Zero-Tolerance Security Paradigm for Enterprise-Specific Industrial Internet of Things
Abstract
:1. Introduction
- (a)
- The ‘zero trust network architecture’ by enforcing a flexible and real-time vulnerability scanning on edge and intermediate nodes (i.e., sensors, actuators, PLCs (programmable logic controllers), routers, gateways). Implementing a zero trust framework allows stakeholders to update their IT security, run their hybrid operations, and access the full array of IIoT apps without fear of compromise.
- (b)
- Aggregate and disseminate required information (i.e., IP address, device physical location, system operation and production data, SCADA data, etc.).
- (c)
- Measure and verify the reliability, precision, integrity, quality and extensibility of the acquired data.
- (d)
- Respond to incidents by enforcing policies. The level of trust that should be allowed was determined with the use of in-depth and comprehensive knowledge about the operational identity and device settings.
- (a)
- analyze attack mapping in terms of behaviors and interactions,
- (b)
- improve the time and duration of detection and management of attacks,
- (c)
- keep track of information on the attacker and the victim,
- (d)
- adjust policy measures to accumulate metric details, and
- (e)
- proactively modify the risk assessment that has proven useful in preventing future risks.
2. Related Work
3. Security Authentication and Data Protection Challenges
3.1. Identification Challenge
3.2. Hardware Shareware Detachment
3.3. Intensity of IIoT Infrastructure SECURITY
- (a)
- Does information (i.e., during aggregation, processing, communication, and storage) need to be private (at edge, intermediate, gateway and base station)?
- (b)
- How many levels (i.e., sensing node, sink node, base station) of an audit will be conducted to obtain a desired data trust level?
- (c)
- What is the acceptable threshold of latency (i.e., in terms of data, network, and anomaly alerts generation)?
- (d)
- What is the applicable Access Control Policy selection and follow-up criteria to revoke a blacklisted device or data stream?
- (e)
- How often does firmware on IIoT devices need to be patched/updated, and what is the ‘access control right’ permission level of devices that need to be functional throughout an ongoing process?
- (f)
- What necessary preliminary steps must be taken before and after devices are decommissioned? This consideration is vital to diminish the risks associated with threats such as spoofing, software tempering, repudiation, denial of service, and regulatory non-compliance.
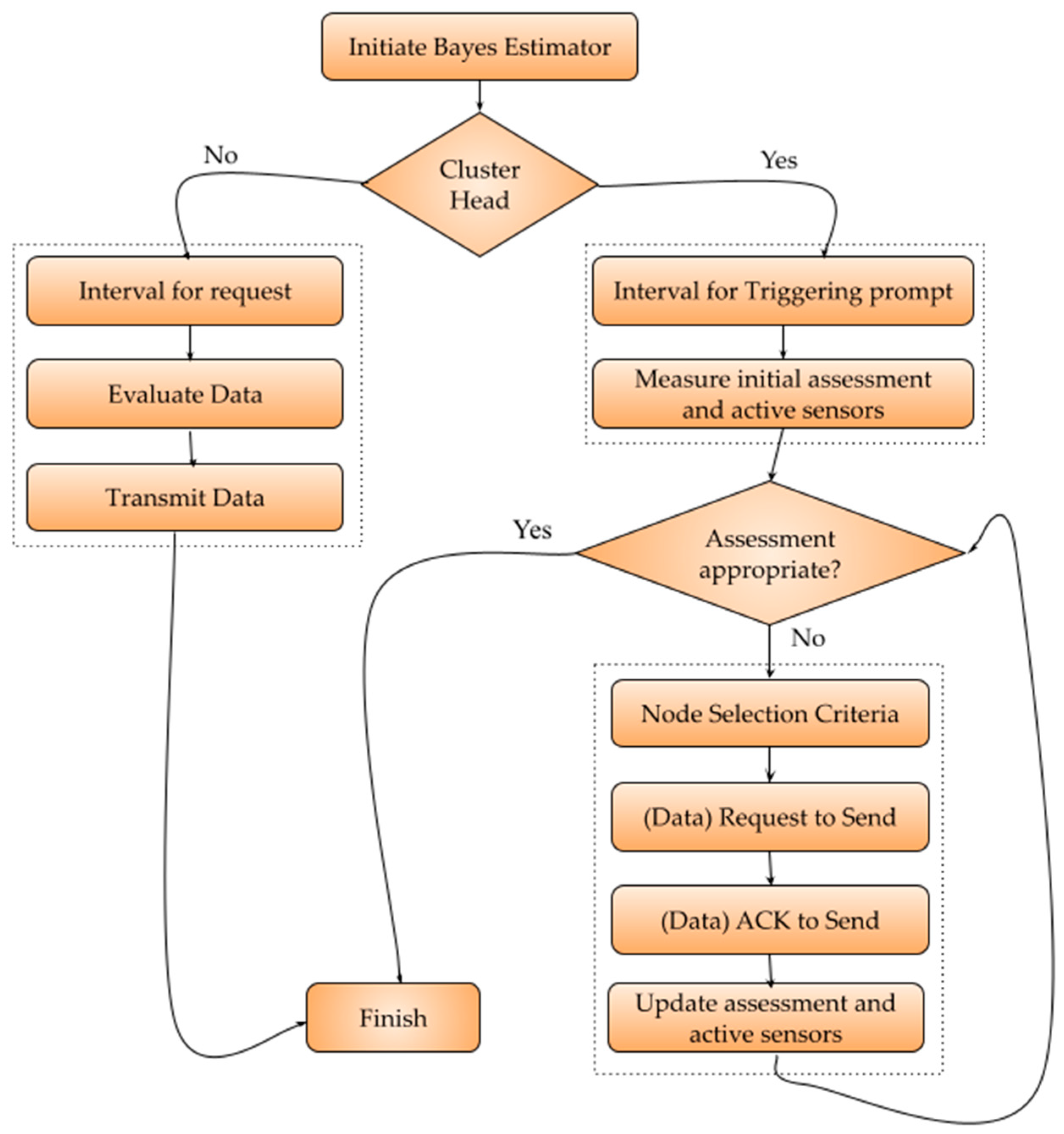
4. Proposed Framework
| Pseudo Code 1 (a): Connection to the server using session token |
| var session = provision.getSession(); var nodeId = session.node_id; var MAC = session.token; var parameters = {nodeID, MAC}; |
| Pseudo Code 1 (b): Alert generation |
| var discourse = "..."; var alert = { type: "indicator", body: "alert_ID", delay: { include_to_history: 01, negotiation_id: messge._id }, indicator: 01 }; var destination_node-Id = 07; attempt { alert.id = indicator.send(destination_node-Id, alert); } latch (m) { if (m.node_indicator === 'indicator_Not_Linked_Error') { } } |
| Pseudo Code 1(c): Ping node by ID |
| attempt { alert.ping(nodeId, utility (error) { if (error) { // no syn-alert received } else { // syn-alert received from node } }); } latch (m) { if (m.ID === 'indicator_Not_Connected_Error') { // not connected to node/server/basestation } } |
| Pseudo Code 1(d): Access Node List |
| try { node.alert.register.get(method(node_list) { }); } latch (m) { if (m.node_indicator === 'indicator_Not_Connected_Error') { } } |
| Pseudo Code 1(e): Add new node to register list |
| var nodeId = 56; attempt { node.alert.register.get (nodeId, method() { }); } latch (m) { if (m.node_indicator === 'indicator_Not_Connected_Error') { } } |
- (a)
- Insecure system devices that operate on nodes which are connected to the network.
