LAN Traffic Capture Applications Using the Libtins Library
Abstract
:1. Introduction
1.1. Libtins
1.1.1. PDU Class
1.1.2. PacketSender and PacketWriter Class
1.1.3. Sniffer and FileSniffer Class
1.1.4. Processing Captured Packets
1.2. Extending the Libtins Library with SIP and RTP Classes for VoIP Packet Analysis
1.2.1. Session Initiation Protocol
1.2.2. Session Description Protocol
1.2.3. Real-Time Transport Protocol
1.3. Building an IDS Using Libtins, Apache Kafka and ksqlDB
1.3.1. Vagrant
1.3.2. Apache Kafka
1.3.3. ksqlDB
1.3.4. Putting It All Together
2. Implementation
2.1. Extending the Libtins Library with SIP and RTP Classes for VoIP Packet Analysis
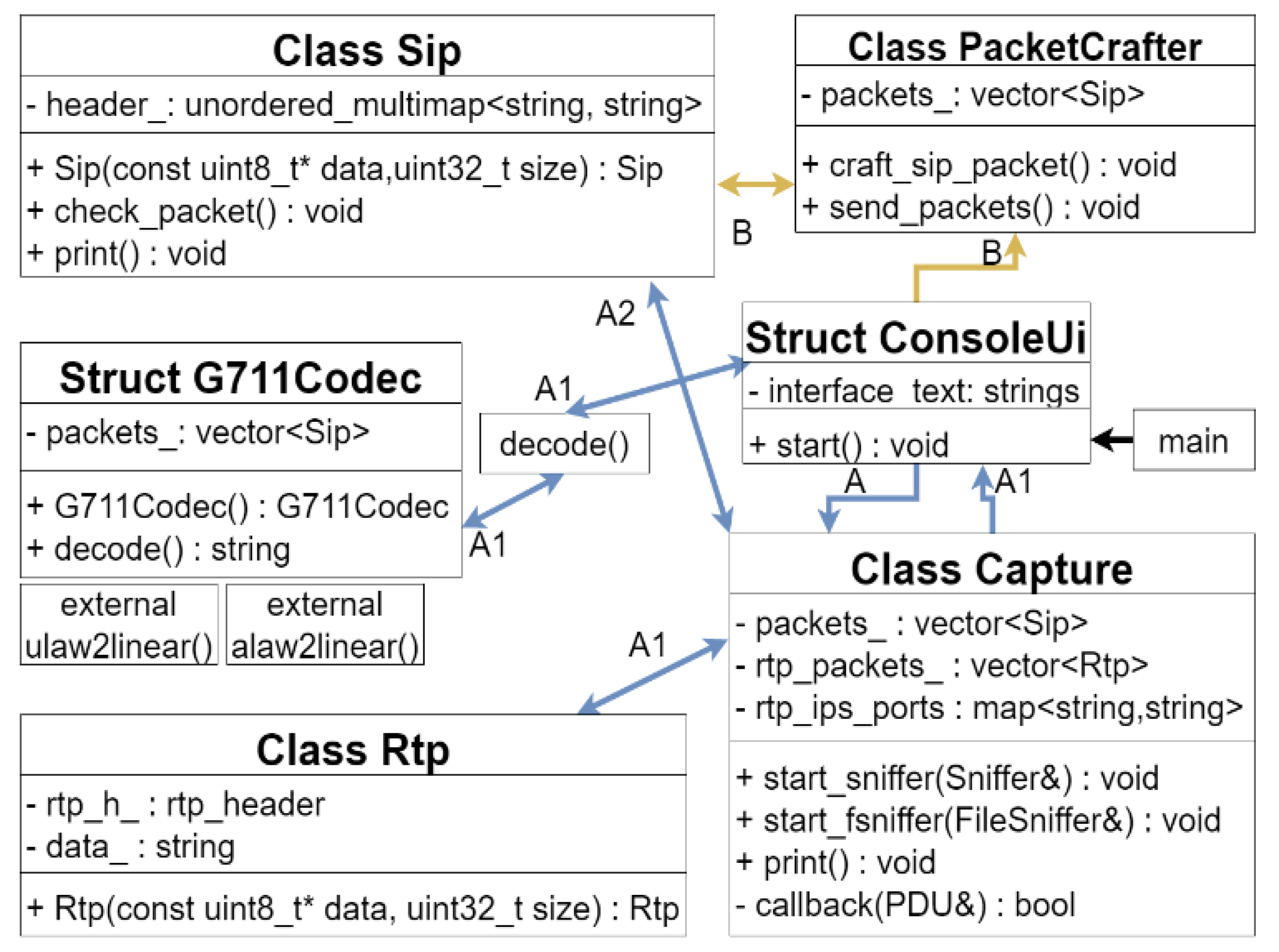
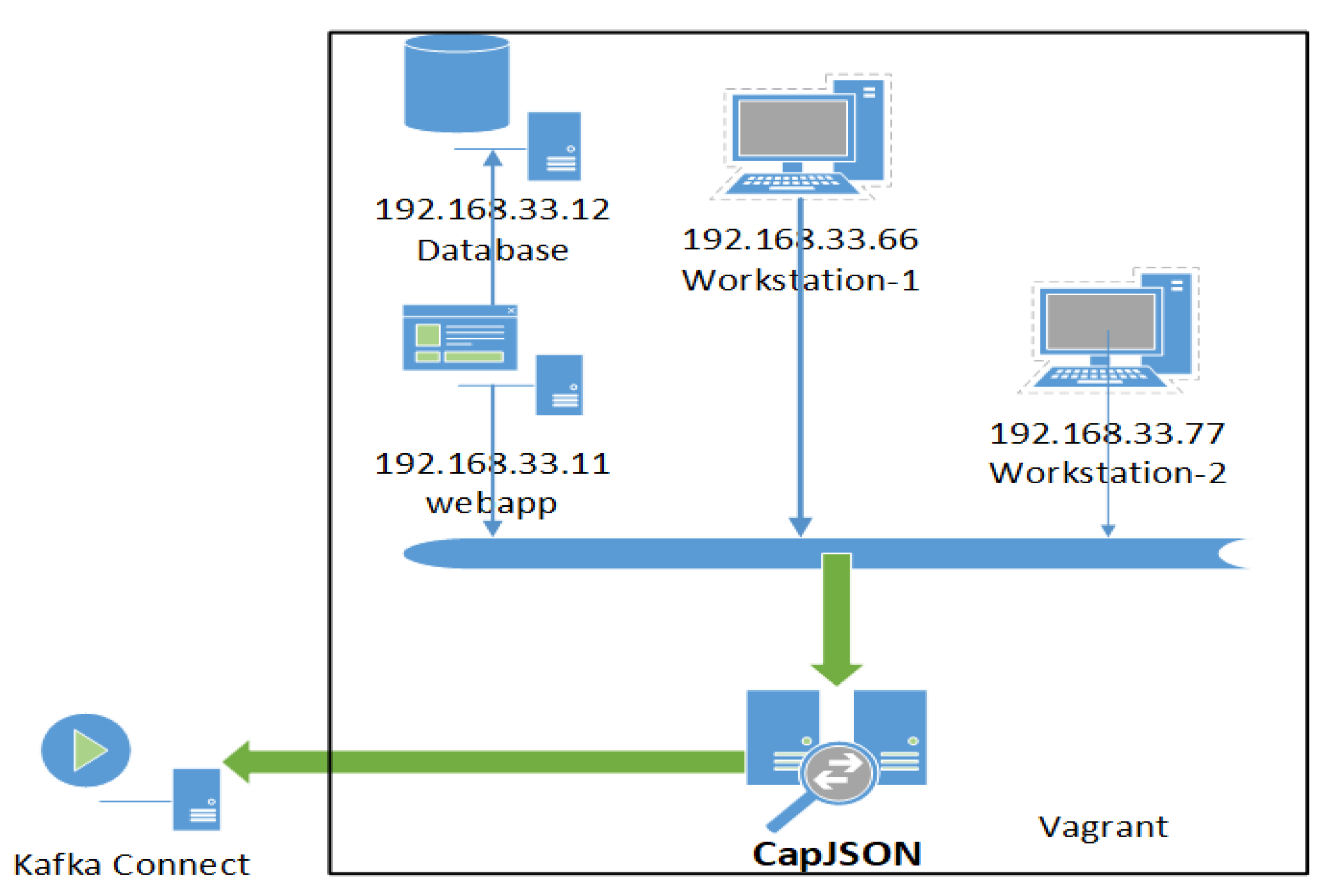
2.1.1. Application Diagram
2.1.2. ConsoleUI Structure
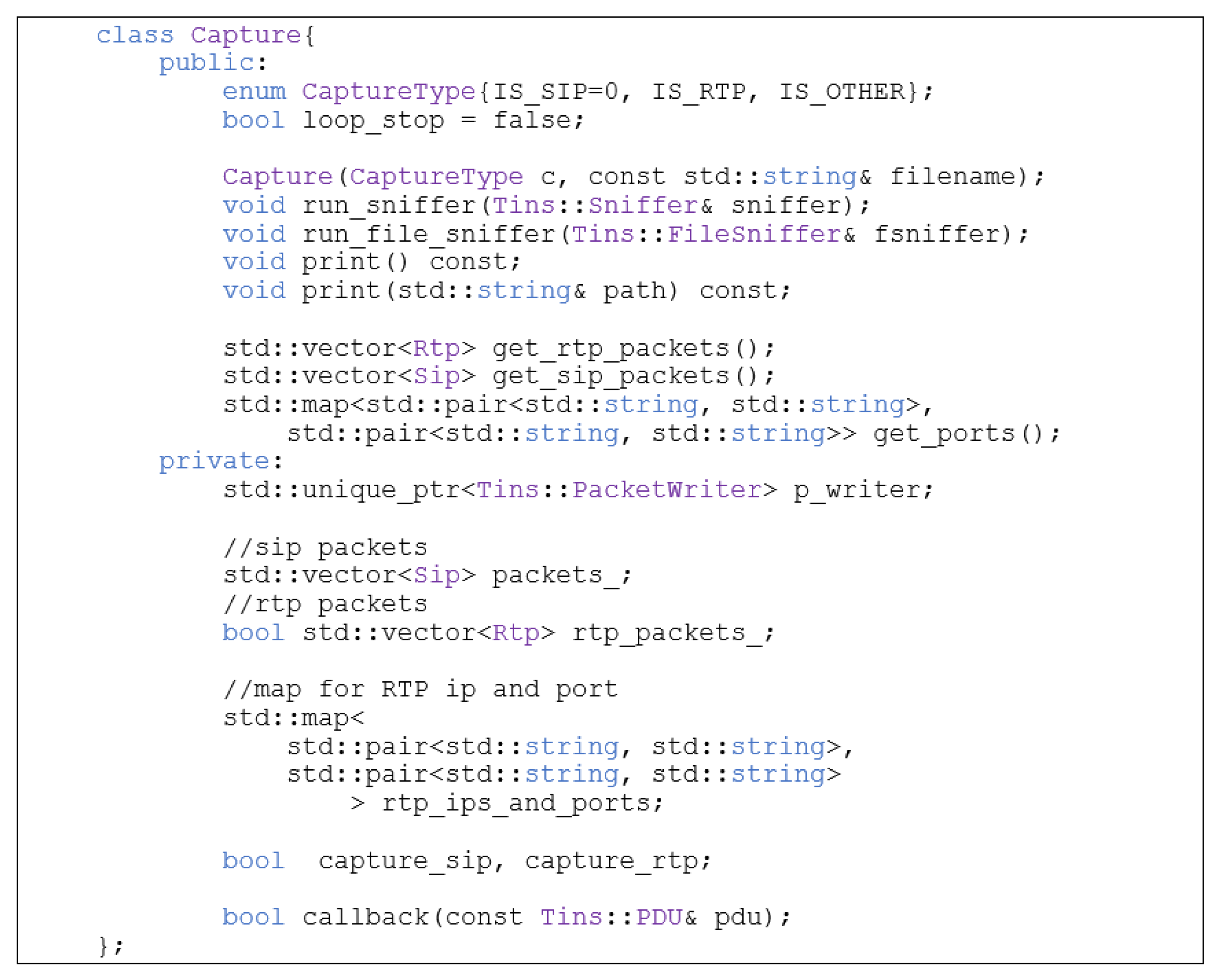
2.1.3. Capture Class
2.1.4. SIP Class
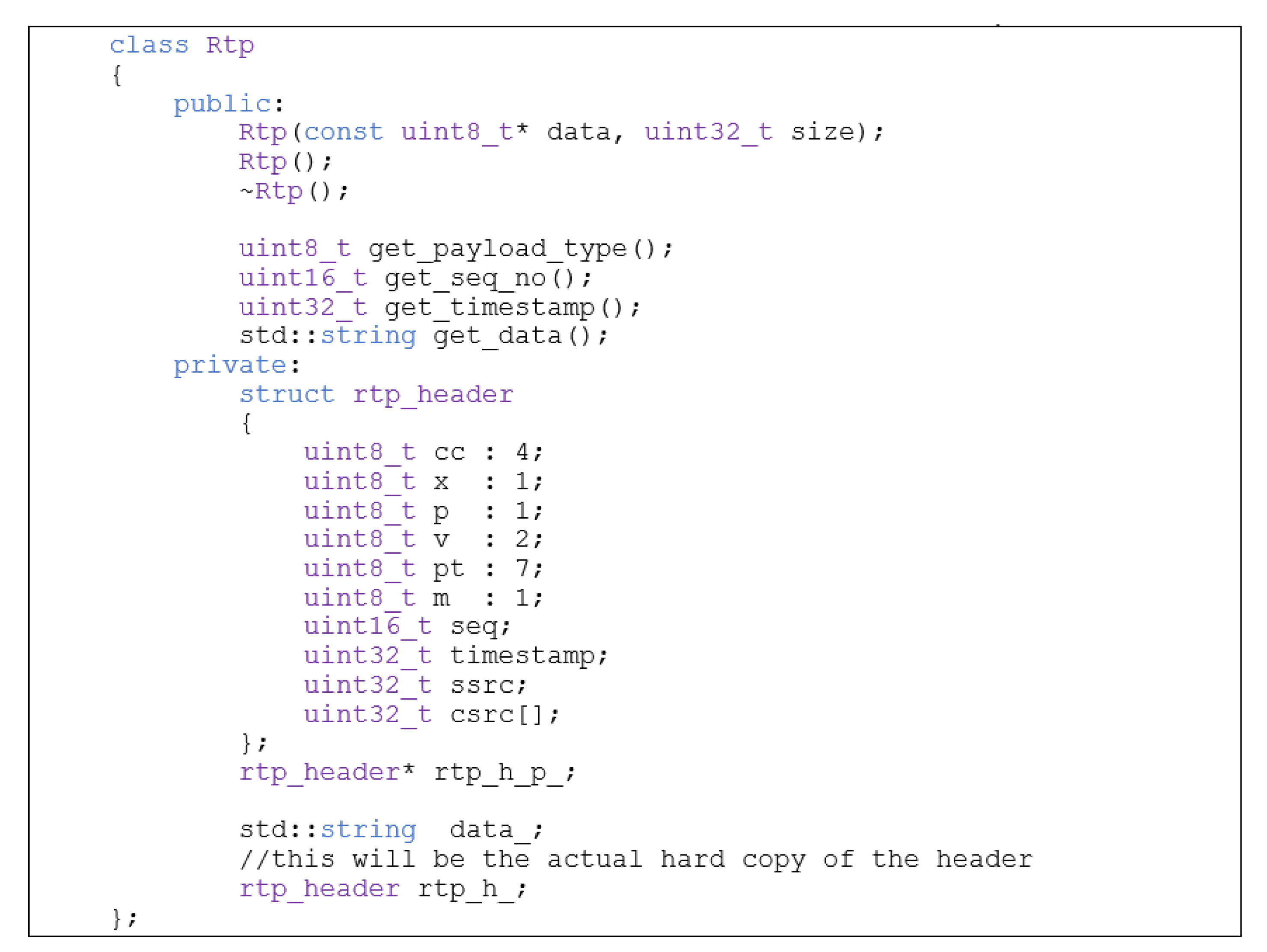
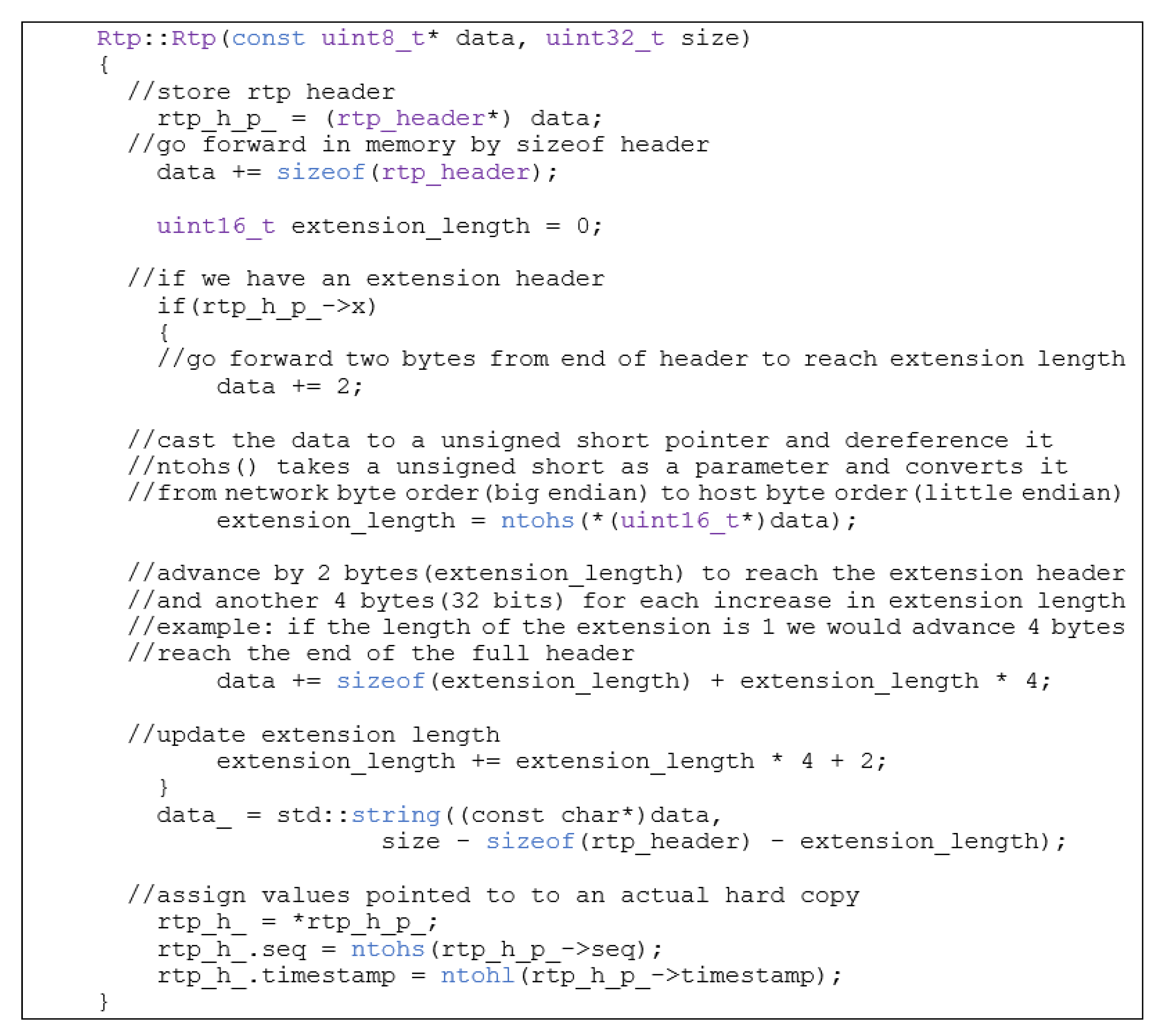
2.1.5. RTP Class
