Maintaining Effective Node Chain Connectivity in the Network with Transmission Power of Self-Arranged AdHoc Routing in Cluster Scenario
Abstract
:1. Introduction
2. Literature Survey
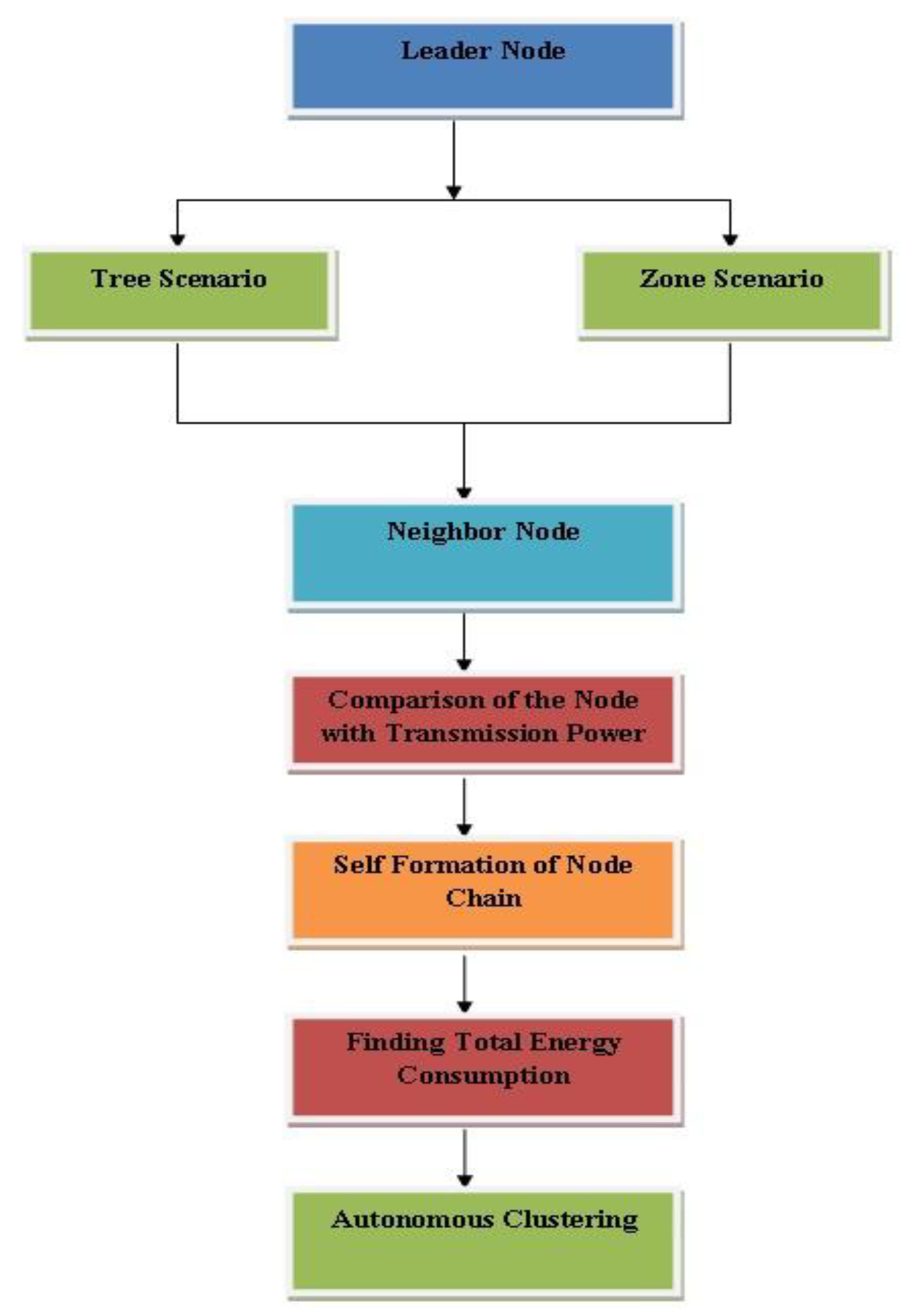
3. Proposed Technique
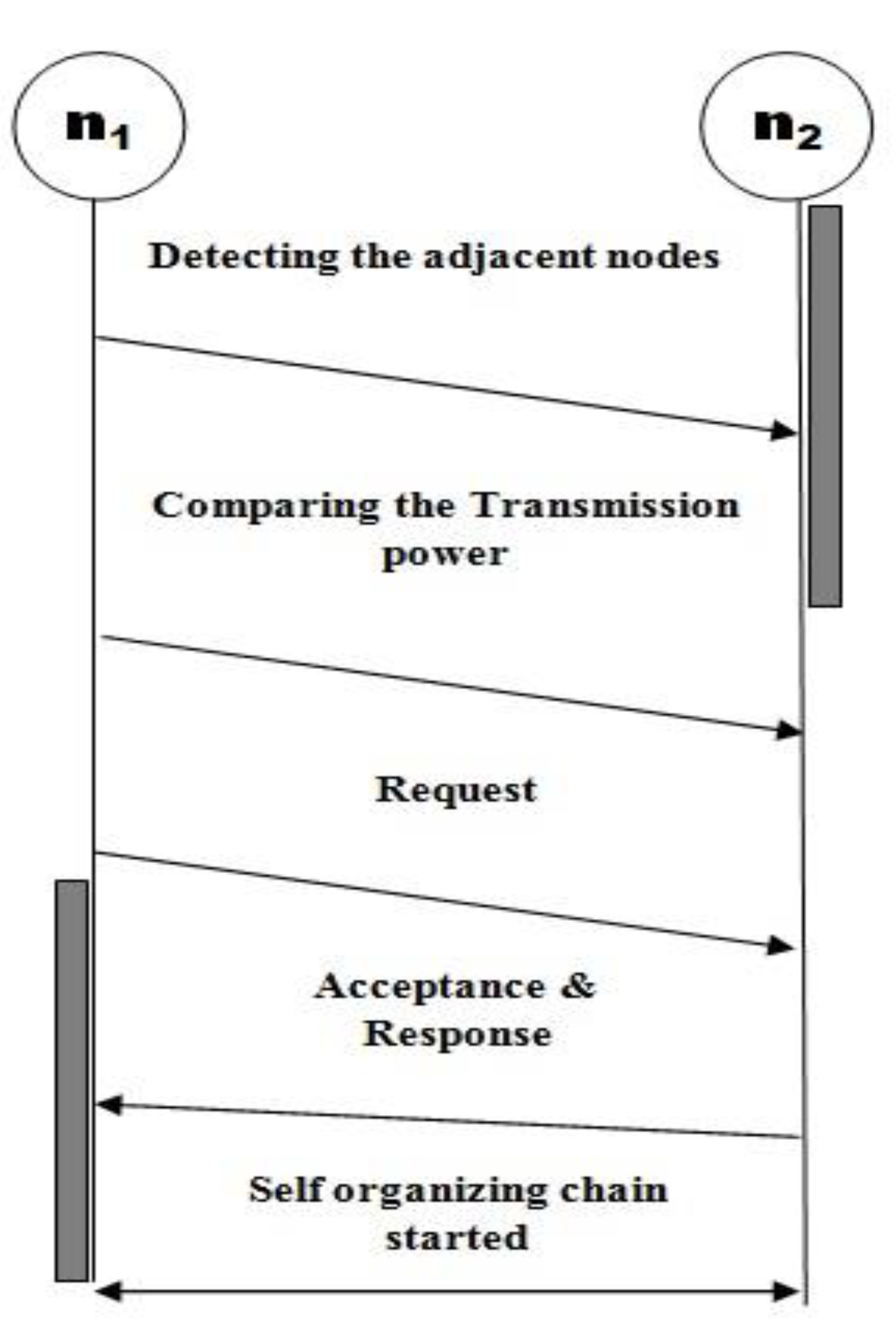
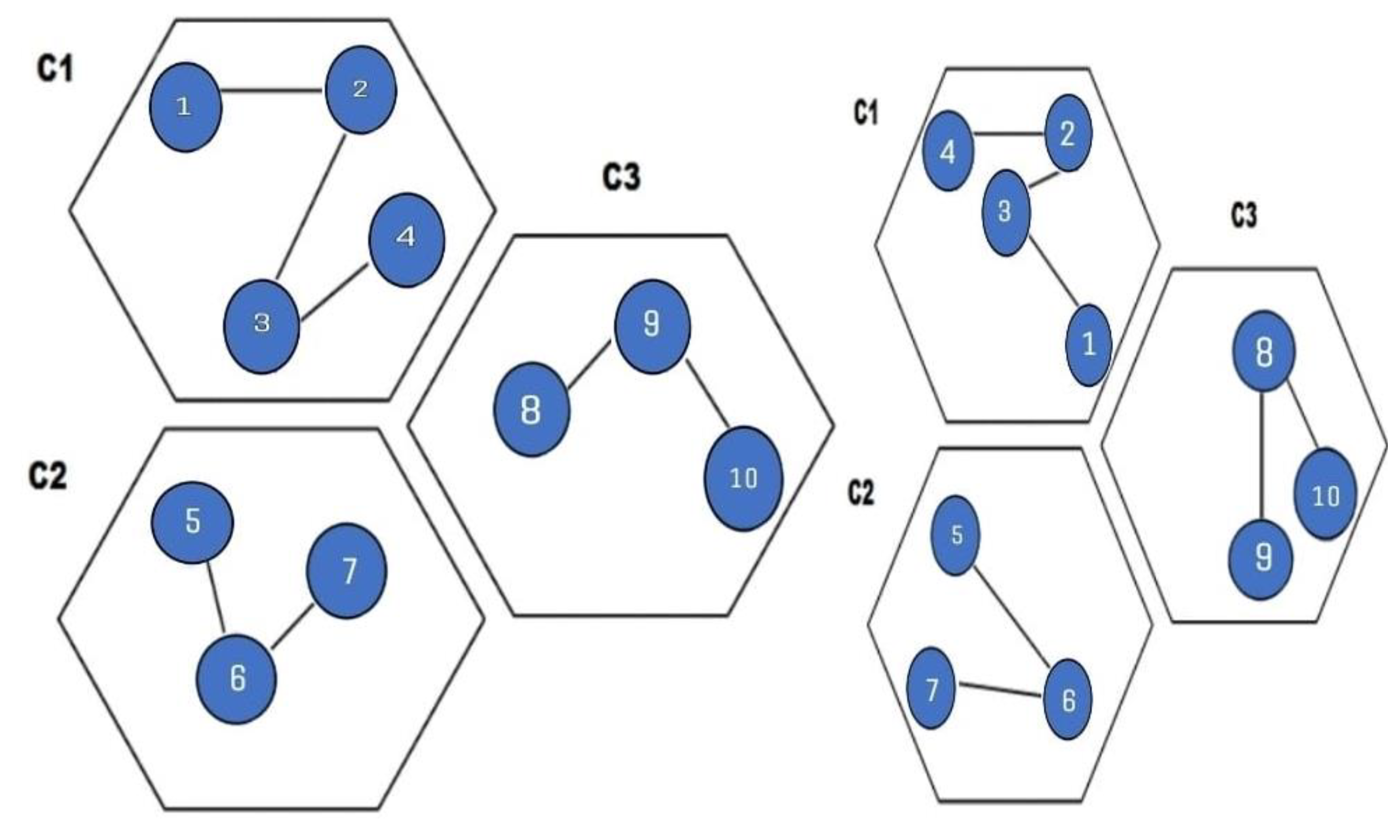
3.1. Autonomous Clustering
3.2. Finding Positions of the Nodes
4. Simulation Analysis
4.1. Transmission Power Range
4.2. Longevity of Nodes
4.3. Ratio of Malicious Nodes
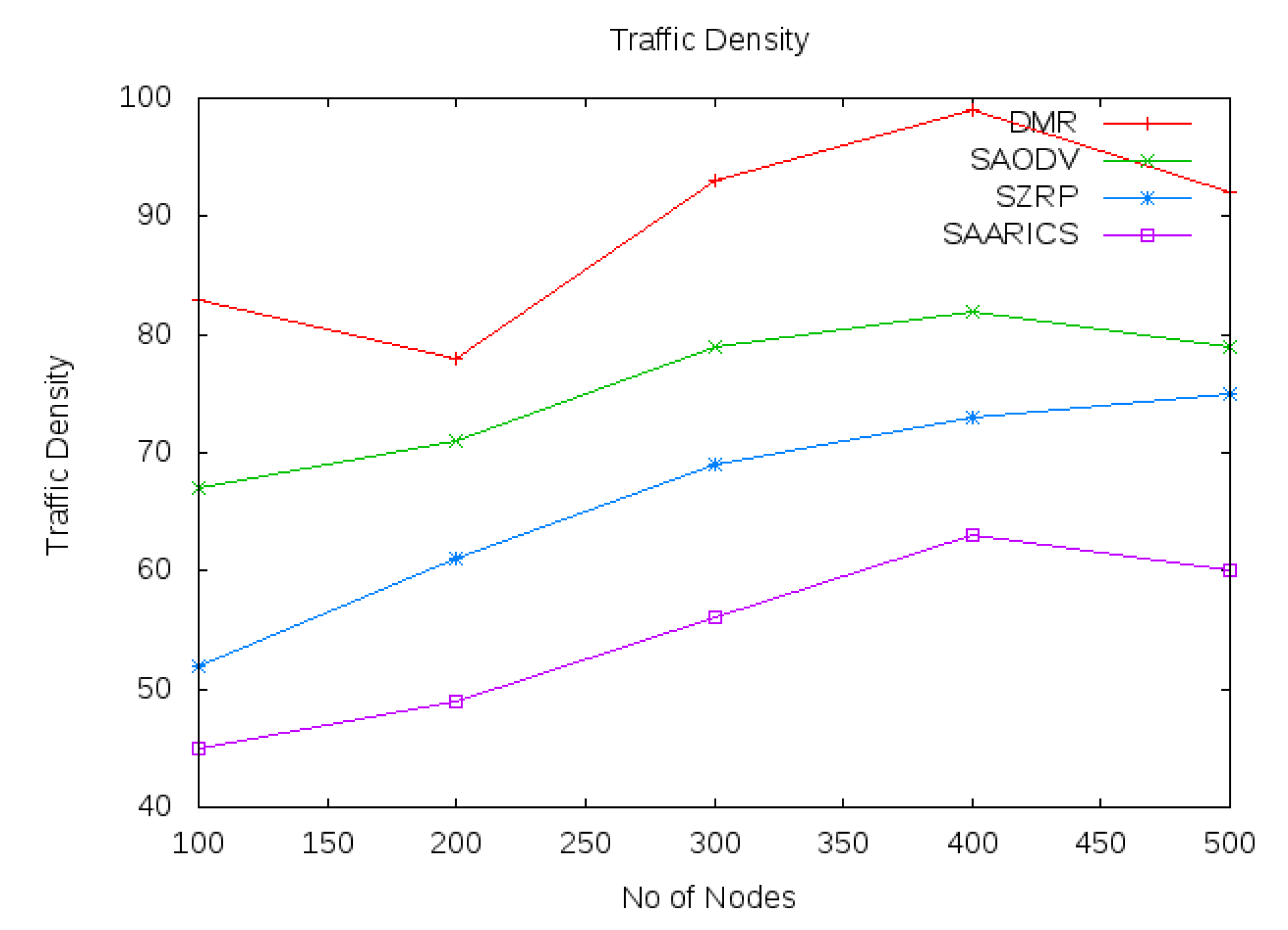
4.4. Traffic Density Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Gupta, P.; Kumar, P.R. The capacity of wireless networks. IEEE Trans. Inf. Theory 2000, 46, 388–404. [Google Scholar] [CrossRef] [Green Version]
- U.S. Department of Defense, Office of Operational Test and Evaluation (DOT&E). Joint Tactical Radio System (JTRS) Ground Mobile Radio (GMR). 2010. Available online: https://www.dote.osd.mil/ (accessed on 18 June 2022).
- Gilmore, J.M. Operational Test and Evaluation Office of the Secretary of Defense. In Testimony before House Armed Services Subcommittee On Air And Land Forces. 2010. Available online: https://www.acq.osd.mil/fo/docs/HASC (accessed on 24 May 2019).
