Lockit: A Logic Locking Automation Software
Abstract
:1. Introduction
- (1)
- It provides a comprehensive comparison of the state-of-the-art logic locking methods.
- (2)
- It develops a proof-of-concept logic locking automation tool compatible with the standard IC design process. The software is demonstrated to successfully obfuscate a gate-level netlist by locking one of its input cones using the SFLL-HD algorithm. The correct functionality of the tool was demonstrated in simulation and the tool succeeds in providing the same obfuscation level as in the algorithm specification.
- (3)
- It provides rigorous analysis of the tool’s performance and the overheads of the resulting netlist in terms of area, power usage, and critical path delay.
2. A Review of Logic Locking Algorithms and Related Attacks
2.1. Principles of Random Logic Locking
2.2. Sensitization Attacks on Random Logic Locking
- Isolated key gates—a key gate without a path to and from any other key gate. A key value of an isolated key gate can be propagated to the output by applying an appropriate input pattern on the unlocked IC.
- Runs of key gates—a set of key gates connected one to another (in a run). A run of key gates can be replaced by only one key gate.
- Dominating key gates—a dominating key gate lies on every path between another key gate and outputs. To determine the value of the dominating key gate, the attacker has to find an input pattern that sensitizes its value to the output and prevents the key value of a dominated key gate from being propagated.
- Concurrently mutable convergent key gates—two gates without a path between one another that converge at the third gate. Key values of both gates can be sensitized to output by muting the effect of the other key gate and the attacker has to find an input pattern that enables this situation.
- Sequentially mutable convergent key gates—two gates without a path between one another that converge at the third gate. The only key value of one gate can be sensitized to output by muting the effect of the other gate, while the reciprocal situation is not possible. The attacker finds the input pattern that unveils the key value of the first gate and replaces it with an inverter or a buffer depending on the determined key value before targeting the other key gate.
- Non-mutable convergent key gates—two gates without a path between one another that converge at the third gate and none of them can be muted to sensitize the other one’s value to the output. In this case, the attacker has to perform a brute force attack.
2.3. Principles of Fault Analysis-Based Logic Locking
2.4. Principles of Strong Logic Locking
2.5. SAT Attacks on Random Logic Locking
2.6. Principles of Cyclic Logic Locking
2.7. Principles of Anti-SAT
2.8. Principles of SARLock
2.9. Removal Attacks on SAT Resilient Techniques
2.10. Inter-Module SAT Techniques
2.11. Principles of Tenacious and Traceless Logic Locking
2.12. Principles of Stripped Functionality Logic Locking—Hamming Distance
2.13. Analysis of Algorithms
2.14. Analysis of Strategies
3. Automation of Logic Locking
3.1. Internal Structure of the Tool
- Parsing the input netlist and transforming it into a graph.
- Application of SFLL-HD on the graph.
- Transforming the resulting graph into the output netlist.