- (b)
- The under-evaluation architecture only used the hardware components that are capable of Zigbee communication protocol usage [19].
- (c)
- Router that is eligible to connect to remote web edges.
- (d)
- In a situation in which it is difficult to keep track of the software, outdated firmware components were investigated.
- (e)
- A lack of ‘physical reinforcement’ that might potentially create an impending cyber-attack or seize native control of built-in Internet of Things devices.
- (a)
- Is the node legitimate?
- (b)
- Is the Sync protocol [20] feature enabled? If a device is not synchronized, it will not be able to join the network, regardless of whether or not it is compatible with certain IoT nodes.
- (c)
- Is the device subject to a particular exception which blocks the device, such as operability and packet exchange capability?
- (d)
- Does the device have a particular exception that allows the device?
- (e)
- Is the device scrambled by an appropriate node access rule?
- (f)
- Is the device restricted by an access rule for the corresponding node?
- (g)
- Does the device have a corresponding node access rule?
- (1)
- Indiscriminately choose a characteristic ‘b’ and a riven assessment ratio ‘m’.
- (2)
- Split ‘A’ into two subclasses by exhausting the rule b < m. The subgroups will match to a left and right sub-tree in ‘C’.
- (3)
- Repeat both steps 1 and 2 recursively, as long as the selected node has only one template or all results in the current node share the same values.
- (1)
- If r(d, f) is close to 1 then ‘d’ is probable to be an inconsistency.
- (2)
- If r(d, f) is less than 0.5, then ‘d’ is assumed to be a valid node.
- (3)
- If r(d, f) is adjacent to 0.5 for all of the criteria in the adopted ruleset and dataset, then the analysis does not indicate any anomalies.
- (a)
- Industrial IoT nodes have been pre-arranged in various clusters based on node features such as location and material type.
- (b)
