Abstract
IEEE 1609/802.11p standard obligates each vehicle to broadcast a periodic basic safety message (BSM). The BSM message comprises a positional and kinematic information of a transmitting vehicle. It also contains emergency information that is to be delivered to all the target receivers. In broadcast communication, however, existing carrier sense multiple access (CSMA) medium access control (MAC) protocol cannot guarantee a high reliability as it suffers from two chronic problems, namely, access collision and hidden terminal interference. To resolve these problems of CSMA MAC, we propose a novel enhancement algorithm called a neighbor association-based MAC (NA-MAC) protocol. NA-MAC utilizes a time division multiple access (TDMA) to distribute channel resource into short time-intervals called slots. Each slot is further divided into three parts to conduct channel sensing, slot acquisition, and data transmission. To avoid a duplicate slot allocation among multiple vehicles, NA-MAC introduces a three-way handshake process during slot acquisition. Our simulation results revealed that NA-MAC improved packet reception ratio (PRR) by 19% and successful transmission by 30% over the reference protocols. In addition, NA-MAC reduced the packet collisions by a factor of 4. Using the real on-board units (OBUs), we conducted an experiment where our protocol outperformed in terms of PRR and average transmission interval by 82% and 49%, respectively.
1. Introduction
Vehicular communication, often referred to as V2X, is among the main pillars for the imminent era of intelligent transportation systems (e.g., autonomous vehicles). Among many other benefits, V2X can reduce traffic congestion and facilitate transportation by exchanging real-time data between the vehicles. Several standard protocols [1,2] have been developed to realize data communication among the vehicles. Most of these protocols allow the vehicles to transmit broadcast and unicast messages through predefined control and service channels [3]. A direct communication between the vehicles is called vehicle-to-vehicle (V2V) communication [1] and is considered to be a key technology that can significantly improve the road safety. Therefore, many researchers are continuously proposing new approaches to enhance the performance of vehicular network.
Motivated by the importance of vehicular communication, the Federal Communication Commission (FCC) has allocated 75 MHz radio spectrum in 5.9 GHz band for dedicated short-range communication (DSRC) [3,4]. DSRC spectrum is exclusively used by V2X communications. This spectrum is further divided into seven orthogonal channels, each of which represents the 10 MHz bandwidth. One of these channels is called a control channel (CCH), which is dedicated to broadcast safety messages. The remaining channels are used for the service data communication. The broadcast messages usually represent shorter size and higher priority. The basic safety message (BSM) [5] is also a broadcast message that is periodically sent by each vehicle over the shared channel to announce the recent dynamic updates [5].
In vehicular network, infrastructure-based communication may not always be available since wide installation of roadside units (RSUs) can be very costly [6,7,8,9]. To identify recent updates in the network, therefore, each vehicle relies on the BSM packets received from one-hop neighbors. To enhance a reception ratio of broadcast messages, medium access control (MAC) protocol must guarantee a robust and interference-free broadcast communication. It must decrease a packet collision event—multiple vehicles transmit their packets at the same time and cause an interference in common receivers. To ensure a reliable broadcast, MAC protocol should also provide acknowledging mechanism, which allows the transmitter to verify whether its broadcast packet is successfully received by all target receivers.
The existing MAC protocol of IEEE 802.11p [10,11] employs an enhanced distributed channel access (EDCA) scheme that differentiates data of the vehicles into various access categories (ACs). Each AC is assigned a different contention window (CW) of well-known carrier sense multiple access (CSMA) algorithm. If vehicle has data with higher AC, then it obtains a smaller CW and shorter arbitrary inter-frame space (AIFS). To avoid potential collision, a transmitter first listens to the channel. Once the channel remains idle until the end of AIFS, the transmitter starts CSMA back-off. If the channel continues being idle until the end of back-off timer, the transmitter sends its data. If transmitter detects a busy channel condition or the event of collision, it restarts its back-off operation with a greater CW. EDCA, however, cannot use a variable CW for broadcast packet transmission, since IEEE 802.11p standard is unable to provide collision detection scheme for broadcast transmission. Hence, EDCA uses the smallest CW for all broadcasts to reduce a channel access and transmission delay. This may increase the probability of collisions, especially when the number of contending vehicles are increased.
To detect an ongoing transmission over the channel, vehicles rely on a fixed channel sensing range. If any vehicle outside of this range executes transmission, it remains undetected and causes interference in common receivers. This interference is often called a hidden terminal interference or collision [11,12,13,14,15].
Figure 1 demonstrates a simple example for the hidden terminal interference. Suppose , , and represent three different vehicles that transmit their packets at the same time. Since these vehicles are separated by long inter-vehicle distances, they cannot detect each other’s transmission. Due to the hidden terminal interference, common receivers (vehicles located in high signal interference area) cannot decode the received packets.
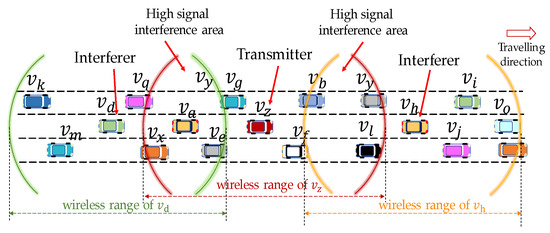
Figure 1.
Hidden terminal collision scenario.
The hidden terminal problem can be eliminated with help of V2I connection, since RSU is capable of covering a large area with a greater number of nodes. While scheduling the channel resources, RSU considers the hidden terminal collision. It avoids allocating the same channel resources to multiple interfering vehicles. The authors of [15] introduced a novel MAC protocol that provides time division multiple access (TDMA)-based broadcasting for safety messages with a coordination of RSUs. The RSU defines the transmission orders in the coverage areas to mitigate collision events and reduce the delay in transmission. Since vehicles are travelling fast, they may quickly go beyond the coverage of RSUs. Then, vehicles start using the standard CSMA-based MAC protocol, again suffering from the hidden node interference. Therefore, the proposed method mainly focuses on broadcast V2V communication and it can also easily be extended to V2I communication scenarios.
2. Related Work
Many alternative MAC protocols have been proposed to improve the performance of standard MAC protocol [16,17,18,19,20,21,22,23,24,25,26,27,28]. The authors of [16] proposed a multichannel TDMA MAC protocol called VeMAC. This protocol improves reliability of broadcast communication by sharing one-hop slot allocation table. In this way, VeMAC reduces duplicate slot allocation in two-hop communication range. However, VeMAC also suffers from the following critical limitations: access collision still may occur since two vehicles can access the channel choosing the same slot; it reduces the hidden terminal collision events at the cost of large protocol overhead; since vehicles travel at a random speed, VeMAC loses the performance due to a merging collision (vehicles using the same slot approach to one another).
