Holding on to Compliance While Adopting DevSecOps: An SLR
Abstract
1. Introduction
2. Background
2.1. Compliance
2.1.1. Security Compliance
2.1.2. Compliance as Code
2.2. DevSecOps
3. Related Work
4. Method
4.1. Research Goal and Questions
4.2. Search Strategy
“compliance” AND (“devsecops” OR “secdevops” OR “devopssec” OR “secure devops” OR “rugged devops”)
4.3. Selection Criteria
4.3.1. Inclusion Criteria
- No restrictions were applied to the publication year. Even though we do not limit the time when a study was published, the selected studies were published within the period of 2012–2022. This makes sense since DevSecOps was first mentioned in 2012.
- The study must be available as a full-text article. Full-text access to licensed content was limited to Østfold University College’s contractual arrangements with publishers.
- The study is included if it addresses at least one compliance aspect integrated into DevSecOps.
4.3.2. Exclusion Criteria
- The study is excluded if it is not written in the English language (there were 11 studies in the German language);
- If the study is available in more than one database, the versions available in databases other than the one that provides the study for download are excluded (no study was available in different databases);
- If the study is available twice, once as a book chapter and then as a whole book, then the book must be excluded and only the relevant chapter should be considered (there were 10 studies in this scenario);
- If the study is inaccessible, it is excluded (20 studies were identified in this case however only one of them was selected for full-text reading after reading the title, abstract, and keywords. Despite that licensed content, we received access later, and the study was included as primary studies.)
4.4. Data Extraction and Selection Process
5. Results
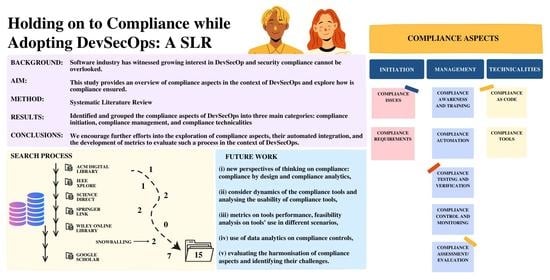
5.1. Categorizing Compliance Aspects (RQ1)
5.1.1. Initiation
5.1.2. Management
5.1.3. Technicalities
5.2. Approaches to Ensure Compliance Aspects (RQ2)
5.3. Emerging Compliance Trends in DevOps literature (RQ3)
6. Discussion and Future Work
7. Conclusions
- Compliance Initiation: This category covers issues related to defining the desired state of security compliance and specifying the compliance requirements;
- Compliance Management: Incorporates all the processes related to the management of compliance such as Automation, Testing and Verification, Validation, Control and Monitoring, Awareness and Training, and Assessment;
- Compliance Technicalities: Includes the technicalities that are used for managing compliance in a DevSecOps environment, such as the compliance as code concept and different compliance tools.
Author Contributions
Funding
Conflicts of Interest
References
- Abrahams, M.Z.; Langerman, J.J. Compliance at Velocity within a DevOps Environment. In Proceedings of the 2018 Thirteenth International Conference on Digital Information Management (ICDIM), Berlin, Germany, 24–26 September 2018; pp. 94–101. [Google Scholar]
- General Data Protection Regulation (GDPR). Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/PDF/?uri=CELEX:32016R0679 (accessed on 22 February 2022).
- Zeeshan, A.A. Compliance and Security. In DevSecOps for NET Core: Securing Modern Software Applications; Zeeshan, A.A., Ed.; Apress: Berkeley, CA, USA, 2020; pp. 265–278. ISBN 978-1-4842-5850-7. [Google Scholar]
- California Consumer Privacy Act (CCPA). Available online: https://oag.ca.gov/privacy/ccpa (accessed on 15 March 2022).
- 201 CMR 17 Standards for the Protection of Personal Information of Residents of the Commonwealth. Available online: https://www.mass.gov/regulations/201-CMR-1700-standards-for-the-protection-of-personal-information-of-residents-of-the-commonwealth (accessed on 15 March 2022).
