1. Introduction
A flying ad-hoc network is a self-organizing wireless network and it takes the form of MANETs (mobile ad-hoc networks) and VANETs (vehicular ad-hoc networks). To perform different kinds of operations, FANETs use driverless aircraft which are also known as unmanned aerial vehicles [
1,
2,
3,
4,
5,
6]. These can be easily installed in non-deterministic areas. Traffic monitoring during congestion, search and rescue operations, patrolling, remote data collection, environmental sensing, and agricultural management are the different applications of FANETs [
7,
8,
9,
10,
11,
12,
13,
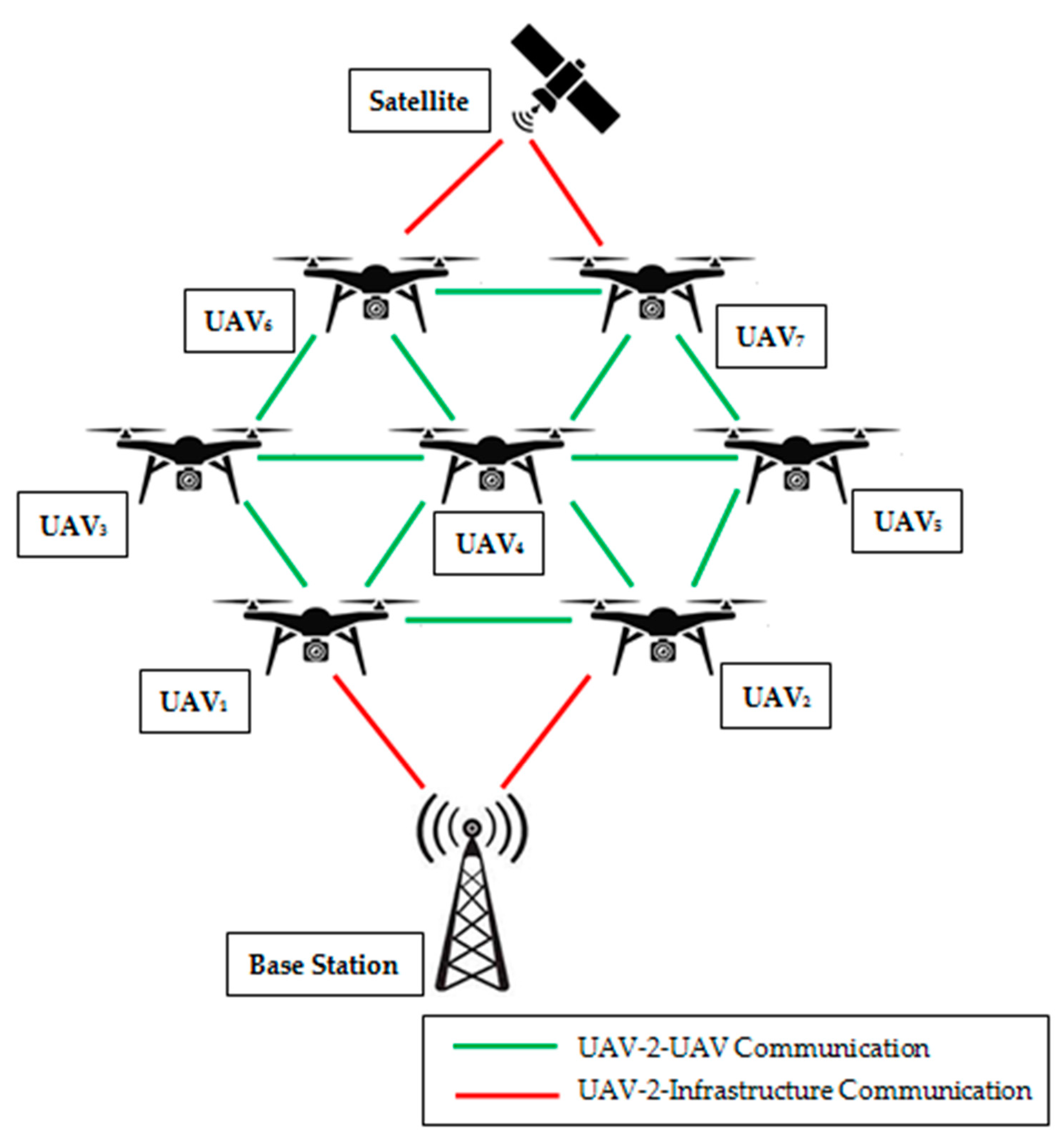
14]. In FANET, there are two categories of communications, namely UAV-2-UAV communication and UAV-2-Infrastructure communication (
Figure 1). UAV-2-UAV can be used for short-range as well as for long-range communication, which is based on the rate of transmission of information (indicated as a green line). On the other side, UAV-2-Infrastructure communication can be used for transmitting and receiving data (indicated as red line) on various operations (either from a base station or from satellite).
Further, in this study, we describe the different major design limitations. Communication is one of the crucial parameters in the design of multiple unmanned aerial vehicles. Another crucial parameter is limited battery energy [
15,
16]. Several other major challenges are flight trajectory selection, energy limitations, adaptive routing protocols, power constraints, etc. that require consideration in this network. The main challenge is high mobility in the FANETs. Another challenge is an irregular change in the structure of the nodes in the specified network. Many researchers have introduced many techniques and algorithms to overcome these challenges in the network [
17,
18,
19,
20,
21,
22,
23,
24]. In this research work, we discuss the solution to overcome these problems, while minimum routing overhead, low computational complexity, and maximum throughput parameters can be used efficiently for load balancing in the network.
