Abstract
With the continuous increase in the proportion of wind power construction and grid connection, the deployment scale of state sensors in wind-power-monitoring systems has grown rapidly with an aim on the problems that the communication authentication process between the wind turbine status sensor and the monitoring gateway is complex and the adaptability of the massive sensors is insufficient. A security access control method for a wind-power-monitoring system based on agile authentication mechanism is proposed in this paper. First, a lightweight key generation algorithm based on one-way hash function is designed. The algorithm realizes fixed-length compression and encryption of measurement data of any length. Under the condition of ensuring security, the calculation and communication cost in the later stage of authentication are effectively reduced. Second, to reduce the redundant process of wind turbine status sensor authentication, an agile authentication model of wind turbine status sensor based on a lightweight key is constructed. Constrained by the reverse order extraction of key information in the lightweight keychain, the model can realize lightweight communication between massive wind turbine status sensors and regional gateways. Finally, the proposed method is compared and verified using the wind turbine detection data set provided by the National New Energy Laboratory of the United States. The experimental results show that this method can effectively reduce the certification cost of a wind-power-monitoring system. Additionally, it can improve the efficiency of status sensor identity authentication and realize the agility and efficiency of the authentication process.
1. Introduction
In China, the ninth meeting of the Central Financial and Economic Commission emphasized that carbon peaking and carbon neutrality should be incorporated into the overall layout of an ecological civilization construction. It advocated for a simple, moderate, green, and low-carbon lifestyle and for building a new power system with new energy as the main body [,]. Among them, wind power as a safe, sustainable, and clean form of new energy, has seen a sharp increase in installed capacity and grid-connected ratio in the past two years. To ensure the safe and stable operation of wind turbines, wind-power-monitoring systems are widely deployed in wind farms []. It collects operating information in real time through the wind turbine state sensor (WTSS) and transmits it to the monitoring center remotely through the gateway (GW). Figure 1 shows the information collection and communication process.
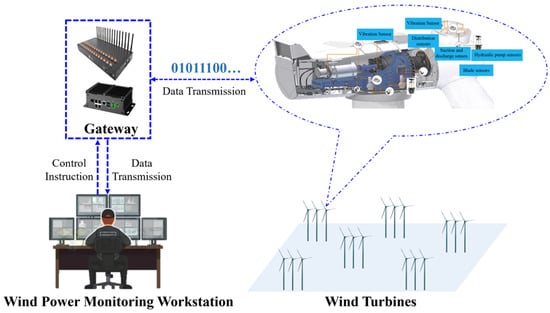
Figure 1.
The information transfer process of wind turbine status sensor authentication.
The fine-grained operating data of wind turbines are acquired in real time through state sensors, which contain a wealth of wind turbine state parameters []. If there are attack problems, such as data leakage and tampering, it will have a serious impact on the security of power generation and then affect the system operation in the grid-connected area []. Therefore, the safe communication of the wind-power-monitoring system is the safe basis for the operation analysis and precise control of the wind turbine. The wind turbine status sensor authentication is the primary condition for realizing data security communication. However, with the rapid growth of wind power grid-connected ratio and installed capacity, secure, agile, and efficient identity authentication for the status sensors of massive wind turbines has become a bottleneck restricting communication security []. It is of great theoretical and engineering significance to study the agile authentication method of wind turbine status sensor identity based on lightweight keys [].
