Abstract
The completeness of event logs and long-distance dependencies are two major challenges for process mining. Until now, most process mining methods have not been able to discover long-distance dependency and assume that the directly-follows relationship in the log is complete. However, due to the existence of high concurrency and the cycle, it is difficult to guarantee that the real-life log is complete regarding the directly-follows relationship. Therefore, process mining needs to be able to deal with incompleteness. In this paper, we propose a method for discovering process models including sequential, exclusive, concurrent, and cyclic structures from incomplete event logs. The method analyzes the co-occurrence class of the log and the model and then uses the technology of combining the behavior profile and co-occurrence class to obtain the communication behavior profile of the co-occurrence class. Furthermore, a method of constructing a substructure from the event log using the co-occurrence class is presented. Finally, the whole process model is built by combining those substructures. The experimental results show that the proposed method can discover process models with complex structures involving cycles from incomplete event logs and also can deal with long-distance dependency in the event log. Meanwhile, the discovered process model has a good degree of consistency with the original model.
1. Introduction
The operation of an information system will generate a large number of event logs. These event logs record what activities will occur and in what order they occur in the business process. In addition, there is much other related information, such as executors and execution resources [1]. Process mining extracts valuable insights about processes from these event logs to analyze, monitor, and improve actual business processes. According to van der Aalst [2], process mining techniques can be divided into three directions: (1) process discovery, which uses event logs to generate process models; (2) conformance checking, which compares the behaviors generated by the model with the behaviors in the event log. The aim is to detect, locate, and explain deviations and to measure the severity of these deviations; and (3) process enhancement, which aims to improve or extend an existing process model using information about the actual process recorded in some event log. To avoid “spaghetti-like” process models, process discovery usually consists of three steps: first, preprocessing the noise behavior in the event log, then discovering the process model from the preprocessed event log, and finally evaluating the quality of the process model [3]. This paper does not consider log preprocessing steps and only focuses on how to discover process models from event logs.
In addition to noise, the real-life event log is often incomplete, that is, it is impossible to show all possible behaviors [4]. Most of the existing process mining algorithms assume that the log is weakly complete, i.e., they assume that the direct successor relationship is complete, the causal dependency is complete, or that the log is complete [5]. Obviously, the assumption that the log is complete is impossible in reality. One of the factors leading to incomplete logs is high concurrency or a cycle. In [6], the authors proposed the concept of a conjoint occurrence class, which solved the incompleteness caused by high concurrency and illustrated how to discover process models from incomplete logs. However, this method has difficulty coping with cycles and does not consider the relationship between the model-based conjoint occurrence class and the log-based conjoint occurrence class.
Based on [6], we further provide a novel concept of a model-based co-occurrence class to capture activities that are always occur together in any executable trace of the model. Meanwhile, the relationship between the model-based co-occurrence class and log-based co-occurrence class is analyzed. Then, how to construct a cyclic structure containing multiple types of substructures is elaborated besides sequential, exclusive, and concurrent structures. Finally, a method of discovering process models from incomplete event logs using the technology of combining the co-occurrence class and behavior profile is presented. The proposed method in this paper solves the problem of the long-distance dependencies and incompleteness caused by the cycle or high concurrency. The experimental results show that when the log is incomplete, the proposed method can still build a process model that has a high degree of consistency with the original model.
In the following, Section 2 first discusses related work. The problem statement is given in Section 3. Section 4 explains some basic knowledge about the co-occurrence class of the log and model. In Section 5, the method of constructing a substructure using the co-occurrence is described. In Section 6, we report on experimental results. Conclusions and future work are presented in Section 7.
2. Related Work
Until now, a series of process mining methods have been proposed, mainly including a directly-follows relationship between activities [7], domain-based theory [8,9,10,11], genetic-based algorithm [12,13], frequency-based technology [14,15,16], cut-based technology [17], abstraction-based technology [18], and so on. Of these, the method based on the directly-follows relationship between activities can only find some subclasses of Petri nets and cannot guarantee soundness and fitness, such as the algorithm [19] and its derivatives [20,21,22]. The technique of domain-based theory mainly includes language-based domain miners [8], state-based domain miners [9], and integer linear programming (ILP) miners [10,11]. Although these methods guarantee the fitness of the model, they cannot guarantee the soundness of the model. The mining method based on the genetic algorithm iterates the process model until the acceptable quality is obtained. It selects the fittest individuals and generates new individuals using two genetic operators, such as crossover and mutation [12,13]. Although the process model obtained by this method has good fitness, it consumes a great deal of running time and cannot guarantee the soundness of the model.
The frequency-based method takes frequencies of events and sequences into account when constructing a process model, such as the Heuristic Mining (HM) algorithm [14], flexible heuristics miner (FHM) [15], or Fodina [16]. It calculates the dependency measure between activities and filters noise behavior by removing causal dependencies below a given threshold. This technique sometimes generates a process model with incorrect behaviors; meanwhile, soundness and fitness are not guaranteed. Cut-based technology, such as the Inductive Miner (IM) [17] and Inductive Miner-infrequent (IMi) algorithms [22], adopts the idea of divide and conquer and uses four cuts to recursively split the log into several sub-logs until it cannot find a cut. Subsequently, it constructs the sub-model from each sub-log. Finally, a block-structured process model can be built by merging all sub-models. Although the soundness of the process model is guaranteed, its precision is very low, that is, the discovered process model is over-generalized. Process discovery algorithms based on abstract techniques, such as fuzzy miner [18], produce models without executable semantics, so neither soundness nor fitness is guaranteed. In [23], state-of-the-art process discovery methods based on the split gateway discovery were presented. Split Miner combines a novel method to filter directly-follows graphs induced by event logs, with a method for identifying combinations of split gateways that accurately capture concurrency, conflict, and causal relations between neighbors in directly-follows graphs. Split Miner is the first method to guarantee that the discovered BPMN model is deadlock-free and is not restricted to producing a block-structured model. However, when the number of activities in the log is large, the time complexity of the algorithm is high.