- Federal Information Security Management Act of 2002. Available online: https://www.govinfo.gov/content/pkg/PLAW-107publ347/pdf/PLAW-107publ347.pdf (accessed on 22 February 2022).
- Family Educational Rights and Privacy Act (FERPA). Available online: https://www2.ed.gov/policy/gen/guid/fpco/ferpa/index.html (accessed on 24 February 2022).
- Sarbanes-Oxley Act of 2002. Available online: https://www.govinfo.gov/content/pkg/PLAW-107publ204/pdf/PLAW-107publ204.pdf (accessed on 22 February 2022).
- Gramm-Leach-Bliley Act. Available online: https://www.ftc.gov/tips-advice/business-center/privacy-and-security/gramm-leach-bliley-act (accessed on 24 February 2022).
- Health Insurance Portability And Accountability Act Of 1996. Available online: https://www.govinfo.gov/content/pkg/PLAW-104publ191/pdf/PLAW-104publ191.pdf (accessed on 22 February 2022).
- National Institute of Standards and Technology. Available online: https://www.nist.gov/ (accessed on 22 February 2022).
- Official PCI Security Standards Council Site–Verify PCI Compliance, Download Data Security and Credit Card Security Standards. Available online: https://www.pcisecuritystandards.org/document_library (accessed on 22 February 2022).
- Capability Maturity Model Integration (CMMI) Institute. Available online: https://cmmiinstitute.com/ (accessed on 16 September 2022).
- COBIT|Control Objectives for Information Technologies. Available online: https://www.isaca.org/resources/cobit (accessed on 23 February 2022).
- CIS Controls v8 Released|SANS Institute. Available online: https://www.sans.org/blog/cis-controls-v8/ (accessed on 23 February 2022).
- Facebook Fined €17m for Data Privacy Laws Breach. Available online: https://www.bbc.com/news/articles/cp9yenpgjwzo (accessed on 10 September 2022).
- Holzhofer, M. Dsgvo-Portal De. Available online: https://www.dsgvo-portal.de/ (accessed on 10 September 2022).
- Initiative (WAI), W.W.A. WCAG 2 Overview. Available online: https://www.w3.org/WAI/standards-guidelines/wcag/ (accessed on 10 September 2022).
- Forsgren, N.; Kersten, M. DevOps Metrics. Commun. ACM 2018, 61, 44–48. [Google Scholar] [CrossRef]
- Angermeir, F.; Voggenreiter, M.; Moyón, F.; Mendez, D. Enterprise-Driven Open Source Software: A Case Study on Security Automation. In Proceedings of the 2021 IEEE/ACM 43rd International Conference on Software Engineering: Software Engineering in Practice (ICSE-SEIP), Madrid, Spain, 25–28 May 2021; pp. 278–287. [Google Scholar]
- Ullah, K.W.; Ahmed, A.S.; Ylitalo, J. Towards Building an Automated Security Compliance Tool for the Cloud. In Proceedings of the 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 1587–1593. [Google Scholar]
- DeLuccia IV, J.; Gallimore, J.; Kim, G.; Miller, B. DevOps Audit Defense Toolkit. Available online: https://itrevolution.com/devops-audit-defense-toolkit/ (accessed on 15 March 2022).
- Amazon Web Services–Labs. Available online: https://github.com/awslabs (accessed on 13 March 2022).
- DevSecOps. Available online: https://www.devsecops.org (accessed on 13 March 2022).
- OpenDevSecOps. Available online: https://github.com/opendevsecops (accessed on 13 March 2022).
- Rugged Software. Available online: http://ruggedsoftware.org/ (accessed on 13 March 2022).
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering 2007. Available online: https://www.researchgate.net/profile/Barbara-Kitchenham/publication/302924724_Guidelines_for_performing_Systematic_Literature_Reviews_in_Software_Engineering/links/61712932766c4a211c03a6f7/Guidelines-for-performing-Systematic-Literature-Reviews-in-Software-Engineering.pdf (accessed on 22 February 2022).
