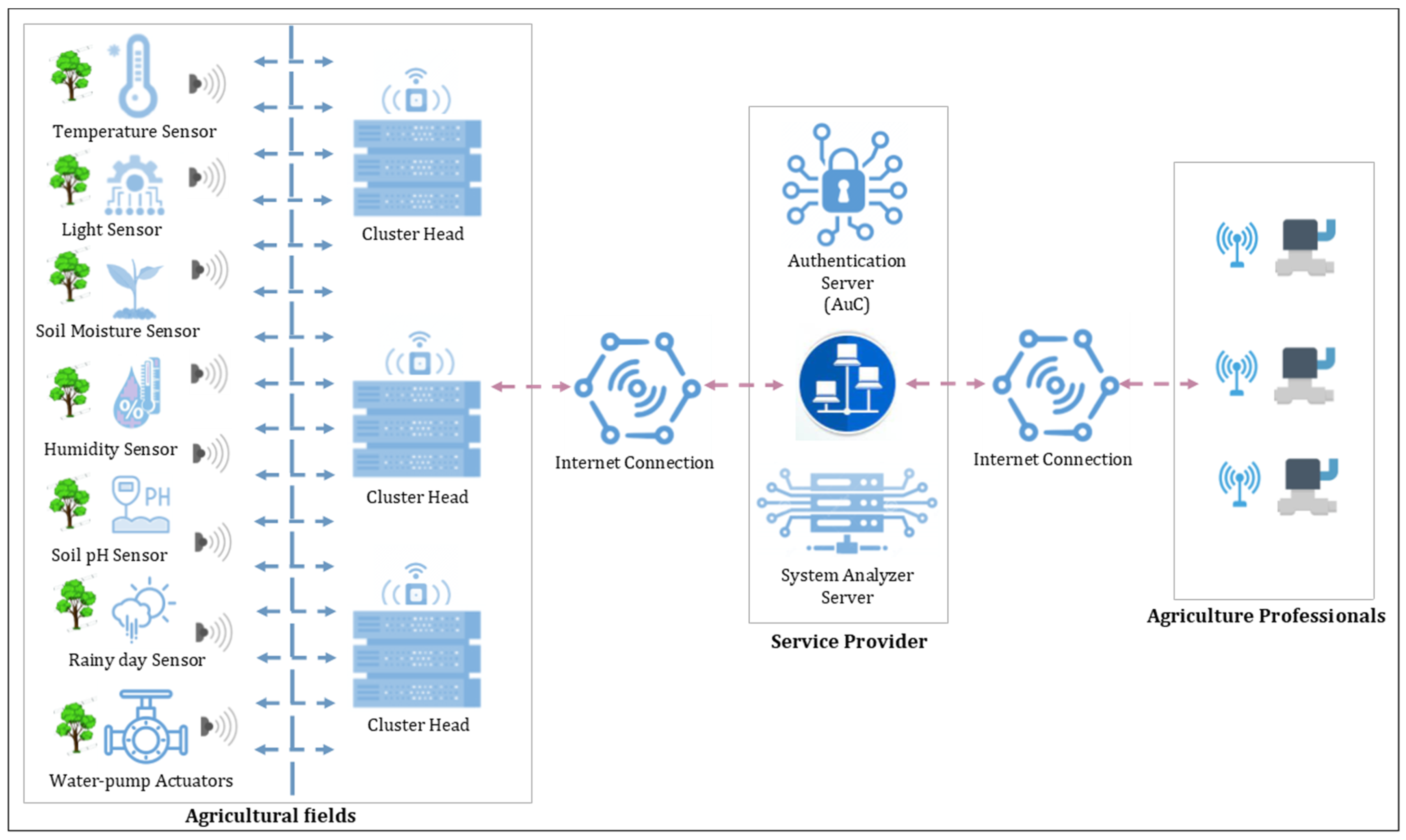
This section examines the security features of the proposed scheme. In the first part, the proposed scheme is verified in order to prove that it can provide mutual authentication formally, using the BAN logic model. The second part presents the informal security analysis, demonstrating that the proposed scheme can achieve attractive security features with the ability to resist well-known attacks. Finally, comparisons based on different security features between the proposed scheme and other authentication schemes that were proposed recently are presented.