2.1.6. PacketCrafter Class
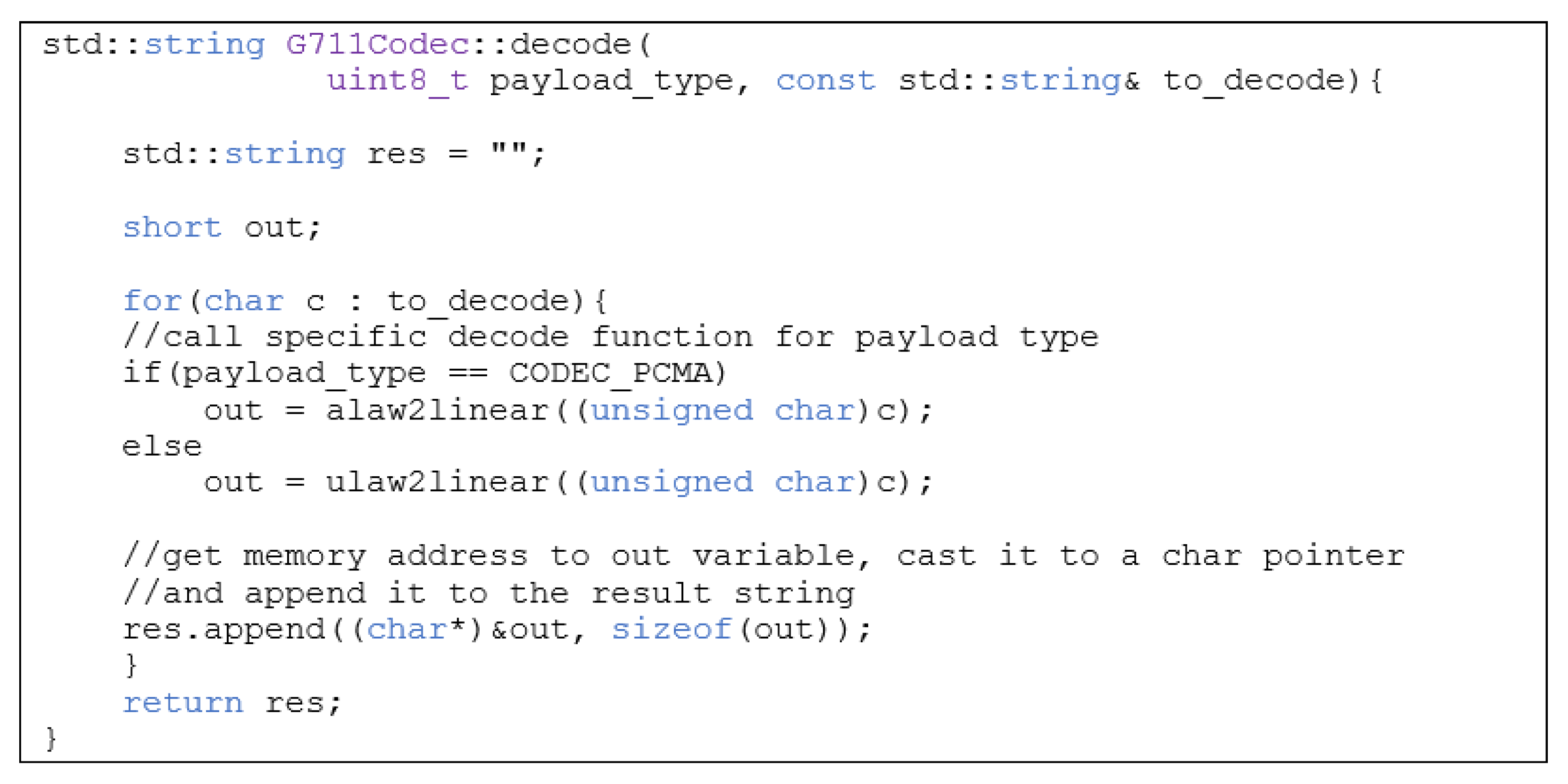
2.1.7. Decoding Algorithm
2.2. Building an IDS Using Libtins, Apache Kafka and ksqlDB
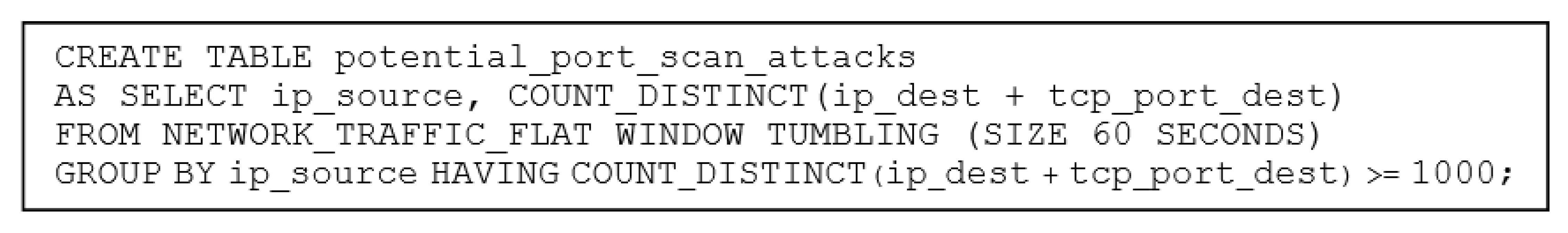
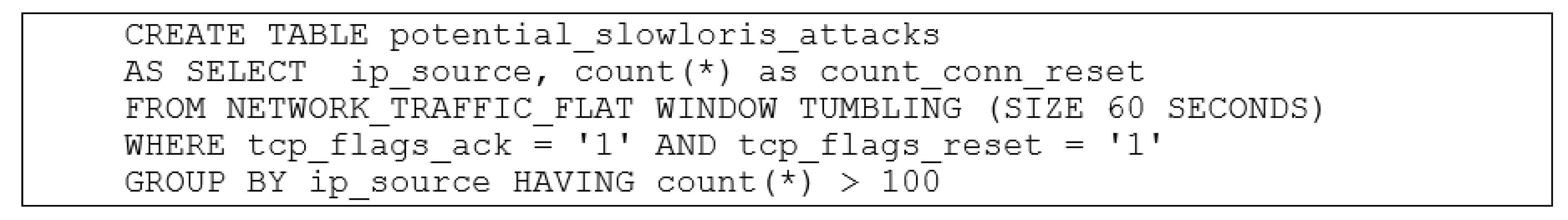
2.2.1. IDS Implementation Using ksqlDB
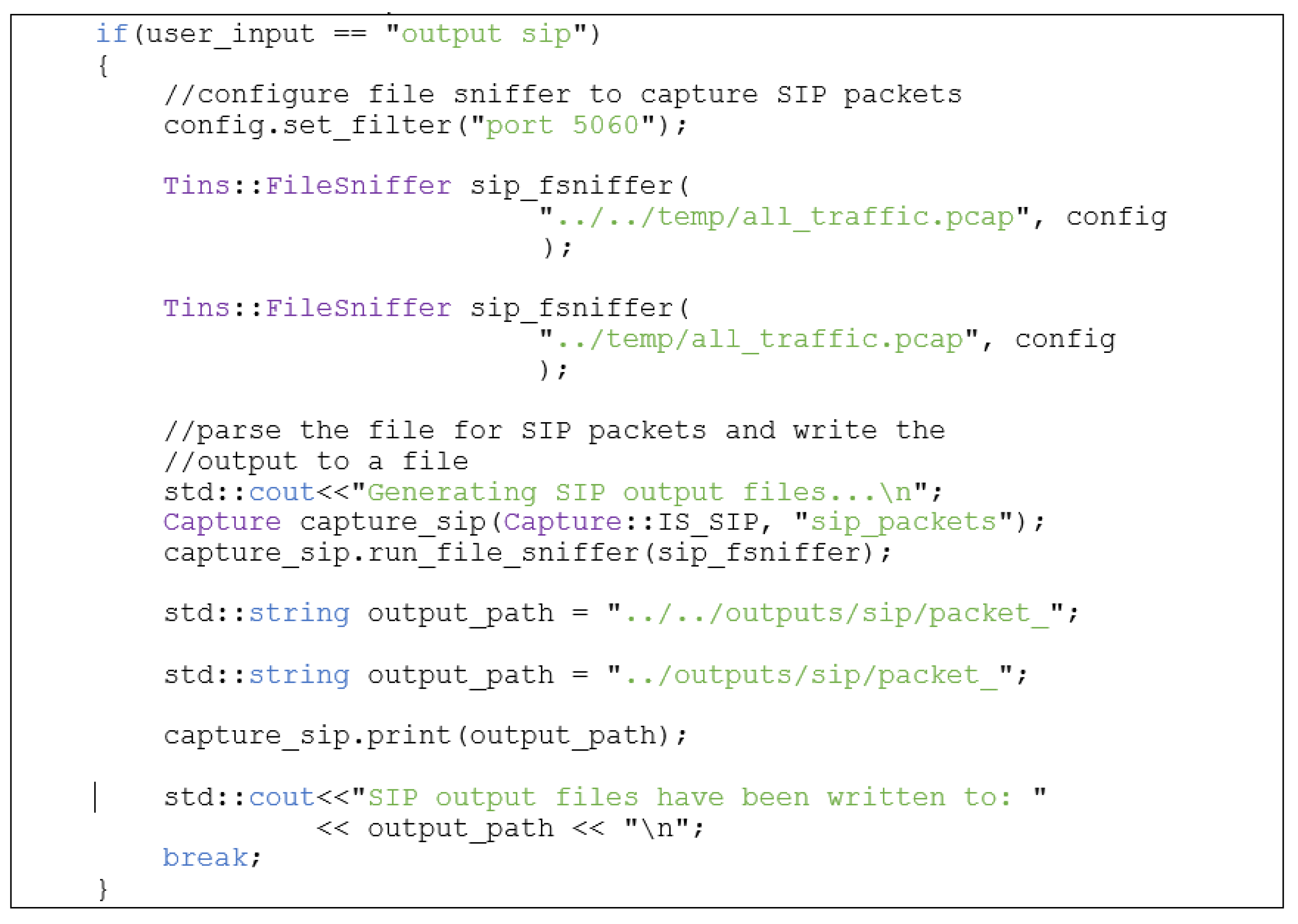
2.2.2. Implementing Custom Packet Capture Tool Using C/C++ and Libtins
- PacketCapture Class
- NetworkPacket structure
- JSON structure
- Utility functions
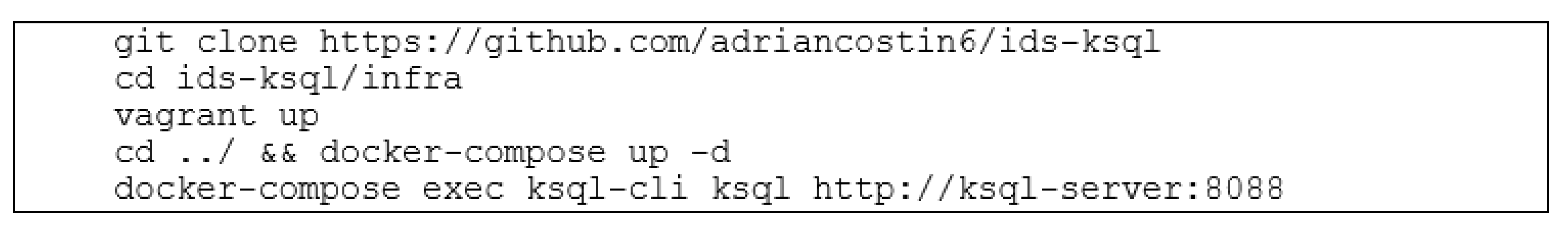
