Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment
Abstract
:1. Introduction
Contributions of This Study
- We develop a new Effective Seeker Optimization with Machine Learning-Enabled Intrusion Detection System (ESOML-IDS) technique for intrusion detection and classification in FC and EC environments;
- To detect and classify intrusions, a group of sub-processes are incorporated with the proposed technique, including pre-processing, ESO-based feature subset selection, a DAE classifier, and CLPSO-based parameter optimization;
- To demonstrate the comparative advantages of the proposed technique over recent approaches, a wide variety of exhaustive simulations are carried out.
2. Related Works
3. The Proposed Model
3.1. Data Normalization
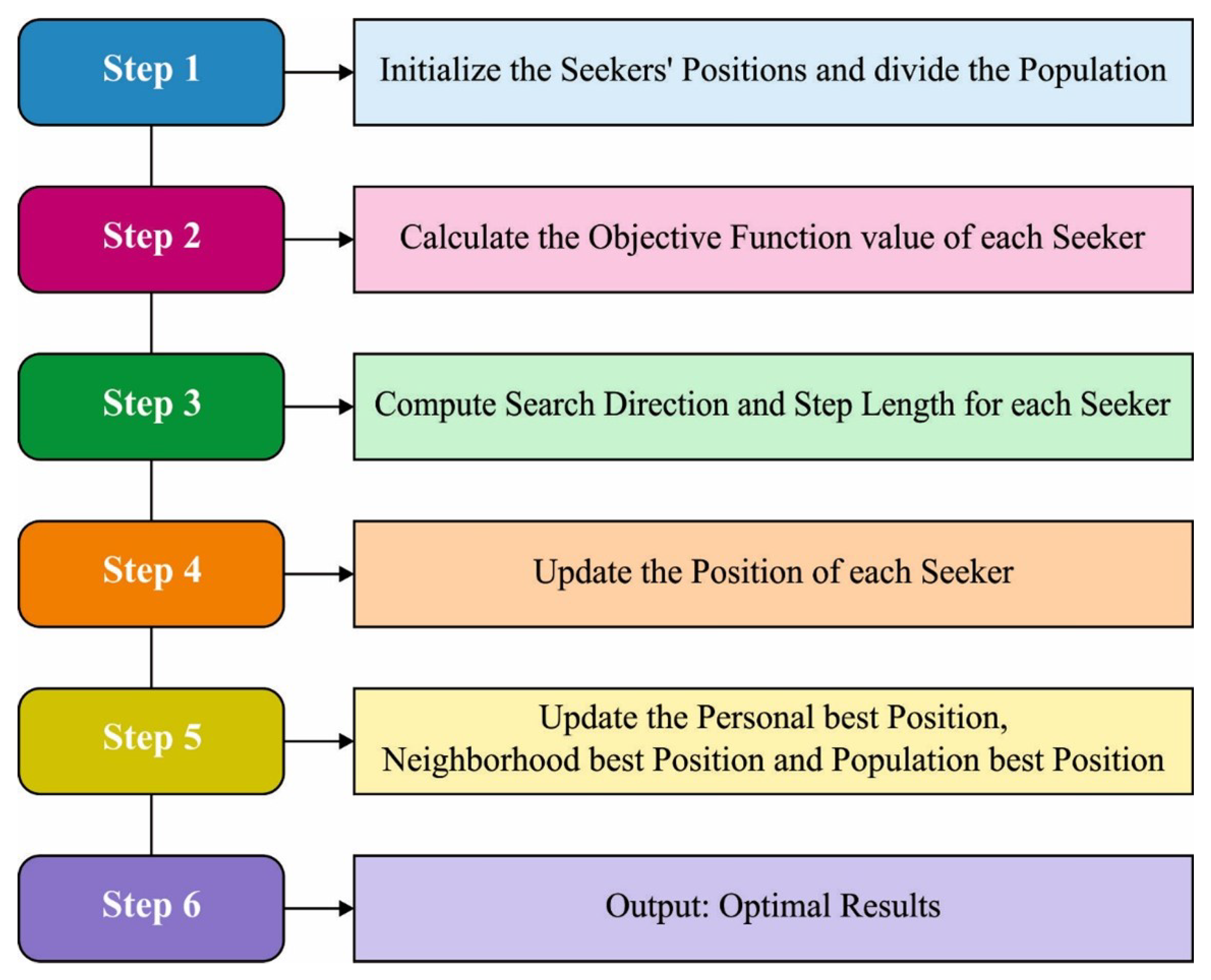
3.2. Design of ESO-Based Feature Selection Technique
3.2.1. Search Direction
3.2.2. Search Step Size
3.2.3. Individual Location Updates
3.3. Process Involved in DAE-Based Classification
3.4. Parameter Tuning Using CLPSO Algorithm
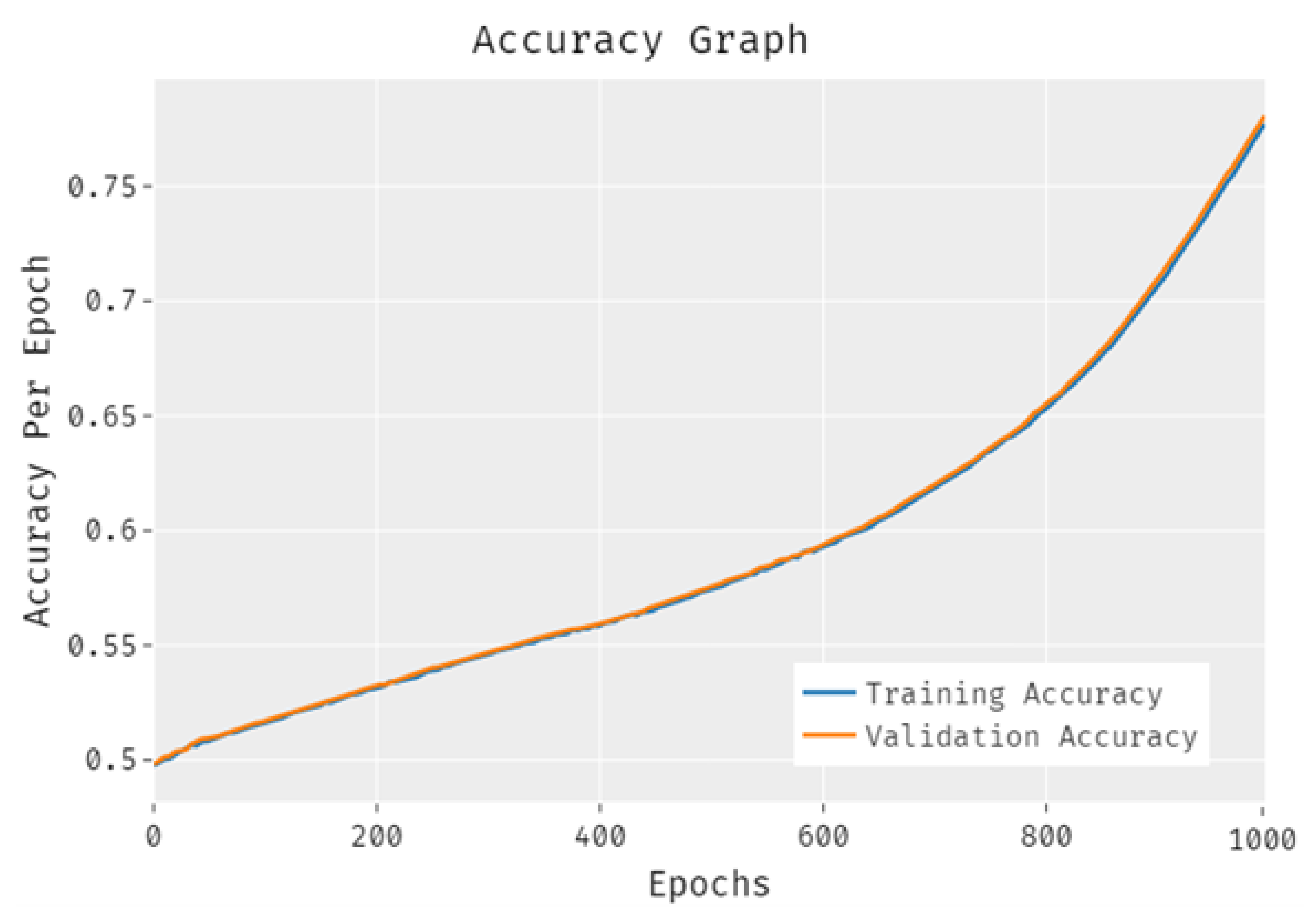
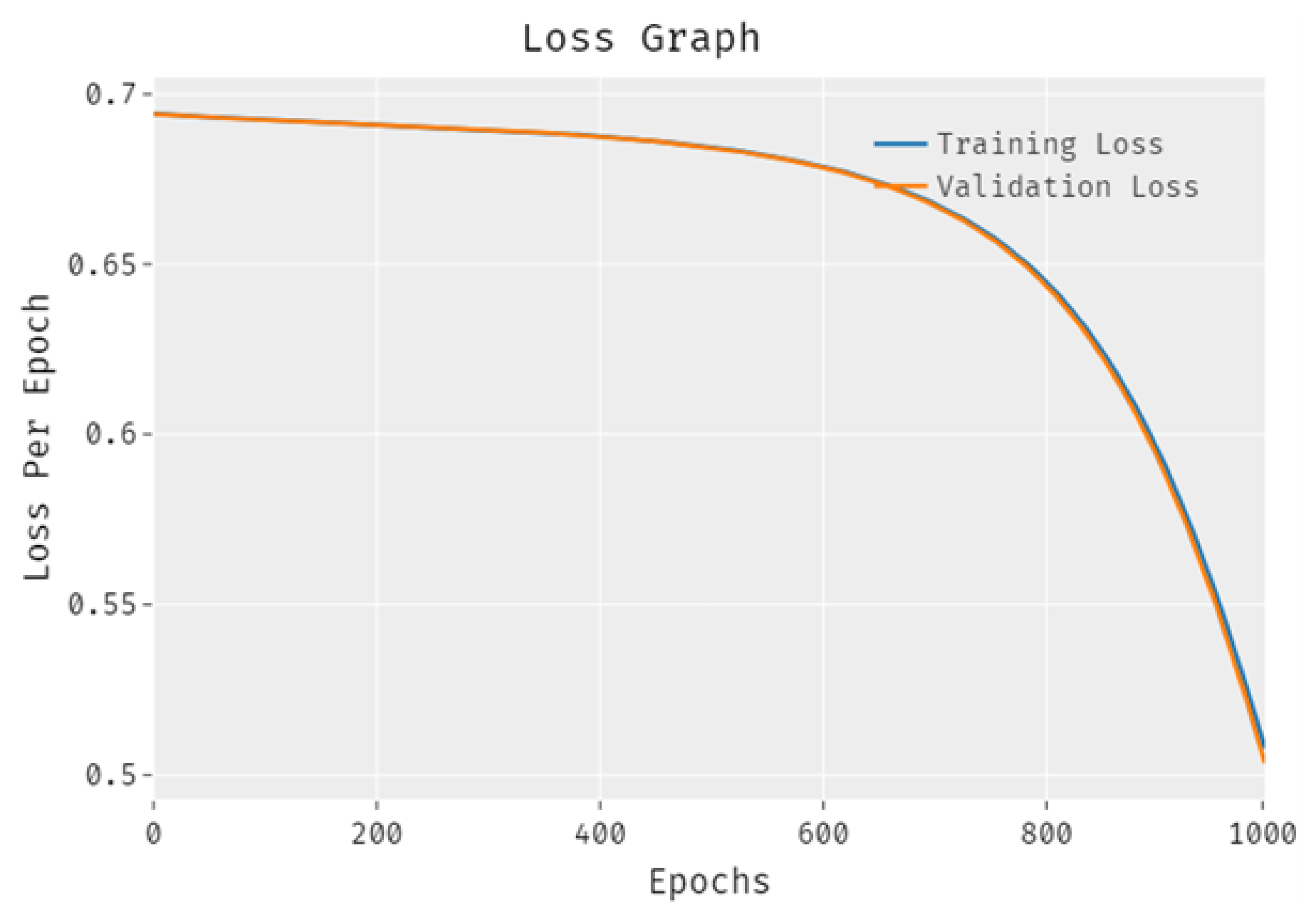
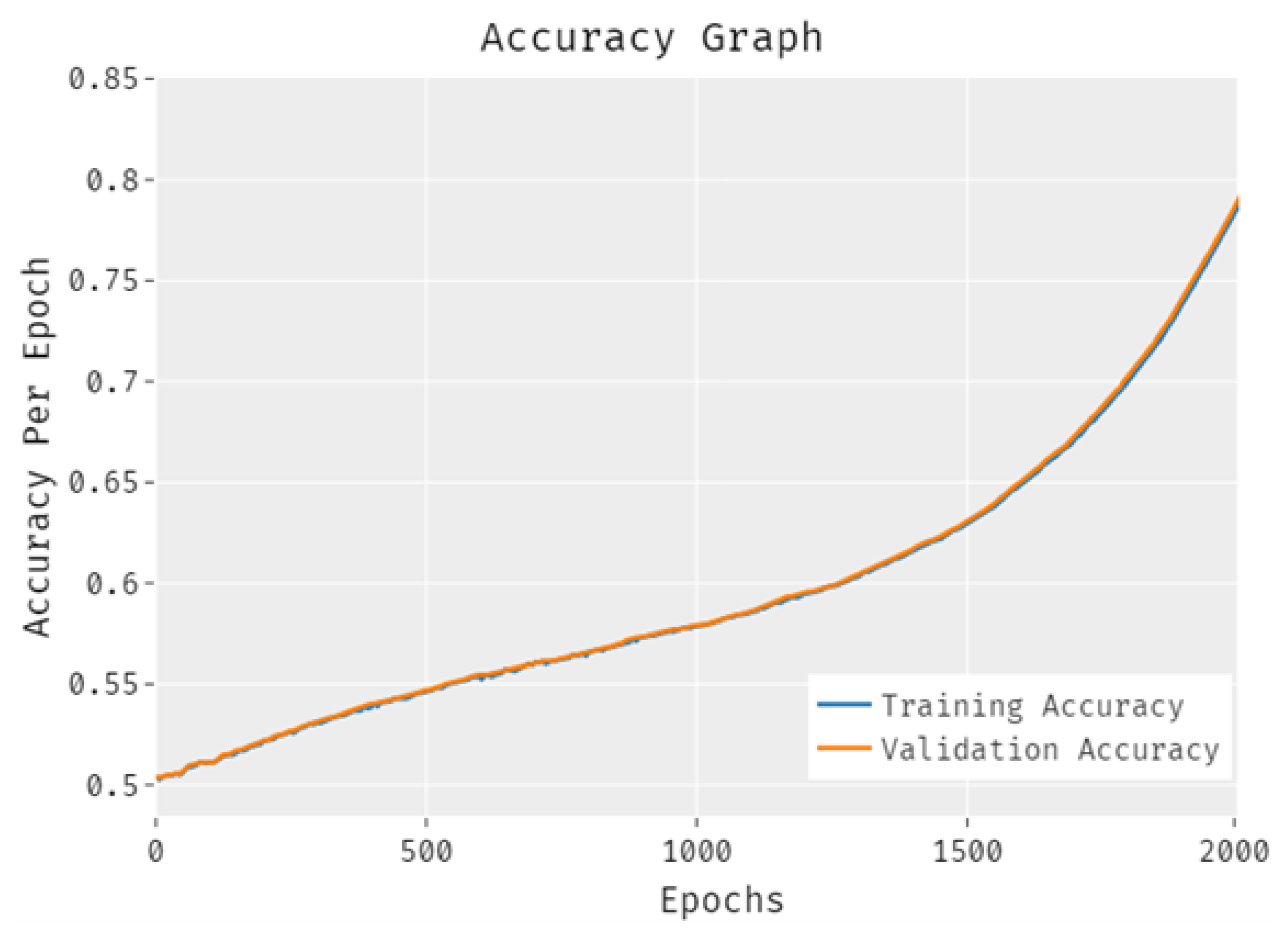
4. Empirical Results and Validation
4.1. Cost Analysis
4.2. Performance Measures and Analysis
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Khater, B.S.; Wahab, A.W.A.; Idris, M.Y.I.; Hussain, M.A.; Ibrahim, A.A.; Amin, M.A.; Shehadeh, H.A. Classifier performance evaluation for lightweight ids using fog computing in iot security. Electronics 2021, 10, 1633. [Google Scholar] [CrossRef]
