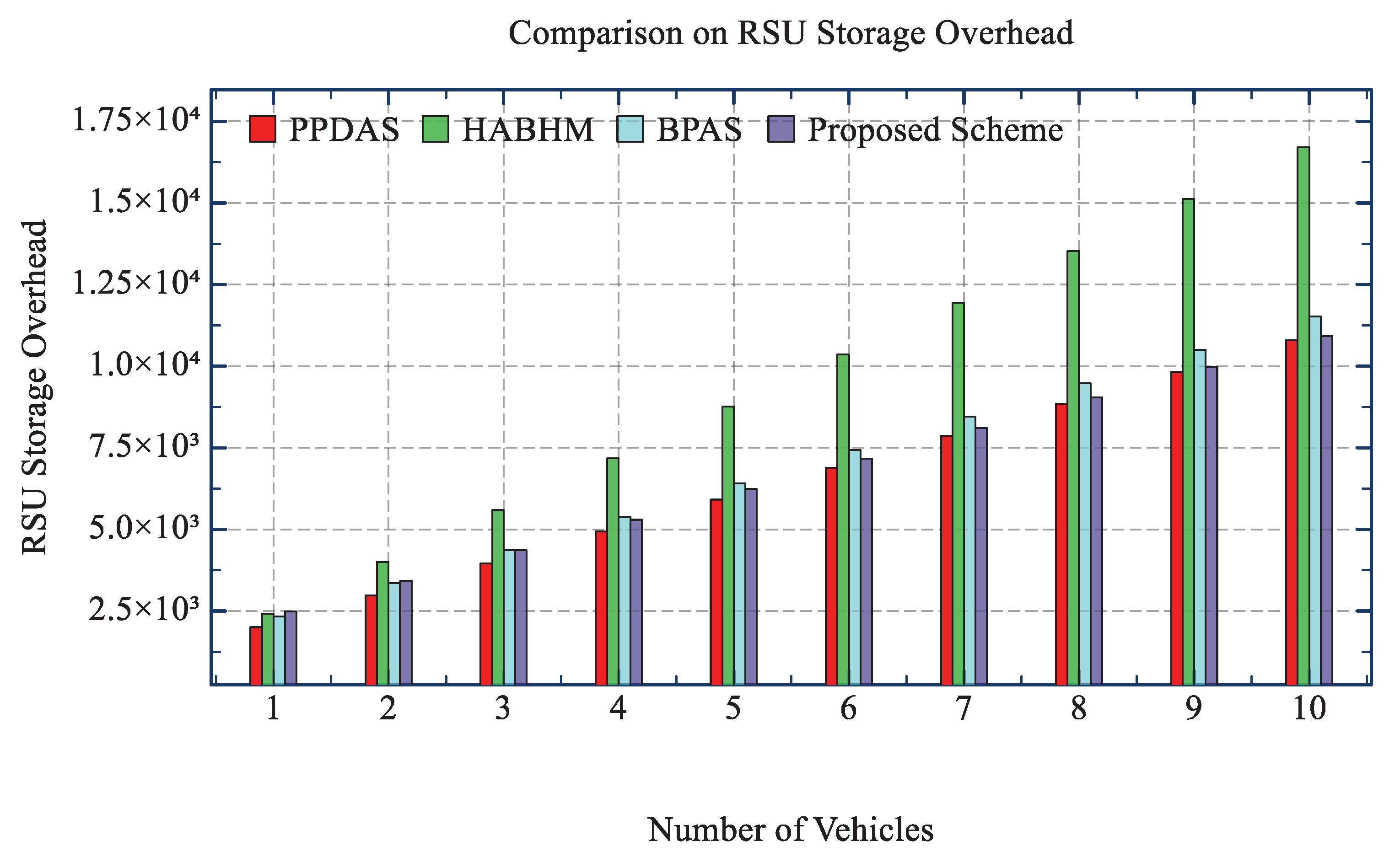
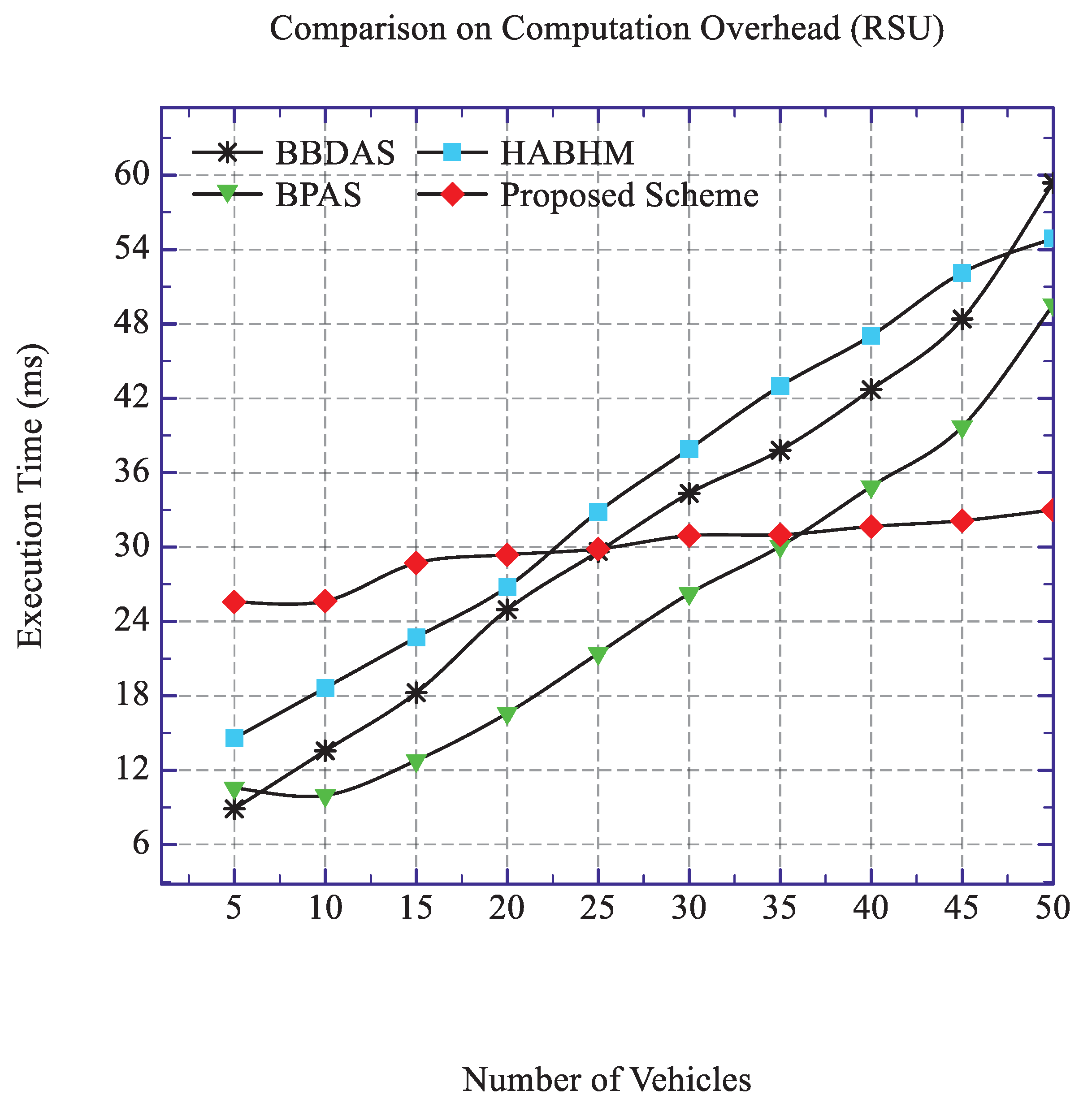
1. Introduction
The tremendous popularization of the intelligent transportation system (ITS), which is considered to be the primary strategy for improving transportation quality, has been prompted by major enhancements in information and communication technology in recent years [
1,
2]. ITS, with its anticipated benefits, is responsible for delivering groundbreaking services and applications covering diverse modes of transport and traffic management, which are of particular interest to metropolitan cities and prosperous regions. Consequently, as the fundamental infrastructure of ITS, the VANET is characterized as the dispersed, self-organized wireless networks developed by heterogeneous vehicle entities. Generally, there are three key components of a typical VANET architecture: trusted authority (TA) as the centralized service provider, RSUs as the fundamental roadside facilities, and vehicles as the terminal users [
3,
4].
TA is in charge of the entire VANET operations including the confidential key allocation. Notably, vast vehicular data from VANET agencies are also consolidated and analyzed on the TA side. Evidently, TA is in strong need of computational and storage capabilities. Nowadays, advanced networking and data transmission approaches, including promising 5G networks and cloud computing, have been devoted to a heterogeneous IoT paradigm including VANETs, where ample computing and storage capacity can be assured [
5]. The remote cloud networks have been able to accommodate communications between several VANETs at the same time, accelerating the creation of a universal global vehicle internet initiative (IoV) [
6]. The RSUs are specified as the dispersed facilities built along the roadsides at fixed intervals. The successful ranges of fixed RSUs are expected to cover all road areas in order to offer services to specified vehicles [
7,
8,
9]. In particular, each RSU is able to perform the requisite key computing task and store critical data in its storage. Each vehicle can then at all times get access to the applications and resources from VANETs. As the terminal users of VANET, the vehicles in turn collaboratively collect vast heterogeneous vehicular data, as well as real-time road characteristics such as traffic congestion and car crash reports. The aggregated data are then transmitted to the VANETs central server for further processing. In the meantime, relevant VANETs services are being forwarded to those vehicles, which dramatically enhances driving safety. Functionally, each vehicle is installed with an on-board unit (OBU) on which wireless communication modules, including transceiver and transponder, are mounted [