- Industrial IoT nodes could be searched by active functions, such as connectivity rank, software type, application eminence and node status.
- (c)
- Installation (device and software) rollouts were actively monitored and were automatically halted if IoT nodes fail to sustain the pre-defined performance indicators (such as: device and application response time in milliseconds, TCP (Transmission Control Protocol) uplink/downlink, communication round trip time, packet loss (percentage) for uplink and downlink, error rate, and yield throughput).
- (d)
- Resilience ratio of errors during firmware updates.
- (e)
- Automatic logging of contextual information related to device activity.
- (f)
- Quarantine the error-prone device which, after identification, will be autonomically fixed (i.e., in accordance with firmware requirements).
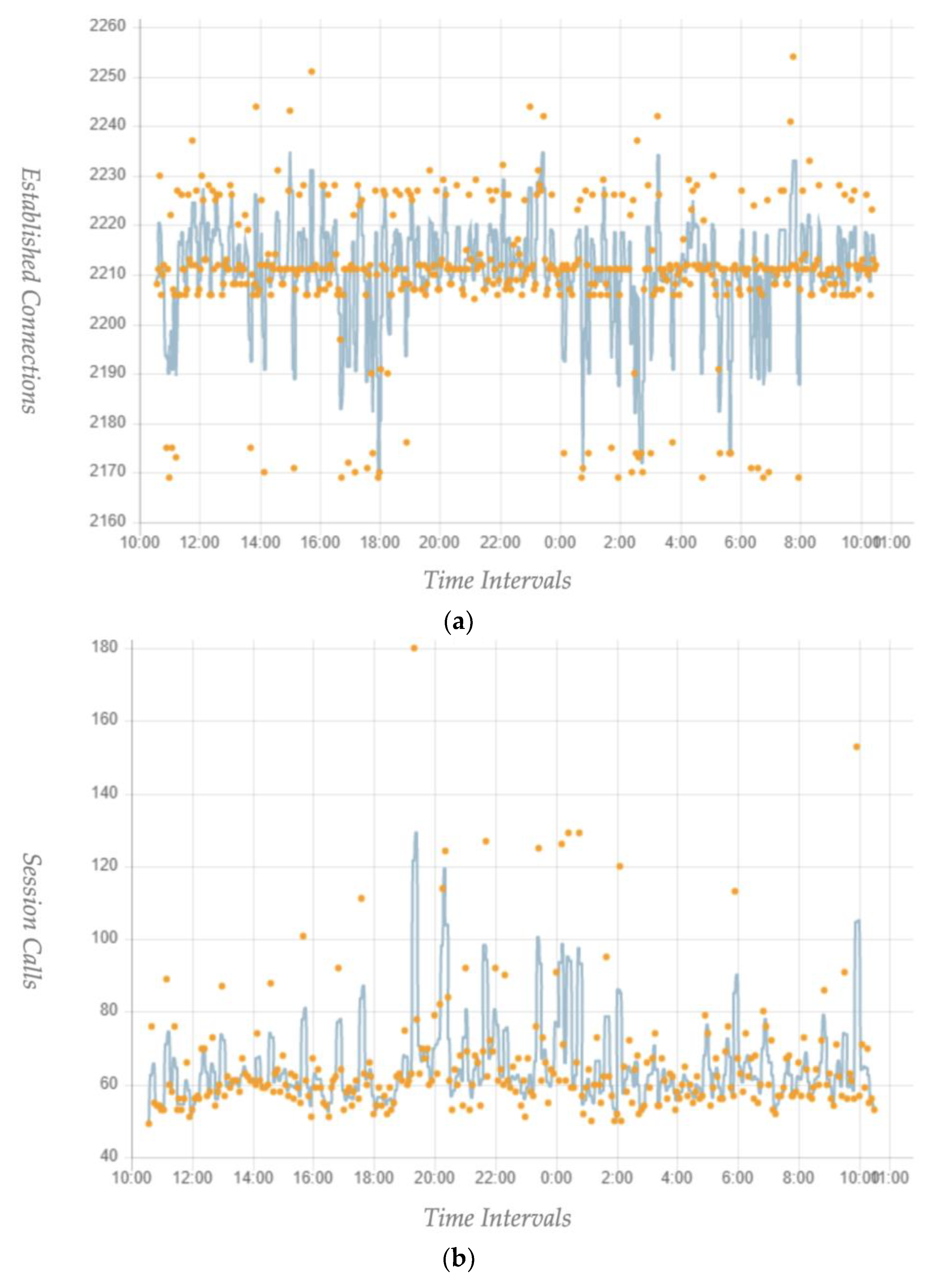
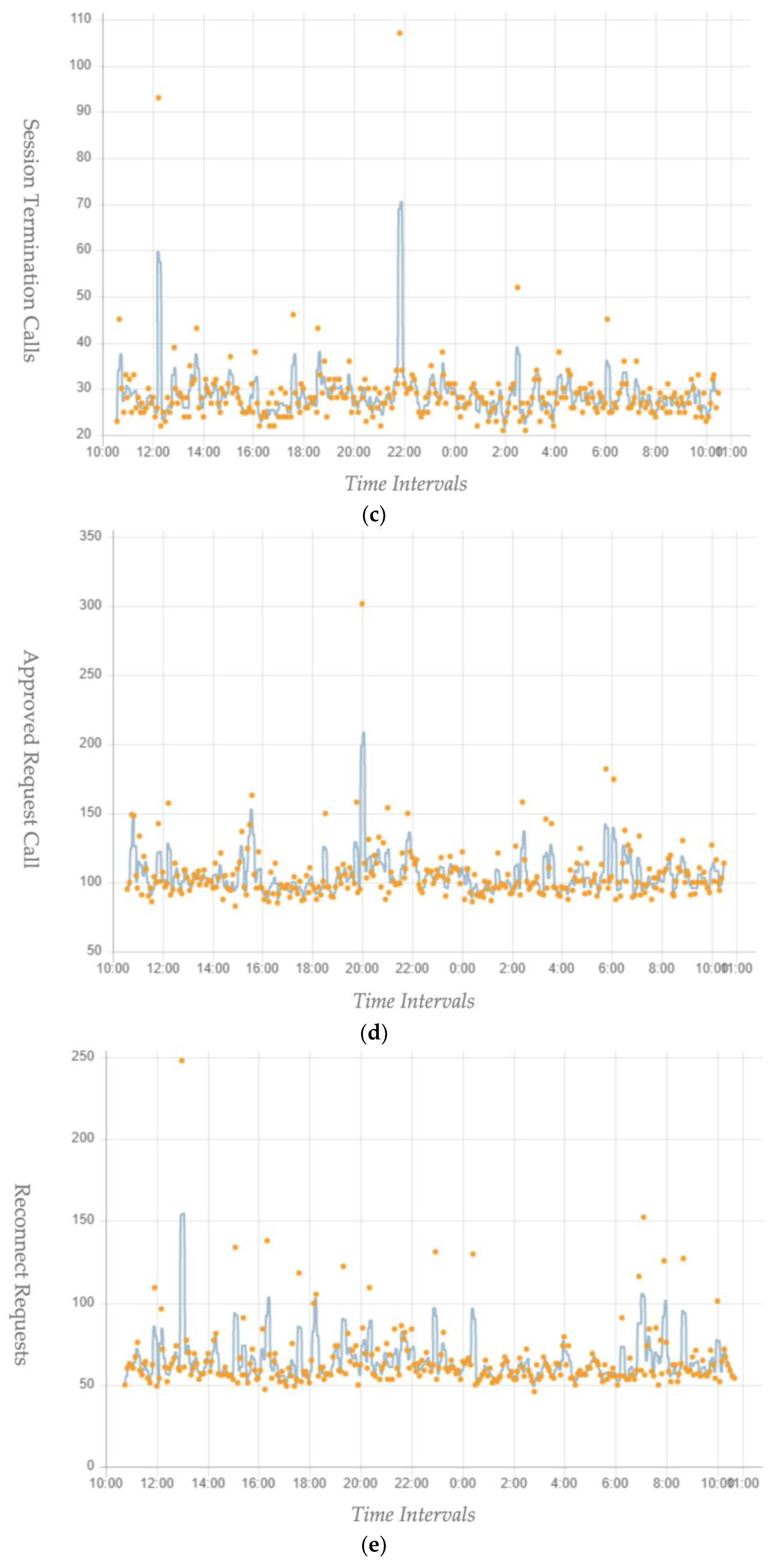
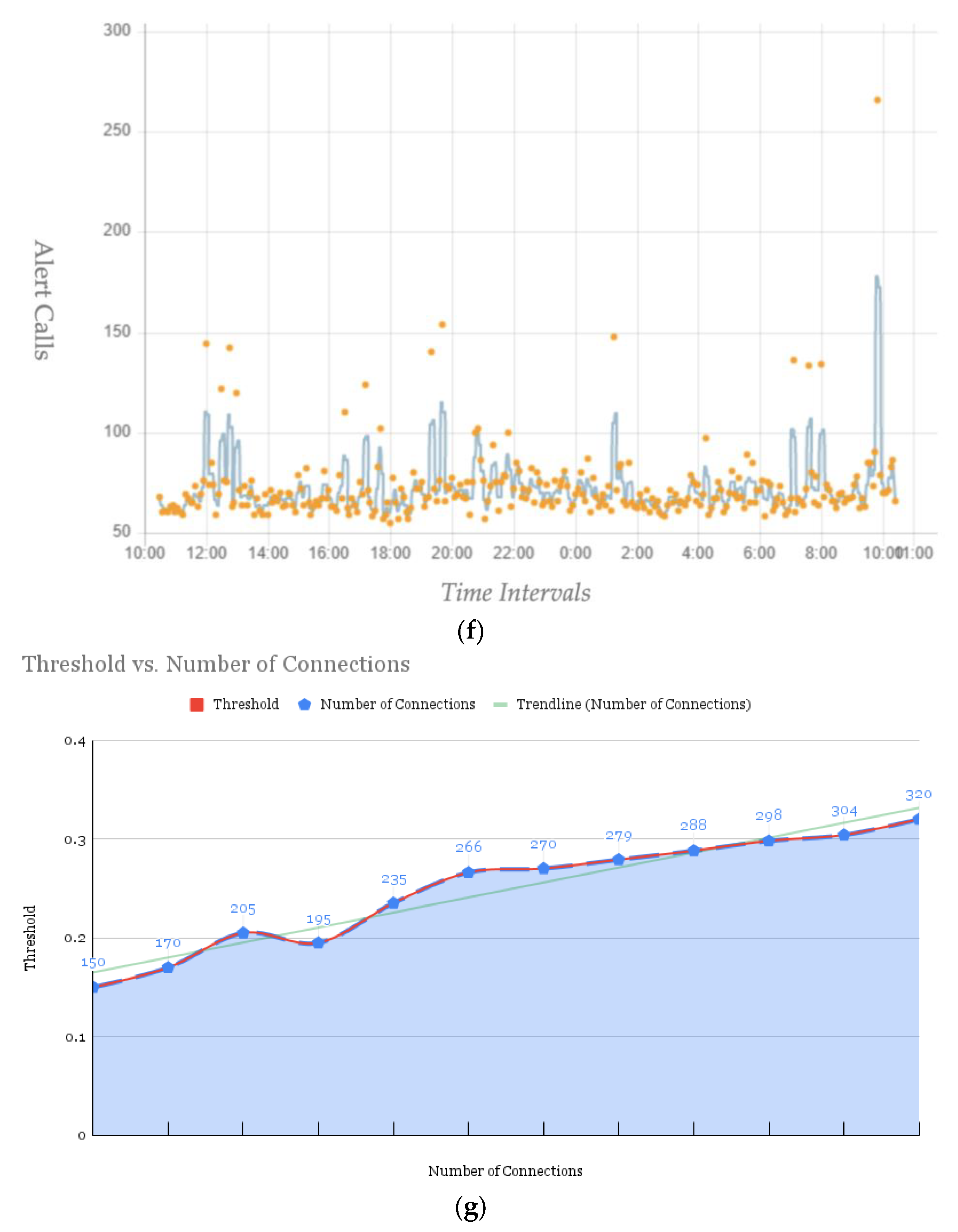
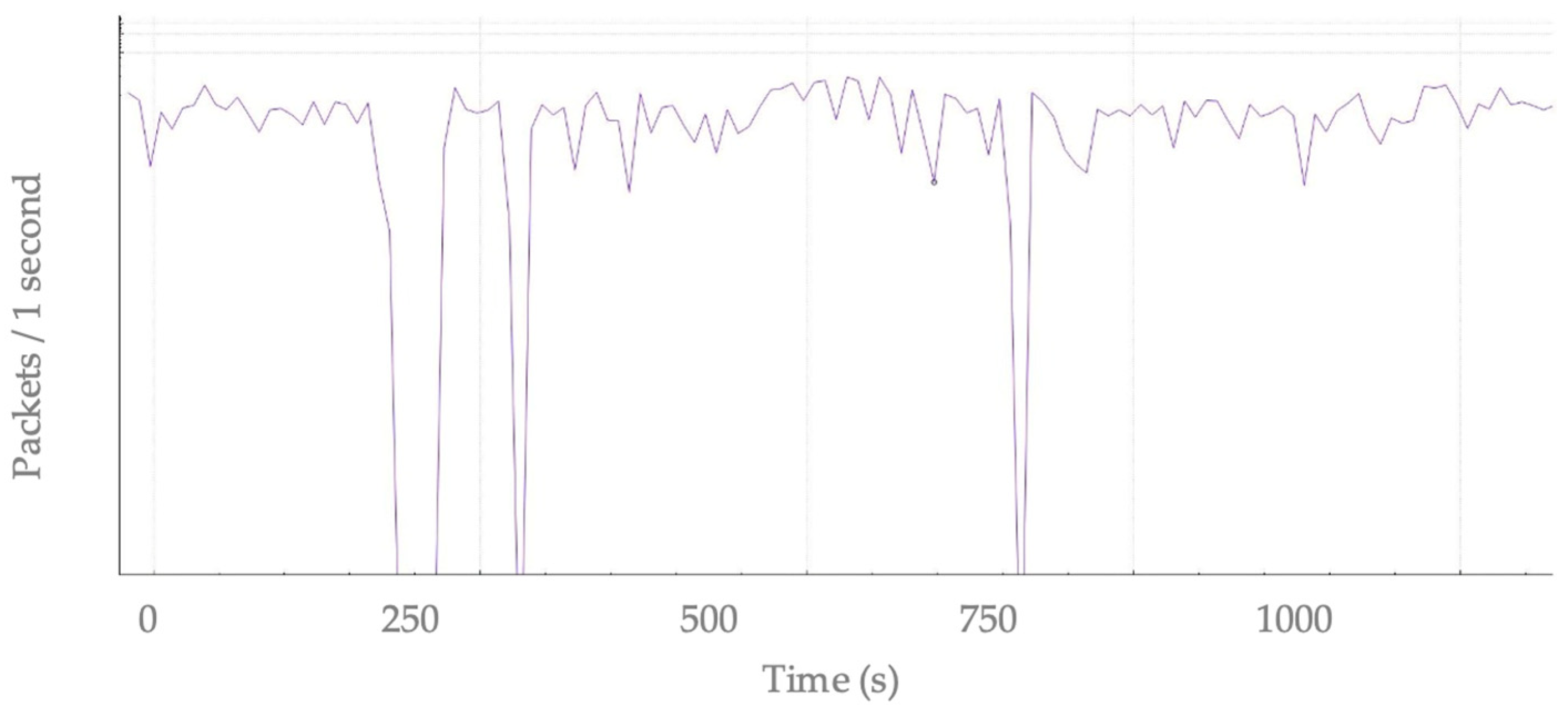
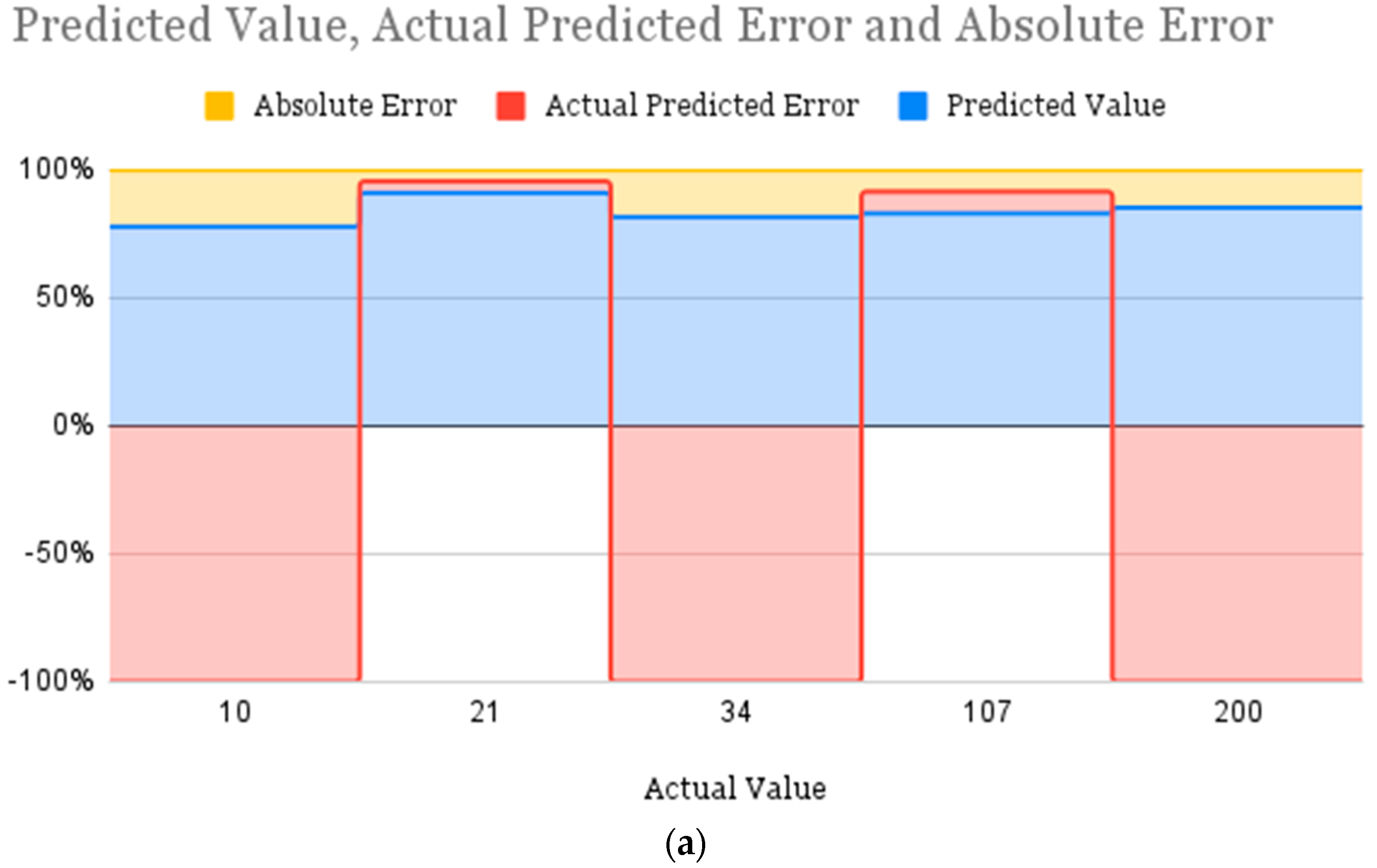
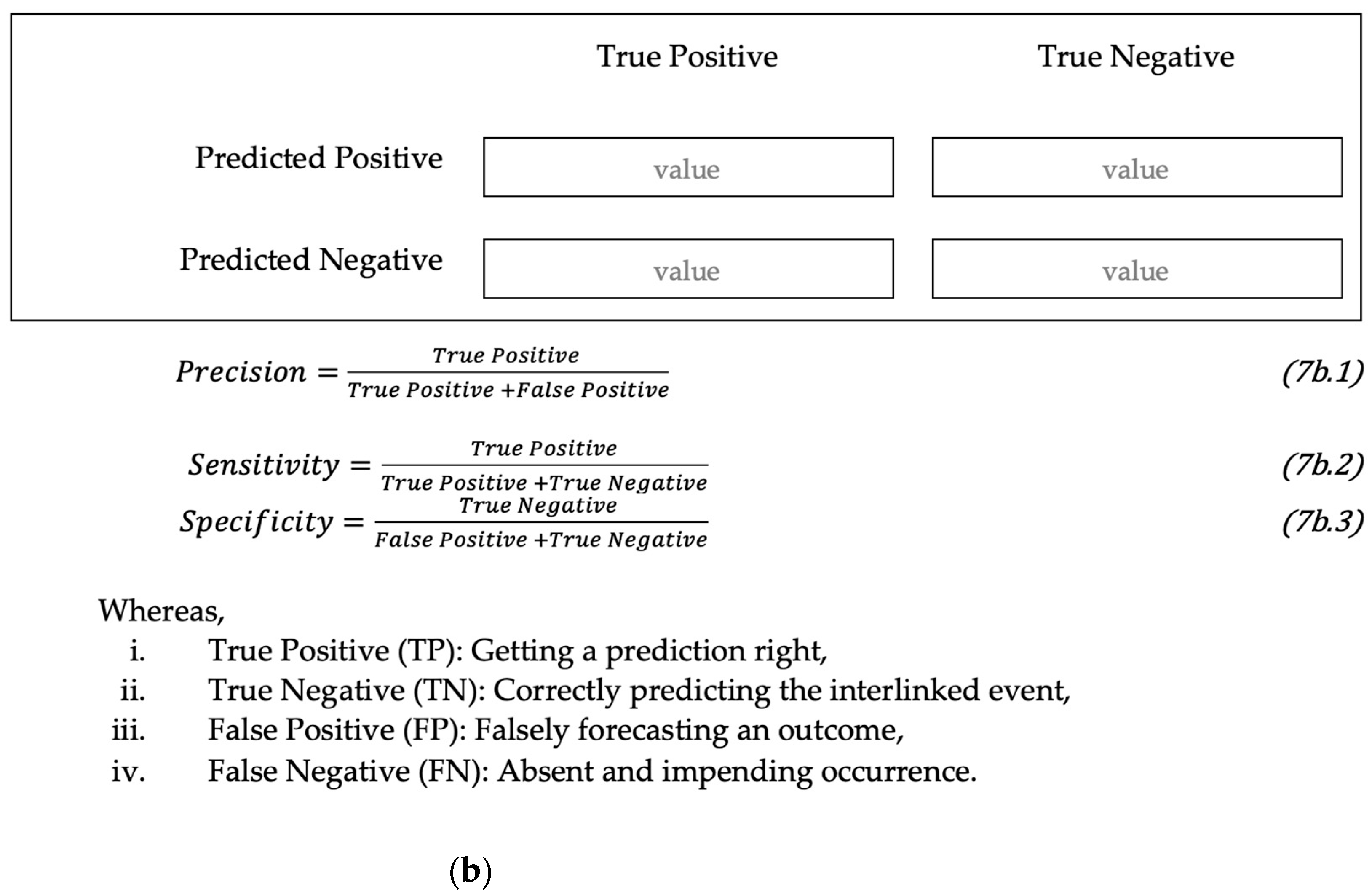