- Editor, C.C. Security–Glossary|CSRC. Available online: https://csrc.nist.gov/glossary/term/security (accessed on 5 October 2021).
- Marlow, A.T. What’s New in ISO 37301:2021 & How It Can Improve Your Compliance Management. Available online: https://emsmastery.com/2021/05/18/whats-new-in-iso-373012021-how-it-can-improve-your-compliance-management/ (accessed on 11 September 2022).
- Kshetri, N. Big Data׳s Impact on Privacy, Security and Consumer Welfare. Telecommun. Policy 2014, 38, 1134–1145. [Google Scholar] [CrossRef]
- Santos, C.; Bielova, N.; Matte, C. Are Cookie Banners Indeed Compliant with the Law? Deciphering EU legal requirements on consent and technical means to verify compliance of cookie banners. arXiv 2020, arXiv:1912.07144v2. [Google Scholar] [CrossRef]
- Dupont, S.; Ginis, G.; Malacario, M.; Porretti, C.; Maunero, N.; Ponsard, C.; Massonet, P. Incremental Common Criteria Certification Processes Using DevSecOps Practices. In Proceedings of the 2021 IEEE European Symposium on Security and Privacy Workshops (EuroS PW), Vienna, Austria, 6–10 September 2021; pp. 12–23. [Google Scholar]
- Julisch, K. Security Compliance: The next Frontier in Security Research. In Proceedings of the 2008 New Security Paradigms Workshop, New York, NY, USA, 22 September 2008; Association for Computing Machinery: New York, NY, USA, 2008; pp. 71–74. [Google Scholar]
- Casagni, M.; Heeren, M.; Cagle, R.; Eng, R.; Flamm, J.; Goldrich, S.; Hanf, D.; Kristan, M.; Brunelle, J.F.; Harvey, T.; et al. March 2018 Federal Devops Summit Report. 31. Available online: https://atarc.org/wp-content/uploads/2019/01/2018-03-01-ATARC-Federal-DevOps-Summit-White-Paper-1.pdf (accessed on 3 March 2022).
- Daud, M.; Rasiah, R.; George, M.; Asirvatham, D.; Thangiah, G. Bridging The Gap Between Organisational Practices and Cyber Security Compliance: Can Cooperation Promote Compliance in Organisations? Int. J. Bus. Soc. 2018, 19, 20. [Google Scholar]
- Wood, C.C. Policies Alone Do Not Constitute a Sufficient Awareness Effort. Comput. Fraud. Secur. 1997, 1997, 14–19. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2013 Information Technology—Security Techniques—Information Security Management Systems—Requirements. Available online: https://www.iso.org/cms/render/live/en/sites/isoorg/contents/data/standard/05/45/54534.html (accessed on 23 February 2022).
- ISO 27001 Annex A.18–Compliance. Available online: https://www.isms.online/iso-27001/annex-a-18-compliance/ (accessed on 23 February 2022).
- Hsu, T.H.-C. Hands-On Security in DevOps: Ensure Continuous Security, Deployment, and Delivery with DevSecOps; Packt Publishing Ltd.: Birmingham, UK, 2018; ISBN 978-1-78899-241-1. [Google Scholar]
- McGraw, G. Software Security. IEEE Secur. Priv. 2004, 2, 80–83. [Google Scholar] [CrossRef]
- Raynaud, F. DevSecOps Whitepaper. Available online: https://pdfcoffee.com/devsecops-whitepaper-pdf-free.html (accessed on 20 February 2022).
- OWASP Top Ten Web Application Security Risks|OWASP. Available online: https://owasp.org/www-project-top-ten/ (accessed on 23 February 2022).