At present, most process discovery methods can deal with noises [24,25,26,27,28]. Apart from noise, another problem of the real event log is incompleteness [29]. Since the event log only records the observed behaviors of the business process during its past, it cannot capture the behaviors that will occur in the future. Hence, the event log is usually incomplete. However, few algorithms have the capability of handling the incompleteness of event logs. In [17], based on the IM algorithm, a process discovery algorithm handling incomplete event logs was proposed, which introduced probabilistic behavioral relations that are less sensitive to incompleteness. It adopted the divide-and-conquer approach in the same way as IM and searched for an optimal partition of activities by estimating probabilities of the relations between activities. However, the method proposed in [17] has difficulty in handling long-distance dependency and cannot handle incompleteness caused by high concurrency well. In [6], the authors presented conjoint occurrence classes to handle the incompleteness caused by the concurrency and cycles. This method can infer the causal and concurrent behavior not exhibited in the log. However, the method in [6] cannot handle loop structures and the long-distance dependency hidden in the log. In this work, a co-occurrence class based-log and based-model are provided, respectively, to solve the incompleteness and long-distance dependency; then, we propose the method of discovering a process model with multiple different structures including cycles.
3. Problem Statement
At present, most process discovery methods cannot discover indirect dependencies between activities, such as long-distance dependencies [15] (such as S1 and S2 in Figure 1). The behavior profile uses the weak order relationship between activities to describe the behavior dependency relationship among activities, involving strict order relation, exclusiveness relation, and interleaving order relation [30]. Among them, the exclusiveness relation is the strictest relationship, indicating that two activities cannot appear in any trace at the same time. However, the behavior profile only describes the behavior dependency between activities and cannot capture the actual occurrence dependency and causal dependency of activities in the actual business process, i.e., whether the occurrence of one activity will affect the occurrence of another activity and vice versa.
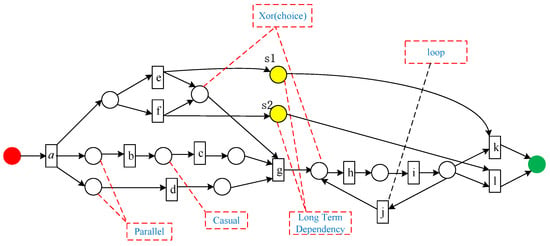
Figure 1.
A Petri net with long-distance dependencies.
The strict order relationship only indicates that there is a sequence constraint between activities, but it cannot illustrate whether an occurrence dependency relationship between activities exists. As shown in Figure 2, activity A and activity B are both in a strict order relationship. From Figure 2 and Table 1, we can know the strict order relationship only indicates that if activities A and B occur at the same time, then activity A must occur before activity B. Hence, the sequence constraint of activity A and activity B is captured, while the actual occurrence dependency between activity A and activity B cannot be captured.
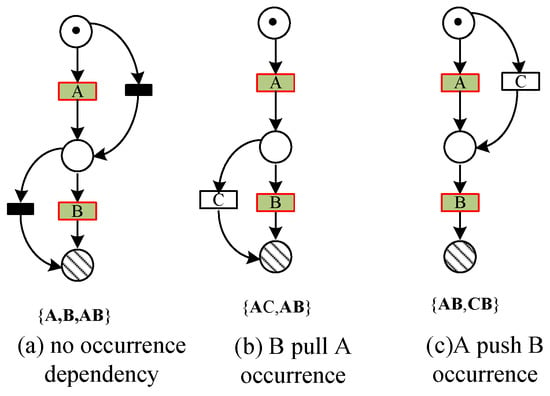
Figure 2.
An example of the strict order relation.

Table 1.
The relationship between activity A and activity B shown in Figure 2.
The interleaving order relationship only indicates that there are no occurrence order constraints between activities, but it does not mandate that activities must be enabled at the same time. For example, activity A and activity B are in an interleaving order relationship in Figure 3. However, only activity A and activity B in Figure 3a are concurrent, which is also the most typical structural feature corresponding to the interleaving order relationship. Table 2 shows the occurrence order and occurrence dependency of activities A and B as shown in Figure 3. Table 2 indicates that the occurrence dependency constraint between activities is difficult to capture only according to the interleaving order relationship.
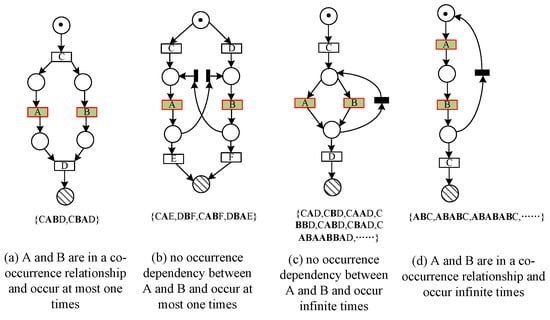
Figure 3.
An example of the interleaving order.

Table 2.
The relationship between activity A and activity B shown in Figure 3.
Another problem is that the event log represents the behavior that has been observed during the actual operation of the system and cannot contain all possible behaviors of the system. Thus, the log is often incomplete. One of the problems faced by process discovery is that the log cannot contain enough information to discover a process model, i.e., the log might be incomplete [29]. This might cause the discovered process model to exclude the actual behaviors or contain some additional behaviors that are not in the real process. The existing process mining usually assumes that either the activities are complete or the directly-follows relationships between activities are complete. However, when there exist high concurrency behaviors, the second assumption is often unrealistic. For example, a process consists of 10 concurrent activities, and the log consists of about 10,000 cases. There are 10! = 3,628,800 possible sequences caused by concurrent behavior. Obviously, the number of cases in the log is far less than the actual possible sequence, so it is impossible that the log samples all possible directly-follows relationships between activities. There are many factors leading to logs being possibly incomplete. However, cycles and high concurrency are important factors. When the number of activities on concurrent branches is large, it is impossible for the event log to sample all possible sequences of activities. Figure 4a shows an initial process model of each concurrent branch containing two activities. An incomplete event log is generated by the model , where .The process model obtained by applying the IM algorithm and the HM algorithm to the event log is shown in Figure 4b,c. The precision of the model is 1, and the fitness is low. The fitness and precision of the model are both 1, but this model is overfitting. Therefore, incomplete logs caused by concurrency will lead to low-quality process models or even erroneous results.
