Abstract
For the problems brought by malicious interference in the unmanned aerial vehicle (UAV) swarm network, we establish a cluster-based UAV swarm information transmission model. We mainly consider four aspects: cluster head selection, channel allocation, power allocation and UAV position. In order to improve the backhaul information rate of UAV swarm, we propose a joint optimization method of spectrum resource with the goal of maximizing the sum throughput of the cluster head UAV. We decompose the original mixed integer nonlinear programming (MINLP) problem into multiple sub-problems based on the block coordinate descent (BCD) technique, and then solve them based on convex optimization and successive convex approximation (SCA) technique. Simulation results show that the proposed method can obtain the spectrum resource optimization strategy of UAV swarm information transmission, reduce the impact of malicious interference, and effectively improve the backhaul information rate of UAV swarm.
1. Introduction
With the world’s new military revolution and the rapid development of high and new technology, the unmanned aerial vehicle (UAV), as a new type of combat force, has been gradually applied to such tasks as investigation and surveillance, electronic countermeasure, fire strike, air early warning, target indication, and communication and command tasks, and UAV has become the core of the unmanned combat system [1]. Although the UAV has the advantages of flexible movement and on-demand deployment, due to its limited energy and load capacity, single UAVs can complete limited types of tasks with low efficiency. However, multiple UAVs cooperate with each other through networking, which can further expand the communication coverage and improve the communication quality [2]. In addition, when a UAV of a network is damaged, other UAV nodes can automatically reconstruct the network to ensure the continuity of information service. Therefore, the UAV swarm, in the form of networking and cooperation, will become the mainstream in the future to perform tasks. In order to ensure effective information transmission, this paper focuses on the problem of cluster-based UAV swarm information transmission. The model is shown in Figure 1.
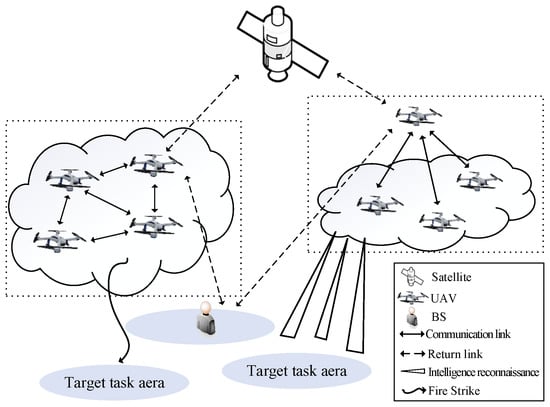
Figure 1.
Unmanned aerial vehicle (UAV) swarm application model.
However, a large number of UAV nodes also determine the complexity of UAV swarm information transmission. On the one hand, the division of spectrum resource within the UAV swarm is the core problem in cluster communication; on the other hand, the UAV group needs to transmit task information back to the satellite or ground base station (BS). If all UAVs transmit information back at the same time, the burden of the backhaul links will inevitably increase. In order to ensure reliable information exchange and data return of UAV swarm, the existing UAV swarm mainly adopts two structures: planar mode [3] and clustered mode [4]. For the large-scale UAV swarm, the planar mode will cause a large delay, so we use the clustered mode to reduce the system delay and network complexity. In addition, due to the open nature of the wireless network, the UAV swarm information transmission system is vulnerable to a variety of external security threats, such as interference, eavesdropping and deception attacks [5,6]. In this paper, we mainly study the malicious interference attacks, which, as an active attack, aims to reduce the signal-to-noise ratio of useful signals in the information transmission link, resulting in poor information transmission quality or even interruption.