There are several important characteristics of flying ad-hoc networks, such as topology change, node speed, mobility model, node mobility, energy constraints, computational power, radio propagation model, and localization, as described in
Table 1 [
25,
26,
27,
28].
A subclass of UAVs can communicate with the satellite in a flying ad hoc network. There are some main differences between traditional networks and flying networks [
29,
30,
31]. MANET and VANET have fewer mobility degrees than FANET. MANET and VANET are used by human beings whereas FANET flies in the sky [
32,
33,
34,
35,
36]. In MANET and VANET, topology changes less frequently than FANET. This is due to the high mobility of flying nodes, and FANET requires the peer-to-peer connection of UAVs. MANET and VANET have less distance, but the distances among flying nodes are much greater than them [
37,
38,
39,
40,
41,
42].
UAVs are rapidly often are widely employed in a variety of industries, and they are gaining traction in the age of big data. The FANET node cannot be moved in most nations’ flight management systems (national) due to airspace regulations. This is the most significant impediment to the expansion of the UAV network in civil aviation. In this regard, it is critical to establish different laws and policies so that the FANET node may operate freely in the air traffic control system. According to the globalized context, the UAV drone market in 2019 in the Asia Pacific was worth
$7012.7 million and is expected to increase at a rate of 17.5% over the next five years. UAV rules in Europe have varied considerably, with considerable variances in criteria for flying licenses evolving with new technology, and as a result, UAV operations are continually altering in response to the demands and laws of Europe’s states parties. To begin with, various nations in Europe utilize different terminology in different laws, e.g., UAV, drone, and remotely operated aircraft. This may be seen in the fast-increasing UAV market, which is predicted to be worth 10 billion euros per year in Europe until 2035, and might be worth more than 15 billion euros per year by 2050 [
43].
The technique introduced by us accurately defines the collisions in the flying nodes within the same network. Unlike most of the existing stochastic techniques, our proposed technique is not as difficult, complicated, and dependent on various vectors. Instead, it specifically depends on two metrics: load key of an optimal path and the threshold of bandwidth utilization. The major contributions of this paper can be summarized as follows:
Based only on two parameters (load key of an optimal path and the threshold of bandwidth utilization), we provide simple yet precise terms and mathematical expressions for various crash nodes in FANET. It computes the possibilities of collisions of multiple nodes in the network, and consequently the security of multiple UAVs. We mainly derive and discuss the mathematical expressions of the predictable number of collisions in the network.
The parameter LoK characterizes the connection of the different node paths in the network. The obtained standard mathematical expression is then used to detect the malicious node that triggered the attack in the network. Furthermore, we achieve accurate expressions compared with two effects, namely secure and insecure two ray and shadowing effects.
To improve the efficiency of the nodes, we propose an enhanced firefly algorithm. The proposed algorithm binds the features of different parameters: low packet loss, delay, and network overhead but high throughput.
A detailed comparative analysis has been carried out to evaluate the security of the network. We validate the obtained results in the graphical representation of the simulation.
The main goal of our proposed technique is to understand the UAVs system evolution, to help the UAVs in safe mode, without collision risk factors, and last but not least handling the issue related to the collision risks. This work involves the algorithm to evaluate the optimal route for sending data from various sources of multiple UAVs. Using the proposed methodology, there are two sections of the firefly algorithm working: one is the flashing behavior of the firefly and the other one is the step-by-step procedure, which defines the set of rules or instructions to be executed in a specific order to get the best-desired output. The firefly algorithm is used to handle optimization problems that exploit the alternating performance of fireflies in nature. Optimization is the concept to find the best path in and the term optimization is the act of making decisions and providing the best solution from the set of all feasible and possible solutions. There are three parameters of optimization techniques, namely a function to optimize, to select a value using possible solutions, and the rule of optimization.
The paper is structured into different sections as follows: In
Section 2, a review of the related literature is presented.
Section 3 presents our proposed analytical approach.
Section 4 validates the analytical results by comparing them against simulation results.
Section 5 concludes the paper and presents the future scope.
2. Related Work
A FANET is another variant of an ad-hoc network which is the sub-domain of MANET and VANET. It is not allowed to directly use the distinctive features of MANET and VANET. However, new techniques or variants of existing techniques that take into account the unique features of an unmanned aerial network are required.
Table 2 provides a comparative study based on parameters that have to be tackled in the majority of existing surveys in the literature and our proposed work. Mahjri et al. [
44] introduced a simple model to illustrate collisions in flying nodes using two input parameters, such as UAVs having accurate detection and avoidance capabilities as well as no accurate detection and avoidance capabilities. In the case of real-world UAV nodes, adequacy and accuracy are the main limits of this stochastic model. Belkhouche et al. [
45] used kinematic equations for the deterministic case and also used for the calculations of the probability of collision between vehicles. This method does not guarantee a non-underestimation of the collision risk, ensuing in damage with respect to the security requirements.
Hung et al. [
46] formulated a framework and algorithm to solve the reinforcement learning (RL) problem. This framework is used for fixed-wing UAVs in the non-stationary stochastic environment. This formulation can apply for better exploration methods to speed up the learning process by using function approximation methods. Mahjri et al. [
47] proposed a 3D distributed and straight-line conflict detection and alerting algorithm. This algorithm is used for only packet loss and uncertainties information at the state level for the perfect environment.
