed on 20 November 2022).
- Promoting Investment in the 3550–3700 MHz Band. Available online: https://www.federalregister.gov/documents/2018/12/07/2018-25795/promoting-investment-in-the-3550-3700-mhz-band (accessed on 20 November 2022).
- CBRS Certified Professional Installer (CPI) Training|WInnForum. Available online: https://cbrs.wirelessinnovation.org/cpi-program-administrator (accessed on 20 November 2022).
- WInnForum Approved CBRS Root CA Operators. Available online: https://cbrs.wirelessinnovation.org/cbrs-root-ca-operators (accessed on 20 November 2022).
- CBRS Baseline Standards Release 1. Wireless Innovation Forum. Available online: https://cbrs.wirelessinnovation.org/release-1-standards-specifications (accessed on 20 November 2022).
- Enhancements to Baseline Specifications. Available online: https://cbrs.wirelessinnovation.org/enhancements-to-baseline-specifications (accessed on 20 November 2022).
- PAL (CBRS) Auction Closes with 4.58B in Bids. Connected Real Estate Magazine, 27 August 2020.
- FCC Announces Winning Bidders of 3.5 GHz Band Auction. Available online: https://www.fcc.gov/document/fcc-announces-winning-bidders-35-ghz-band-auction (accessed on 20 November 2022).
- Inside the CBRS Ecosystem. Available online: https://cbrs.wirelessinnovation.org/cbrs-status-summary (accessed on 20 November 2022).
- Lin, Z.; An, K.; Niu, H.; Hu, Y.; Chatzinotas, S.; Zheng, G.; Wang, J. SLNR-Based Secure Energy Efficient Beamforming in Multibeam Satellite Systems. IEEE Trans. Aerosp. Electron. Syst. 2022, 1–4. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Wang, J.-B.; de Cola, T.; Wang, J. Joint Beamforming and Power Allocation for Satellite-Terrestrial Integrated Networks with Non-Orthogonal Multiple Access. IEEE J. Sel. Top. Signal Process. 2019, 13, 657–670. [Google Scholar] [CrossRef]
- Lin, Z.; Niu, H.; An, K.; Wang, Y.; Zheng, G.; Chatzinotas, S.; Hu, Y. Refracting RIS-Aided Hybrid Satellite-Terrestrial Relay Networks: Joint Beamforming Design and Optimization. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 3717–3724. [Google Scholar] [CrossRef]
- Tian, Z.; Chen, Z.; Wang, M.; Jia, Y.; Dai, L.; Jin, S. Reconfigurable Intelligent Surface Empowered Optimization for Spectrum Sharing: Scenarios and Methods. IEEE Veh. Technol. Mag. 2022. [Google Scholar] [CrossRef]
- CBRS Sharing Ecosystem Assessment. Available online: https://www.nist.gov/programs-projects/cbrs-sharing-ecosystem-assessment (accessed on 20 November 2022).









| Power | Delay | Bandwidth | References | |
| ✔ | X | X | [15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37] | |
| X | ✔ | X | [19,20,21,22,23,26,27,32,33,38,39,40,41,42,43,44] | |
| X | X | ✔ | [15,16,29,31,34,45,46,47,48,49,50,51,52] | |
| ✔ | ✔ | X | [19,20,21,22,23,26,27,32,33] | |
| ✔ | X | ✔ | [15,16,29,31,35] | |
| Resource | Distance | Traffic | Users | References |
| Allocation | ✔ | X | X | [16,17,24,29,35,41,44,45,53,54,55,56] |
| X | ✔ | X | [15,18,19,39,42,52,53,57,58] | |
| X | X | ✔ | [15,16,25,28,32,33,36,43,52,53,59,60,61,62] | |
| ✔ | ✔ | X | [31,41,53,63] | |
| X | ✔ | ✔ | [15,53] | |
| ✔ | X | ✔ | [16,53] |
| Obfuscation-Based Schemes | Cryptography-Based Schemes |
|---|---|
| [10,11,12,44,59,72], | [73,74,75,76,77,78], |
| [79,80,81,82,83,84], | [85,86,87,88,89,90], |
| [91,92,93,94,95,96] | [97] |
| Parameter | Related Works |
|---|---|
| Location | [10,44,72,79,80], |
| [81,82,83,84,91,92,93], | |
| Operation Time | [12,59] |
| Operation Frequency | [11,94,95] |
| Entity | Roles |
|---|---|
| NTIA & FCC | They are jointly responsible for spectrum management in the US. |
| IRAC [99] | Federal agencies provide input to NTIA and FCC deliberations through the Interdepartmental Radio Advisory Committee (IRAC). |
| 47 CFR— | Title 47 Section 96 sets forth the regulations governing the use of |
| Part 96—CBRS | devices in CBRS. CBSDs may be used in the frequency bands listed |
| [100] | in S:96.11, and their operation shall be coordinated by one or more |
| authorized Spectrum Access Systems (SASs). Similarly, PAL and | |