In References [17,18,19], the authors proposed the so-called HER-MAC protocol, which partitions the transmission interval into two periods: (1) reservation period (TDMA time slot-based data transmission period) and (2) contention period (CSMA random back-off-based slot reservation period). HER-MAC allows vehicles to transmit their broadcast packet in reservation period using time slots to improve the reliability. In order to reserve a non-interfering time slot, vehicle broadcasts slot-reservation packet in contention period. Since CSMA already suffers from hidden terminal interference, vehicles may face collision problem in contention period. Moreover, in HER-MAC, each vehicle shares its one-hop slot allocation table to obtain two-hop range slot reservation status. Thus, this method also generates a big overhead, like VeMAC.
The authors of [20,21] introduce a self-organized TDMA (STDMA) MAC protocol that was actually created to support communication between the vessels. This technique, however, demonstrates a poor performance in high vehicle density. It does not provide additional techniques to detect duplicate slots, and thus it performs low packet reception ratio for high density.
Another promising algorithm is presented in [22], where the authors introduced hybrid cooperative MAC (HCMAC), which supports the concept of VeMAC by solving its critical limitations. The HCMAC combines a channelization feature of TDMA with random-access mechanism of CSMA to create a hybrid MAC. As a result, HCMAC reduces the access collision cases. To detect the collision, HCMAC uses an error list that contains the details of duplicate slots and then attaches this list to the periodic broadcast packets. This means that HCMAC also generates a large protocol overhead to maintain the reliable broadcast in distributed vehicular network.
An interesting study was conducted in [23] in order to enhance the reliability of one-hop broadcast (beacon) packet transmission. The authors of [23] divided OFDM channels of DSRC band into subframes and subchannels, wherein the smallest radio resource is called basic resource unit (resource in time and frequency domain). To allocate the basic resource units, the authors proposed two allocation protocols: centralized and distributed resource allocation MAC protocols. In terms of their centralized MAC protocol, each vehicle’s channel access procedure is coordinated with its neighbors to solve the hidden terminal problems. To ensure the rustiness in broadcast communication, the authors used commonly shared preambles (the part of basic resource unit) to support distributed resource reservation and to detect and solve the collision. Once a vehicle acquires its resource, it uses this slot persistently until it detects the collision.
In Reference [24], authors studied the problem of transmitting the broadcast messages without an infrastructure support. The main target was to minimize a total number of retransmitted packets under various mobility conditions. This protocol supports non-safety and delay tolerant applications. Using this protocol, a vehicle does not instantly retransmit a broadcast packet received from the original source. Instead, it waits and verifies whether this broadcast packet has already been retransmitted by other receivers. The authors of this protocol tried to increase a coverage of all broadcast packets in the predefined target area. The authors also encouraged the vehicles to send the acknowledgement as a feedback for received broadcast message. Therefore, in high vehicle density scenarios, this method generates high volume of protocol overhead, which results in the degradation of channel utilization. In addition, long broadcast packets often experience collision and increase cases of redundant retransmissions.
A time slot sharing MAC protocol proposed in [25] provides a distributed periodic broadcast message transmission with variable beaconing rate. In this scheme, time slots are shared amongst the different vehicles as each vehicle periodically updates the state of slot allocation. According to this state-of-the-art protocol, each vehicle selects its time slot on the basis of broadcast frame information received from neighboring vehicles. In high vehicle density scenario, however, multiple new vehicles within the same communication range may access the channel simultaneously by experiencing the access collision problem. Therefore, the broadcast frames exchanged among the vehicle may not completely eliminate the hidden terminal collision problem. Due to this reason, the scheme proposed in [25] may not provide a reliability broadcast communication in high-density scenarios.
A mobility-aware MAC (MoMAC) protocol proposed in [26] divides transmission interval into different segments according to the number of lanes on the road, directions, and intersections. Each vehicle collects slot allocation information within its channel sensing range and attaches this information to the header of its periodic broadcast packets. Due to this attached control information, the header of broadcast packets becomes very large, and thus this method may not be efficient in terms of channel utilization. Moreover, a long packet tends to have high bit error rate according to the research conducted in [27]. The authors of [28] proposed a scalable and cooperative MAC (SCMAC) protocol, which divides the inter-packet interval into multiple slots and uses cooperative beaconing technique to propagate the future state of the control channel. It also adaptively adjusts the inter-packet interval over CCH on the basis of the vehicle density. However, the authors of this method did not consider the hidden terminal interference problem, and thus the performance of this method may be exacerbated in high vehicle density scenarios.
In this paper, we propose a novel protocol called neighbor association-based MAC (NA-MAC), which supports a hybrid of TDMA and CSMA MAC configuration like HCMAC. To further improve the reliability, NA-MAC introduces a new three-way handshake process with neighbor vehicles called associated neighbors (ANs) during its slot acquisition procedure. It extends the concept of request-to-send/clear-to-send (RTS/CTS) for unicast of CSMA to support broadcast communication in vehicular network [29]. To acquire the slot, transmitting vehicle broadcasts request-to-broadcast (RTB) message in predefined phase of selected slot. When the ANs of transmitting vehicle receive RTB, they broadcast clear-to-broadcast (CTB) messages indicating that the current slot is free. In NA-MAC, each vehicle does not need to share one-hop slot allocation table, and thus it significantly reduces the protocol overhead. In summary, our contributions are as follows:
- For the first time, in order to avoid a duplicate slot allocation, NA-MAC applies a three-way handshake process in broadcast communication.
- NA-MAC minimizes access and hidden terminal collision events.
- NA-MAC minimizes protocol overhead and guarantees high reliability.
- NA-MAC is implemented in the real commercial V2X devices.
The remainder of this paper is organized as follows. Section 3 specifies the network model while Section 4 introduces NA-MAC protocol. Section 5 defines simulation environment and simulation results. Section 6 presents the experiment scenario with real hardware devices and discusses the experiment results, while Section 7 ends this paper with a brief conclusion.
3. Network Model
In this paper, we consider IEEE 1609/802.11p standard over DSRC channel as a link layer protocol. In our system model, each vehicle periodically transmits a broadcast safety message in every predefined transmission interval over the shared channel. Our method employs a channelization concept of TDMA to partition the transmission interval into frames, each of which is divided into slots, as shown in Figure 2. Each slot should be allocated to only one vehicle within the two-hop communication distance.
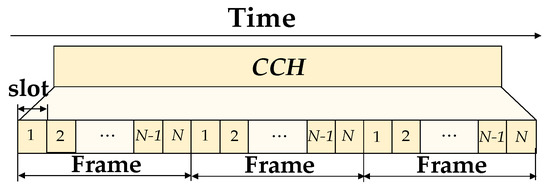
Figure 2.
Time division multiple access (TDMA) frame structure of the proposed protocol.
