Detection of Adversarial DDoS Attacks Using Symmetric Defense Generative Adversarial Networks
Abstract
:1. Introduction
2. Related Work
2.1. Artificial Intelligence for DDoS Detection
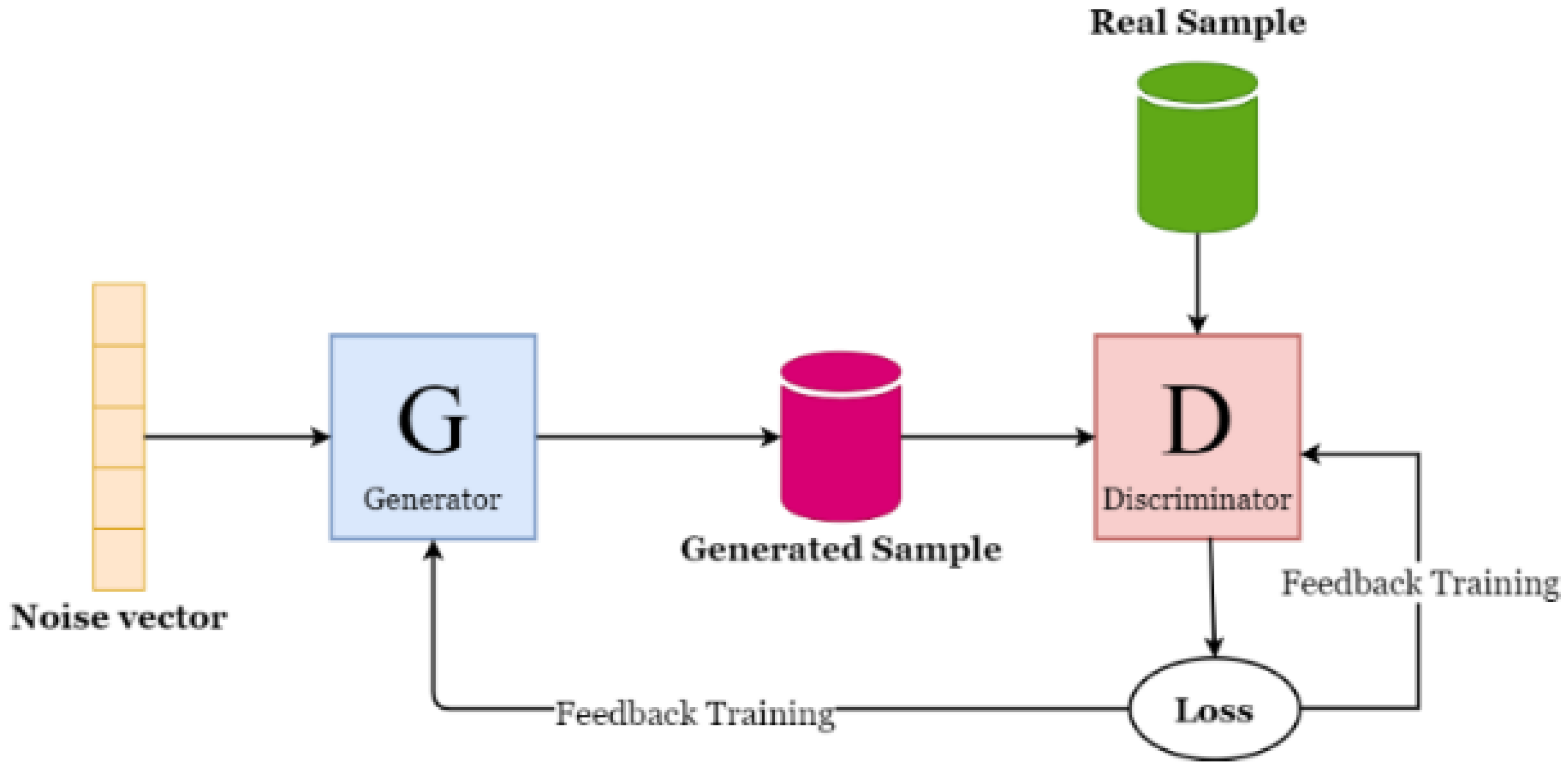
2.2. Generative Adversarial Networks
2.3. Adversarial DDoS Attacks
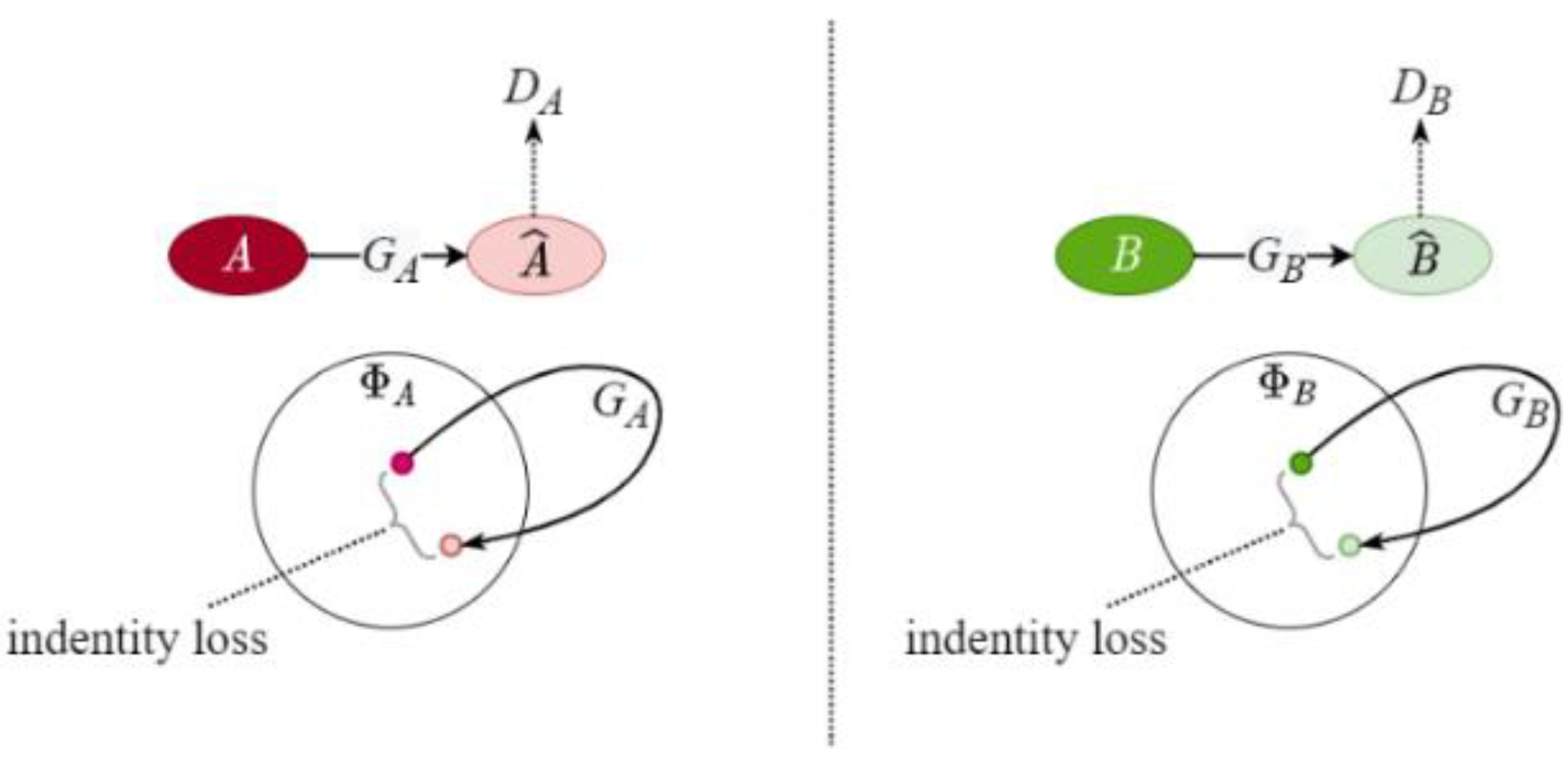
2.4. CycleGAN
