A Brief Review on Internet of Things, Industry 4.0 and Cybersecurity
Abstract
:1. Introduction
2. Methods
- Q1: What are the challenges of IoT cybersecurity in smart manufacturing?
- Q2: What types of cybersecurity are used in IoT for smart manufacturing?
- Removed for not being in English;
- Six duplicate publications were discarded;
- One hundred and twenty-four publications were excluded due to their title;
- Sixteen publications were excluded due to their content (little relevance).
| Study | Cybersecurity Method | Application |
|---|---|---|
| [10] | Blockchain | Smart manufacturing |
| [6] | State of the art | Smart manufacturing |
| [11] | Physical Hash | 3D Production by STL |
| [12] | Blockchain | IoT |
| [13] | Innovative random hybrid neural network (HDRaNN) | Industrial IoT |
| [14] | Random neural network (RaNN) | Industrial IoT |
| [15] | Cybersecurity Guidelines | Smart manufacturing |
| [16] | Authentication Mechanism | Industrial IoT |
| [17] | Convolution Neural Network (CNN). | IoT |
| [18] | Decision tree (DT), random forest (RF), and extreme gradient boosting (XGBoost) | Industry 4.0 and IoT |
| [19] | State of the art | IoT |
| [20] | State of the art | IoT |
| [21] | State of the art Authentication Mechanism | IoT |
| [2] | A methodology to assess the impacts of cyber-attacks | Industry 4.0 |
| [22] | Collaborative Learning Model for Cyberattack Detection | Industry 4.0 and IoT |
| [23] | Cyber security architecture | Industry 4.0 and IoT |
| [24] | Microsoft Threat Modelling Tool | Smart manufacturing |
| [25] | State of the art | Industry 4.0 and IoT |
| [26] | Deep Learning | IIoT |
| [27] | Logistic regression, decision tree, k-nearest neighbors, random forest, and autoencoder | Industry 4.0 |
| [28] | State of the art, Blockchain | Industry 4.0 |
| [29] | Protect machine-to-machine communication | IIoT |
| [30] | State of the art | IIoT |
| [31] | State of the art, Blockchain | Industry 4.0 and IoT |
| [32] | Basic cybersecurity requirements | Industry 4.0 |
| [33] | Testbed | IoT |
| [34] | State of the art, cybersecurity threats | Industry 4.0 |
| [35] | Ontology-Based Cybersecurity Framework | IoT |
| [36] | Hierarchical Network Intrusion Detection | IoT |
| [37] | Deep Learning | IoT |
3. Results
- Physical layer—consists of several sensors, microcomputers, and actuators. The sensors perform data collection and preprocessing, then send it through blockchain layers to the actuators.