- Chatterjee, R. Security in DevOps and Automation. In Red Hat and IT Security: With Red Hat Ansible, Red Hat OpenShift, and Red Hat Security Auditing; Chatterjee, R., Ed.; Apress: Berkeley, CA, USA, 2021; pp. 65–104. ISBN 978-1-4842-6434-8. [Google Scholar]
- Sun, X.; Cheng, Y.; Qu, X.; Li, H. Design and Implementation of Security Test Pipeline Based on DevSecOps. In Proceedings of the 2021 IEEE 4th Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Chongqing, China, 18–20 June 2021; Volume 4, pp. 532–535. [Google Scholar]
- MacDonald, N.; Head, I. DevSecOps: How to Seamlessly Integrate Security Into DevOps. Gartner Research 2016. Available online: https://www.gartner.com/en/documents/3463417 (accessed on 22 February 2022).
- Riungu-Kalliosaari, L.; Mäkinen, S.; Lwakatare, L.E.; Tiihonen, J.; Männistö, T. DevOps Adoption Benefits and Challenges in Practice: A Case Study. In Product-Focused Software Process Improvement; Abrahamsson, P., Jedlitschka, A., Nguyen Duc, A., Felderer, M., Amasaki, S., Mikkonen, T., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2016; Volume 10027, pp. 590–597. ISBN 978-3-319-49093-9. [Google Scholar]
- Carturan, S.B.O.G.; Goya, D.H. A Systems-of-Systems Security Framework for Requirements Definition in Cloud Environment. In Proceedings of the 13th European Conference on Software Architecture–ECSA ’19, Paris, France, 9–13 September 2019; ACM Press: Paris, France, 2019; Volume 2, pp. 235–240. [Google Scholar]
- Mohan, V.; ben Othmane, L.; Kres, A. BP: Security Concerns and Best Practices for Automation of Software Deployment Processes: An Industrial Case Study. In Proceedings of the 2018 IEEE Cybersecurity Development (SecDev), Cambridge, MA, USA, 30 September 2018–2 October 2018; pp. 21–28. [Google Scholar]
- Carter, K. Francois Raynaud on DevSecOps. IEEE Softw. 2017, 34, 93–96. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. Modeling Continuous Security: A Conceptual Model for Automated DevSecOps Using Open-Source Software over Cloud (ADOC). Comput. Secur. 2020, 97, 101967. [Google Scholar] [CrossRef]
- Yasar, H. Overcoming DevSecOps Challenges: A Practical Guide for All Stakeholders; Carnegie-Mellon Univ: Pittsburgh, PA, USA, 2020. [Google Scholar]
- Rahman, A.A.U.; Williams, L. Software Security in DevOps: Synthesizing Practitioners’ Perceptions and Practices. In Proceedings of the 2016 IEEE/ACM International Workshop on Continuous Software Evolution and Delivery (CSED), Austin, TX, USA, 14–15 May 2016; pp. 70–76. [Google Scholar]
- Sen, A. DevOps, DevSecOps, AIOPS- Paradigms to IT Operations. In Proceedings of the Evolving Technologies for Computing, Communication and Smart World; Singh, P.K., Noor, A., Kolekar, M.H., Tanwar, S., Bhatnagar, R.K., Khanna, S., Eds.; Springer: Singapore, 2021; pp. 211–221. [Google Scholar]
- Mohan, V.; Othmane, L.B. SecDevOps: Is It a Marketing Buzzword?–Mapping Research on Security in DevOps. In Proceedings of the 2016 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 542–547. [Google Scholar]
- Lie, M.F.; Sánchez-Gordón, M.; Colomo-Palacios, R. DevOps in an ISO 13485 Regulated Environment: A Multivocal Literature Review. In Proceedings of the 14th ACM/IEEE International Symposium on Empirical Software Engineering and Measurement (ESEM), Bari, Italy, 5 October 2020; ACM: Bari, Italy, 2020; pp. 1–11. [Google Scholar]