3.1. Formal Verification Analysis
In the literature review, the BAN logic model is considered the most popular formal verification model that is used to examine the source, freshness, and originality of the authentication messages exchanged during authentication scheme execution [
20].
In the proposed scheme, the registration, login, and password change phases are executed through secure channels or are not used frequently. Therefore, this part concentrates on the soundness of the authentication phases between the main elements of the irrigation system. In this section, the BAN logic model is used to demonstrate that the authentication messages that have been exchanged throughout the authentication phases between system elements are original and fresh messages. The main used notation of the BAN logic model can be summarized as follows:
X|≡ F means that the statement (X) is considered a true statement for a principle (F);
F ⊲ X means that the statement (X) can be received and forwarded by a principle (F);
F|~ X means that the principle (F) can send a message containing statement (X);
F ⟹ X means that the principle (F) has an authority on statement (X);
⋕(X) means that the statement (X) is an original and fresh statement;
(X, Y) means that the statements (X) and/or (Y) are a portion of the formula (X, Y);
<X> Y means that the statement (X) has been merged with the statement (Y);
{X}K means that the statement (X) has been encrypted by a shared key (K);
(F → K ← Q) means that principles (F) and (Q) can communicate with each other using the shared key (K);
SK denotes a session key for the current communication session.
The authentication and key agreement phase use different parameters to support mutual authentication between APi, AuC, and CHj. Ki and Kj are symmetric secret keys that are used to encrypt authentication messages between the APi and AuC, and CHj and AuC, respectively. Kij is an agreed symmetric secret key between APi and CHj. The exchanged messages comprise fresh parameters, such as timestamps (T1, T2, T3, T4) and random numbers (R4, R5, and R6).
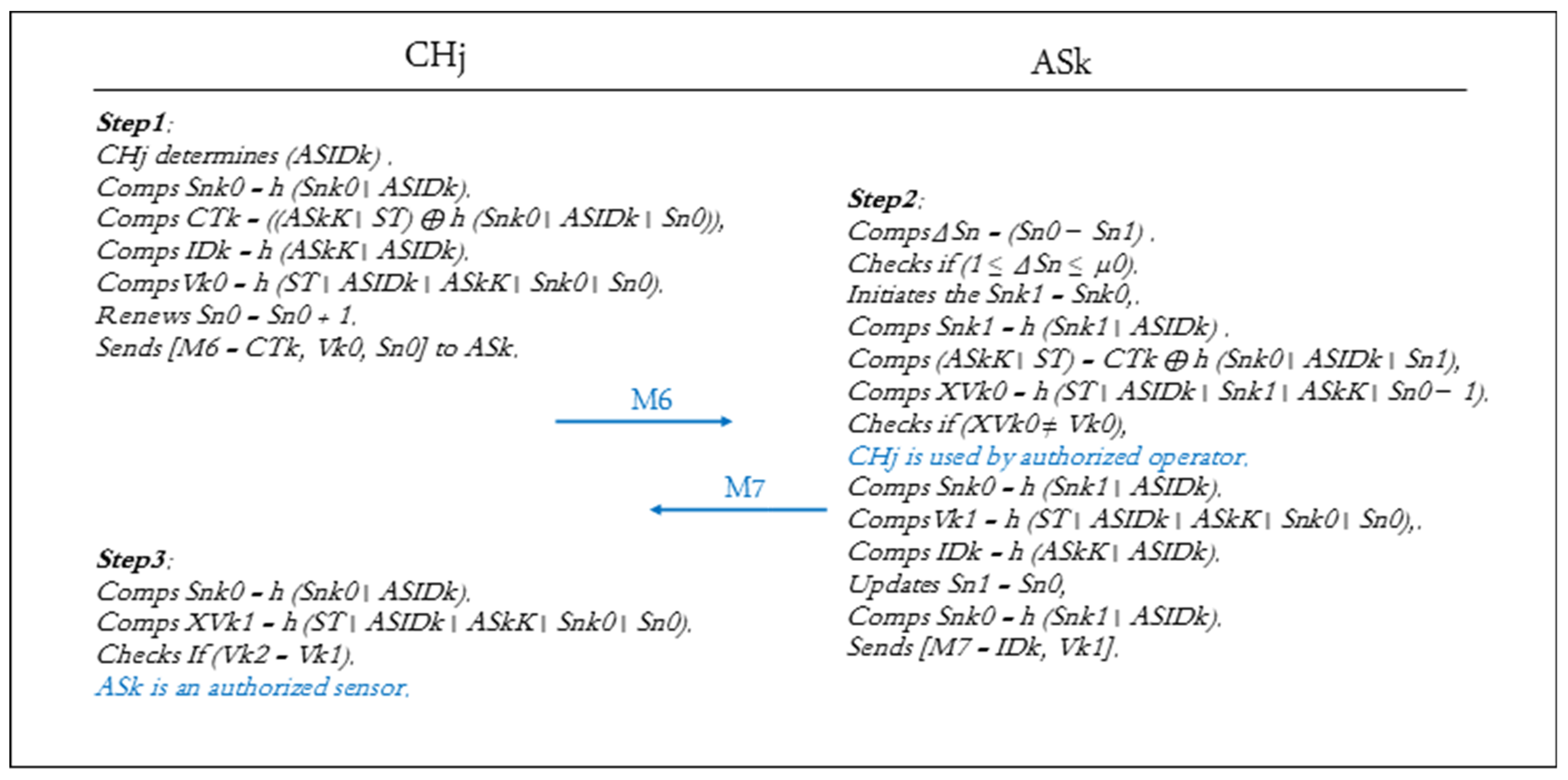
Meanwhile, to support mutual authentication in the AS authentication phase, both of CHj and ASk utilize a set of sequential numbers (Sn0, Sn1), session numbers (Snk0, Snk1), and a symmetric secret key (ASkK), which is used to encrypt the authentication messages between them. The validation and verification processes of the authentication and key agreement phase can be summarized as follows:
(1) Using M1, a1: (AuC ⊲ IDi, Vi1, CTi1: ⟨ (T0, SeNi) ⟩ Ki) can be seen. From a1, A9, Ru3, and Ru1, a2: (AuC|≡ APi|∼⟨ (T0, SeNi) ⟩ Ki) can be obtained. Using A3 and Ru2, a3: (AuC|≡ #⟨ (T0, SeNi) ⟩Ki) can be obtained. Then, using a2, a3, and Ru4, a4: (AuC|≡ APi|≡ ⟨ (T0, SeNi) ⟩Ki) can be obtained. Thus, from a3, a4, and Ru6, a5: (AuC|≡ (AuC → SK ← Ui) can be deduced, which represents Go1. Considering A4, a5, and Ru4, Q6: (AuC|≡ APi|≡ AuC → SK ← APi) can also be deduced, which leads to Go2.
(2) Using M2, b1: (CHj ⊲ CH0j, CTj0, Vj0: ⟨ (T1, R4) ⟩ Kj) can be seen. Therefore, from b1, A11, Ru3, and Ru1, b2: (CHj|≡ AuC|∼ (⟨ (T1, R4) ⟩ Kj) can be obtained. Next, using A6 and Ru2, b3: (CHj|≡ # (⟨ (T1, R4) ⟩ Kj) can be obtained. Then, using b2, b3, and Ru4, b4: (CHj|≡ AuC|≡ (⟨ (T1, R4) ⟩ Kj) can be obtained. Thus, from b3, b4, and Ru6, b5: (CHj|≡ CHj → SK ← AuC) can be deduced, which represents Go3. Then, using A7, b5, and Ru4, b6: (CHj|≡ AuC|≡ CHj → SK ← AuC) can also be deduced, which leads to Go4.