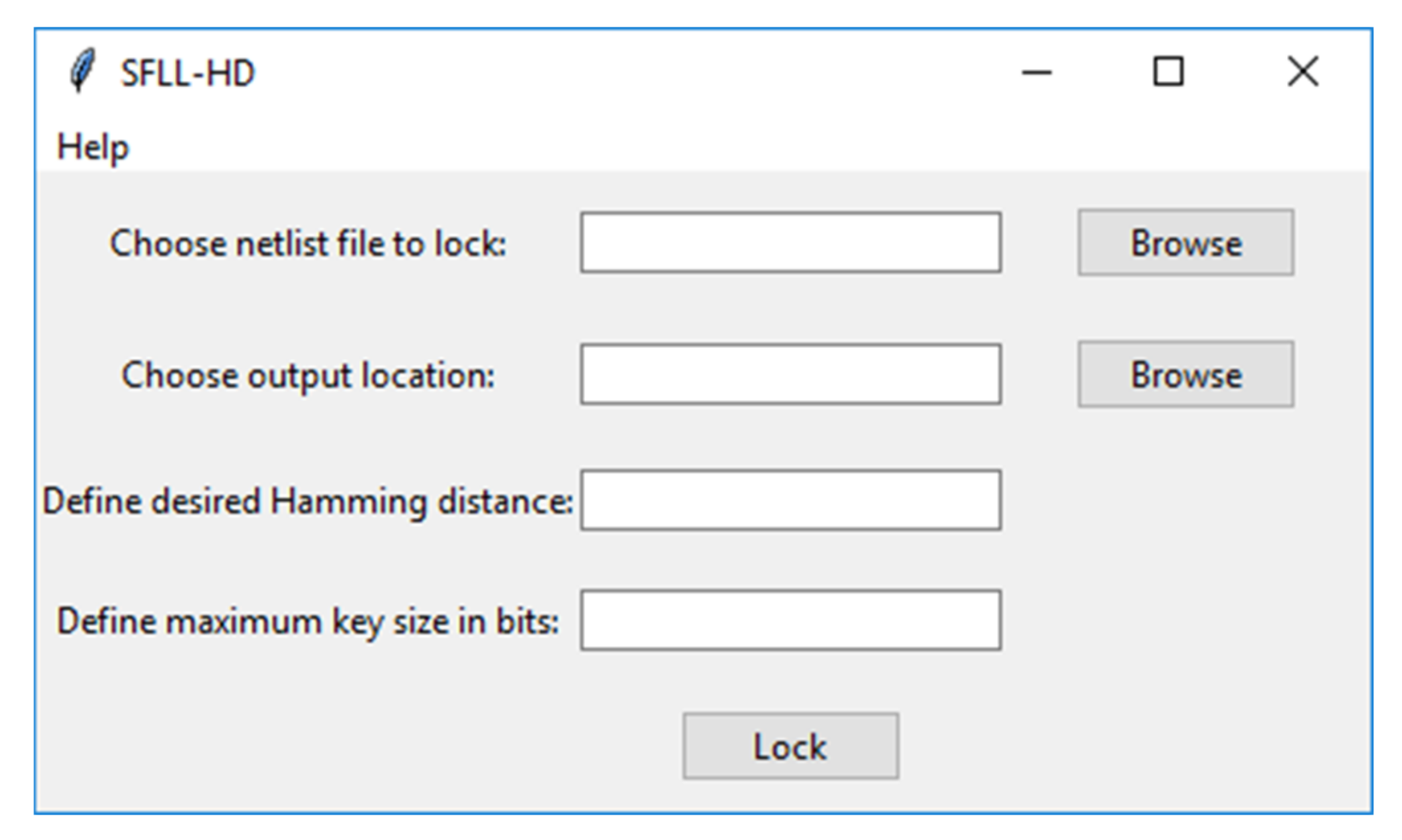
3.2. Graphical User Interface
3.3. Graph Representation
- Attribute type—indicates the node type (gate, state_el, input, output, or wire).
- Attribute gate (only for gates and state elements)—indicates the name of the actual gate from the library.
- Attribute pinout (only for gates and state elements)—a list containing information about the gate or register pins and the wire, input, or output it is connected to.