Liu et al. [
48] proposed a 3D UAV relative localization framework and showed the performance which is based on the localization accuracy of the UAVs. This framework is only used for MDS-based algorithms, but it can be used for other relative localization purposes in the future. Tang et al. [
49] investigated and proved the machine learning technologies in the network with a 6G intelligent network. This paper surveyed distinctive challenges in the particular networks. The proactive security methods can be used in a 6G intelligent network. Temel et al. [
50] proposed a novel directional MAC protocol (LODMAC) which increased the spatial reuse and overall network capacity in the 3D environment of the existing network. This work is only limited to FANET MAC protocols. Khabbaz et al. [
51] discussed how to improve the data communication performance using different parameters, such as the speed and density of the nodes in the networks. The work of Tang et al. [
52] is based on location-based social networks (LBSNs) to compute the data in the cloud. Thus, the authors showed the mechanism for the effectiveness of the UAV-mounted, cloudlet-aided network with parameters accurate throughput and low packet delay. Wen et al. [
53] presented a distributed optimization algorithm for flying nodes in the networks. They showed the simulation work with parameters such as improved network throughput, limited the E2E delay (end-to-end), and reduced co-channel interference. Rosati et al. [
54] compared the two different routing protocols and showed the performance of the predictive–optimized link state routing (P-OLSR) and optimized link state routing (OLSR) in the flying ad-hoc networks.
In terms of world legalization, the authors discussed the UAV legislation in Germany and the significant developments in the area of UAV safety and reliability from 2017 to 2018 [
55]. A further study concentrated on German UAV laws. According to European law, UAV activities in German airspace were considered in the submission. It said that Germany has established legislative frameworks to assist in the development and implementation of laws for UAV makers and operators [
56].
The desire for consistent legality remains a difficult challenge for regulators since laws must account for UAV technology innovation and creative capabilities as they arise [
57], which necessitates continual regulatory revisions over time. Rules are continually constantly re-evaluated and standardized in countries with current UAV legality. Practically all of the above restrictions have been developed or revised in the last few years [
58]. The European Commission is now working on unifying UAV laws and establishing consistent specifications, to submit a proposal to incorporate all UAVs, irrespective of their size, into the European flight safety framework [
59]. The new European drone laws (which went into effect on 1 January 2021) constitute a major step toward European standardization since they establish guidelines for all European nations, such as airspace classifications, UAV operating categories, and so on. Furthermore, the new European provisions include part of the world requirements as well as national regulatory requirements that must be met by individual European member states.
With the latest technologies, it provides results that are reliable, ideal, and best-suited. However, there are points of improvement in the computational methods involved in it that are way too high and complex. The time constraint required by them is much longer than required to produce optimal results. It refers to the initially randomized multi-valued solutions and converges the results with iteration following the global solution in an improvised manner. Due to the large randomization of selected values and large population size, some algorithms work at a slow pace. We are well aware that technology upgrades quickly with time, so do the network structures. Therefore, because of the high movements of UAVs, we get restricted to the processing power of UAVs. Such kinds of methods and techniques involve a lot of time to reach the valid result and frequently more time is consumed for an invalid output which cannot be utilized further for changing the structure of the network. These energy-based approaches are not suited for techniques using high computational and expensive parameters towards the networking area.
3. Proposed Methodology
In this section, we begin with mathematical notations and data structures of the considered network. We then consider two parts, namely the load key of an optimal path and the threshold of bandwidth utilization.
Table 3 presents the lists of mathematical notations and data structures of the flying nodes. Moreover, we present the complete descriptions of the mathematical notations used. Here, we explain the metrics of the network as mentioned below:
A Load Key (LoK) of an Optimal Path
This metric has been defined to recognize the connection of the different node paths in the complete routing process. This is also defined as the distribution of the different packets in the network. When we analyze the network, we observe some flying nodes that are overloaded. The reason behind this is that the nodes receive the most data transmissions in the network. In this paper, we aim to change this specific load away from overloaded networks and shift to other alternate routes. We describe the metric named Load Key (LoK) for this intent, where we look for optimal paths at each flying node in the network.
Case 1: Suppose a variable as ‘’ which represents a time period, and the total load of the entire network is denoted as ‘’.
In simple words, we can say it is the sum of the entire loads on all the flying nodes in the network, which is mentioned below in (1):
where,
m is equivalent to
n−1.
Case 2: If the flying nodes are not connected in the network, then we can use the input vector as ‘
’ at the same time period, where ‘
y’ and ‘
z’ variables are set for nodes from 1 to
n as mentioned below in (2):
where
Case 3: We need to calculate the average load of the flying nodes in the network. The average load ‘
’ of the nodes is defined as:
Now, we need to substitute from (2) to (3), to obtain the final equation as:
B Threshold of Bandwidth Utilization (TB)
This metric has been defined to calculate the actual bandwidth of the network. TB can be defined as a link from one point to another link for the network. The metric TB can be used to monitor the efficiency of the network. This metric also can be used to improve network utilization in flying ad-hoc networks. Here, we have defined the total bandwidth ‘
’ of the network as follows:
where ‘
’ is the fixed bandwidth of the flying nodes.
The technique will result in lower overheads, less congestion, and increase efficiency. This metric can be expressed as an optimization model (TB
max) as stated below:
Finally, this indicates that all the flying nodes are connected to the network with the optimal path from source to destination. There are different steps to implement the proposed methodology, such as selection of path, the possibility of paths, moving of nodes in other directions. Apart from this, it is easy to change the route of the flying nodes due to the change of the topology structure. Here, the two-ray model (Raytwo) is used for the secure routing of the nodes from one place to another using the
Rayf(
x) function.