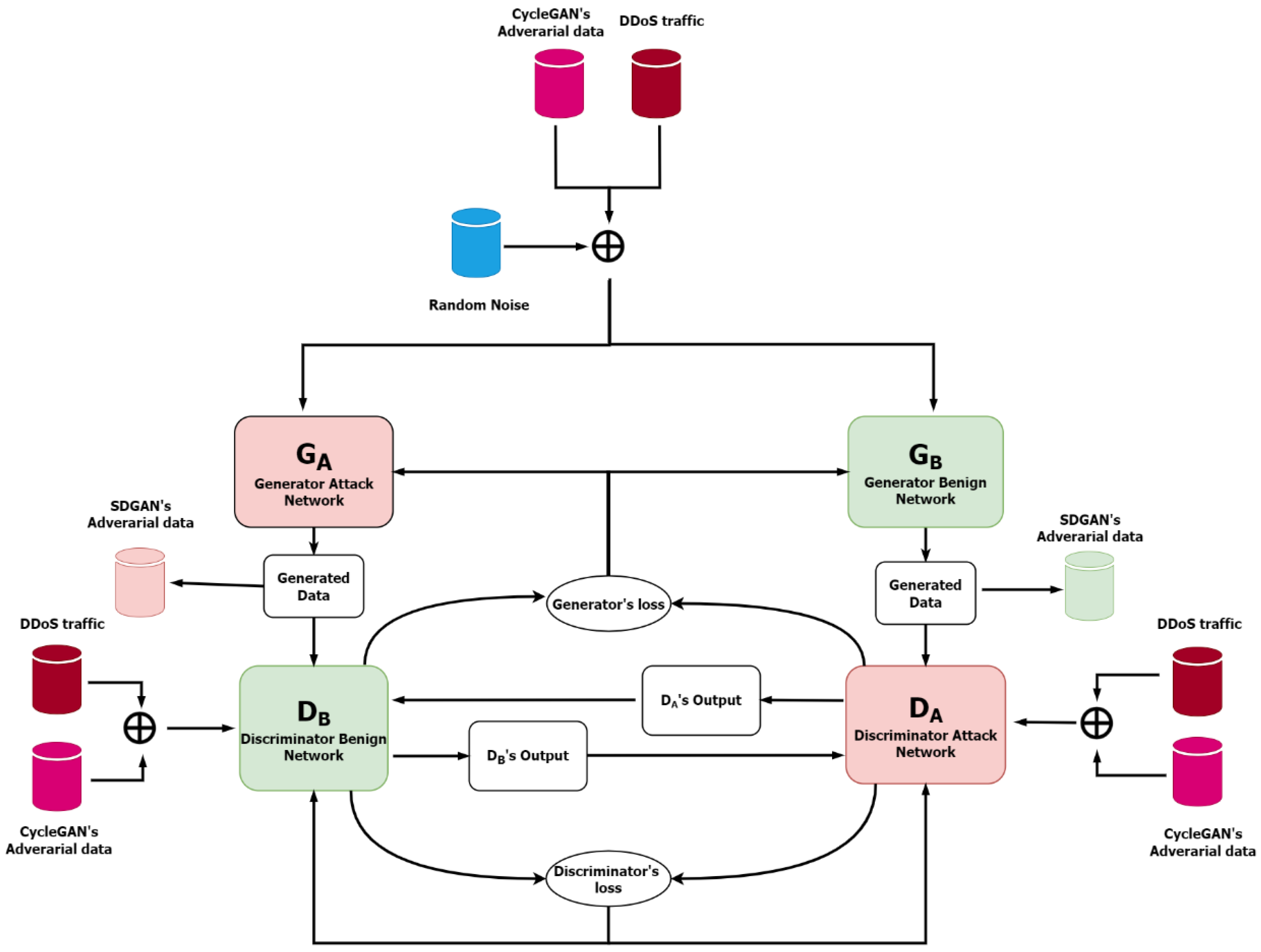
3. Proposed Approach
3.1. Proposed Approach
3.2. Loss Functions
- Adversarial Loss
- Cycle Consistency Loss
- Identity Loss
- Generator Loss Function
| Algorithm 1. Training of the CycleGAN architecture generating system |
| Input: : benign domain Output: Trained CycleGAN architecture system
|
3.3. Adversarial DDoS Attack Detection Using Symmetric Defense GAN (SDGAN)
| Algorithm 2. Algorithm for SDGAN |
| Input: : benign domain discriminator, N: noise, B: benign traffic, A: normal DDoS attack, E: adversarial attack generated by CycleGAN Output: Trained SDGAN
|
4. Experimental Results and Discussion
- ML-based and SDGAN are highly effective in DDoS detection.