To improve the certification efficiency and meet the requirements of lightweight certification of wind turbine status sensors, most scholars worldwide have started to use lightweight encryption algorithms for lightweight access authentication of computing-constrained devices, such as wind turbine status sensors [,]. For example, elliptic curve cryptography (ECC) is one of the typical lightweight encryption algorithms []. It can achieve the same level of security as other encryption algorithms with shorter keys. Due to its above-mentioned characteristics, ECC has been widely used in the authentication process of computing-constrained devices in recent years. Wu et al. [] designed a lightweight authentication protocol based on ECC, which provides functions, such as anonymity and privacy protection, and does not require a trusted third party to intervene in the online authentication process to reduce overhead. However, Wang et al. [] noticed the protocol in the above-mentioned document cannot resist private key leakage attacks and cannot provide a perfect forward secrecy problem. Qi et al. [] designed two authentication protocols for the problem of efficiently degrading the computing overhead. However, Gope et al. [] noticed the conventions in Qi et al. [] have security loopholes and cannot resist man-in-the-middle attacks and replay attacks. In addition to wind turbine status sensors, the ECC algorithm is also applicable to other computing-constrained devices, according to Wan et al. []. In Hammi et al. [], a lightweight authentication method based on ECC and one-time pad was proposed for the application of RFID tags in IoT devices. Jangirala et al. [,] used the ECC algorithm to improve the lightweight RFID authentication protocol. Alladi et al. [] presented an ECC-based mutual authentication method that can be applied to embedded devices and cloud servers. In addition to elliptic curve cryptography, some scholars also use physical unclonable function (PUF) to complete verification. PUF is a hardware-based verification method using digital circuits [,]. Liang et al. [] solved the key storage problem by applying deep learning technology to APUF. Aghapour et al. [] presented a broadcast authentication scheme named PUF-BA, which can ensure security during authentication, but the computational cost is high. On this basis, Farha et al. [] presented some improvement schemes using the BCH coding algorithm to correct the errors so the PUF response becomes reliable, and the computational overhead is successfully reduced.
To sum up, existing research has conducted in-depth discussions on wind turbine status sensor authentication. However, there are still problems that the authentication algorithm calculation is time-consuming, and the authentication process is too complicated. To solve the above problems, the security access control method for a wind-power-monitoring system based on agile authentication mechanism is proposed in this paper. This method can effectively reduce the computational cost and authentication process complexity of wind turbine status sensor authentication. The wind turbine status sensor authentication method is analyzed in terms of computational overhead, communication cost, and security. The results show the proposed method has obvious advantages in terms of the computational cost and authentication speed compared with authentication schemes, such as Paillier encryption, identity-based encryption, and other authentication schemes.
The main contributions of this paper are as follows:
- A lightweight key generation algorithm based on one-way hash function is proposed to solve the problem of high computational cost of wind turbine status sensor authentication. The algorithm achieves fixed-length compressed encryption of arbitrary length measurement data. It effectively reduces the computational overhead and communication cost of authentication.
- To reduce the complexity of the authentication process between the wind turbine status sensor terminal and the central gateway, an agile authentication model for wind turbine status sensors with a lightweight key chain is constructed. The model achieves online agile authentication of wind turbine status sensor identities by extracting key information in lightweight key chains in reverse order.
- The proposed method has been successfully certified, and the results obtained have been compared with the existing methods. The results show the superior performance of the proposed method. It provides a low-overhead and highly agile method for secure authentication of wind turbine status sensor.
This paper is organized as follows. Section 2 provides an analysis of the agile authentication requirements for wind turbine status sensors. The specific process of agile authentication based on lightweight key is described in detail in Section 3. Section 4 presents the experimental computational overhead of the method as well as the authentication results and security performance analysis. Finally, conclusions and future recommendations are contained in Section 5.
2. Demand Analysis for Agile Authentication of Wind Turbine Status Sensor
During the communication process of the wind power monitoring system, the wind turbine status sensor periodically transmits the collected data to the regional gateway. Due to the privacy of the transmitted data, this part of the data may carry sensitive wind turbine state parameters and sensor identities. Additionally, with the widespread deployment of the smart grid, many problems may arise that threaten the availability of the smart grid []. For example, when network attackers set it to listen to the communication link, intercept information, attempt to crack, etc. [,], the attacker can obtain the identity information in the wind turbine status sensor and the regional gateway and then enter the subsequent data transmission stage. Finally, the attacker can maliciously break the authentication process and disrupt the normal operation of the system [].
Through the analysis of the authentication process of wind turbine status sensor, the demand analysis is proposed to measure the degree of network attack suffered during the authentication process. As shown in Figure 2, it can be divided into three levels: security, agile, and overhead. The specific target requirements are as follows:
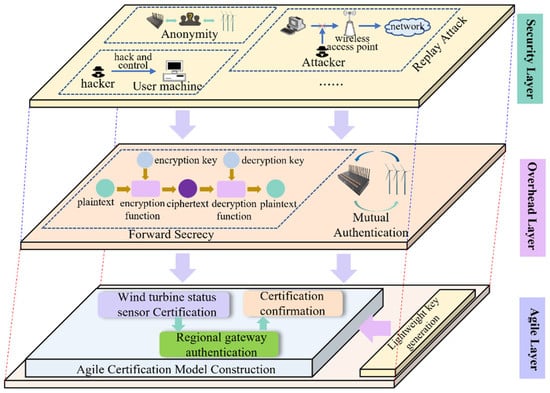
Figure 2.