- Lee, J.; Kang, K.; Shim, C. Devsecops for Small and Medium-Sized Enterprises: A Systematic Literature Review. SSRN 2022. [Google Scholar] [CrossRef]
- Rajapakse, R.N.; Zahedi, M.; Babar, M.A.; Shen, H. Challenges and Solutions When Adopting DevSecOps: A Systematic Review. arXiv 2021, arXiv:2103.08266. [Google Scholar] [CrossRef]
- Rafi, S.; Yu, W.; Akbar, M.A. Towards a Hypothetical Framework to Secure DevOps Adoption: Grounded Theory Approach. In Proceedings of the Evaluation and Assessment in Software Engineering, New York, NY, USA, 15 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 457–462. [Google Scholar]
- Rios, E.; Iturbe, E.; Larrucea, X.; Rak, M.; Mallouli, W.; Dominiak, J.; Muntés, V.; Matthews, P.; Gonzalez, L. Service Level Agreement-Based GDPR Compliance and Security Assurance in(Multi)Cloud-Based Systems. IET Softw. 2019, 13, 213–222. [Google Scholar] [CrossRef]
- Steffens, A.; Lichter, H.; Moscher, M. Towards Data-Driven Continuous Compliance Testing. 7. Available online: CSE2018_preface (ceur-ws.org) (accessed on 1 February 2022).
- Moyón, F.; Soares, R.; Pinto-Albuquerque, M.; Mendez, D.; Beckers, K. Integration of Security Standards in DevOps Pipelines: An Industry Case Study. In Proceedings of the Product-Focused Software Process Improvement; Morisio, M., Torchiano, M., Jedlitschka, A., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 434–452. [Google Scholar]
- Vadlamudi, S.; Sam, J. A Novel Approach to Onboarding Secure Cloud-Native Acquisitions into Enterprise Solutions. In Proceedings of the 2021 International Conference on Disruptive Technologies for Multi-Disciplinary Research and Applications (CENTCON), Bengaluru, India, 22–24 November 2021; Volume 1, pp. 228–233. [Google Scholar]
- Jimenez-Maggiora, G.A.; Bruschi, S.; Qiu, H.; So, J.-S.; Aisen, P.S. ATRI EDC: A Novel Cloud-Native Remote Data Capture System for Large Multicenter Alzheimer’s Disease and Alzheimer’s Disease-Related Dementias Clinical Trials. JAMIA Open 2022, 5, ooab119. [Google Scholar] [CrossRef]
- Peldszus, S.; Bürger, J.; Kehrer, T.; Jürjens, J. Ontology-Driven Evolution of Software Security. Data Knowl. Eng. 2021, 134, 101907. [Google Scholar] [CrossRef]
- Shameem Ahamed, W.S.; Zavarsky, P.; Swar, B. Security Audit of Docker Container Images in Cloud Architecture. In Proceedings of the 2021 2nd International Conference on Secure Cyber Computing and Communications (ICSCCC), Jalandhar, India, 21–23 May 2021; pp. 202–207. [Google Scholar]
- Shields, M. The Secret to Achieving a Faster ATO. Available online: https://pyramidsystems.com/wp-content/uploads/2020/09/Pyramid-ATO-ebook-1.pdf (accessed on 10 March 2022).
- Desai, R.; Nisha, T.N. Best Practices for Ensuring Security in DevOps: A Case Study Approach. J. Phys. Conf. Ser. 2021, 1964, 042045. [Google Scholar] [CrossRef]
- Preidel, C.; Borrmann, A. Towards Code Compliance Checking On The Basis Of A Visual Programming Language. 20. Available online: 2016_25.content.01707.pdf (itcon.org) (accessed on 22 February 2022).
- Kim, S.H.; Yang, K.H.; Park, S. An Integrative Behavioral Model of Information Security Policy Compliance. Sci. World J. 2014, 2014, 1–12. [Google Scholar] [CrossRef] [PubMed]
- Automation and the DevOps Workflow. Available online: https://www.chef.io/docs/default-source/legacy/automation-and-the-devops-workflow.pdf (accessed on 23 February 2022).