- Blockchain service layer—the most critical layer that contains all the modules and services needed for the blockchain technology, it is subdivided into two parts, one related to real-time asymmetric cryptography with ARM Cortex-M processors and a private blockchain network which, through the proof of authentication (PoAh) consensus algorithm, allows the easy addition of new transactions.
- Application layer—layer with a user interface that allows the control, management, and visualization of systems and data.
4. Discussion
4.1. Analysis of the Analyzed Studies
4.2. Relation with Industry 4.0 and the IoT
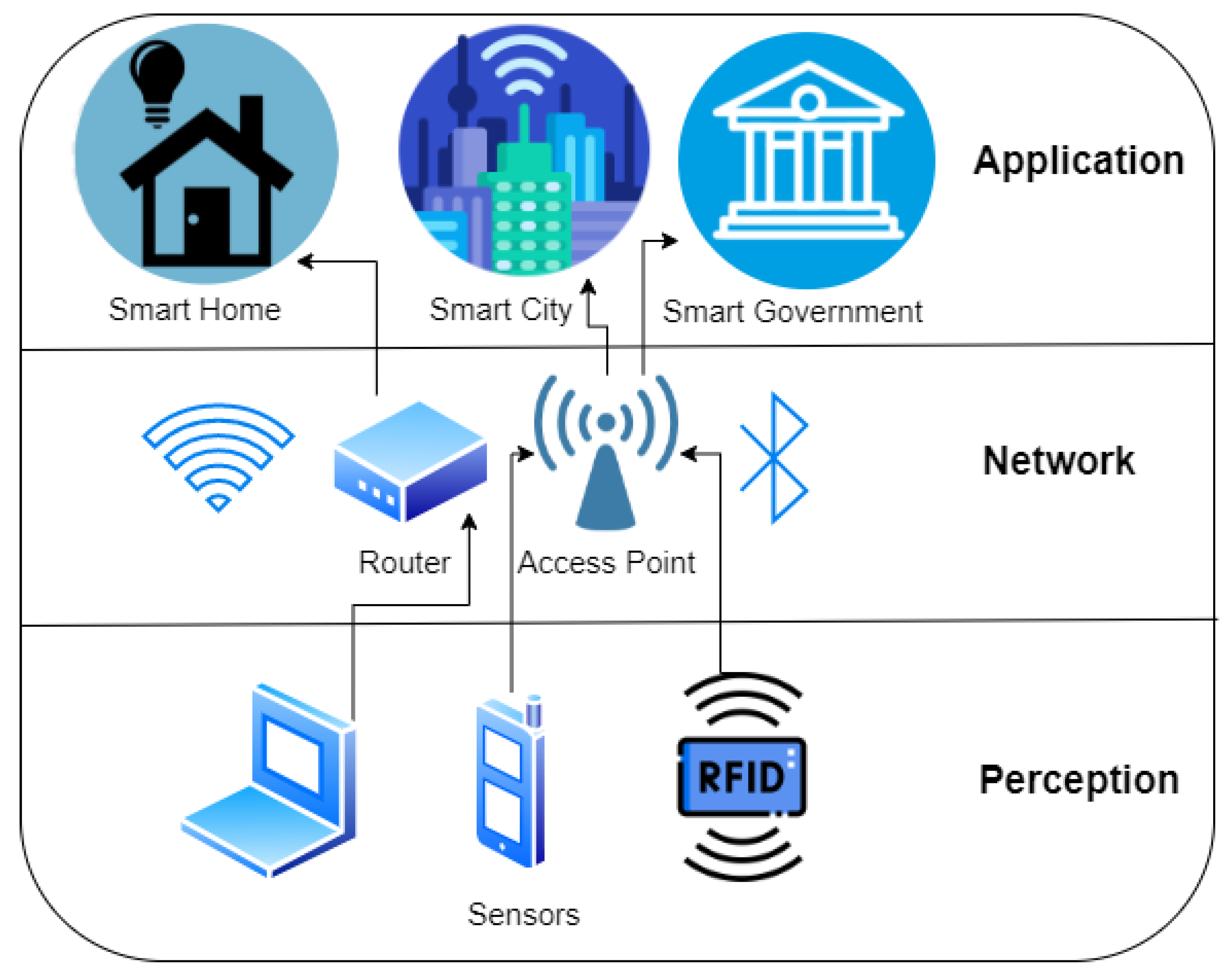
4.2.1. Perception Layer
4.2.2. Network Layer
4.2.3. Application Layer
4.3. Most Common Security Solutions Applied in the IoT Architecture
4.3.1. Authentication on the Perception Layer
- Triple data encryption algorithm (3DES or TDES)—a type of encryption where encryption algorithms are applied three times to each block of data;
- Advanced encryption standard (AES)—uses only a single key to encrypt and decrypt the information and is widely used for secure authentication [56];
- Asymmetric cryptography, or public-key cryptography, uses a pair of keys to encrypt and decrypt information, where one of the keys is public, and the other is private [57];
- Elliptic curve digital signature algorithm (ECDSA) is a digital signature algorithm that uses keys derived from elliptic curve cryptography, widely used on the web [58];
- Transport layer security (TLS) is a protocol whose objective is to guarantee communication security in a computer network. Transport layer security pre-shared key cipher suites (TLS-PSK) are a set of cryptographic protocols that allow secure transmission using pre-shared keys. TLS-DHE-RSA uses Rivest–Shamir–Adleman (RSA) key exchange, which is a public-key encryption system, and the Diffie–Hellman (DHE) protocol, which is a secure public key exchange system, to perform authentication [59,60];
- Multi-factor authentication, which uses biohashing, which that incorporates tax tokens, such as smart cards, and anonymity that allows hiding the identity of third parties, is another method that enables the performance of a secure authentication [59];
- A blockchain is a database that contains a distributed record so that there is not just one computer that includes the entire chain. Instead, users have a copy of the string. Blockchain allows the recording of transactions or any other digital interaction. It was designed to be safe and resistant to interruptions [61].
