Active Directory Attacks—Steps, Types, and Signatures
Abstract
:1. Introduction
- Domain services mediate communication between users and domains, save consolidated data, and offer search and login functions.
- Certificate services issue, maintain, and distribute secure certificates.
- Open (LDAP) protocol-compatible directory-enabled apps are supported by lightweight directory services.
- Directory federation services enable single sign-on (SSO) for users to log in to a variety of online apps in a single session.
- Rights management guards digital content that is subject to copyright by prohibiting its unlawful use and dissemination.
- Domain name resolution is performed via the DNS service.
- Summarize the main characterizing attributes of the Advanced Persistent Threats by exploring their meaning, signs, lifecycle, techniques, types of targets, comparison with malware, as well as protection and detection mechanisms.
- Illustrate the typical attack lifecycle for Active Directory and describe the different techniques.
- Show the signatures for pass the hash attack and Kerberoasting attack.
- Show how Kerberos protocol is exploited in various stages of the attack lifecycle.
2. Background
2.1. Kerberos Authentication Workflow
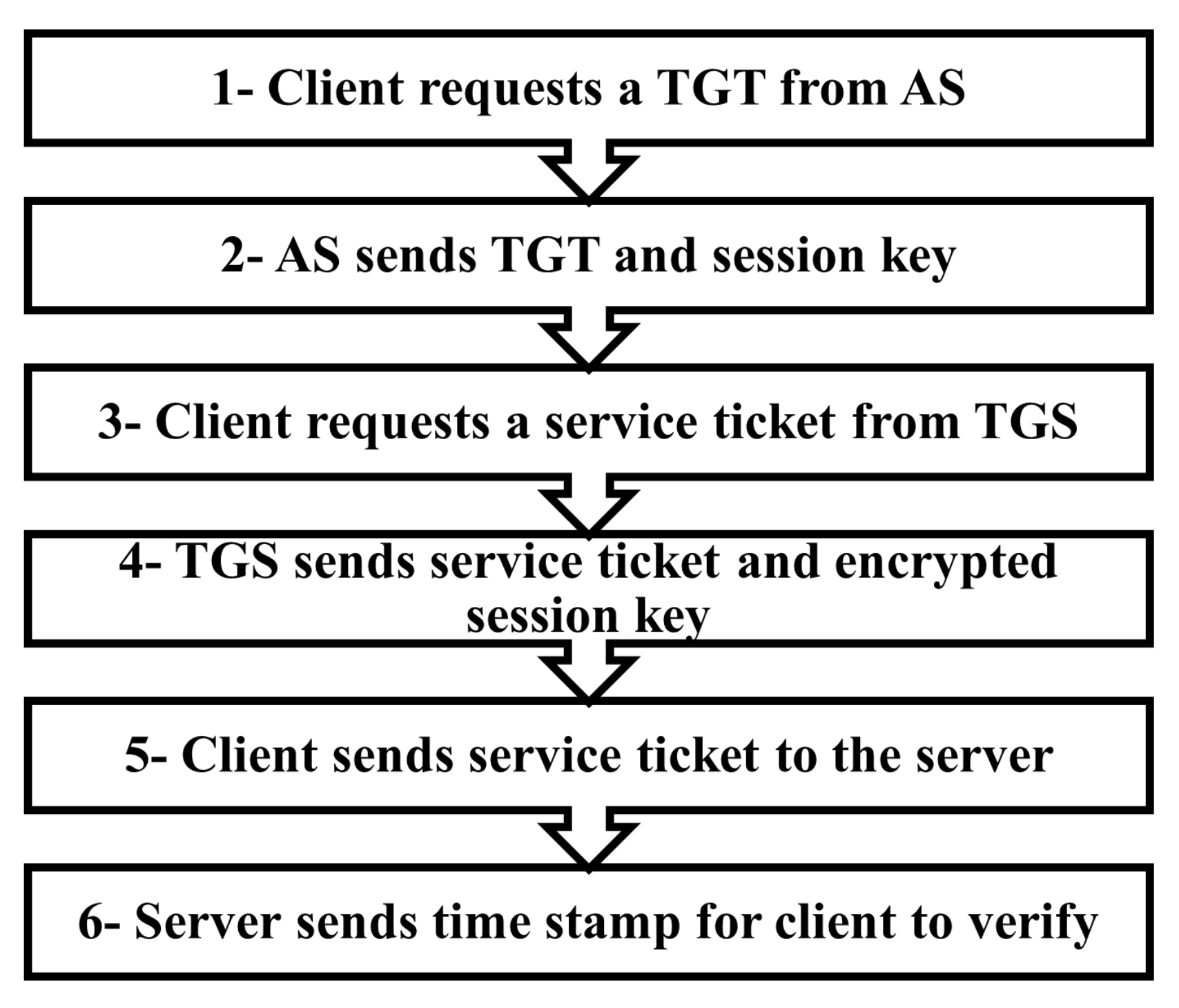
- The client hashes the user’s password. This hash is used as the secret key to secure communication between the client and the KDC.
- The client sends an encrypted timestamp with the secret key to the AS, and the AS verifies that the client knows the user’s password by decrypting the timestamp with the hash of the user’s password existing in the AD database. If the decryption is performed successfully, this implies that the client knows the correct user’s password.
- The AS replies to the above request by sending two sections of information:
- (a)
- The encryption key used for subsequent requests to the KDC, which is encrypted with the user’s hash.
- (b)
- The ticket-granting ticket (TGT) containing information about the user. This TGT is encrypted with the krbtgt account password which is known only by the TGS. This TGT is forwarded to the TGS in future requests for any service.
- Using the TGT received previously, the client creates a request for a specific service and sends the request along with the TGT to the TGS.
- The TGS decrypts the TGT and the request, verifies its legitimacy, and sends back a reply containing two parts to the client:
- (a)
- One part is a service ticket encrypted with the service secret key aimed to be sent to the server. This ticket contains the user’s group information, a session key to communicate with the client, and a timestamp.
- (b)
- This part contains the session key to be used between the client and the server. This part is encrypted with the key received from the AS’s reply in step 3.
- The client sends a request for the remote server coupled with the service ticket received in the previous step. The server accepts this request if it decrypts the service ticket successfully with the key shared between it and the KDC, which implies that this request is authorized by the KDC.
2.2. Kerberos Security Issues
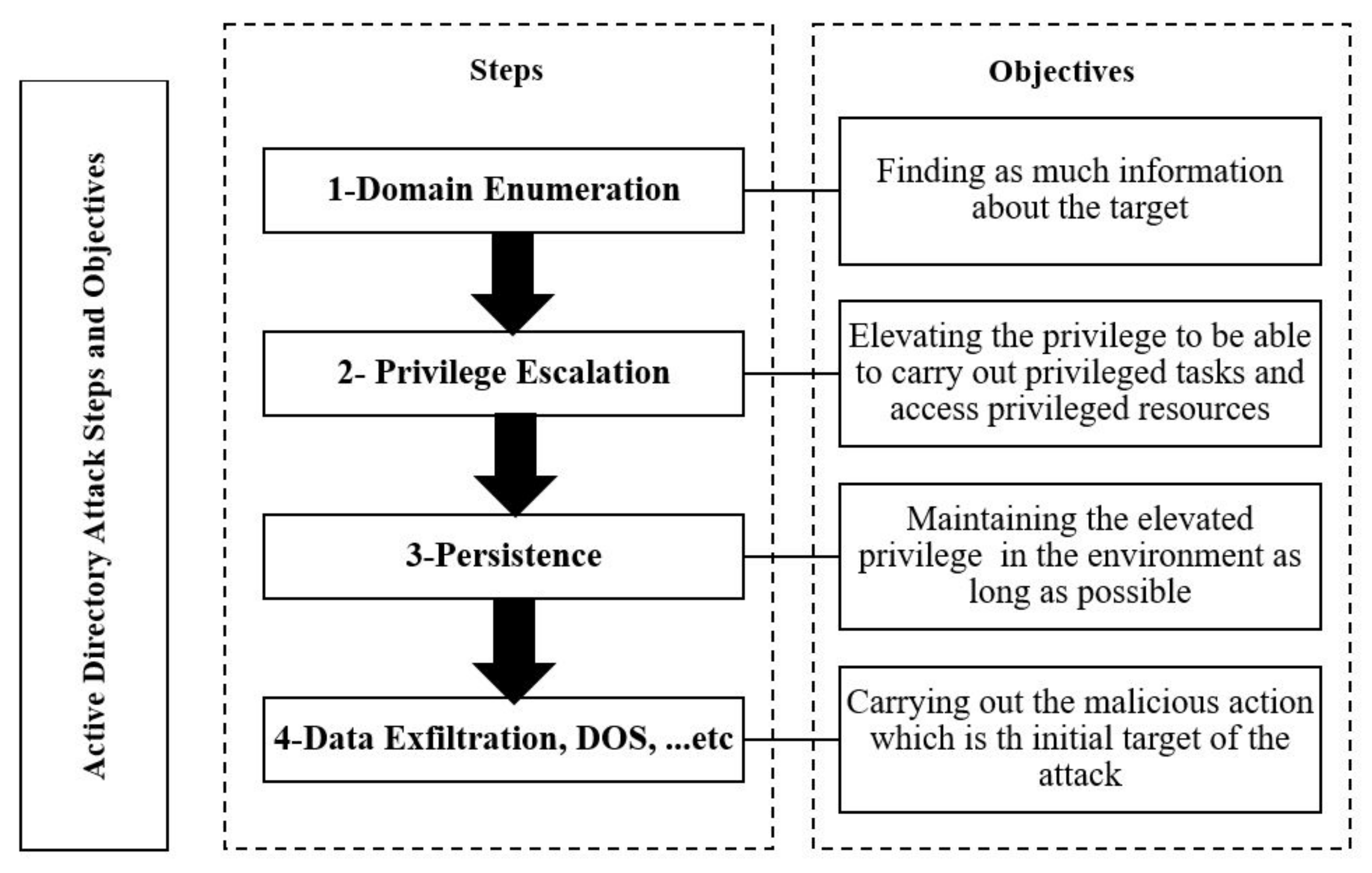
3. Active Directory Attack Phases
3.1. Domain Enumeration
- Net.exe: The net.exe is a built-in tool in Windows that can be used to carry out tasks on groups, users, accounts, policies, etc. [17]. Using the net.exe tool, the attacker can see all the attributes of users and groups and hunt for critical groups such as AD domain admins and can then see information about the user’s group membership.