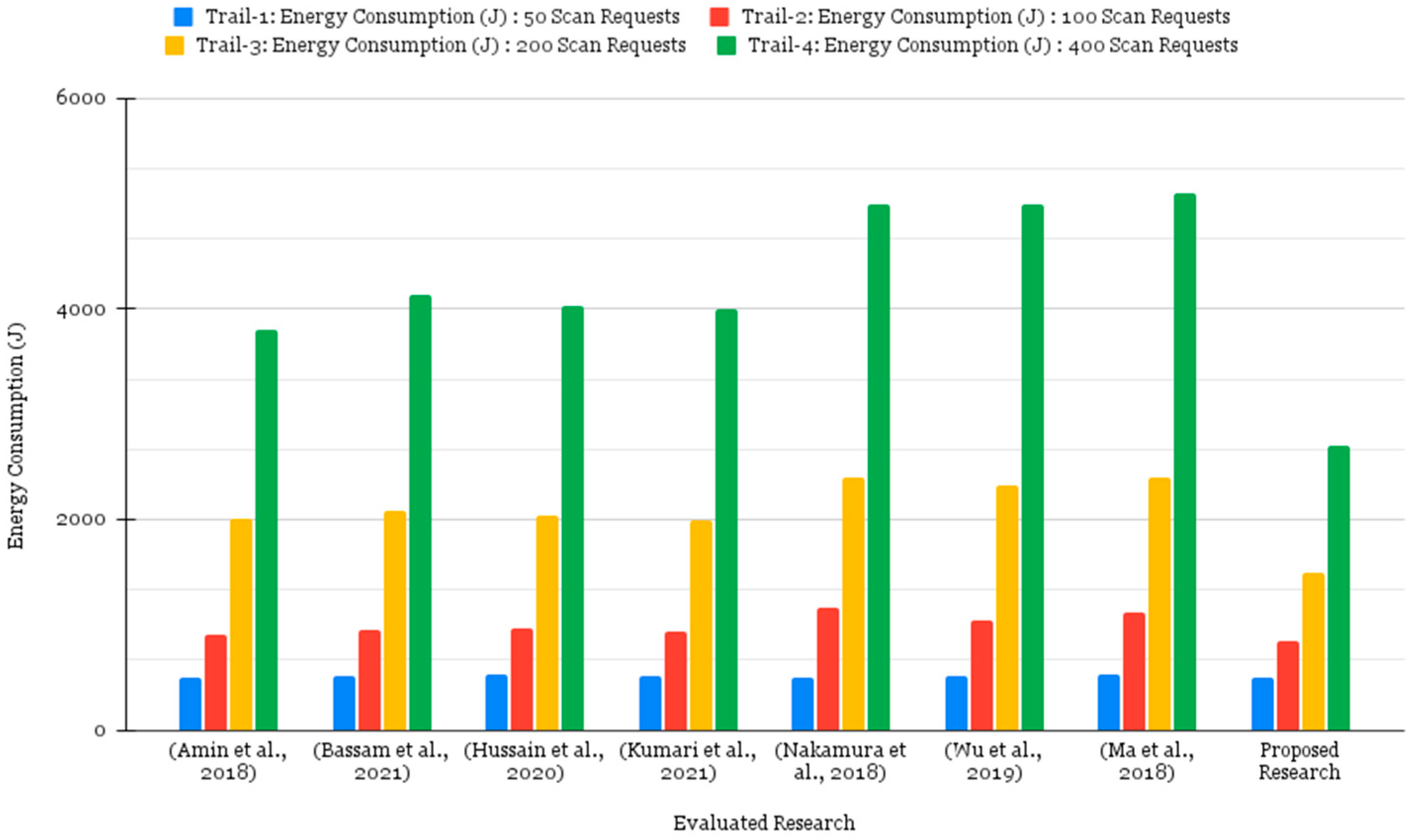
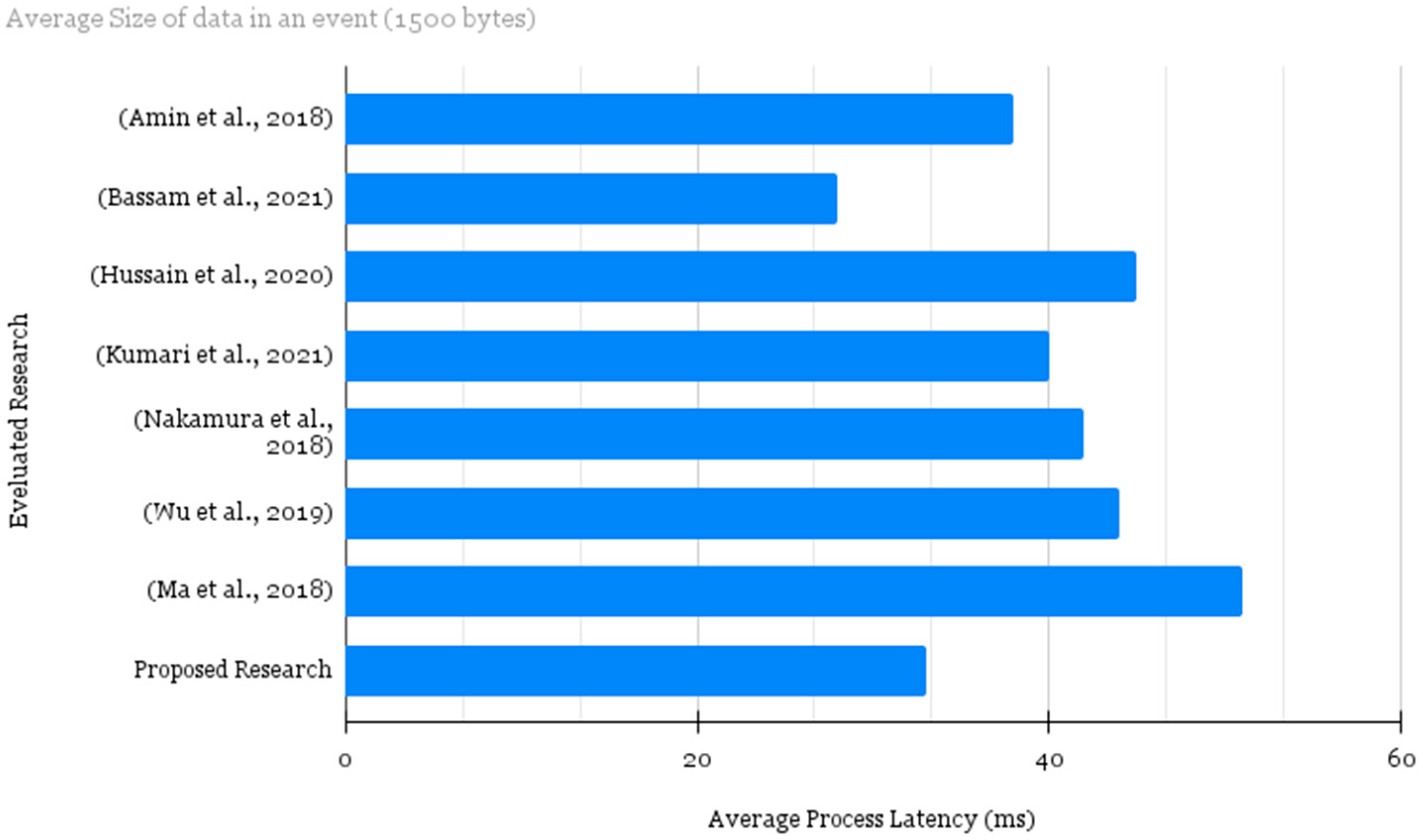
5. Performance Evaluation
- (a)
- Examining assets for potential security flaws.
- (b)
- Ranking the severity of the risks associated with these vulnerabilities.
- (c)
- Fixing security flaws through applying patches, managing configurations, or setting up workarounds.
- (a)
- locate underutilized resources and connections.
- (b)
- reduce the complexity of prioritizing devices and connecting them.
- (c)
- better data management by transferring useful data to the network’s periphery.
- (d)
- improve the efficiency of a network system.
- (e)
- introduce new application potential,
Device-Oriented Commendations
- (a)
- Periodically, verify the ‘clock-sync’ to sustain serial communication paradigm.
- (b)
- All data stored and transmitted from devices must be encrypted to achieve the privacy requirement.
- (c)
- Remote execution of privileged instruction (i.e., read and write control registers which varies in Bit count from 8 bits to 16 bits) should verify the source credentials.
- (d)
- The eligible device must be capable of scanning the desired TCP port for device characteristics.
6. Conclusions
- (a)
- Protect communication no matter where the interconnected node is located,
- (b)
- Allow admission to distinct resources only on a per-session basis,
- (c)
- Manage the input of nodes to resources through a set of active rules,
- (d)
- Evaluate the security rating of all assets while assessing requests,
- (e)
- Sustain an uninterrupted cycle of permitting/rejecting access, scanning and weighing risks, adjusting, and constantly re-valuing trust in enduring communications, and
- (f)
- Accumulate information related to data and interconnected devices to autonomously improve network behavior.
Future Work
- (a)
- It is possible to investigate implementing Blockchain on the FPGA hardware itself.
- (b)
- The proposed approach is capable of being evaluated in relation to a variety of various cyberattacks.