4.3.2. Secure Communication Solutions/Network Layer
4.3.3. Application Security/Application Layer
- Secure coding corresponds to a good software development practice to avoid the accidental introduction of security vulnerabilities;
- The secure boot protects against malicious attacks that can happen before the operating system starts;
- Access control list (ACL), which allows the specification of an object or user with access to a specific part of the system, allows only authorized processes [56];
- Firewall and IDS [63];
- Secure software updates correspond to software updates to ensure security [63].
4.4. Promising Cyber Security Techniques
4.4.1. Blockchain
4.4.2. Machine Learning
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nwakanma, C.; Islam, F.; Maharani, M.; Lee, J.-M.; Kim, D.-S. Detection and Classification of Human Activity for Emergency Response in Smart Factory Shop Floor. Appl. Sci. 2021, 11, 3662. [Google Scholar] [CrossRef]
- Corallo, A.; Lazoi, M.; Lezzi, M. Cybersecurity in the context of industry 4.0: A structured classification of critical assets and business impacts. Comput. Ind. 2020, 114, 103165. [Google Scholar] [CrossRef]
- Balda, J.C.; Mantooth, A.; Blum, R.S.; Tenti, P. Cybersecurity and Power Electronics: Addressing the Security Vulnerabilities of the Internet of Things. IEEE Power Electron. Mag. 2017, 4, 37–43. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Shrouf, F.; Ordieres, J.; Miragliotta, G. Smart factories in Industry 4.0: A review of the concept and of energy management approached in production based on the Internet of Things paradigm. In Proceedings of the 2014 IEEE International Conference on Industrial Engineering and Engineering Management, Selangor Darul Ehsan, Malaysia, 9–12 December 2014. [Google Scholar]
- Tuptuk, N.; Hailes, S. Security of smart manufacturing systems. J. Manuf. Syst. 2018, 47, 93–106. [Google Scholar] [CrossRef]
- Angelopoulos, A.; Michailidis, E.T.; Nomikos, N.; Trakadas, P.; Hatziefremidis, A.; Voliotis, S.; Zahariadis, T. Tackling Faults in the Industry 4.0 Era—A Survey of Machine-Learning Solutions and Key Aspects. Sensors 2020, 20, 109. [Google Scholar] [CrossRef] [Green Version]
- Etikan, I.; Alkassim, R.; Abubakar, S. Comparision of snowball sampling and sequential sampling technique. Biom. Biostat. Int. J. 2016, 3, 55. [Google Scholar] [CrossRef] [Green Version]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef]
- Latif, S.; Idrees, Z.; Ahmad, J.; Zheng, L.; Zou, Z. A blockchain-based architecture for secure and trustworthy operations in the industrial Internet of Things. J. Ind. Inf. Integr. 2021, 21, 100190. [Google Scholar] [CrossRef]
- Brandman, J.; Sturm, L.; White, J.; Williams, C. A physical hash for preventing and detecting cyber-physical attacks in additive manufacturing systems. J. Manuf. Syst. 2020, 56, 202–212. [Google Scholar] [CrossRef]
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Huma, Z.E.; Latif, S.; Ahmad, J.; Idrees, Z.; Ibrar, A.; Zou, Z.; Alqahtani, F.; Baothman, F. A Hybrid Deep Random Neural Network for Cyberattack Detection in the Industrial Internet of Things. IEEE Access 2021, 9, 55595–55605. [Google Scholar] [CrossRef]
- Latif, S.; Zou, Z.; Idrees, Z.; Ahmad, J. A Novel Attack Detection Scheme for the Industrial Internet of Things Using a Lightweight Random Neural Network. IEEE Access 2020, 8, 89337–89350. [Google Scholar] [CrossRef]
- Mullet, V.; Sondi, P.; Ramat, E. A Review of Cybersecurity Guidelines for Manufacturing Factories in Industry 4.0. IEEE Access 2021, 9, 23235–23263. [Google Scholar] [CrossRef]