As described earlier, NA-MAC allows each vehicle to execute CSMA back-off operation before accessing the channel in the selected slot. According to CSMA concept, each vehicle listens to the channel until the end of a random back-off interval. If a vehicle selects the shortest back-off interval of all the other vehicles, then it gains the earliest access to the shared channel. In the unicast communication, the CSMA/CA scheme utilizes a collision avoidance operation by exchanging RTS and CTS messages between source and destination stations, as shown in Figure 3a. When the destination receives an RTS packet from the source, it responds with a CTS packet, indicating that the channel is clear for source node to use. When other nodes in the same two-hop range hear RTS and CTS packets, they defer their transmission to allow the current transmitter to use the channel. The exchange of RTS/CTS messages may only eliminate hidden terminal collision in unicast communication. Before our work, there has been no similar enhancement proposed to ensure collision avoidance in broadcast communication.
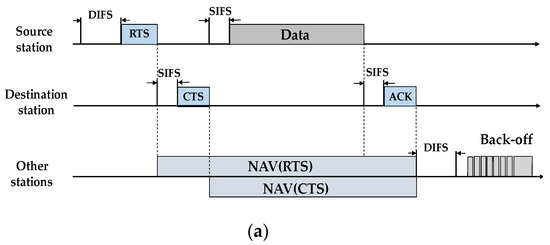
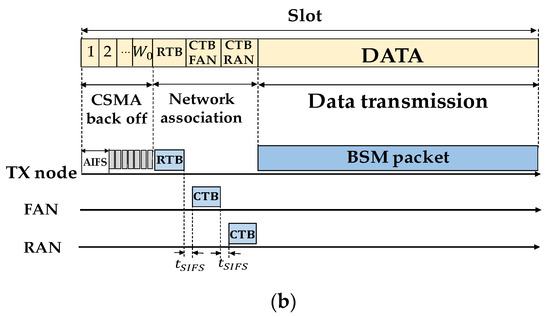
Figure 3.
(a) IEEE 802.11′s collision avoidance scheme in unicast scenario using request-to-send/clear-to-send (RTS/CTS)/data/acknowledgement (ACK); (b) proposed collision avoidance scheme in broadcast scenario using three phases in each TDMA slot.
NA-MAC allows each vehicle to select a random slot out of slots, as shown in Figure 2. Within the selected slot, each transmitter first listens to the channel for a random CSMA back-off period. If the channel is idle, the transmitter sends a packet in the current slot. Otherwise, the transmitter selects another slot.
Each vehicle is equipped with an on-board unit (OBU). The OBU includes a global positioning system (GPS) receiver that provides an accurate time synchronization signal, satisfying the synchronization requirement of TDMA time slot [30]. For simplicity, we assume that all nodes use fixed transmission power, which provides wireless range of meters, and that the carrier sense range is the same as the wireless range. We briefly describe all notations used in this paper in Table 1. In this paper, we consider V2X networks on multilane highway, while NA-MAC also can be applied to city networks with complex intersections. For simplicity, we consider only V2V communication, while NA-MAC can also be easily applied to the networks with both V2V and V2I. We also assume that the communication channel is ideal, and thus transmission failures occur only due to collisions. The communication links are assumed to be symmetric. In other words, if node A can receive a data of node B, node B can also receive a data of node A.

Table 1.
Brief description of notations.
4. NA-MAC Protocol
This section introduces the proposed protocol NA-MAC. We first describe the TDMA frame structure of NA-MAC, followed by the definition of RTB/CTB packet formats. Second, we explain selection of ANs followed by the slot acquisition procedure in NA-MAC. Third, we explain a collision detection and acknowledgment procedure.
4.1. TDMA Frame Structure
We define the set of time slots as . As shown in Figure 3b, each slot has three phases: (1) CSMA back-off phase, ; (2) network association phase, ; and (3) data transmission phase, .
Each vehicle listens to the channel for one TDMA frame to identify a set of free slots defined as , where . contains the slots that are not occupied by any vehicle in distance (double the wireless range) from . Then, the transmitter verifies whether the selected slot is indeed free by the following steps. First, during the back-off phase of selected slot, the transmitter picks a random back-off counter and calculates its back-off timer. Second, if the channel remains free until the end of back-off timer, the transmitter starts the association process in which it exchanges RTB and CTB control packets with selected ANs. Third, once RTB/CTB packets are successfully exchanged, the transmitter broadcasts its packet.
4.2. RTB and CTB Packets
During the association phase of , the transmitter exchanges control packets with associated front and rear neighbors (as illustrated in Figure 4, where selected as front AN and as rear AN) to verify the state of selected slot. The transmitter sends a control RTB packet and receives an acknowledging CTB packet from selected front and rear ANs, as shown in Figure 4. Once RTB and CTB packets are successfully exchanged, the transmitter acquires this slot and starts sending its BSM packet during data transmission phase of .
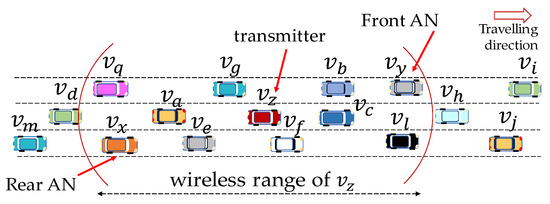
Figure 4.
A selection of associative front and rear neighbors.
The acquired slot is used by the transmitter for a time period defined by . is a slot reselection period that is represented in terms of number of frames. is randomly selected in the range of (in simulation, we set and ).
Figure 5a presents the RTB message format, which consists of 9 bytes. RTB packet is transmitted as a broadcast message. RTB consists of the following data fields:
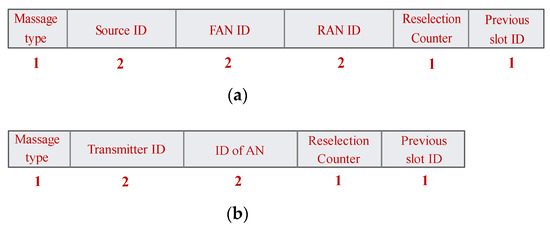
Figure 5.
Format of (a) request-to-broadcast (RTB) and (b) clear-to-broadcast (CTB) messages.
- Message type (MT) (1 byte) assists in specifying the type of broadcast message;
- Transmitter ID (TID) (2 bytes) represents pseudo-ID of transmitting vehicle;
- Pseudo-ID of front AN (PIF) (2 bytes) specifies the pseudo-ID of AN located in the front;
- Pseudo-ID of rear AN (PIR) (2 bytes) defines the pseudo-ID of AN located in the rear;
- Reselection counter (RC) (1 byte) is a counter decrement to reinitiate slot acquisition;
- Previous slot index (PSI) (1 byte) stores an index of slot previously used by the transmitter.