1.1. Related Works
Scholars have carried out a lot of research work on the problem of UAV swarm information transmission. In [7], aiming at the problem of dynamic spectrum allocation of UAV swarm in malicious interference scenarios, the authors constructed a dynamic spectrum allocation model based on the Stackelberg game, in which the game follower uses random learning automata to select the channel. The proposed algorithm effectively improved the throughput performance. However, they did not consider the clustered mode and the movement characteristics of UAVs. They only built a game model to avoid the impact of malicious interference by optimizing channel selection. In [8], the authors mainly studied the dynamic spectrum allocation of multiple UAVs as air base stations to provide temporary services for ground equipment, mainly involving three aspects: UAV and ground user matching, sub-channel allocation, and power allocation. In order to ensure the fairness of user communication, they proposed a joint optimization algorithm to solve the above mixed integer nonlinear optimization problem. Similarly, they did not consider the movement characteristics of UAVs nor the objective of backhaul information rate. In [9], the authors studied the trajectory optimization problem in UAV data transmission, with the objective of minimizing the UAV information transmission time, but they only considered two UAVs and did not consider the optimization of spectrum resource. In [10], the UAV was used as the cluster head and the ground node is used as the cluster member; they then studied the trajectory optimization and clustering mechanism to improve service information. However, they did not consider the optimization of channel allocation and power allocation. In addition to traditional anti-interference methods, the authors in [11,12] studied an effective alternative to massive antenna systems to enhance the signal quality and suppress interference through deploying UAVs integrated with intelligent reflective surfaces. In [13,14,15], the authors studied several optimization algorithms which proved to be successful in resource optimization of wireless communication scenarios.
1.2. Contribution and Structure
In view of the challenges and shortcomings of the current research, this paper proposes a joint optimization method of spectrum resource to improve the backhaul information rate of UAV swarm. Compared with the existing research, the contributions and innovations of this paper are as follows:
(1) Aiming at the information transmission network of UAV swarm under the malicious interference scenario, we establish the cluster-based UAV swarm information transmission model. We comprehensively consider cluster head selection, channel allocation, power allocation and UAV position optimization and propose a joint optimization method of spectrum resource in order to improve the sum backhaul information rate of the UAV swarm.
(2) The original mixed integer nonlinear programming (MINLP) problem is decomposed into multiple sub-problems which can be optimized alternately until convergence through the BCD technique. For the convex sub-problems of cluster head selection, channel allocation and power allocation, the convex optimization solver CVX [16] is used to directly solve them. For the non-convex sub-problem of position optimization, the relaxation variables are introduced to convex it and then the successive convex approximation (SCA) technique is used to solve it. Finally, we obtain a relative optimal solution of the original optimization problem.
(3) Based on the analysis of convergence and complexity of the proposed method, we conclude that the proposed method can effectively reduce the impact of malicious interference and improve the backhaul information rate of UAV swarm.
The remainder of this paper is organized as follows. In Section 2, we present the system model and problem formulation. In Section 3, we describe how we solve the four sub-problems and provide the convergence and complexity analysis of the proposed method. Section 4 shows the simulation results and discussion. Finally, Section 5 concludes this work.
2. System Model and Problem Formulation
2.1. System Model
As shown in Figure 2, considering that the UAV swarm has completed the information collection of the target area, it is necessary to summarize the collected information and finally send it back to the satellite or ground base station. This paper mainly considers the problem of information backhaul within the UAV swarm. The system consists of a set of of M UAVs, a set of of J jamming nodes, and a set of of N channels. Suppose that the UAV hovers at a fixed altitude H, which represents the lowest flight altitude to avoid obstacles and the interference node conducts full channel interference on the frequency spectrum in the region.
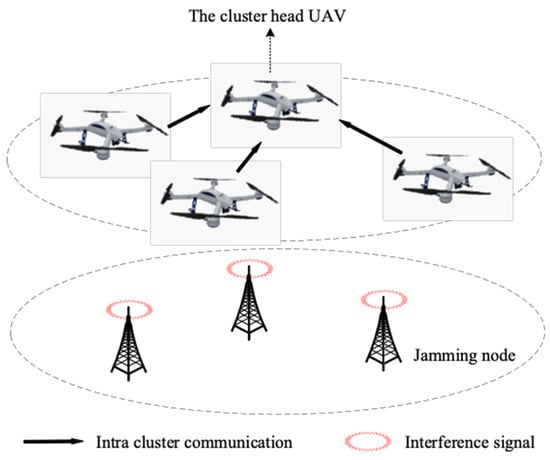
Figure 2.
