1. Introduction
The increasing demand of high data rates on future communication systems leads to more complex signal processing hardware and more energy consumption. Green communication will play an increasing role in future communication networks. The radio signal enabled energy harvesting (EH) technology has drawn great interest in recent years. In simultaneous wireless information and power transfer (SWIPT) systems, the radio frequency signal plays a role in both information transmission and energy transfer [
1,
2,
3,
4,
5].
Recently, intelligent reflecting surfaces (IRS), a planar array composed of a great number of reconfigurable elements, is regarded as a potential solution for achieving higher efficiency of both the energy and spectrum for the future communication systems, and has been proposed and studied in [
6,
7]. A sufficient survey on the topic of IRS can be found in [
6]. The IRS passively reflects the RF signals with programmable phase shifts of the reflecting elements. By adaptively tuning the phase shifts, the IRS can help to strengthen the desired signals or suppress the undesired signals. Therefore, the beamforming vector at the source can be jointly optimized with the passive reflection coefficients of the IRS to improve, e.g., the signal to noise ratio (SNR) at the receiver for the multiple-input single-output (MISO) channel [
7].
The IRS has recently been considered as a new technology for 6G [
8,
9]. As one of the requirements for 6G is to support air-to-ground communications, the IRS can be deployed to extend the coverage of the cellular networks to the aerial users (AUs) and improve the air-ground communication network performance [
9]. Another promising technology for 6G is the Terahertz (THz) communication. However, the THz signals are readily blocked by obstacles, which leads to communication interruption. The IRS can be explored in the 6G system to assist the THz system [
10,
11]. The fundamental limit of the capacity of an IRS-assisted multiple-input multiple-output (MIMO) channel was characterized by jointly optimizing the transmit covariance matrix and the IRS reflection coefficients in [
12]. Assuming the channels were frequency-selective, the authors in [
13] studied an IRS-enhanced orthogonal frequency division multiplexing (OFDM) system, in which the IRS elements were grouped, and a practical channel estimation transmission protocol was proposed to reduce the training overhead. Based on the grouping method, the achievable rate was maximized by jointly optimizing the IRS reflection coefficients and the transmit power allocation.
Furthermore, the efficient beamforming gain of the IRS not only benefits the information transmission but is also appealing for the wireless power transfer. By optimizing the energy transfer beamforming vector and the reflecting coefficients of the IRS, the RF signal attenuation of long-distance can be compensated; thus, the efficiency of the RF-enabled wireless energy transfer can be increased. In [
14], an IRS-assisted SWIPT system was considered, where an access point (AP) served several information-receiving users and several EH receivers. The weighted sum-power maximization problem under the individual SINR constraints for the information decoding receivers was proposed, and a sub-optimal solution was derived. In particular, it was sufficient that the AP transmits only the information signals while satisfying both the information transmission and energy transfer requirements. Similar to the problem considered in [
14], the authors in [
15] considered an IRS-assisted SWIPT system assuming the information-receiving users and the EH receivers are equipped with multiple antennas. The weighted sum rate was maximized by jointly optimizing the transmit precoding matrices at the AP and the passive phase shift matrix at the IRS. A more general IRS-assisted SWIPT system was considered in [
16], where the energy transfer and information transmission from an AP to multiple energy and information users were assisted by deploying multiple IRSs. A penalty-based optimization method was proposed to solve the joint optimization problem of transmitting precoders and reflecting phase shifts at all IRSs.
