Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network
Abstract
:1. Introduction
2. Related Works
3. Security Requirements of Medical Sensors
- Mutual authentication: The proposed protocol should include mutual authentication to ensure participants’ protection. Participants interacting should be authenticated [27].
- Data integrity: Data integrity refers to the fact that all data values’ syntactic and semantic specifications are met without unauthorized interference. Two specific and reliable criteria are implemented. Data integrity can be divided into four categories: integrity of individuals, the integrity of places, referential integrity, and integrity defended by primary keys, controls, laws, and external triggers [25].
- Backward and Forward Secrecy: Backward and forward secrecy play critical roles in securing exchanged messages in previous and next communication. Therefore, any proposed scheme needs to provide this property to prevent adversaries from obtaining the session keys. In case the adversary receives the current session key, he/she cannot obtain the previous and next session key [28].
- Data Usability: The use of data implies the usage of data or data structures by approved users. Big data provides immense benefits and crucial challenges, including false data and non-standard data. Moreover, unauthorized access-caused data manipulation or failure often destroys data usability [29].
- Various attack resistance: In a multi-server environment, the authentication scheme should be able to resist specific passive and active attacks, practically in real-world applications [28].
- Key Agreement for Secure Session: The proposed scheme should provide a secure session key to encrypt communication and protect the authentication message between entities [26].
4. Preliminaries
4.1. Hash Functions
- It is easy to find O = H(String) if the string is described.
- If O = H(String) is illustrated, the string cannot be identified.
- The difficult job is to differentiate between the inputs of String1 and String2, so H(String1) = H(String2). It has called collision resistance.
4.2. Elliptic Curve Cryptography
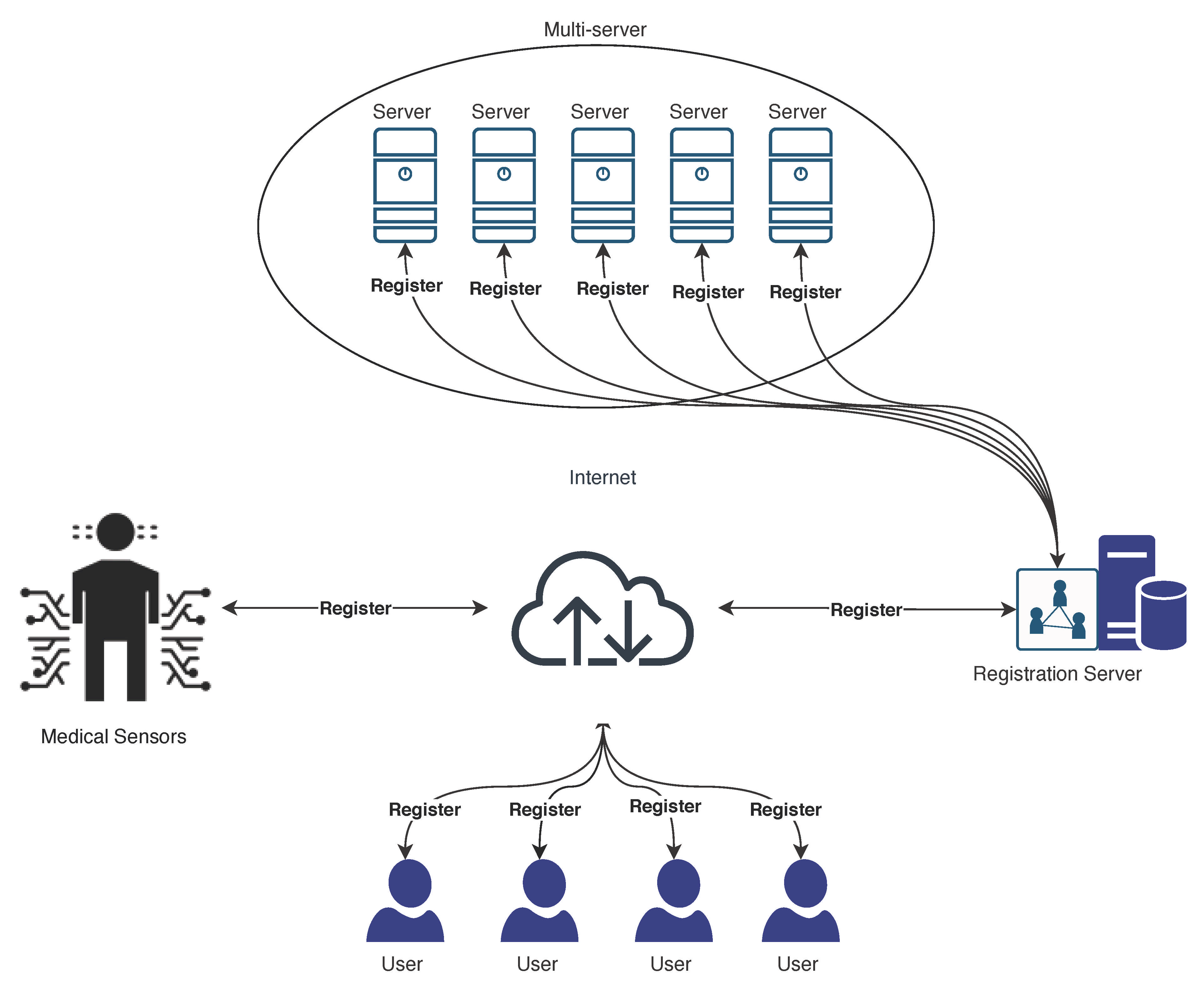
5. Cross-SN Scheme
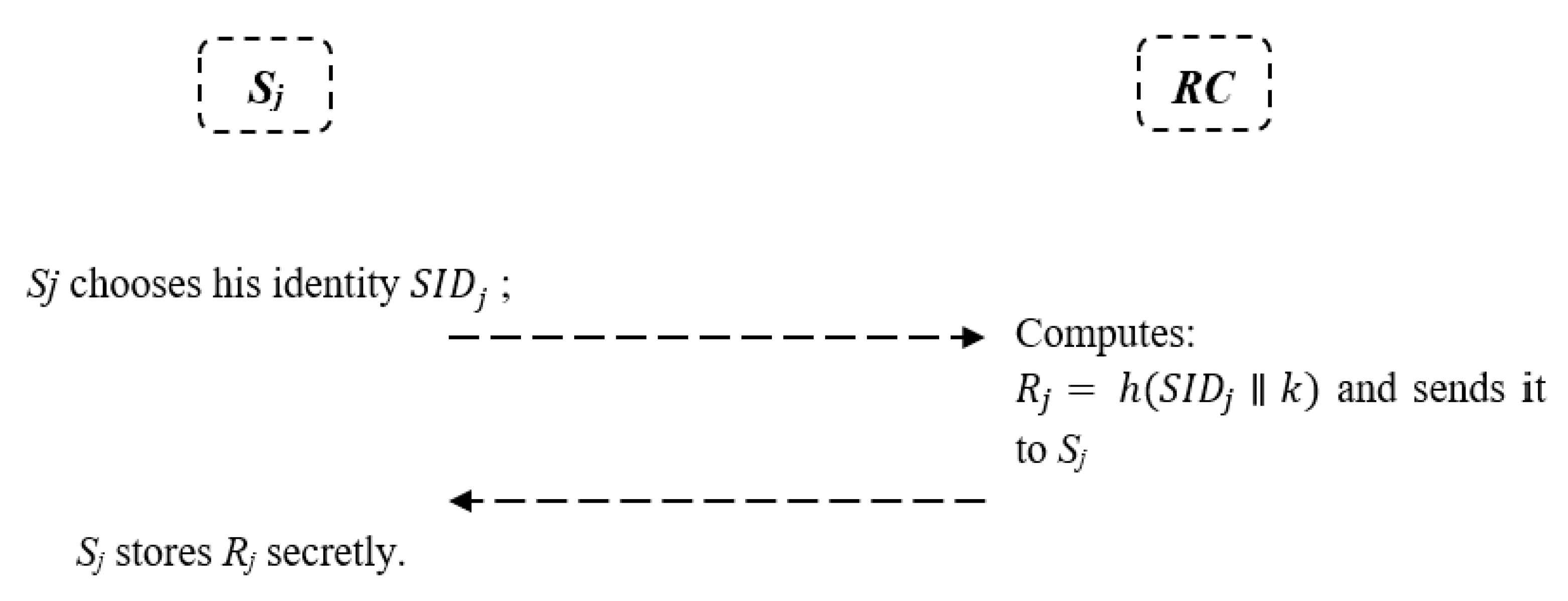
5.1. Server Registration Phase
- The server first selects an identity ; then, through a secure channel, the message will be forwarded to the RC.
- RC receives the server identity and computes ; then, it sends the message to the .
- Now, the server receives the message and store securely.