- Active Directory module: Active Directory [18] allows administrators to query and make changes to Active Directory with PowerShell. It comprises a set of PowerShell cmdlets that can retrieve a lot of information about the current domain [19]. While this module needs remote server administration tools (RSAT) installed [19], there are ways in which the attacker can leverage to import this module into any workstation [20].
- Powerview: Powerview is part of the Powersploit framework, and it is a PowerShell tool used in domain enumeration that can act as a replacement for Windows net commands [21]. It can provide the same functionality as the AD module. It also has some extra functions which the attacker can leverage to identify the locations in the network where specific users are logged in to [22].
- Bloodhound: Bloodhound is a GUI tool used by red and blue teams to visualize AD domains and to facilitate the identification of complex attack paths and gain deep knowledge about privilege relationships in AD systems [23].
3.2. Privilege Escalation
- Pass the hash attack: The pass the hash (PTH) attack has been evolving for years. It depends on hash extraction from a compromised machine and using this hash to create tokens that allow access to sensitive resources or hosts across the domain. While Microsoft has been implementing many security measures in each new Windows version to prevent PTH attacks, new techniques evolve continuously to carry out this attack successfully [25].Windows hosts store credentials in the form of NT hashes [25]. In PTH attacks, adversaries use the fact that NTLM hashes can be used for authentication without using the user’s password. PTH involves two stages: (1) the first stage is extracting the hashes of certain users depending on their availability and (2) the second stage is creating tokens using extracted hashes by tools such as Mimikatz [26]. It is important to note that PTH can give attackers privileges equivalent to the user’s password without having to know the actual password. Attackers usually try to extract high-privileged accounts’ passwords and use them in PTH attacks to escalate their privilege.The most common technique to carry out stage (1) is to dump the credentials in the memory of the Local Security Authority Subsystem Service (LSASS) process. LSASS stores information in its memory about all accounts that are used actively including the NT hash [27]. These hashes are used to provide a single sign-on experience to users in order to avoid entering the password each time the user wants to access a resource [28]. Extracting the hash of a domain admin account provides the attacker with the ability to access the same resources granted to the domain admin user without knowing its password. The most secure measure to protect against PTH attacks is to protect the memory of the LSASS process and prevent accessing it [29]. This feature is implemented in Windows Defender Credential Guard (WDCG) which makes the LSASS process not accessible to malicious applications [29]. While this feature prevents hash extraction from LSASS memory, other ways can be used to extract the hashes [30].
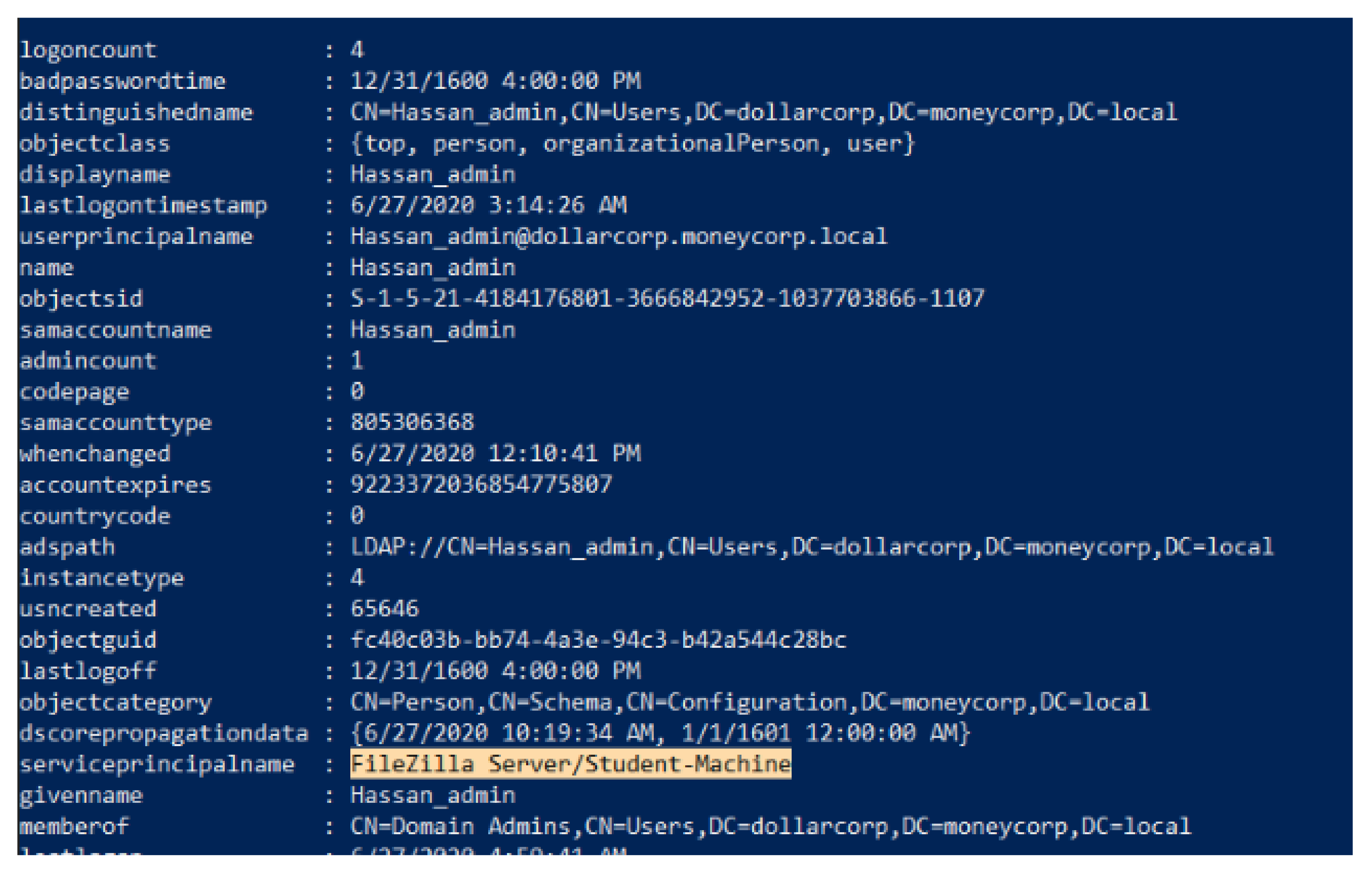
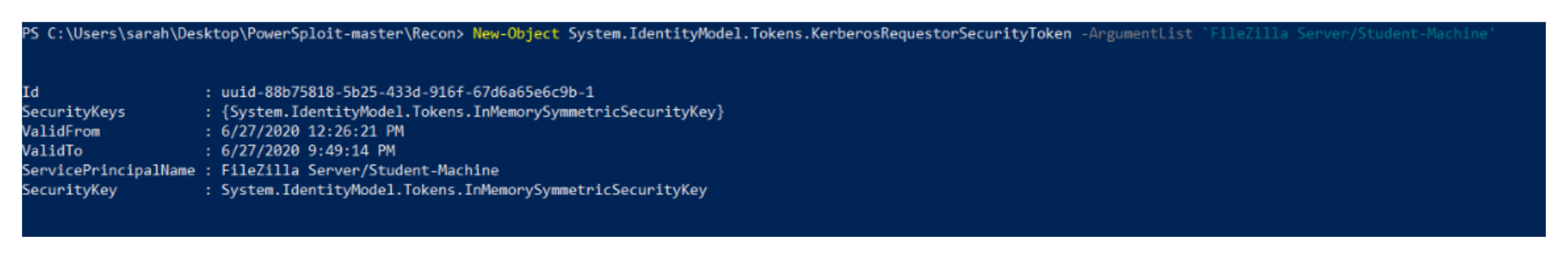
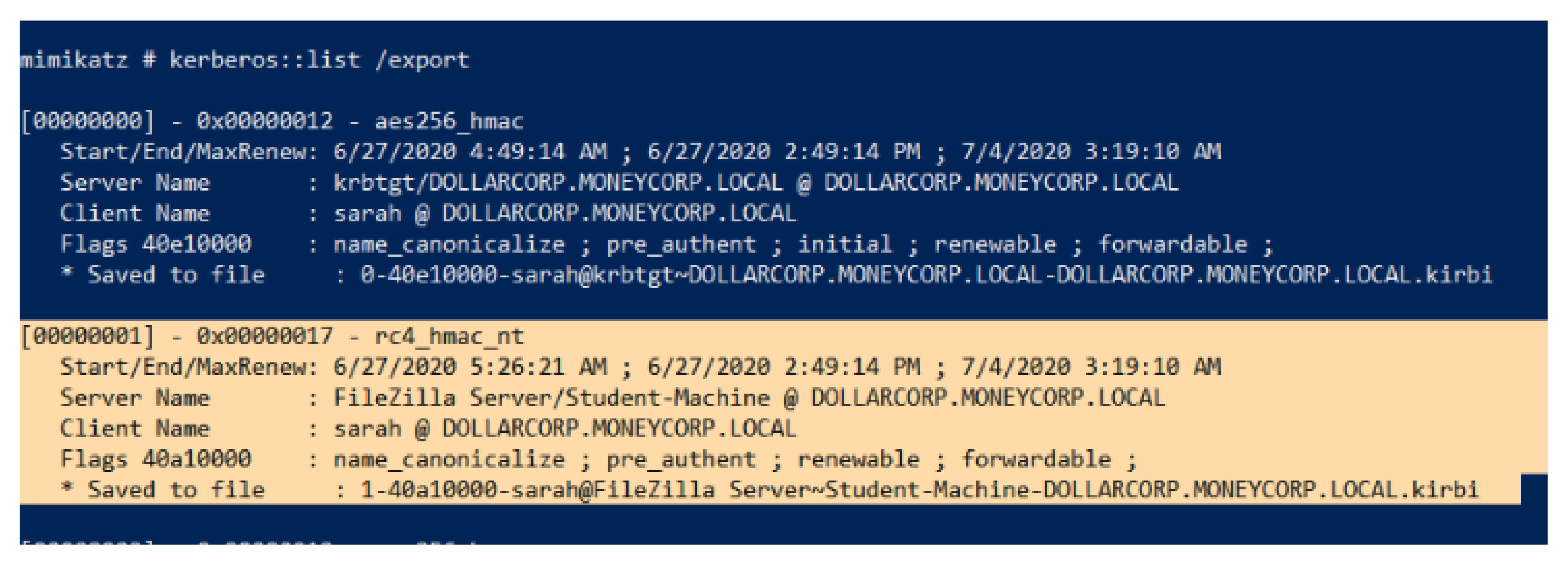
- Kerberoasting attack: Kerberoasting is an attack relying on the fact that some services run under normal user accounts. If a service runs under a user account, the service ticket provided by AD for this service is encrypted by the NTLM hash of the user’s password. Grabbing the ticket and brute forcing it allows access to the plaintext password of the target user. The service principal name (SPN) attribute of a user indicates if a service is running under this user account. The procedure for performing a Kerberoasting attack is shown in Figure 3, and it is carried out as follows:The attacker scans the AD environment for any user who has the SPN attribute defined as PowerShell, LDAP queries, or any custom tool such as Powersploit. After grabbing the target account, the user asks the AD for a service ticket using the SPN value of the target account. Exporting the ticket to the disk and brute forcing it reveals the user’s password, which is the final stage. Another variation of the Kerberoasting attack is the targeted Kerberoasting attack, which can be of two types:
