Breaking KASLR Using Memory Deduplication in Virtualized Environments
Abstract
:1. Introduction
- (1)
- We present a novel VM-based side-channel attack that exploits a deduplication technique of hypervisors. The main idea of the proposed attack is to infer the sensitive information from a timing difference of write access latency between a duplicate and deduplicated page. The proposed attack breaks KALSR in the latest versions of the Linux kernel equipped with the state-of-the-art kernel defense mechanism.
- (2)
- We evaluate the proposed attack by conducting extensive experiments under real virtualization environments where practical hypervisors such as KVM and VMware ESXi are used. The evaluation results support the feasibility and effectiveness of the proposed attack.
2. Background
2.1. Kernel Address Space Layout Randomization (KASLR)
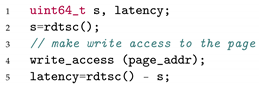
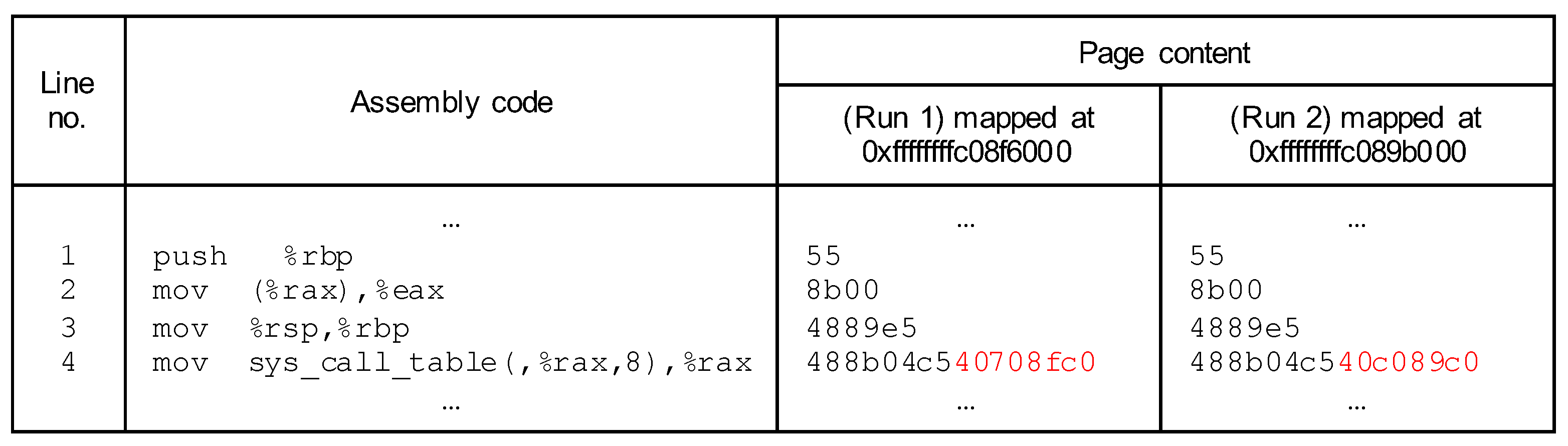
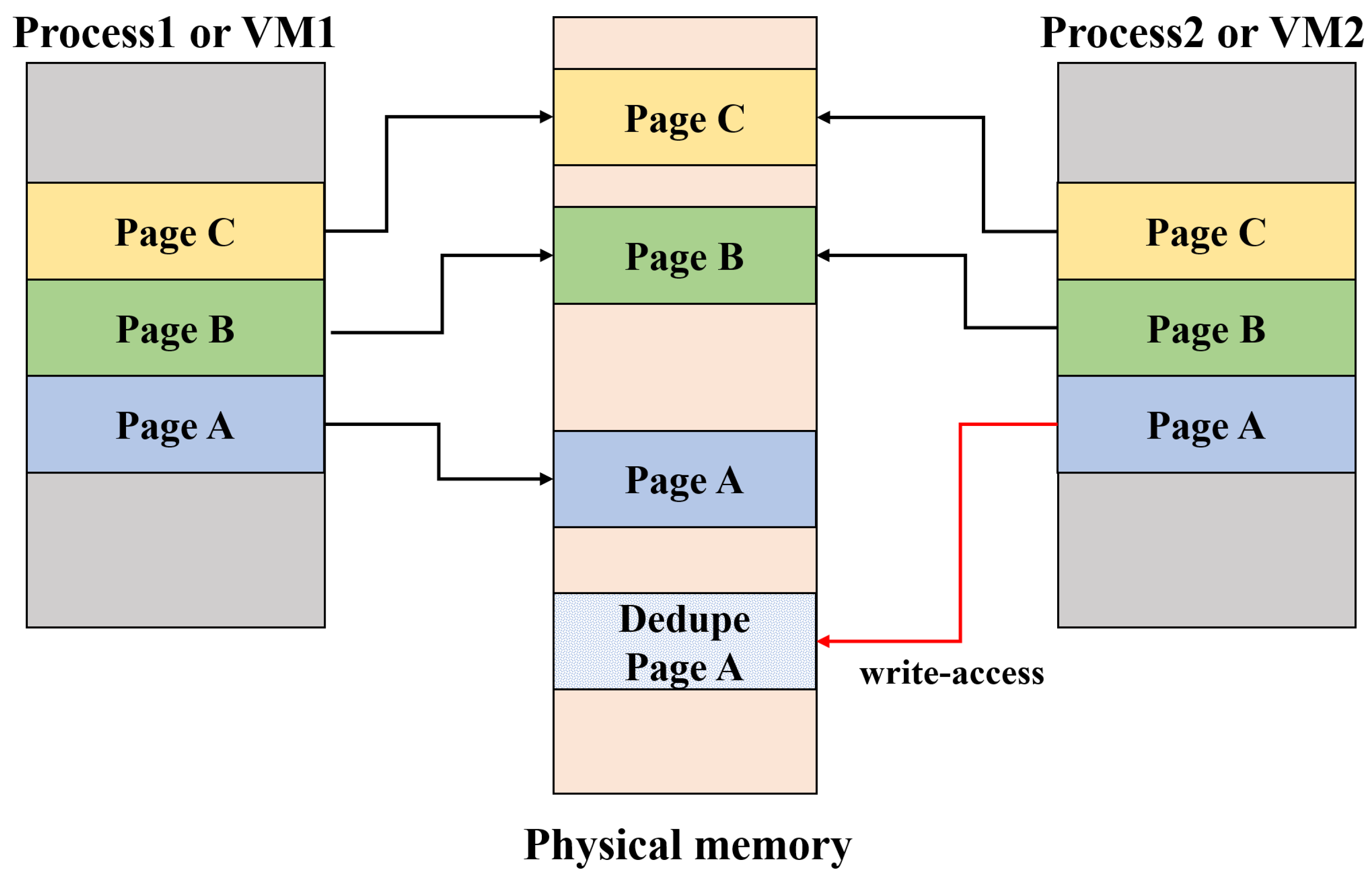