UAV swarm information transmission system under jamming attack.
Due to the relatively high flight distance of a UAV, its air-to-air channel model can be approximately modeled as a free-space path-loss model, which can be expressed as: , where represents the channel power gain at the unit reference distance and is the air-to-air path-loss index and represents the position coordinates of UAV m; in this paper, we make . At the same time, considering the lower bound of the communication system performance in the interference environment, that is, there is no occlusion between the interference node and the UAV, the channel between the interference node j and the UAV m can also be modeled as , where represents the position coordinates of the interference node j. Therefore, the transmission rate from UAV i to UAV m in channel n can be expressed as:
where B is the channel bandwidth, is the background noise power, is the transmission power of UAV i, and is the transmission power of the jamming node.
2.2. UAV Clustering
The UAV swarm information transmission network adopts a clustered mode; that is, if UAV m is the cluster head, it can only receive information but cannot send information and if UAV m is a member of the cluster, it can only send information but cannot receive information. Therefore, we can use binary variables to represent the communication scheduling between UAVs, which can be given by:
At the same time, there are constraints such that only one UAV can act as the cluster head in UAV swarm, which can be given by:
2.3. Channel Allocation
In order to ensure effective communication between UAVs, their communication adopts orthogonal frequency division multiplexing mode, and we introduce the binary decision variables to represent the channel occupation, which is expressed as:
Considering that only one UAV user is allowed to be served in one channel, and the UAV has the maximum number of antennas due to its load capacity limitation. Assuming that the maximum number of access channels is Num, there are constraints:
where represents the cluster head UAV.
2.4. Power Allocation
Since UAVs reuse the spectrum resource of existing users in the area to retrieve information, it is necessary to control their transmission power in order not to interfere with existing users. Assuming that the transmission power of the same UAV in all channels is the same, there are constraints:
where is the transmission power of UAV m, is the channel gain from UAV m to existing user S, and is the maximum interference threshold of the existing user.
At the same time, the transmission power of UAV in all channels should not exceed the upper limit of its transmission power, which can be given by:
2.5. UAV Position
This paper considers the rotor UAV, which can hover in the air, so it must meet the maximum speed limit:
In order to ensure the safety of UAV flight, the minimum distance between UAVs needs to be limited, which can be given by:
2.6. Problem Formulation
For UAV swarm information transmission, the optimization is to maximize the throughput of cluster head UAV under the constraints of UAV clustering, channel allocation, power allocation and UAV position, so as to improve the backhaul information rate, which can be given by:
where describes that there is only one UAV in the UAV swarm as the cluster head; describes that one channel can only be occupied by one UAV at most; describes that each UAV except the cluster head UAV must occupy one channel and no more than Num channels to ensure effective information transmission; describes that the interference of any UAV to existing user should not exceed its maximum interference threshold; describes that the transmission power of a UAV in all channels should not exceed its maximum transmission power limit; describes that the position movement of a UAV within a time slot cannot exceed the maximum distance limit; and describes that the minimum distance limit should be met to ensure the safety flight of a UAV.
3. Problem Solving
Since the objective function involves binary variables , and real variables , , The problem expressed in Equation (11) is a mixed integer nonlinear programming (MINLP) problem, which is difficult to solve directly. Therefore, this paper proposes a joint optimization method of spectrum resource based on BCD technique and SCA technique to solve this problem. Specifically, we transform the original MINLP problem into four sub-problems and alternately optimize them until the growth value of objective function is less than ζ or reaches the maximum number of iterations.
3.1. UAV Clustering Optimization
Given the channel allocation, power allocation, and UAV position, the original problem can be transformed into:
This problem is a standard integer linear programming problem, which can be effectively solved by MOSEK [16] in CVX.
3.2. Channel Allocation Optimization
Given the clustering strategy, power allocation and UAV position, the original problem can be transformed into:
The problem expressed in Equation (13) is a linear function of , and the constraints are affine functions. Therefore, the problem is a standard convex optimization problem, which can be solved by CVX.