However, due to the open nature of the wireless channel, the security problem presents a serious threat to the confidential information transmission in the SWIPT system [
17]. Most of the existing works focusing on the physical security layer of the SWIPT systems can be divided into two classes: (1) maximizing the achievable secrecy rate, while the minimum harvested energy requirements are satisfied at the EH receiver [
18]; (2) maximizing the energy harvested at the EH receiver, while the achievable secrecy rate of the legitimate users must be larger than the minimum requirement [
19,
20]. In previous work, considering physical layer security, transmit beamforming vectors were designed to maximize the SNR at the legitimate receivers and keep the SNR at the eavesdroppers as small as possible. However, if the wiretap channel of the eavesdropper is highly correlated with the main channel of the legitimate users, the SNR at the eavesdropper may also be increased with the beamforming vectors designed to maximize the SNR of the legitimate receiver. When the IRSs are deployed, due to the configurable reflection coefficients of the IRS, as mentioned above, we can jointly design information beamforming vectors and the reflection coefficients such that the SNR at the legitimate receiver is increased and the SNR at the eavesdropper is suppressed. Thus, the secrecy performance can be improved. In [
21,
22], an IRS-assisted secure wireless communication was considered, assuming the eavesdropping channel was correlated with the legitimate channel and was stronger than the legitimate channel. An IRS-aided MISO broadcast system with multiple eavesdroppers was considered in [
23], where a minimum-secrecy rate maximization problem was formulated under practical constraints on the reflecting coefficients of the IRS. The authors in [
24,
25] considered an IRS-assisted MISO wiretap channel and an IRS-assisted MIMO multi-antenna-eavesdropper (MIMOME) wiretap, respectively. In the former scenario, the secrecy rate under a delay-limited quality-of-service (QoS) was maximized by optimizing the beamforming vector at the transmitter and the phase shifts at the IRS. In the latter scenario, the input covariance matrix and the IRS phase shifts were jointly optimized to maximize the secrecy rate. Iterative optimizations were proposed to solve the optimization problems, and numerical results were shown to demonstrate the superiority of the proposed methods. The work in [
26,
27,
28] considered the IRS-assisted SWIPT systems in the MISO channels with external eavesdropper(s) assuming a different number of energy-harvesting receivers, eavesdroppers, or IRSs, respectively. Different methods were proposed to solve the secrecy rate maximization problems. The secrecy rate maximization problem for an IRS aided MIMO channel with SWIPT was considered in [
29], assuming all nodes were equipped with multiple antennas. Xue et al. [
30] proposed a hybrid scheme to jointly optimize the hybrid precoders of the transceiver and phase shift of the IRS to maximize the secrecy in the mmWave MIMO system with SWIPT.
In this paper, we consider an IRS-assisted SWIPT system with an external EH eavesdropper. The multi-antenna AP transfers energy to the single-antenna EH receiver and simultaneously transmits confidential information to the legitimate information receiver. The EH receiver is also a potential eavesdropper. The confidential information should be kept as secret as possible from the eavesdropper.
We aim at maximizing the achievable secrecy rate of legitimate users, while satisfying the minimum harvested energy requirements at the EH receiver. Specifically, we jointly optimize the energy transfer beamforming vector and the information transmit beamforming vector at the AP and phase shift matrix of the IRS. This is a non-convex optimization problem, which is hard to solve directly. To solve this non-convex optimization problem, we introduce the semi-definite relaxation (SDR) method and alternating optimization (AO) approaches to convert the original optimization problem to a series of semi-definite programs (SDPs), which are solved iteratively. Numerical results are then presented to show the achievable secrecy rate performance of the IRS-assisted SWIPT system. The main contributions of this paper are summarized as follows:
(1) The IRS-assisted SWIPT system—where the energy harvesting receiver is simultaneously a potential eavesdropper—was considered to show the possible application of the IRS in wireless energy transfer and secrecy information transmission.
(2) A joint optimization problem was designed to optimize the active and passive beamforming. The AO algorithm is proposed to iteratively solve the optimization problem by optimizing the active beamforming vectors and the phase shift matrix.
(3) We also show that when information should be kept secret to the energy harvesting receiver, a dedicated energy beam should be designed, which is different to that in the IRS-assisted SWIPT system without eavesdroppers.
The organization of the rest of the paper is as follows. The system model and problem formulation are presented in
Section 2. The solution to the optimization problem is given in
Section 3. In
Section 4, we present the numerical results.
Section 5 concludes the paper.
Notations: Scalars, vectors, and matrices are denoted by italic letters, bold-face lower-case letters, and bold-face upper-case letters, respectively. The Euclidean norm of a complex-valued vector is denoted by . The notation denotes a diagonal matrix with each diagonal element being the corresponding element in , and is a vector, each element of which is the phase of the corresponding element in . The space of complex-valued matrices is denoted by . Tr() and means the trace and inverse of a square matrix . means the matrix is positive and semi-definite. The conjugate, transpose, and rank of any matrix are denoted by , , and rank(), respectively.