- Adversarial DDoS attacks from the CycleGAN generation system have the ability to bypass ML-based DDoS detection systems.
- The proposed SDGAN system is effective in identifying adversarial DDoS attacks.
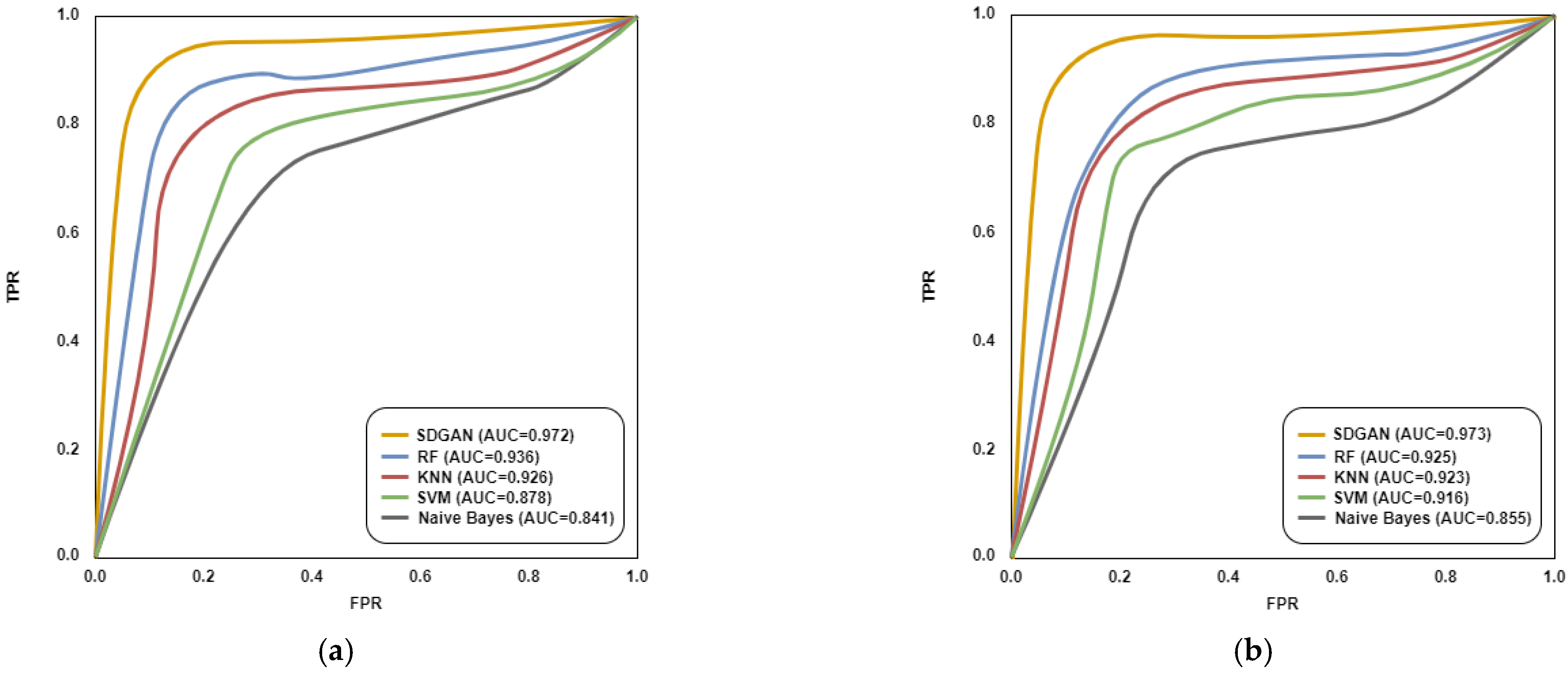
4.1. ML-Based and SDGAN Detection of Conventional DDoS
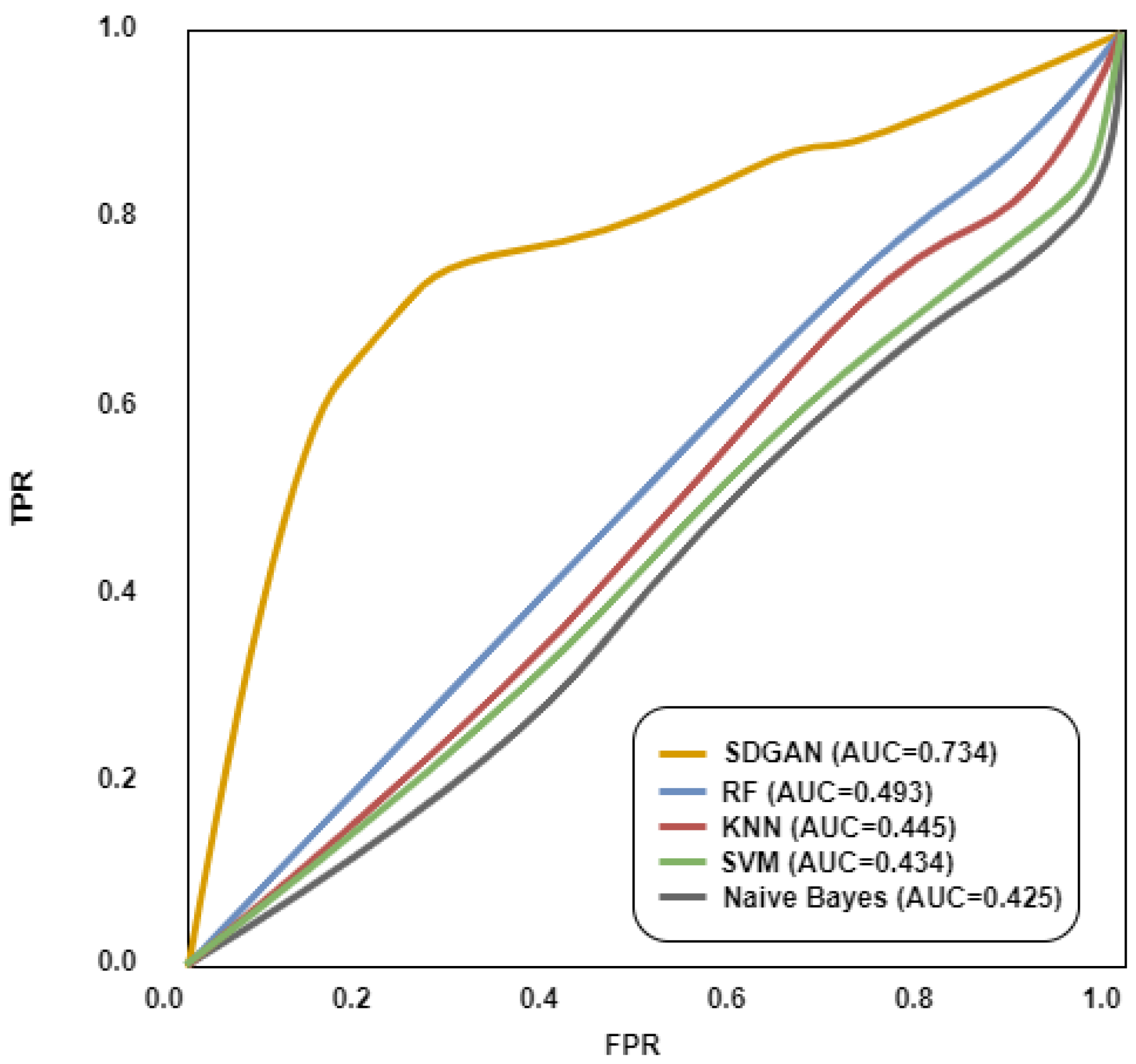
4.2. Detection of Adversarial DDoS Attacks with SDGAN
4.2.1. Adversarial DDoS Attack Synthesis Employing CycleGAN
4.2.2. Detection of Adversarial DDoS Attacks with SDGAN
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gligor, V.D. A Note on Denial-of-Service in Operating Systems. IEEE Trans. Softw. Eng. 1984, 3, 320–324. [Google Scholar] [CrossRef]
- Mirchev, M.J.; Mirtchev, S.T. System for DDoS attack mitigation by discovering the attack vectors through statistical traffic analysis. Int. J. Inf. Comput. Secur. 2020, 13, 309–321. [Google Scholar] [CrossRef]
- DDoS Report 1st Half-Year 2021. Cyber Resilience Made in Germany—Link11. Available online: https://www.link11.com/en/downloads/ddos-report-1st-half-2021/ (accessed on 24 May 2022).