3.3. Power Allocation Optimization
Given the clustering strategy, channel allocation, and UAV position, the original problem can be transformed into:
It is easy to prove that the problem expressed in Equation (14) is a standard convex problem and can be solved directly by convex optimization.
3.4. UAV Position Optimization
Given the clustering strategy, channel allocation and power allocation, the original problem can be transformed into:
In order to solve the non-convexity caused by constraints and objective function, we first introduce two relaxation variables and make them meet the constraints:
Then, the problem expressed in Equation (15) is equivalent to the following optimization problem:
Currently, the objective function is a convex function. Since the objective function of a maximization convex optimization problem must be a concave function, we use the following lemma to obtain a lower bound concave function of the original convex function:
Lemma 1.
Given a feasible solution, the lower bound ofis:
Proof.
It is easy to know that is a convex function, and its first-order Taylor expansion at can be expressed as:
Based on the above formula, let , and then the lemma is proved. □
Using the above lemma, optimization problem expressed in Equation (18) is transformed into a new optimization problem, which provides the lower bound of the original problem:
By introducing the relaxation variable , Constraint expressed in Equation (16) can be transformed into:
Since the right side of Equation (23) is still non-convex, the lower bound of can be obtained by first-order Taylor expansion at the point :
Similarly, we square both sides of Equation (10) and use the first-order Taylor expansion to convert them into convex constraints:
Based on the above discussion, the original optimization problem expressed in Equation (15) is translated into:
The above problem is a standard convex optimization problem, so we can use CVX to solve it.
3.5. Joint Optimization Method and Convergence
The steps of the joint optimization method we proposed are as follows Algorithm 1:
| Algorithm 1: Joint optimization method of spectrum resource |
| Input: the number of UAVs M, the number of jamming nodes J, the number of channels N, the initial position of UAVs |
|
In this part, we prove that the proposed algorithm creates a non-decreasing sequence of objective values of problem expressed in Equation (11) and converges to a feasible solution. First, it can be verified after the initialization step or after each r-iteration of the approximation process that we achieve a feasible solution of , , , . For step 3 of Algorithm 1, since the optimal solution of problem expressed in Equation (12) is obtained for given , and , we have:
where represents the objective value of problem expressed in Equation (11). Second, for the given and , can be obtained in step 4 of Algorithm 1; it follows that:
Moreover, for the given and , can be obtained in step 5 of Algorithm 1; it follows that:
Finally, for the given and , can be obtained in step 6 of Algorithm 1; it follows that:
where we define as the objective value of problem expressed in Equation (26), and (a) holds since Algorithm 1 achieves the solution for the given , and ; (b) holds since the objective value of problem expressed in Equation (26) is the lower bound of the objective of its original problem expressed in Equation (15) at because the SCA technique is applied. Using the results in Equations (27)–(30), we obtain that:
which indicates that the objective value of problem expressed in Equation (11) is non-decreasing after each iteration of Algorithm 1. Since the backhaul information rate as the optimization objective must have an upper limit, the proposed algorithm is guaranteed to converge to a feasible solution. This completes the proof.
For the analysis of complexity, the clustering optimization sub-problem is a standard integer linear programming problem with a complexity of ; both channel allocation and power allocation sub-problems are standard convex optimization problems. The complexity of them is [17] by using the interior point method in CVX, where x represents the number of variables. So, the complexity is and respectively; the position optimization sub-problem is transformed into a convex problem by introducing relaxation variables and using the SCA technique. Its complexity is . Therefore, the total complexity of the proposed joint spectrum resource optimization method is , where L is the number of convergence times of the method.
4. Simulation Results and Discussion
4.1. Parameter Settings
In this section, we carried out corresponding experimental simulation to verify the effectiveness of the proposed method. In order to make the parameter settings more reasonable, we referred to [18] to set the simulation parameters, as shown in Table 1. Unless otherwise specified, all simulation experiments in this paper use the parameters in Table 1.

Table 1.