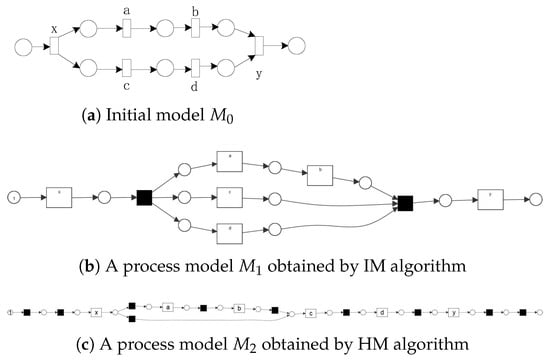
Figure 4.
Process mining results of incomplete logs caused by high concurrency.
To solve the above problems, a method for discovering the process model from incomplete logs is presented. We adopt the technology of combining behavioral profiles and co-occurrence classes to analyze the structural characteristics and communication behavior relationships of co-occurrence classes, then merge several co-occurrence classes into a larger substructure to find the process model. The research framework of the proposed method is shown in Figure 5. The proposed method solves the problem that behavior profiles cannot capture the occurrence dependency between activities and the incompleteness caused by high concurrency. The experimental results show that the proposed method can find long-distance dependency, and the discovered process model has a good consistency with the original model.
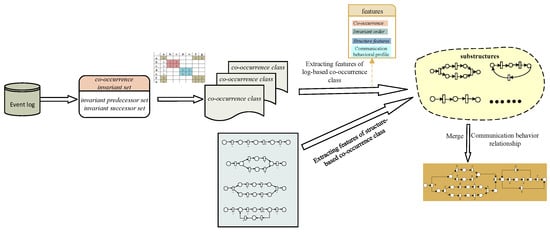
Figure 5.
Framework of the proposed method.
4. Construction Method of Co-Occurrence Class
In the actual business process, some activities may be mandatory nodes of the whole process, and the occurrence of some activities will lead to the subsequent occurrence of other activities, or the occurrence of some activities can be accompanied by the occurrence of some activities that precede it. Obviously, in addition to the constraints on the order of occurrence, there also exist occurrence dependencies between activities. Therefore, this section analyzes the invariant predecessor set and invariant successor set of activities to capture the co-occurrence invariant set of activities in the log or model. Activities are divided into several subsets with co-occurrence dependency in the log or model through the co-occurrence classes. Section 4.1 presents the method of discovering co-occurrence classes from the event log and analyzes the characteristics of co-occurrence classes. Section 4.2 provides the method of discovering co-occurrence classes from the model.
4.1. Discovery of Co-Occurrence Classes from Logs
The event log shows the actual execution of activities in the business process. By analyzing the occurrence dependencies between activities in each trace, the occurrence dependency between activities in the log can be found. In the following, the relevant definitions of trace handling operations are given.
Definition 1
(Trace handling operations [6]). Let L be an event log, is an activity set over L. For , if there exists a trace , such that , where :
(1) indicates that the k-th element in the trace σ is an activity a;
(2) such that ;
(3) The direct predecessor activity of the i-th activity in the trace σ is defined as ;
(4) The direct successor activity of the i-th activity in the trace σ is defined as ;
(5) Invariant set of activities that appear before activity a in trace σ is denoted as ,
(6) Invariant set of activities that appear after activity a in trace σ is denoted as ,
For example, considering a trace , using Definition 1, we obtain ,, , , , , , .
consists of activities appearing between two activities a together and before the first occurrence of the activity a. consists of activities appearing between two activities a together and after the last occurrence of the activity a. Therefore, and denote the set of possible activities that must occur before the activity a and after the activity a in any trace , respectively. To capture the predecessor and successor activities that have co-occurrence dependencies with an activity in the log, Definition 2 gives the invariant predecessor set and the invariant successor set of the activity in the log.
Definition 2
((Log) Invariant predecessor set, Invariant successor set). Let L be an event log, is an activity set over L. For , invariant predecessor set of activity a is defined as , and invariant successor set of activity a is defined as .
The invariant predecessor set in Definition 2 represents the set of activities that always occur before the activity a in any trace of the log. Similarly, the invariant successor set represents the activity set that always occurs after the activity a in any trace of the log. The activities in the invariant predecessor set or the invariant successor set not only have a strict order relationship with the activity a but also have a co-occurrence relationship with the activity a. Definition 3 further gives the concept of a co-occurrence invariant set based on Definition 2.
Definition 3
((Log) Co-occurrence invariant set). Let L be an event log, is an activity set over L. For , co-occurrence invariant set of activities a is denoted as .
In Definition 3, presents a set of activities that occur simultaneously with the activities a in any trace of the log L. There is not only a behavior dependency but also a co-occurrence dependency between them.
For example, given an activity log as shown in Table 3, the process model shown in Figure 6 is the original model of the log . This paper takes the event log as an example to illustrate the solution process of our proposed method.

Table 3.
An event log .
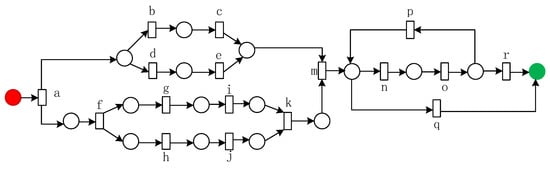
Figure 6.
The original model of log .
Table 4 presents the invariant predecessor set, invariant successor set, and co-occurrence invariant set for each activity in the event log .

Table 4.
Invariant set of all activities in the log .
Since the co-occurrence invariant set represents the set of activities that appear simultaneously with the current activity in all traces of the log, based on this, this paper adopts the co-occurrence invariant set to capture the occurrence dependency between activities. To facilitate the discovery of a co-occurrence dependency among several activities, the activities in the log can be divided into several subsets with equivalent behavior by using the co-occurrence invariant set. Therefore, Definition 5 introduces the concept of co-occurrence classes.
Definition 4
(Co-occurrence matrix). Let L be an event log, and is an activity set over L and . Matrix is called as the co-occurrence matrix, where represents the co-occurrence relation between , if ; then, .
Definition 5
(Co-occurrence class). Let L be an event log, is an activity set over L. is a co-occurrence matrix of the log L. , an activity set is called a co-occurrence class if and only if ,where .
Definition 5 indicates that there exists a co-occurrence dependency between all activities in the co-occurrence class; that is, they always appear in a trace of the log together. Table 5 shows the co-occurrence relationship matrix of the event log.

Table 5.
Co-occurrence matrix for log .
Using Definition 5, we can get co-occurrence classes from Table 5:
, where , , , , , , , .