| GAA Users must not cause harmful interference to Incumbent Users | |
| and must accept interference from Incumbent Users. At the same | |
| time, GAA Users must not cause harmful interference to Priority | |
| Access Licensees, and must accept interference from Priority Access | |
| Licensees. | |
| 3GPP | It defines the 4G and 5G standards used in the CBRS band. Since |
| the CBRS band is technology-neutral, therefore, other | |
| access technologies can also be used in this band. | |
| CBRS Alliance | It promotes the adoption of 3GPP technologies in the CBRS band |
| through its members, which include vendors, carriers, service | |
| providers and SAS/ESC providers. It also defines specifications and | |
| manages the certification program for OnGo. OnGo is the CBRS | |
| Alliance created a brand for LTE-based CBRS equipment and its | |
| certification program. | |
| WinnForum | It focuses on the CRBS spectrum sharing mechanism, testing, and |
| certification.However, its scope is much wider than CBRS. | |
| It includes other countries, bands and ways to manage spectrum | |
| such as software-defined radio, cognitive radio, and | |
| dynamic spectrum access. |
| Year | Activity |
|---|---|
| 2010 | The presidential memorandum called NTIA and FCC to fully utilize the government-held spectrum to spur economic growth. |
| 2012 | US President initiated reforming spectrum policy and improve America’s wireless infrastructure. |
| 2013 | Presidential memorandum giving the FCC a mandate to pursue spectrum-sharing opportunities for the 3.5 GHz band. |
| 2014 | The FCC finalized a proposal for the creation of CBRS. WInnForum formed a Spectrum Sharing Committee to develop baseline standards. |
| 2015 | The FCC formally released a three-tier CBRS model. |
| 2016 | The FCC adopted rules for shared commercial use of the 3550–3700 MHz band, with three-tiered access and authorization framework. |
| 2017 | The FCC finalized rules for spectrum sharing in the CBRS band. |
| 2018 | The FCC increased PAL license areas to county size and lengthens PAL license terms to 10 years in the 3rd Report and Order. Several standardization initiatives from FCC, NTIA, CBRS Alliance, and WInnForum. |
| 2019 | WInnForum released CBRS Baseline Standards (Release 1). Approval of vendors for CBRS Certified Professional Installer (CPI) Training program Administrator and Root CA operator by WInnForum and SAS administrators by FCC. |
| 2020 | WInnForum released an enhancement to CBRS Baseline standards (Release 2) [111]. The completion of FCC auction of PAL licenses in August 2020. |
| 2021 | The issuance of PAL Licenses is expected by the FCC in 2021. FCC-approved SAS Administrators working to implement PAL support based on the current FCC rules and established WInnForum standards. |
| 2022 | NASCTN’s next project, the CBRS Sharing Ecosystem Assessment, seeks to provide data-driven insight into the CBRS sharing ecosystem’s effectiveness between commercial and DoD radar systems and to track changes in the spectrum environment over time. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Agarwal, P.; Manekiya, M.; Ahmad, T.; Yadav, A.; Kumar, A.; Donelli, M.; Mishra, S.T. A Survey on Citizens Broadband Radio Service (CBRS). Electronics 2022, 11, 3985. https://doi.org/10.3390/electronics11233985
Agarwal P, Manekiya M, Ahmad T, Yadav A, Kumar A, Donelli M, Mishra ST. A Survey on Citizens Broadband Radio Service (CBRS). Electronics. 2022; 11(23):3985. https://doi.org/10.3390/electronics11233985
Chicago/Turabian StyleAgarwal, Pranay, Mohammedhusen Manekiya, Tahir Ahmad, Ashish Yadav, Abhinav Kumar, Massimo Donelli, and Saurabh Tarun Mishra. 2022. "A Survey on Citizens Broadband Radio Service (CBRS)" Electronics 11, no. 23: 3985. https://doi.org/10.3390/electronics11233985
APA StyleAgarwal, P., Manekiya, M., Ahmad, T., Yadav, A., Kumar, A., Donelli, M., & Mishra, S. T. (2022). A Survey on Citizens Broadband Radio Service (CBRS). Electronics, 11(23), 3985. https://doi.org/10.3390/electronics11233985