- Onah, J.O.; Abdulhamid, S.M.; Abdullahi, M.; Hassan, I.H.; Al-Ghusham, A. Genetic algorithm based feature selection and naïve bayes for anomaly detection in fog computing environment. Mach. Learn. Appl. 2021, 6, 100156. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Gupta, G.P.; Tripathi, R. A distributed framework for detecting ddos attacks in smart contract-based blockchain-iot systems by leveraging fog computing. Trans. Emerg. Telecommun. Technol. 2021, 32, e4112. [Google Scholar] [CrossRef]
- Alzubi, O.A.; Qiqieh, I.; Alzubi, J.A. Fusion of deep learning based cyberattack detection and classification model for intelligent systems. Clust. Comput. 2022, 1–12, in press. [Google Scholar] [CrossRef]
- Zwayed, F.A.; Anbar, M.; Sanjalawe, Y.; Manickam, S. Intrusion detection systems in fog computing- a review. In Advances in Cyber Security; Abdullah, N., Manickam, S., Anbar, M., Eds.; Springer: Singapore, 2021; pp. 481–504. [Google Scholar]
- Aliyu, F.; Sheltami, T.; Shakshuki, E.M. A detection and prevention technique for man in the middle attack in fog computing. Procedia Comput. Sci. 2018, 141, 24–31. [Google Scholar] [CrossRef]
- Alrawais, A.; Alhothaily, A.; Hu, C.; Cheng, X. Fog computing for the internet of things: Security and privacy issues. IEEE Internet Comput. 2017, 21, 34–42. [Google Scholar] [CrossRef]