Simulation parameters of Unmanned aerial vehicle (UAV) swarm information transmission system.
4.2. Simulation Results
Figure 3 shows the change in UAVs’ total backhaul information rate with the number of channels. It can be seen that the more channels there are, the higher the UAVs’ total backhaul will be. As the number of channels continues increasing, the growth of the total backhaul rate will slow down. This is because the UAVs’ total transmission power is limited. The more channels there are, the smaller the transmission power allocated to each channel will be. In addition, there is a significant growth in total return rate when the interference power is low.
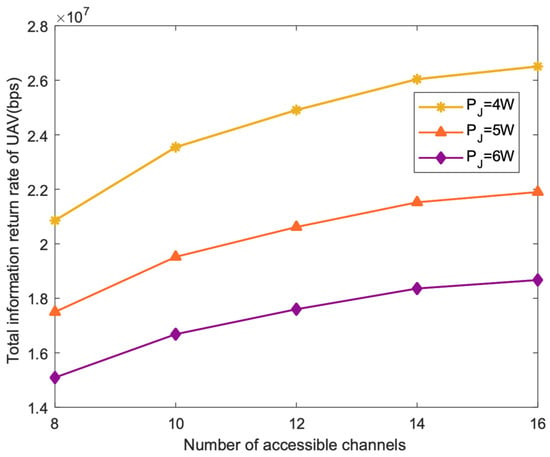
Figure 3.
The total backhaul information rate of UAV varies with the number of channels.
Figure 4 shows the cluster head selection and position optimization of the UAV swarm under the conditions of 8 UAVs, 12 channels and after optimization of the proposed method. It can be seen that UAV 1 is finally selected as the cluster head UAV, and other UAVs are as far away from the interference node as possible and close to UAV 1, meeting the limit of moving distance. Figure 5 shows the channel allocation and power allocation strategies optimized by the proposed method under this condition.
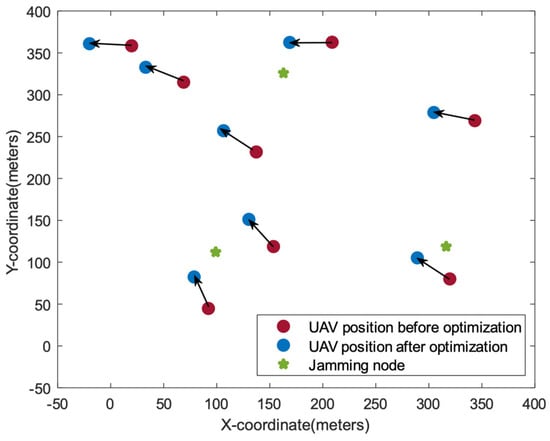
Figure 4.
UAV position of the proposed method.
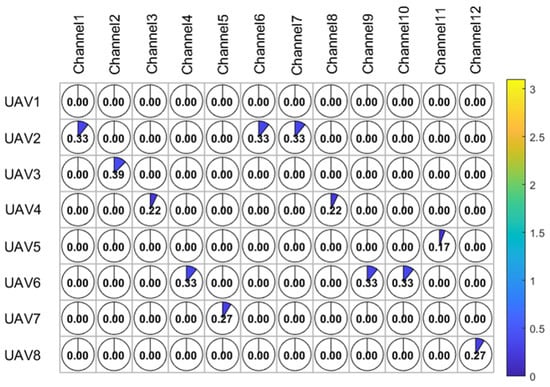
Figure 5.
Channel allocation and power allocation of the proposed method.
Figure 6 shows the convergence curve of the joint optimization method of spectrum resource under different channel numbers under the conditions of . It can be seen that the objective function value increases continuously in the iteration process and finally tends to converge.