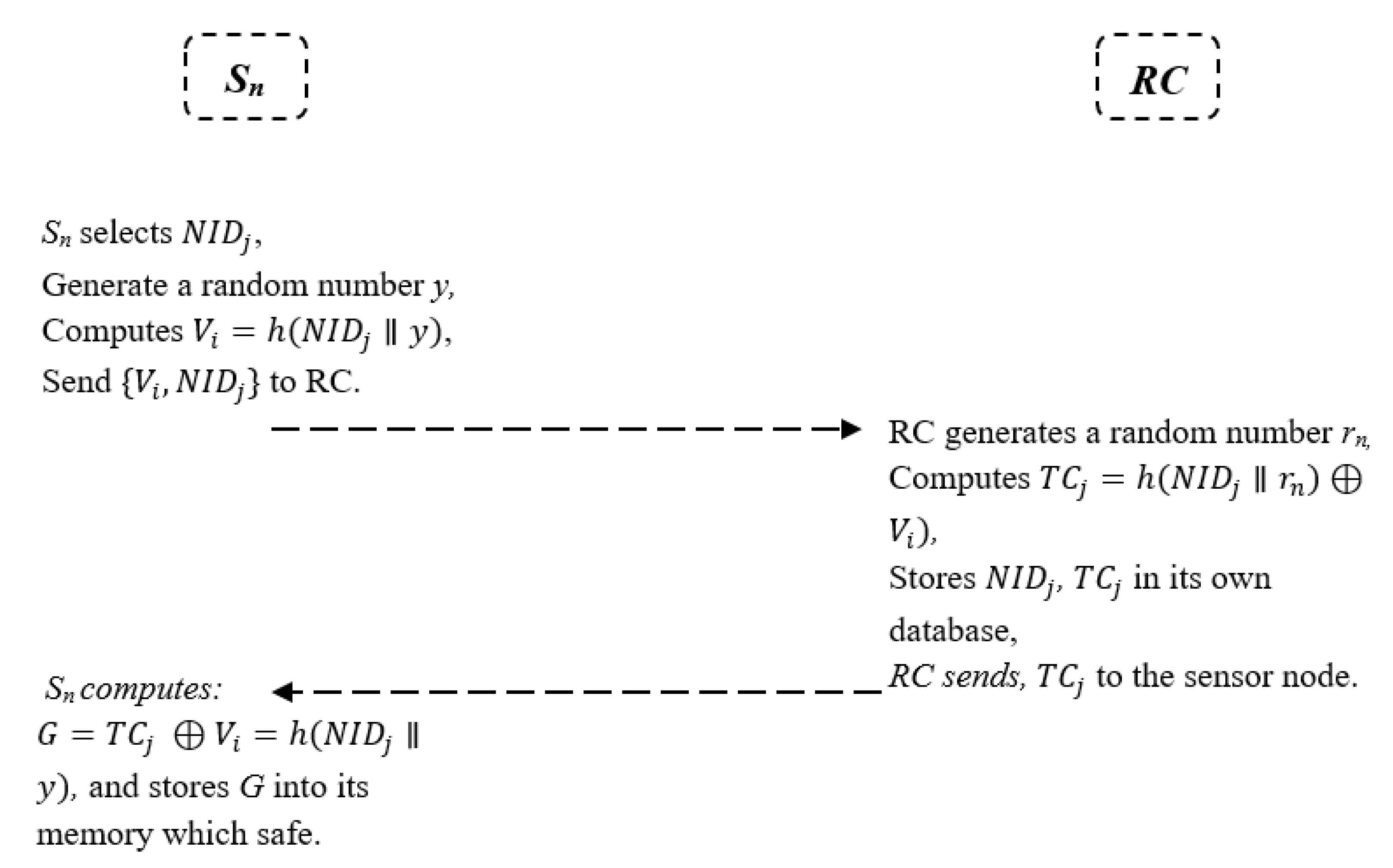
5.2. Sensor Node Registration Phase
- (1)
- First, the sensor node Sn selects and a random number y; then, it computes and send the message to RC through a secure channel.
- (2)
- RC receives the message ; RC generates a random number rn computing and stores in its database. Then, RC sends to the sensor node through a secure channel.
- (3)
- After RC receives the message from the sensor node, Sn computes and stores G into its memory, which is safe.
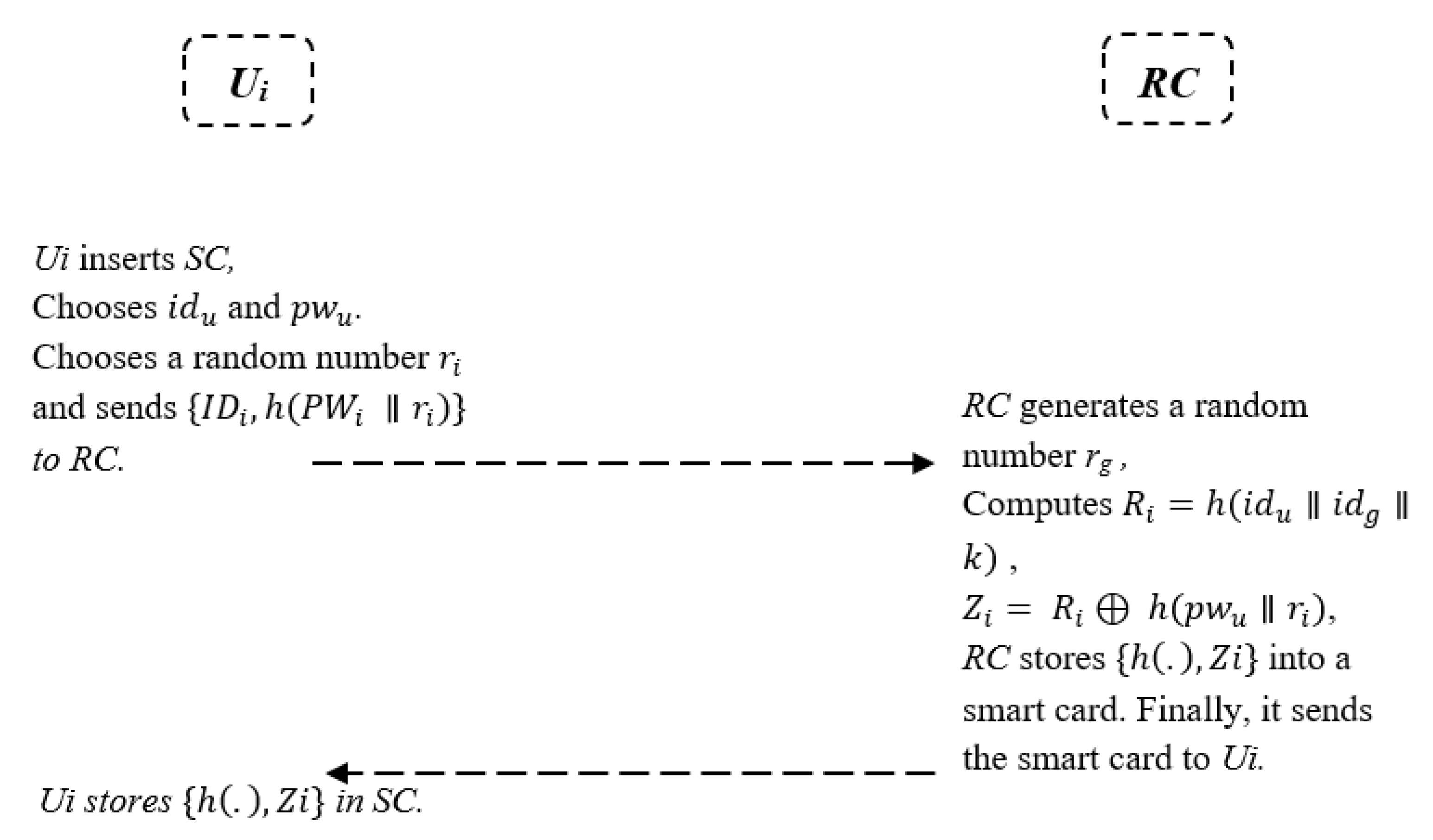
5.3. User Registration Phase