The co-occurrence class has some interesting properties. The relevant conclusions and proofs are given below.
Property 1
(Co-occurrence). Let L be an event log, is a co-occurrence class got from event log L. For , if such that , then for , holds.
Proof.
If such that , then and . So and . Obviously, . Therefore, cannot both belong to . There exists a contradiction. □
Property 2
(Invariant order). Let L be an event log, is a co-occurrence class got from the event log L. If , activities satisfy partial order relation , for , if , then activities also satisfy partial order relation in a trace . i.e., if activities in occurred in a trace, they should occur in the same order.
Proof.
Assume there exist two activities that appear in two different traces in different orders, and let two activities be , holds in trace , but holds in trace . Thus, , . Clearly, .Therefore, it is impossible for to belong to the same co-occurrence class at the same time. There exists a contradiction. □
Algorithm 1, Algorithm 2, and Algorithm 3, respectively, show how to obtain the invariant predecessor set, invariant successor set, and co-occurrence class of any activity from the log.
| Algorithm 1: An invariant predecessor set of any activity |
 |
| Algorithm 2: An invariant successor set of any activity |
 |
| Algorithm 3: Getting co-occurrence classes from the event log |
 |
In Algorithm 1, Step 2 initializes the invariant predecessor set to an empty set, Steps 3–9 solve the invariant predecessor set of the activity in each trace, Steps 10–15 get the invariant predecessor set of the activity in the log, and Steps 11–14 indicate that once the invariant predecessor set becomes an empty set, the algorithm is stopped.
In Algorithm 2, Step 2 initializes the invariant successor set to an empty set, Steps 3–9 solve the invariant successor set of the activity in each trace, Steps 10–15 obtain the invariant successor set of the activity in the log, and Steps 11–14 indicate that once the invariant successor activity set becomes an empty set, the algorithm is stopped.
Steps 1–5 in Algorithm 3 are used to find the invariant set of any activity, Steps 7–11 initialize each element in the co-occurrence relationship matrix to 0, Steps 12–20 update the value of the co-occurrence relationship matrix according to the invariant activity set, Steps 22–25 set each activity to an initial co-occurrence class, and Steps 21–37 construct all possible co-occurrence classes by merging the initial co-occurrence classes according to the co-occurrence relationship matrix.
4.2. Discovering Co-Occurrence Classes from Models
The co-occurrence invariant relationship of activities in the log is closely related to their structural relationship in the model. To facilitate the discovery of their structural relationship in the model according to the co-occurrence invariant relationship of activities in the log, we present some definitions related to the invariance of activity occurring in the model.
Definition 6
(Execution sequence). Execution sequence of the process model is defined as an executable sequence of the form from the start activity to the end activity of the process model. All execution sequences of the process modelN are denoted as .
Definition 7
((Model) Invariant predecessor set, Invariant successor set). Let N be a process model, be an activity set of model, and be a set of executable sequences of the model. For , the invariant predecessor set of activity a is defined as , and the invariant successor set of activity a is defined as .
The set of invariant predecessors of activity a in model N represents the set of activities that occur before a in all executable sequences of the model N. Similarly, the set of invariant successors of activity a in the model represents the set of activities that occur after a in all executable sequences of the model N.
Definition 8
((Model) co-occurrence invariant set). Let N be a process model and be an activity set of models. For , the co-occurrence invariant set of activity a is defined as .
Definition 8 denotes , which represents the set of activities that always occur simultaneously with the activity a in any execution sequence of the model.
Definition 9
((Model) co-occurrence class). Let N be a process model and be an activity set of the model, where , is the co-occurrence relationship matrix of the model N. For , a set of activities is called as a co-occurrence class if and only if , where .
Clearly, Definition 9 denotes , if , then , i.e., activities in a co-occurrence always occur simultaneously in an execution sequence.
According to Definition 9, Table 6 gives the invariant predecessor set, invariant successor set, and co-occurrence invariant set of each activity in the four basic structures (as shown in Figure 7). Table 7 presents co-occurrence classes of the four basic structures obtained from Table 6.

Table 6.
Invariant set of activities in four basic structures.
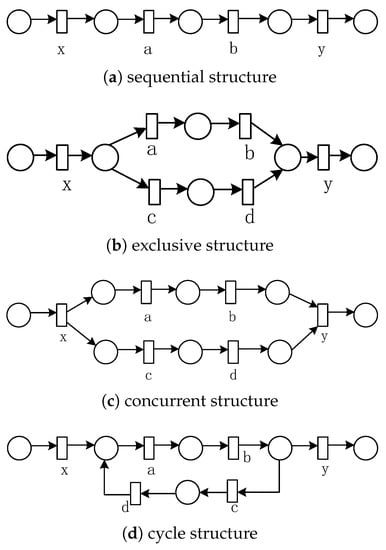
Figure 7.
Four basic structures.

Table 7.
Co-occurrence classes of the four basic structures.
Table 7 shows that the exclusive structure and the cyclic structure have the same set of co-occurrence classes, the sequential structure has only one co-occurrence class that contains all activities, and the concurrent structure is decomposed into two co-occurrence classes according to the concurrent branch, one of which contains the and-gateway activities.
5. Building Substructures Using Log Co-Occurrence Classes
Section 4 presents the solution method for the co-occurrence invariant set of any activity in the log or model; then, the co-occurrence class is provided. This section further illustrates how to leverage the co-occurrence classes in the event log to build a model substructure that includes the sequence, conflict, concurrency, and cycle. Section 5.1 presents the method of constructing the basic substructure from a single co-occurrence class, and Section 5.2 addresses the communication behavior relationship between the co-occurrence classes and how to combine multiple co-occurrence classes into larger substructures.
5.1. Building the Basic Substructure from a Single Co-Occurrence Class
Properties 1 and 2 indicate that although activities in the co-occurrence class always occur simultaneously in the same order, the structural features of activities in the co-occurrence class are unknown. Theorems 1, 2, and 3, respectively, give their corresponding substructures according to the behavioral relationship of activities in the co-occurrence class in the log.
Theorem 1
(A substructure corresponding to the co-occurrence class with a directly-follows relationship). Let L be an event log and , , if holds, then form a sequential substructure.
Proof.