- Srinivas, J.; Das, A.K.; Wazid, M.; Kumar, N. Anonymous Lightweight Chaotic Map-Based Authenticated Key Agreement Protocol for Industrial Internet of Things. IEEE Trans. Dependable Secur. Comput. 2018, 17, 1133–1146. [Google Scholar] [CrossRef]
- Jeon, J.; Park, J.H.; Jeong, Y.-S. Dynamic Analysis for IoT Malware Detection with Convolution Neural Network Model. IEEE Access 2020, 8, 96899–96911. [Google Scholar] [CrossRef]
- Tran, M.-Q.; Elsisi, M.; Mahmoud, K.; Liu, M.-K.; Lehtonen, M.; Darwish, M.M.F. Experimental Setup for Online Fault Diagnosis of Induction Machines via Promising IoT and Machine Learning: Towards Industry 4.0 Empowerment. IEEE Access 2021, 9, 115429–115441. [Google Scholar] [CrossRef]
- Lu, Y.; Da Xu, L. Internet of Things (IoT) Cybersecurity Research: A Review of Current Research Topics. IEEE Internet Things J. 2018, 6, 2103–2115. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of Threats? A Survey of Practical Security Vulnerabilities in Real IoT Devices. IEEE Internet Things J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Nandy, T.; Bin Idris, M.Y.I.; Noor, R.; Kiah, M.L.M.; Lun, L.S.; Juma’At, N.B.A.; Ahmedy, I.; Ghani, N.A.; Bhattacharyya, S. Review on Security of Internet of Things Authentication Mechanism. IEEE Access 2019, 7, 151054–151089. [Google Scholar] [CrossRef]
- Khoa, T.V.; Saputra, Y.M.; Hoang, D.T.; Trung, N.L.; Nguyen, D.; Ha, N.V.; Dutkiewicz, E. Collaborative Learning Model for Cyberattack Detection Systems in IoT Industry 4.0. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Korea, 25–28 May 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Vijayakumaran, C.; Muthusenthil, B.; Manickavasagam, B. A reliable next generation cyber security architecture for industrial internet of things environment. Int. J. Electr. Comput. Eng. 2020, 10, 387–395. [Google Scholar] [CrossRef]
- AbuEmera, E.A.; ElZouka, H.A.; Saad, A.A. Security Framework for Identifying threats in Smart Manufacturing Systems Using STRIDE Approach. In Proceedings of the 2022 2nd International Conference on Consumer Electronics and Computer Engineering (ICCECE), Guangzhou, China, 14–16 January 2022. [Google Scholar]
- Abdullahi, M.; Baashar, Y.; Alhussian, H.; Alwadain, A.; Aziz, N.; Capretz, L.F.; Abdulkadir, S.J. Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Electronics 2022, 11, 198. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Chang, V.; Hawash, H.; Chakrabortty, R.K.; Ryan, M. Deep-IFS: Intrusion Detection Approach for Industrial Internet of Things Traffic in Fog Environment. IEEE Trans. Ind. Inform. 2020, 17, 7704–7715. [Google Scholar] [CrossRef]
- Chang, V.; Doan, L.M.T.; Di Stefano, A.; Sun, Z.; Fortino, G. Digital payment fraud detection methods in digital ages and Industry 4.0. Comput. Electr. Eng. 2022, 100, 107734. [Google Scholar] [CrossRef]
- Leng, J.; Ye, S.; Zhou, M.; Zhao, J.L.; Liu, Q.; Guo, W.; Cao, W.; Fu, L. Blockchain-Secured Smart Manufacturing in Industry 4.0: A Survey. IEEE Trans. Syst. Man Cybern. Syst. 2020, 51, 237–252. [Google Scholar] [CrossRef]
- Dhirani, L.L.; Armstrong, E.; Newe, T. Industrial IoT, Cyber Threats, and Standards Landscape: Evaluation and Roadmap. Sensors 2021, 21, 3901. [Google Scholar] [CrossRef]
- Shah, Y.; Sengupta, S. A survey on Classification of Cyber-attacks on IoT and IIoT devices. In Proceedings of the 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 28–31 October 2020. [Google Scholar]