- The first is where the attacker grabs the AS-REP Kerberos messages which are encrypted by the user’s hash. For this attack to happen, the UserAccountControl settings must contain the “Don’t require Kerberos pre-authentication“ setting to be enabled.
- The second is when the attacker has a high privilege to set the SPN value of any user to any dummy service and then request a service ticket for this service which can then be cracked to obtain the user password.
Mitigations for this attack include enforcing a strong and complex password policy, enabling Kerberos encryption rather than RC4, and limiting the privileges for service accounts [1]. - Constrained and unconstrained delegation abuse: Delegation is an Active Directory feature that permits the impersonation of an account by users or computers [31]. Enabling this feature is available through the delegation tab on a user or computer account [32]. Through this tab, constrained and unconstrained delegation can be enabled and customized.
3.3. Unconstrained Delegation
- Constrained delegation: Unlike unconstrained delegation, constrained delegation provides access to a specific set of services listed in the ]msDS-AllowedToDelegateTo attribute on the user configuration. The steps for abusing the constrained delegation are illustrated in Figure 4 and are as follows. The attacker compromises an account with constrained delegation enabled by dumping its hash, using Mimikatz for example. The attacker then can request a TGT for the compromised account and then a TGS to access any service listed on the msDS-AllowedToDelegateTo attribute as any privileged user.One interesting fact about this attack is that the SPNS is not checked when requesting TGS, which leads the attacker to access any service running under the same account. For example, if the CIFS service is listed in the msDS-AllowedToDelegateTo attribute then the attacker can access any service which is running under the same account as the CIFS service [35]. The above fact can lead to the compromise of the entire domain if exploited successfully.Mitigations for constrained delegation abuse typically put critical accounts in the protected users group or mark the account as sensitive and cannot be delegated on the account tab [36].
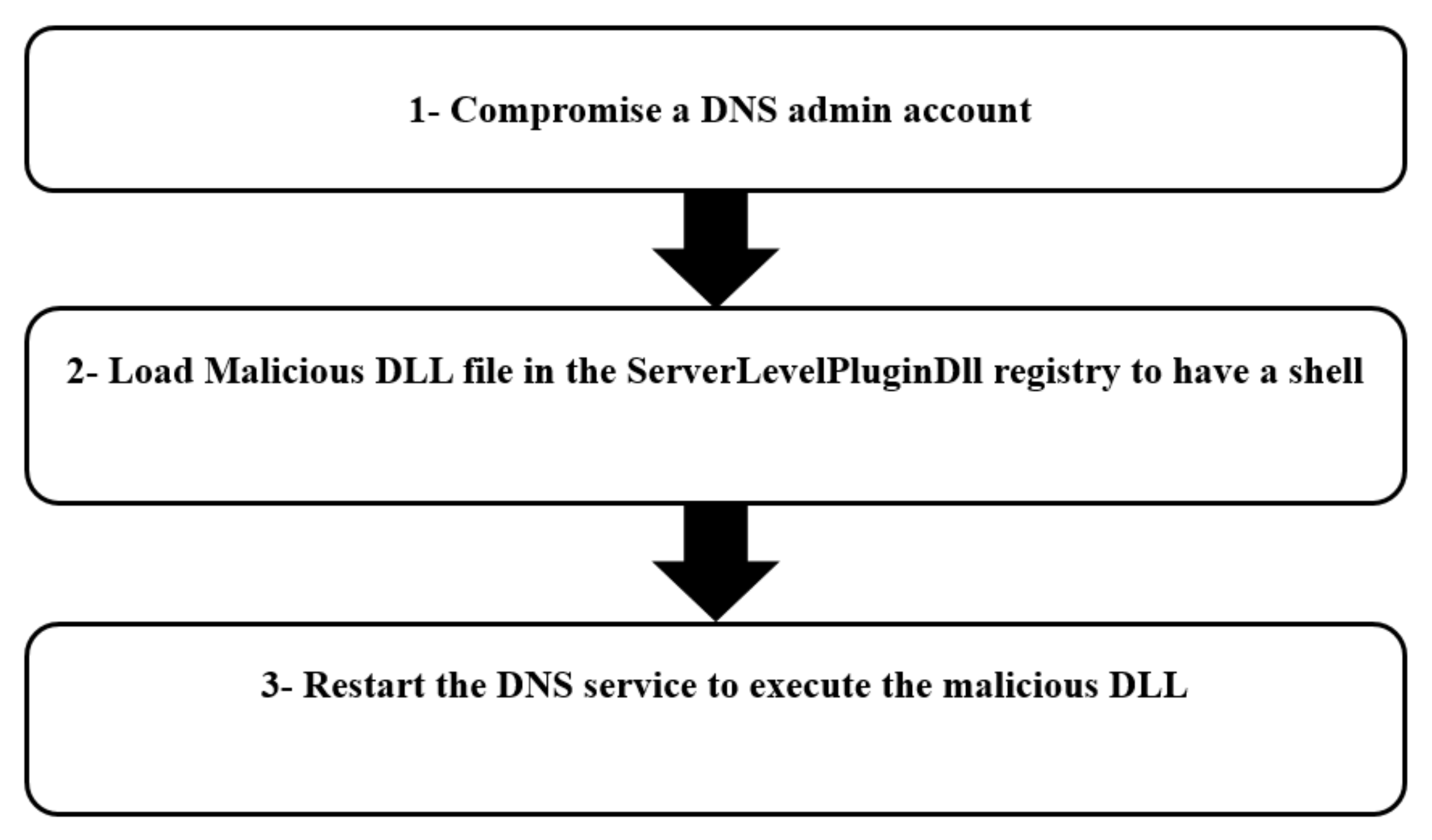
- Abusing DNS admins’ privileges: Abusing DNS admins’ privileges is a technique where a DNS admin member can escalate their privileges to system privilege if he has the rights to configure server-level plugin DLL and to restart the DNS service [36]. By injecting a malicious DLL executing a reverse shell to the attacker machine into the dns.exe service and restarting the service, the attacker can have a shell on the DNS server as a system account which is the highest privileged account.While the DNS admins are not granted the necessary privileges by default, it is common for DNS admins to be given the right to restart the DNS service and to inject the DLLs in the HKEY_LOCAL_MACHINE∖SYSTEM∖CurrentControlSet∖services∖DNS∖Parameters∖ServerLevelPluginDll registry.The stages for performing this attack are shown in Figure 5 and are illustrated as follows: The attacker compromises a machine having a ticket for a DNS admin user and having a local admin privilege on it. The attacker uses the ticket to inject the malicious DLL file containing a reverse shell in the ServerLevelPluginDll registry. Next step is to force a restart for the DNS service. Once the DNS service is restarted, the dns.exe executes the malicious DLL as the system user and returns a reverse shell to the attacker as the system account. If the DNS server in the environment is the same domain controller server, the above attack leads to the compromise of the entire domain. Common mitigations for this attack are monitoring the DNS service status and the ServerLevelPluginDll registry for any changes and limiting the privilege to load DLL files to only specific users, not all the DNS admins, if required.