We assume activities constitute non-sequential substructures, i.e., these activities can constitute the substructure of a cycle, concurrency, or conflict except sequence. From the characteristics of a cycle, concurrency, and conflict substructure, it is known that activities cannot belong to the same co-occurrence class. Therefore, there exists a contradiction with the assumption. □
If activities in the co-occurrence class occur continuously in any trace, it can be known from Theorem 1 that there exists a causal dependence between these activities.
For the concurrent structure, according to the behavioral characteristics of the concurrent structure, different concurrent branches will produce different co-occurrence classes. For instance, the concurrent structure shown in Figure 7c produces two co-occurrence classes {x,a,b,y} and {c,d}. Since the order of activities on different concurrent branches does not have restrictions, the activities in a co-occurrence class may not necessarily occur consecutively in an executable trace. In Figure 7c, the activities in the co-occurrence class {x,a,b,y} do not occur consecutively in the executable sequence {xacbdy}. However, causal occurrence dependencies still exist between the activities from each concurrent branch. In the following, Theorem 2 describes the substructure characteristics corresponding to co-occurrence classes with concurrent relationships.
Theorem 2
(A substructure corresponding to the co-occurrence class with a concurrent relationship). Let L be an event log, and , . if , , holds, then the activities from and form a sequential substructure, respectively.
Proof.
As , and holds, then and contain activities from different concurrent branches, respectively, and one of the branches should include and-split and and-join activities. From the interleaving behavior relationship, we can know that there is no ordering constraint between activities from two concurrent branches in a trace. According to Property 2, , holds. Therefore, even if the activities in or do not occur consecutively in the trace, there still exists a causal dependency between the activities from each co-occurrence class. As a result, the activities from each concurrent branch constitute a sequential substructure respectively. □
Theorem 2 shows that activities in concurrent branches constitute sequential substructures even if they do not occur consecutively in the trace. Theorem 3 addresses the substructure characteristics formed by activities in other co-occurrence classes.
Theorem 3
(A substructure corresponding to the co-occurrence class with strict order relationship). Let L be an event log and be an activity set over L, , if , (where ) and for , and are not in a concurrent relationship, then form a sequence substructure, along with form a sequence substructure. Meanwhile, there exists a non-sequential substructure containing at least one visible activity between and .
Proof.
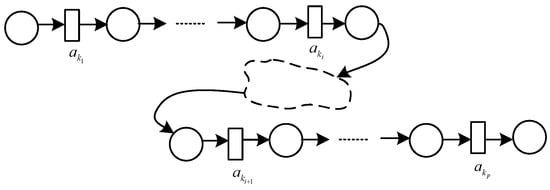
As , there exists a trace such that and do not occur consecutively. For , as and are not in a concurrent relationship, it can be seen that the activities in do not belong to any concurrent branch. Thus, when activities do not occur consecutively, this indicates that there exists at least one activity on the path from to ; meanwhile, they belong to the other co-occurrence class without . Obviously, the activity is in a sequential relationship with and ; otherwise, the activity must belong to the same co-occurrence class with and . Therefore, there is a non-sequential substructure containing at least one activity between and . According to Theorems 1 and 2, the remaining activities of form sequential substructures, respectively. The activities in form the substructure shown in Figure 8. □

Figure 8.
A substructure corresponding to the co-occurrence class with a strict order relationship.
5.2. Merging Structures of Co-Occurrence Classes
Section 5.1 illustrates a method for discovering a substructure from a single co-occurrence class. This section presents the method for merging the structure of co-occurrence classes according to the communication behavior relationship between them to construct more complex substructures. Section 5.2.1 addresses the communication behavior relationship between co-occurrence classes, and Section 5.2.2 explains how to merge multiple structures of co-occurrence classes to discover more complex substructures.
5.2.1. Communication Behavior Relationship between Co-Occurrence Classes
According to the behavior dependencies of the activities from different co-occurrence classes in the log, the communication behavior dependencies between the co-occurrence classes can be obtained. These communication behavior relationships include a sequential communication relationship, exclusive communication relationship, concurrent communication relationship, and cycle communication relationship. The analysis of the communication behavior relationship between the co-occurrence classes provides a theoretical basis for constructing a larger substructure by combining the co-occurrence classes.
Property 3
(Sequential communication relationship). Let L be an event log, and is a set of co-occurrence classes from event log L. If , , , holds, then .
Proof.
Assume and . and holds; meanwhile, also holds. Therefore, and are in a sequential relationship. □
Property 4
(Concurrent communication relationship). Let L be an event log, is a set of co-occurrence classes from the event log L. , , if holds, then .
Proof.
Assume , , and holds. , , if holds, then there must exist an activity (called and-split activity) where by firing this activity, each branch where the activity a or activity b is included will receive a token. If and-split and and-join are visible activities, according to the characteristics of concurrent structure, then and-split and and-join activities must appear in the co-occurrence invariant set of activity a or b.Therefore, they must belong to the co-occurrence class of activity a or b. If and-split and and-join are invisible activities, then they do not appear in the co-occurrence class of the activity a or b. Assume are the visible and-split and and-join activities, respectively. As , and , holds, , we denote as . □
Property 5
(Exclusive communication relationship). Let L be an event log, is a set of co-occurrence classes from the event log L. If , , holds, then .
Proof.
Obviously it is true. □
Property 6
(Cycle communication relationship). Let L be an event log, is a set of co-occurrence classes from the event log L. If , , holds, then .
Proof.
As , and holds. Meanwhile, as , holds. Therefore, the activity from and are in cycle relationship. □
5.2.2. Combining Multiple Co-Occurrence Classes to Find More Complex Substructures
According to the communication behavior relationship between co-occurrence classes, the method of constructing multiple substructures from co-occurrence classes is provided below. These substructures include concurrency, conflict, sequence, and loop.
If for , holds, then it is abbreviated as: .If holds, then it is abbreviated as: . Similarly, for and +, it is abbreviated as: , .
(1) Concurrent substructure: It is known that , if exists activities , where , , , and holds, then corresponding to and-split and and-join activity respectively. If not exist or such that or , then and-split or and-join are hidden transitions. Meanwhile, , , holds, then the typical substructure of and is shown in Figure 9.
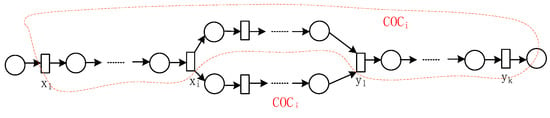
Figure 9.