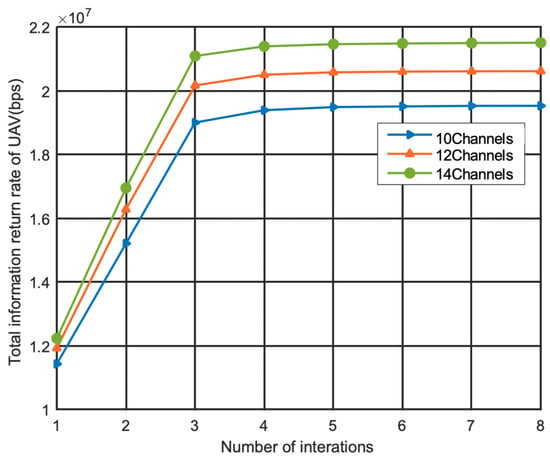
Figure 6.
Convergence diagram of proposed method.
In order to further verify the effectiveness of the proposed method in the UAV swarm information transmission scenario under jamming attack, we use a simulation comparison method and compare the proposed method with the cluster-head-fixed algorithm, power-fixed algorithm, position-fixed algorithm and random-channel allocation algorithm. Cluster-head-fixed algorithm: find a clustering strategy with the shortest distance from the cluster member UAVs to the cluster head UAV at the initial position through calculation and use it as the final cluster head selection. Random-channel allocation algorithm: under the condition that all cluster member UAVs occupy the channel, randomly allocate the channels, and take the average value through 50 simulation experiments. Figure 7 shows the performance curve comparison of the total backhaul information rate of UAVs with the transmission power of the jammer under the conditions of 8 UAVs and 12 channels. In particular, except for the change in the corresponding sub-problem-solving algorithm, other parameters are consistent with the proposed algorithm. It can be seen that the total backhaul rate of UAVs decreases with the increase in jamming power, and the rate gradually slows down. In addition, the proposed method performs better than the other four comparison algorithms because it optimizes multiple variables at the same time.
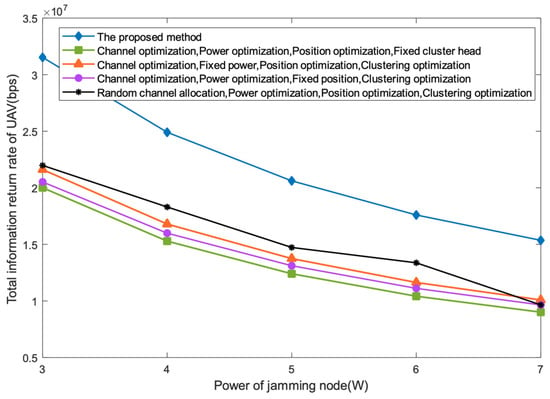
Figure 7.
Performance comparison of different algorithms.
5. Conclusions
In this paper, we constructed the cluster-based UAV swarm information transmission model, for the problems brought by malicious interference in the UAV swarm network. To solve the underlying MINLP problem, we used the alternating optimization approach and proposed a joint optimization method of spectrum resource. In particular, for the convex sub-problems of cluster head selection, channel allocation and power allocation, we used the convex optimization solver CVX to directly solve them. For the non-convex sub-problem of position optimization, we introduced the relaxation variables to convex it and then used the SCA technique to solve it. Simulation results have demonstrated the effectiveness of the proposed method in that it could reduce the impact of malicious interference and improve the sum backhaul information rate of UAV swarm. Moreover, we showed that the number of sub-channels and the power of interference nodes have strong impacts on the total backhaul information rate.
At present, the consideration of flight control factors only focuses on UAV speed and safe flight distance. In the next step of research, we will further consider the flight acceleration, flight steering angle and other parameters of a UAV. In addition, considering the load limitation of a UAV, its carrying energy is limited and its power dissipation for flight or hover is far greater than the power dissipation of communication transmission, so the energy efficiency of a UAV is also an important optimization index. It is planned to obtain a spectrum resource allocation strategy with excellent energy efficiency and spectral efficiency by introducing weight factor in UAV swarm information transmission.