3. Solution to the Secrecy Rate Maximization Problem
The problem (P1) is a non-convex optimization problem, since the beamforming vectors and are in quadratic terms and the optimization variables involved are coupled. In addition, the objective function, which is the difference of two logarithmic functions, is a non-convex one. It is hard to solve this optimization problem directly. In this paper, we introduce an SDR-based algorithm to convert the original optimization problem (P1) to SDPs and apply an alternating optimization approach to solve the SDPs by optimizing the phase shift matrix and the beamforming vectors ( and ) iteratively with the other fixed.
First, as shown in [
31], there always exists a constraint
such that the following problem,
has the same optimal solution as (P1), where
is a slack variable introduced to avoid the non-convexity caused by the differences of two logarithmic functions of the objective function and the third constraint is introduced to restrict the maximum allowable information leaked to the EH Eve. For any given
, let the optimal solution to the optimization problem (P2) be denoted by
. Then the optimal value of the original optimization problem is (P1)
. Therefore, by a one-dimensional search over
, the maximum secrecy rate
can be derived, where
is determined by:
where
,
and
is the
n-th column vector of the matrix
, the second inequality is due to the facts that
and
.
Next, we turn to solve the problem (P2). The AO approach is applied to solve problem (P2) by iteratively optimizing the phase shift matrix
, and the beamforming vectors
and
. First, for any fixed
, we employ the SDR-based algorithm [
32] to solve the problem (P2). Defining
and
, the optimization problem (P2) is re-expressed as:
where
and
. The rank-one constraints
and
are omitted. However, as proved in [
32],
and
always hold at the optimum of problem (P3) for any fixed
. The proof is omitted here for brevity.
The problem (P3) is now a linear fractional optimization problem. We use the Charnes-Cooper transformation [
33] to transform the problem (P3) to an SDP. Introducing an auxiliary variable
, defining the transformation
and
, and utilizing the Charnes-Cooper transformation, we have:
The equivalence between the problems (P2) and (P4) for any fixed
and
can be easily established. The problem (P4) is a semi-definite program and can be solved by the numerical solver CVX [
34].
In the following steps, we optimize the problem (P2) over the phase shift matrix for any fixed active beamforming vectors. Again, let
where
. The involved expressions in (
9) are re-expressed as
and
. Thus, we have
where
and
. Similarly, we have
,
and
where
,
,
,
,
and
. With these definitions, we further define
,
,
,
,
. For any given beamforming vectors
and
, the problem (P2) is equivalent to:
We employ the SDR-based algorithm [
32] to solve the problem (P5). Defining
, the optimization problem (P5) is re-expressed as:
The constraint
is omitted. The problem (P6) is a linear fractional program. Taking similar steps as problem (P4), defining the transformation
, and utilizing the Charnes-Cooper transformation [
33], we have:
The problem (P7) is an SDP and can be solved optimally by a numerical solver such as the CVX [
34]. However, the relaxed constraint
may not be satisfied in general. In order to derive a rank-one solution from the optimal solution to problem (P7), the Gaussian randomization method, as shown in [
7], was used, and the main steps are as follows. First, the optimal solution
to the problem (P7) is the eigenvalue decomposed as
. A sub-optimal solution to (P5) is constructed as
where
is a Gaussian variable satisfying
with zero meaning and covariance matrix
. Accordingly, the sub-optimal solution to the problem (P2) for any fixed beamforming vectors
and
is
, where
, the function ang
means the angle of the complex variable
x. Independently generating the random vector
a sufficiently large number of times, the vector
, which achieves the maximal value of the problem (P2) is selected as the solution to (P5) for any fixed
and
.
Finally, with the solutions to problems (P4) and (P7), problem (P2) for any fixed can be solved via alternating optimizations, in which problems (P4) and (P7) are solved iteratively until the convergence. By a one-dimensional search over , with methods such as the bisection golden search, the optimal value can be achieved. The AO algorithm is summarized in Algorithm 1.
Next, we discuss the convergence of the proposed AO algorithm. The AO algorithm, as shown in Algorithm 1, can be shown to converge as follows. Denote the objective function of the problem (P2) by
. For any given
, the solution to (P2) is derived by solving problem (P4) and (P7) iteratively. It follows that:
where the first inequality comes from (
12) since
and
correspond to the maximizer of
and the second inequality comes from (
15) due to a similar reason.