10,
11,
12]. The OBU of the vehicle is designed to manage both transmission and receiving of messages in the high-mobility environment.
Connectivity between the vehicle and its surrounding RSU can be accomplished by the communication between vehicle to RSU (V2R). Meanwhile, data exchange between vehicles can be assured by vehicle to vehicle connection (V2V). Self-organized wireless networks comprising multiple vehicles within specified locations can also be built [
13,
14], providing real-time data sharing and aggregation. Note that the dedicated short-range communications (DSRC) technique is implemented in both V2V and V2R communication. The interconnected system of VANETs is therefore developed with high connectivity and complex topology. However, critical V2V and V2R data sharing are carried out in the open wireless environment of realistic VANET circumstances. Therefore, serious vulnerability to various security threats and privacy risks exists [
15,
16]. The critical key details and user secrets may be unlawfully exposed to malicious attackers or unauthorized users, which may compromise the whole VANET network. In this case, efficient security preservation and privacy protection mechanisms in VANETs need to be deployed [
17].
In practical VANET circumstances, the VANET data exchange is highly restrained by complicated physical environments and changeable communication conditions [
18]. Specifically, the geographical barriers including high mountains and skyscrapers may obstruct the regular message delivery for V2V and V2R data sharing. Moreover, the dynamic wireless ad hoc topologies constructed by the spontaneous high-speed vehicles lead to a temporary and indisciplined interaction paradigm [
19], which brings challenges to real-time V2V communication. In this case, the VANET connectivities will be drastically impacted, resulting in insufficient availability and low scalability. To address this practical issue, additional auxiliary facilities can be implemented in the VANET model for active connectivity improvement. Hence, multi-hop message forwarding can be provided with extra routes. With this motivation, the unmanned aerial vehicles (UAVs) can be applied to practical VANETs as the autonomous switching nodes for advancing the transmission quality and availability [
20,
21,
22]. Apparently, with its unique advantages including substitutability, low expense, and applicability, the UAV-assisted VANETs could play a substantial part in practical VANET implementation [
23]. In this case, the studies emphasizing UAV secure association and its correlation with the remaining VANET entities are imperative [
24,
25,
26].