- After the user, , inserts the smart card and selects the identity and password , he/she chooses a random number and, then, sends the message to RC via a secure channel;
- Now, the RC has the message and generates a random number rrc. Later, it calculates , , where k is RC’s secret key. After that, RC stores into a smart card. RC finally sends the embedded SC to the user .
- The user stores into the smart card.
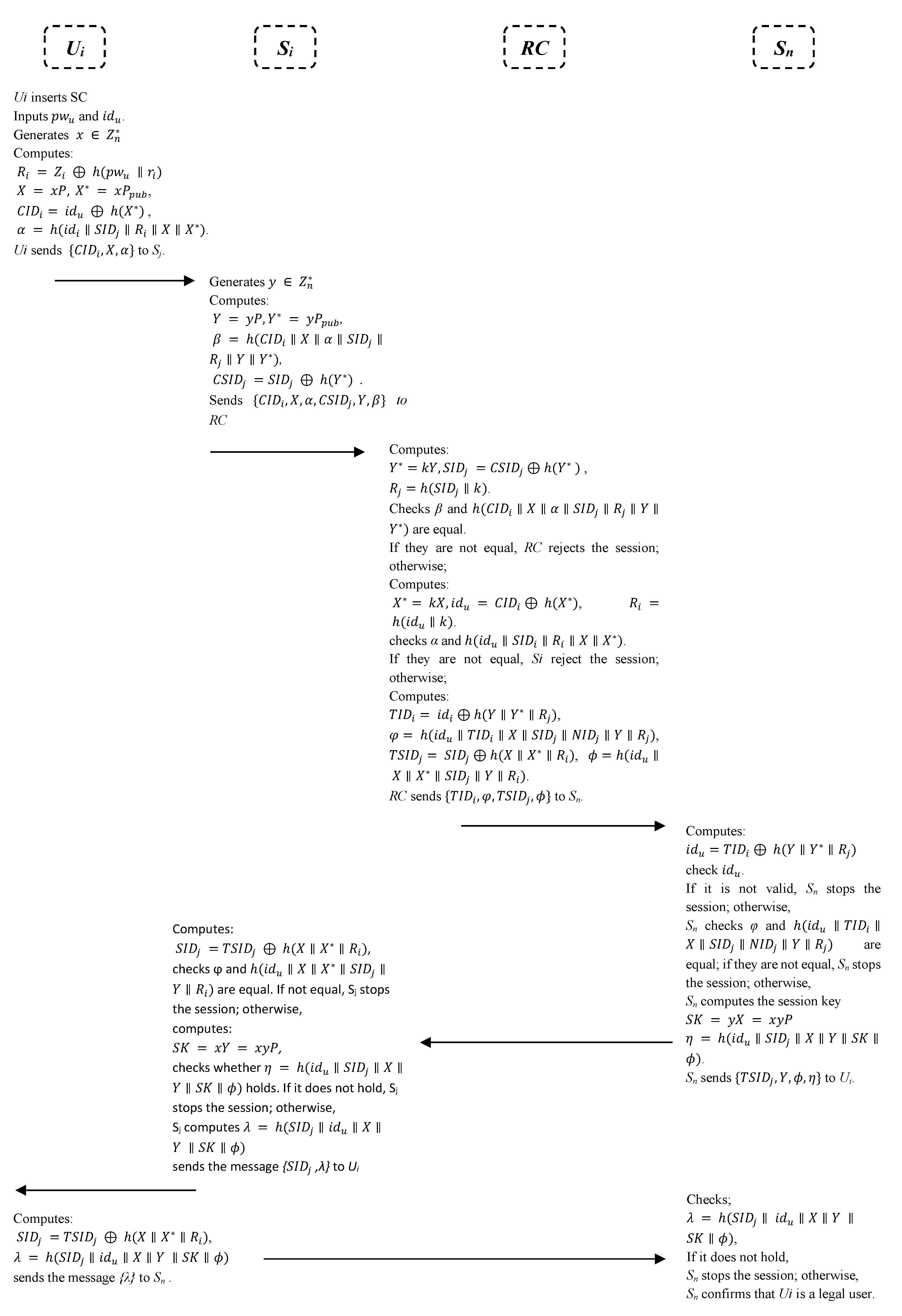
5.4. Login and Authentication Phase
- The user first inserts his/her smart card and types the username and password . It chooses a random number to compute , , , and . sends the message to .