Since the proposed optimal scheme is based on SDP, its computational complexity of each iteration critically depends on the size and number of the constraints and variables. The total size and number of the constraints and variables of the problems (P4) and (P7) of each iteration are shown in
Table 1.
| Algorithm 1: Alternating optimization |
- 1:
Initialzation: - 2:
Set - 3:
repeat - 4:
Set - 5:
With given , solve problem (P4) to derive and , find the eigenvectors corresponding to the largest eigenvalues of and respectively, and denote them by , , , respectively. - 6:
Set , - 7:
With given and , solve problem (P7) to derive , and let the eigenvalue decomposition of be . - 8:
Applying Gaussian randomization method to derive . - 9:
Set . - 10:
Set according to (7). - 11:
until
|
4. Numerical Results
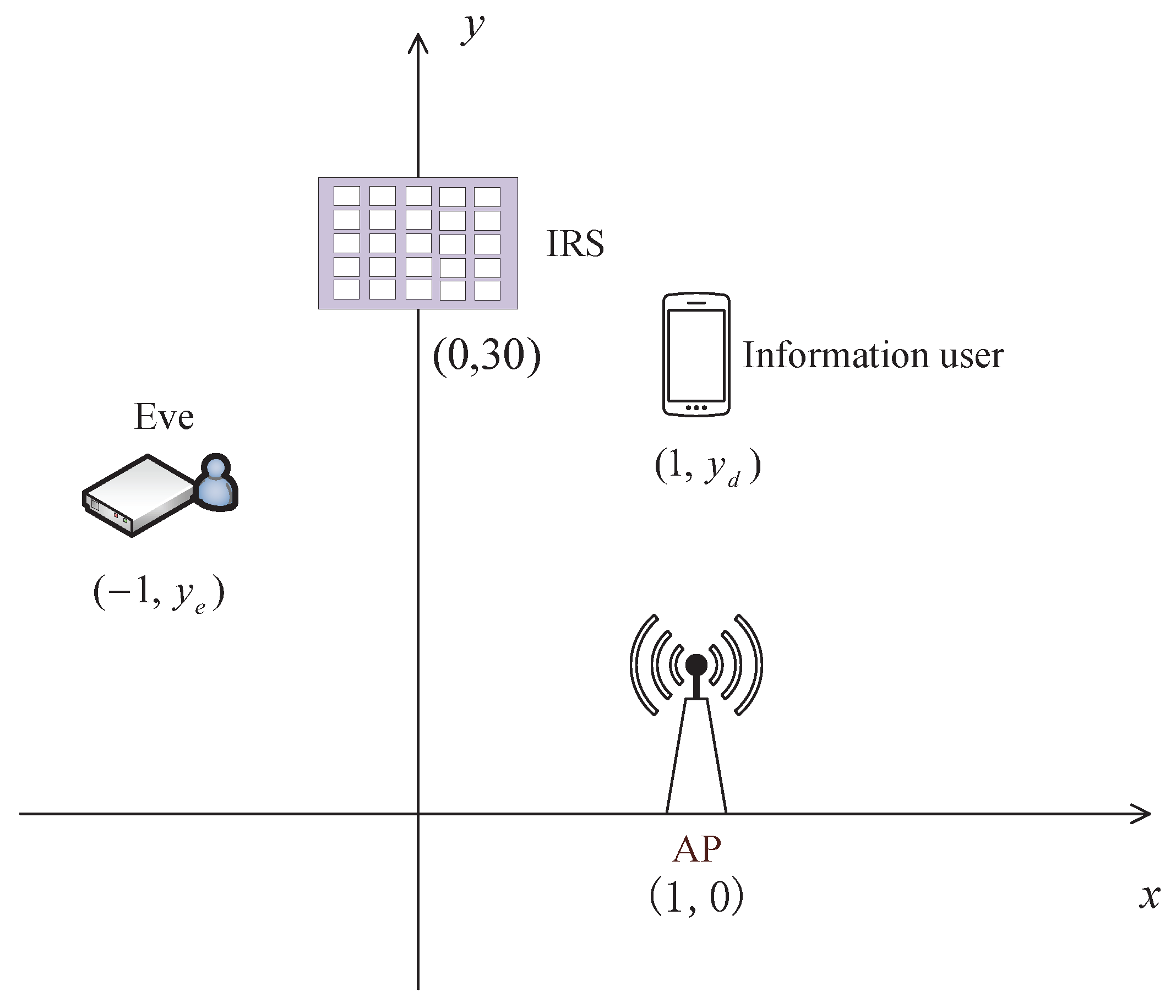
In this section, we present numerical results to show the achievable secrecy rate performance of the IRS-assisted SWIPT system with an energy-harvesting eavesdropper. In the simulation, we consider a two-dimensional coordinate system where the AP with
antennas, the legitimate user, and the energy harvesting eavesdropper (each equipped with one antenna) were located at
,
, and
in meter (
m) in the X-Y plane, respectively. It is assumed that the IRS composed of
reflecting elements, the center of which is deployed at
in the X-Y plane and is 3 meters high from the X-Y plane. We consider two cases: (1) the location of the energy-harvesting eavesdropper fixed at
, while the legitimate user moves along the horizontal line parallel to the y-axis in the X-Y plane from the location
to
; (2) the location of the legitimate user fixed at
, while the energy-harvesting eavesdropper moves along the horizontal line parallel to the y-axis from the location
to
. The simulation setup is shown in
Figure 2. In both cases, we compare the performance of the IRS-assisted SWIPT system considered in this paper with that of the SWIPT system without IRS.