- Domain persistence The next step after escalating privileges in an AD attack is to persist as long as possible with an elevated privilege in order to achieve the attack target. While there are many techniques of postexploitation persistence in the AD system, some of the techniques are common, while others are rare and have many limitations. In this section, we illustrate the common attacks by which an adversary persists in the AD environment. We go through the golden and silver ticket attacks in detail, as they are more common and give brief information about some other tactics which are less common and have more limitations.
- (a)
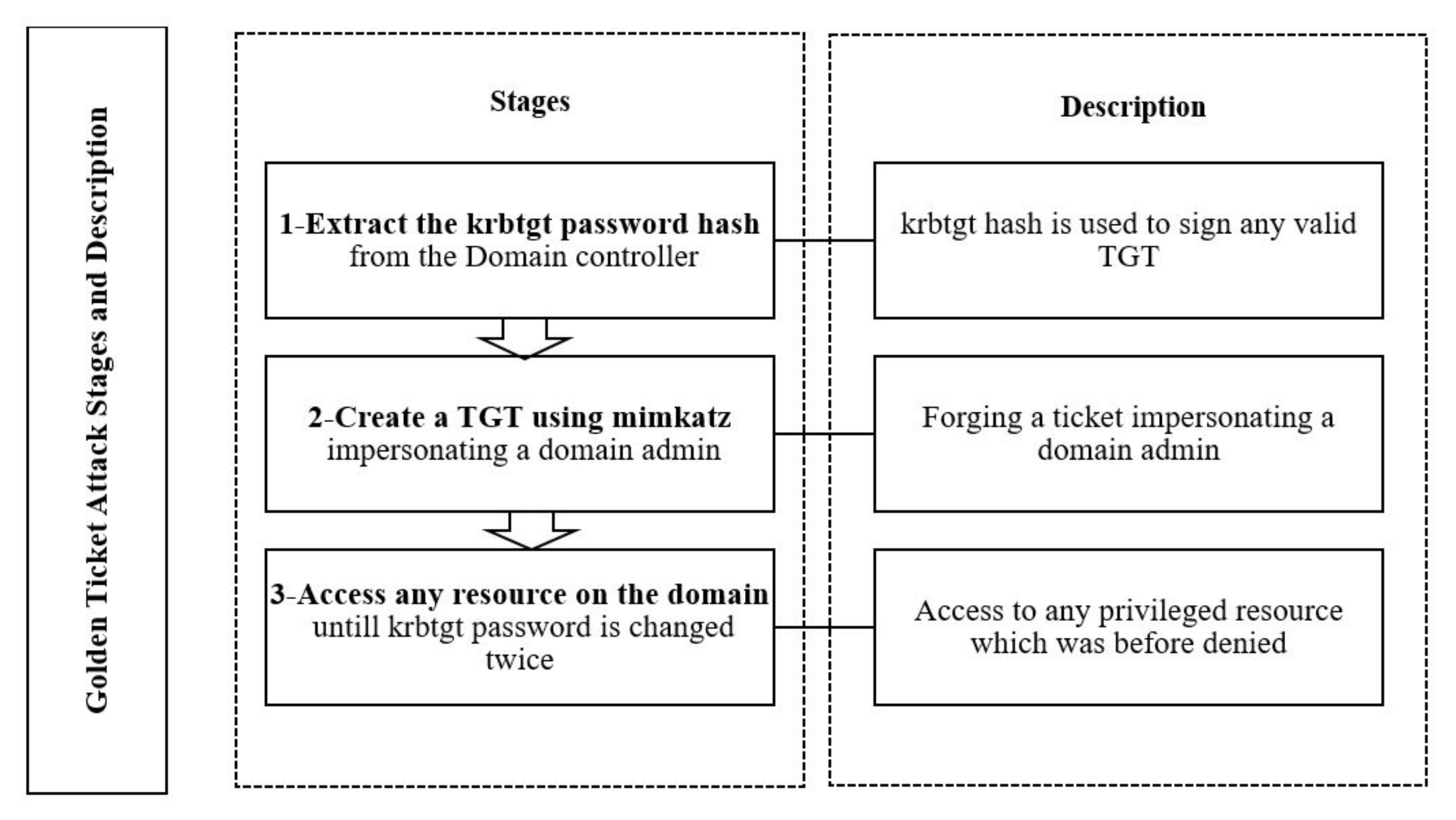
- Golden ticket attack: Golden tickets are user-created TGTs which are used to give the attackers access to specific resources. Intruders use the TGTs to obtain service tickets from the domain controller without verifying the contents of the TGT [37]. In Kerberos protocol, the TGT is used to prove to the KDC service on the domain controller that the user is authenticated to the DC. The TGT is encrypted with the krbtgt account NTLM hash. The way the KDC verifies the integrity of the TGT is by trying to decrypt it with the krbtgt hash. Once it is decrypted successfully, the KDC grants the user the service tickets without verifying the contents of the TGT unless the TGT’s age is older than 20 min [38]. Given the above behavior, an attacker who has domain admin privileges to the DC can follow the steps in Figure 6 to dump the krbtgt hash and use it to forge a TGT impersonating any user and persisting with high privileges for a very long time. Interesting facts about this attack are that the attacker can impersonate any user, even if the user does not exist in the domain on any machine joined or not joined to the domain, and also that the krbtgt password is rarely changed [38]. Once this attack is carried out successfully, the only way to stop it is to change the krbtgt account password twice. The dumping and generation of golden tickets are usually conducted using the Mimikatz tool, which provides the ability to modify the security identifier (SID) history attribute in the TGT. The SID is an identifier that is used by the AD system to verify the privilege of a user, and the SID history is an attribute that includes more than one SID. This attribute can be exploited to include the SIDs of various domains and exploit the entire forest.