- Gao, J.; Chai, S.; Zhang, B.; Xia, Y. Research on network intrusion detection based on incremental extreme learning machine and adaptive principal component analysis. Energies 2019, 12, 1223. [Google Scholar] [CrossRef]
- Alzubi, O.A.; Alzubi, J.A.; Al-Zoubi, A.M.; Hassonah, M.A.; Kose, U. An efficient malware detection approach with feature weighting based on harris hawks optimization. Clust. Comput. 2022, 25, 2369–2387. [Google Scholar] [CrossRef]
- Zong, W.; Chow, Y.-W.; Susilo, W. A two-stage classifier approach for network intrusion detection. In Information Security Practice and Experience; Su, C., Kikuchi, H., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 329–340. [Google Scholar]
- Alzubi, O.A.; Alzubi, J.A.; Shankar, K.; Gupta, D. Blockchain and artificial intelligence enabled privacy-preserving medical data transmission in internet of things. Trans. Emerg. Telecommun. Technol. 2021, 32, e4360. [Google Scholar] [CrossRef]
- Alazab, M.; Khurma, R.A.; Awajan, A.; Camacho, D. A new intrusion detection system based on moth–flame optimizer algorithm. Expert Syst. Appl. 2022, 210, 118439. [Google Scholar] [CrossRef]
- Alzubi, O.A. Quantum readout and gradient deep learning model for secure and sustainable data access in iwsn. PeerJ Comput. Sci. 2022, 8, e983–e1007. [Google Scholar] [CrossRef]