(3) Using M3, c1: (AuC ⊲ CHIDjs, CTj1, Vj1: ⟨ (T2, R5) ⟩ Kj) can be seen. Thus, from c1, A10, Ru3, and Ru1, c2: (AuC|≡ CHj|∼ (⟨ (T2, R5) ⟩ Kj) can be obtained. Next, using A3 and Ru2, c3: (AuC|≡ # (⟨ (T2, R5) ⟩ Kj) can be obtained. Then, using c2, c3, and Ru4, c4: (AuC|≡ CHj (⟨ (T2, R5) ⟩ Kj) can be obtained. Thus, from c3, c4, and Ru6, c5: (AuC|≡ AuC → SK ← CHj) can be deduced, which leads to Go5. Then, using A5, c5, and Ru4, c6: (AuC|≡ CHj|≡ AuC → SK ← CHj) can also be deduced, which leads to Go6.
(4) Using M4, d1: (APi ⊲ CTi1, Vi1: ⟨ (T3, SeNi, R6) ⟩ Ki) can be seen. Thus, from d1, A8, Ru3, and Ru1, d2: (APi|≡ AuC|∼ (⟨ (T3, SeNi, R6) ⟩ Ki) can be obtained. Next, using A1 and Ru2, d3: (APi|≡ # (⟨ (T3, SeNi, R6) ⟩ Ki) can be obtained. Then, using d2, d3, and Ru4, d4: (APi|≡ AuC|≡ (⟨ (T3, SeNi, R6) ⟩ Ki) can be deduced. Thus, from d3, d4, and Ru6, d5: (APi|≡ APi → SK ← AuC) can be deduced, which leads to Go7. Then, according to A2, d5, and Ru4, d6: (APi|≡ AuC|≡ APi → SK ← AuC) can also be deduced, which leads to Go8.
According to (1), (2), (3), and (4), the authentication and key agreement phase goals can be proven using the BAN logic model and, thus, mutual authentication can be achieved between APi, CHj, and AuC throughout this phase.
The validation and verification processes of the AS authentication phase can be summarized as follows:
(5) Using M6, e1: (ASk ⊲ CTk, Vk0: ⟨Sn0, Snk0⟩ h(ASkK)) can be seen. From e1, A17, Ru3, and Ru1, e2: (ASk|≡ CHj|∼ (⟨Sn0, Snk0⟩) h(ASkK)) can be obtained. Then, using A14 and Ru2, e3: (ASk|≡ # (⟨Sn0, Snk0⟩) h(ASkK)) can be obtained. Then, using e2, e3, and Ru4, e4: (ASk|≡ CHj|≡ (⟨Sn0, Snk0⟩) h(ASkK)) can be obtained. Thus, from e3, e4, and Ru6, e5: (ASk|≡ ASk → SK ← CHj) can be deduced, which represents Go9. Considering A15, e5, and Ru4, e6: (ASk |≡ CHj|≡ Ask → SK ← CHj) can also be deduced, which leads to Go10.
(6) Using M7, f1: (CHj ⊲ Vk2: ⟨ (Sn0, Snk0) ⟩ h(ASkK)) can be seen. Therefore, from f1, A16, Ru3, and Ru1, f2: (CHj|≡ ASk |∼ ⟨ (Sn0, Snk0) ⟩ h(ASkK)) can be obtained. Next, using A12 and Ru2, f3: (CHj|≡ # ⟨ (Sn0, Snk0) ⟩ h(ASkK)) can be obtained. Then, using f2, f3, and Ru4, f4: (CHj|≡ ASk |≡ ⟨ (Sn0, Snk0) ⟩ h(ASkK)) can be obtained. Thus, from f3, f4, and Ru6, f5: (CHj|≡ CHj → SK ← ASk) can be deduced, which represents Go11. Then, using A13, f5, and Ru4, f6: (CHj|≡ ASk |≡ CHj → SK ← ASk) can also be deduced, which leads to Go12.
According to (5) and (6), the goals of the AS authentication phase can be proven using the BAN logic model and, so, mutual authentication can be achieved between the CHj and ASk throughout this phase. Therefore, the proposed scheme can support mutual authentication among the APi, CHj, ASk, and AuC elements during the authentication phases.
3.2. Informal Verification Analysis
This section assures that the proposed scheme can achieve attractive security features and is fully protected against well-known types of attacks.