V2V communication provides instant and spontaneous data sharing channel for the nearby vehicles of comparatively short distances [
27]. Therefore, open and legitimate data interactions among neighboring vehicles can be achieved, specifically for vehicles within one RSU domain. However, the V2V communication topology constructed by high-mobility vehicles may not properly satisfy the requirements for constant and reliable vehicular data exchange for long-distance vehicles. That is, due to the high mobility of participating vehicles, the constructed V2V network appears to be temporary and time-oriented [
28]. For example, two vehicles within one RSU domain can easily access the VANET and conduct V2V communication according to their own will. Both the V2V and V2R channels are securely preserved with advanced cryptographic techniques and strategies. However, the two vehicles are then traveling to different spots in the next moment, and each is in the range of individual RSU. At this moment, assuming the two vehicles have to disseminate subsequent messages, the conventional V2V communication intended for short-distance data exchange is not suitable. Meanwhile, the multi-hops channel among other vehicles is not efficient in this case. The long-distance remote V2V communications should be further studied accordingly. However, the corresponding remote V2V message delivery topic for long-distance vehicular communication in the range of different RSUs has not been properly researched so far.
Motivated by the above issues on secure VANET communication and V2V remote message dissemination, in this paper, the novel UAV-based VANET infrastructure is constructed initially. Therefore, VANET communication connectivity can be significantly improved, specifically for practical vehicular communication scenarios. Accordingly, the efficient group verification and key management process for the participating UAVs are presented. Moreover, the remote vehicular message dissemination for long-distance vehicles within different RSU domains is investigated. In the cross-domain authentication (CDA) paradigm, the decentralized V2V connection strategy with RSUs assistance is proposed.
Our Research Contributions
In this paper, the RSU-aided remote V2V message dissemination design with group association for UAV-assisted VANETs is proposed. The nontrivial efforts can be briefly summarized as follows:
Secure and efficient UAV association design with batch verification: Our design adopts the UAV-assisted VANETs infrastructure, where multiple UAV entities are involved in V2V and V2R communications for connectivity improvement. The certificateless mutual authentication process for UAV association is developed. The partial secret key is utilized by the central server and UAV itself. Non-repudiation, user anonymity, and conditional privacy for each UAV can be guaranteed. Moreover, batch verification is provided in our design. Reliable vehicular data transmission in practical VANET environments can be achieved via the constructed UAV networks.
Dynamic key management and updating mechanism for UAV-assisted VANETs: Upon verification, the corresponding UAV group key can be generated and safely distributed to the requesting UAVs. The efficient key updating method for all the involved UAVs is achieved. Notably, the dynamic UAV revocation is enabled, while the updated group key is timely acquired by the remaining legitimate UAVs. Heterogeneous vehicular data can then be forwarded through UAV assistance so that the geographic obstructions and interferences can be avoided with the alternative routes provided by UAV interactions.
RSU-aided remote V2V message dissemination with anonymity: The remote vehicular data exchange method is presented for long-distance V2V communication. Particularly, the proposed design is conducted without remote cloud assistance. With the pre-stored driving records collected from the CDA process, the disseminated vehicular message can be forwarded through the edge RSUs and finally transmitted to the destination vehicle. Subsequently, anonymity for the participating vehicles can be guaranteed. Moreover, the superiority on both the security and performance characteristics can be achieved with the formal analysis and performance comparison.
The remainder of this paper is formulated as follows: The corresponding research development is briefly introduced in
Section 2. To gain a better understanding of the topic,
Section 3 outlines the requisite preliminary works and the developed UAV-assisted VANET system model. In
Section 4, the secure UAV group authentication and key management, and V2V remote message dissemination are presented in detail. The security analysis and performance discussion are presented in
Section 5 and
Section 6, respectively. The conclusions are drawn in
Section 7.
2. Related Works
Nowadays, secure vehicular communication in VANET scenarios has been widely investigated. Various schemes on the authentication and key management for VANETs entities have been proposed so far. In 2012, to enhance privacy preservation and efficiency for key updating, Lu et al. [
5] proposed the dynamic authenticated key management scheme with location-based services (LBSs) in VANETs. The double-registration detection mechanism is applied in the proposed DIKE scheme. The LBS session key is assigned to each time slot divided from LBS session. The backward secrecy can be achieved with the integrated threshold technique. Subsequently, the EMAP protocol intended for certificate revocation of VANET is developed in [
18]. The received message is validated with the current certificate revocation lists (CRLs) for verifying the authenticity. Meanwhile, the generated keys for the related efficient revocation checking process are shared among the non-revoked vehicles. Subsequently, Lin et al. proposed an efficient cooperative authentication scheme for massive message validation in VANETs [
9]. The authentication overhead for the individual vehicle can be reduced. Thereafter, the two-factor lightweight VANETs authenticating scheme (2FLIP) is designed by Wang et al. [
4]. The decentralization of certificate authority (CA) and biological-password-based two-factor 2FA are applied. The lightweight hashing process with fast message authentication code (MAC) regeneration design is utilized for efficient user verification. The overhead of certificate management can be reduced with the decentralized CA structure. Similarly, Lo et al. developed the paring-free identity-based message authentication scheme with the batch signature mechanism [
27], thus optimized performance in terms of time consumption can be achieved. Recently, several VANET authentication schemes emphasizing on lightweight vehicular verification and privacy-preserving have been developed [
7,
13].
As for secure V2V data exchange, Liu et al. proposed a dual authenticated key agreement scheme (PPDAS) for secure V2V communication in the IoV paradigm [
19]. The historical vehicle trust reputation evaluation method is adopted for the final V2V session key establishment. The dual verification leverages anonymous vehicle identity and behavior authentication to improve decision-making accuracy. In the next, the decentralized lightweight authentication protocol for vehicular networks is developed in [
2]. The biometric device (BD) and tamper-proof device (TPD) are used for vehicle verification and key preservation. The authentication signature protocol with hash-chain key generation is introduced for V2V interactions. Anonymous identities for vehicles are applied. Similarly, Wu et al. presented the privacy-preserving mutual authentication protocol for secure vehicular data exchange in dynamic topographical VANET scenarios [
17]. Recent research also includes the V2V authentication method developed by Vasudev et al. [
12].