- Kryptowire®: Mobile Security Company. Available online: https://www.kryptowire.com/ (accessed on 12 April 2022).
- Compliance in a DevOps Culture. Available online: https://martinfowler.com/articles/devops-compliance.html (accessed on 22 October 2022).
- Myrbakken, H.; Colomo-Palacios, R. DevSecOps: A Multivocal Literature Review. In Proceedings of the Software Process Improvement and Capability Determination; Mas, A., Mesquida, A., O’Connor, R.V., Rout, T., Dorling, A., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 17–29. [Google Scholar]
- MUSA Project Website. Available online: https://www.musa-project.eu/ (accessed on 23 February 2022).
- Dynamic Application Security Testing: DAST Basics. Available online: https://www.whitesourcesoftware.com/resources/blog/dast-dynamic-application-security-testing/ (accessed on 4 March 2022).
- OpenSCAP Portal. Available online: https://www.open-scap.org/ (accessed on 22 February 2022).
- Building End-to-End AWS DevSecOps CI/CD Pipeline with Open Source SCA, SAST and DAST Tools. Available online: https://aws.amazon.com/blogs/devops/building-end-to-end-aws-devsecops-ci-cd-pipeline-with-open-source-sca-sast-and-dast-tools/ (accessed on 4 March 2022).
- Secure Standardized Logging–AWS CloudTrail–Amazon Web Services. Available online: https://aws.amazon.com/cloudtrail/ (accessed on 4 March 2022).
- Standards, E. EN IEC 62443-4-1. Available online: https://www.en-standard.eu/csn-en-iec-62443-4-1-security-for-industrial-automation-and-control-systems-part-4-1-secure-product-development-lifecycle-requirements/ (accessed on 23 February 2022).
- MacDonald, N.; Haight, C. DevOpsSec: Creating the Agile Triangle. Available online: https://www.gartner.com/en/documents/1896617 (accessed on 25 October 2022).
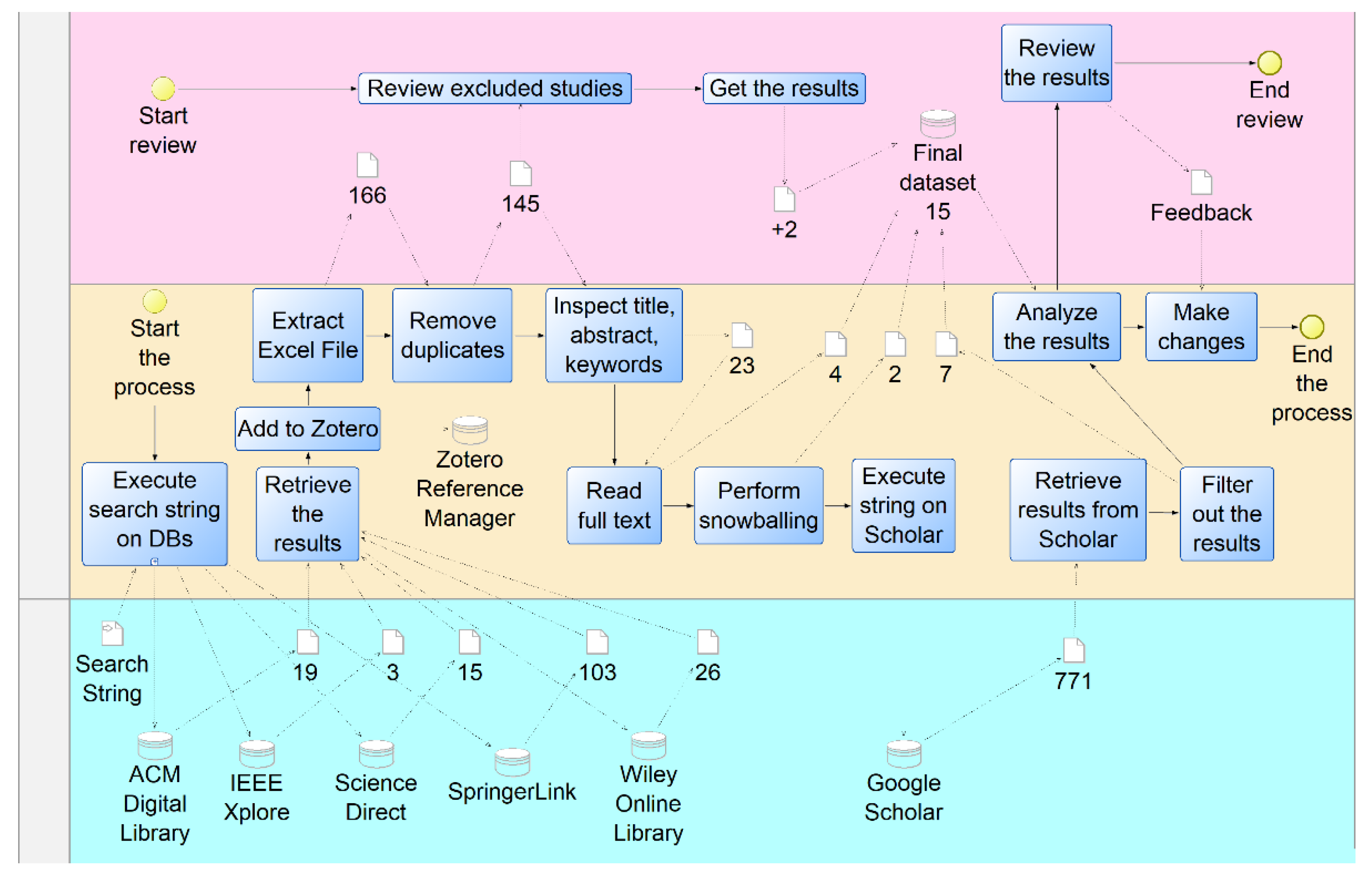

| Database | Initial Search | Remove Duplicates and Other Languages | Read Title, Keywords, and Abstract | Full Text Reading |
|---|---|---|---|---|
| ACM Digital Library | 19 | 19 | 11 | 1 |
| IEEE Xplore | 3 | 3 | 3 | 1 |
| ScienceDirect | 15 | 15 | 6 | 2 |
| Springer Link | 103 | 82 | 3 | 2 |
| Wiley | 26 | 26 | 0 | 0 |