3.2.1. Security Features Achievement
Proposition 1. The proposed scheme can achieve session key agreement.
Proof. Based on the Diffie–Hellman key agreement technique, elements of the irrigation system generate a set of shared secret keys to execute the authentication and key agreement phase. Ki is used to achieving mutual authentication between the AuC and APi, Kj is used to achieve mutual authentication between the AuC and CHj, and Kij represents the agreed session key between the APi and CHj. During this authentication phase, the AuC generates P with two generator numbers (βi and βj) in order to produce the public keys (Ai0 and Aj0) for APi and CHj, respectively. The APi, according to the P-value, generates two generator numbers (δ1 and δ2) to produce the public keys (Ai1 and Ai2) for AuC and CHj. The CHj, according to the P-value, generates two generator numbers (δ3 and δ4) to produce the public keys (Aj1 and Aj2) for AuC and APi. It should be noted that all the public keys are exchanged between system elements using different one-way hash functions in order to prevent man-in-the-middle and replay attacks. □
In the AS authentication phase, the CHj generates the ASkK key randomly and sends it to the ASk in a secure manner through the use of a one-way hash function in order to achieve the mutual authentication feature between them.
Thus, the proposed scheme is able to provide the key agreement feature between the elements of the irrigation system.
Proposition 2. The proposed scheme can achieve mutual authentication.
Proof. The authentication and session key agreement phase contains set verification checkpoints that are performed to validate a fully mutual authentication between the APi, AuC, and CHj elements. Mutual authentication between the AuC and APi can be achieved as follows: The AuC verifies the M1 message via the received challenge authentication parameters [CTi0 and Vi0] in order to verify the legality of APi. In the same manner, the APi verifies the legitimacy of the AuC by verifying the M4 message via the received challenge authentication parameters [CTi1 and Vi1]. □
Similarly, the mutual authentication between AuC and CHj can be achieved as follows: the CHj verifies the M2 message via the received challenge authentication parameters [CH0j, CTj0, and Vj0] in order to verify the legality of the AuC. Next, the AuC verifies the legitimacy of the CHj by verifying the M3 message via the received challenge authentication parameters [CHIDjs, CTj1, and Vj1].
In the AS authentication phase, both ASk and CHj verify each other through two verification checkpoints, as follows: ASk verifies the authenticity of the CHj by checking the received authentication parameters through the M6 message that contains [CTk, Vk0, and Sn0], while CHj verifies the authenticity of the ASk by checking the received authentication parameters through the M7 message that contains [IDk, and Vk2].
Thus, the proposed scheme is able to support fully mutual authentication between the elements of the irrigation system.
Proposition 3. The proposed scheme can achieve anonymity and untraceability.
Proof. In the authentication and key agreement phase, in order to preserve the anonymity and untraceability for the users of the APi and CHj, all authentication messages exchanged within the authentication process do not include the actual identities, nor that of the APi (APIDi) or the CHj (CHIDj). Instead, the authentication process uses pseudonym identities (IDi and CHIDjs), which are created by one-way hash functions after completing each authentication session for the APi and CHj. Therefore, it is considered impossible for an unauthorized party to extract the actual identities of either the APi or CHj from the messages exchanged. □
Similarly, in the AS authentication phase, the exchanged messages between CHj and ASk do not include the actual identity of the ASk (ASIDk). Instead, the authentication process uses pseudonym identities (IDk).
Thus, the proposed scheme can achieve full anonymity and untraceability for the elements of the irrigation system.
Proposition 4. The proposed scheme can achieve perfect forward secrecy.
Proof. In the proposed scheme, if an adversary obtains one or more keys of the system elements, such as Ki, Kj, or ASkK, in some way, they still cannot acquire the secret session key (Kij) that is generated by the APi and CHj during the next authentication session. The reason for this is that, after completing the authentication and key agreement phase successfully, the generator numbers (δ1, δ2, δ3, and δ4) are changed for each authentication session. □
Similarly, if an adversary obtains the secret key ASkK, they still cannot acquire the secret session key for the next authentication session between the ASk and CHj, wherein this key will be changed in each authentication session between them using a one-way hash function.