The channels between the AP-User, AP-eavesdropper, IRS-user, and IRS-eavesdropper are assumed to be Rayleigh fading. The LoS channel is assumed between the AP and IRS. The path loss model is given by:
where
d is the distance of the link,
is the path loss exponent and
is the signal attenuation at a reference distance
meter. We set
and
for all channels. The average transmit power at the AP is
and the minimum required power at the energy-harvesting eavesdropper is
. The number of Gaussian randomizations of the beamforming vectors is set to be 1000. We set
as the stopping threshold for the alternating optimization approach. The other parameters are set as follows:
,
. All simulation results are averaged over 1000 random fading realizations.
Figure 3,
Figure 4,
Figure 5 and
Figure 6 compare the secrecy performance, transmitted power, and harvested power of the schemes with or without IRS under the above two cases. In all cases, the IRS-assisted scheme considered in this paper achieves a higher secrecy rate than that without the assistance of an IRS.
From
Figure 3, it can be found that the achievable secrecy rate decreases as the legitimate user moves away from the AP. This fact is apparent since the achievable rate of the legitimate user gets smaller as it moves far away from the source. It is worthy of noting that when the legitimate user is located close to the IRS and Eve, i.e., at the location
in the X-Y plane, the secrecy rate decreases rapidly. This is quite different from the results derived in the literatures [
6] where no extra Eve exists. It was shown in [
6] that when the information decoder is close to the IRS, it leads to a better user SNR. However, when there’s an Eve, as shown in this paper, if the legitimate user and the Eve are both close to the IRS, the Eve SNR may also be better, which causes more information leakage. Therefore, the secrecy rate is decreased in this case. The harvested power shown in
Figure 4 also illustrates this fact. In can be observed that the harvested power at the Eve is the largest, though the energy transfer power is the lowest when the legitimate user moves to the location
in the X-Y plane. We also show the secrecy rate assuming no energy signals. The achievable secrecy rate with no energy signals is much lower than that when the energy signals are jointly optimized with the information signals.