The demand analysis of wind turbine status sensor agile authentication.
Anonymity: The authentication information of the wind turbine status sensor and the regional gateway is an important basis for mutual authentication. Once the authentication is exposed, the attacker can forge the authentication. Therefore, the proposed method should ensure the security of the authentication information of both parties during authentication.
Uniqueness: Since both the wind turbine status sensor and the regional gateway are at risk of being forged by attackers, it is necessary to confirm the authentication to ensure the uniqueness of the authentication.
Anti-attack: Considering the attacker can intercept the messages sent by the authenticating parties or modify and inject their own messages into the communication, it is necessary to fully consider the possible attack methods that attackers may take after obtaining information, such as simulation attacks, message modification attacks, and replay attacks, and be able to defend against them.
Confidentiality: For asymmetric encryption algorithms, the security of the private key is very important. If using the same private key for a long time, it may be obtained by an attacker through brute force cracking. Therefore, the proposed method should provide complete forward secrecy.
Agility: On the basis of ensuring the security of wind turbine status sensor certification, the certification process is simplified, and the total certification time is short. When the authentication process encounters changes, such as attacks, errors, and omissions, it can respond flexibly and delicately.
3. Wind Turbine Status Sensor Agile Authentication Based on Lightweight Key Operation
To avoid potential power security risks, such as data privacy leakage [], network attack, and information interception [,], traditional wind turbine state sensor authentication schemes mostly use exponential or bilinear paired high-overhead operations. However, when a large number of wind turbine state sensors are connected to the monitoring system, the authentication frequency of state sensors and regional gateways increases significantly. The calculation and communication costs of traditional authentication methods have increased, and the lack of authentication efficiency has become a new shortcoming. This will lead to higher computational and communication costs for the two-way authentication process, making the high-overhead encryption algorithm decadent in terms of authentication efficiency [].
Based on the above problems, this paper proposes a security access control method for a wind-power-monitoring system based on an agile authentication mechanism. In the key generation stage, based on the one-way and anti-collision of the one-way hash function, the method can ensure the public and verifiable constraint ability of the metering data content of the status sensor. It also enables fixed-length compression and encryption of measurement data of any length. In the identity authentication stage, an agile authentication model of wind turbine status sensor based on lightweight key is constructed. Based on reverse extraction of key information in lightweight key chains, this model enables lightweight communication between large-scale wind turbine status sensors and regional gateways.
3.1. Lightweight Key Generation Algorithm Based on One-Way Hash Function
The complexity of the key and verification key determines the security and agility of wind turbine status sensors and gateway authentication. The one-way hash function calculation process is irreversible []. To meet the requirements of fast key generation and secure transmission, this paper uses a one-way hash function to generate keys and iteratively connects the keys to form a key chain. At this stage, it is mainly operated by calculation and storage capabilities than by the gateway of the wind turbine status sensor. The gateway is responsible for the generation and initialization of the hash key chain, wind turbine status sensor identity information, wind turbine status sensor secret parameters, and secret parameter series. The main process of lightweight key generation is shown in Figure 3.
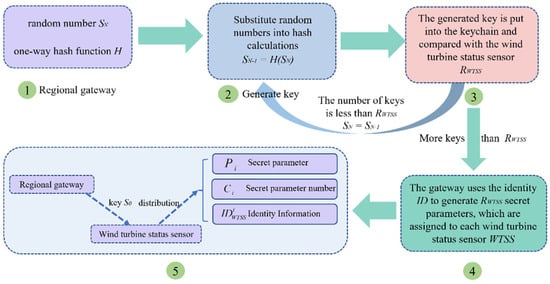
Figure 3.
Lightweight key generation process.
Step 1: Regional gateway selects a random number, , and a one-way hash function, .
Step 2: Calculate the variable or random number to calculate and generate key, , according to the Equation (1).
Step 3: Add to the key chain and determine whether the number of keys in the key chain is more than the number of wind turbine status sensors in the region. If the number of keys is greater than or equal to the number of wind turbine status sensors , execute Step 4; otherwise, it will be substituted into Step 2 and executed.