The research on UAV communication has attracted lots of attention from academia. In 2017, Yoon et al. proposed the security authentication system employing the encrypted channel for UAV networks [
24]. The hijacking problem for UAV control can be addressed. Subsequently, Zhou et al. developed the physical layer security improvement method through UAV with air-to-ground jammer for secure wireless communication [
25]. In 2020, Gope et al. constructed the authenticated key agreement scheme for edge-assisted UAV networks. The mobile edge computing service providers are responsible for UAV verification in this scheme. In the next, Zhang et al. presented the gateway-oriented two-server authenticated key agreement [
20]. The security of user passwords can be guaranteed in this way. Recently, a mobile edge computing (MEC) system with UAV assistance is developed in [
23]. The ground users could offload the computing tasks to the nearby legitimate UAVs. Notably, the jamming signals are to be transmitted from the full-duplex legitimate UAV and other non-offloading ground users. The latency of the MEC system can be reduced accordingly. Aliev et al. proposed a scalable and lightweight group key management and matrix-based message encryption method for confidentiality preservation of V2V broadcasting [
22]. The distributed and scalable VANET architecture is applied. Overall, the existing V2V schemes mainly focus on the close vehicular communication within the single RSU domain, while the long-distance remote V2V communication has not been properly studied so far.
3. Preliminaries and Model Definitions
In this section, the relevant cryptographic principles and fundamental knowledge are presented in order to promote the reader’s comprehension of the proposed schemes. The concepts of Lagrange polynomial interpolation, bilinear pairing, Chinese remainder theorem, and homomorphic encryption are introduced, respectively. Subsequently, the related notations, the UAV-assisted VANET system model, the security criteria, and network assumptions are defined.
3.1. Lagrange Polynomial Interpolation
Given a set of
different data points
,
,
holds. Define the polynomial of the degree
k in a finite field
as
, where
for
. Hence, for
,
holds. The interpolation polynomial
in the Lagrange form can be defined as the linear combination as follows:
Note that the Lagrange basis polynomials
(
) are computed as
That is,
holds. Accordingly, for
,
Hence, for the polynomial of degree k, with different data points on the graph of polynomial and , the reconstruction of the polynomial can be conducted accordingly.
3.2. Bilinear Pairing
Let and be the cyclic additive group and multiplicative group generated with the same prime order q. A mapping function can be defined as a bilinear pairing if all of the following three properties are satisfied:
- (1)
Bilinearity: and
, there is
- (2)
Non-degeneracy: such that , where is the identity element of .
- (3)
Computability:, there is an efficient algorithm to calculate .
The bilinear map satisfying the above properties can be constructed with the modified Weil pairing or Tate pairing on the supersingular elliptic curve , where the following characteristics are presented.
Definition 1 (Elliptic Curve Discrete Logarithm Problem (ECDLP)).
Define , where . Hence, for any probabilistic polynomial-time (PPT) adversary , the advantage in finding the integer to solve the ECDLP problem is defined as , which is negligible as the following equation: Definition 2 (Computational Diffie–Hellman Problem (CDHP)).
Define as the cyclic group with the large prime order q. Given for , where P is the generator of the cyclic group . Hence, for any probabilistic polynomial-time (PPT) adversary , the advantage in finding computing for solving the given CDHP problem is defined as , which is negligible as the following equation: 3.3. Chinese Remainder Theorem (CRT)
Let
be the pairwise co-prime positive integers. For an arbitrary sequence of integers
, the system congruences defined as
has a unique solution modulo
. In this case, for
, we can get
Hence,
and
for
. The solution can be computed as
3.4. Homomorphic Encryption
The homomorphic encryption design allows the predefined standard computations on ciphertexts, with which the output matches the encryption result on the computations conducted on plaintexts. With its unique properties, homomorphic encryption can be widely applied to vast security designs and privacy-preserving strategies. Hence, the transmitted data can be securely processed and out-sourced without revealing privacy-related information. The encryption and decryption functionalities can be considered as the homomorphisms between plaintext and ciphertext spaces. In practical communication scenarios with semi-trusted entities, homomorphic encryption could remove privacy barriers inhibiting data sharing since the operations on encrypted data can be performed instead of direct calculations on the confidential user data. The Paillier cryptosystem is one of the homomorphic cryptosystems for public key infrastructure (PKI). The security of Paillier cryptosystem is based on the decisional composite residuosity assumption (DCRA) described as follows:
Definition 3 (Decisional Composite Residuosity Assumption (DCRA)). Let be two large primes such that . Given , if there exist satisfying , hence α is defined as the n-th residue modulo . Notably, given the composite n and an integer β, it is hard to decide whether β is the n-th residue modulo .
The Paillier encryption process is additively homomorphic. That is, the product of the two ciphertexts will decrypt to the sum of their corresponding plaintexts. Let
be the plaintexts,
be the random integers during encryption. The following additive homomorphic properties can be satisfied:
where
holds.
denotes the encrypting operation.
3.5. Notations
The notations used in the proposed scheme, as well as the corresponding descriptions are listed in the following
Table 1.