- Alazab, M.; Layton, R.; Broadhurst, R.; Bouhours, B. Malicious spam emails developments and authorship attribution. In Proceedings of the 2013 Fourth Cybercrime and Trustworthy Computing Workshop, Sydney, Australia, 21–22 November 2013; IEEE: Minneapolis, MN, USA, 2013; pp. 58–68. [Google Scholar]
- Kumar, V.; Sinha, D.; Das, A.K.; Pandey, S.C.; Goswami, R.T. An integrated rule based intrusion detection system: Analysis on unsw-nb15 data set and the real time online dataset. Clust. Comput. 2019, 23, 1397–1418. [Google Scholar] [CrossRef]
- Alzubi, O.A. A deep learning- based frechet and dirichlet model for intrusion detection in iwsn. J. Intell. Fuzzy Syst. 2022, 42, 873–883. [Google Scholar] [CrossRef]
- Chen, T.M.; Blasco, J.; Alzubi, J.; Alzubi, O. Intrusion detection. Eng. Technol. Ref. 2014, 1, 1–9. [Google Scholar] [CrossRef]
- Lin, F.; Zhou, Y.; An, X.; You, I.; Choo, K.-K.R. Fair resource allocation in an intrusion-detection system for edge computing: Ensuring the security of internet of things devices. IEEE Consum. Electron. Mag. 2018, 7, 45–50. [Google Scholar] [CrossRef]
- Li, Q.; Hou, J.; Meng, S.; Long, H. Glide: A game theory and data-driven mimicking linkage intrusion detection for edge computing networks. Complex 2020, 2020, 7136160:1–7136160:18. [Google Scholar] [CrossRef]