Therefore, the proposed scheme can achieve fully perfect forward secrecy in future authentication sessions.
3.2.2. Resistance against Well-Known Attacks
Despite the fact that the exchanged messages between the elements of the system can be blocked, modified, replaced, tracked, and retransmitted over insecure communication channels by the opponent, this section demonstrates that the proposed scheme can withstand well-known attacks.
Proposition 5. The proposed scheme can resist desynchronization attacks.
Proof. In order to support anonymity and untraceability, the proposed scheme uses a set of pseudonym identities, such as APIDi, CHIDj, and ASIDk, along with a set of the one-way hash functions to renew such identities for each authentication session. Furthermore, to support the perfect forward secrecy feature, the proposed scheme uses set verification codes, such as Vi0, Vj0, Vj1, Vi1, Vix, Vk0, and Vk1, with a set of the one-way hash functions, random numbers, and timestamps to renew such codes. Therefore, the synchronization of the computed hash values must be preserved in the proposed scheme between the APi, CHj, ASk, and AuC. In the authentication and key agreement phase, the synchronization of the APIDi and hash chain values of SeNi will be guaranteed by APIDip and APIDis in each authentication session between the APi and AuC. Similarly, in each authentication session between the CHj and AuC, the values of CHIDjp and CHIDjs are used to ensure that the CHIDj and the hash chain value of SeNj are synchronized. In the AS authentication phase, the synchronization of the ASIDk and hash chain values of Snk0 will be guaranteed by IDk in each authentication session between the ASk and CHj. As the one-way hash functions used in the proposed scheme are collision hash functions, even if the opponent can block authentication messages, the APi, CHj, ASk, and AuC can resynchronize the hash values between them. To make the discussion more precise regarding the ability of the proposed scheme to withstand desynchronization attacks, consider the following possible desynchronization attack scenarios:
S1: Suppose the opponent has blocked M1. Obviously, this will not affect the synchronization between APi and AuC during the next authentication session, wherein the elements of the system have not yet begun renewing the values of the IDi nor h(SeNi). Thus, this scenario will be ignored.
S2: Suppose the opponent has blocked M2. Obviously, this will not affect the synchronization between the APi, CHj, and AuC during the following sessions. In this case, the hash values of SeNj and CHIDjs have only been updated on the AuC. However, M3 has not been received by the AuC. Thus, the AuC can resend M2 again, using a new CH0j with distinct values of T1 and R4. Alternatively, the CHj using the value of ΔCH01j can resynchronize and update the hash values of SeNj and CHIDjs, as in the AuC. Thus, the AuC can resynchronize the next session with the CHj.
S3: Suppose the opponent has blocked M3. Obviously, this will not affect the synchronization between the APi, CHj, and AuC during the next session. This scenario is similar to S2. In this case, the hash values of the SeNj and CHIDjs have been renewed in AuC and CHj. However, M3 has not been received by the AuC. Thus, the AuC will send M2 again, using distinct values for T1 and R4. Then, the CHj, using the value of ΔCH01j, can resynchronize and renew the hash values of SeNj and CHIDjs, as in the AuC. Next, the CHj can send M3again, using new values for T2 and R5. Thus, the AuC can resynchronize in the next session with CHj.
S4: Suppose the opponent has blocked M4. Obviously, this will not affect the synchronization between the APi, CHj, and AuC during the next session. In this case, the hash values of SeNi and APIDis have not yet been renewed in the APi nor AuC, and only synchronization is needed for the hash value of IDi in the APi. However, M4has not been received by the APi. Thus, the APi can send M1 again, using a distinct value of T0. As the value of IDi for the AuC is equal to APIDis, the AuC can send M4 using the new values for T3 and R6. Thus, the APi can resynchronize in the next session with AuC.