3.6. System Model
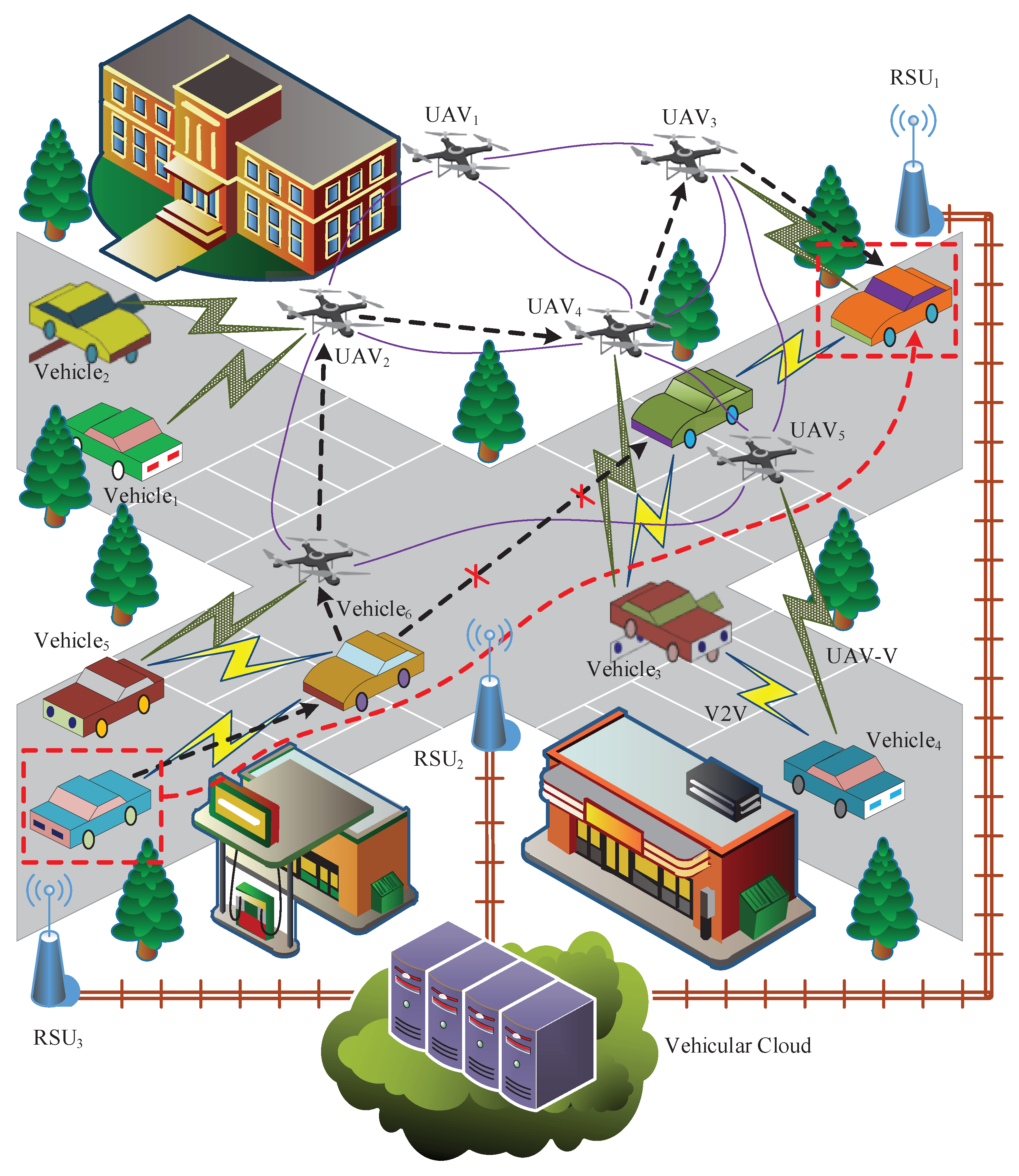
The UAV-assisted VANET infrastructure of our design is briefly explained in this section. In our assumption, the UAVs participate in the vehicular communication process as the significant message forwarding and transmission node. The VANET wireless network connectivity can be improved in order to overcome the negative impacts caused by geographical obstructions and signal interferences. As shown in
Figure 1, the typical VANETs system model consists of four different layers with distinctive functionalities: the vehicular cloud as the central server, the edge layer containing the RSU facilities, the vehicle layer regarding the terminal vehicles/users, and the UAV layer for connectivity improvement. The relevant descriptions of the four VANET layers are respectively presented as follows.
Vehicular cloud is regarded as the core storage facility in charge of data storing and processing. Heterogeneous vehicular data of the whole VANET are analyzed in the vehicular cloud (VC). Notably, the utilized cloud architecture is able to provide sufficient processing and storage capabilities for multiple VANET prototypes simultaneously, which drastically facilitates the implementation of global IoV initiatives. Additionally, efficient data interchanges with nearby VANET facilities can be accomplished with the dedicated 5G communicating infrastructure. With full authority, the essential operations for the entire VANET system, including the vehicle registration, session key allocation, and user authentication, are all carried out by the VC, which is considered as the legitimate and trustworthy data server in the assumption. Note that VC is defined to be valid and trustworthy anytime.
Edge layer is defined as the distributed local VANET facility composed of various RSU clusters. Each RSU cluster maintains collaborative wired connections among the neighboring RSUs within the vicinity. Accordingly, the decentralized edge network for instant vehicular data exchange and service provision can be guaranteed. Each RSU cluster is responsible for essential vehicular information sharing and distributive edge computation. Overall, in the cloud-assisted VANET system, heterogeneous vehicular data are analyzed and stored in the cloud server, while the edge computing RSU clusters are deployed. Low latency, better response time, and transfer rates can be guaranteed in V2R interactions, which leverages the physical proximity to the terminal user. That is, the frequently used data requested from VC can be temporarily cached in the local edge server so that rapid response to the vehicles can be guaranteed. The bandwidth burden for VC can be significantly alleviated in this way.
Vehicle layer refers to the vehicle networks constructed during V2V and V2R communication. The embedded OBU within each vehicle is equipped with wireless transceiver and transponder for message delivery in high-mobility VANET scenarios. Meanwhile, the implemented TPD is for confidential information preservation. Notably, the vehicle, the OBU, and the driver are considered as one entity in our system model. Considering of the resource limitation, lightweight designs in terms of authentication and secure data exchange are crucial for practical VANETs.