- Wang, Y.; Meng, W.; Li, W.; Liu, Z.; Liu, Y.; Xue, H. Adaptive machine learning-based alarm reduction via edge computing for distributed intrusion detection systems. Concurr. Comput. Pract. Exp. 2019, 31, e5101. [Google Scholar] [CrossRef]
- Khater, B.S.; Wahab, A.W.B.A.; Idris, M.Y.I.B.; Hussain, M.A.; Ibrahim, A.A. A lightweight perceptron-based intrusion detection system for fog computing. Appl. Sci. 2019, 9, 178. [Google Scholar] [CrossRef]
- An, X.; Su, J.; Lü, X.; Lin, F. Hypergraph clustering model-based association analysis of ddos attacks in fog computing intrusion detection system. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 249–259. [Google Scholar] [CrossRef]
- Mourad, A.; Tout, H.; Wahab, O.A.; Otrok, H.; Dbouk, T. Ad hoc vehicular fog enabling cooperative low-latency intrusion detection. IEEE Internet Things J. 2021, 8, 829–843. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Chang, V.; Hawash, H.; Chakrabortty, R.K.; Ryan, M. Deep-ifs: Intrusion detection approach for industrial internet of things traffic in fog environment. IEEE Trans. Ind. Inform. 2021, 17, 7704–7715. [Google Scholar] [CrossRef]
- Pacheco, J.; Benitez, V.H.; Félix-Herrán, L.C.; Satam, P. Artificial neural networks-based intrusion detection system for internet of things fog nodes. IEEE Access 2020, 8, 73907–73918. [Google Scholar] [CrossRef]
- Duan, S.; Luo, H.; Liu, H. An elastic collision seeker optimization algorithm for optimization constrained engineering problems. Math. Probl. Eng. 2022, 2022, 1344667. [Google Scholar] [CrossRef]