Author Contributions
Methodology, D.W.; validation, D.W.; writing—original draft, D.W.; writing—review and editing, D.W., Y.Z. and Y.C.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Zeng, Y.; Zhang, R.; Lim, T.J. Wireless communications with unmanned aerial vehicles: Opportunities and challenges. IEEE Commun. Mag. 2016, 54, 36–42. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Zywiolek, J.; Ullah, I. Swarm of UAVs for network management in 6G: A technical review. IEEE Trans. Netw. Serv. Manag. 2022, in press. [Google Scholar] [CrossRef]
- Pelusi, L.; Passarella, A.; Conti, M. Opportunistic networking: Data forwarding in disconnected mobile ad-hoc networks. IEEE Commun. Mag. 2006, 44, 134–141. [Google Scholar] [CrossRef]
- Yu, J.Y.; Chong, P.H.J. A survey of clustering schemes for mobile ad-hoc networks. IEEE Commun. Surv. Tutor. 2005, 7, 32–48. [Google Scholar] [CrossRef]
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765. [Google Scholar] [CrossRef]
- Zhang, L.; Ding, G.; Wu, Q.; Zou, Y.; Han, Z.; Wang, J. Byzantine attack and defense in cognitive radio networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1342–1363. [Google Scholar] [CrossRef]
- Wu, D.; Qian, P.Z.; Chen, Y. Dynamic spectrum allocation algorithm of UAV based on Stackelberg game in the condition of malicious interference. Inf. Countermeas. Technol. 2022, 1, 71–78. (In Chinese) [Google Scholar]
- Wu, D.; Qian, P.Z.; Chen, Y. Joint optimization of user matching and spectrum resources in multi-UAV auxiliary communication. Telecomunication Eng. 2022, in press. [Google Scholar]
- Wang, H.; Wang, J.; Ding, G.; Chen, J.; Gao, F.; Han, Z. Completion time minimization with path planning for fixed-wing UAV communications. IEEE Trans. Wirel. Commun. 2019, 18, 3485–3499. [Google Scholar] [CrossRef]
- Wang, Y.S.; Hong, Y.W.P.; Chen, W.T. Trajectory learning, clustering and user association for dynamically connectable UAV base stations. IEEE Trans. Green Commun. Netw. 2020, 4, 1091–1105. [Google Scholar] [CrossRef]
- Khan, W.U.; Lagunas, E.; Ali, Z.; Javed, M.A.; Ahmed, M.; Chatzinotas, S.; Ottersten, B.; Popovski, P. Opportunities for physical layer security in UAV communication enhanced with intelligent reflective surfaces. IEEE Wirel. Commun. Mag. 2022, in press. [Google Scholar]
- Mahmood, A.; Vu, T.; Khan, W.U.; Chatzinotas, S.; Ottersten, B. Optimizing Computational and Communication Resources for MEC Network Empowered UAV-RIS Communications. TechRxiv 2022, in press. [Google Scholar]
- Preitl, Z.; Precup, R.E.; Tar, J.K.; Takács, M. Use of multi-parametric quadratic programming in fuzzy control systems. Acta Polytech. Hung. 2006, 3, 29–43. [Google Scholar]
- Singh, D.; Shukla, A. Manifold optimization with MMSE hybrid precoder for Mm-Wave massive MIMO communication. Sci. Technol. 2022, 25, 36–46. [Google Scholar]
- Zamfirache, I.A.; Precup, R.E.; Roman, R.C.; Petriu, E.M. Reinforcement learning-based control using Q-learning and gravitational search algorithm with experimental validation on a nonlinear servo system. Inf. Sci. 2022, 583, 99–120. [Google Scholar] [CrossRef]
- Guimaraes, D.A.; Floriano, G.H.F.; Chaves, L.S. A tutorial on the CVX system for modeling and solving convex optimization problems. IEEE Lat. Am. Trans. 2015, 13, 1228–1257. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Wu, Q.; Ng, D.W.K. Robust trajectory and transmit power design for secure UAV communications. IEEE Trans. Veh. Technol. 2018, 67, 9042–9046. [Google Scholar] [CrossRef]
- Wu, Y. Research on Resource Optimization for Jamming Attack in UAV Communication. Ph.D. Thesis, Army Engineering University of PLA, Nanjing, China, June 2021. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).