UAV Cluster is defined as a set of autonomous switching nodes for advancing the transmission quality and availability. Upon validation, the legitimate UAV networks are responsible for the low-cost and multi-hop routing network construction. In practical VANET occasions, the geographical barriers such as high mountains and skyscrapers may interfere with regular V2V or V2R connections. In this case, the VANETs could take advantage of the self-organized UAV network and built substantial routing paths via dynamic UAV connections. Apparently, with its unique advantages including substitutability, low expense, and applicability, the UAV-assisted VANETs could play an imperative part in practical VANET implementation. The studies emphasizing UAV secure association and its correlation with the remaining VANET entities are vital.
3.7. Network Assumptions
As illustrated in
Figure 1, the wired connections involving the VC and various local RSUs enable reliable vehicular data exchange with all the participating vehicles. Accordingly, effective strategies and techniques could be executed. Moreover, the connectivity between the vehicle and its surrounding RSU can be accomplished by V2R communication, while the data exchange between vehicles can be assured by V2V communication. All are supported by the dedicated short-range communications (DSRC) technique. However, critical V2V and V2R data sharing are carried out in the open wireless environment of realistic VANET circumstances. Therefore, serious vulnerability to various security threats and privacy risks exists. The critical key details and user secrets may be unlawfully exposed to malicious attackers or unauthorized users, which may compromise the whole VANET network. In this case, efficient security preservation and privacy protection mechanisms in VANETs need to be deployed.
Additionally, the geographical barriers may also obstruct the regular message delivery for stable V2V and V2R data sharing. The dynamic wireless ad hoc topologies constructed by the spontaneous high-speed vehicles lead to a temporary and indisciplined interaction paradigm, which brings challenges to real-time V2V communication. In this case, the VANET connectivities will be drastically impacted, resulting in insufficient availability and low scalability. With this motivation, the unmanned aerial vehicles, as the additional auxiliary facilities, can be applied to practical VANETs as the autonomous switching nodes for advancing the transmission quality and availability. Hence, proper security methods are of significance for the interactions among UAVs and vehicles.
3.8. Security Objectives
The objectives of our design are to enhance the security assurance of UAV-assisted VANETs wireless transmissions and to address the remote V2V communication for long-distance, remote vehicles. The following security requirements for VAENT key management and authentication scheme should be fully satisfied:
Anonymity: Messages originated from the same device carry unique patterns for verification of the receiver side. In the open wireless environment, by analyzing the eavesdropped information, vital parameters including the user location may be extracted, which endangers user privacy. Therefore, anonymity for all the participating vehicles during the whole VANET communications is extremely crucial.
Unforgeability: The adversary may selectively forge the valid certificates, keys, or signatures in wireless VANET transmission in order to pass the verification process and acquire crucial system secrets. Unforgeability is the key property of safe data sharing against the selected message attack.
Session Key Establishment: Upon validation, the shared session key between individual vehicles and the VANET system should be established so as to provide safe data exchange. Due to the semi-trustworthiness of intermediate RSUs, the constructed session key should be hidden from the interacting RSUs.
Conditional Privacy Preserving: As one of the essential privacy criteria, conditional privacy is mainly composed of user privacy protection, and device identity retrieving. On the one hand, private information regarding user identity should be preserved during the entire transmission process. Hence, the illegal tracing toward the specific device cannot be performed. On the other hand, the legal authority should be capable of revealing the real identity of the individual vehicle under specific situations. The compromised or corrupted vehicle can then be timely traced.
Non-repudiation: The message sender of VANET is unable to deny the authenticity of its signature on the messages transmitted. Non-repudiation guarantees that the information transmitted is valid.
Mutual Authentication: Mutual authentication is the fundamental but leading security property in the VANET architecture, ensuring that the participating two VANET entities of the same communication session authenticate each other.
4. Proposed UAV Association and V2V Dissemination Scheme
In this section, the UAV authenticated key management scheme is developed, followed by the remote V2V message dissemination design. The proposed UAV group association design applies the certificateless cryptography technique for key escrow avoidance, where the partial secret key set is respectively managed by VC and individual UAV device. The user anonymity for the participating UAVs is provided accordingly. The edge RSU structure is responsible for pairing-based computations, while complicated processing tasks for resource-constrained UAVs are exempted during the whole process. Upon verification, the dynamic UAV group key distribution mechanism is conducted subsequently. Notably, efficient batch UAV validation design is enabled. In the next, the remote V2V message dissemination is presented. The RSU-aided vehicle communication is conducted through the RSU clusters along the driving path, while the vehicle route retrieving is achieved in this way.
The proposed scheme regarding UAV association can be roughly classified into the UAV batch authentication and group key distribution. In the initial UAV batch authentication, the UAV device registration and the nontrivial mutual verification design are executed. Subsequently, the universal group key is constructed for the universal UAV networks, which is of benefit to connectivity improvement in VANET implementation with geographical obstructions. Afterward, the remote V2V message delivery is composed of remote vehicular verification and V2V message dissemination, where the RSU-aided identity route retrieving method with remote VC assistance is developed.
4.1. UAV Batch Authentication
Initially, the corresponding UAV registration prior to the verification process is conducted, which is explicitly performed on the VC side. In this case, VC is in charge of vital UAV parameter allocation and essential key distribution to the destined UAVs. Firstly, and are respectively defined as the cyclic groups with the same large prime order q, where denotes the generator of . Meanwhile, the map function is defined as the bilinear pairing. The cryptographic hash functions and are respectively defined as , , , , , , , , , . At this point, VC is able to generate the unique confidential secret set for each validated RSU, where denotes the identity, and denotes the RSU partial secret key randomly generated by VC. At this moment, the confidential RSU information set is safely shared among TA and each RSU itself.