Figure 5b shows the format of broadcast CTB packet that consists of 7 bytes. Most fields of CTB message are the same as the abovementioned fields of RTB. The only difference is pseudo-ID of AN, which represents the identity of either front or rear AN. Thus, each transmitter should receive two CTB packets (one from front AN and one from rear AN) for its transmitted RTB packet. As shown in Figure 5, the proposed RTB and CTB packets are much shorter than the standard RTS and CTS packets defined in IEEE 802.11. Hence, NA-MAC incurs negligible overhead during the slot acquisition procedure, which is explained in Section 4.4.
4.3. Selection of Associative Neighbors
Each vehicle conducts a background operation to identify one-hop neighbors from received beacons. Then, from one-hop neighbors, it selects two ANs—one AN is selected from front one-hop neighbors and another one is from rear one-hop neighbors. For all one-hop neighbors , a transmitter selects a if it best satisfies the following associative neighbor selection conditions:
- (a)
- neighbor should be in the farthest distance from ;
- (b)
- neighbor should travel at a speed the closest to ’s speed;
- (c)
- neighbor should have fewer association links with other vehicles (except ).
Condition (a) ensures that the selected AN propagates slot reservation information of transmitter as far a distance as possible in two-hop range. Condition (b) allows the transmitter to keep connecting with selected AN for as long as possible and to avoid frequent reselection of AN. Condition (c) allows NA-MAC to fairly distribute an association overhead among vehicles. In NA-MAC, each vehicle attaches a special counter to its periodic broadcast packet to indicate the number of vehicles it is associated with. By monitoring this counter, associative neighbor selection algorithm can avoid choosing ANs that are associated with too many transmitters. In highway scenario (this paper considers mostly highway scenario), each transmitter selects two ANs, a front AN (FAN) and a rear AN (RAN). A FAN is selected amongst one-hop leading neighbors; a RAN is selected amongst one-hop lagging neighbors. In Figure 4, transmitter selected neighbors and as FAN and RAN, respectively. During slot acquisition procedure described below, exchanged RTB and CTB messages with its RAN and FAN .
Every time a transmitter changes its slot, it also may reselect its FAN and RAN. However, if current AN still best satisfies all three conditions, transmitter may keep current AN instead of selecting new ANs.
4.4. Slot Acquisition Using Association
Algorithm 1 describes the basic steps of slot acquisition procedure in NA-MAC. Let be the vehicle that runs this algorithm to acquire a new slot. Let us further assume that chooses and as FAN and RAN, respectively, as shown in Figure 6a. In step 2 of Algorithm 1, checks whether it has already acquired its own slot (acquired slot). If has not acquired its slot yet or its reselection counter has decremented to zero, selects a random from a set of free slots defined as and a new from . Otherwise, keeps using its selected slot. Suppose that has not yet acquired its slot, it thus runs step 3 to select a random from . Once is reached, conducts the three phases illustrated in Figure 3b.
| Algorithm 1 Slot acquisition procedure in NAMAC | |
| Input: A set of free slots | |
| Output: Slot and slot reselection counter | |
| 1 | loop |
| 2 | if slot is not acquired or then //acquire a new slot |
| 3 | Select random from and from [] |
| 4 | else //slot has been acquired |
| 5 | Continue using the previous |
| 6 | endif |
| 7 | while current slot is not do |
| 8 | Execute Rx operation //receive neighbors’ packet |
| 9 | Move to next slot |
| 10 | end while |
| 11 | //[Phase 1] CSMA back-off phase |
| 12 | Run CSMA and determine //select random back-off time |
| 13 | while is not expired do //start CSMA back-off process |
| 14 | if RTB/CTB message is received then |
| 15 | Suspend and go to step 3 //select a new slot |
| 16 | Endif |
| 17 | Decrement |
| 18 | end while //end the back-off process |
| 19 | //[Phase 2] association phase |
| 20 | Broadcast RTB message |
| 21 | while is not expired do // is the association period |
| 22 | Execute Rx operation //receive CTB packets |
| 23 | Decrement |
| 24 | end while |
| 25 | if any CTB message from AN is not received then |
| 26 | Suspend and go to step 3 //pick new slot from |
| 27 | endif |
| 28 | //[Phase 3] data transmission phase |
| 29 | Send BSM packet |
| 30 | Decrement |
| 31 | end loop |
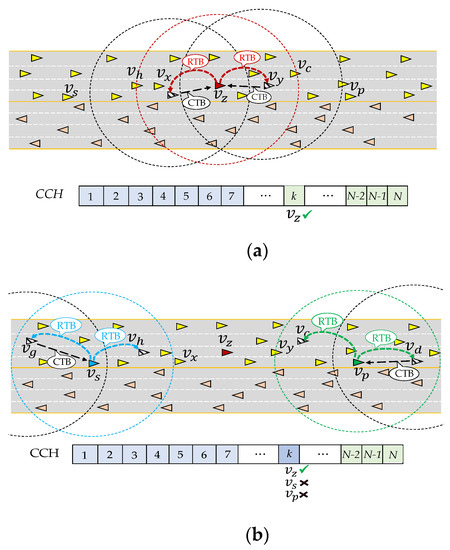
Figure 6.
Slot acquisition procedure: (a) success scenario; (b) failure scenario.
[Phase 1] starts back-off phase by determining a random back-off timer denoted as (in step 12). During , if receives RTB or CTB message (or any signal power greater than the predefined threshold) from another vehicle, concludes that this slot is occupied and aborts the back-off operation. Then, it reruns step 3 to acquire another random slot from .
[Phase 2] If the channel remains idle until the end of , enters the association phase with a conclusion that no vehicle occupies in one-hop communication distance (one-hop range), and broadcasts its RTB message as indicated in step 20 of Algorithm 1. Then, waits for CTB packet from and . If the expected CTB packet is not received either from or from , then concludes that has been occupied by another vehicle in two-hop range. Thus, re-executes step 3 to select another slot from . If successfully receives CTB packet from both and , then concludes that no vehicle occupies in two-hop range and it launches the next phase.
[Phase 3] Once identifies that is free in two-hop distance, it sends its BSM packet in without causing any interference to other neighbors. After every successful transmission, decrements its (as shown in step 30).
To further improve the reliability, runs all operations described in the above three phases before broadcasting its BSM in acquired . Figure 6a shows an example of successful acquisition of by . Once RTB and CTB packets are exchanged, all vehicles in two-hop distance from mark as a busy slot at least during frames. Figure 6b illustrates the effect of ’s RTB/CTB exchange on other neighbors outside of ’s wireless range. For example, let us consider the scenario where ’s three-hop neighbors and try to acquire the same . Here, is on the front side of , while is on the rear side. To acquire their slots, and also transmit their RTB messages in . Suppose that selected as FAN and as RAN, while selected as FAN and as RAN. As we can observe from Figure 6a, (FAN of ) and (BAN of ) would have already received CTB packets from and , respectively. Therefore, and would ignore the RTB packets of and , respectively. Hence, and would not receive expected CTB packets in an association phase of , and thus they would consider as an occupied slot.