- Bakr, A.; El-Aziz, A.A.A.; Hefny, H.A. A Survey on Mitigation Techniques against DDoS Attacks on Cloud Computing Architecture. Int. J. Adv. Sci. Technol. 2019, 28, 12. [Google Scholar]
- Priya, S.S.; Sivaram, M.; Yuvaraj, D.; Jayanthiladevi, A. Machine Learning based DDOS Detection. In Proceedings of the 2020 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 12–14 March 2020; pp. 234–237. [Google Scholar] [CrossRef]
- Das, S.; Mahfouz, A.M.; Venugopal, D.; Shiva, S. DDoS Intrusion Detection Through Machine Learning Ensemble. In Proceedings of the 2019 IEEE 19th International Conference on Software Quality, Reliability and Security Companion (QRS-C), Sofia, Bulgaria, 22–26 July 2019; pp. 471–477. [Google Scholar] [CrossRef]
- Dincalp, U.; Guzel, M.S.; Sevine, O.; Bostanci, E.; Askerzade, I. Anomaly Based Distributed Denial of Service Attack Detection and Prevention with Machine Learning. In Proceedings of the 2018 2nd International Symposium on Multidisciplinary Studies and Innovative Technologies (ISMSIT), Ankara, Turkey, 19–21 October 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Khuphiran, P.; Leelaprute, P.; Uthayopas, P.; Ichikawa, K.; Watanakeesuntorn, W. Performance Comparison of Machine Learning Models for DDoS Attacks Detection. In Proceedings of the 2018 22nd International Computer Science and Engineering Conference (ICSEC), Chiang Mai, Thailand, 21–24 November 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Ramanauskaitė, S.; Goranin, N.; Čenys, A.; Juknius, J. Modelling influence of Botnet features on effectiveness of DDoS attacks. Secur. Commun. Netw. 2015, 8, 2090–2101. [Google Scholar] [CrossRef]
- Yang, X.; Li, Z.; Zhou, W. An Analytical Model for DDoS Attacks and Defense. In Proceedings of the 2006 International Multi-Conference on Computing in the Global Information Technology—(ICCGI’06), Bucharest, Romania, 1–3 August 2006; p. 66. [Google Scholar] [CrossRef]
- Yong, W.; Tefera, S.H.; Beshah, Y.K. Understanding Botnet: From Mathematical Modelling to Integrated Detection and Mitigation Framework. In Proceedings of the 2012 13th ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing, Kyoto, Japan, 8–10 August 2012; pp. 63–70. [Google Scholar] [CrossRef]
- Goodfellow, I.; Pouget-Abadie, J.; Mirza, M.; Xu, B.; Warde-Farley, D.; Ozair, S.; Courville, A.; Bengio, Y. Generative Adversarial Nets. Adv. Neural Inf. Process. Syst. 2014, 27. Available online: https://papers.nips.cc/paper/2014/hash/5ca3e9b122f61f8f06494c97b1afccf3-Abstract.html (accessed on 24 May 2022).
- Zhu, J.-Y.; Park, T.; Isola, P.; Efros, A.A. Unpaired Image-to-Image Translation Using Cycle-Consistent Adversarial Networks. In Proceedings of the 2017 IEEE International Conference on Computer Vision (ICCV), Venice, Italy, 22–29 October 2017; pp. 2242–2251. [Google Scholar] [CrossRef] [Green Version]
- Kolosnjaji, B.; Demontis, A.; Biggio, B.; Maiorca, D.; Giacinto, G.; Eckert, C.; Roli, F. Adversarial Malware Binaries: Evading Deep Learning for Malware Detection in Executables. In Proceedings of the 2018 26th European Signal Processing Conference (EUSIPCO), Rome, Italy, 3–7 September 2018; pp. 533–537. [Google Scholar] [CrossRef] [Green Version]
- Song, W.; Li, X.; Afroz, S.; Garg, D.; Kuznetsov, D.; Yin, H. MAB-Malware: A Reinforcement Learning Framework for Attacking Static Malware Classifiers. arXiv 2021, arXiv:2003.03100. Available online: http://arxiv.org/abs/2003.03100 (accessed on 24 May 2022).