- (b)
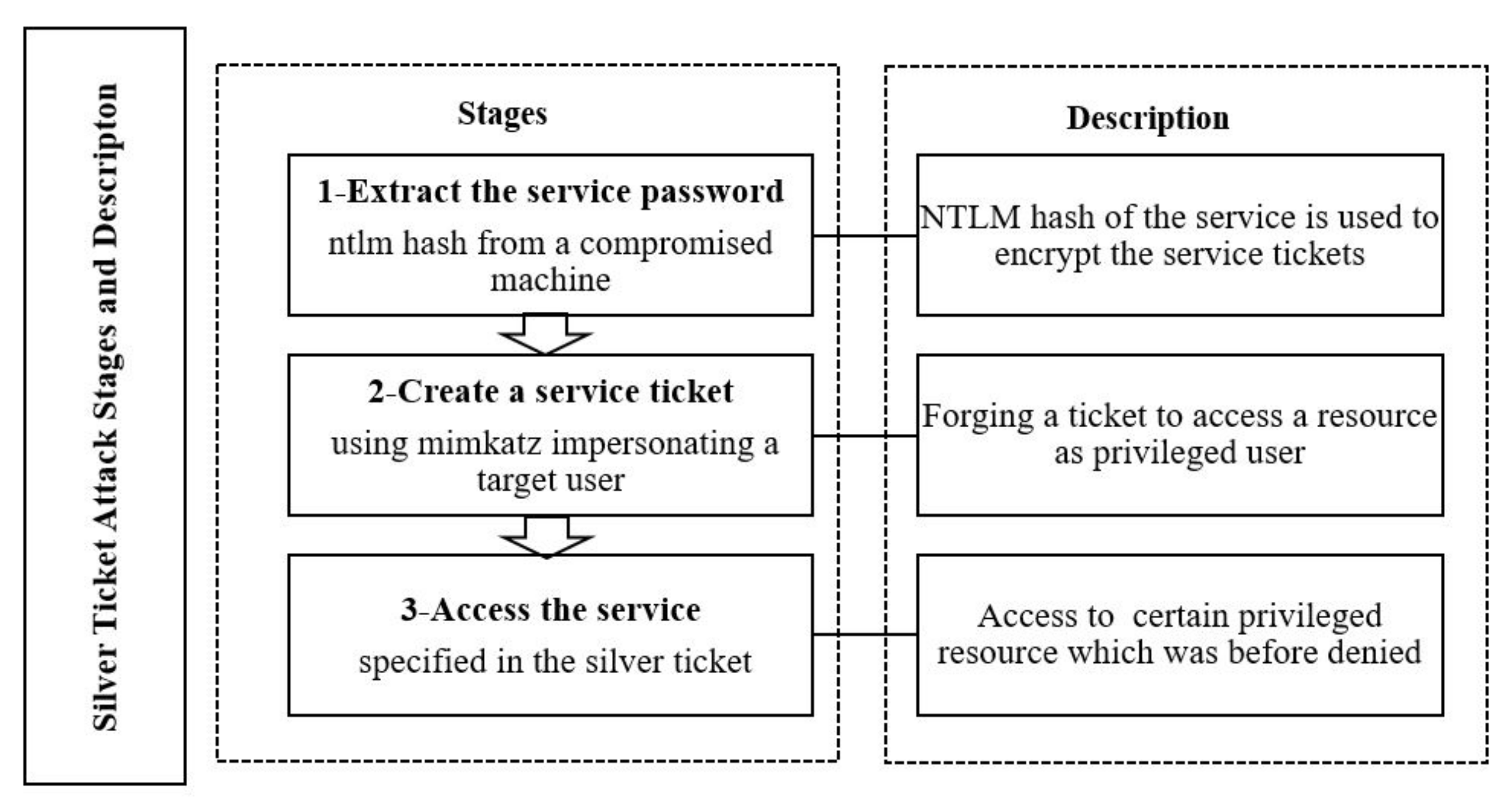
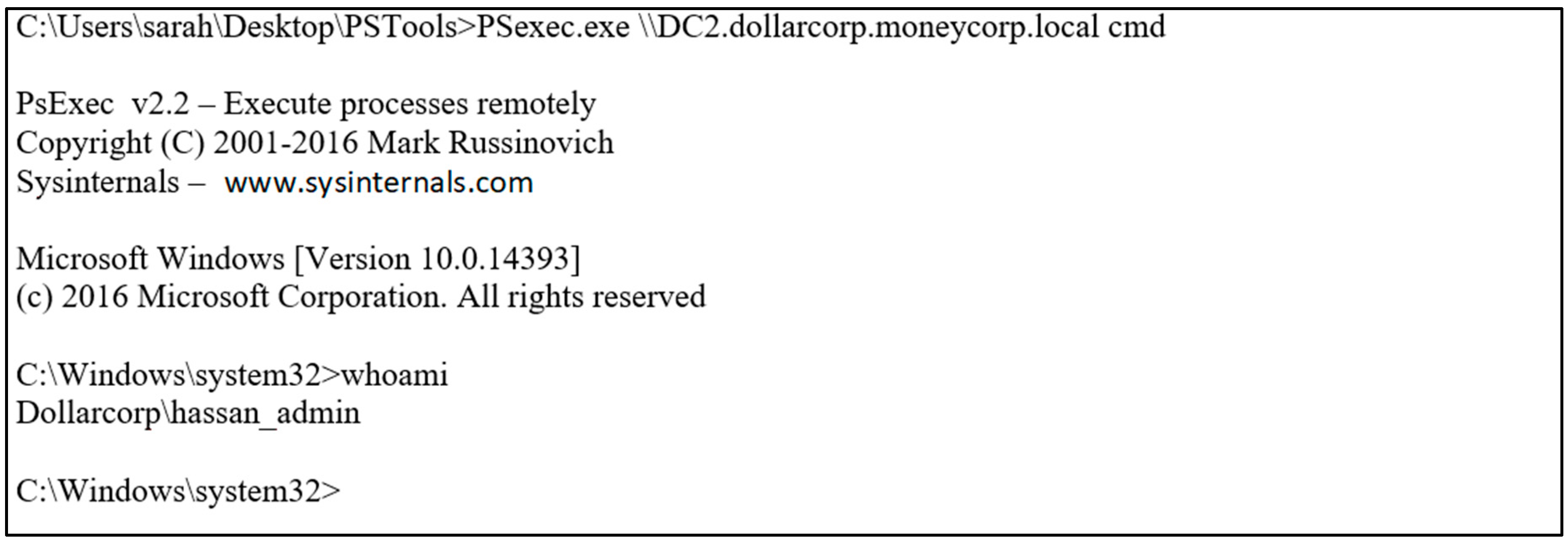
- Silver ticket attack: Silver tickets are service tickets that are used to access certain services, unlike golden tickets which are TGTs providing access to all services. The flow for the silver ticket is presented in Figure 7. The attacker gets access to the NTLM hash of a service account and then uses a tool such as Mimikatz to forge a service ticket to access this service, impersonating any user.The authors in [39] showed how to use a silver ticket attack to compromise the domain controller again after the golden ticket attack has been stopped by resetting the krbtgt password twice. The attack is carried out against the host service of the domain controller to create a scheduled task to dump the credentials using Mimikatz and obtain the krbtgt password again. While the silver ticket attack has a narrower scope than the golden ticket attack, according to [39], it has a more dangerous effect, as it is easier to be performed and its technique does not involve communication with the domain controller, which makes it stealthier and harder to detect. The best way to prevent silver ticket attacks is to enforce security controls and use complex passwords for service accounts to minimize the probability of their exposure [39].
- (c)
- Skeleton key attack: Skeleton key is an attack carried out against the domain controllers. The adversary targets the Local Security Authority Subsystem Service (LSASS) process in the domain controller [40]. The LSASS process is responsible for the entire system of authentication in the Active Directory. The attacker patches the LSASS process to create a master password to work for any account. Although the attack is not compatible with Windows Server 12 or later, it still possesses a great risk, as a lot of companies still use outdated versions of Windows [40]. The procedure for carrying out the skeleton key attack is as follows. The attacker compromises the domain controller and acquires the domain admin privileges. He then runs mimikatz.exe “privilege::debug” “misc::skeleton” exit on the domain controller. After running successfully, a master password is created which enables login with any account with password Mimikatz. Upon running, the skeleton key carries out the tasks shown in Table 2.
- i.
- Check for one of the following compatible 64-bit versions. The malware does not work with 32-bit Windows versions or with Windows Server versions beginning with Windows Server 2012 (6.2).
- ii.
- Use the SeDebugPrivilege function to acquire the necessary elevated privileges to write to the (LSASS) process. This process controls user account authentication.
- iii.
- Enumerate available processes to acquire a handle to the LSASS process.
- iv.
- Obtain addresses for authentication-related functions that should be patched.
- A.
- CDLocateCSystem—placed in cryptdll.dll.
- B.
- SamIRetrieveMultiplePrimaryCredentials—placed in samsrv.dll.
- C.
- SamIRetrievePrimaryCredentials—placed in samsrv.dll.
- v.
- Perform OS-specific modifications using the global variable set during the compatibility check in step 1.
- vi.
- Use the OpenProcess function to get a handle to the LSASS process.
- vii.
- Reserve the required memory space to alter and patch the LSASS process’s memory.
- viii.
- Patch relevant functions depending on the operating system:
- A.
- CDLocateCSystem (all compatible Windows versions).
- B.
- SamIRetrieveMultiplePrimaryCredentials (only Windows 2008 R2 (6.1)).
- C.
- SamIRetrievePrimaryCredentials (all compatible Windows versions other than Windows 2008 R2 (6.1)).
After rebooting the DC, the LSASS process memory is refreshed and the master password is no longer valid. In addition, for this attack to operate successfully without error, the skeleton key needs to be installed on all domain controllers to answer any logon attempt successfully [41]. The best prevention for this attack is to limit the number of domain admins and ensure they cannot log in to less protected machines where their credentials can be dumped [29]. - (d)
- DSRM persistence: The directory services restore mode (DSRM) account is a local administrator account existing on every domain controller. The DSRM password is set at the time of promoting the DC and it is seldom changed [42]. The main function of the DSRM account is to provide the administrator with a backdoor to the database to recover or repair any failure. While this account does not provide access to the domain or its services by default, the attacker can manipulate its configuration to have local admin access to the domain controller and compromise the entire domain [43]. The attacker performs this attack using Mimikatz by dumping the SAM database of the domain controller and performing the pass the hash attack using the NTLM hash acquired to maintain a valid TGT, providing access to all domain services. The mitigation technique for this attack is to make sure that the registry key DsrmAdminLogonBehavior does not exist or its value equal to 1 to disable logging in with the DSRM account [42].
- (e)
- SSP persistence attacks: The security support provider (SSP) is an API used by Windows to carry out the authentications of Windows login. It is a DLL file that provides security packages to other applications. This DLL stacks itself up in LSA when the system starts, making it a start-up process. After it is loaded in LSA, it can access all the Windows credentials. An SSP attack can be carried out using Mimikatz by issuing the MemSSP command, and this command registers a malicious SSP on a Windows host [44]. The injected SSP logs all the logged-on user’s passwords in cleartext [44]. Once an attacker has domain admin privileges to a domain controller, he can issue this malicious command to obtain the passwords of another privileged account who has logged on to the domain controller. To detect this attack, the c:\Windows\System32 path for a log file called mimilsa.log file which is produced by Mimikatz should be monitored [44].
- (f)
- Access Control List abuse: Access rights for any object in the AD environment are provided through an Access Control Entry (ACE). An ACE defines the access or audit permission granted for a specific user or group. An ACL is an attribute for any object in AD. Each ACL contains a group of ACEs defining the right for each user to access this object [45]. Modifying the ACLs of certain objects in the AD tree can give the attacker access to resources that cannot be accessed by default. In this section, we illustrate uses by cyber criminals to modify the ACLs of objects in common techniques in AD to persist in the environment and gain high privilege.