In this way, each vehicle acquires its slot and persistently uses it during frames. Once for selected slot decrements to zero, the vehicle picks another slot from in order to allow fair opportunity to other vehicles. To guarantee a reliable broadcast communication, the proposed NA-MAC protocol uses three-way handshake operation where transmitter exchanges RTB and CTB messages with its ANs. Although this three-way handshake operation consumes additional time within the allocated slot, it does not affect transmission delay performance since all of these operations are executed within the same acquired slot.
4.5. Collision Detection through Implicit Acknowledgement
In NA-MAC, each vehicle receives acknowledgement (ACK) for its every transmitted BSM packet. The ACK is attached to BSM packets sent from ANs in a piggy-back fashion. Each vehicle checks ACK in the BSM packet received from its AN. The ACK comprises four bytes: 1 byte for slot ID; 2 bytes for vehicle’s pseudo-ID (slot owner), and 1 byte for RC. Figure 7 shows an example where an acknowledging process is carried out between and its ANs, and . Let us assume that is acquired by . Then, all neighbors located in in two-hop () distance from would record ’s occupied in their slot allocation table as shown in Figure 7. In Figure 7a, sends its BSM in , and then expects to receive ACKs from in and from in . knows that and are occupied by and , respectively. If receives ACKs successfully from both ANs, then concludes that ’s BSM packet has been correctly received by all one-hop neighbors. In Figure 7b, sends ACK to in , which indicates that BSM packet of has been received by all one-hop front neighbors. In Figure 7c, receives ACK from in , indicating that BSM packet of has been correctly delivered to one-hop rear neighbors.
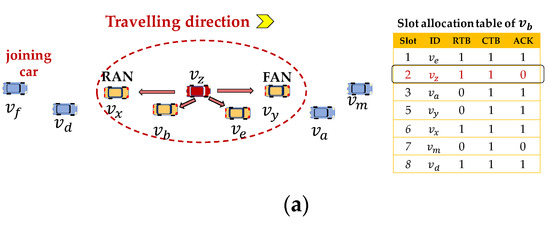
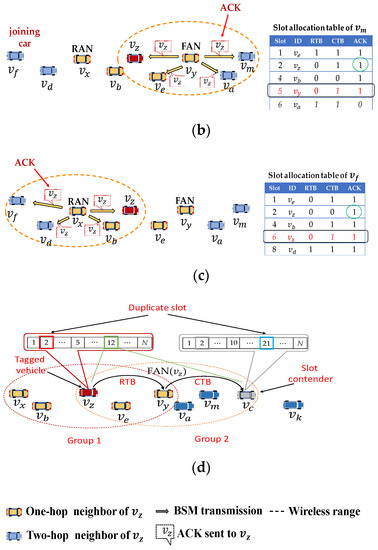
Figure 7.
Implicit acknowledging in neighbor association-based medium access control (NA-MAC): (a) is sending a broadcast packet in ; (b) is sending ACK to in ; (c) is sending ACK to in ; (d) acquires new slot after detection of collision.
If does not receive ACK from any AN, then concludes that one of two-hop neighbors is also using . Let us define this neighbor as a “slot contender”. Then, selects a new slot defined as from . While is waiting for , if it receives CTB packet, checks whether PSI field of the received CTB contains . If so, concludes that the slot contender has changed its slot and thus keeps using . If does not receive a CTB message with PSI field indicating , then runs line 7–29 of Algorithm 1 to acquire . While acquiring , sends RTB packet containing index of in PSI field to ANs (e.g., and ). Then, this PSI field (index of ) is further propagated to the second hop inside CTB packets of and . In case the slot contender of , in the second hop receives such CTB packet, it concludes that has acquired a new slot. Then, the slot contender keeps .
Figure 7d shows a scenario where two groups of vehicles, group 1 and group 2, are merging. Suppose that does not receive ACK from its FAN in due to a slot contender in the second hop. For simplicity, Figure 7d illustrates only a FAN of assuming that has successfully received ACK from RAN. Then, concludes that there is a slot contender among two-hop neighbors located in front. Then, selects a new (free) slot . Similarly, suppose that also discovers that its BSM has not been received by its lagging neighbors in , and thus it picks free . Since has selected earlier slot than , runs its slot acquisition operation earlier in . Then, propagates its previous slot () information to in PSI field of CTB packet transmitted by . Once receives CTB packet from , discovers that , a slot contender, has changed its to . Therefore, aborts its slot acquisition procedure scheduled in and sticks with . In this way, NA-MAC ensures only one of slot contenders change its slot when there is a collision occurs due to merging vehicles. In this way, NA-MAC avoids wasting slots and ensures all slots maximally utilized.
Figure 7 also shows slot allocation tables where three binary parameters (RTB, CTB, and ACK) are defined for individual slots. These parameters specify the reservation status of each slot in two-hop distance. For example, in Figure 7b, vehicle knows that is reserved by , since receives CTB and ACK from . This acknowledging method also helps joining vehicles to identify busy slots. In Figure 7b, let be a joining vehicle. As approaches to and , it starts receiving their BSMs (including ACKs). Thus, can identify a set of slots taken by , , and .
5. Evaluation with Simulation
5.1. Simulation Setup
To evaluate the performance of our protocol, we implemented the proposed protocol using a network simulator NS3 (V.3.24) with “highway” mobility scenarios. The length of the highway is 5 km. More information about simulation parameters is given in Table 2.

Table 2.
Simulation parameters.
Performance Metrics
- Packet reception ratio: For each broadcasted packet, reception ratio is calculated by X/Y, where Y represents the total number of expected receivers while X is the number of actual receivers in the wireless range of a transmitter.
- Average number of successfully transmitted packets (in one-hop neighborhood) per frame.
- The number of collision events represents the average number of collision events per frame.
- Average transmission interval is average time period between consecutive packets received from each neighbor.
- Average per-packet overhead is the control overhead transmitted by each vehicle under various protocols.
5.2. Simulation Result
Figure 8 demonstrates the simulation results obtained using the above test scenario. Figure 8a shows packet reception ratios (PRRs) for various network densities. As is observable, PRR decreased as the vehicle density increased. For the case of VeMAC and HCMAC, there was a high probability that vehicles often selected the duplicate slots in high vehicle density. Therefore, more collision and interference tended to occur as the vehicle density increased, causing loss of PRR. In contrast, using three-way handshake operation, NA-MAC quickly identified duplicate slots and effectively eliminated imminent collisions, providing much higher PRR than VeMAC and HCMAC. VeMAC suffered from frequent access collisions and merging collisions, leading to sharp PRR loss for growing density. HCMAC let vehicles sense the availability of channel before sending BSM in the selected slot, which improved PRR over VeMAC. However, HCMAC attached large overhead (one-hop slot-allocation and error lists) to each BSM packet, which increased the bit error rate probability and reduced PRR. Overall, NA-MAC improved PRR by 19% and 7% over VeMAC and HCMAC, respectively, for the density of 300 veh/km.