Similarly, it is essential for each UAV to conduct the registration process in advance. The UAV identity
and the partial secret key
are then assigned by VC. Hence, the key pair for UAV is defined as
. With the purpose of user anonymity preservation, each registered RSU randomly generates
and computes its temporary session identity
as
, where the current timestamp
is adopted. In this case, each session identity
is valid within a certain time interval. The partial secret key pair is stored as
, while
is kept secret to VC. Meanwhile, the homomorphic encryption design is utilized. That is, each RSU computes
satisfying
, where
and
denote the prime values randomly selected by RSU itself. Hence, RSU chooses random
and computes
and
, where the function
. At this point, the RSU encryption key pair can be extracted as
. Subsequently, the following calculations are conducted by RSU
where
denotes the latest timestamp. At this point, the RSU parameters set
is published to all entities in its effective range. In the next, the UAV batch authentication process is described step by step. Assuming
n, UAVs with identity set
(
) are organized in the range of one RSU, and each UAV itself generates the partial secret key
on its own. At this moment, the partial secret key pair
is stored in UAV storage. Hence, the temporary identity used in the authentication session is computed as
. Meanwhile, all the UAVs are acknowledged of the published RSU parameters set
. By validating the certificate
, the integrity of the received message can be guaranteed. Thereafter, each UAV computes
and calculates the signature as
, which combines the published RSU parameters with vehicle partial secret keys
. The authentication requests
from
n vehicles are respectively delivered to RSU for further verification.
Upon receipt of the
n requesting messages, the RSU checks the freshness of the received timestamp
and verifies
according to its session identity
. Subsequently, RSU forwards
to the VC for final identification. As mentioned above, significant identity information
involving all the legitimate UAVs is stored in VC. Therefore, VC adopts the delivered
and
to the records and computes the UAV identity with the received one. If it matches, the identity of the UAV is confirmed. Hence, VC extracts the partial secret
and computes
and
, which will be forwarded to the RSU with session identity
. At this moment, the confidential information set
for
n UAVs are acquired by local RSU. Hence, RSU executes the following batch authentication calculation for
n UAVs as
The correctness of Equation (
3) can be briefly elaborated as follows:
The batch authentication process involving n UAVs is performed in this way. Therefore, if the request message does not pass the validation process, the current authentication session is terminated. Otherwise, for the n UAVs, RSU computes and and distributes the acknowledgment message , where denotes the latest timestamp.
Upon receiving the acknowledgement message, UAV first checks the freshness of and then validates the correctness of and according to . Note that the current UAV identity is now updated as to provide message unlinkability. At this point, mutual authentication among UAVs and RSU is provided, which adopts the certificateless cryptographic technique for key escrow avoidance. The partial secret keys of individual UAV are respectively generated by VC and UAV itself. Moreover, bilinear pairing is utilized, while the complicated pairing calculations are exempted in UAV sides. In our design, the shared session key for the individual UAV is independently constructed as , which can be used for the following UAV group key distribution process.
4.2. Group Key Distribution
The group key involving all the n validated UAVs is distributed in each RSU domain so that the substantial UAV networks can be built. Initially, for , RSU computes and satisfying for . In the next, RSU chooses the distinctive UAV group key and extracts the keying value as . At this point, the keying function can be constructed in the form of , which can be further transformed into . Notably, the corresponding coefficients set is extracted. Therefore, , holds. Hence, the following computation is conducted as , where denotes the secure hash function. Accordingly, RSU broadcasts the keying packet as . Finally, all the n UAVs receive the keying packet and reconstruct the function so that the group key can be correctly derived as . In this way, the UAV group key is shared among all requesting n UAVs.
4.3. Remote Vehicular Verification
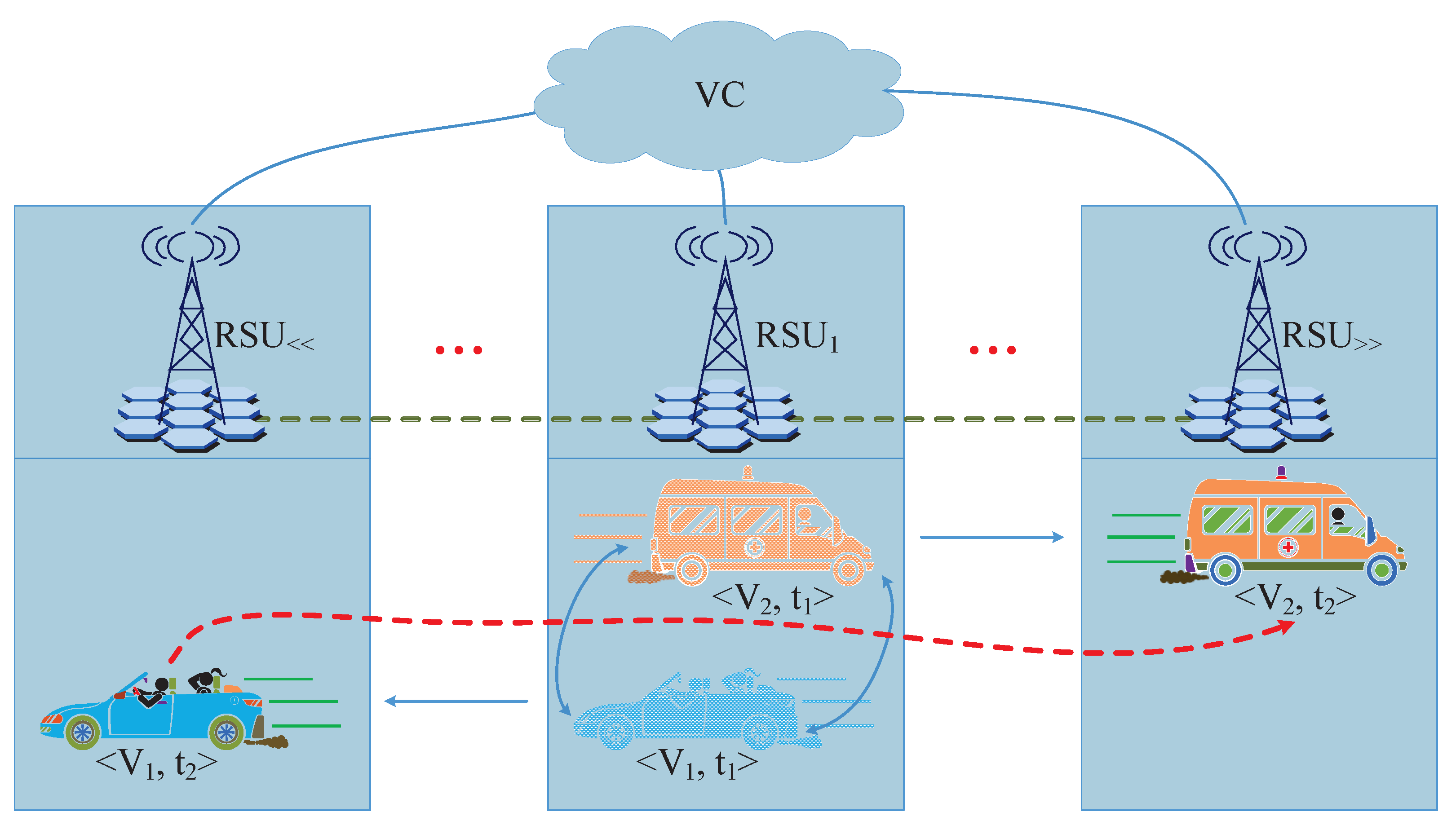
In this section, the V2V communication assumptions are presented at first. As shown in
Figure 2, assuming at timepoint
, the vehicles
and
are in the range of original
, the instant V2V interactions between
and
can be achieved through multiple existing schemes so far [
19,
22,
29]. At the current time
(
), both
and
are now arriving at different RSU domains. At this moment, the
vehicular connection is required in the case for the subsequent message dissemination, which has not been properly addressed in the existing VANET schemes. Therefore, the remote vehicular verification is introduced in this section, followed by the remote V2V message dissemination in the next section.