3.4. Abusing AdminSDHolder ACL
3.5. Remote Access Methods for ACL Abuse
- WMI ACL abuse: WMI is the Microsoft implementation of web-based enterprise management (WBEM). Data in WMI are grouped into WMI classes. For example, there is a WMI class for logical drives (Win32_LogicalDisk), and there is a class for running processes (Win32_Process). WMI classes are then grouped into WMI namespaces. Most of the WMI classes exist under the root∖cimv2 WMI namespace, but there are other namespaces (for example, rootMicrosoftExchangev2) that contain WMI classes related to a specific Microsoft application. To find data, an administrator can navigate through the hierarchy. For example, if there is a need to find the amount of free disk space on a logical disk, navigation should be performed as follows.root∖cimv2 namespace>Win32_LogicalDisk WMI>A WMI namespace is just a container for WMI classes. By keeping different WMI classes in different WMI namespaces, Windows allows users to specify different access permissions for different WMI classes. Connecting to a remote computer using WMI requires the correct distributed component object model (DCOM) settings and WMI namespace security settings to be enabled for the connection. ACLs exist for DCOM endpoints and for WMI namespaces to ensure authorized users access the resources only [47]. An adversary having domain admin privileges can modify the ACLs of the DCOM endpoint and the WMI namespaces to allow connecting to different computers using WMI. For example, the below PowerShell command allows WMI access to ops-mssql computer for lab users without being a member of any privileged group [47]. Set-RemoteWMI -ComputerName ops-mssql -SamAccountName labuser –VerboseIt is worth mentioning that WMI ACL modification does not leave any event logs, but 4624 and 4634 logs appear when using WMI access [47].
- PS remoting ACL abuse: PowerShell remoting is a Windows feature that allows interactive sessions with remote computers, running commands or scripts, and starting a persistent session with a remote computer [48]. By default, administrator privilege is required to use PowerShell remoting. However, an attacker having domain admin privileges can modify the ACL of the PowerShell remoting endpoint to give a user read, write, and execute permissions. Once these permissions are granted, the user can connect to remote computers and run commands or scripts without having domain admin privilege [47]. As for WMI access, accessing machines using PS remoting does not leave any logs except 4264 and 4634 when logging in and out.
4. Related Work
4.1. Defending against Credential Theft Attacks
4.2. Assessing Active Directory Security and Vulnerabilities
4.3. Active Directory Attack Detection
4.4. Defending against Account Lockout Attacks
5. Experimental Work and Analysis
5.1. Lab Setup and Methodology
5.2. Pass the Hash Attack
5.3. Kerberoasting Attack
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kotlaba, L.; Buchovecká, S.; Lórencz, R. Active Directory Kerberoasting Attack: Detection using Machine Learning Techniques. In Proceedings of the 7th International Conference on Information Systems Security and Privacy (ICISSP 2021), Online, 11–13 February 2021; pp. 376–383. [Google Scholar]
- Gkotsis, P. Creating a Windows Active Directory Lab and Performing Simulated Attacks. Master’s Thesis, University of Piraeus, Piraeus, Greece, 2021. [Google Scholar]
- Pektaş, A.; Başaranoğlu, E. Practical Approach For Securing Windows Environment: Attack Vectors And Countermeasures. In Proceedings of the 7th International Conference on Information Systems Security and Privacy (ICISSP 2021), Online, 11–13 February 2021; pp. 376–383. [Google Scholar]
- Matsuda, W.; Fujimoto, M.; Mitsunaga, T. Detecting apt attacks against active directory using machine learning. In Proceedings of the 2018 IEEE Conference on Application, Information and Network Security (AINS), Langkawi, Malaysia, 21–22 November 2018; pp. 60–65. [Google Scholar]
- Jeun, I.; Lee, Y.; Won, D. A practical study on advanced persistent threats. In Computer Applications for Security, Control and System Engineering; Springer: Berlin/Heidelberg, Germany, 2012; pp. 144–152. [Google Scholar]
- Advanced Persistent Threat (APT) Attacks. Available online: https://www.cynet.com/advanced-persistent-threat-apt-attacks/ (accessed on 30 July 2022).
- Fireeye Advanced Threat Report 2013: FireEye Labs. 2013. Available online: https://www2.fireeye.com/rs/fireye/images/fireeye-advanced-threat-report-2013.pdf (accessed on 30 July 2022).
- Quintero-Bonilla, S.; Martín del Rey, A. A new proposal on the advanced persistent threat: A survey. Appl. Sci. 2020, 10, 3874. [Google Scholar] [CrossRef]
- Kaspersky. Kaspersky’s 2019 IT Security Economics Report. Available online: https://go.kaspersky.com/rs/802-IJN-240/images/GL_Kaspersky_Report-IT-Security-Economics_report_2019.pdf (accessed on 9 September 2021).
- Steiner, J.G.; Neuman, B.C.; Schiller, J.I. Kerberos: An Authentication Service for Open Network Systems. In Proceedings of the Usenix Winter, Dallas, Texas, USA, 9–12 February 1988; pp. 191–202. [Google Scholar]
- Alva, D.; Benjamin, D. Abusing Microsoft Kerberos. Available online: https://www.blackhat.com/docs/us-14/materials/us-14-Duckwall-Abusing-Microsoft-Kerberos-Sorry-You-Guys-Don’t-Get-It.pdf (accessed on 9 September 2021).
- Github. BloodHoundAD. Available online: https://github.com/BloodHoundAD/BloodHound (accessed on 13 September 2021).
- Will Schroeder. PowerSploit. Available online: https://github.com/PowerShellMafia/PowerSploit/tree/master/Recon (accessed on 13 September 2021).
- Cybersecurity Bits, Bobs. Active Directory Domain Enumeration. Available online: https://mlcsec.com/active-directory-domain-enumeration/# (accessed on 13 September 2021).
- Motero, C.D.; Higuera, J.R.B.; Higuera, J.B.; Montalvo, J.A.S.; Gómez, N.G. On Attacking Kerberos Authentication Protocol in Windows Active Directory Services: A Practical Survey. IEEE Access 2021, 9, 109289. [Google Scholar] [CrossRef]
- Diogenes, Y.; Ozkaya, E. Cybersecurity—Attack and Defense Strategies: Infrastructure Security with Red Team and Blue Team Tactics; Packt Publishing Ltd.: Birmingham, UK, 2018. [Google Scholar]
- White, S. Net.exe. Available online: https://docs.microsoft.com/en-us/windows/win32/winsock/net-exe-2 (accessed on 13 September 2021).
- Ebad, S.A. Lessons learned from offline assessment of security-critical systems: The case of microsoft’s active directory. Int. J. Syst. Assur. Eng. Manag. 2022, 13, 535. [Google Scholar] [CrossRef]
- Microsoft. Active Directory. Available online: https://docs.microsoft.com/en-us/powershell/module/activedirectory/?view=windowsserver2019-ps (accessed on 13 September 2021).
- Melnick, J. How to Create New Active Directory Users with Powershell, SysAdmin Magazine, June 2019. Available online: https://blog.netwrix.com/2018/06/07/how-to-create-new-active-directory-users-with-powershell/ (accessed on 13 January 2022).
- Fletcher, D.R., Jr. Cyber Threat Intelligence Uses, Successes and Failures: The SANS 2017 CTI Survey. Available online: www.sans.org/reading-room/whitepapers/analyst/cyber-threat-intelligence-uses-successes-failures-2017-cti-survey-37677 (accessed on 14 March 2017).
- TNelson; Kettani, H. Open source powershell-written post exploitation frameworks used by cyber espionage groups. In Proceedings of the 2020 3rd International Conference on Information and Computer Technologies (ICICT), San Jose, CA, USA, 9–12 March 2020; pp. 451–456. [Google Scholar]
- Lemmens, M. BloodHound—Sniffing Out the Path Through Windows Domains. Available online: https://www.sans.org/blog/bloodhound-sniffing-out-path-through-windows-domains/ (accessed on 13 September 2021).
- Myllyla, J.; Costin, A. Reducing the Time to Detect Cyber Attacks: Combining Attack Simulation With Detection Logic. In Proceedings of the Conference of Open Innovations Association FRUCT (FRUCT Oy, 2021), Oulu, Finland, 27–29 October 2021. [Google Scholar]
- Rights, R.F. Use Offense to Inform Defense. Find Flaws before the Bad Guys Do; SANS Institute: Rockville, MD, USA, 2015. [Google Scholar]
- El-Hadidi, M.G.; Azer, M.A. Traffic Analysis for Real Time Applications and its Effect on QoS in MANETs. In Proceedings of the 2020 15th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, 15–16 December 2020; pp. 1–6. [Google Scholar]
- Dimov, D.; Tzonev, Y. Pass-the-hash: One of the most prevalent yet underrated attacks for credentials theft and reuse. In Proceedings of the 18th International Conference on Computer Systems and Technologies (2017), Ruse, Bulgaria, 23–24 June 2017; pp. 149–154. [Google Scholar]
- Roobol, S.; Offerman, N.; de Laat, C.; van de Wouw, D.; Huijgen, A. Development of Techniques to Remove Kerberos Credentials from Windows Systems, M.Sc; Security and Network Engineering, School of Computer Science, University of Amsterdam: Amsterdam, The Netherlands, 2019. [Google Scholar]
- Badhwar, R. Advanced Active Directory Attacks and Prevention. In The CISO’s Next Frontier; Springer: Midlothian, VA, USA, 2021; pp. 131–144. [Google Scholar]
- Ah-Fat, P.; Huth, M.; Mead, R.; Burrell, T.; Neil, J. Effective detection of credential thefts from windows memory: Learning access behaviours to local security authority subsystem service. In Proceedings of the 23rd International Symposium on Research in Attacks, Intrusions and Defenses (RAID 2020), San Sebastian, Spain, 14–15 October 2020; pp. 181–194. [Google Scholar]
- Higgs, C. Authorisation and Delegation in the Machination Configuration System. LISA 2008, 8, 191–199. [Google Scholar]
- Warren, J. Unconstrained Delegation Permissions. Available online: https://stealthbits.com/blog/unconstrained-delegation-permissions/ (accessed on 10 September 2021).