Furthermore, we need to calculate the secure shadow value, i.e.,
Shadow(
v), as follows:
where
Tr and
Ts represent transmit receiver and transmit sender, respectively.
Finally, we need to calculate the accurate flying nodes as per sender data (
Sd) and receiver data (
Rd) in the network,
By using Equations (8) and (9), we obtain the secure shadow effects of the flying nodes in the network and the result of this work is useful for the verification of FANET nodes, which can be directly used in all the wireless prediction area.
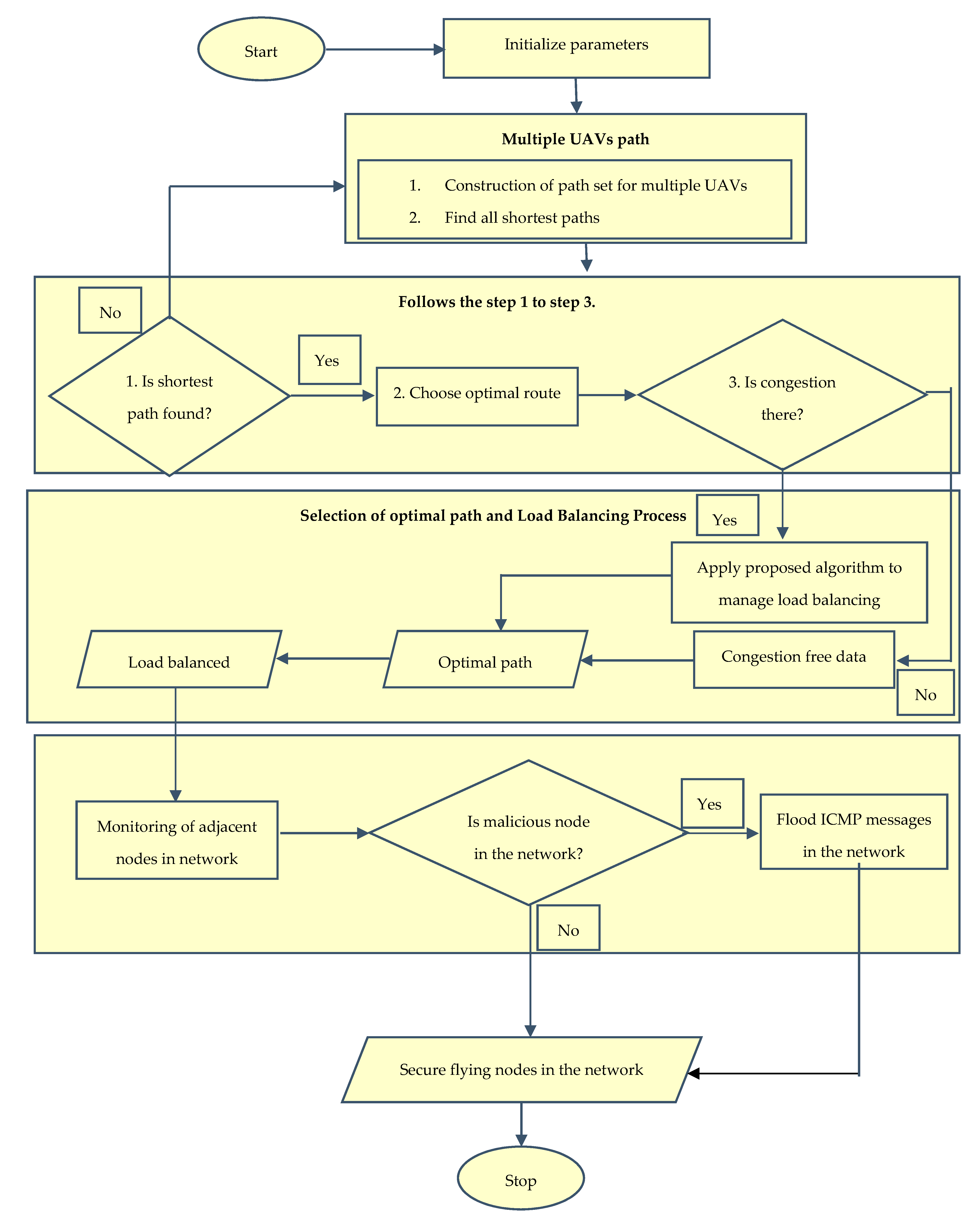
3.1. Selection of Path
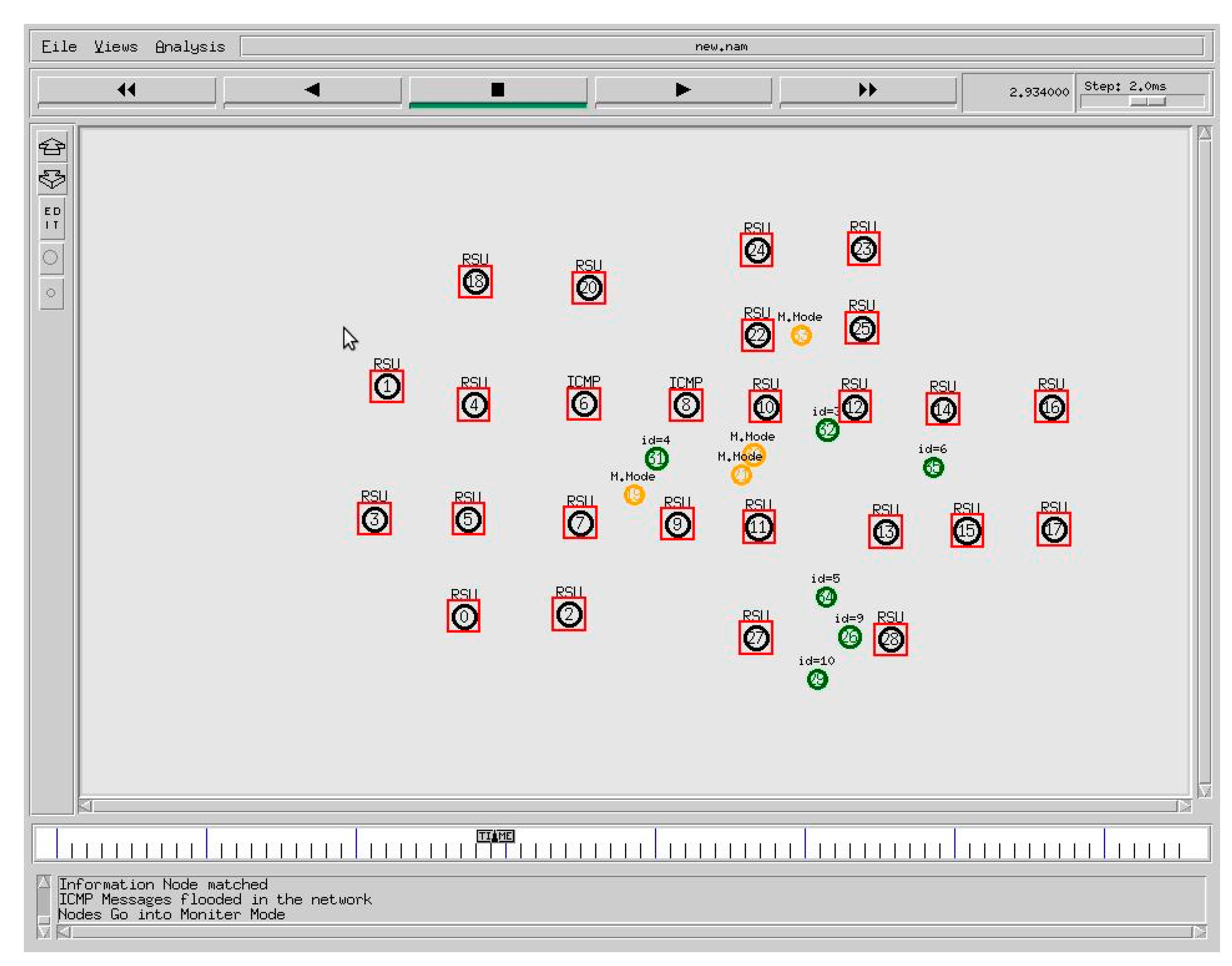
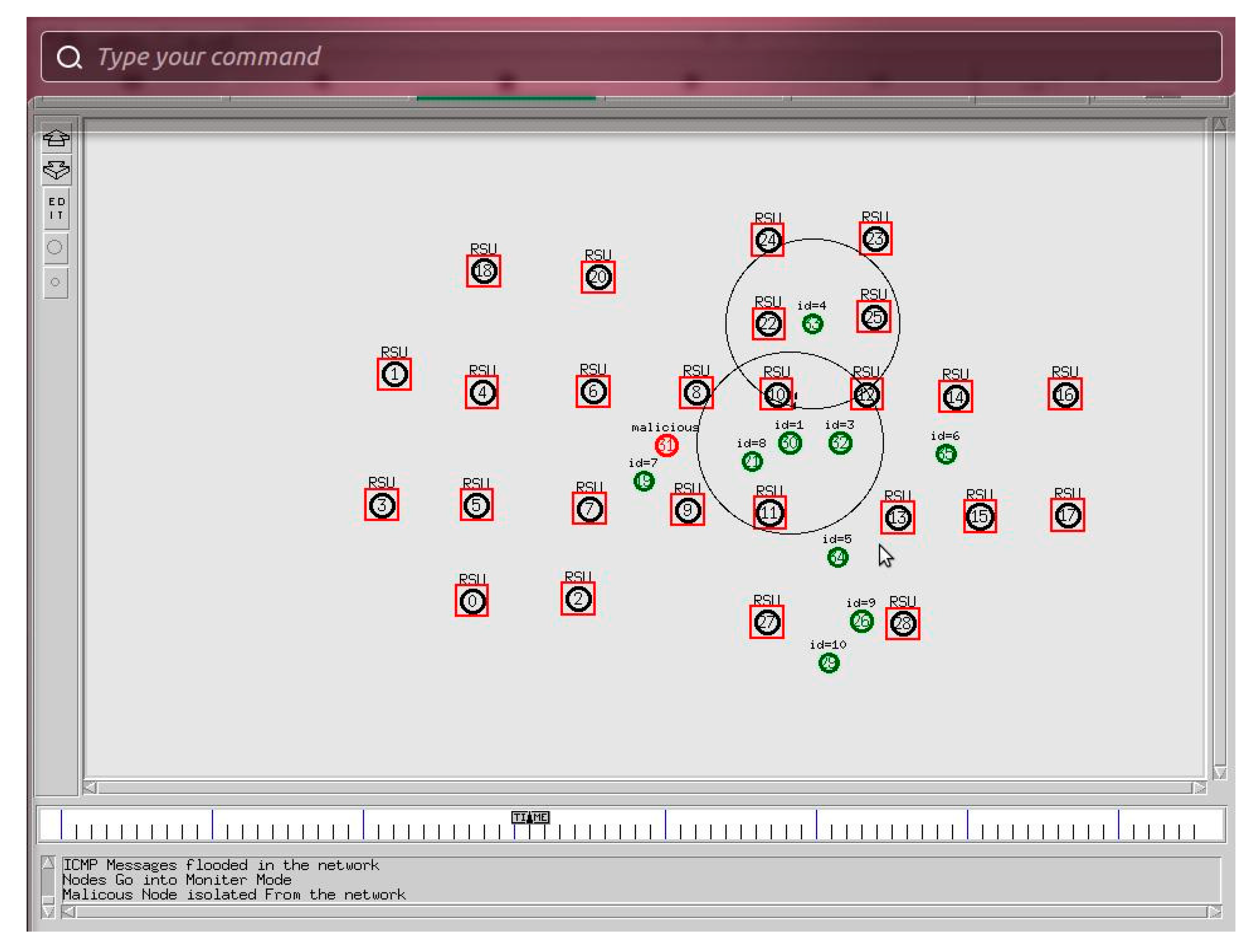
In the path selection method, multiple paths are used in this system to send the data at the same time. When only one route is used, traffic is concentrated at a few nodes, resulting in congestion, as described in
Figure 2. As a result, we use the firefly algorithm to find the optimal path as described in Algorithm 1 and we can keep the benefits of multipath routing without losing the consistency of the paths we use. Any route has a zero count at first, and the top route is chosen for packet routing. After each packet transmission over a given path, the count of that path is increased. When this count equals, the next route is chosen.