Step 4: The gateway uses to generate , random secret parameter, , and the secret parameter number, ; and are a one-to-one correspondence. Then, assign an identity information, , for each .
Step 5: sends the first key, , of the hash keychain to all in the area it is responsible for through a secure channel. Then, sends a secret parameter, , a secret parameter serial number, , and their own identity information, , to each separately.
3.2. The Agile Authentication Model of Wind Turbine Status Sensor Based on Lightweight Key
The agile authentication model based on the lightweight key of the wind turbine status sensor is mainly divided into three stages: the wind turbine status sensor authentication stage, the regional gateway authentication stage, and the authentication confirmation stage. The certification process of each stage is shown in Figure 4.
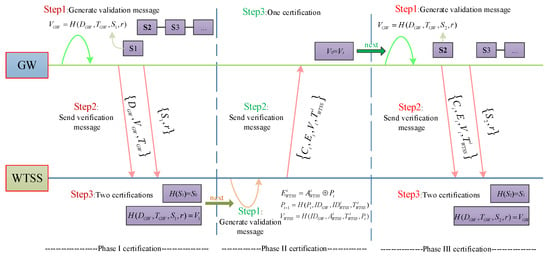
Figure 4.
Execution process of agile certification model.
It can be seen from Figure 4 that first authenticates , ensuring the information receiver is credible. At the same time, sends control information to and requests it to start authentication. Then, authenticates to ensure the sender of the information is credible. Finally, the authentication confirmation stage is to return the successful information of the authentication to and orders it to start transmitting data.
3.2.1. Wind Turbine Status Sensor Authentication Stage
Step 1: For the first verification, selects the smallest key, , in the key chain that he saved. At the same time, generates a random number, , and then uses Equation (2) to generate verification information, .
Among them, is the gateway control information; is the gateway timestamp.
Step 2: sends data and to all in the area. After the sending is completed, deletes in the system.
Step 3: After receiving and , calculates and judges whether the time interval is less than the time delay, . If the conditions are met, then calculates and judges whether is equal to and whether is equal to .
Step 4: If one of the two authentications of is not passed, the news will be discarded. If both authentications pass, then completes the authentication of . Finally, will be replaced by in and starts the authentication of the next stage.
3.2.2. Regional Gateway Authentication Stage
Step 1: For the following calculations on the , first calculate the confirmation information, , of the encryption based on the Equation (3).
where is the confirmation information of the ith wind turbine status sensor.
Then, calculate the new secret parameter according to Equation (4).
Finally, the verification information is calculated based on Equation (5).
Step 2: After completing the calculation, sends data to , while saving new secret parameters, , replacing the original, .
Step 3: finds the corresponding according to , and then calculates through Equation (6).
After obtaining , is also calculated based on Equation (5).
Step 4: If is equal to , verification passes. Next, calculates according to Equation (4), replaces the original , and the authentication is completed, and the next stage is verified. If the verification is not passed, will require to send the message again, and three more times, will feedback the error message.
3.2.3. Authentication Confirmation Stage
Step 1: selects the smallest serial, , in the saved key chain, and then generates a random number, , and uses Equation (2) to calculate .
Step 2: sends data and to all in the area. After the sending is completed, deletes in the system.
Step 3: After receiving data, and , judges whether is less than . If the conditions are met, then calculates and judges whether is equal to and whether is equal to .
Step 4: If one of the two authentications fails, the message is discarded and is required to resend the message. If both authentications are passed, the authentication is completed. After that, is replaced by . Finally, the command of the control command is executed, and data transmission starts.
4. Experimental Results and Analysis
To verify the effectiveness of the proposed method, this paper uses the wind turbine detection data set provided by the National New Energy Laboratory of the United States for experimental analysis []. Experiments were performed on Windows 10 Home Edition, AMD Ryzen 5 3500 U CPU with Radeon Vega Mobile Gfx 2.30 GHz, 12 G RAM machine.
4.1. Security Analysis
Security is the key issue for mutual authentication between wind turbine status sensors and regional gateways. This part shows the advantages of the method proposed in this paper from the comparative analysis of six security indicators: authentication and key agreement, device anonymity, forward secrecy, replay attack resistance, impersonation attack resistance, and private key disclosure masquerading attack resistance, as shown in Table 1.