- Upon receiving the message , server selects a random number , and calculates , , and . Then, it sends to RC.
- The RC receives , and computes and . It then verifies and . If not valid, end the session; else, RC calculates , , and . Also, verify by computing . If valid, , , , and . Otherwise, it ends the session. Later, the RC sends to the sensor node Sn.
- The sensor node receives the message , and computes . Then, validate the identity . If not, end the session; otherwise, it validates and . If valid, it calculates the session key and ); else, end the session. After that, Sn sends the message to .
- The message is now received by the to calculate . It validates and ). If valid, it computes the session key P and checks whether ); if not, the server ends the session.
- The user receives , and computes , and ; then, it sends to the sensor node Sn.
- Sn checks by calculating ). If it does not hold, it ends the session; otherwise, Sn confirms that is a legal user.
5.5. Password Updates Phase
- After inserting the SC into a card reader, the user types and .Then, has to type the newly selected password .
- SC calculates , , and
- Finally, is replaced with .
6. Security Analysis
6.1. BAN Logic Proof
- Goal 1: .
- Goal 2: .
- Goal 3: .
- Goal 4: .
- Msg 1:
- Msg 2:
- Msg 3:
- Msg 4:
- Msg 5:
- Msg 6:
- A1: .
- A2: .
- A3:
- A4: .
- A5: .
- A6: .
- A7: .
- A8: .
- A9: .
- A10: .
- A11: .
- A12: .
- A13: .
- A14: .
- 1.
- Message 1:
- S1) RC ◃.// The message-meaning rule is applied according to assumption A4 to obtain the following:
- S2) .// We could obtain it according to Msg 2.
- 2.
- Message 2:
- S3) RC ◃.// Based on the assumption A6, the message-meaning is applied to obtain
- S4) RC .// Then, we obtain S5, according to Msg 3.
- 3.
- Message 3:
- S5) Sn ◃.// The message meaning is applied to obtain S6 based on assumption A4.
- S6) Ui . // We applied the freshness conjuncatention based on assumption A3 to obtain S7.
- S7) Ui . // Then, we apply the BAN logic rule to break conjunction according to S7.
- S8) Ui . //Under assumption A7, we apply the law of competence to obtain
- S9) Ui . // According to , we could obtain
- S10) Ui . Goal 1.
- 4.
- Message 4:
- S11) Sj ◃ // We applied the message meaning according to assumption A7 to obtain
- S12) Sj . // We apply the freshness conjuncatention rule to obtain S13 under assumption A2.
- S13) Sn .// Again, the BAN logic rule is extended to break conjunctions.
- S14) Sn . // According to , we could obtain
- S16) Sn . Goal 2.
- 5.
- Message 5:
- S17) Sj ◃. // We apply the message sense rule according to assumption A10.
- S18) Sj . // We apply the A1 freshness conjuncatenation rule.
- S19) Ui .// Then, we apply the BAN logic rule for breaking the S20 conjunction.
- S20) Ui . // Goal 3.
- 6.
- Message 6:
- S21) Sn ◃.// We use the message meaning rule to get S22.
- S22) Sn . // Again, under assumption A13, we use the freshness conjuncatention rule.
- S23) Sn . // Then, we apply BAN to break the conjunction in order to produce
- S24) Sn . Goal 4.
6.2. Informal Security Analysis
- Multi-server Support: From the abovementioned, we know that Ui has access to numerous services from different servers and only needs to register with RC once. One authentication password is required for the user to remember. The proposed framework is, therefore, suitable for configuration of the multi-server.
- Data integrity: In the proposed scheme, the one-way hash function h(.) is used to protect the identity and the password before transmission, which modifies the message to be impossible . In addition, the information is attached to a random number that it generates freshly. Therefore, the message’s modification is difficult in our scheme; thus, it provides data integrity.