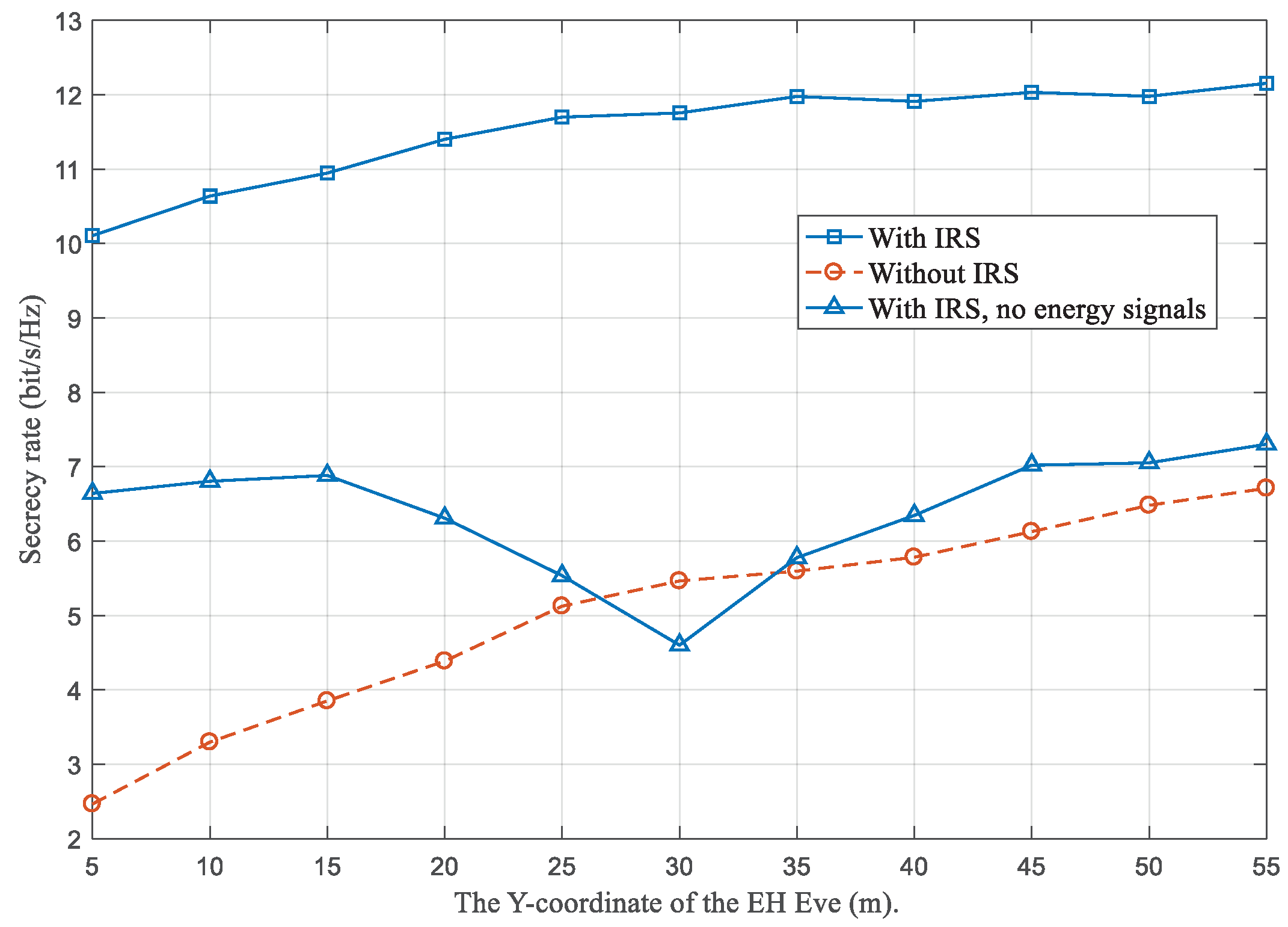
Figure 5 and
Figure 6 show the performance comparison when the location of the legitimate user is fixed, while the Eve moves from
to
in the X-Y plane. The secrecy rates increases as the Eve moves far away from the AP. It is interesting to find from
Figure 6 that the harvested power of both schemes, with or without IRS, are nearly equal to each other. However, the energy transfer power with IRS is larger than that without IRS. This means that by optimizing the phase shift matrix of the IRS and the beamforming vector at the AP, efficient power allocation can be achieved and a higher secrecy rate can be obtained by the IRS-assisted system. From
Figure 5, it is interesting to find that the secrecy rate with no energy signals decreases as the EH Eve moves closer to the IRS. This is quite different from the case when the energy and information signals are jointly optimized with or without IRS. As the EH Eve moves far apart from the IRS, the secrecy rate increases. The existence of the IRS makes the channels of the legitimate IR and EH Eve be correlated. This increases the possibility for the EH Eve to eavesdrop the confidential information, especially when the EH Eve and legitimate IR are close to the IRS. This result further verifies the analysis in Remark 1. It is necessary to send dedicated energy signals and jointly optimize them with the information signals. Next, we give an analysis on Remark 1.