- Wolfgang, K.; Mauve, M. A survey on real-world implementations of mobile ad-hoc networks. Ad. Hoc. Netw. 2007, 5, 324–339. [Google Scholar]
- Wei, Q.; Bai, K.; Zhou, L.; Hu, Z.; Jin, Y.; Li, J. A Cluster-Based Energy Optimization Algorithm in Wireless Sensor Networks with Mobile Sink. Sensors 2021, 21, 2523. [Google Scholar] [CrossRef] [PubMed]
- Hubaux, J.P.; Gross, T.; le Boudec, J.Y.; Vetterli, M. Toward self-organized mobile ad hoc networks: The Terminodes Project. IEEE Commun. Mag. 2001, 39, 118–124. [Google Scholar] [CrossRef] [Green Version]
- Razzaque, M.A.; Dobson, S.; Nixon, P. Enhancement of Self- organization in Wireless Networking through a Cross-layer Approach. In International Conference on Ad Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Basagni, S. Distributed clustering for ad hoc networks. In Proceedings of the Fourth International Symposium on Parallel Architectures, Algorithms, and Networks (I-SPAN’99), Perth/Fremantle, WA, Australia, 23–25 June 1999. [Google Scholar]
- Mohammed, N.; Otrok, H.; Wang, L.; Debbabi, M.; Bhattachary, P. Mechanism Design-Based Secure Leader Election Model for Intrusion Detection in MANET. IEEE Trans. Dependable Secur. Comput. 2011, 8, 89–103. [Google Scholar] [CrossRef]