- Backward and forward secrecy support: If the attackers know the current session key, it will be challenging to know the next session key. The session key is calculated , where the secret values are generated randomly by the Ui, Sj, and Sn. These values are different when the protocol is executed. Every session is independent; thus, even though the session’s current key is known, the previous and future key cannot be obtained.
- Mutual authentication: In the proposed scheme, the user Ui, server Sj, and sensor node Sn authenticate each other. The server authenticates the user if the values and calculated are valid. In addition, the RC authenticates the server if the value and ) calculated by the RC are equal to the message received from the server. The sensor node then validates the message received from the RC and ); if the calculated value is equal, then the Sn authenticates the RC.
- Session key agreement: In the proposed scheme, the adversary cannot obtain the key session’s information to compute the key for the next session even if the adversary knows the current key because the key session is calculated as , where the secret values are generated randomly by the Ui, Sj, and Sn. The values are different when the protocol is executed. The key session is developed independently in every session. Therefore, the key session agreement is achieved in the proposed scheme.
- Stolen verifier attack: RC calculates the Ui secret key and sends it to Ui during the proposed scheme’s user registration phase. RC does not maintain an Ui password or secret key verifier table. Then, even though the opponent may access the Ui database, the adversary cannot obtain authentication information. The proposed scheme should therefore avoid a stolen attack by the verifier.
- Man-in-the-middle attack: We are aware of the discussion that the scheme proposed could provide mutual authentication between Ui, Sj, Sn, and RC. The proposed scheme should therefore avoid an attack also on the man in the middle.
- Impersonation attack: The adversary cannot send a legal message , even though they obtains two authentication factors. The suggested scheme, therefore, resists a user-impersonation attack.
- Server spoofing attack: To impersonate Ui, Sj, Sn, and RC, the adversary has to generate the valid message . It is easy to know to obtain authentication, but he/she cannot finish the task since they do not know Rj and whether is a secure hash function. The proposed scheme could therefore resist a server spoofing attack.
- Offline password guessing attack: If the adversary steals the user’s smart card and extracts information using a side-channel attack, the adversary might be able to guess the password . The accuracy of the value, however, is secured by a secure hash function and is not plaintext. In addition, by comparing the RC with the one in the database, it checks the password and identification. The proposed scheme is, therefore, immune to an offline attack.
- Replay attack: Suppose that an intruder intercepts the message and attempts to replay Ui by replaying it with Sj. They could detect the attack by checking the validity of . Using a similar approach, it might be shown that Ui finds a replay attack by testing the validity of ). The proposed scheme could therefore withstand a replay attack.
- Modification attack: In the authentication phase, the authentication message i s sent as a hash value and contains a unique random number. Therefore, the server then calculates , ), and to check if there was any modification carried out. If the message is modified, the server will detect it and the rest of the values will not be decrypted. Likewise, when the server Sj sends the message to the RC, it will verify the message by computing and ); if the message is not valid, the RC will end the session. Therefore, the proposed scheme withstands a modification attack.
- Stolen smart card attack: let us assume that the adversary can extract the information after it is st olen by a side-channel attack. The RC will recalculate the message that received and verified it with the stored one. In this case, the attacker cannot obtain the correctness of the value due to the hash function that hides the username and password in the hash value. Therefore, the proposed scheme achieves resistance against a stolen smart card attack.
7. Functionality Analysis
7.1. Computation Cost
7.2. Communication Cost
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Landaluce, H.; Arjona, L.; Perallos, A.; Falcone, F.; Angulo, I.; Muralter, F. A Review of IoT Sensing Applications and Challenges Using RFID and Wireless Sensor Networks. Sensors 2020, 20, 2495. [Google Scholar] [CrossRef]
- Ugrenovic, D.; Gardasevic, G. CoAP protocol for Web-based monitoring in IoT healthcare applications. In Proceedings of the 2015 23rd Telecommunications Forum Telfor (TELFOR), Belgrade, Serbia, 24–26 November 2015; pp. 79–82. [Google Scholar]
- Khalid, H.; Lun, K.Y.; Othman, M.; Ahmad, I. Authentication Groups With Privacy-Protection of Machine-to-Machine in LTE-LTE-A networks. J. Theor. Appl. Inf. Technol. 2017, 95, 2896–2905. [Google Scholar]