| Total studies | 166 | 145 | 23 | 6 |
| Snowballing | 2 | |||
| Google Scholar | 771 | 27 | 7 | |
| Primary studies | 15 |
| Category | # | Compliance Aspects | Primary Studies |
|---|---|---|---|
| Initiation | 1 | Compliance Issues | [1,3,61,62,63] |
| 2 | Compliance Requirements | [1,58,60,61,62,63] | |
| Management | 3 | Compliance Awareness and Training | [1,43,61,62] |
| 4 | Compliance Automation | [1,20,50,61,63] | |
| 5 | Compliance Testing and Verification | [1,3,20,43,60,61,63,64,65,66] | |
| 6 | Compliance Validation | [1,50,60,61,63] | |
| 7 | Compliance Control and Monitoring | [1,3,43,59,67] | |
| 8 | Compliance Assessment/Evaluation | [1,61,62] | |
| Technicalities | 9 | Compliance as Code | [1,20,43,50,66] |
| 10 | Compliance Tools | [1,20,62,66] |
| Database | Reference | Year | Type * | Title |
|---|---|---|---|---|
| ACM Digital Library | [58] | 2020 | C | Towards a Hypothetical Framework to Secure DevOps Adoption: Grounded Theory Approach |
| IEEE Xplore | [1] | 2018 | C | Compliance at Velocity within a DevOps Environment |
| [62] | 2021 | C | A Novel Approach to Onboarding Secure CloudNative Acquisitions into Enterprise Solutions | |
| [65] | 2021 | C | Security Audit of Docker Container Images in Cloud Architecture | |
| [20] | 2021 | C | Enterprise-Driven Open Source Software: A Case Study on Security Automation | |
| ScienceDirect | [64] | 2021 | J | Ontology-driven evolution of software security |
| [50] | 2020 | J | Modeling Continuous Security: A Conceptual Model for Automated DevSecOps using Open-source Software Over the Cloud (ADOC) | |
| Springer Link | [61] | 2020 | C | Integration of Security Standards in DevOps Pipelines: An Industry Case Study |
| [43] | 2021 | B | Security in DevOps and Automation | |
| [3] | 2020 | B | Compliance and Security | |
| Wiley | [59] | 2019 | J | Service Level Agreement-based GDPR Compliance and Security Assurance in (multi)Cloud-based Systems |
| Other | [60] | 2018 | J | Towards Data-driven Continuous Compliance Testing |
| [67] | 2021 | J | Best Practices for Ensuring Security in DevOps: A Case Study Approach | |
| [66] | 2020 | B | The Secret to Achieving a Faster ATO | |