- De Clercq, J.; Grillenmeier, G. Microsoft Windows Security Fundamentals: For Windows 2003 SP1 and R2; Elsevier: Amsterdam, The Netherlands, 2011; ISBN 9780080491882. [Google Scholar]
- Amador, M.; Bagwell, K.; Frankel, A. A note on interval delegation. Econ. Theory Bull. 2018, 6, 239. [Google Scholar] [CrossRef]
- Suman, B.; Justin, H. Configuring Kerberos Delegation for Group Managed Service Accounts. Available online: https://docs.microsoft.com/en-us/windows-server/security/group-managed-service-accounts/configure-kerberos-delegation-group-managed-service-accounts (accessed on 10 September 2021).
- Kevin, J. Constrained Delegation Abuse: Abusing Constrained Delegation to Achieve Elevated Access. Available online: https://blog.stealthbits.com/constrained-delegation-abuse-abusing-constrained-delegation-to-achieve-elevated-access/ (accessed on 10 September 2021).
- Markoff, J. Attack of the zombie computers is growing threat. New York Times 2007, 157, 1. [Google Scholar]
- Soria-Machado, M.; Abolins, D.; Boldea, C.; Socha, K. Kerberos golden ticket protection. Mitigating Pass-the-Ticket Act. Dir. CERT-EU Secur. Whitepaper 2014, 7, 2016. [Google Scholar]
- Metcalf, S. Red vs. Blue: Modern Active Directory Attacks, Detection, & Protection. Available online: https://www.blackhat.com/docs/us-15/materials/us-15-Metcalf-Red-Vs-Blue-Modern-Active-Directory-Attacks-Detection-And-Protection.pdf (accessed on 10 September 2021).
- Liu, J.; Akhtar, N.; Mian, A. Adversarial training for commonsense inference. IEEE Trans. Neural Netw. Learn. Syst. Rev. 2020, 47, 777–780. [Google Scholar]
- Tramèr, F.; Papernot, N.; Goodfellow, I.; Boneh, D.; McDaniel, P. The space of transferable adversarial examples. arXiv 2017, arXiv:1704.03453. [Google Scholar]
- Barker, S. White Paper ©; Copyright Quest® Software, Inc.: Aliso Viejo, CA, USA, 2007. [Google Scholar]
- Boger, T. Directory Services Restore Mode (DSRM), & Protection. Available online: https://searchwindowsserver.techtarget.com/definition/Directory-Services-Restore-Mode-DSRM (accessed on 13 September 2021).
- Warren, J. Stealing Credentials with a Security Support Provider (SSP). Available online: https://stealthbits.com/blog/stealing-credentials-with-a-security-support-provider-ssp/ (accessed on 13 September 2021).
- Jacobs, M.; Satran, M. How Access Control Works in Active Directory Domain Services. Available online: https://docs.microsoft.com/en-us/windows/win32/ad/how-access-control-works-in-active-directory-domain-services (accessed on 13 September 2021).
- Metcalf, S. Sneaky Active Directory Persistence #15: Leverage AdminSDHolder & SDProp to (Re)Gain Domain Admin Rights. Available online: https://adsecurity.org/?p=1906 (accessed on 13 September 2021).
- Mittal, N. RACE—Minimal Rights and ACE for Active Directory Dominance. Available online: http://www.labofapenetrationtester.com/2019/08/race.html (accessed on 13 September 2021).
- Wheeler, S.; Wilson, C. Running Remote Commands. Available online: https://docs.microsoft.com/en-us/powershell/scripting/learn/remoting/running-remote-commands?view=powershell-7 (accessed on 13 September 2021).
- Nichols, J.A.; Taylor, B.A.; Curtis, L. Security resilience: Exploring windows domain-level defenses against post-exploitation authentication attacks. In Proceedings of the 11th Annual Cyber and Information Security Research Conference (2016), Oak Ridge, TN, USA, 5–7 April 2016; pp. 1–4. [Google Scholar]
- Jadeja, N.; Vaghasia, M. Analysis and Impact of Different Mechanisms of Defending Pass-the-Hash Attacks. In Cyber Security; Springer: Singapore, 2018; pp. 179–191. [Google Scholar]
- Binduf, A.; Alamoudi, H.O.; Balahmar, H.; Alshamrani, S.; Al-Omar, H.; Nagy, N. Active directory and related aspects of security. In Proceedings of the 2018 21st Saudi Computer Society National Computer Conference (NCC) (IEEE, 2018), Riyadh, Saudi Arabia, 25–26 April 2018; pp. 4474–4479. [Google Scholar]
- Fujimoto, M.; Matsuda, W.; Mitsunaga, T. Detecting Abuse of Domain Administrator Privilege Using Windows Event Log. In Proceedings of the 2018 IEEE Conference on Application, Information and Network Security (AINS), Langkawi, Malaysia, 21–22 November 2018; pp. 15–20. [Google Scholar]
- Liu, Y.; Squires, M.R.; Taylor, C.R.; Walls, R.J.; Shue, C.A. Account Lockouts: Characterizing and Preventing Account Denial-of-Service Attacks. In Proceedings of the International Conference on Security and Privacy in Communication Systems, Orlando, FL, USA, 23–25 October 2019; 2019; pp. 26–46. [Google Scholar]






| Attribute | Main Features | Description |
|---|---|---|
| Nomenclature meaning | Advanced | The adversary is knowledgeable with intrusion tools and tactics and is capable of developing unique exploits. |
| Persistent | The attacker plans to complete a mission, receive orders, and strike particular targets. | |
| Threat | The adversary is well coordinated, well funded, and motivated. | |
| Signs | Players | Attacks are frequently carried out by actors who have a specific goal in mind. These actors usually have the support of nation-states or groups funded by corporations. APT28, OilRig, and Deep Panda are a few examples of groups. |
| Goals | The goal is to continuously acquire intelligence while undermining target capabilities. This data theft or sabotage may be performed for strategic or political reasons. | |
| Timeliness | Attacks prioritize gaining access quickly and keeping it there for a prolonged period of time. Over the course of an attack, attackers frequently return to an infiltrated system many times. | |
| Resources | Planning and carrying out APT attacks requires a lot of resources. This covers the following: time, development and security skills, and hosting. | |
| Risk tolerance | Attackers are more likely to concentrate on specific targets rather than launch wide strikes. APT attackers are also more watchful to avoid detection or to cause unusual system activity. | |
| Methods | APT assaults frequently make use of complex methods that have a need for security knowledge. Rootkits, DNS tunneling, social engineering, and rogue Wi-Fi are a few examples of these methods. | |
| Attack source | APT assaults can come from many different places and can happen during an attack meant to divert security personnel. Before deciding on an entry point, attackers frequently take the time to completely map out a system’s vulnerabilities. | |
| Attack value | The size of the target or the size of the attack operations are both considered to be components of attack value. APTs tend to target larger enterprises more frequently than smaller ones. | |
| Go-around detection tools | It is possible for APT assaults to go beyond typical detection methods, which depend on signature-based detection. Attackers achieve this by employing cutting-edge strategies such as fileless malware or tactics that let them hide their tracks. | |
| Lifecycle | Initial reconnaissance | The phase in which the attacker researches a target, monitors the network, and accumulates data for use in subsequent attacks. |
| Initial compromise | When an attacker successfully runs malware on one or more hosts within the target systems. | |
| Establish foothold | This is the phase in which the attacker takes control of newly compromised systems and keeps it that way. | |
| Escalate privileges | Increased access to systems and their data is attained at the escalate privileges stage by using various techniques including password hash dumping. | |
| Internal reconnaissance | During this phase, the attacker probes the compromised system to better understand its surroundings. | |
| Move laterally | The process by which an attacker uses his access to move across systems in a compromised environment. | |
| Maintain presence | The attacker secures ongoing access to the environment through techniques such as installing backdoors. | |
| Complete mission | This is the point at which the attacker achieves his primary objective, which is often data exfiltration from the target environment. | |
| Techniques | Social engineering | A user’s information systems are compromised using social engineering. Instead of involving aleatory assaults on systems, this strategy targets individuals with privileged access, coercing them into disclosing personal information in order to carry out a harmful attack. |
| Spear-phishing | This tactic focuses on one particular organization in an effort to obtain user passwords, financial information, or other private data. | |
| Watering hole | In terms of cyberespionage, it is comparable to spear-phishing. The attacks are customized to the victim’s needs. Attackers attempt to learn information about the victim by taking into account his or her own interests in order to do this. | |
| Drive-by download | Using this method, malicious software is unintentionally downloaded and executed when a malicious website is accessed. | |
| Types of targets | Government and public sector | Services are interrupted by government organizations, governmental policy, and private information leaks. |
| IT | This involves IT service interruptions and members’ private details being disclosed. | |
| Financial sector | This involves Financial Information Leakage in the Sector and Leaks of members’ private information. | |
| Energy and electricity | Gas and electricity supplies are cut off and members’ private information is leaked. | |
| Medical and health treatment | This is the disruption of health services and the disclosure of private medical data that is sensitive. | |
| Traffic and logistics | This involves system interruptions of the transportation and logistics networks. | |