- Yu, S.; Park, Y. SLUA-WSN: Secure and Lightweight Three-Factor-Based User Authentication Protocol for Wireless Sensor Networks. Sensors 2020, 20, 4143. [Google Scholar] [CrossRef] [PubMed]
- Alezabi, K.A.; Hashim, F.; Hashim, S.J.; Ali, B.M. A new tunnelled EAP based authentication method for WiMAX networks. In Proceedings of the 2013 IEEE 11th Malaysia International Conference on Communications (MICC), Kuala Lumpur, Malaysia, 28–30 November 2013; pp. 412–417. [Google Scholar]
- Wu, T.; Redouté, J.M.; Yuce, M.R. A wearable wireless medical sensor network system towards internet-of-patients. In Proceedings of the 2018 IEEE SENSORS, New Delhi, India, 28–30 October 2018; pp. 1–3. [Google Scholar]
- Azmi, N.; Kamarudin, L.M. Enabling IoT: Integration of Wireless Sensor Network for Healthcare Application Using WASPMOTE; AIP Publishing LLC: New York, NY, USA, 2017; Volume 1808, p. 020010. [Google Scholar]
- Gardašević, G.; Katzis, K.; Bajić, D.; Berbakov, L. Emerging Wireless Sensor Networks and Internet of Things Technologies—Foundations of Smart Healthcare. Sensors 2020, 20, 3619. [Google Scholar] [CrossRef]
- Kumar, P.; Lee, H.J. Security issues in healthcare applications using wireless medical sensor networks: A survey. Sensors 2012, 12, 55–91. [Google Scholar] [CrossRef] [Green Version]
- Khalid, H.; Hashim, S.J.; Ahmad, S.M.; Hashim, F.; Chaudary, M.A. Cybersecurity in Industry 4.0 context: Background, issues, and future directions. Nine Pillars Technol. Ind. 2020, 263–307. [Google Scholar] [CrossRef]
- Ko, J.; Lu, C.; Srivastava, M.B.; Stankovic, J.A.; Terzis, A.; Welsh, M. Wireless sensor networks for healthcare. Proc. IEEE 2010, 98, 1947–1960. [Google Scholar] [CrossRef] [Green Version]
- He, D.; Wang, D. Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 2014, 9, 816–823. [Google Scholar] [CrossRef]
- Mir, O.; Munilla, J.; Kumari, S. Efficient anonymous authentication with key agreement protocol for wireless medical sensor networks. Peer Peer Netw. Appl. 2017, 10, 79–91. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. An improved and anonymous two-factor authentication protocol for health-care applications with wireless medical sensor networks. Multimed. Syst. 2017, 23, 195–205. [Google Scholar] [CrossRef]
- Ever, Y.K. Secure-anonymous user authentication scheme for e-healthcare application using wireless medical sensor networks. IEEE Syst. J. 2018, 13, 456–467. [Google Scholar] [CrossRef]
- Zmezm, H.F.; Hashim, S.; Sali, A.; Alezabi, K.A. Pre-authentication design for seamless and secure handover in mobile WiMAX. Int. Rev. Comput. Softw. (IRECOS) 2015, 10, 764–772. [Google Scholar] [CrossRef]
- Khalid, H.; Hashim, S.J.; Syed Ahmad, S.M.; Hashim, F.; Akmal Chaudhary, M. Security and Safety of Industrial Cyber-Physical System : Systematic Literature Review. Palarch’S J. Archaeol. Egypt/Egyptol. 2020, 17, 1592–1620. [Google Scholar]
- Kumar, P.; Lee, S.G.; Lee, H.J. E-SAP: Efficient-strong authentication protocol for healthcare applications using wireless medical sensor networks. Sensors 2012, 12, 1625–1647. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Sangaiah, A.K.; Li, X.; Wu, F. An enhanced three factor based authentication protocol using wireless medical sensor networks for healthcare monitoring. J. Ambient. Intell. Humaniz. Comput. 2018, 1–22. [Google Scholar] [CrossRef]
- Shuai, M.; Liu, B.; Yu, N.; Xiong, L. Lightweight and secure three-factor authentication scheme for remote patient monitoring using on-body wireless networks. Secur. Commun. Netw. 2019, 2019. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Syst. J. 2019, 14, 39–50. [Google Scholar] [CrossRef]
- Mo, J.; Hu, Z.; Lin, Y. Cryptanalysis and Security Improvement of Two Authentication Schemes for Healthcare Systems Using Wireless Medical Sensor Networks. Secur. Commun. Netw. 2020, 2020. [Google Scholar] [CrossRef]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Security and privacy in the medical internet of things: A review. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef]
- Pal, S.; Hitchens, M.; Rabehaja, T.; Mukhopadhyay, S. Security requirements for the internet of things: A systematic approach. Sensors 2020, 20, 5897. [Google Scholar] [CrossRef] [PubMed]
- Somasundaram, R.; Thirugnanam, M. Review of security challenges in healthcare internet of things. Wirel. Netw. 2020, 1–7. [Google Scholar] [CrossRef]
- Sun, Y.; Lo, F.P.W.; Lo, B. Security and privacy for the internet of medical things enabled healthcare systems: A survey. IEEE Access 2019, 7, 183339–183355. [Google Scholar] [CrossRef]
- Zhang, Y.; Luo, M.; Choo, K.K.R.; He, D. A General Architecture for Multiserver Authentication Key Agreement with Provable Security. Secur. Commun. Netw. 2018, 2018. [Google Scholar] [CrossRef] [Green Version]
- Cichonski, J.; Marron, J.; Hastings, N.; Ajmo, J.; Rufus, R. [Project Description] Security for IoT Sensor Networks: Building Management Case Study (Draft). Available online: https://csrc.nist.gov/publications/detail/white-paper/2019/02/01/security-for-iot-sensor-networks/draft (accessed on 2 February 2019).