| [63] | 2022 | J | ATRI EDC: A Novel Cloud-native Remote Data Capture System for Large Multicenter Alzheimer’s Disease and Alzheimer’s Disease-related Dementias Clinical Trials |
| Category | Aspects | 2018 | 2019 | 2020 | 2021 | 2022 | Total | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [1] | [60] | [59] | [50] | [61] | [58] | [66] | [3] | [64] | [43] | [67] | [62] | [65] | [20] | [63] | ||||
| Initiation | 1 | Issues | X | X | X | X | X | 5 | ||||||||||
| 2 | Requirements | X | X | X | X | X | X | 6 | ||||||||||
| Management | 3 | Awareness and Training | X | X | X | X | 4 | |||||||||||
| 4 | Automation | X | X | X | X | X | 5 | |||||||||||
| 5 | Testing and Verification | X | X | X | X | X | X | X | X | X | X | 10 | ||||||
| 6 | Compliance Validation | X | X | X | X | X | 5 | |||||||||||
| 7 | Control and Monitoring | X | X | X | X | X | 5 | |||||||||||
| 8 | Assessment/ Evaluation | X | X | X | 3 | |||||||||||||
| Technicalities | 9 | Compliance as Code | X | X | X | X | X | 5 | ||||||||||
| 10 | Tools | X | X | X | X | 4 | ||||||||||||
| Total | 10 | 3 | 1 | 3 | 7 | 1 | 3 | 3 | 1 | 4 | 1 | 5 | 1 | 4 | 5 | |||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramaj, X.; Sánchez-Gordón, M.; Gkioulos, V.; Chockalingam, S.; Colomo-Palacios, R. Holding on to Compliance While Adopting DevSecOps: An SLR. Electronics 2022, 11, 3707. https://doi.org/10.3390/electronics11223707
Ramaj X, Sánchez-Gordón M, Gkioulos V, Chockalingam S, Colomo-Palacios R. Holding on to Compliance While Adopting DevSecOps: An SLR. Electronics. 2022; 11(22):3707. https://doi.org/10.3390/electronics11223707
Chicago/Turabian StyleRamaj, Xhesika, Mary Sánchez-Gordón, Vasileios Gkioulos, Sabarathinam Chockalingam, and Ricardo Colomo-Palacios. 2022. "Holding on to Compliance While Adopting DevSecOps: An SLR" Electronics 11, no. 22: 3707. https://doi.org/10.3390/electronics11223707
APA StyleRamaj, X., Sánchez-Gordón, M., Gkioulos, V., Chockalingam, S., & Colomo-Palacios, R. (2022). Holding on to Compliance While Adopting DevSecOps: An SLR. Electronics, 11(22), 3707. https://doi.org/10.3390/electronics11223707