2.2.3. Integrating the Custom Sniffer into Ids-Ksql Project and Environment Configuration
- Forking ids-ksql
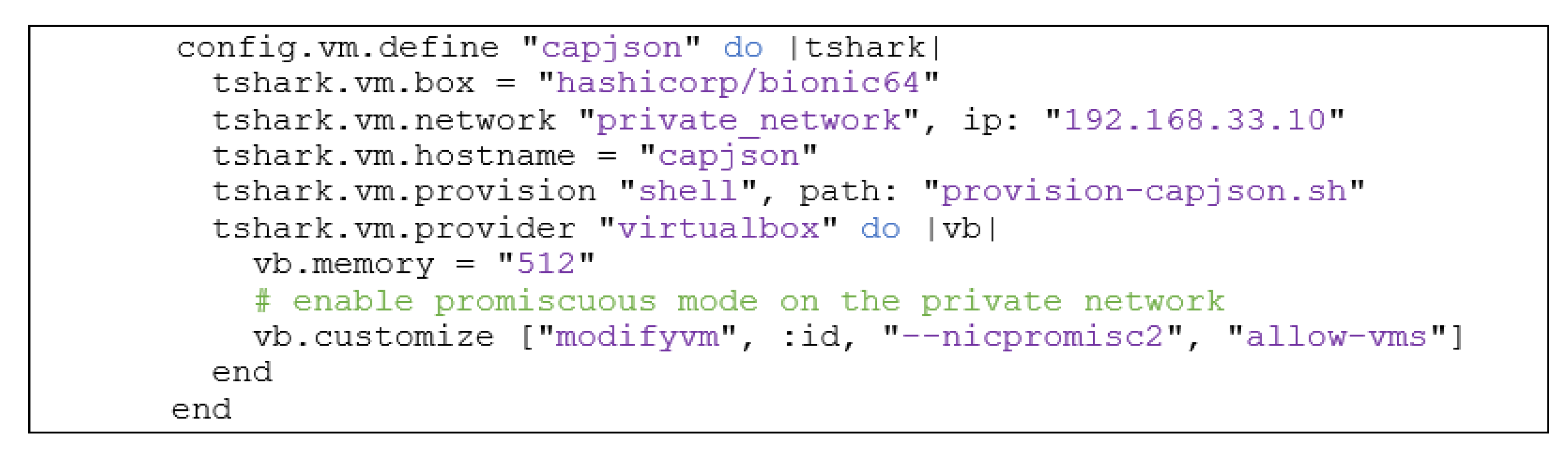
- Vagrant configuration
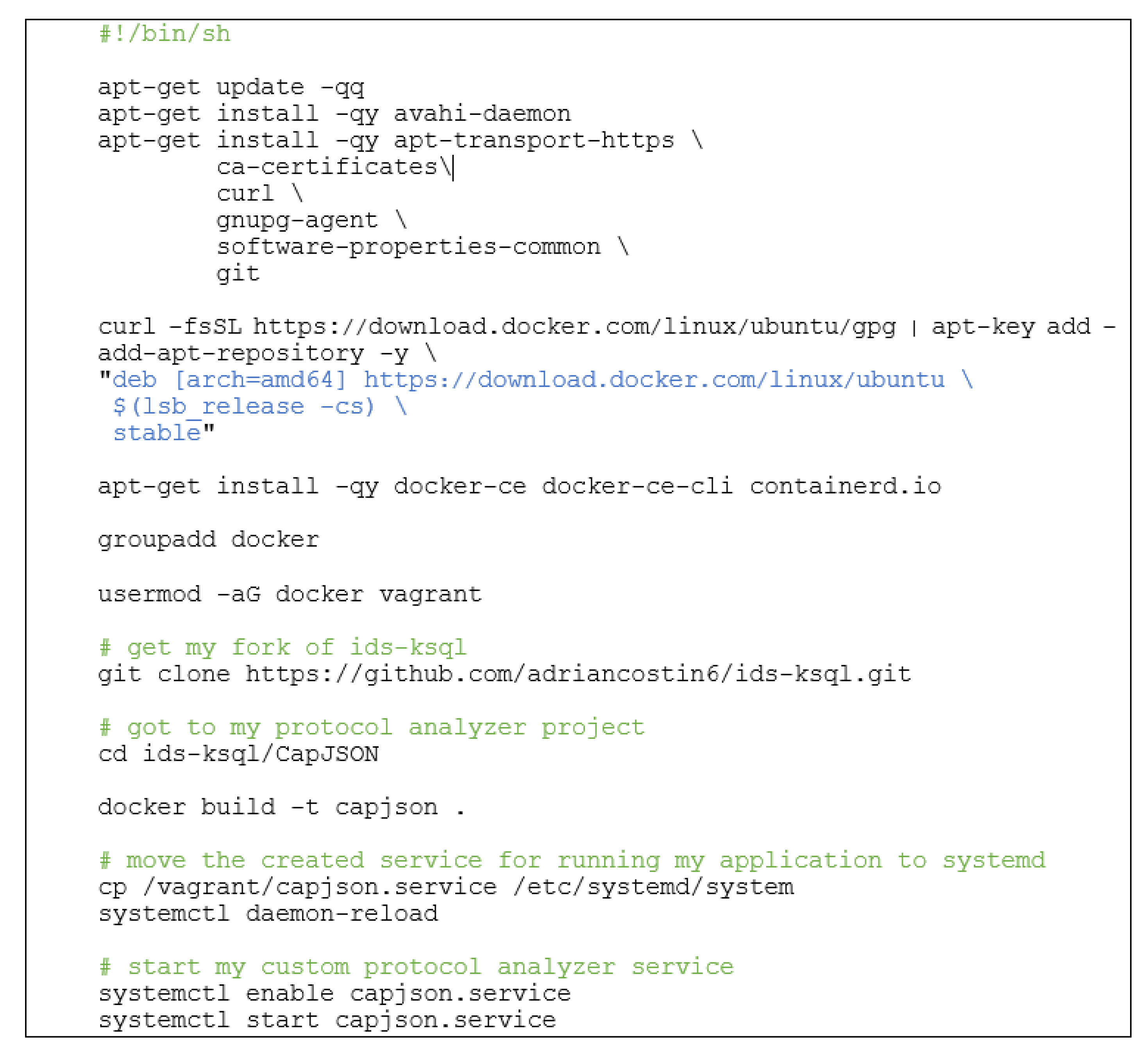
- Provisioning script
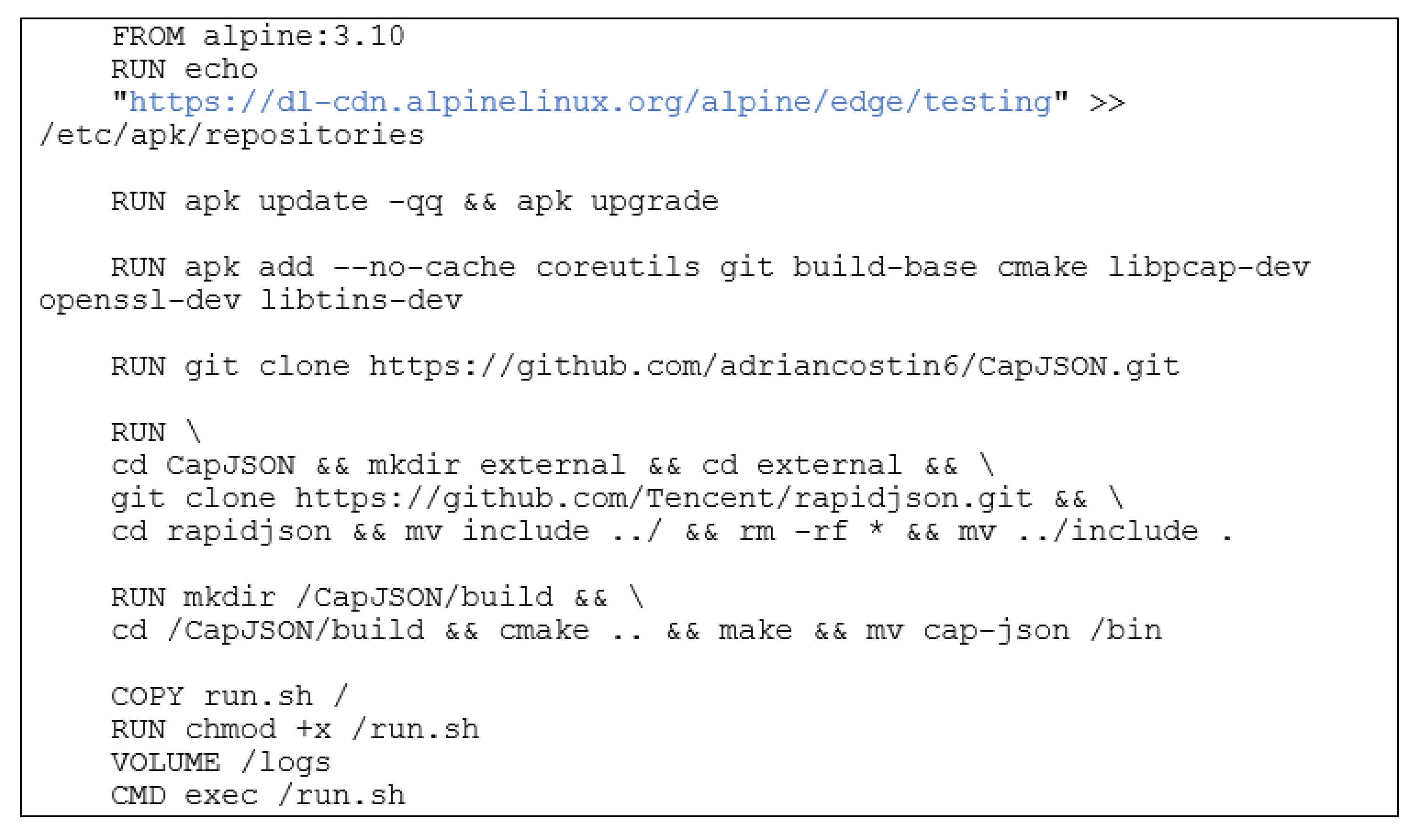
- Dockerfile for building the protocol analyzer
- Creating and configuring a service for the protocol analyzer
3. Results
3.1. Results for the SIP/RTP Packet Extractor
3.1.1. Performance
3.1.2. Capturing and Processing a VoIP Call