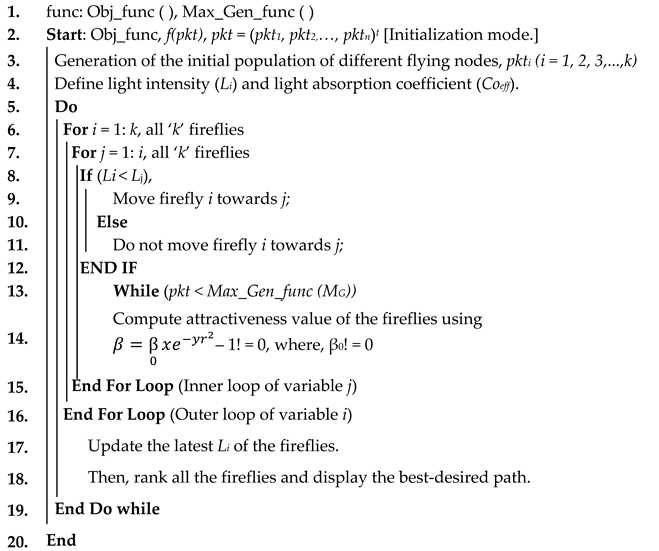
| Algorithm 1. Selection of path using firefly algorithm. |
![Electronics 10 03164 i001]() |
3.2. Possibility of Paths
The calculated Max_Gen_func (MG) represents the possible path and path that are categorized on the behalf of their counted attractiveness. A path with the greater firefly value shows a superior path and therefore it is used more frequently than the other paths. Consequently, a path with a greater value has a greater path selection ratio. Various paths are exploited for packet delivery to a destination. Among the various paths available for a destination, only some of the paths are used for the best path.
3.3. Moving of Nodes to Other Direction
When the selected route is not detected as the connection no longer exists, then the node should be moved to the other direction. After evaluating new solutions and updates light intensity, we need to check the path of the node, such that the path is indeed the