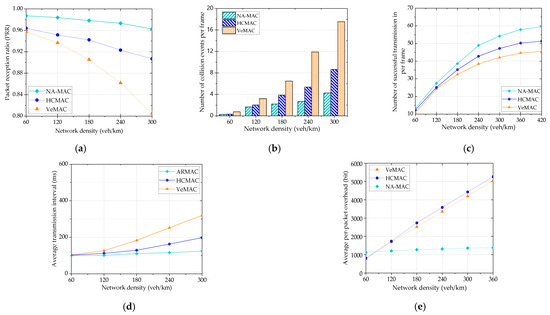
Figure 8.
Simulation results: (a) packet reception ratio vs. network density; (b) number of collision events vs. network density; (c) number of successful transmissions per frame; (d) average transmission interval; (e) average per-packet overhead vs. various protocols.
In Figure 8b, we demonstrated the number of collision events per frame for the three protocols. Both reference protocols exchanged large one-hop slot allocation table to identify the duplicate slots (detect the collision). In contrast, NA-MAC was able to immediately detect duplicate slots via RTB and CTB packets, and thus it experienced fewer collisions in comparison to VeMAC and HCMAC. In NA-MAC, transmitter verified correct reception of BSM packet, with implicit acknowledging scheme explained in the previous section. The transmitter considers its BSM packet lost only if it did not receive ACK from its AN. For the vehicle density of 300 veh/km, VeMAC and HCMAC experienced 17.4 and 8.2 collisions per frame, respectively, while NA-MAC experienced only around 4 collisions.
Figure 8c compares number of successful transmitted packets per frame for all three protocols. NA-MAC outperformed VeMAC and HCMAC since it eliminated a need for one-hop slot-allocation table. Thus, BSM packet size in NA-MAC was significantly smaller than the packet size in other protocols. As a result, NA-MAC provided a higher BSM packet reception ratio. Figure 8c shows that NA-MAC improved number of successfully transmitted packets by around 30% over VeMAC for the highest vehicle density scenario (420 veh/km). For the same density scenario, NA-MAC performed 15% more successfully transmitted packets in comparison to HCMAC. From this result, we can conclude that the proposed protocol can also enhance the throughput as it significantly increased average number of successfully transmitted packets per frame. We can say that our method guarantees a high goodput if we only consider the payload size of broadcast packet without adding long control information attached and transmitted within the packets of the reference protocols.
Figure 8d presents average transmission interval versus network density. As we increased vehicle density, most of the slots became occupied and more vehicles competed with each other to acquire free slots. Therefore, in high vehicle density, transmission interval was found to be significantly increased for all protocols. This behavior even can be observed for standard CSMA-based MAC protocol [27]. This experiment proved that our NA-MAC protocol provided a shorter average transmission interval than VeMAC and HCMAC. This was due to the fact that NA-MAC allowed each vehicle to acquire its slot faster than the other protocols. In contrast, VeMAC and HCMAC consumed a few frames to identify the duplicate slot allocation. We calculated the average transmission interval from the receiver’s point of view. Therefore, for every time packet lost, the average transmission interval increased for the corresponding transmitter. In the highest density, NA-MAC performed on an average 124 ms transmission interval while reference protocols VeMAC and HCMAC performed 319 and 197 ms, respectively.
Figure 8e presents the average per-packet overhead in various protocols. In VeMAC and HCMAC, each vehicle piggybacked its one-hop slot allocation table on every BSM packet, resulting in rapidly growing overhead for increasing vehicle density. For example, in the highest density, average per-packet overhead of VeMAC and HCMAC became higher than 5000 bits per packet. As the density increased, the transmitted packets experienced more collision due to duplicate slots in the same two-hop range. To report these duplicate slots, HCMAC attached error list to one-hop slot allocation table in each BSM packet, consequently incurring rapidly growing overhead, as shown in Figure 9. In contrast, NA-MAC exhibited substantially lower overhead with a nearly constant value of 1290 bits per packet over the entire range of vehicle density tested.
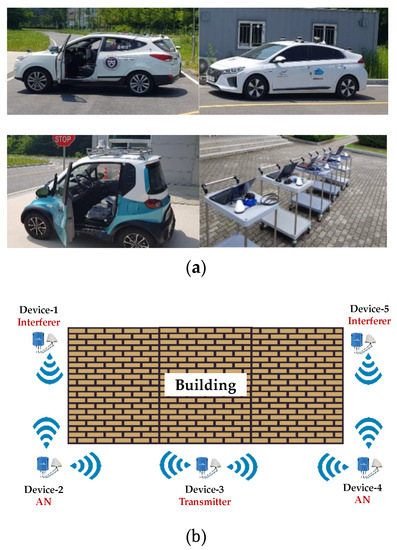
Figure 9.
A testing scenario with real OBU devices: (a) OBUs with omnidirectional antennas are installed in the cars and hand-carrying carts; (b) a layout of five OBUs placed around the building.
6. Evaluation with Hardware Devices
6.1. Experiment Setup
In this subsection, we disclose the configuration of real hardware devices used for the performance evaluation. We then describe the layout of the experiment with five OBUs.
6.1.1. Hardware Configuration
During the experiment, we used five OBUs [31], as illustrated in Figure 9a. These OBUs support IEEE 1609 standard. Each OBU is equipped with global positioning system (GPS) receiver, which provides accurate time synchronization. Table 3 shows additional details of OBU device. We configured OBU in a way that it uses a single control channel (DSRC channel ID is 178 at 5.9 GHz band) to transmit/receive BSM packets. Each device broadcasts BSM packet every 100 ms.

Table 3.
Specification of on-board unit (OBU) device.
6.1.2. Test Scenario
Figure 9b shows the layout of our experiment, where five different OBUs were deployed around the building. Although all OBUs were located in the same wireless range, some of them cannot detect one another, since the building blocked the signals transmitted from the OBUs around it. Connectivity condition of each device with other devices is given in Table 4.

Table 4.
Connectivity condition (R is reachable, U is unreachable).
For example, in the experiment shown in Figure 9b, Device-3 (tagged node) selected Device-2 and Device-4 as ANs. Each time Device-3 tried to acquire a new slot, it exchanged RTB and CTB packets with Device-2 and Device-4. Once Device-3 acquired its slot, it should receive ACK from Device-2 and Device-4. On the other hand, Device-1 (interferer) and Device-5 (interferer) also tried to select their random slots and exchange control RTB/CTB packets with Device-2 and Device-5, respectively.