- Mishra, A.; Nadkarni, K.; Patcha, A. Intrusion detection in wireless ad hoc networks. IEEE Wirel. Commun. 2004, 11, 48–60. [Google Scholar] [CrossRef]
- Otrok, H.; Mohammed, N.; Wang, L.; Debbabi, M.; Bhattacharya, P. An Efficient and Truthful Leader IDS Election Mechanism for MANET. In Proceedings of the Third IEEE International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), White Plains, NY, USA, 8–10 October 2007. [Google Scholar]
- Akbani, R.; Korkmaz, T.; Raju, G.V.S. Mobile Ad hoc Network Security. In Lecture Notes in Electrical Engineering; Springer: New York, NY, USA, 2012; Volume 127, pp. 659–666. [Google Scholar]
- Hu, Y.; Perrig, A.; Johnson, D. Ariadne: A secure on-demand routing protocol for ad hoc networks. Wirel. Netw. 2002, 11, 21–38. [Google Scholar] [CrossRef]
- Hu, Y.; Johnson, D.; Perrig, A. SEAD: Secure efficient distance vector routing for mobile wireless. Ad. Hoc. Netw. 2003, 1, 175–192. [Google Scholar] [CrossRef]
- Johnson, D.; Maltz, D. Dynamic Source Routing in ad hoc wireless Networks. In Mobile Computing; Springer: Boston, MA, USA, 1996; Chapter 5; pp. 153–181. [Google Scholar]
- Kang, N.; Shakshuki, E.; Sheltami, T. Detecting misbehaving nodes in MANETs. In Proceedings of the 12th International Conference on Information Integration and Web-Based Applications & Services, Bangkok, Thailand, 8 November 2010; pp. 216–222. [Google Scholar]