S5: Suppose the opponent has blocked M5. Obviously, it will not affect the synchronization between the APi, CHj, and AuC during the next session. In this case, the hash values IDi and APIDip have been renewed in the APi nor AuC, wherein IDi = APIDip, and the (SeNi) has been renewed in the APi, but has not yet been updated on the AuC. However, the APi will not be able to receive processed data from the AuC. Therefore, APi can send M1 again, using a distinct value of T0. As the value of IDi for the AuC will be equal to APIDip and APIDis ≠ Φ, the AuC will send M4 again to the APi, using distinct values of T3 and R6. Therefore, the APi can send M5 and resynchronize in the next session with AuC.
S6: Suppose the opponent has blocked M6. Obviously, this will not affect the synchronization between the ASk and CHj during the next session. In this case, the values of CTk, Snk0, and IDk have only been renewed in the CHj. However, M7 has not been received by the CHj. Therefore, the CHj can send M6 using distinct values of ASkK and Sn0. Then, the ASk, according to the ΔSn value, can renew the IDk, S0k1, and Snk1 values, as in the CHj. Thus, the CHj can resynchronize in the next session with ASk.
S7: Suppose the opponent has blocked M7. Obviously, this will not affect the synchronization between the ASk and CHj during the next session. In this case, the values of CTk, IDk, and Snk0 have been updated on both ASk and CHj. However, M7 has not been received by the CHj. Therefore, the CHj can send M6, using distinct values for ASkK and (Snk0. The ASk, using the new value of ΔSn, can renew the hash values of IDk, SSk1, and SNk1, as in the CHj. Next, the ASk can send M7 again. Thus, the CHj can resynchronize in the next session with ASk. □
Thus, based on the analysis of the above-discussed attack scenarios (S1–S7), the proposed scheme can resist desynchronization attacks.
Proposition 6. The proposed scheme can resist impersonation attacks.
Proof. To make the discussion more precise regarding the ability of the proposed scheme to withstand impersonation attacks, consider the following possible impersonation attack scenarios:
S8: Suppose the opponent has intercepted M1, which is sent to the AuC to impersonate the APi, wherein CTi0 = EKi (T0‖Ai2‖CHIDj) and Vi0 = h (T0‖Ai2‖SeNi). The decryption of CTi1 is not an obtainable value, wherein the opponent cannot know Ki. Besides, the actual SeNi and Ai2 values are not available. Thus, the opponent would be unable to impersonate APi by computing Vi0 with completely separate T0 and SeN1values.
S9: Suppose the opponent has intercepted M2, which is sent to the CHj to impersonate the AuC, wherein CTj0 = EKj (T1‖R4‖Ai2) and Vj0 = h (T1‖Ai2‖CHIDjp‖R4). The decryption of CTj0is not an obtainable value, wherein the opponent cannot know Kj, which is considered an invisible value. Besides, the actual CHIDjp and Aj2 values are not available. Thus, the opponent would be unable to impersonate the AuC by computing Vj0 with completely separate T1 and R4 values.
S10: Suppose the opponent has intercepted M3, which is sent to the AuC to impersonate the CHj, wherein CTj1 = EKj (T2‖R5‖Aj2) and Vj1 = h (T2‖Aj2‖CHIDjs‖R5). The decryption of CTj1 is not an obtainable value, wherein the opponent cannot know Kj (an invisible value). Besides, the actual CHIDjp and Aj2 values are not available. Thus, the opponent would be unable to impersonate the AuC by computing Vj0 with completely separate T2 and R5 values.
S11: Suppose the opponent has intercepted (M6), which is sent to the ASk to impersonate the CHj, wherein the CTk = ((ASkK‖ST) ⊕ h (Snk0‖ASIDk‖Sn1)), IDk = h (ASkK‖ASIDk), and Vk0 = h (ST‖ASIDk‖ASkK‖Snk0‖Sn0). Neither of the CTk nor IDK is obtainable values, wherein the opponent cannot know ASkK, which is considered an invisible value. Besides, the actual ASIDk and Snk0 values are not available. Thus, the opponent would be unable to impersonate the CHj by computing Vk0 with completely separate ASkK and ASIDk values. □
Therefore, according to the above-discussed attack scenarios (S8–S11), the proposed scheme can resist impersonation attacks.