The experiment conducted in [32] proved that relative speed of vehicles does not particularly affect packet delivery ratio. According to the results in [32], vehicles travelling at 200 km/h relative speed experience only 4% drop in their packet delivery ratio. Therefore, the results acquired from our experiment scenario can be considered quite reliable, even though we did not consider velocity by fixing position of the devices at predefined locations.
6.2. Measurement Results
During the experiment, we compared our proposed protocol with standard IEEE 802.11p. Since we had a limited number of OBU devices, we cannot compare NA-MAC with HCMAC. With limited number of OBUs, an enhancement of the proposed method over HCMAC remained unnoticeable. Therefore, in the experiment, we compared our NA-MAC protocol with standard IEEE 802.11p. Figure 10 demonstrates packet reception ratio under various channel congestion ratio (CCR). The x-axis of Figure 10a represents CCR, which ranged from 5% to 35%. To create different congestion ratio, in IEEE 802.11p, we adjusted transmission parameters (packet size and transmission interval) of the interferers. For instance, CCR of 10% corresponded to packet size of 1500 bytes and transmission interval of 20 ms. In NA-MAC, we allowed interferers to occupy multiple slots to emulate high vehicle density in the testing field. As we mention in the experiment, Device-3 represents tagged transmitter while Device-1 and Device-5 act as two interferers. Figure 10a proves that increased congestion ratio incurred significant impact on PRR. For example, for a CCR of 15%, the PRR of IEEE 802.11p was 0.831, while for a CRR 35%, the PRR significantly reduced to 0.53. In Figure 10a, we can see that our proposed NA-MAC protocol successfully mitigated the hidden terminal interference and demonstrated a stable PRR around 0.97.
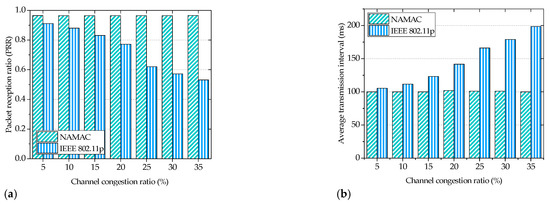
Figure 10.
Experiment results: (a) packet reception ratio (PRR) under different channel congestion ratio (CCR) levels; (b) average transmission interval under different CCR levels.6.2. Measurement Results.
Figure 10b shows an average transmission interval under various CRR levels. As we can see, the average transmission interval of IEEE 802.11p increased as the CCR level grew. For instance, the average transmission interval became around 123.2 ms at a CRR of 15%, while it went up to 198.5 at a CCR of 35%. On the other hand, average transmission interval for NA-MAC remained unchanged (around 102) for all CCR levels, which correlated with PRR results reported in Figure 10a.
7. Conclusions
In this paper, we proposed a novel protocol called neighbor association-based MAC (NA-MAC) aimed at highly reliable broadcast communication for vehicular networks. It takes advantage of both TDMA and CSMA MAC protocols. NA-MAC utilizes CSMA to conduct channel sensing and random back-off operations to resolve the access collision, while it introduces TDMA time slot acquisition to avoid hidden terminal problem. We introduced a novel associative handshake method in TDMA time slot acquisition that effectively eliminates the hidden terminal collisions in broadcast communication. The associative handshake method utilizes control messages called request-to-broadcast and clear-to-broadcast between the transmitter and its predefined associative neighbors. In this way, NA-MAC guarantees that every vehicle propagates its slot reservation information up to its two-hop communication distance. Consequently, unlike the previous methods, NA-MAC does not require every transmitted packet to carry the transmitter’s full information of one-hop slot allocation. Therefore, NA-MAC can significantly reduce the overhead of control information in the broadcast packets. Our extensive simulation results demonstrated that NA-MAC outperforms the existing VeMAC and HCMAC protocols in the performance of packet reception ratio and per-packet overhead. We also conducted performance measurement with V2X hardware devices, proving that NA-MAC can significantly enhance the reliability in comparison to IEEE 802.11p.
Author Contributions
Conceptualization, O.U. and H.K.; methodology, H.K.; software, O.U.; validation, O.U. and H.K.; formal analysis, H.K.; writing—original draft preparation, O.U. and H.K.; writing—review and editing, H.K.; funding acquisition, H.K. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by IITP grant (No. 2020-0-01304), Development of Self-learnable Mobile Recursive Neural Network Processor Technology Project, and also supported by the Grand Information Technology Research Center support program (IITP-2020-0-01462) supervised by the IITP and funded by the MSIT (Ministry of Science and ICT), Korean government. It was also supported by Industry coupled IoT Semiconductor System Convergence Nurturing Center under System Semiconductor Convergence Specialist Nurturing Project funded by the National Research Foundation (NRF) of Korea (2020M3H2A107678611).
Conflicts of Interest
The authors declare there is no conflict of interest.
References
- Intelligent Transport Systems (ITS). Decentralized Congestion Control for Intelligent Transport Systems Operating in the 5 GHz Range; Access Layer Part, Document ETSI 102 687 V1.1.1; European Telecommunications Standards Institute: Sophia, France, 2018. [Google Scholar]
- IEEE. IEEE Standard for Wireless Access in Vehicular Environment (WAVE); IEEE Vehicular Technology Society Supported by the Intelligent Transmission Systems Committee, Revised Draft; IEEE: New York, NY, USA, 2014. [Google Scholar]
- Standard Specification for Telecommunications and Information Exchange Between Roadside and Vehicle Systems—5 GHz Band Dedicated Short Range Communications (DSRC) Medium Access Control (MAC) and Physical Layer (PHY) Specifications; ASTM Std. E2213: Washington DC, USA, 2010.
- IEEE 1609 Working Group. IEEE Standard for Wireless Access in Vehicular Environments (WAVE)-Multi-Channel Operation; IEEE: New York, NY, USA, 2016. [Google Scholar]
- SAE International Standard for Dedicated Short Range Communications (DSRC) Message Set Dictionary J2735_200911. Available online: https://www.sae.org/standards/content/j2735_200911 (accessed on 2 February 2021).