- Howard, A.; Mataric, J.; Sukhatme, G. Mobile sensor network deployment using potential fields: A distributed, scalable solution to the area coverage problem. In Distributed Autonomous Robotic Systems 5; Springer: Tokyo, Japan, 2002; pp. 299–308. [Google Scholar]
- Kumar, S. Prediction of Node and Link Failures in Mobile Ad Hoc Network Using Hello Based Path Recovery Routing Protocol. Wirel. Pers. Commun. 2020, 115, 725–744. [Google Scholar] [CrossRef]
- Han, Z.; Xue, W.; Du, X. Research on Clustering Protocol in Mobile Ad Hoc Networks. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology, Melbourne, Australia, 14–17 December 2021; pp. 471–475. [Google Scholar]
- Parthasarathy, R. A Collective and Comparative Study of Various Routing Protocols and the Threats in MANET. Int. J. Knowl. Syst. Sci. (IJKSS) 2021, 12, 11. [Google Scholar]





| Simulator | NS3 Simulator |
|---|---|
| Area | 1000 × 1000 m |
| Network Size | 100 to 500 nodes |
| Mobility Model | Random Way Point |
| Traffic Type | FTP |
| Simulation Time | 600 s |
| Standard | IEEE 802.11 G |
| Routing protocol | SAODV, SZRP, DMR |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Devi Murugavel, K.; Ramadass, P.; Mahendran, R.K.; Khan, A.A.; Haq, M.A.; Alharby, S.; Alhussen, A. Maintaining Effective Node Chain Connectivity in the Network with Transmission Power of Self-Arranged AdHoc Routing in Cluster Scenario. Electronics 2022, 11, 2455. https://doi.org/10.3390/electronics11152455
Devi Murugavel K, Ramadass P, Mahendran RK, Khan AA, Haq MA, Alharby S, Alhussen A. Maintaining Effective Node Chain Connectivity in the Network with Transmission Power of Self-Arranged AdHoc Routing in Cluster Scenario. Electronics. 2022; 11(15):2455. https://doi.org/10.3390/electronics11152455
Chicago/Turabian StyleDevi Murugavel, Kiruthiga, Parthasarathy Ramadass, Rakesh Kumar Mahendran, Arfat Ahmad Khan, Mohd Anul Haq, Sultan Alharby, and Ahmed Alhussen. 2022. "Maintaining Effective Node Chain Connectivity in the Network with Transmission Power of Self-Arranged AdHoc Routing in Cluster Scenario" Electronics 11, no. 15: 2455. https://doi.org/10.3390/electronics11152455
APA StyleDevi Murugavel, K., Ramadass, P., Mahendran, R. K., Khan, A. A., Haq, M. A., Alharby, S., & Alhussen, A. (2022). Maintaining Effective Node Chain Connectivity in the Network with Transmission Power of Self-Arranged AdHoc Routing in Cluster Scenario. Electronics, 11(15), 2455. https://doi.org/10.3390/electronics11152455