- Cheng, J.; Yin, J.; Liu, Y.; Cai, Z.; Wu, C. DDoS Attack Detection Using IP Address Feature Interaction. In Proceedings of the 2009 International Conference on Intelligent Networking and Collaborative Systems, Barcelona, Spain, 4–6 November 2009; pp. 113–118. [Google Scholar] [CrossRef]
- Vu, N.H.; Choi, Y.; Choi, M. DDoS attack detection using K-Nearest Neighbor classifier method. In Proceedings of the IASTED International Conference on Telehealth/Assistive Technologies, Baltimore, MD, USA, 16–18 April 2008; pp. 248–253. [Google Scholar]
- Fadlil, A.; Riadi, I.; Aji, S. Review of Detection DDOS Attack Detection Using Naive Bayes Classifier for Network Forensics. Bull. EEI 2017, 6, 140–148. [Google Scholar] [CrossRef]
- Wang, C.; Zheng, J.; Li, X. Research on DDoS Attacks Detection Based on RDF-SVM. In Proceedings of the 2017 10th International Conference on Intelligent Computation Technology and Automation (ICICTA), Changsha, China, 9–10 October 2017; pp. 161–165. [Google Scholar] [CrossRef]
- Gavrilis, D.; Dermatas, E. Real-time detection of distributed denial-of-service attacks using RBF networks and statistical features. Comput. Netw. 2005, 48, 235–245. [Google Scholar] [CrossRef]
- Ibrahim, L.M. Anomaly Network Intrusion Detection System Based on Distributed Time-Delay Neural Network (DTDNN). J. Eng. Sci. Technol. 2010, 5, 457–471. [Google Scholar]
- Pandya, R.; Pandya, J. C5. 0 Algorithm to Improved Decision Tree with Feature Selection and Reduced Error Pruning. Int. J. Comput. Appl. 2015, 117, 18–21. [Google Scholar] [CrossRef]
- Sahoo, K.S.; Tripathy, B.K.; Naik, K.; Ramasubbareddy, S.; Balusamy, B.; Khari, M.; Burgos, D. An Evolutionary SVM Model for DDOS Attack Detection in Software Defined Networks. IEEE Access 2020, 8, 132502–132513. [Google Scholar] [CrossRef]
- Tan, L.; Pan, Y.; Wu, J.; Zhou, J.; Jiang, H.; Deng, Y. A New Framework for DDoS Attack Detection and Defense in SDN Environment. IEEE Access 2020, 8, 161908–161919. [Google Scholar] [CrossRef]
- Arjovsky, M.; Chintala, S.; Bottou, L. Wasserstein generative adversarial networks. In Proceedings of the 34th International Conference on Machine Learning, Sydney, NSW, Australia, 6–11 August 2017; Volume 70, pp. 214–223. [Google Scholar]
- Gulrajani, I.; Ahmed, F.; Arjovsky, M.; Dumoulin, V.; Courville, A.C. Improved Training of Wasserstein GANs. Adv. Neural Inf. Process. Syst. 2017, 30. Available online: https://papers.nips.cc/paper/2017/hash/892c3b1c6dccd52936e27cbd0ff683d6-Abstract.html (accessed on 24 May 2022).
- Sun, D.; Yang, K.; Shi, Z.; Chen, C. A New Mimicking Attack by LSGAN. In Proceedings of the 2017 IEEE 29th International Conference on Tools with Artificial Intelligence (ICTAI), Boston, MA, USA, 6–8 October 2017; pp. 441–447. [Google Scholar] [CrossRef]
- Hu, W.; Tan, Y. Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN. arXiv 2017, arXiv:1702.05983. Available online: http://arxiv.org/abs/1702.05983 (accessed on 24 May 2022).
- Ebrahimi, M.; Zhang, N.; Hu, J.; Raza, M.T.; Chen, H. Binary Black-box Evasion Attacks Against Deep Learning-based Static Malware Detectors with Adversarial Byte-Level Language Model. arXiv 2020, arXiv:2012.07994. [Google Scholar]
- NSL-KDD|Datasets|Research|Canadian Institute for Cybersecurity|UNB. Available online: https://www.unb.ca/cic/datasets/nsl.html (accessed on 24 May 2022).