- (c)
- Further optimization of the proposed system is possible by establishing limits for data exploration, monitoring, and discovery.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Amin, H.; Burkett, R. SAMIIT: Spiral attack model in IIoT mapping security alerts to attack life cycle phases. In Proceedings of the 5th International Symposium for ICS & SCADA Cyber Security Research, Hamburg, Germany, 29–30 August 2018; pp. 11–20. [Google Scholar]
- Bassam, Z.; Hussaini, A.; Ali-Gombe, A. IIoT-ARAS: IIoT/ICS Automated Risk Assessment System for Prediction and Prevention. In Proceedings of the Eleventh ACM Conference on Data and Application Security and Privacy, Virtual Event, 26–28 April 2021; pp. 305–307. [Google Scholar]
- Hussain, A.; Johnson, A.; Hill, R.; Lane, P.; Alsboui, T. Hardware-intrinsic multi-layer security: A new frontier for 5G ena-bled IIoT. Sensors 2020, 20, 1963. [Google Scholar]
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain-Based Massive Data Dissemination Handling in IIoT Environ-ment. IEEE Netw. 2021, 35, 318–325. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. Towards design and implementation of security and privacy framework for internet of medical things (iomt) by leveraging blockchain and ipfs technology. J. Supercomput. 2021, 77, 7916–7955. [Google Scholar] [CrossRef]
- Rahman, M.; Jahankhani, H. Security vulnerabilities in existing security mechanisms for IoMT and potential solutions for mitigating cyber-attacks. In Information Security Technologies for Controlling Pandemics; Springer: Cham, Switzerland, 2021; pp. 307–334. [Google Scholar]
- Du, R.; Zhen, L. Multiuser physical layer security mechanism in the wireless communication system of the IIOT. Comput. Secur. 2022, 113, 102559. [Google Scholar] [CrossRef]
- Goswami, P.; Mukherjee, A.; Maiti, M.; Tyagi, S.S.K.; Yang, L. A neural network based optimal resource allocation method for secure IIoT network. IEEE Internet Things J. 2021, 9, 2538–2544. [Google Scholar] [CrossRef]
- Xiong, H.; Wu, Y.; Jin, C.; Kumari, S. Efficient and privacy-preserving authentication protocol for heterogeneous systems in IIoT. IEEE Internet Things J. 2020, 7, 11713–11724. [Google Scholar] [CrossRef]
- Li, J.; Lyu, L.; Liu, X.; Zhang, X.; Lv, X. FLEAM: A federated learning empowered architecture to mitigate DDoS in industrial IoT. IEEE Trans. Ind. Inform. 2021, 18, 4059–4068. [Google Scholar] [CrossRef]
- Nguyen, T.A.; Min, D.; Choi, E.; Lee, J.W. Dependability and security quantification of an internet of medical things infrastructure based on cloud-fog-edge continuum for healthcare monitoring using hierarchical models. IEEE Internet Things J. 2021, 8, 15704–15748. [Google Scholar] [CrossRef]
- Echeverría, A.; Cevallos, C.; Ortiz-Garces, I.; Andrade, R.O. Cybersecurity model based on hardening for secure internet of things implementation. Appl. Sci. 2021, 11, 3260. [Google Scholar] [CrossRef]
- Kim, H.Y.; Xu, L.; Shi, W.; Suh, T. A secure and flexible FPGA-based blockchain system for the IIoT. Computer 2021, 54, 50–59. [Google Scholar] [CrossRef]
- Taheri, R.; Shojafar, M.; Alazab, M.; Tafazolli, R. Fed-IIoT: A Robust Federated Malware Detection Architecture in Industrial IoT. IEEE Trans. Ind. Inf. 2021, 17, 8442–8452. [Google Scholar] [CrossRef]
- Chia-Shin, Y.; Chen, S.; Li, I. Implementation of MQTT protocol based network architecture for smart factory. Proc. Inst. Mech. Eng. Part B J. Eng. Manuf. 2019, 235, 2132–2142. [Google Scholar]
- Cooper, D.; Santesson, S.; Farrell, S.; Boeyen, S.; Housley, R.; Polk, W. Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. [online] Request for Comments: 5280. Available online: https://datatracker.ietf.org/doc/html/rfc5280 (accessed on 24 April 2022).
- Tariq, U.; Aseeri, A.O.; Alkatheiri, M.S.; Zhuang, Y. Context-Aware Autonomous Security Assertion for Industrial IoT. IEEE Access 2020, 8, 191785–191794. [Google Scholar] [CrossRef]
- Buddhadeb, P.; Vijayakumar, V.; Pratihar, S.; Kumar, D.; Reddy, K.H.K.; Roy, D.S. A genetic algorithm based energy efficient group paging approach for IoT over 5G. J. Syst. Archit. 2021, 113, 1–8. [Google Scholar]
- Dimitrios-Georgios, A.; Harishankar, M.; Weber, M.; Tague, P. Zigator: Analyzing the security of zigbee-enabled smart homes. In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Abu Dhabi, United Arab Emirates, 8 July 2020; pp. 77–88. [Google Scholar]
- Xuxin, Z.; Liu, Y.; Zhang, Y. A Secure Clock Synchronization Scheme for Wireless Sensor Networks Against Malicious Attacks. J. Syst. Sci. Complex. 2021, 33, 1–14. [Google Scholar]
- Jinxin, L.; Kantarci, B.; Adams, C. Machine learning-driven intrusion detection for contiki-NG-based IoT networks exposed to NSL-KDD dataset. In Proceedings of the 2nd ACM Workshop on Wireless Security and Machine Learning, New York, NY, USA, 16 July 2020; pp. 25–30. [Google Scholar]
- El, M.S.; Fettach, M.; Tragha, A. High frequency implementation of cryptographic hash function Keccak-512 on FPGA devices. Int. J. Inf. Comput. Secur. 2018, 10, 361–373. [Google Scholar]
- Nakamura, E.T.; Ribeiro, S.L. A Privacy, Security, Safety, Resilience and Reliability Focused Risk Assessment Methodology for IIoT Systems Steps to Build and Use Secure IIoT Systems. In Proceedings of the Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4 June 2018; pp. 1–6. [Google Scholar]
- Wu, T.Y.; Chen, C.M.; Wang, K.H.; Wu JM, T. Security analysis and enhancement of a certificateless searchable public key encryption scheme for IIoT environments. IEEE Access 2019, 7, 49232–49239. [Google Scholar] [CrossRef]
- Ma, M.; He, D.; Kumar, N.; Choo, K.-K.R.; Chen, J. Certificateless searchable public key encryption scheme for industrial Internet of Things. IEEE Trans. Ind. Inf. 2018, 14, 759–767. [Google Scholar] [CrossRef]




| Method | Layer | Description | Focused Issues |
|---|---|---|---|
| Security and privacy framework [5] | Application | To deal with failure points, privacy and security issues, Interplanetary File System (IPFS) cluster nodes have been integrated into the consortium Blockchain environment. | A framework has been established to ensure safety and control of devices. Applied technique does not promise effectiveness for real-time application systems, specifically when system is dense due to large number of peers. |
| Mitigating cyberattacks [6] | Application and Network | Performance evaluation of cryptographic authentication protocols, and critical review of IoMT network security vulnerabilities. | Rahman et al. proposed a novel mechanism to evade the impact of DDoS, Jamming, Node-Injection and Node-Hijacking associated with healthcare devices. Proposed method did not emphasize post-attack device behavior and how to subtract insecure code from victim nodes. |