Table 1.
Comparative analysis of identity authentication security between wind turbine status sensors and regional gateways.
As can be seen from Table 1, the proposed method increases the time verification operation compared with the Paillier encryption authentication scheme; thus, it provides the function of defending against replay attacks. Crucially, the proposed method does not use third-party management software so there is no problem of key leakage in advance. Moreover, the key chain generated by the single-item hash function is irreversible, which can better defend against key leakage camouflage attacks than other existing schemes.
4.2. Computational Cost Analysis
Computational overhead refers to the total computation time spent on the wind turbine status sensor side and the side during the authentication process. Computational overhead is an important indicator of model agility, and shorter computational elapsed time indicates more rapid and agile authentication of wind turbine status sensors. This part compares three typical wind turbine status sensor authentication methods: Paillier encryption (PE), identity-based encryption (IBE), and elliptic curve Qu–Vanstone (ECQV). The experiment tests the time of various calculations in the authentication process in the same environment, and the time-consuming result of the operation is as follows: Montgomery power module operation, , elliptic curve multiplication operation, , one-way hash function operation, , and elliptic point addition operation, , and XOR operation, , can be ignored. The comparison of the computational cost of each algorithm is shown in Figure 5.
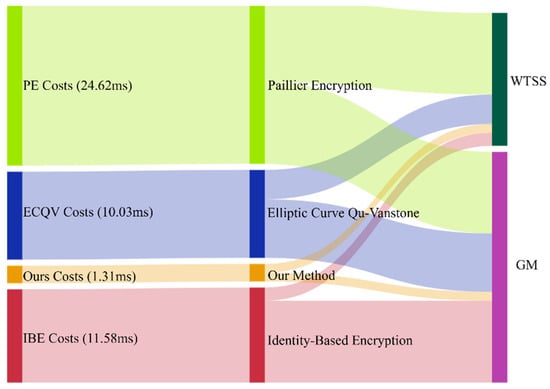
Figure 5.
Computational cost comparison.
According to the analysis of the calculation cost comparison result in Figure 5, the calculation cost in the Paillier encryption authentication scheme is relatively high. This is because the calculation needs to use the modular exponentiation multiple times. The calculation overhead of both the side and the side needs to use the fourth modular exponentiation operation. In the identity-based encryption authentication scheme, the main computational overhead is concentrated on the side. The method requires three multiplications and six hash operations in and only addition and hash operations in . Compared with the identity-based encryption authentication scheme, the calculation overhead of the elliptic curve Qu-Vanstone authentication scheme is reduced in , which only two elliptic curve addition operations and three elliptic curve multiplication operations are required. The method proposed in this paper uses one-way hash operation and XOR operation with low computational cost. Since the time-consuming one-way hash operation and XOR operation are much less than other schemes, the proposed method can effectively reduce the time loss in terms of side, side, and total computational overhead.
4.3. Communication Cost Analysis
The communication cost of the authentication process includes the number of bits of information transmitted for a complete successful authentication. Elliptic curve point information is 320 bits, the output length of the one-way hash function is 256 bits, the timestamp is 64 bits, the length of the control information and confirmation information is 128 bits, the length of the random number and the secret parameter serial number is 32 bits, the device identity information is 64 bits. The communication cost analysis of each method is performed according to the above-mentioned setting data, as shown in Figure 6A,B.
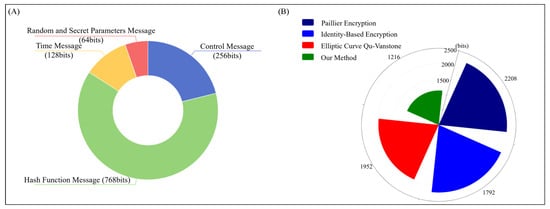
Figure 6.
(A) Components of communication. (B) Communication cost comparison.
The proposed method transmits information, including , , and . It can be seen from Figure 6A this information can be divided into four parts: one-way hash function information, control information, random number and secret parameter information, and timestamp. Its cost of communication is bits. Figure 6B shows the communication overhead of the four algorithms. The Paillier encryption authentication scheme has the highest communication cost. This is because it uses a large number of transport message authentication codes and additional information for authentication, resulting in a high total cost. The identity-based encryption authentication scheme abandons the transmission of additional information and timestamps and introduces hash keys to reduce communication costs. Elliptic curve Qu-Vanstone authentication scheme communication uses hash function and secret parameter information at the same time to increase security, resulting in a slight rise in communication cost. In general, the communication cost of the method proposed in this paper is significantly reduced.