Typical concurrent substructure composed of and .
(2) Conflict substructure: If , then and constitute the branch of the conflict substructure, respectively.
(3) Loop substructure: For loop structures, the key is to distinguish the do and redo part in a loop structure. Firstly, the characteristics of three different loop substructures are analyzed, and the invariant predecessor set, invariant successor set, co-occurrence invariant set, and co-occurrence class of each activity in different loop substructures are obtained. Then, different loop substructures are obtained according to the characteristics of the invariant predecessor set, the invariant successor set, the co-occurrence invariant set, and the co-occurrence class of the activities in the log.
When the loop body is a sequential structure, a typical structure is shown in Figure 10, and Table 8 shows the invariant predecessor (or successor) set and co-occurrence invariant set of each activity in the loop substructure.
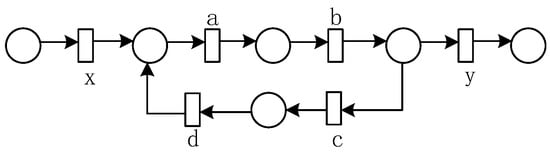
Figure 10.
Loop substructure with a sequential structure.

Table 8.
Invariant set of activities in Figure 9.
Co-occurrence classes obtained from Table 8 are
Corollary 1.
Let L be an event log, are co-occurrence classes from the event log L, and . If , holds, then is the redo substructure of the loop structure, while is the do substructure of the loop structure.
When the loop body is an exclusive structure, a typical structure is shown in Figure 11, and Table 9 shows the invariant predecessor (or successor) set and co-occurrence invariant set of each activity in the loop substructure.
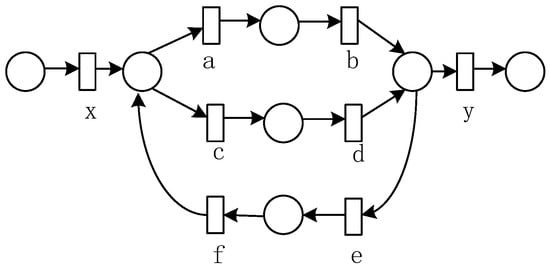
Figure 11.
Loop substructure with an exclusive structure.

Table 9.
Invariant set of activities in Figure 11.
Co-occurrence classes obtained from the Table 9 are as follows:
.
Corollary 2.
Let L be an event log, are co-occurrence classes from the event log L, and , if the following two conditions hold:
(1) For , ;
(2) , or
where represents the number of times the sequence formed by appears in the trace σ, then is the do part of the loop structure with and in an exclusive substructure, and is the redo part of the loop structure.
When the loop body is a concurrent structure, a typical structure is shown in Figure 12, and Table 10 shows the invariant predecessor (or successor) set and co-occurrence invariant set of each activity in the loop substructure.
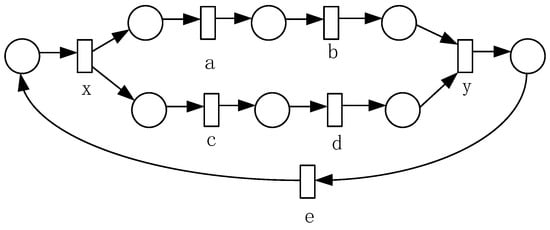
Figure 12.
Loop substructure with a concurrent structure.

Table 10.
Invariant set of activities in Figure 12.
Co-occurrence classes obtained from Table 10 are .
Corollary 3.
Let L be an event log, are co-occurrence classes from the event log L, and . If the following two conditions hold,
(1) for , , ,
(2) for , ,
then is the do part of the loop structure with and in a concurrent substructure, while is the redo part of the loop structure.
Definition 10.
[Merge activities in relation → [6]] When the left activities in two → relations are the same (a→ b, a→ c), two possible substructures can be created.
(a) The places of → relations are merged into a single one if and only if . This is denoted as .
(b) The places of→ relation are not merged if and only if . This is denoted as .
Similarly, for → relations when the right activity is common, i.e., , the substructure created will be either or accordingly. In general, a set of → relations in the form may produce either or . Consequently, the merging can be applied to composed relations, i.e., and leads .
Algorithm 4 presents the construction steps for discovering process models from event logs using the methods in Section 5.1 and Section 5.2. Step 1 constructs the co-occurrence class from the event log, Steps 2–4 use the method in Section 5.1 to construct the corresponding substructure for each co-occurrence class, Steps 5–7 use the method in Section 5.2.1 to obtain the communication behavior relationship between any two co-occurrence classes, Steps 8–13 use the method proposed in Section 5.2.2 to merge several co-occurrence classes into a larger sub-module, and Step 14 further merges the remaining sub-modules into a complete process model through the directly-follows relationship between activities.
| Algorithm 4: Construct Petri net from the event log |
 |
6. Experiment Evaluation
Experiment purpose. In this section, we experimentally evaluate whether the method proposed in this paper can discover long-distance dependencies from event logs and can rediscover process models with complex cycle structures from small event logs. Several event logs were used to compare our method with other process discovery methods, such as Inductive Miner (IM) [17], the Heuristics Miner (HM) algorithm [14], Inductive Miner-Incompleteness (IMin) [17], and Conjoint Occurrence Miner (CoM) [6]. The experimental evaluation in this section mainly answers two questions. The first question is whether the proposed method can discover long-distance dependencies. The second question is whether the proposed method can correctly discover the original model with a complex structure from incomplete event logs caused by concurrency. In addition to concurrent, sequential, and exclusive structures, the model also may contain complex loop structures.
Experiment design. For problem 1, we generate event logs containing 1000 traces by simulating the model M1 with long-distance dependencies shown in Section 3. Then, we try to use these logs to rediscover the process model using different methods. We report on the experimental comparison results of the quality of the process model and the consistency between the original model and the discovered model [31]. Meanwhile, we report the discovery of long-distance dependencies in the original model. For problem 2, event logs with different completeness levels of directly-follows relationships are generated by simulating model M2 shown in Figure 6. These logs are obtained by removing some of the directly-follows relationships derived from the concurrent structure. Different algorithms are used to reconstruct the original process model M2 from these event logs of different sizes, and the differences between the discovered process model and the original model are reported. The method proposed in [31] is used to measure the Degree of Trace Consistency (DTC) and Degree of Profile Consistency (DPC) of alignment between the models. All miners use default parameters, and h in IMin is set to 0.