- Cumbal, R.; Palacios, H.; Hincapie, R. Optimum deployment of RSU for efficient communications multi-hop from vehicle to infrastructure on VANET. In Proceedings of the 2016 IEEE Colombian Conference on Communications and Computing (COLCOM), Cartagena, CO, USA, 27–29 April 2016; pp. 1–6. [Google Scholar]
- Li, P.; Huang, C.; Liu, Q. Delay Bounded Roadside Unit Placement in Vehicular Ad Hoc Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 937673. [Google Scholar] [CrossRef]
- Trullols, O.; Fiore, M.; Casetti, C.E.; Chiasserini, C.F.; Ordinas, J.B. Planning roadside infrastructure for information dissemination in intelligent transportation systems. Comput. Commun. 2010, 33, 432–442. [Google Scholar] [CrossRef]
- Demir, U.; Toker, C.; Ekici, O. Energy-Efficient Deployment of UAV in V2X Network Considering Latency and Backhaul Issues. In Proceedings of the 2020 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Odessa, Ukraine, 26–29 May 2020; pp. 1–6. [Google Scholar]
- Peng, F.; Peng, B.; Qian, D. Performance analysis of IEEE 802.11e enhanced distributed channel access. IET Commun. 2010, 4, 728. [Google Scholar] [CrossRef]
- Eichler. Performance Evaluation of the IEEE 802.11p WAVE Communication Standard. In Proceedings of the 66th IEEE Vehicular Technology Conference, VTC Fall 2007, Baltimore, MD, USA, 30 September–3 October 2007; pp. 2199–2203. [Google Scholar]
- Sjöberg, K.; Uhlemann, E.; Strom, E.G. How Severe Is the Hidden Terminal Problem in VANETs When Using CSMA and STDMA? In Proceedings of the 2011 IEEE Vehicular Technology Conference (VTC Fall), San Francisco, CA, USA, 5–8 September 2011; pp. 1–5. [Google Scholar]
- Viriyasitavat, W.; Tonguz, O.; Bai, F. UV-CAST: An urban vehicular broadcast protocol. IEEE Commun. Mag. 2011, 49, 116–124. [Google Scholar] [CrossRef]
- Schwartz, R.S.; Das, K.; Scholten, H.; Havinga, P. Exploiting beacons for scalable broadcast data dissemination in VANETs. In Proceedings of the Ninth ACM International Workshop on Vehicular Inter-Networking, Systems, and Applications—VANET’12; ACM: New York, NY, USA, 2012; p. 53. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, M.; Lee, T.-J. Coordinated Multichannel MAC Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2016, 65, 6508–6517. [Google Scholar] [CrossRef]
- Omar, H.A.; Zhuang, W.; Li, L. VeMAC: A TDMA-Based MAC Protocol for Reliable Broadcast in VANETs. IEEE Trans. Mob. Comput. 2013, 12, 1724–1736. [Google Scholar] [CrossRef]
- Dang, D.N.M.; Dang, H.N.; Nguyen, V.; Htike, Z.; Hong, C.S. HER-MAC: A Hybrid Efficient and Reliable MAC for Vehicular Ad Hoc Networks. In Proceedings of the 2014 IEEE 28th International Conference on Advanced Information Networking and Applications, Victoria, BC, Canada, 13–16 May 2014; pp. 186–193. [Google Scholar]
- Dang, D.N.M.; Nguyen, V.; Chuan, P.; Oo, T.Z.; Hong, C.S. A reliable multi-hop safety message broadcast in Vehicular Ad hoc Networks. In Proceedings of the 16th Asia-Pacific Network Operations and Management Symposium, Busan, Korea, 27–29 September 2006; pp. 1–6. [Google Scholar]
- Dang, D.N.M.; Dang, H.N.; Vo, P.L.; Ngo, Q.T. A Cooperative Efficient Reliable MAC protocol for Vehicular Ad hoc Networks. In Proceedings of the Advanced Technologies for Communications (ATC) 2015 International Conference, Ho Chi Minh City, Vietnam, 14–16 October 2015; pp. 383–388. [Google Scholar]
- Gallo, L.; Jérôme, H. Analytical study of self-organizing TDMA for V2X communications. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 2406–2411. [Google Scholar]
- Bilstrup, K.; Uhlemann, E.; Ström, E.; Bilstrup, U. On the Ability of the 802.11p MAC Method and STDMA to Support Real-Time Vehicle-to-Vehicle Communication. EURASIP J. Wirel. Commun. Netw. 2009, 2009, 902414. [Google Scholar] [CrossRef]
- El-Gawad, M.A.A.; ElSharief, M.; Kim, H. A cooperative V2X MAC protocol for vehicular networks. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 65. [Google Scholar] [CrossRef]
- Mosavat-Jahromi, H.; Li, Y.; Ni, Y.; Cai, L. Distributed and Adaptive Reservation MAC Protocol for Beaconing in Vehicular Networks. IEEE Trans. Mob. Comput. 2020, 1. [Google Scholar] [CrossRef]
- Ros, F.J.; Ruiz, P.M.; Stojmenovic, I. Acknowledgment-Based Broadcast Protocol for Reliable and Efficient Data Dissemination in Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2010, 11, 33–46. [Google Scholar] [CrossRef]
- Lyu, F.; Zhu, H.; Zhou, H.; Xu, W.; Zhang, N.; Li, M.; Shen, X. SS-MAC: A Novel Time Slot-Sharing MAC for Safety Messages Broadcasting in VANETs. IEEE Trans. Veh. Technol. 2017, 67, 3586–3597. [Google Scholar] [CrossRef]
- Lyu, F.; Zhu, H.; Zhou, H.; Qian, L.; Xu, W.; Li, M.; Shen, X. MoMAC: Mobility-Aware and Collision-Avoidance MAC for Safety Applications in VANETs. IEEE Trans. Veh. Technol. 2018, 67, 10590–10602. [Google Scholar] [CrossRef]
- Song, C. Performance Analysis of the IEEE 802.11p Multichannel MAC Protocol in Vehicular Ad Hoc Networks. Sensors 2017, 17, 2890. [Google Scholar] [CrossRef] [PubMed]
- Cao, Y.; Zhang, H.; Zhou, X.; Yuan, D. A Scalable and Cooperative MAC Protocol for Control Channel Access in VANETs. IEEE Access 2017, 5, 9682–9690. [Google Scholar] [CrossRef]
- Ullah, S.; Hassan, M.M.; Hossain, M.S.; Alelaiwi, A. Performance Evaluation of RTS/CTS Scheme in Beacon-Enabled IEEE 802.15.6 MAC Protocol for Wireless Body Area Networks. Sensors 2020, 20, 2368. [Google Scholar] [CrossRef] [PubMed]
- Hasan, K.F.; Feng, Y.; Tian, Y.-C. GNSS Time Synchronization in Vehicular Ad-Hoc Networks: Benefits and Feasibility. IEEE Trans. Intell. Transp. Syst. 2018, 19, 3915–3924. [Google Scholar] [CrossRef]
- Cohda Wireless MK5 OBU & RSU. Available online: https://cohdawireless.com/solutions/hardware/ (accessed on 2 November 2020).
- El-Gawad, M.A.A.; ElSharief, M.; Kim, H. A Comparative Experimental Analysis of Channel Access Protocols in Vehicular Networks. IEEE Access 2019, 7, 149433–149443. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).