4.4. Comprehensive Analysis
Comprehensive comparative analysis can intuitively watch the performance of the certification scheme in all aspects. This part compares and analyzes the pros and cons of each algorithm from the five comprehensive attributes of sensitivity, anonymity, confidentiality, security, and cost under different method models, as shown in Figure 7.
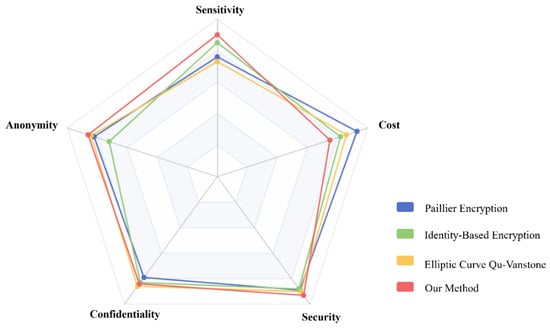
Figure 7.
Comprehensive attribute comparison.
The four colored polylines in Figure 7 represent four authentication scheme models. The closer each polyline point is to the attribute point, the better the performance of the authentication scheme model in this attribute. In terms of cost overhead, the farther away from the attribute point, the lower the cost overhead. As can be seen from Figure 7, the Paillier encryption authentication scheme has a higher cost than other authentication schemes. The identity-based encryption authentication scheme is obviously inferior to other authentication schemes in terms of anonymity. The elliptic curve Qu-Vanstone certification scheme is less sensitive. In the authentication scheme proposed in this paper, the comprehensive attributes have obvious advantages compared with other authentication schemes. Through the lightweight keychain gateway authentication based on one-way hash function and secret parameters, this authentication scheme is particularly outstanding in terms of sensitivity and cost overhead.
5. Conclusions
As the number of wind turbine status sensors continue to increase, the number of status sensors in the region and the authentication frequency between them and the central gateway increases significantly. The authentication efficiency of wind turbine status sensors using high-cost authentication algorithms decreases. How to improve the agility of authentication and shorten the authentication time on the basis of ensuring the security of wind turbine status sensor identity authentication has become an urgent problem that it faces. From the perspective of reducing cost and improving efficiency, this paper proposes a security access control method for a wind-power-monitoring system based on an agile authentication mechanism. The experimental results verified the following main conclusions:
- The proposed lightweight key generation algorithm based on one-way hash function can improve the security of wind turbine status sensor and gateway authentication and realize the forward secrecy of the authentication process. In particular, lightweight keys effectively reduce the computational cost required for authentication.
- The constructed wind turbine status sensor agile authentication method based on the lightweight key chain can quickly authenticate the status sensor, and the authentication complexity is significantly reduced. The communication cost of the proposed method is 44.9% and 32.1% lower than that of the Paillier encryption and identity-based encryption authentication schemes, respectively.
- Comprehensive experimental analysis results show this method ensures the safe operation of certification. It also significantly improves the agility of the certification process by coordinating the security and rapid response requirements of certification.
In addition, we will try to improve the time consumption of reinitialization of the one-way hash key chain and further improve the agility of wind turbine status sensor authentication. In future research, trusted key management technology can be introduced to develop a more manageable agile authentication model. The issue of security during data transfer is also worth discussing. With the continuous advancement of new power systems, it is also an interesting issue to study the implementation of agile certification models for energy management systems.
Author Contributions
Conceptualization, Y.S. and Q.Y.; methodology, Y.S.; software, W.K.; validation, L.K.; formal analysis, Y.S.; investigation, Q.Y.; resources, Y.S.; data curation, W.K.; writing—original draft preparation, L.K.; writing—review and editing, Y.S.; visualization, Q.Y.; supervision, Y.S.; project administration, W.K.; funding acquisition, L.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Basic Research (T01) Project of Shenzhen Science and Innovation Commission (no. JCYJ20180307124010740); the Science and Technology Development Program of Jilin Province (no. 20191001040XH); the Science and Technology Projects of Jilin Province Department of Education (no. JJKH20191262KJ, JJKH20191258KJ).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript; or in the decision to publish the results.