- Dubrawsky, I. Eleventh Hour Security+: Exam SY0-201 Study Guide; Syngress: Boston, MA, USA, 2009. [Google Scholar]
- Hankerson, D.; Menezes, A.J.; Vanstone, S. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Rubin, A.D.; Honeyman, P. Formal Methods for the Analysis of Authentication Protocols; Technical Report; Center for Information Technology Integration: Ann Arbor, MI, USA, 8 November 1993. [Google Scholar]
- Chen, C.L.; Chen, Y.X.; Lee, C.F.; Deng, Y.Y.; Chen, C.H. An efficient and secure key agreement protocol for sharing emergency events in VANET systems. IEEE Access 2019, 7, 148472–148484. [Google Scholar] [CrossRef]
- Chen, C.L.; Lin, D.P.; Chen, H.C.; Deng, Y.Y.; Lee, C.F. Design of a Logistics System with Privacy and Lightweight Verification. Energies 2019, 12, 3061. [Google Scholar] [CrossRef] [Green Version]
- Sammoud, A.; Chalouf, M.A.; Hamdi, O.; Montavont, N.; Bouallegue, A. A secure and lightweight three-factor authentication and key generation scheme for direct communication between healthcare professionals and patient’s WMSN. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar]

| Notation | Abbreviation |
|---|---|
| SC | Smart Card |
| Server | |
| RC | Registration Centre |
| Node Sensor | |
| User | |
| Identity of server | |
| k | Server’s private key |
| Identity of node sensor | |
| , | Random Numbers |
| User identity | |
| User Password | |
| Registration Centre identity | |
| Hash function |
| Notation | Abbreviation |
|---|---|
| P believes X | |
| X is fresh | |
| P has jurisdiction over X | |
| P sees X | |
| P once said X | |
| X or Y is one part of (X, Y) | |
| X combined with Y | |
| X is fresh with the key K | |
| P and Q use the shared key K to communicate | |
| The current session key | |
| The message-meaning rule | |
| The freshness-conjuncatenation rule | |
| The nonce verification | |
| The jurisdiction rule |
| Feature | He et al. [12] | Wu et al. [14] | Sammoud et al. [35] | Proposed Scheme |
|---|---|---|---|---|
| Multi-server Support | ✓ | ✕ | ✕ | ✓ |
| Data integrity | ✕ | ✕ | ✕ | ✓ |
| Backward and forward secrecy | ✓ | ✕ | ✓ | ✓ |
| Data Usability | ✕ | ✕ | ✕ | ✓ |
| Mutual Authentication | ✓ | ✓ | ✓ | ✓ |
| Session key agreement | ✕ | ✕ | ✓ | ✓ |
| Stolen Verifier Attack | ✓ | ✓ | ✕ | ✓ |
| Man-in-the-middle attack | ✓ | ✕ | ✓ | ✓ |
| Impersonation Attack | ✓ | ✓ | ✓ | ✓ |
| Server Spoofing Attack | ✓ | ✓ | ✕ | ✓ |
| Offline Password Guessing Attack | ✕ | ✓ | ✕ | ✓ |
| Replay Attack | ✓ | ✓ | ✓ | ✓ |
| Modification Attack | ✓ | ✕ | ✕ | ✓ |
| Stolen Smart Card Attack | ✕ | ✕ | ✕ | ✓ |
| / | Wu et al. [14] | Sammoud et al. [35] | He et al. [12] | Cross-SN Scheme |
|---|---|---|---|---|
| E1 | ||||
| E2 | ||||
| E3 | ||||
| E4 | ||||
| E5 | ||||
| E6 | ||||
| E7 | ||||
| E8 | ||||
| E9 | ||||
| Total Computation Cost | 0.0622 ms | 0.5857 ms | 0.6524 ms | 0.0957 ms |
| Total Communication Cost | 1632 bits | 1056 bits | 980 bits | 800 bits |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khalid, H.; Hashim, S.J.; Syed Ahmad, S.M.; Hashim, F.; Chaudhary, M.A. Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network. Electronics 2021, 10, 790. https://doi.org/10.3390/electronics10070790
Khalid H, Hashim SJ, Syed Ahmad SM, Hashim F, Chaudhary MA. Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network. Electronics. 2021; 10(7):790. https://doi.org/10.3390/electronics10070790
Chicago/Turabian StyleKhalid, Haqi, Shaiful Jahari Hashim, Sharifah Mumtazah Syed Ahmad, Fazirulhisyam Hashim, and Muhammad Akmal Chaudhary. 2021. "Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network" Electronics 10, no. 7: 790. https://doi.org/10.3390/electronics10070790
APA StyleKhalid, H., Hashim, S. J., Syed Ahmad, S. M., Hashim, F., & Chaudhary, M. A. (2021). Cross-SN: A Lightweight Authentication Scheme for a Multi-Server Platform Using IoT-Based Wireless Medical Sensor Network. Electronics, 10(7), 790. https://doi.org/10.3390/electronics10070790