3.1.3. Processing a Large Number of SIP Packets
3.1.4. Processing a Large Number of RTP Packets
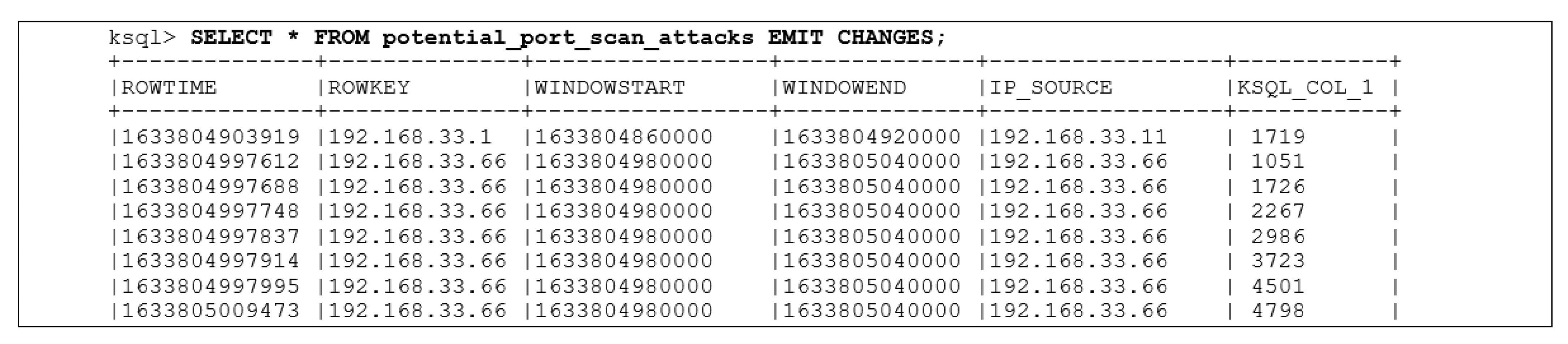
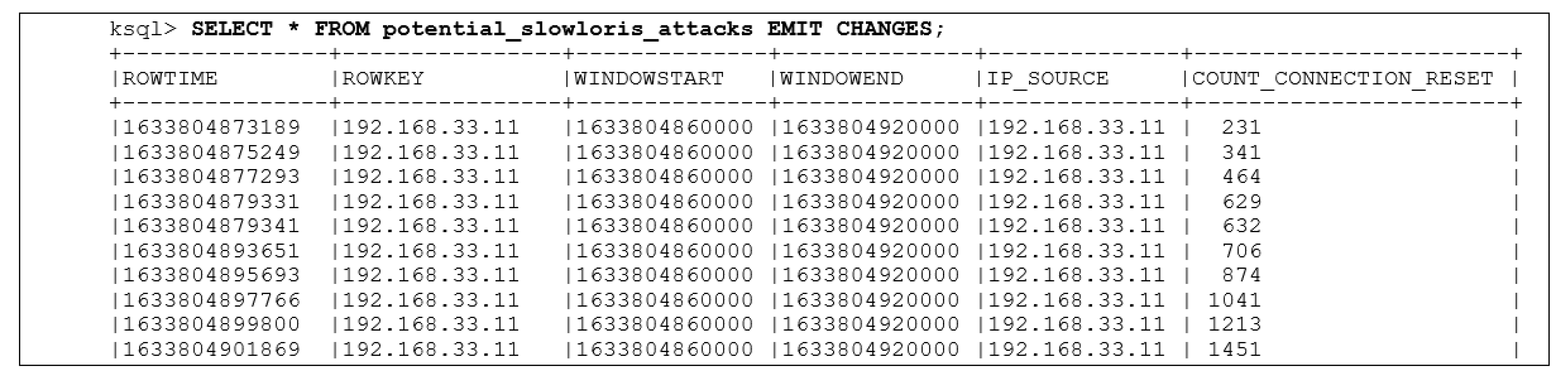
3.2. Results for the IDS
3.2.1. Running the Simulation
3.2.2. Resulting Output in Ksql Command-Line Interface
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Fontanini, M. Libtins (Version 4.2) [Source Code]. Available online: https://github.com/mfontanini/libtins (accessed on 5 September 2021).