References
- Vargas, S.A.; Esteves, G.R.T.; Maçaira, P.M.; Bastos, B.Q.; Oliveira, F.L.C.; Souza, R.C. Wind power generation: A review and a research agenda. J. Clean. Prod. 2019, 218, 850–870. [Google Scholar] [CrossRef]
- Dai, J.; Yang, X.; Wen, L. Development of wind power industry in China: A comprehensive assessment. Renew. Sustain. Energy Rev. 2018, 97, 156–164. [Google Scholar] [CrossRef]
- Zhao, X.; Wang, C.; Su, J.; Wang, J. Research and application based on the swarm intelligence algorithm and artificial intelligence for wind farm decision system. Renew. Energy 2019, 134, 681–697. [Google Scholar] [CrossRef]
- Kou, L.; Li, Y.; Zhang, F.; Gong, X.; Hu, Y.; Yuan, Q.; Ke, W. Review on Monitoring, Operation and Maintenance of Smart Offshore Wind Farms. Sensors 2022, 22, 2822. [Google Scholar] [CrossRef] [PubMed]
- Demolli, H.; Dokuz, A.S.; Ecemis, A.; Gokcek, M. Wind power forecasting based on daily wind speed data using machine learning algorithms. Energy Convers. Manag. 2019, 198, 111823. [Google Scholar] [CrossRef]
- Zhu, L.; Li, M.; Zhang, Z.; Xu, C.; Zhang, R.; Du, X.; Guizani, N. Privacy-preserving authentication and data aggregation for fog-based smart grid. IEEE Commun. Mag. 2019, 57, 80–85. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, Q.; Hong, T.; Kang, C. Review of smart meter data analytics: Applications, methodologies, and challenges. IEEE Trans. Smart Grid 2018, 10, 3125–3148. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, L.; Yin, S.; Chi, C.H.; Liu, R.; Zhang, Y. A lightweight authentication scheme with privacy protection for smart grid communications. Future Gener. Comput. Syst. 2019, 100, 770–778. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Sain, M.; Martin, A.; Ha, P.H. Lightweight authentication and key agreement for smart metering in smart energy networks. IEEE Trans. Smart Grid 2018, 10, 4349–4359. [Google Scholar] [CrossRef]
- Sowjanya, K.; Dasgupta, M.; Ray, S.; Obaidat, M.S. An efficient elliptic curve cryptography-based without pairing KPABE for Internet of Things. IEEE Syst. J. 2019, 14, 2154–2163. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Li, X.; Kumari, S.; Karuppiah, M.; Obaidat, M.S. A lightweight and provably secure key agreement system for a smart grid with elliptic curve cryptography. IEEE Syst. J. 2018, 13, 2830–2838. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Choo, K.K.R.; He, D. Blockchain-based anonymous authentication with key management for smart grid edge computing infrastructure. IEEE Trans. Ind. Inform. 2019, 16, 1984–1992. [Google Scholar] [CrossRef]
- Qi, M.; Chen, J. Two-pass privacy preserving authenticated key agreement scheme for smart grid. IEEE Syst. J. 2020, 15, 3201–3207. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. A privacy-aware reconfigurable authenticated key exchange scheme for secure communication in smart grids. IEEE Trans. Smart Grid 2021, 12, 5335–5348. [Google Scholar] [CrossRef]
- Wan, J.; Li, J.; Imran, M.; Li, D. A blockchain-based solution for enhancing security and privacy in smart factory. IEEE Trans. Ind. Inform. 2019, 15, 3652–3660. [Google Scholar] [CrossRef]
- Hammi, B.; Fayad, A.; Khatoun, R.; Zeadally, S.; Begriche, Y. A lightweight ECC-based authentication scheme for Internet of Things (IoT). IEEE Syst. J. 2020, 14, 3440–3450. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Vasilakos, A.V. Designing secure lightweight blockchain-enabled RFID-based authentication protocol for supply chains in 5G mobile edge computing environment. IEEE Trans. Ind. Inform. 2019, 16, 7081–7093. [Google Scholar] [CrossRef]