| Multiuser physical layer authentication [7] | Physical | SVM-PO based self-directed parameter optimization to find out the best channel matrix aspect. | Du et al. demonstrated the security authentication mechanism using matrix channel estimation. Presented method did not discuss the perseverance of deployment and node location factor, as location identification can be a vital factor to authenticate egress and ingress nodes. |
| Optimal Resource Allocation [8] | Application and Network | Ensuring the channel security and applying convolutional neural network (CNN) to guarantee optimal channel state. | Goswami et al. simulated a novel technique to diminish the loss of network resources and identify data-driven vulnerabilities. Allocating resources proved its usefulness to balance the load and improve system performance. Unfortunately, proposed method lays the emphasis on QoS (quality of service) relevant to network communication and did not effectively consider energy consumption as a considerable data point during resource allocation. |
| Security Attributes | Xiong et al. [9] | Li et al. [10] | Nguyen et al. [11] | Echeverría et al. [12] | Kim et al. [13] |
|---|---|---|---|---|---|
| Dynamic authentication | Yes | No | Yes | No | No |
| Anonymity | No | No | No | No | No |
| Strong encryption | Yes | No | No | Yes | Yes |
| Forward secrecy | Yes | Yes | No | No | |
| Autonomous mechanism | No | No | Yes | Yes | No |
| Secure mutual user/device authentication | Yes | No | Yes | No | No |
| Secure user/device registration | No | No | Yes | No | Yes |
| Device impersonation attacks | No | Yes | Yes | No | No |
| DDoS attacks | No | Yes | No | Yes | No |
| Stolen device verify attacks | No | No | Yes | No | No |
| Wormhole attack | No | Yes | No | No | No |
| Node malfunction attacks | No | No | No | No | No |
| DID | Interface Name | IP Address | Interface Type | DAPM | VLAN Identifier | SCAs |
|---|---|---|---|---|---|---|
| 1 | Android | 10.0.13.2 | Dynamic | Disabled | 13 | Timing attack, Electromagnetic attack, Simple and Differential power analysis |
| 2 | Dynamic | 10.0.12.2 | Dynamic | Disabled | 12 | |
| 3 | Management | 10.0.11.2 | Static | Enabled | 11 | |
| 4 | Ubuntu | 10.0.10.2 | Dynamic | Disabled | 10 |
| To Network and Devices | Physical Layer | Sensing Edge/Boundary | Internal Network | Host | Applied Application | Information |
|---|---|---|---|---|---|---|
| Controlling physical admittance | ✓ | ◯ | ◯ | ◯ | ◯ | ✕ |
| Restricting logical access | ✕ | ✓ | ✓ | ◯ | ◯ | ◯ |
| Reinforcement | ✓ | ◯ | ✓ | ✓ | ◯ | ◯ |
| Defending undesirable alteration of data | ✓ | ◯ | ◯ | ✓ | ✓ | ✓ |
| Observing applied protocols | ✕ | ✓ | ✓ | ✓ | ✓ | ✕ |
| Product | Specification |
|---|---|
| ×86 Computers | Long-lasting industrial standardized computing equipment. |
| ZigBee Router (RM-23BZBSR) | Transmits supervision signal for application to augment routing consistency. |
| Magnum 10RX Router | 16× GbE, 10× WAN, 32× Serial |
| Operating System | Moxa Industrial Linux |
| Enterprise data Storage | PowerVault ME4012 (2.2 GHz, 2-core) with maximum capacity of 3 PB |
| Network Type | Heterogeneous |
| Surveillance Type | SCADA |
| Sensors | NCD IoT Cycle Counter Transmitters, Pressure Sensor Transmitters, Activity Sensor Transmitters |
| Packet Analyzer | Wireshark |
| Connection-oriented protocol | TCP |
| Data Acquisition Protocol | MQTT (Message Queuing Telemetry Transport) |
| Data Broadcast Protocol | DDS (Data Distribution Service) |
| Average Packet Length | 1500 bytes |
| Data Outcome Format | PCAP file |
| Total Number of Samples | 200,000 samples |
| Evaluated Attack Types | Remote Code Execution. Nmap Scanning, Command Injection, Man-in-the-middle attack (MITM), DoS (denial of service), Malicious Latency Protocol, Legacy Protocols, and Cryptojacking. |
| Solution Type | Method Used | Consequences Claimed | Research Gap | |
|---|---|---|---|---|
| Nakamura et al. [23] | Risk Assessment (accidental, malicious, natural) | Confidentiality, resilience, influence assessment and trustworthiness representing incidents in IIoT | Comparatively efficient | Administration and execution enrichment is compulsory |
| Wu et al. [24] | Enhancement in SCF-MCLPEKS scheme | Searchable public key encryption | Latency free retrieval of encrypted data | Inadequate to device level security |
| Ma et al. [25] | SCF-MCLPEKS | Bilinear Pairing | Diminished process computation time, and communication cost | Application focused and limited to anomaly type |
| Amin et al. [1] | SAMIIT: adversarial tactics, techniques, and common knowledge | Machine learning focused anomaly classified IDS | Mapping alerts to attack segments | Improvement for real-time application with inadequate to device level security |
| Bassam et al. [2] | Risk assessment system, clustering technique | Intrusion detection system | Discovered several risks caused by the IT/OT (information technology (IT) systems with operational technology (OT) systems) union | Processing delay with extraordinary computational cost |
| Hussain et al. [3] | Multi-Layer security | FPGA and PUF-based system security | Satisfactory security framework with high computational capabilities and flexible architectures | Behavior configurations can be considered to make proposed scheme less exposed to anomalies |
| Kumari et al. [4] | QoS aware secure Peer-to-Peer network | Blockchain-based protected distributed model | Enhanced data load balancing with reduced communication delay | Processing delay, application centric protocol security gaps should be addressed (i.e., accuracy, detection, mitigation, etc.) |
| Proposed Scheme | Detection and Moderation | Automated authentication, profiling. DoS for malicious node, and policy management | Secured network transmission, reduced computational cost, diminished energy consumption | Performance augmentation is vital |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tariq, U. Zero-Tolerance Security Paradigm for Enterprise-Specific Industrial Internet of Things. Electronics 2022, 11, 3953. https://doi.org/10.3390/electronics11233953
Tariq U. Zero-Tolerance Security Paradigm for Enterprise-Specific Industrial Internet of Things. Electronics. 2022; 11(23):3953. https://doi.org/10.3390/electronics11233953
Chicago/Turabian StyleTariq, Usman. 2022. "Zero-Tolerance Security Paradigm for Enterprise-Specific Industrial Internet of Things" Electronics 11, no. 23: 3953. https://doi.org/10.3390/electronics11233953
APA StyleTariq, U. (2022). Zero-Tolerance Security Paradigm for Enterprise-Specific Industrial Internet of Things. Electronics, 11(23), 3953. https://doi.org/10.3390/electronics11233953