- IDS 2018|Datasets|Research|Canadian Institute for Cybersecurity|UNB. Available online: https://www.unb.ca/cic/datasets/ids-2018.html (accessed on 24 May 2022).
- KDD Cup 1999 Data. Available online: http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html (accessed on 24 May 2022).
- C. I. for Cybersecurity, Canadian Institute for Cybersecurity/CIC Flow Meter. 2022. Available online: https://github.com/CanadianInstituteForCybersecurity/CICFlowMeter (accessed on 24 May 2022).



| Actual | Attack | Normal | |
|---|---|---|---|
| Predicted | |||
| Attack | TP (true positive) | FP (false positive) | |
| Normal | FN (false negative) | TN (true negative) | |
| Layer | Configuration |
|---|---|
| Input | (None, 40) |
| Dense | (None, 20) |
| PReLU | (None, 20) |
| Dense | (None, 10) |
| PReLU | (None, 10) |
| Dense | (None, 10) |
| Dropout | (None, 10) |
| Dense | (None, 2) |
| PReLU | (None, 2) |
| Epoch/Batch Size | Learning Rate | Optimizer | Lambda | Mu |
|---|---|---|---|---|
| 500/60 | 0.000135 | Adam | 10 | 0.1 |
| Model | TPR | FPR |
|---|---|---|
| RF | 0.911 | 0.048 |
| KNN | 0.902 | 0.059 |
| SVM | 0.864 | 0.124 |
| Naïve Bayes | 0.844 | 0.188 |
| SDGAN | 0.973 | 0.032 |
| Model | TPR | FPR |
|---|---|---|
| RF | 0.925 | 0.074 |
| KNN | 0.922 | 0.075 |
| SVM | 0.91 | 0.075 |
| Naïve Bayes | 0.806 | 0.063 |
| SDGAN | 0.977 | 0.029 |
| Layer | Configuration |
|---|---|
| Input (conventional DDoS) | (None, 40) |
| Dense | (None, 20) |
| Leaky ReLU | (None, 20) |
| Dense | (None, 10) |
| Leaky ReLU | (None, 10) |
| Dense | (None, 10) |
| Leaky ReLU | (None, 10) |
| Dense | (None, 20) |
| Input (conventional DDoS) | (None, 40) |
| Epoch/Batch Size | Learning Rate | Optimizer | Lambda | Mu |
|---|---|---|---|---|
| 500/60 | 0.00014 | Adam | 10 | 0.1 |
| NSL-KDD | CIC-IDS2018 | |
|---|---|---|
| RF | 0.177 | 0.185 |
| KNN | 0.159 | 0.161 |
| SVM | 0.137 | 0.142 |
| Naïve Bayes | 0.096 | 0.138 |
| SDGAN | 0.857 | 0.872 |
| RF | KNN | SVM | NB | SDGAN | |
|---|---|---|---|---|---|
| TPR | 0.094 | 0.047 | 0.034 | 0.031 | 0.709 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shieh, C.-S.; Nguyen, T.-T.; Lin, W.-W.; Lai, W.K.; Horng, M.-F.; Miu, D. Detection of Adversarial DDoS Attacks Using Symmetric Defense Generative Adversarial Networks. Electronics 2022, 11, 1977. https://doi.org/10.3390/electronics11131977
Shieh C-S, Nguyen T-T, Lin W-W, Lai WK, Horng M-F, Miu D. Detection of Adversarial DDoS Attacks Using Symmetric Defense Generative Adversarial Networks. Electronics. 2022; 11(13):1977. https://doi.org/10.3390/electronics11131977
Chicago/Turabian StyleShieh, Chin-Shiuh, Thanh-Tuan Nguyen, Wan-Wei Lin, Wei Kuang Lai, Mong-Fong Horng, and Denis Miu. 2022. "Detection of Adversarial DDoS Attacks Using Symmetric Defense Generative Adversarial Networks" Electronics 11, no. 13: 1977. https://doi.org/10.3390/electronics11131977
APA StyleShieh, C.-S., Nguyen, T.-T., Lin, W.-W., Lai, W. K., Horng, M.-F., & Miu, D. (2022). Detection of Adversarial DDoS Attacks Using Symmetric Defense Generative Adversarial Networks. Electronics, 11(13), 1977. https://doi.org/10.3390/electronics11131977