3.4. Technology
3.5. Netlist Parsing
3.6. Selection of an Input Cone to Lock
3.7. Key Generation
3.8. Functionality Strip
3.9. Functionality Restore
3.10. Gate Size Reduction
3.11. Technology Mapping of the Gates
3.12. Writing out the Locked Netlist
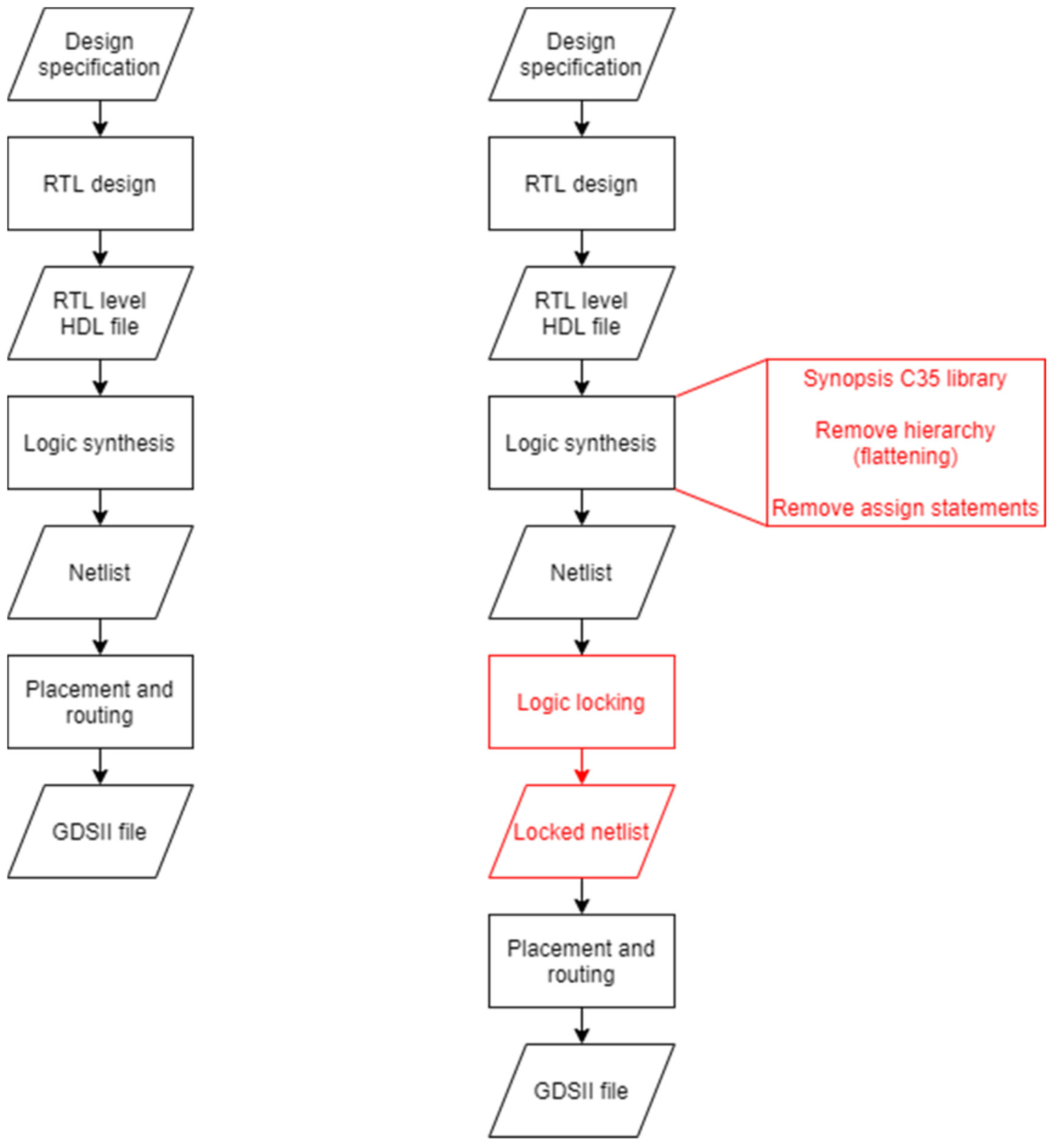
3.13. Integration of the Tool with the IC Design Process
4. Case Studies and Comparison of Overheads
4.1. Introduction
4.2. Computational Complexity and Performance Evaluation
4.3. Functional Verification
4.4. Security Evaluation
4.5. Comparison of Overheads
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Roy, J.A.; Koushanfar, F.; Markov, I.L. EPIC: Ending Piracy of Integrated Circuits. In Proceedings of the 2008 Design, Automation and Test in Europe, Munich, Germany, 10–14 March 2008; pp. 1069–1074. [Google Scholar]
- Chakraborty, R.S.; Bhunia, S. HARPOON: An Obfuscation-Based SoC Design Methodology for Hardware Protection. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2009, 28, 1493–1502. [Google Scholar] [CrossRef]
- Engels, S.; Hoffmann, M.; Paar, C. The End of Logic Locking? A Critical View on the Security of Logic Locking. IACR Cryptol. ePrint Arch. 2019, 2019, 796. [Google Scholar]
- Rajendran, J.; Pino, Y.; Sinanoglu, O.; Karri, R. Security analysis of logic obfuscation. In Proceedings of the 49th Annual Design Automation Conference on—DAC’12, San Francisco, CA, USA, 3–7 June 2012; pp. 83–89. [Google Scholar]
- Rajendran, J.; Zhang, H.; Zhang, C.; Rose, G.; Pino, Y.; Sinanoglu, O.; Karri, R. Fault Analysis-Based Logic Encryption. IEEE Trans. Comput. 2013, 64, 410–424. [Google Scholar] [CrossRef]
- Subramanyan, P.; Ray, S.; Malik, S. Evaluating the security of logic encryption algorithms. In Proceedings of the 2015 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 5–7 May 2015; pp. 137–143. [Google Scholar]
- Shamsi, K.; Li, M.; Meade, T.; Zhao, Z.; Pan, D.Z.; Jin, Y. Cyclic Obfuscation for Creating SAT-Unresolvable Circuits. In Proceedings of the Great Lakes Symposium on VLSI 2017, Banff, AB, Canada, 10 May 2017; pp. 173–178. [Google Scholar]
- Zhou, H.; Jiang, R.; Kong, S. CycSAT: SAT-based attack on cyclic logic encryptions. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; pp. 49–56. [Google Scholar]
- Xie, Y.; Srivastava, A. Anti-SAT: Mitigating SAT Attack on Logic Locking. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2018, 38, 199–207. [Google Scholar] [CrossRef]
- Yasin, M.; Mazumdar, B.; Rajendran, J.J.V.; Sinanoglu, O. SARLock: SAT attack resistant logic locking. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 236–241. [Google Scholar]