- ElMamy, S.; Mrabet, H.; Gharbi, H.; Jemai, A.; Trentesaux, D. A Survey on the Usage of Blockchain Technology for Cyber-Threats in the Context of Industry 4.0. Sustainability 2020, 12, 9179. [Google Scholar] [CrossRef]
- lhan, İ.; Karaköse, M. Requirement Analysis for Cybersecurity Solutions in Industry 4.0 Platforms. In Proceedings of the 2019 International Artificial Intelligence and Data Processing Symposium (IDAP), Malatya, Turkey, 21–22 September 2019. [Google Scholar]
- Lee, S.; Lee, S.; Yoo, H.; Kwon, S.; Shon, T. Design and implementation of cybersecurity testbed for industrial IoT systems. J. Supercomput. 2018, 74, 4506–4520. [Google Scholar] [CrossRef]
- Pereira, T.; Barreto, L.; Amaral, A. Network and information security challenges within Industry 4.0 paradigm. Procedia Manuf. 2017, 13, 1253–1260. [Google Scholar] [CrossRef]
- Mozzaquatro, B.A.; Agostinho, C.; Goncalves, D.; Martins, J.; Jardim-Goncalves, R. An Ontology-Based Cybersecurity Framework for the Internet of Things. Sensors 2018, 18, 3053. [Google Scholar] [CrossRef] [Green Version]
- Bovenzi, G.; Aceto, G.; Ciuonzo, D.; Persico, V.; Pescapé, A. A hierarchical hybrid intrusion detection approach in IoT scenarios. In Proceedings of the GLOBECOM 2020—2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020. [Google Scholar]
- Nascita, A.; Cerasuolo, F.; Di Monda, D.; Garcia, J.T.A.; Montieri, A.; Pescape, A. Machine and Deep Learning Approaches for IoT Attack Classification. In Proceedings of the 2022 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Virtual, 2–5 May 2022. [Google Scholar]
- Gubán, M.; Kovács, G. Industry 4.0 conception. Acta Tech. Corviniensis-Bull. Eng. 2017, 10, 111–114. [Google Scholar]
- Hermann, M.; Pentek, T.; Otto, B. Design principles for industrie 4.0 scenarios. In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016. [Google Scholar]
- Grabowska, S. Smart factories in the age of Industry 4.0. Manag. Syst. Prod. Eng. 2020, 28, 90–96. [Google Scholar] [CrossRef]
- Wheeler, K. How a ‘Segment of One’ Approach Can Help Businesses Connect with Their Customers. Available online: https://www.fourthsource.com/general/how-a-segmentof-one-approach-can-help-businesses-connect-with-theircustomers-23392 (accessed on 12 November 2019).
- Ferguson, G.T. Have your objects call my objects. Harv. Bus. Rev. 2002, 80, 138–144. [Google Scholar]
- Madakam, S.; Ramaswamy, R.; Tripathi, S. Internet of Things (IoT): A literature review. J. Comput. Commun. 2015, 3, 164. [Google Scholar] [CrossRef] [Green Version]
- Georgios, L.; Kerstin, S.; Theofylaktos, A. Internet of things in the context of industry 4.0: An overview. Int. J. Entrep. Knowl. 2019, 7, 4–19. [Google Scholar]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015. [Google Scholar]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The social internet of things (siot)—When social networks meet the internet of things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Leo, M.; Battisti, F.; Carli, M.; Neri, A. A federated architecture approach for Internet of Things security. In Proceedings of the 2014 Euro Med Telco Conference (EMTC), Naples, Italy, 12–15 November 2014. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Emeishan, Chinay, 14–15 December 2013. [Google Scholar]
- Zhang, Y.; Wen, J. The IoT electric business model: Using blockchain technology for the internet of things. Peer-to-Peer Netw. Appl. 2017, 10, 983–994. [Google Scholar] [CrossRef]
- Deogirikar, J.; Vidhate, A. Security attacks in IoT: A survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017, Analytics and Cloud) (I-SMAC).