- Libtins Documentation. Available online: https://libtins.github.io/tutorial/ (accessed on 5 September 2021).
- Sadrhaghighi, S.; Dolati, M.; Ghaderi, M.; Khonsari, A. SoftTap: A Software-Defined TAP via Switch-Based Traffic Mirroring. In Proceedings of the 2021 IEEE 7th International Conference on Network Softwarization (NetSoft), Tokyo, Japan, 28 June–2 July 2021; pp. 303–311. [Google Scholar] [CrossRef]
- Libpcap. Available online: https://www.tcpdump.org/ (accessed on 5 September 2021).
- Li, J.; Wu, C.; Ye, J.; Ding, J.; Fu, Q.; Huang, J. The Comparison and Verification of Some Efficient Packet Capture and Processing Technologies. In Proceedings of the 2019 IEEE International Conference on Dependable, Autonomic and Secure Computing, International Conference on Pervasive Intelligence and Computing, International Conference on Cloud and Big Data Computing, International Conference on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech), Fukuoka, Japan, 5–8 August 2019; pp. 967–973. [Google Scholar] [CrossRef]
- Bonelli, N.; Giordano, S.; Procissi, G. Enabling packet fan-out in the libpcap library for parallel traffic processing. In Proceedings of the 2017 Network Traffic Measurement and Analysis Conference (TMA), Dublin, Ireland, 21–23 June 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Vormayr, G.; Fabini, J.; Zseby, T. Why are My Flows Different? A Tutorial on Flow Exporters. IEEE Commun. Surv. Tutor. 2020, 22, 2064–2103. [Google Scholar] [CrossRef]
- Ivoševia, M.; Vranješ, M.; Pekoviű, V.; Kaprocki, Z. Client-side solution for QoS measurement of video content delivery over IP networks. In Proceedings of the 2018 IEEE 8th International Conference on Consumer Electronics—Berlin (ICCE-Berlin), Berlin, Germany, 2–5 September 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Zubow, A.; Zehl, S.; Wolisz, A. BIGAP—Seamless handover in high performance enterprise IEEE 802.11 networks. In Proceedings of the NOMS 2016—2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 445–453. [Google Scholar] [CrossRef]
- Morrell, C.; Ransbottom, J.S.; Marchany, R.; Tront, J.G. Scaling IPv6 address bindings in support of a moving target defense. In Proceedings of the 9th International Conference for Internet Technology and Secured Transactions (ICITST-2014), London, UK, 8–10 December 2014; pp. 440–445. [Google Scholar] [CrossRef]
- Ghazanfar, S.; Hussain, F.; Rehman, A.U.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT-Flock: An Open-source Framework for IoT Traffic Generation. In Proceedings of the 2020 International Conference on Emerging Trends in Smart Technologies (ICETST), Karachi, Pakistan, 26–27 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Costin, A.-T.; Zinca, D. Extending the libtins library with SIP and RTP classes. In Proceedings of the 2020 International Symposium on Electronics and Telecommunications (ISETC), Timisoara, Romania, 5–6 November 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Gruber, M.; Fankhauser, F.; Taber, S.; Schanes, C.; Grechenig, T. Trapping and analyzing malicious VoIP traffic using a honeynet approach. In Proceedings of the 2011 International Conference for Internet Technology and Secured Transactions, Abu Dhabi, United Arab Emirates, 11–14 December 2011; pp. 442–447. [Google Scholar]
- Aziz, A.; Hoffstadt, D.; Rathgeb, E.; Dreibholz, T. A distributed infrastructure to analyse SIP attacks in the Internet. In Proceedings of the 2014 IFIP Networking Conference, Trondheim, Norway, 2–4 June 2014; pp. 1–9. [Google Scholar] [CrossRef]
- Wireshark. Available online: https://www.wireshark.org/ (accessed on 5 September 2021).
- Chappell, L. Wireshark Network Analysis, 2nd ed.; Chappell University: Reno, Nevada, 2019; ISBN 978-1-893939-94-3. [Google Scholar]
- Barry, M.A.; Tamgno, J.K.; Lishou, C.; Cissé, M.B. QoS impact on multimedia traffic load (IPTV, RoIP, VoIP) in best effort mode. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Korea, 11–14 February 2018; pp. 694–700. [Google Scholar] [CrossRef]
- Pathania, N.; Singh, R.; Malik, A. Comparative Study of Audio and Video Chat Application Over the Internet. In Proceedings of the 2018 International Conference on Intelligent Circuits and Systems (ICICS), Phagwara, India, 19–20 April 2018; pp. 251–257. [Google Scholar] [CrossRef]
- François, J.; State, R.; Engel, T.; Festor, O. Digital forensics in VoIP networks. In Proceedings of the 2010 IEEE International Workshop on Information Forensics and Security, Seattle, WA, USA, 12–15 December 2010; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Langthasa, B.; Acharya, B.; Sarmah, S. Classification of network traffic in LAN. In Proceedings of the 2015 International Conference on Electronic Design, Computer Networks & Automated Verification (EDCAV), Shillong, India, 29–30 January 2015; pp. 92–99. [Google Scholar] [CrossRef]
- RFC 3261—SIP: Session Initiation Protocol. Available online: https://tools.ietf.org/html/rfc3261 (accessed on 5 September 2021).
- Carvajal, L.; Chen, L.; Varol, C.; Rawat, D. Detecting unprotected SIP-based voice over IP traffic. In Proceedings of the 2016 4th International Symposium on Digital Forensic and Security (ISDFS), Little Rock, AR, USA, 25–27 April 2016; pp. 44–48. [Google Scholar] [CrossRef]
- Moon, S. Packet Sniffer Code in C using Linux Sockets (BSD)-Part 2. 2020. Available online: https://www.binarytides.com/packet-sniffer-code-in-c-using-linux-sockets-bsd-part-2/ (accessed on 5 September 2021).
- Herculea, M.; Blaga, T.; Dobrota, V. Evaluation of Security and Countermeasures for a SIP-based VoIP Architecture. In Proceedings of the 7th RoEduNet International Conference “Networking in Education and Research”, Cluj-Napoca, Romania, 28–30 August 2008; pp. 34–39, ISBN 978-973-662-393-6. [Google Scholar]
- RFC 4566—SDP: Session Description Protocol. Available online: https://tools.ietf.org/html/rfc4566 (accessed on 5 September 2021).