- Yasin, M.; Mazumdar, B.; Sinanoglu, O.; Rajendran, J. Security analysis of Anti-SAT. In Proceedings of the 2017 22nd Asia and South Pacific Design Automation Conference (ASP-DAC), Chiba, Japan, 16–19 January 2017; pp. 342–347. [Google Scholar]
- Yasin, M.; Mazumdar, B.; Sinanoglu, O.; Rajendran, J. Removal Attacks on Logic Locking and Camouflaging Techniques. IEEE Trans. Emerg. Top. Comput. 2020, 8, 517–532. [Google Scholar] [CrossRef] [Green Version]
- Yasin, M.; Sengupta, A.; Schafer, B.C.; Makris, Y.; Sinanoglu, O.; Rajendran, J. What to Lock? Functional and Parametric Locking. In Proceedings of the Great Lakes Symposium on VLSI 2017, Banff, AB, Canada, 10 May 2017. [Google Scholar]
- Yasin, M.; Sengupta, A.; Nabeel, M.T.; Ashraf, M.; Rajendran, J.; Sinanoglu, O. Provably-Secure Logic Locking: From Theory to Practice. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October 2017. [Google Scholar]
- Yasin, M.; Zhao, C.; Rajendran, J.J. SFLL-HLS: Stripped-Functionality Logic Locking Meets High-Level Synthesis. In Proceedings of the 2019 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019; pp. 1–4. [Google Scholar]
- Pilato, C.; Chowdhury, A.B.; Sciuto, D.; Garg, S.; Karri, R. ASSURE: RTL Locking Against an Untrusted Foundry. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2021, 29, 1306–1318. [Google Scholar] [CrossRef]
- Šišejković, D.; Merchant, F.; Reimann, L.M.; Leupers, R.; Kegreiß, S. Scaling Logic Locking Schemes to Multi-module Hardware Designs. In International Conference on Architecture of Computing Systems; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2020; pp. 138–152. [Google Scholar]
- Chakraborty, P.; Cruz, J.; Bhunia, S. SAIL: Machine Learning Guided Structural Analysis Attack on Hardware Obfuscation. In Proceedings of the 2018 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Hong Kong, China, 17–18 December 2018; pp. 56–61. [Google Scholar]
- Alaql, A.; Forte, D.; Bhunia, S. Sweep to the Secret: A Constant Propagation Attack on Logic Locking. In Proceedings of the 2019 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Xi’an, China, 16–17 December 2019; pp. 1–6. [Google Scholar]
- Šišejković, D.; Merchant, F.; Reimann, L.M.; Leupers, R.; Giacometti, M.; Kegreiß, S. A secure hardware-software solution based on RISC-V, logic locking, and microkernel. In Proceedings of the 23rd International Workshop on Software and Compilers for Embedded Systems, St. Goar, Germany, 25 May 2020; pp. 62–65. [Google Scholar]