path noted for next use. This will happen when the status field of that path is attractive. We just need to recognize, rank the fireflies, and search the path to be used next. To observe this, we should determine the current path of the node for the other paths for a similar destination. We need to apply post-processing on the best results so far and need to visualize the flying nodes.
5. Conclusions
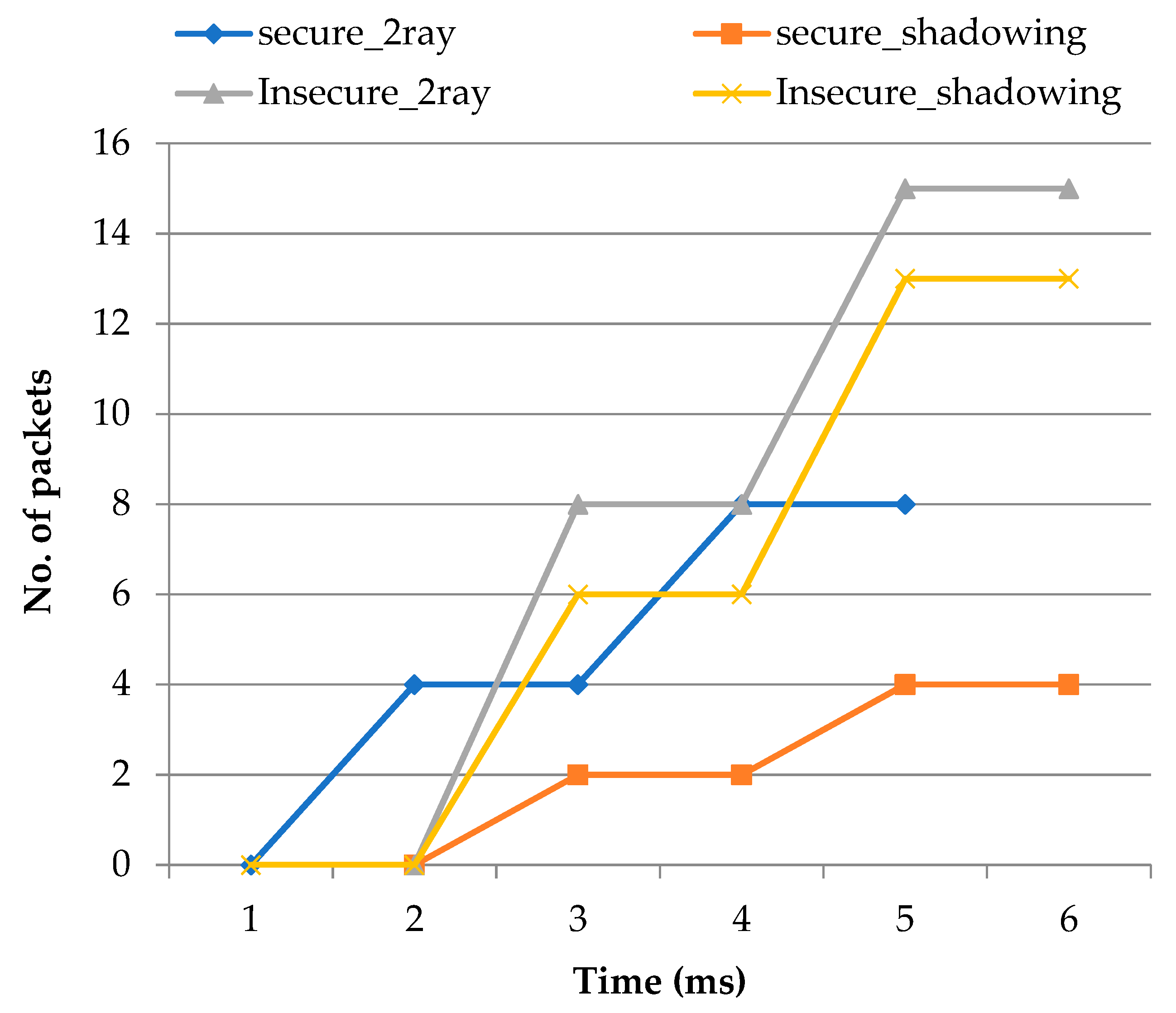
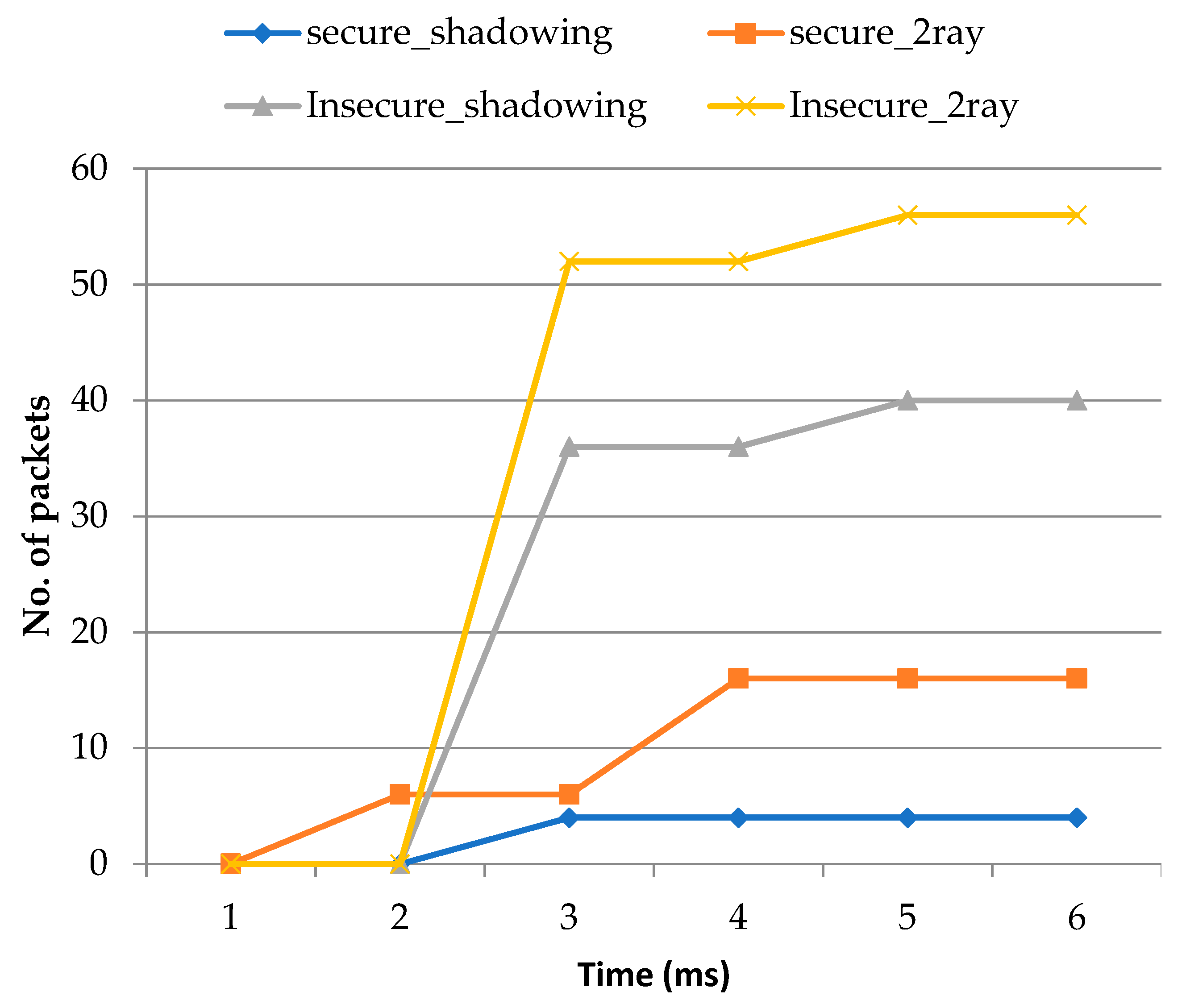
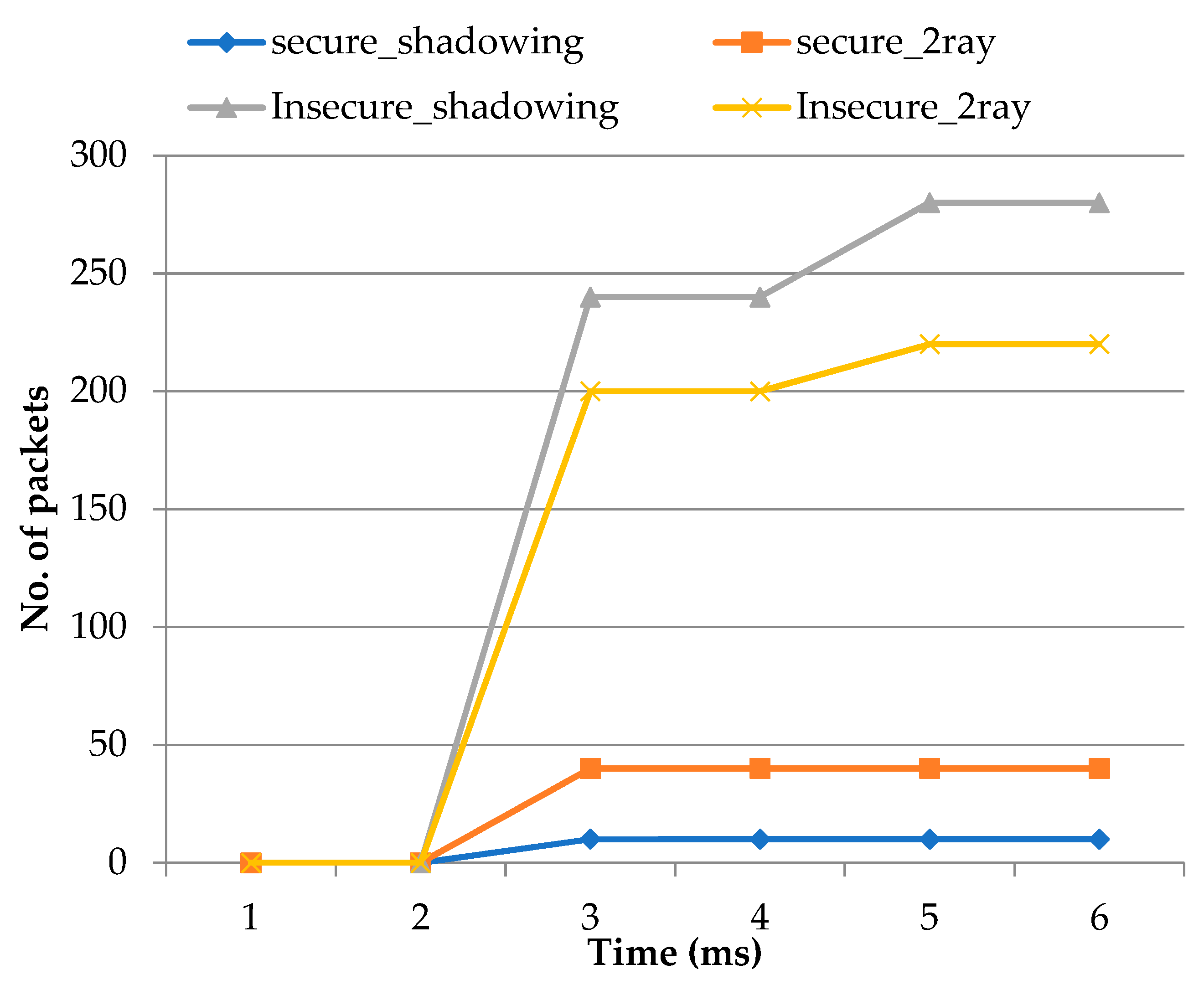
The major revelation from this study is that we have considered the firefly algorithm which holds three major relevant aspects for the optimization technique. The deployment of an efficient approach has played a major role in achieving the secure optimization of flying nodes in the network. We analyzed the different factors used to evaluate the optimal route for sending data from various sources of multiple UAVs and detected the malicious nodes in the network using the two-ray model and shadow effects.
The conducted simulations provide useful and important insights concerning the accuracy of the proposed algorithm for the load balancing technique. Furthermore, the simulation showed the results with different parameters, such as packet loss, throughput, end-to-end delay, routing overhead with secure and insecure two-ray and shadow effects, which further indicates that the parameters can extend the predictable objective by adjusting the flying node position in the ad-hoc network. Further research is required to compare with more security models of the flying nodes in the future. Because FANETs are subject to a variety of attacks, the geographic position-oriented routing protocol can be improved to include the identification of different types of attacks in its design. In the future, it can be improved by creating a new strategy for detecting and locating rogue nodes among Internet of Things devices.