- RFC 3550—RTP: A Transport Protocol for Real-Time Applications. Available online: https://tools.ietf.org/html/rfc3550 (accessed on 5 September 2021).
- De Bernonville, G.D.; Ribera, M. Intrusion Detection with ksqlDB. Available online: https://www.confluent.io/blog/build-a-intrusion-detection-using-ksqldb (accessed on 5 September 2021).
- Vagrant. Available online: https://www.vagrantup.com/intro (accessed on 5 September 2021).
- Apache Kafka. Available online: https://kafka.apache.org/ (accessed on 5 September 2021).
- Seymour, M. Mastering Kafka Streams and ksqlDB; O’Reilly Media Inc.: Sebastopol, CA, USA, 2021. [Google Scholar]
- Vyas, S.; Tyagi, R.K.; Jain, C.; Sahu, S. Literature Review: A Comparative Study of Real Time Streaming Technologies and Apache Kafka. In Proceedings of the 2021 Fourth International Conference on Computational Intelligence and Communication Technologies (CCICT), Sonepat, India, 3 July 2021; pp. 146–153. [Google Scholar] [CrossRef]
- Van Dongen, G.; Van den Poel, D. Evaluation of Stream Processing Frameworks. IEEE Trans. Parallel Distrib. Syst. 2020, 31, 1845–1858. [Google Scholar] [CrossRef]
- Nguyen, S.; Salcic, Z.; Zhang, X.; Bisht, A. A Low-Cost Two-Tier Fog Computing Testbed for Streaming IoT-Based Applications. IEEE Internet Things J. 2021, 8, 6928–6939. [Google Scholar] [CrossRef]
- Chen, C.; Cai, J.; Ren, N.; Cheng, X. Design and Implementation of Multi-tenant Vehicle Monitoring Architecture Based on Microservices and Spark Streaming. In Proceedings of the 2020 International Conference on Communications, Information System and Computer Engineering (CISCE), Kuala Lumpur, Malaysia, 3–5 July 2020; pp. 169–172. [Google Scholar] [CrossRef]
- Tidjon, L.N.; Frappier, M.; Mammar, A. Intrusion Detection Systems: A Cross-Domain Overview. IEEE Commun. Surv. Tutor. 2019, 21, 3639–3681. [Google Scholar] [CrossRef]
- ksqlDB. Available online: https://ksqldb.io/overview.html (accessed on 5 September 2021).
- Rocha, A.D.; Freitas, N.; Alemão, D.; Guedes, M.; Martins, R.; Barata, J. Event-Driven Interoperable Manufacturing Ecosystem for Energy Consumption Monitoring. Energies 2021, 14, 3620. [Google Scholar] [CrossRef]
- Chira, C.-M.; Portase, R.; Tolas, R.; Lemnaru, C.; Potolea, R. A System for Managing and Processing Industrial Sensor Data: SMS. In Proceedings of the 2020 IEEE 16th International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 3–5 September 2020; pp. 213–220. [Google Scholar] [CrossRef]
- Nokia. Available online: https://www.nokia.com/networks/solutions/voice-over-5g-vo5g-core/ (accessed on 30 November 2021).