- Aghili, S.F.; Mala, H.; Kaliyar, P.; Conti, M. SecLAP: Secure and lightweight RFID authentication protocol for Medical IoT. Future Gener. Comput. Syst. 2019, 101, 621–634. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V. HARCI: A two-way authentication protocol for three entity healthcare IoT networks. IEEE J. Sel. Areas Commun. 2020, 39, 361–369. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Long, J.; Li, K.C.; Zhang, D.; Li, K. A double PUF-based RFID identity authentication protocol in service-centric internet of things environments. Inf. Sci. 2019, 503, 129–147. [Google Scholar] [CrossRef]
- Wang, W.; Chen, Q.; Yin, Z.; Srivastava, G.; Gadekallu, T.R.; Alsolami, F.; Su, C. Blockchain and PUF-based lightweight authentication protocol for wireless medical sensor networks. IEEE Internet Things J. 2021, 9, 8883–8891. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Zhang, D.; Li, X.; Li, K.C. A mutual security authentication method for RFID-PUF circuit based on deep learning. ACM Trans. Internet Technol. (TOIT) 2021, 22, 1–20. [Google Scholar] [CrossRef]
- Aghapour, S.; Kaveh, M.; Martín, D.; Mosavi, M.R. An ultra-lightweight and provably secure broadcast authentication protocol for smart grid communications. IEEE Access 2020, 8, 125477–125487. [Google Scholar] [CrossRef]
- Farha, F.; Ning, H.; Ali, K.; Chen, L.; Nugent, C. SRAM-PUF-based entities authentication scheme for resource-constrained IoT devices. IEEE Internet Things J. 2020, 8, 5904–5913. [Google Scholar] [CrossRef]
- Wang, W.; Huang, H.; Zhang, L.; Su, C. Secure and efficient mutual authentication protocol for smart grid under blockchain. Peer-to-Peer Netw. Appl. 2021, 14, 2681–2693. [Google Scholar] [CrossRef]
- Abbasinezhad-Mood, D.; Ostad-Sharif, A.; Nikooghadam, M.; Mazinani, S.M. A secure and efficient key establishment scheme for communications of smart meters and service providers in smart grid. IEEE Trans. Ind. Inform. 2019, 16, 1495–1502. [Google Scholar] [CrossRef]
- Qu, Z.; Zhang, Z.; Liu, S.; Cao, J.; Bo, X. Knowledge-driven recognition methodology for electricity safety hazard scenarios. Energy Rep. 2022, 8, 10006–10016. [Google Scholar] [CrossRef]
- Kou, L.; Huang, Z.; Jiang, C.; Zhang, F.; Ke, W.; Wan, J.; Li, H. Data Encryption based on 7D Complex Chaotic System with Cubic Memristor for Smart Grid. Front. Energy Res. 2022, 10, 980863. [Google Scholar] [CrossRef]
- Li, Y.; Li, J.; Wang, Y. Privacy-preserving spatiotemporal scenario generation of renewable energies: A federated deep generative learning approach. IEEE Trans. Ind. Inform. 2021, 18, 2310–2320. [Google Scholar] [CrossRef]
- Qu, Y.; Yu, S.; Zhou, W.; Peng, S.; Wang, G.; Xiao, K. Privacy of things: Emerging challenges and opportunities in wireless internet of things. IEEE Wirel. Commun. 2018, 25, 91–97. [Google Scholar] [CrossRef]
- Kumar, P.; Lin, Y.; Bai, G.; Paverd, A.; Dong, J.S.; Martin, A. Smart grid metering networks: A survey on security, privacy and open research issues. IEEE Commun. Surv. Tutor. 2019, 21, 2886–2927. [Google Scholar] [CrossRef]
- Garg, S.; Kaur, K.; Kaddoum, G.; Rodrigues, J.J.; Guizani, M. Secure and lightweight authentication scheme for smart metering infrastructure in smart grid. IEEE Trans. Ind. Inform. 2019, 16, 3548–3557. [Google Scholar] [CrossRef]
- Tutueva, A.V.; Karimov, A.I.; Moysis, L.; Volos, C.; Butusov, D.N. Construction of one-way hash functions with increased key space using adaptive chaotic maps. Chaos Solitons Fractals 2020, 141, 110344. [Google Scholar] [CrossRef]
- Martinez-Luengo, M.; Kolios, A.; Wang, L. Structural health monitoring of offshore wind turbines: A review through the Statistical Pattern Recognition Paradigm. Renew. Sustain. Energy Rev. 2016, 64, 91–105. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).