- Liang, P.; Shi, W.; Zhang, X. Remote sensing image classification based on stacked denoising autoencoder. Remote. Sens. 2017, 10, 16. [Google Scholar] [CrossRef]
- Ji, Y.; Zhao, X.; Hao, J. A novel uav path planning algorithm based on double-dynamic biogeography-based learning particle swarm optimization. Mob. Inf. Syst. 2022, 2022, 8519708. [Google Scholar] [CrossRef]


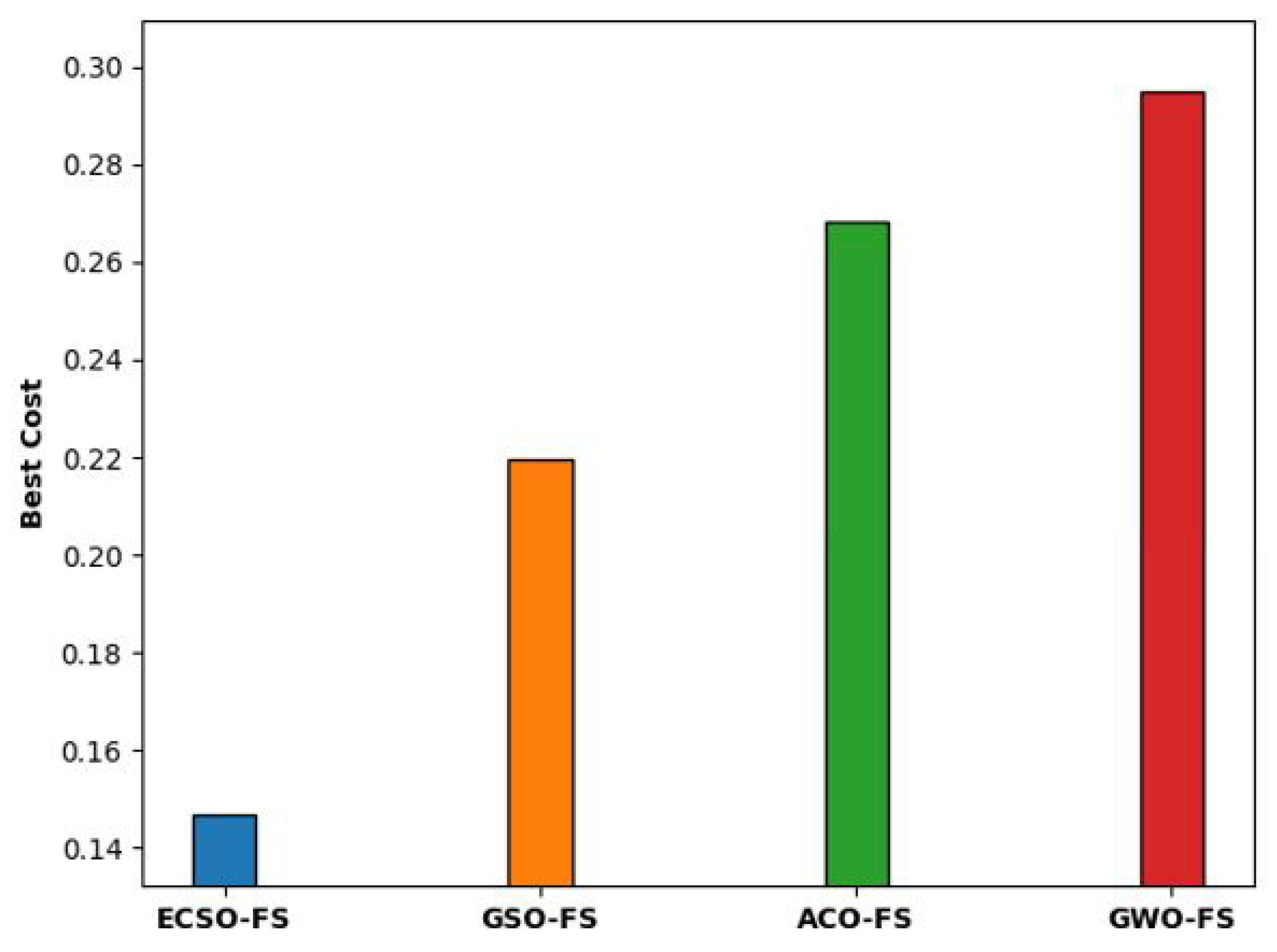


| Methods | No. of Features Selected | Best Cost |
|---|---|---|
| ESO-FS | 12 | 0.1468 |
| GSO-FS | 16 | 0.2194 |
| ACO-FS | 18 | 0.2681 |
| GWO-FS | 24 | 0.2947 |
| Epoch-1000 | ||||||
|---|---|---|---|---|---|---|
| Class Labels | Training Accuracy | Validation Accuracy | Test Accuracy | Precision | Recall | F1-Score |
| Normal | 83.38 | 83.56 | 78.22 | 82.72 | 81.50 | 80.59 |
| DoS | 83.14 | 83.50 | 80.18 | 82.10 | 83.47 | 81.99 |
| Backdoor | 83.86 | 81.75 | 80.32 | 82.45 | 82.02 | 82.89 |
| Exploits | 83.03 | 83.56 | 78.32 | 83.21 | 81.28 | 83.98 |
| Analysis | 83.07 | 82.24 | 77.92 | 81.59 | 81.99 | 80.63 |
| Generic | 282.46 | 82.88 | 80.43 | 82.08 | 81.21 | 80.87 |
| Fuzzers | 81.32 | 81.90 | 77.41 | 81.68 | 81.42 | 80.40 |
| Shellcode | 83.52 | 81.65 | 77.33 | 82.88 | 82.82 | 80.34 |
| Reconnaissance | 83.25 | 83.41 | 77.38 | 82.97 | 82.44 | 80.34 |
| Worms | 81.17 | 82.49 | 78.24 | 81.51 | 81.74 | 81.26 |