- Di Mauro, M.; Liotta, A. An Experimental Evaluation and Characterization of VoIP Over an LTE-A Network. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1626–1639. [Google Scholar] [CrossRef]
- Biondi, P.; Bognanni, S.; Bella, G. VoIP Can Still Be Exploited—Badly. In Proceedings of the 2020 Fifth International Conference on Fog and Mobile Edge Computing (FMEC), Paris, France, 20–23 April 2020; pp. 237–243. [Google Scholar] [CrossRef]
- Costin, A.-T. VoIP-Analyzer [Source Code]. Available online: https://github.com/adriancostin6/VoIP-Analyzer (accessed on 5 September 2021).
- Costin, A.-T. Ids-Ksql (Fork) [Source Code]. Available online: https://github.com/adriancostin6/ids-ksql (accessed on 5 September 2021).
- Costin, A.-T. CapJSON [Source Code]. Available online: https://github.com/adriancostin6/CapJSON (accessed on 5 September 2021).
- Tencent, Rapidjson [Source Code]. Available online: https://github.com/Tencent/rapidjson (accessed on 5 September 2021).
- rapidjson Documentation. Available online: https://rapidjson.org/index.html (accessed on 9 September 2021).
- Zenika, Ids-Ksql [Source Code]. Available online: https://github.com/Zenika/ids-ksql (accessed on 5 September 2021).
- Watson, J. Eleven Best Packet Sniffers in 2021, Comparitech Limited. 2021. Available online: https://www.comparitech.com/net-admin/packet-sniffer-network-analyzers/ (accessed on 9 October 2021).






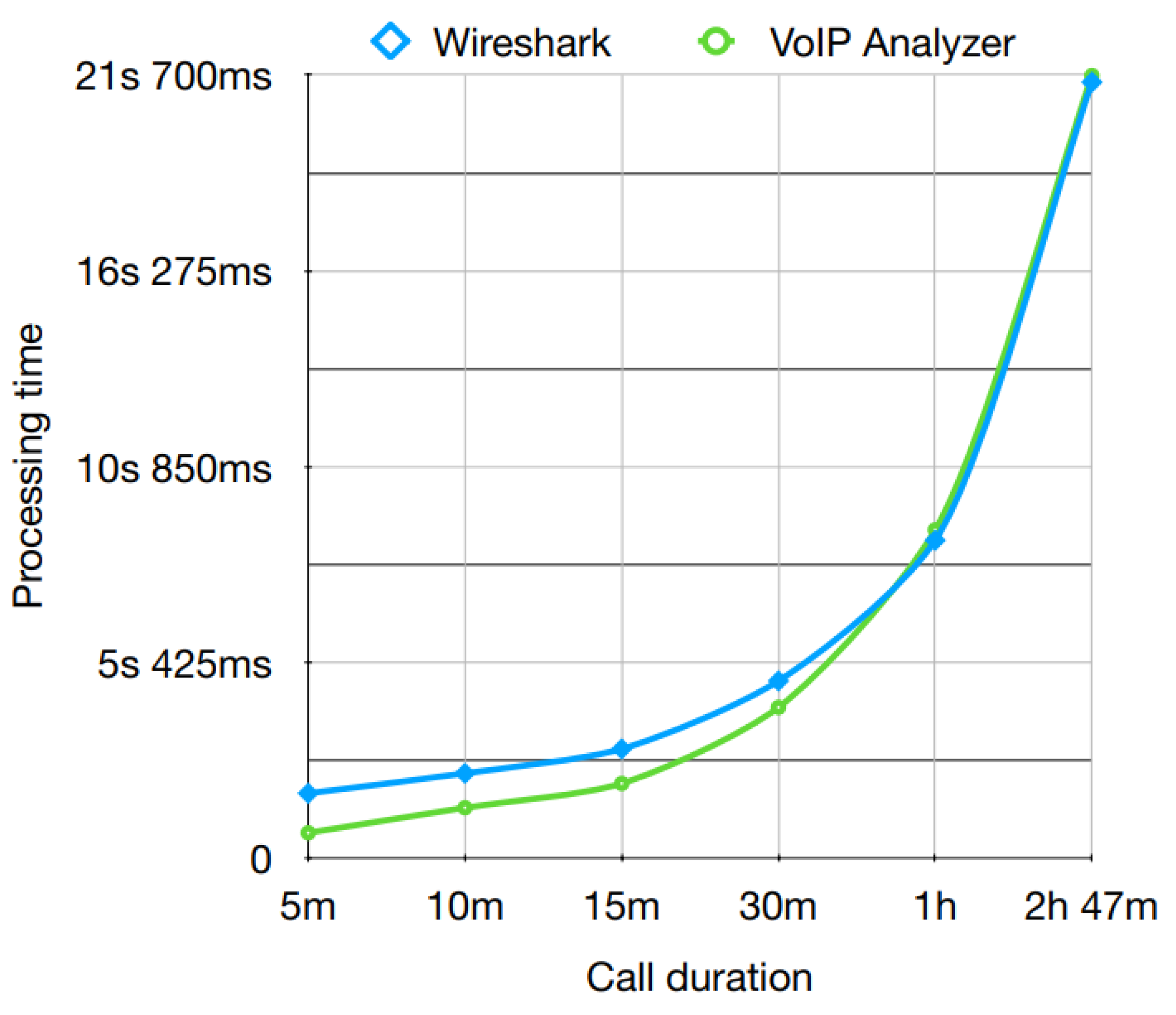
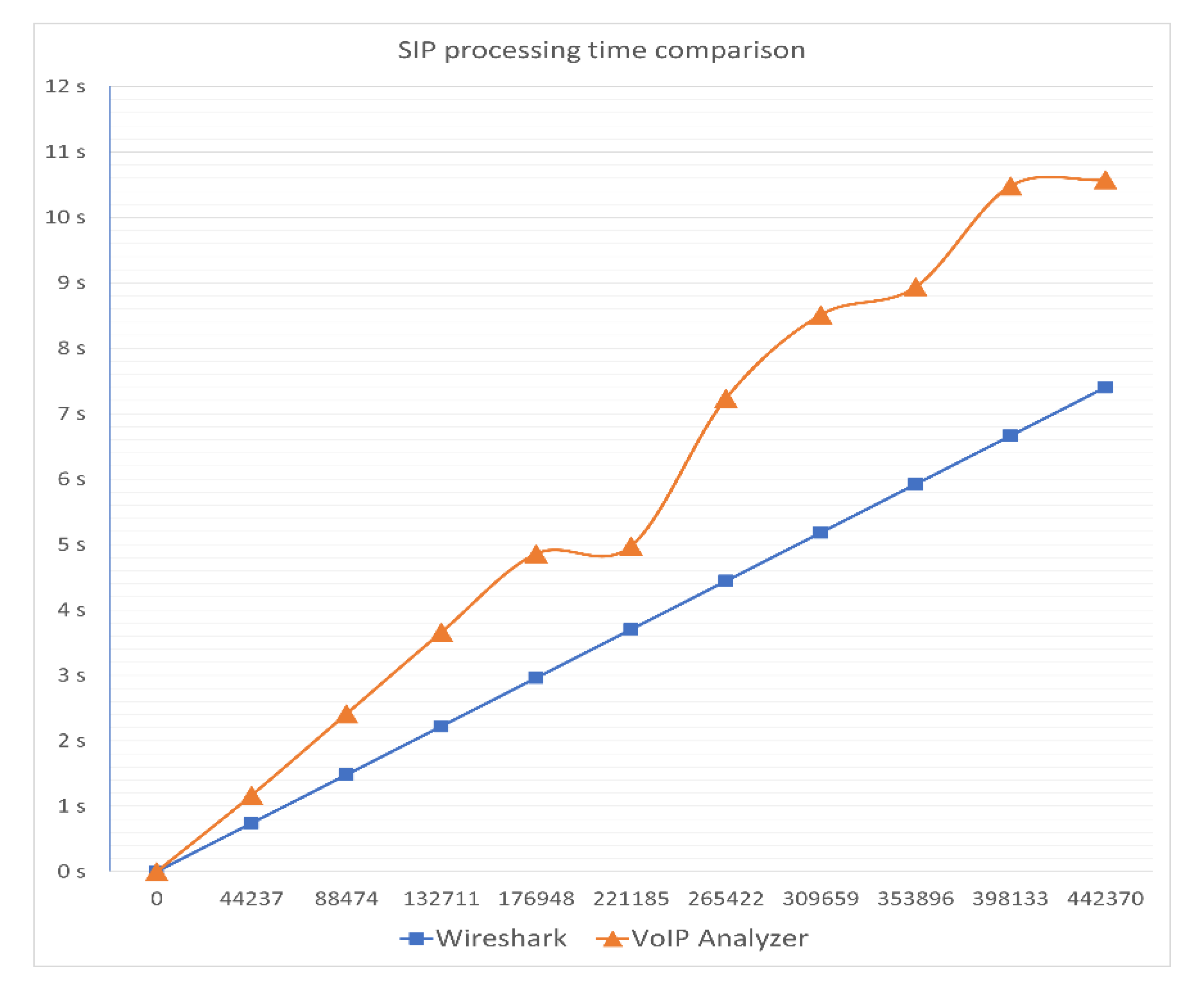
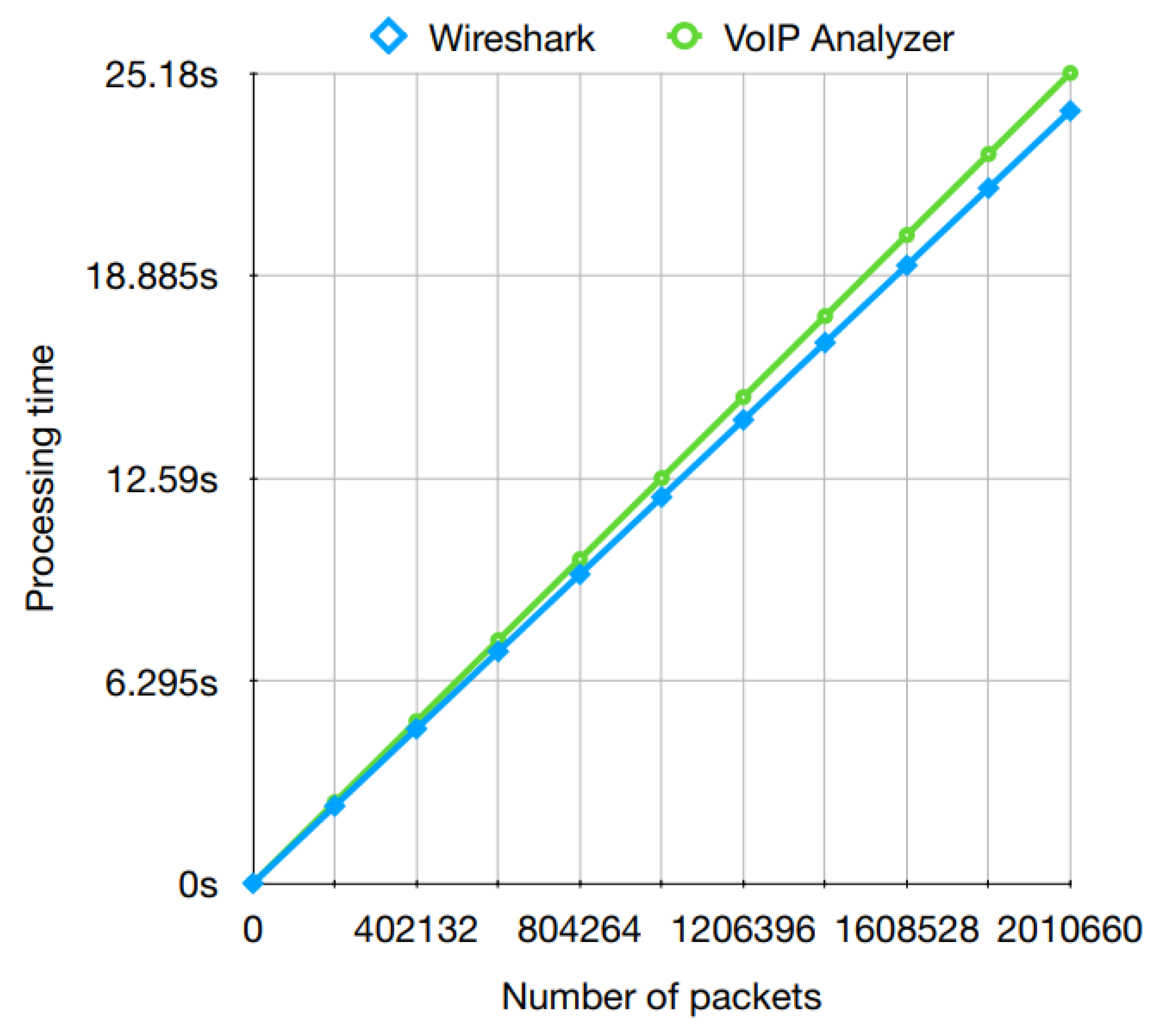
| Call Information | Processing Time (Milliseconds) | ||
|---|---|---|---|
| Duration (Minutes) | Number of Packets | Wireshark | VoIP Analyzer |
| 5 | 74,250 | 1785 | 689 |
| 10 | 147,144 | 2338 | 1384 |
| 15 | 220,309 | 3015 | 2057 |
| 30 | 454,741 | 4900 | 4167 |
| 60 | 882,308 | 8800 | 9089 |
| 167 | 2,460,609 | 21,505 | 21,688 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Costin, A.-T.; Zinca, D.; Dobrota, V. LAN Traffic Capture Applications Using the Libtins Library. Electronics 2021, 10, 3084. https://doi.org/10.3390/electronics10243084
Costin A-T, Zinca D, Dobrota V. LAN Traffic Capture Applications Using the Libtins Library. Electronics. 2021; 10(24):3084. https://doi.org/10.3390/electronics10243084
Chicago/Turabian StyleCostin, Adrian-Tiberiu, Daniel Zinca, and Virgil Dobrota. 2021. "LAN Traffic Capture Applications Using the Libtins Library" Electronics 10, no. 24: 3084. https://doi.org/10.3390/electronics10243084
APA StyleCostin, A.-T., Zinca, D., & Dobrota, V. (2021). LAN Traffic Capture Applications Using the Libtins Library. Electronics, 10(24), 3084. https://doi.org/10.3390/electronics10243084