Initially, assuming the vehicle with original identity
and that the partial secret key pair
is approaching the communicating range of specific RSU, its temporary identity can be updated as
. Meanwhile, the vehicle extracts the encryption key pair
from the published
. Following the same way as that of the RSU, the vehicle homomorphic encryption design with encryption key pair
and decryption key pair
is constructed. Therefore, the vehicle calculates
, with
and sends the requesting packet
to RSU for further verification.
Upon receipt of the packet, RSU decrypts the received using the the decryption key and then extracts . If the values of and are validated, RSU stores the vehicle homomorphic encryption key pair . Moreover, the value can be calculated as . At this point, RSU uploads to VC for remote identification. Thereafter, VC computes and replies to RSU with the acknowledgment . Subsequently, RSU updates the vehicle identity as , where the RSU key pair is adopted. Note that, in our design, anonymous identity of the participating vehicle is safely updated as soon as a verification session is finished successfully. In this case, the message unlinkability for different communication sessions can be guaranteed. Untraceability of specific vehicle is provided as well.
With the aforementioned vehicle key pair and its own , RSU conducts the vehicle homomorphic encryption process and computes and . Hence, RSU is able to broadcast the packet to the destined vehicle. Upon validation on the timestamp , the vehicle is able to decrypt the received and successfully extract . Notably, of the delivered packet is for integrity validation. Therefore, the vehicle extracts the final verification process as . At this point, the vehicle validation with the original RSU is completed. The session key established between VC and vehicle is generated as , which can be used as the unique identifier between vehicle and VC. Meanwhile, the unique proof for each validated vehicle is issued as , where () is the newly generated pseudorandom for remote vehicle verification. Moreover, the relevant certificate is computed as . In this case, the original RSU will deliver the packet to all its neighboring RSUs via the edge networks. Upon receiving the packet, all its neighboring RSUs temporarily store it in their storage for possible further use. If not required in a certain time interval , the packet will be abandoned.
In our assumption, the vehicle is on the path of
. Hence, in the domain of
with RSU parameter set
, the vehicle randomly generates
and computes
Subsequently, the vehicle conducts the RSU encryption using the broadcast key
of
as
which will be delivered to
for fast verification.
Upon receiving
,
is able to decrypt it and extract
. Notably,
has already received
from the original
. Therefore, the validation
could be executed. The correctness can be elaborated as
At this point, the current identity and the previous received should be updated as and . In this case, computes the certificate information for final authentication on the vehicle side, which is encrypted with vehicle homomorphic encryption key pair and the generated pseudorandom as , where is the current timestamp for authentication. The packet is then sent to the vehicle for mutual verification. Upon receiving , the vehicle derives to confirm the identity of .
4.4. V2V Message Dissemination
In the assumption, in further time
of the
n cross-domain verification sessions,
will be broadcast by
, where
Intuitively, the anonymous identity for each vehicle is updated in each session. The is also updated based on the previously validated proofs and the keys from the current . As mentioned above, each RSU around the path safely preserves the identities, valid proofs, and the corresponding timestamps for all the passing-by legitimate vehicles. The remote long-distance V2V message dissemination method can be constructed accordingly.
Assuming a vehicle intends to conduct remote vehicular data exchange with the vehicle at time , is in the range of , is in the range of . Notably, both and crossed the original previously and conducted V2V communication at (). In this case, assuming the vehicle is with original identity and the partial secret key pair , the two historical temporary identities in the range of are and . The vehicle is able to retrieve the from its historical transmission record. In this case, the current broadcast to all. In the meantime, the current identity of vehicle is . The vehicle generates the packet to be delivered as , where . Respectively, and denote the current timestamp generated on vehicle , and the previous timestamp associated with time . refers to the temporary identity previous used by the destined vehicle at . The identifier is adopted for distinction on . refers to the confidential data intended to be sent.
The current then decrypts the packet and derives after validation on and . Notably, the vehicle has already passed the cross-domain validation process conducted by . Therefore, the corresponding identity acquired from is also stored in side. The packet is then forwarded to the previous RSUs following the sequence of . Each RSU in the sequence holds the record of vehicle on (). The remote V2V packet can then be delivered to the original . Subsequently, extracts the record of and continues broadcasting the packet to neighboring RSUs. Each RSU holds the record of vehicle on (). Finally, the message can be delivered to by . The remote V2V message dissemination process is completed.