| Average | 82.82 | 82.69 | 78.58 | 82.32 | 81.99 | 81.33 |
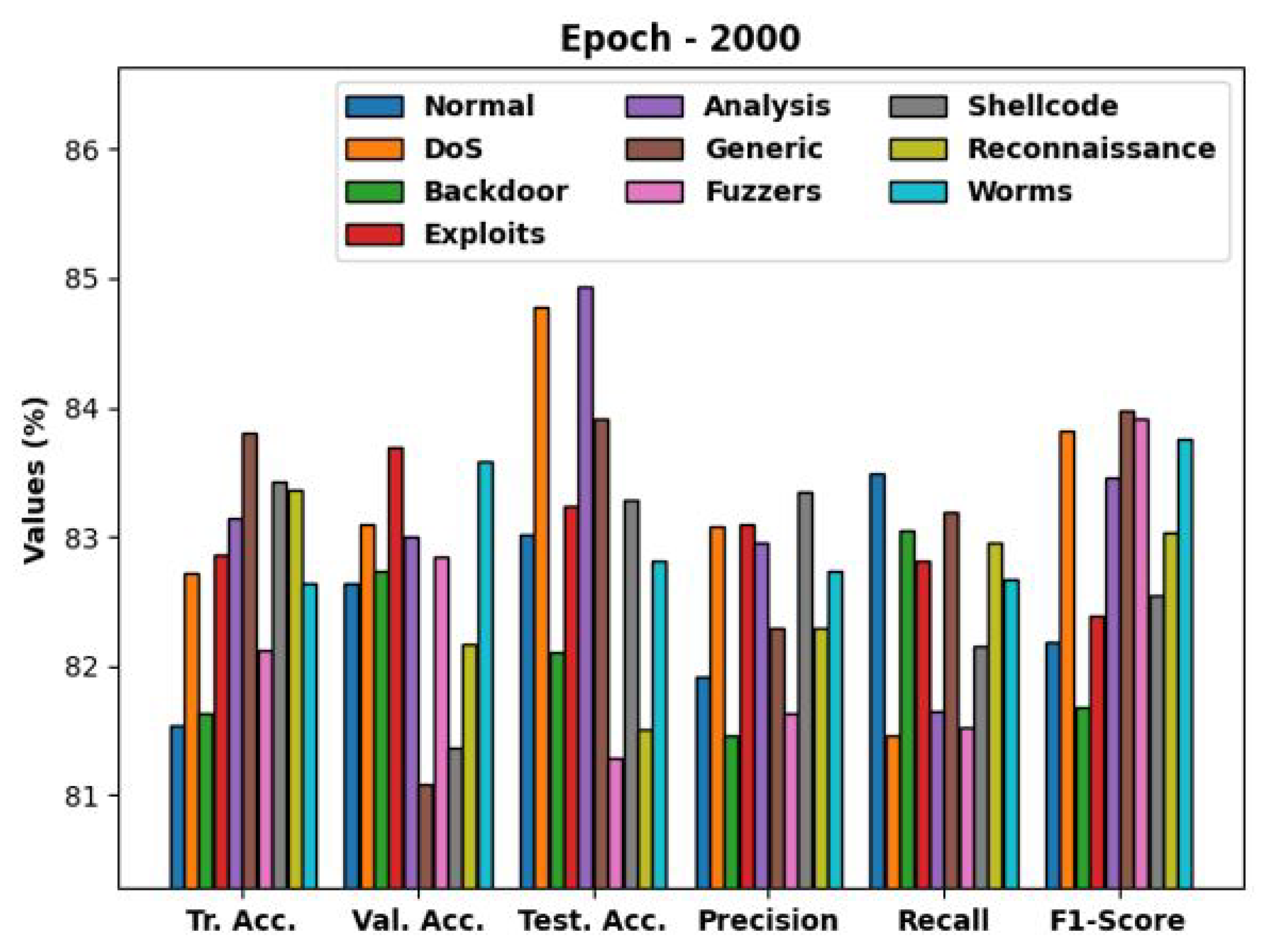
| Epoch-2000 | ||||||
|---|---|---|---|---|---|---|
| Class Labels | Training Accuracy | Validation Accuracy | Test Accuracy | Precision | Recall | F1-Score |
| Normal | 81.54 | 82.64 | 83.02 | 81.92 | 83.49 | 82.18 |
| DoS | 82.72 | 83.10 | 84.78 | 83.08 | 81.46 | 83.82 |
| Backdoor | 81.63 | 82.73 | 82.11 | 81.47 | 83.05 | 81.69 |
| Exploits | 82.86 | 83.70 | 83.24 | 83.10 | 82.82 | 82.39 |
| Analysis | 83.15 | 83.01 | 84.93 | 82.95 | 81.65 | 83.46 |
| Generic 83.80 | 81.09 | 83.92 | 82.29 | 83.19 | 83.97 | |
| Fuzzers 82.12 | 82.85 | 81.29 | 81.64 | 81.53 | 83.92 | |
| Shellcode | 83.42 | 81.37 | 83.29 | 83.35 | 82.15 | 82.55 |
| Reconnaissance | 83.37 | 82.17 | 81.51 | 82.29 | 82.95 | 83.04 |
| Worms | 82.64 | 83.59 | 82.82 | 82.74 | 82.68 | 83.75 |
| Average | 82.73 | 82.63 | 83.09 | 82.48 | 82.50 | 83.08 |
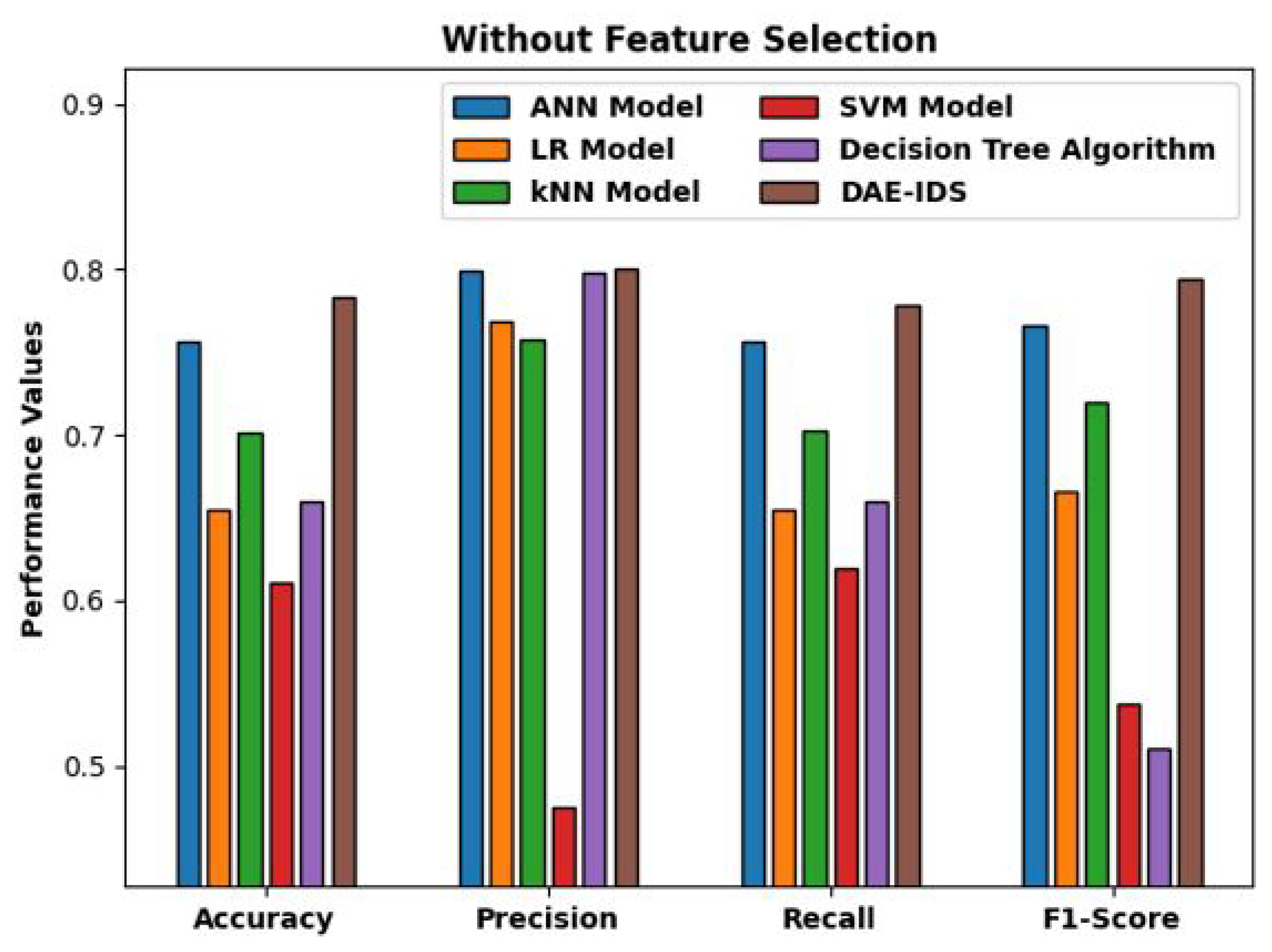
| Methods | Accuracy | Precision | Recall | F1 Score |
|---|---|---|---|---|
| ANN Model | 0.7562 | 0.7992 | 0.7561 | 0.7658 |
| LR Model | 0.6553 | 0.7691 | 0.6554 | 0.6662 |
| kNN Model | 0.7009 | 0.7579 | 0.7021 | 0.7203 |
| SVM Model | 0.6109 | 0.4747 | 0.6200 | 0.5377 |
| Decision Tree Algorithm | 0.6603 | 0.7982 | 0.6604 | 0.5112 |
| DAE-IDS | 0.7834 | 0.8010 | 0.7786 | 0.7946 |