- Sisejkovic, D.; Merchant, F.; Leupers, R.; Ascheid, G.; Kegreiss, S. Inter-Lock: Logic Encryption for Processor Cores Beyond Module Boundaries. In Proceedings of the 2019 IEEE European Test Symposium (ETS), Baden-Baden, Germany, 27–31 May 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Šišejković, D.; Merchant, F.; Leupers, R.; Ascheid, G.; Kegreiss, S. Control-lock: Securing processor cores against software-controlled hardware trojans. In Proceedings of the 2019 on Great Lakes Symposium on VLSI, Tysons Corner, VA, USA, 13 May 2019; pp. 27–32. [Google Scholar]
- Sisejkovic, D.; Merchant, F.; Leupers, R.; Ascheid, G.; Kiefer, V. A Critical Evaluation of the Paradigm Shift in the Design of Logic Encryption Algorithms. In Proceedings of the 2019 International Symposium on VLSI Design, Automation and Test (VLSI-DAT), Hsinchu, Taiwan, 22–25 April 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Yang, F.; Tang, M.; Sinanoglu, O. Stripped Functionality Logic Locking With Hamming Distance-Based Restore Unit (SFLL-hd)—Unlocked. IEEE Trans. Inf. Forensics Secure. 2019, 14, 2778–2786. [Google Scholar] [CrossRef]
- Sirone, D.; Subramanyan, P. Functional Analysis Attacks on Logic Locking. IEEE Trans. Inf. Forensics Secure. 2020, 15, 2514–2527. [Google Scholar] [CrossRef] [Green Version]
- Duvalsaint, D.; Jin, X.; Niewenhuis, B.; Blanton, R.D. Characterization of Locked Combinational Circuits via ATPG. In Proceedings of the 2019 IEEE International Test Conference (ITC), Washington, DC, USA, 9–15 November 2019; pp. 1–10. [Google Scholar]
- Halak, B. Lockit: A Logic Locking Tool. Available online: https://www.researchgate.net/publication/353195333_Source_Code_for_The_Lockit_Tool (accessed on 13 September 2021).

























| Algorithm | Sensitization Attack Resilience | SAT Attack Resilience | Removal Attack Resilience | Corruptibility |
|---|---|---|---|---|
| Random | No | No | Yes | High |
| Fault-based | No | No | Yes | Highest |
| SLL | Yes | No | Yes | High |
| Cyclic | Yes | Yes | Yes | High |
| Anti-SAT | Yes | Yes | No | Low |
| SARLock | Yes | Yes | No | Low |
| TTL | Yes | Yes | Yes | Low |
| SFLL-HD | Yes | Configurable | Configurable | Configurable |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kajtez, N.; Zhang, Y.; Halak, B. Lockit: A Logic Locking Automation Software. Electronics 2021, 10, 2817. https://doi.org/10.3390/electronics10222817
Kajtez N, Zhang Y, Halak B. Lockit: A Logic Locking Automation Software. Electronics. 2021; 10(22):2817. https://doi.org/10.3390/electronics10222817
Chicago/Turabian StyleKajtez, Nemanja, Yue Zhang, and Basel Halak. 2021. "Lockit: A Logic Locking Automation Software" Electronics 10, no. 22: 2817. https://doi.org/10.3390/electronics10222817
APA StyleKajtez, N., Zhang, Y., & Halak, B. (2021). Lockit: A Logic Locking Automation Software. Electronics, 10(22), 2817. https://doi.org/10.3390/electronics10222817