| Manufacturing industry | This is IT system disruption in the manufacturing industry and the disclosure of business trade secrets. | |
| Comparison with malware | Definition | APT attacks are smart, targeted, and well organized. Malware is harmful software that is used to attack and disable any system (for example, ransomware). |
| Attacker | APT attackers can be government officials and organized crime organizations. Malware attackers are crackers. | |
| Target | APT attacks target organizations engaged in diplomacy, the information technology sector, and other industries. Malware targets any computer, personal or professional. | |
| Purpose | APT attacks aim to harm a specific target or filter private information, while malware attackers seek self-acknowledgment. | |
| Attack lifecycle | APT attacks attempt to maintain perseverance while trying various methods. Malware attacks come to an end when security measures discover it (e.g., anti-virus software). | |
| Detection and protection measures | Email screening | The majority of APT attempts uses phishing to obtain first access. Email filtering and blocking malicious links or attachments within emails might help to thwart these intrusion attempts. |
| Endpoint security | APT attacks entail the compromise of endpoint devices. Advanced anti-malware protection and Endpoint Detection and Response can assist in identifying and responding to an endpoint breach by APT attackers. | |
| Access control | Effective authentication safeguards and careful account management— paying particular attention to privileged accounts—can lessen the dangers of an APT. | |
| Examining traffic, user, and entity activity | This can assist in identifying penetrations, lateral movement, and exfiltration at various stages of an APT attack. |
| Skeleton Key Attack Step | Comment |
|---|---|
| 1- Search for a 64-bit version that is compatible. | The malware is incompatible with 32-bit Windows. versions or with Windows Server versions beginning with Windows Server 2012 (6.2). |
| 2- Utilize the SeDebugPrivilege command. | This procedure is in charge of user account authentication. to gain the necessary higher rights to write to the (LSASS) process. |
| 3- List all existing procedures. | This is done to get a hold on the LSASS process. |
| 4- Find the addresses of the functions that are linked to authentication and need to be patched. | Examples of these functions are: - CDLocateCSystem — placed in cryptdll.dll. - SamIRetrieveMultiplePrimaryCredentials — placed in samsrv.dll. - SamIRetrievePrimaryCredentials — placed in samsrv.dll. |
| 5- Make changes that are particular to the OS. | This is carried out with the help of the global variable that was set during the compatibility check in step 1. |
| 6- Use the OpenProcess function. | This is performed to get a handle to the LSASS process. |
| 7- Set aside the needed memory space to change and fix the LSASS process’s memory. | This is conducted to alter and patch the LSASS process’s memory. |
| 8- Patch relevant functions. | This depends on the operating system: a- CDLocateCSystem (all compatible Windows versions). b- SamIRetrieveMultiplePrimaryCredentials (only Windows 2008 R2 (6.1)) c- SamIRetrievePrimaryCredentials (all compatible Windows versions other than Windows 2008 R2 (6.1)). |
| Stages | Techniques | Description |
|---|---|---|
| Domain enumeration | Net.exe | This allows attackers to see all the attributes of users and groups and hunt for critical groups such as AD domain admins and can then see information about the user’s group membership. |
| AD module | This allows administrators to query and make changes to Active Directory with PowerShell. | |
| Powerview | This has some extra functions which the attacker can leverage to identify the locations in the network where specific users are logged into. | |
| Bloodhound | This helps to visualize AD domains and to facilitate identifying complex attack paths and gain deep knowledge about privilege relationships in AD systems. | |
| Privilege escalation | Pass the hash | It depends on hash extraction from a compromised machine and using this hash to create tokens that allow access to sensitive resources or hosts across the domain. |
Kerberoasting | This relies on the fact that some services run under normal user accounts. The service ticket provided by AD for this service is encrypted by the NTLM hash of the user’s password. Grabbing the ticket and brute forcing it allows access to the plaintext password of the target user. | |
| Delegation abuse | Delegation is an Active Directory feature that permits the impersonation of an account by users or computers. Constrained and unconstrained delegation can be enabled and customized. Constrained delegation provides access to a specific set of services listed in the msDS-Allowed To Delegate to attribute on the user configuration. Unconstrained delegation is the permission for a computer to impersonate any service. Once it is enabled, any time a user connects to this computer, their TGT is stored in the computer memory for later use. | |
| Abusing DNS admins’ privileges | Abusing DNS admins’ privileges is a technique by which a DNS admins member can escalate their privileges to system privileges if he has the rights to configure server-level plugin DLL and to restart the DNS service. | |
| Domain persistence | Golden ticket | Golden tickets are user-created TGTs which are used to give the attackers access to specific resources. Intruders use the TGTs to obtain service tickets from the domain controller without verifying the contents of the TGT. |
| Silver ticket | Silver tickets are service tickets that are used to access certain services. The attacker gets access to the NTLM hash of a service account and then uses a tool such as Mimikatz to forge a service ticket to access this service, impersonating any user. | |
| Skeleton key | Skeleton Key is an attack carried out against the domain controllers. The adversary targets the Local Security Authority Subsystem Service (LSASS) process in the domain controller. The LSASS process is responsible for the entire system of authentication in the Active Directory. The attacker patches the LSASS process to create a master password to work for any account. | |
| DSRM persistence | The main function of the DSRM account is to provide the administrator with a backdoor to the database to recover or repair any failure. The attacker can manipulate its configuration to have local admin access to the domain controller and compromise the entire domain. | |
| SSP persistence | The security support provider (SSP) is an API used by Windows to carry out the authentications of Windows login. It is a DLL file that provides security packages to other applications. This DLL stacks itself up in LSA when the system starts, making it a start-up process. After it is loaded in LSA, it can access all the Windows credentials. | |
| ACL abuse | Modifying the Access Control Lists of certain objects of the AD tree can give the attacker access to resources that cannot be accessed by default. |
| Tool | Origin | Description |
|---|---|---|
| VMware Workstation 14 | VMware, Inc., Palo Alto, CA, USA | A hypervisor used to host the test machines. |
| WindowsServer 2016 | Microsoft Corp., One Microsoft Wasy, Redmond, Washington, DC, USA | The server providing the domain controller rule. |
| Windows10 Enterprise | Microsoft Corp., One Microsoft Wasy, Redmond, Washington, DC, USA | Client machine. |
| WindowsPowerShell | Microsoft Corp., One Microsoft Wasy, Redmond, Washington, DC, USA | Shell used to launch different tools. |
| Mimikatz 2.0 | BenjaminDelpy, Security Researcher, France | Tool used to extract the tickets and launch different attacks. |
| WindowsEvent Viewer | Microsoft Corp., One Microsoft Wasy, Redmond, Washington, DC, USA | Windows default tool to log events. |
| PSEXEC | Microsoft Corp., One Microsoft Wasy, Redmond, Washington, DC, USA) | A tool for running command over the network in Windows. |
| FileZilla Server | Open Source FTP server | FTP server used in Kerberoasting attack. |
| Hashcat | Open Source | Tool used for cracking passwords. |
| Powerview | Matt Graeber | Active Directory enumeration tool. |
| Source Host | Target Host | Domain Controller |
|---|---|---|
| 4648—A logon was attempted using explicit credentials. | 4624—An account was successfully logged on (logon type 3, NTLM). | 4776—The computer attempted to validate the credentials for an account. |
| 4624—An account was successfully logged on (logon type = 9; logon process = Seclogo). | 4672—Special privileges were assigned to new logon. | |
| 4672—Special privileges were assigned to new logon (logged-on user, not impersonated user). |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mokhtar, B.I.; Jurcut, A.D.; ElSayed, M.S.; Azer, M.A. Active Directory Attacks—Steps, Types, and Signatures. Electronics 2022, 11, 2629. https://doi.org/10.3390/electronics11162629
Mokhtar BI, Jurcut AD, ElSayed MS, Azer MA. Active Directory Attacks—Steps, Types, and Signatures. Electronics. 2022; 11(16):2629. https://doi.org/10.3390/electronics11162629
Chicago/Turabian StyleMokhtar, Basem Ibrahim, Anca D. Jurcut, Mahmoud Said ElSayed, and Marianne A. Azer. 2022. "Active Directory Attacks—Steps, Types, and Signatures" Electronics 11, no. 16: 2629. https://doi.org/10.3390/electronics11162629
APA StyleMokhtar, B. I., Jurcut, A. D., ElSayed, M. S., & Azer, M. A. (2022). Active Directory Attacks—Steps, Types, and Signatures. Electronics, 11(16), 2629. https://doi.org/10.3390/electronics11162629