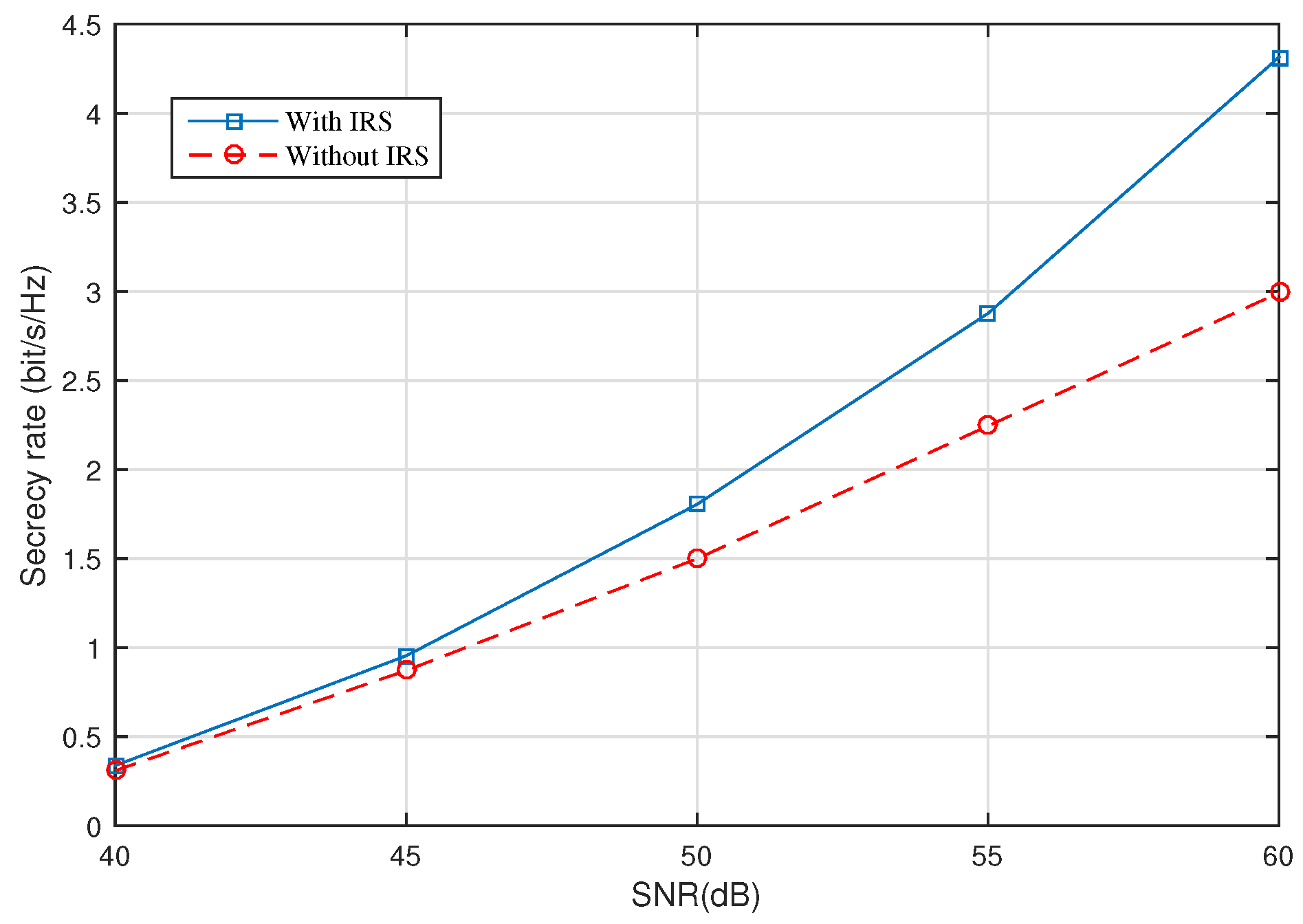
In order to show the secrecy rate with different SNR levels, we fix the locations of the IR and EH Eve at
and
, respectively. The transmit power Ps at the AP are set to 30 dBm, such that the minimum harvested energy requirements can be satisfied. We illustrate the achievable secrecy rate in
Figure 7, assuming the mean power of the Gaussian noise varies from −10 dBm to −30 dBm, i.e., the transmit SNR from 50 dB to 80 dB. It is clear that the achievable secrecy rate increases with the SNR in both cases with or without the assistance of the IRS. From
Figure 7, it can be found that the gap of the secrecy rates between the two cases becomes larger as the SNR increases. This further verifies the effectiveness of the proposed IRS-aided SWIPT system considered in this paper.