- El-Hajj, M.; Fadlallah, A.; Chamoun, M.; Serhrouchni, A. A Survey of Internet of Things (IoT) Authentication Schemes. Sensors 2019, 19, 1141. [Google Scholar] [CrossRef] [Green Version]
- Kumar, S.; Sahoo, S.; Mahapatra, A.; Swain, A.K.; Mahapatra, K.K. Security enhancements to system on chip devices for IoT perception layer. In Proceedings of the 2017 IEEE International Symposium on Nanoelectronic and Information Systems (iNIS), Bhopal, India, 18–20 December 2017. [Google Scholar]
- Yang, Z.; Yue, Y.; Yang, Y.; Peng, Y.; Wang, X.; Liu, W. Study and application on the architecture and key technologies for IOT. In Proceedings of the 2011 International Conference on Multimedia Technology, Hangzhou, China, 26–28 July 2011. [Google Scholar]
- Santos, L.; Rabadao, C.; Gonçalves, R. Intrusion detection systems in Internet of Things: A literature review. In Proceedings of the 2018 13th Iberian Conference on Information Systems and Technologies (CISTI), Caceres, Spain, 13–16 June 2018. [Google Scholar]
- Nastase, L. Security in the internet of things: A survey on application layer protocols. In Proceedings of the 2017 21st International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania, 29–31 May 2017. [Google Scholar]
- Islam, M.R.; Aktheruzzaman, K.M. An Analysis of Cybersecurity Attacks against Internet of Things and Security Solutions. J. Comput. Commun. 2020, 8, 11–25. [Google Scholar] [CrossRef] [Green Version]
- Hodgson, R. Solving the security challenges of IoT with public key cryptography. Netw. Secur. 2019, 2019, 17–19. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Noor, M.B.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Leloglu, E. A Review of Security Concerns in Internet of Things. J. Comput. Commun. 2016, 5, 121–136. [Google Scholar] [CrossRef] [Green Version]
- Wu, M.; Song, Z.; Moon, Y.B. Detecting cyber-physical attacks in CyberManufacturing systems with machine learning methods. J. Intell. Manuf. 2019, 30, 1111–1123. [Google Scholar] [CrossRef]
- Li, P.; Su, J.; Wang, X. iTLS: Lightweight Transport-Layer Security Protocol for IoT with Minimal Latency and Perfect Forward Secrecy. IEEE Internet Things J. 2020, 7, 6828–6841. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, S.; Li, Z.; Zhang, Y.; Deng, Q.; Ray, S.; Jin, Y. Internet-of-Things Security and Vulnerabilities: Taxonomy, Challenges, and Practice. J. Hardw. Syst. Secur. 2018, 2, 97–110. [Google Scholar] [CrossRef]
- Butun, I.; Osterberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef] [Green Version]
- Haber, S.; Stornetta, W.S. How to time-stamp a digital document. J. Cryptol. 1991, 3, 99–111. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. Bitcoin. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 14 May 2022).
- Dinh, T.T.A.; Liu, R.; Zhang, M.; Chen, G.; Ooi, B.C.; Wang, J. Untangling Blockchain: A Data Processing View of Blockchain Systems. IEEE Trans. Knowl. Data Eng. 2018, 30, 1366–1385. [Google Scholar] [CrossRef] [Green Version]
- Rathi, R.; Sharma, N.; Manchanda, C.; Bhushan, B.; Grover, M. Security challenges & controls in cyber physical system. In Proceedings of the 2020 IEEE 9th International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 10–12 April 2020. [Google Scholar]
- Halpin, H.; Piekarska, M. Introduction to Security and Privacy on the Blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and Privacy in Decentralized Energy Trading Through Multi-Signatures, Blockchain and Anonymous Messaging Streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar] [CrossRef]
- Bahga, A.; Madisetti, V.K. Blockchain Platform for Industrial Internet of Things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef] [Green Version]
- Zhang, X.-D. Machine Learning, in a Matrix Algebra Approach to Artificial Intelligence; Springer: Berlin/Heidelberg, Germany, 2020; pp. 223–440. [Google Scholar]
- Buczak, A.L.; Guven, E. A survey of data mining and machine learning methods for cyber security intrusion detection. IEEE Commun. Surv. Tutor. 2015, 18, 1153–1176. [Google Scholar] [CrossRef]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine Learning in IoT Security: Current Solutions and Future Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef] [Green Version]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rudenko, R.; Pires, I.M.; Oliveira, P.; Barroso, J.; Reis, A. A Brief Review on Internet of Things, Industry 4.0 and Cybersecurity. Electronics 2022, 11, 1742. https://doi.org/10.3390/electronics11111742
Rudenko R, Pires IM, Oliveira P, Barroso J, Reis A. A Brief Review on Internet of Things, Industry 4.0 and Cybersecurity. Electronics. 2022; 11(11):1742. https://doi.org/10.3390/electronics11111742
Chicago/Turabian StyleRudenko, Roman, Ivan Miguel Pires, Paula Oliveira, João Barroso, and Arsénio Reis. 2022. "A Brief Review on Internet of Things, Industry 4.0 and Cybersecurity" Electronics 11, no. 11: 1742. https://doi.org/10.3390/electronics11111742
APA StyleRudenko, R., Pires, I. M., Oliveira, P., Barroso, J., & Reis, A. (2022). A Brief Review on Internet of Things, Industry 4.0 and Cybersecurity. Electronics, 11(11), 1742. https://doi.org/10.3390/electronics11111742