Experiment Result. From Table 11, it can be seen that the proposed method and the CoM method can discover long-distance dependencies, but compared with the CoM method, the proposed method can better discover the cyclic structure. IMin, IM, and HM cannot rediscover the original process model due to their inability to discover long-distance dependencies. The CoM method also cannot discover the original process model due to its limitations in the cyclic structure. When different methods are applied to the event log generated by M1, the consistency between the discovered process model and the original model is measured from two aspects by using the method given in [31]. The experimental results show that the method proposed in this paper has good results regarding the consistency of the discovered process model and the original model in terms of both the degree of trace consistency and degree of profile consistency. Since long-distance dependencies do not affect the behavior profile relationship between activities, the process model obtained by the IMin, IM, and HM algorithms has a good degree of profile consistency with the original model.

Table 11.
Experimental results obtained by different methods.
Figure 13 shows that the IM algorithm and the HM algorithm require that the event log is complete with a directly-follows relationship, and IMin, COM, and the proposed method can handle an incomplete event log. Although the IMin method can handle the incompleteness of the event log, it cannot discover the long-distance dependency; thus, the value of DTC is lower than that of DPC between the model discovered by IMin and the original model. IMin mainly retains the behavior relationship with high probability based on the directly-follows relationship between activities to determine the behavior between the activities. Hence, the requirement for completeness of IMin is lower than that of the IM and HM algorithms but is higher than the proposed method and the CoM method. The proposed method and CoM method require that the completeness degree of the log is up to 85%. However, because the CoM method has some limitations in discovering the cycle structure, the consistency degree between the discovered model and the original model cannot reach 1, even if the log completeness degree is more than 85%. IMin requires the completeness ratio of the log to be about 90%. However, since the process model discovered by IMin is block-structured, some hidden transitions can be added when building the model. These hidden transitions may cause the model to generate additional behaviors, which may lead to a certain deviation between the discovered model and the original model. Thus, for the IMin method, even if the log completeness ratio reaches 90%, the consistency degree between the discovered model and the original model is still less than 1.
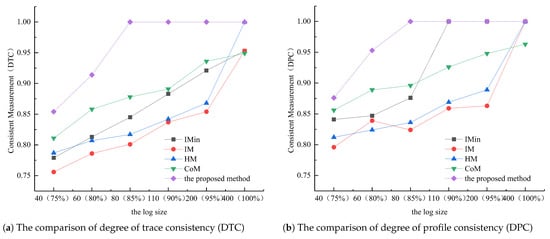
Figure 13.
The degree of consistency comparison.
As the results of our experiments show, the proposed method has two advantages compared to the others. One advantage is that our method can handle incomplete event logs better than the IMin algorithm. However, the IM and HM approaches are heavily dependent on the log completeness. Although both the proposed method and the COM method can deal with the incompleteness caused by high concurrency, the COM method has limitations in discovering the loop structure, whereas the proposed method can also discover complex loop structures in addition to sequential, exclusive, and concurrent structures. The other advantage is that the proposed method can discover long-distance dependencies from the event logs. As the experiment shows, IMin, IM, and HM do not have an inability to discover long-distance dependencies.
7. Conclusions and Future Work
Based on [6], a method for discovering a process model with multiple structure types from incomplete event logs is presented that can discover not only sequential, concurrent, and conflicting structures but also complex cyclic structures. This paper analyzes the relationship between co-occurrence classes from log and co-occurrence classes from the model and addresses communication behavior profiles between co-occurrence classes from a log using the technology of the behavior profile. A series of propositions are presented to point out how to construct the substructure through the co-occurrence class. Subsequently, the whole process model is constructed from the event log. The proposed method can still discover the original process model from an incomplete event log, even if the model contains a complex cyclic structure. In addition, it also can correctly discover a long-distance dependency implied in the log. For large event logs, it will be time-consuming to construct co-occurrence classes and analyze their communication behavior profiles. In the future, we will consider using co-occurrence classes to construct frequent patterns from event logs to analyze local behaviors in business processes.
Author Contributions
Methodology, L.W.; formal analysis, L.W.; writing—original draft preparation, L.W.; writing—review and editing, X.F.; visualization, C.S.; project administration, X.F.; supervision, X.F. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Natural Science Foundation, China (No. 61572035, 61402011), the Leading Backbone Talent Project in Anhui Province, China (No. 2020-1-12), the Natural Science Foundation of Anhui Province, China (No. 2008085QD178), Anhui Province Academic and Technical Leader Foundation (No. 2019H239), Anhui Province College Excellent Young Talents Fund Project of China (No. gxyqZD2020020), Open Research Fund of Anhui Province Engineering Laboratory for Big Data Analysis and Early Warning Technology of Coal Mine Safety (NO. CSBD2022-ZD03).