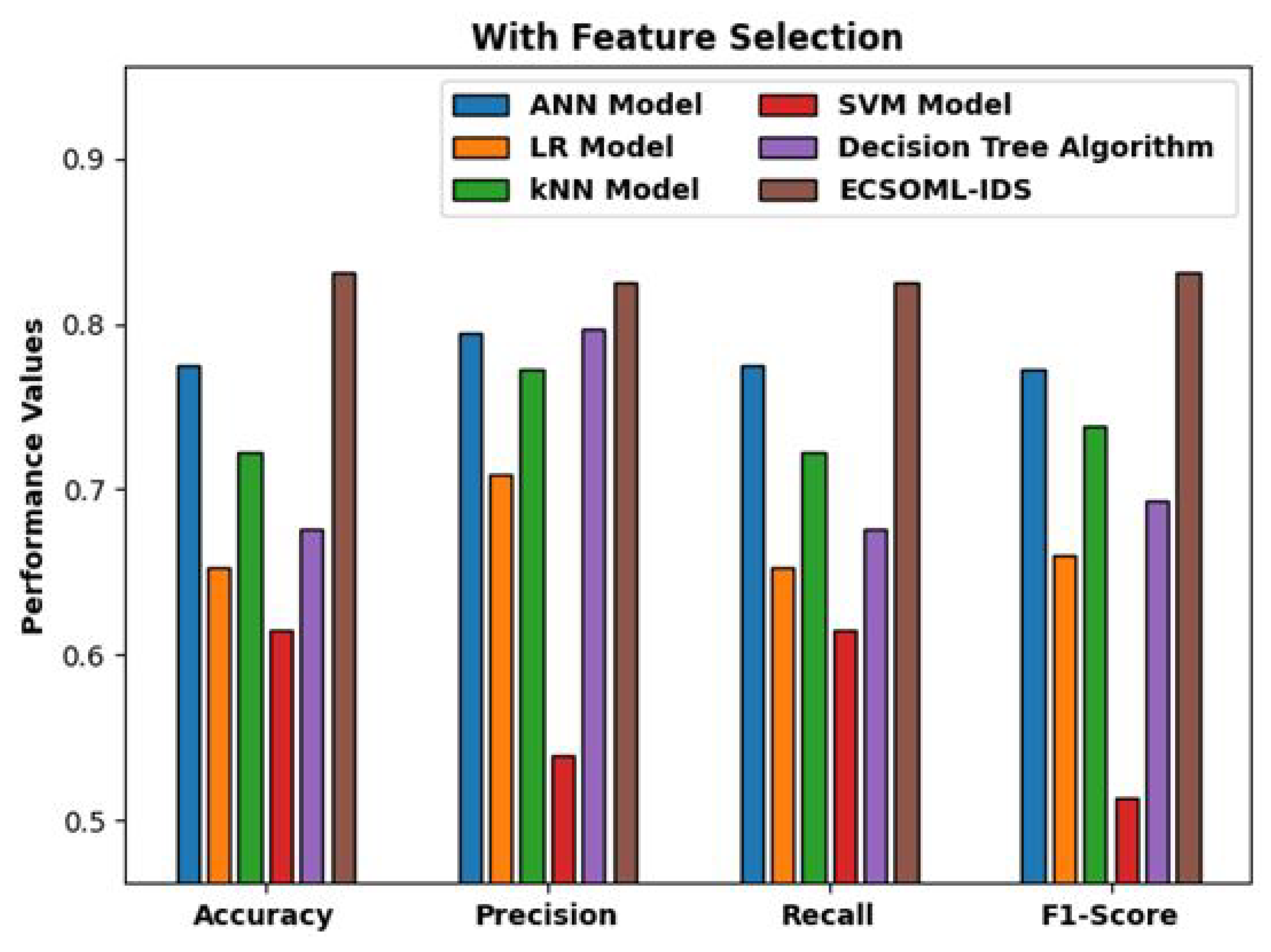
| Methods | Accuracy | Precision | Recall | F1 Score |
|---|---|---|---|---|
| ANN Model | 0.7751 | 0.7950 | 0.7753 | 0.7728 |
| LR Model | 0.6529 | 0.7088 | 0.6529 | 0.6596 |
| kNN Model | 0.7230 | 0.7724 | 0.7230 | 0.7381 |
| SVM Model | 0.6153 | 0.5395 | 0.6152 | 0.5131 |
| Decision Tree Algorithm | 0.6757 | 0.7966 | 0.6756 | 0.6926 |
| ESOML-IDS | 0.8309 | 0.8248 | 0.8250 | 0.8308 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alzubi, O.A.; Alzubi, J.A.; Alazab, M.; Alrabea, A.; Awajan, A.; Qiqieh, I. Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment. Electronics 2022, 11, 3007. https://doi.org/10.3390/electronics11193007
Alzubi OA, Alzubi JA, Alazab M, Alrabea A, Awajan A, Qiqieh I. Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment. Electronics. 2022; 11(19):3007. https://doi.org/10.3390/electronics11193007
Chicago/Turabian StyleAlzubi, Omar A., Jafar A. Alzubi, Moutaz Alazab, Adnan Alrabea, Albara Awajan, and Issa Qiqieh. 2022. "Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment" Electronics 11, no. 19: 3007. https://doi.org/10.3390/electronics11193007
APA StyleAlzubi, O. A., Alzubi, J. A., Alazab, M., Alrabea, A., Awajan, A., & Qiqieh, I. (2022). Optimized Machine Learning-Based Intrusion Detection System for Fog and Edge Computing Environment. Electronics, 11(19), 3007. https://doi.org/10.3390/electronics11193007