Proposition 7. The proposed scheme can resist replay attacks.
Proof. The proposed scheme uses a set of timestamps, random numbers, and serial numbers, which are incorporated into the exchange authentication messages. In order to make the discussion more precise regarding the ability of the proposed scheme to withstand replay attacks, consider the following possible replay attack scenarios:
S12: Suppose the opponent has retransmitted M1 that was sent by the APi. The AuC will refuse the authentication request and close the authentication session, as T0 has become out of range.
S13: Suppose the opponent has retransmitted M2 that was sent by the AuC. The CHj will refuse the authentication request and close the authentication session, as ΔCH01j will be out of the irrigation system specifications and T1 has become out of range.
S14: Suppose the opponent has retransmitted M6 that was sent by CHj. The ASk will refuse the authentication request and close the authentication session, as ΔSn will be out of the irrigation system specifications. □
Thus, based on the analysis of the above-discussed attack scenarios (S12–S14), the proposed scheme can resist replay attacks.
Proposition 8. The proposed scheme can resist stolen password table attacks.
Proof. The proposed scheme does not have an AP password table or a CHj password table stored in the AuC at all. □
Thus, the proposed scheme will not be exposed to stolen verifier table attacks and can resist such attacks.
Proposition 9. The proposed scheme can resist incorrect password login attacks.
Proof. Suppose the opponent tries to use an incorrect password. In the proposed scheme, the password verification code APVi = h ((SeNi‖Si) ⊕ (Ci‖Ai0)) is stored in the smart card of the APi, which is used to validate the APi’s password. If the APi enters an incorrect password (PWi) or security code (Si), the verification codes (XAPVi ≠ APVi) are not equal, and the SCi will refuse the login request. Similarly, the CHj has the password verification code CHVj = h ((SeNj‖Sj) ⊕ (Cj‖Aj0)) stored in the smart card of the CHj, which is used to validate the operator password of the CHj. If the operator enters an incorrect password (PWj) or security code (Sj), the verification codes (XCHVj ≠ CHVj) will not be equal, and the SCj will refuse the login request. □
Therefore, the proposed scheme can resist an incorrect password login attack without increasing the network overhead and going back to the AuC.
Proposition 10. The proposed scheme can resist smartcard loss attacks.
Proof. Suppose the opponent attempts to steal the concealed data from a smartcard, wherein the proposed authentication scheme utilizes three factors (3F) during the login phases (i.e., identity, password, and security code). Even if an opponent is able to steal such concealed data from a smartcard, they will be incapable of logging in, whether as an APi user or CHj operator. This is as the opponent also requires knowledge of the actual user’s identities (APIDi, CHIDj), (PWi, PWj), and (Si, Sj) in order to create a login message. □
Thus, the proposed scheme can resist smartcard loss attacks without increasing the network overhead and going back to the AuC.
Proposition 11. The proposed scheme can resist man-in-the-middle attacks.
Proof. Suppose the opponent tries to forge either legitimate challenge or response messages. As the proposed scheme uses the Diffie–Hellman key agreement technique, the values of public keys (A0i, Aj0, A1i, A1j, A2i, and Aj2) are exchanged as concealed values between the elements of the irrigation system within hash values. Besides, challenge or response messages that have been exchanged are protected by (Ki and SeNi) and (Kj and SeNj), and an opponent without these pairs of keys cannot forge such legitimate messages. □
Thus, the proposed scheme can resist man-in-the-middle attacks.
Proposition 12. The proposed scheme can resist insider privileged attacks.
Proof. Suppose the inside workers within the service provider try to carry out privileged insider attacks. In the proposed scheme, when the APi executes the registration phase, the (PWi, Si) values are sent as hidden values using a hash value Ci = h (APIDi‖PWi‖Si). Similarly, when the CHj executes the registration phase, the (PWj, Sj) values are sent as hidden values using a hash value Cj = h (CHIDj‖PWj‖Sj). The collision feature of the one-way hash function, which is used to compute (Ci, Cj), can stop the insider from revealing the actual values. □
Thus, the proposed scheme can resist insider privileged attacks.