Data Availability Statement
All the data in this paper were obtained by simulating the model. Experimental data and code related to this paper can be obtained by contacting the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Van Der Aalst, W. Process Mining: Discovery, Conformance and Enhancement of Business Processes; Springer: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Van Der Aalst, W. Process Mining: Overview and Opportunities. ACM Trans. Manag. Inf. Syst. (TMIS) 2012, 3, 1–17. [Google Scholar] [CrossRef]
- Van Der Aalst, W. Process Mining: A 360 Degree Overview; Springer: Cham, Switzerland, 2022; pp. 3–34. [Google Scholar]
- Farkhady, R.Z.; Aali, S.H. A probabilistic approach for process mining in incomplete and noisy logs. Lect. Notes Eng. Comput. Sci. 2011, 2188, 415–420. [Google Scholar]
- ZarehFarkhady, R.; Aali, S.H. A two phase approach for process mining in incomplete and noisy Logs. Int. J. Comput. Sci. Issues (IJCSI) 2012, 9, 160–165. [Google Scholar]
- Tapia-Flores, T.; Rodríguez-Pérez, E.; López-Mellado, E. Discovering Process Models from Incomplete Event Logs using Conjoint Occurrence Classes. In Proceedings of the ATAED@ Petri nets/ACSD, CEUR Workshop Proceedings 1592, Torun, Poland, 20–21 June 2016; pp. 31–46. [Google Scholar]
- Leemans, S.J.; Poppe, E.; Wynn, M.T. Directly follows-based process mining: Exploration & a case study. In Proceedings of the 2019 International Conference on Process Mining (ICPM), Aachen, Germany, 24–26 June 2019; pp. 25–32. [Google Scholar]
- Bergenthum, R.; Desel, J.; Lorenz, R.; Mauser, S. Process mining based on regions of languages. In Proceedings of the International Conference on Business Process Management, Brisbane, Australia, 24–28 September 2007; pp. 375–383. [Google Scholar]
- Solé, M.; Carmona, J. Process mining from a basis of state regions. In Proceedings of the International Conference on Applications and Theory of Petri Nets, Braga, Portugal, 21–25 June 2010; pp. 226–245. [Google Scholar]
- van derWerf, J.M.E.; van Dongen, B.F.; Hurkens, C.A.; Serebrenik, A. Process discovery using integer linear programming. Fundam. Inform. 2009, 94, 387–412. [Google Scholar] [CrossRef]
- van Zelst, S.J.; van Dongen, B.F.; van der Aalst, W.M.; Verbeek, H. Discovering workflow nets using integer linear programming. Computing 2018, 100, 529–556. [Google Scholar] [CrossRef]
- de Medeiros, A.K.A.; Weijters, A.J.; van der Aalst, W.M. Genetic process mining: An experimental evaluation. Data Min. Knowl. Discov. 2007, 14, 245–304. [Google Scholar] [CrossRef]
- Van der Aalst, W.M. Decomposing Petri nets for process mining: A generic approach. Distrib. Parallel Databases 2013, 31, 471–507. [Google Scholar] [CrossRef]
- Weijters, A.; van Der Aalst, W.M.; De Medeiros, A.A. Process mining with the heuristics miner-algorithm. Tech. Univ. Eindhoven Tech. Rep. WP 2006, 166, 1–34. [Google Scholar]
- Weijters, A.; Ribeiro, J.T.S. Flexible heuristics miner (FHM). In Proceedings of the 2011 IEEE symposium on computational intelligence and data mining (CIDM), Paris, France, 11–15 April 2011; pp. 310–317. [Google Scholar]
- vanden Broucke, S.K.; De Weerdt, J. Fodina: A robust and flexible heuristic process discovery technique. Decis. Support Syst. 2017, 100, 109–118. [Google Scholar] [CrossRef]
- Leemans, S.J.; Fahland, D.; van der Aalst, W.M. Discovering block-structured process models from incomplete event logs. In Proceedings of the International Conference on Applications and Theory of Petri Nets and Concurrency, Tunis, Tunisia, 23–27 June 2014; pp. 91–110. [Google Scholar]
- Günther, C.W.; Van Der Aalst, W.M. Fuzzy mining–Adaptive process simplification based on multi-perspective metrics. In Proceedings of the International Conference on Business Process Management, Brisbane, Australia, 24–28 September 2007; pp. 328–343. [Google Scholar]
- Van der Aalst, W.; Weijters, T.; Maruster, L. Workflow mining: Discovering process models from event logs. IEEE Trans. Knowl. Data Eng. 2004, 16, 1128–1142. [Google Scholar] [CrossRef]
- De Medeiros, A.A.; Van Dongen, B.F.; Van der Aalst, W.M.; Weijters, A. Process mining: Extending the α-algorithm to mine short loops. Eindh. Univ. Technol. 2004, 10, 145–170. [Google Scholar]
- Wen, L.; Van Der Aalst, W.M.; Wang, J.; Sun, J. Mining process models with non-free-choice constructs. Data Min. Knowl. Discov. 2007, 15, 145–180. [Google Scholar] [CrossRef]
- Guo, Q.; Wen, L.; Wang, J.; Yan, Z.; Yu, P.S. Mining invisible tasks in non-free-choice constructs. In Proceedings of the International Conference on Business Process Management, Rio de Janeiro, Brazil, 18–22 September 2016; pp. 109–125. [Google Scholar]
- Augusto, A.; Conforti, R.; Dumas, M.; La Rosa, M.; Polyvyanyy, A. Split miner: Automated discovery of accurate and simple business process models from event logs. Knowl. Inf. Syst. 2019, 59, 251–284. [Google Scholar] [CrossRef]
- Li, W.; Zhu, H.; Liu, W.; Chen, D.; Jiang, J.; Jin, Q. An anti-noise process mining algorithm based on minimum spanning tree clustering. IEEE Access 2018, 6, 48756–48764. [Google Scholar] [CrossRef]
- Sun, X.; Hou, W.; Yu, D.; Wang, J.; Pan, J. Filtering out noise logs for process modelling based on event dependency. In Proceedings of the 2019 IEEE International Conference on Web Services (ICWS), Milan, Italy, 8–13 July 2019; pp. 388–392. [Google Scholar]
- Nolle, T.; Luettgen, S.; Seeliger, A.; Mühlhäuser, M. Analyzing business process anomalies using autoencoders. Mach. Learn. 2018, 107, 1875–1893. [Google Scholar] [CrossRef]
- Zhang, Z.; Hildebrant, R.; Asgarinejad, F.; Venkatasubramanian, N.; Ren, S. Improving Process Discovery Results by Filtering Out Outliers from Event Logs with Hidden Markov Models. In Proceedings of the 2021 IEEE 23rd Conference on Business Informatics (CBI), Bolzano, Italy, 1–3 September 2021; Volume 1, pp. 171–180. [Google Scholar]
- Tax, N.; Sidorova, N.; van der Aalst, W.M. Discovering more precise process models from event logs by filtering out chaotic activities. J. Intell. Inf. Syst. 2019, 52, 107–139. [Google Scholar] [CrossRef]
- Munoz-Gama, J. Handling Noise and Incompleteness; Springer: Cham, Switzerland, 2016; pp. 61–73. [Google Scholar]
- Weidlich, M.; Polyvyanyy, A.; Desai, N.; Mendling, J.; Weske, M. Process compliance analysis based on behavioural profiles. Inf. Syst. 2011, 36, 1009–1025. [Google Scholar] [CrossRef]
- Weidlich, M.; Mendling, J.; Weske, M. Efficient consistency measurement based on behavioral profiles of process models. IEEE Trans. Softw. Eng. 2010, 37, 410–429. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).