2.2. Memory Deduplication Attack
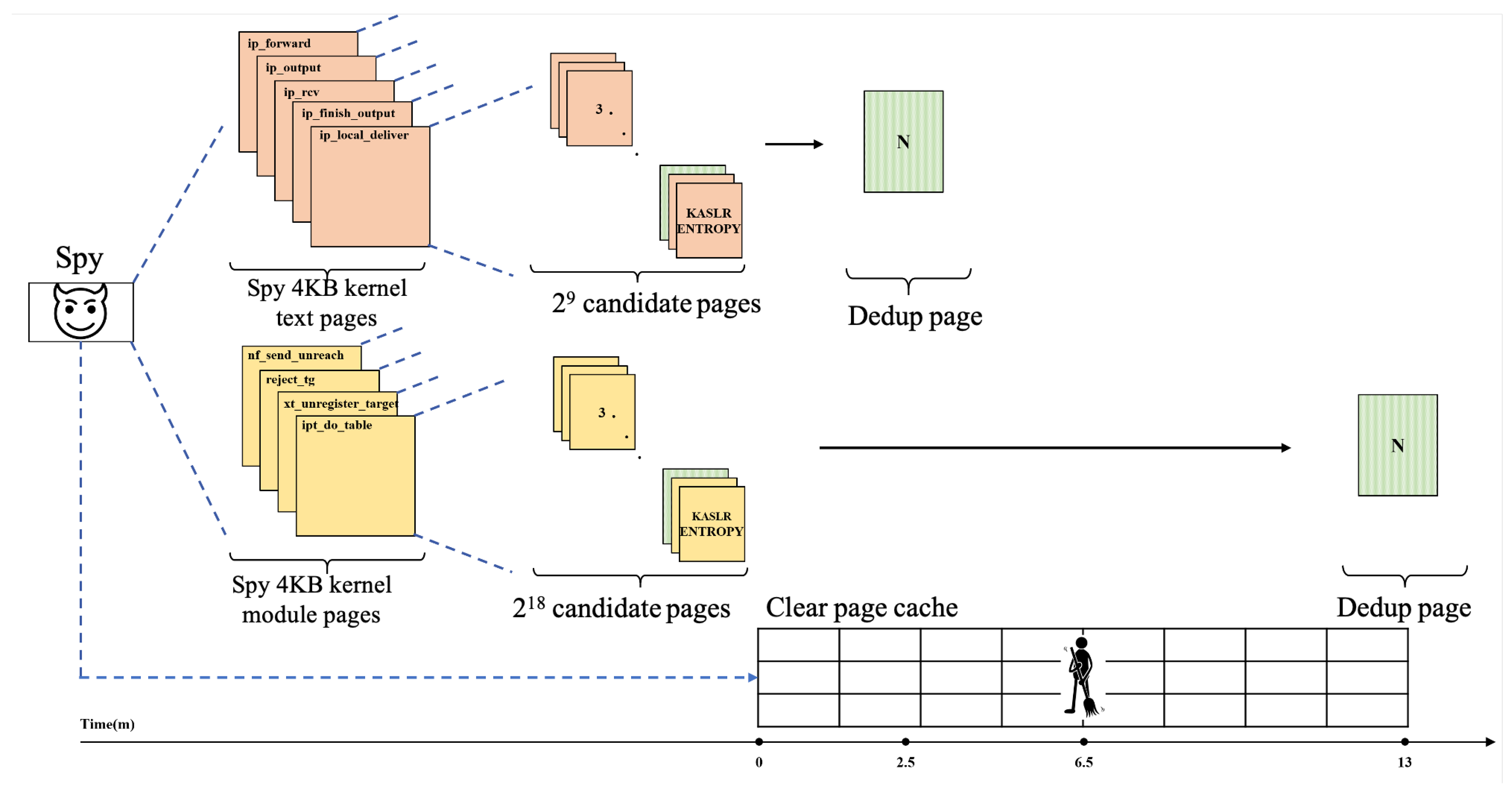
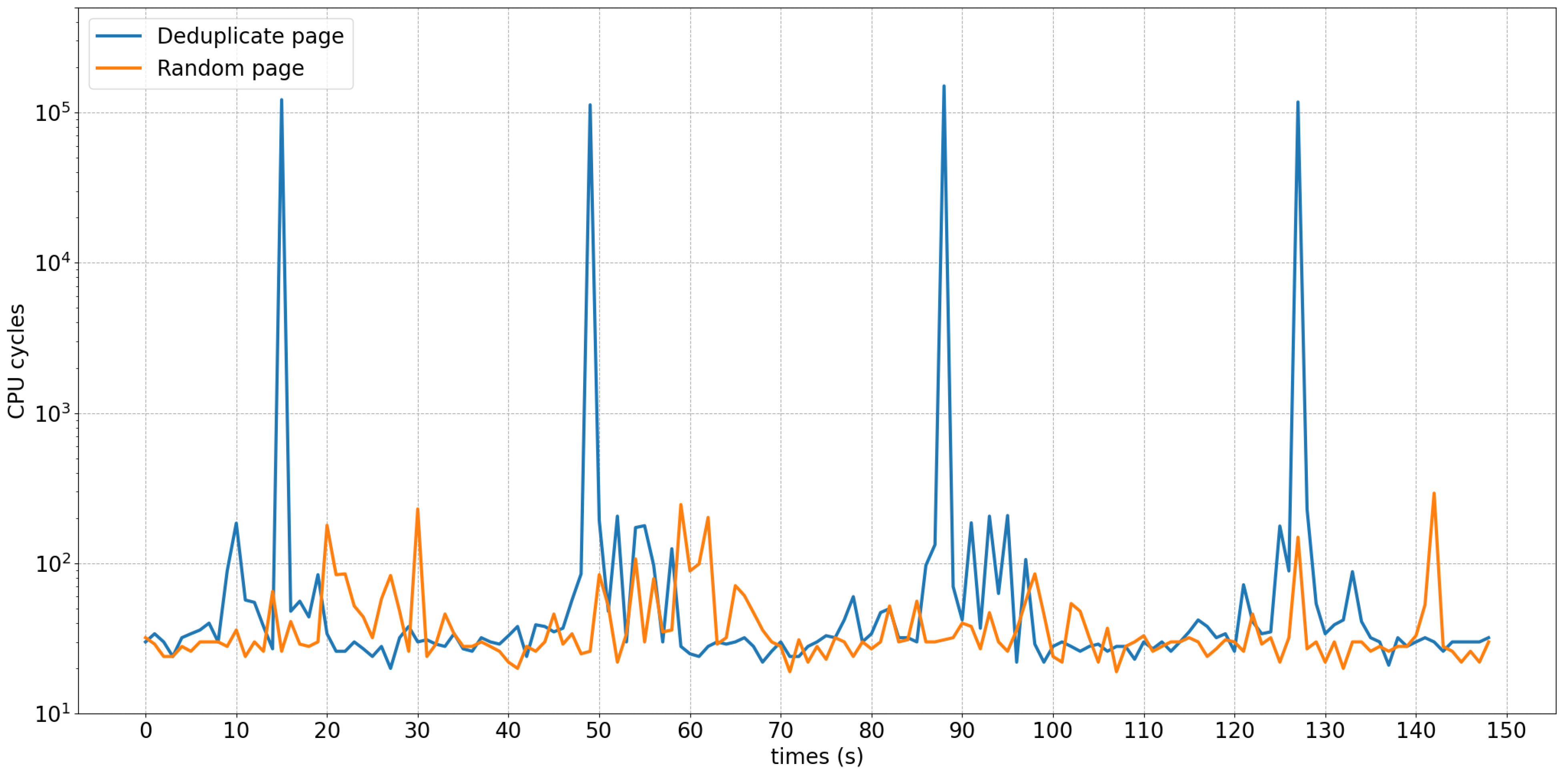
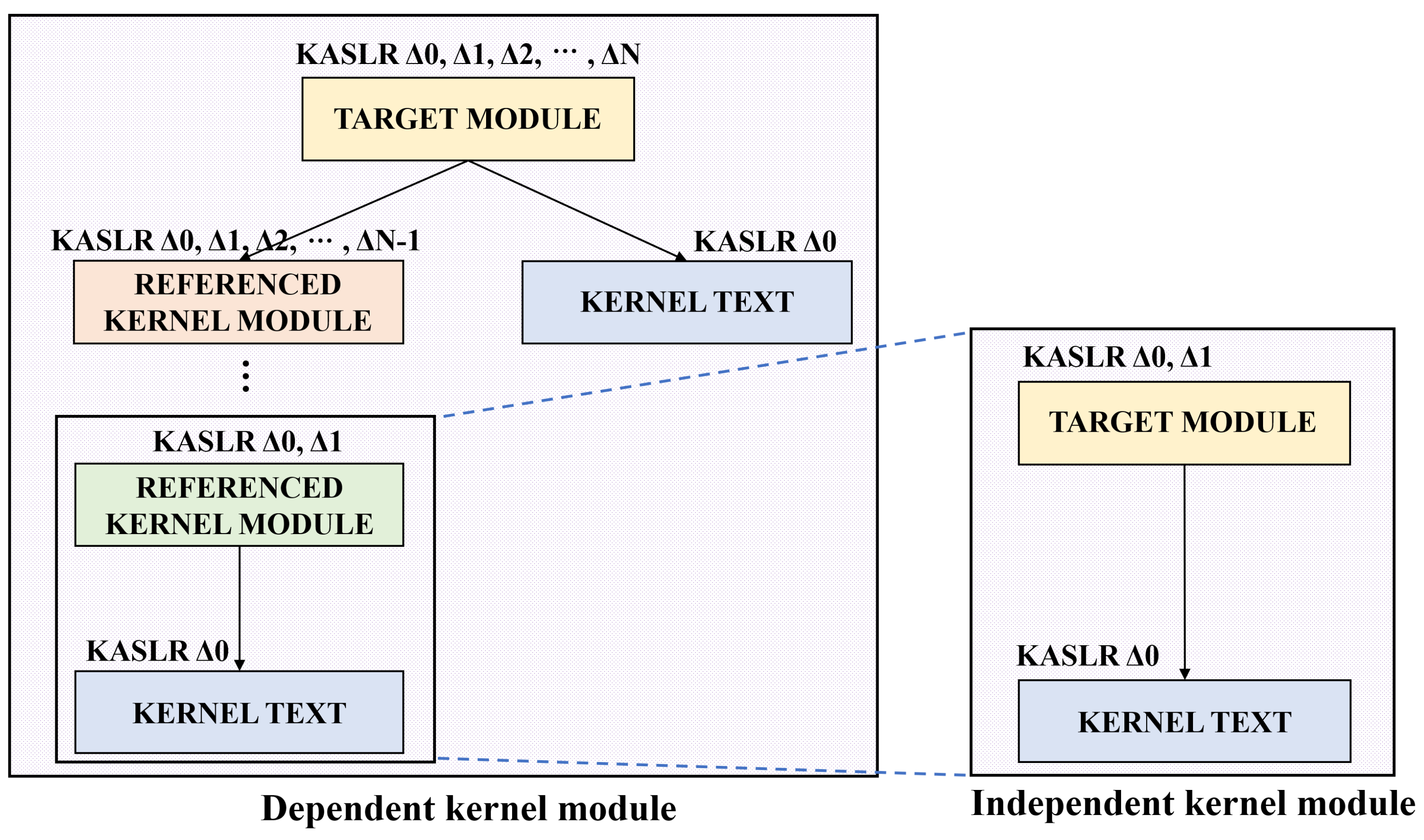
3. Proposed Attack Technique
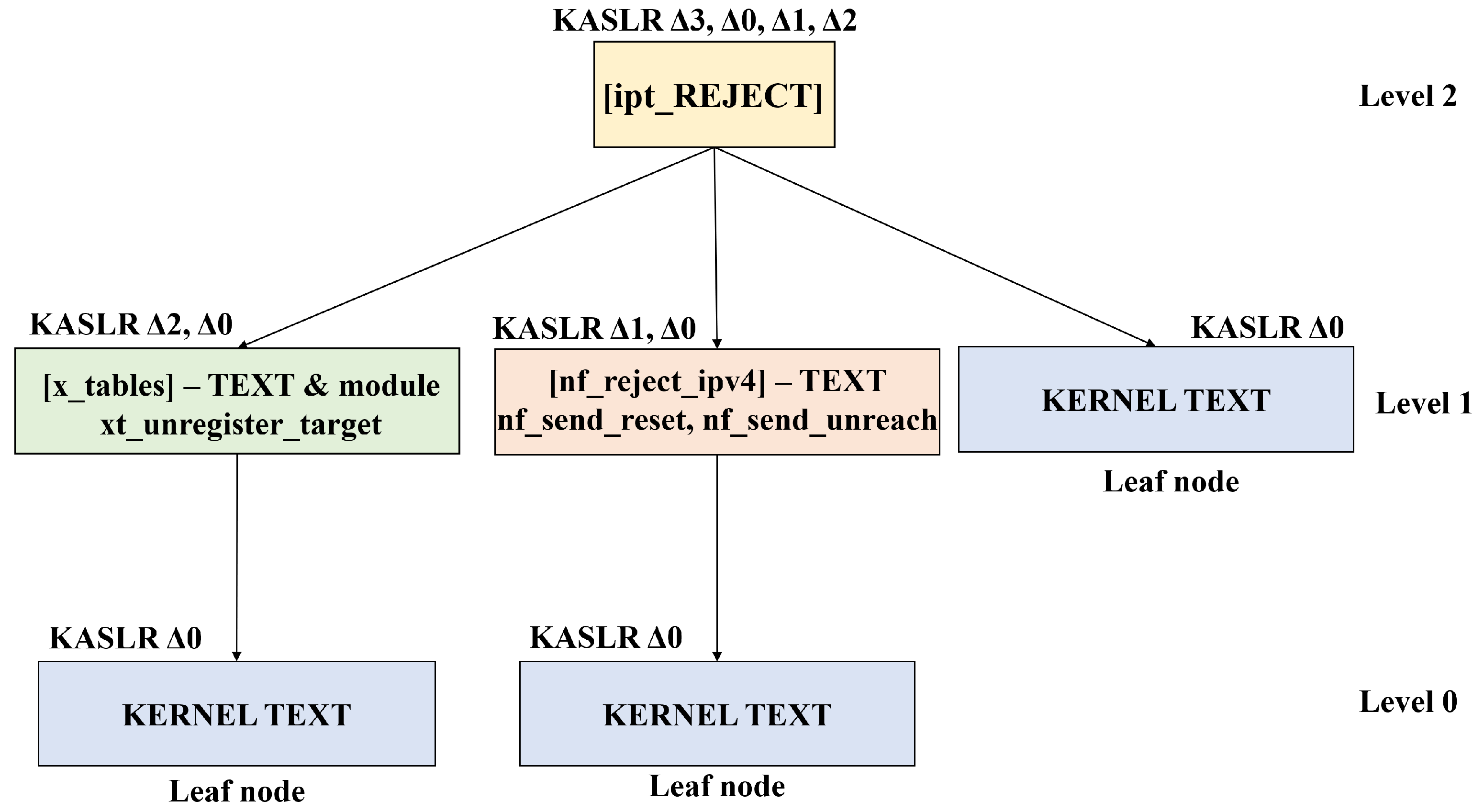
Case Study and Evaluation
4. Countermeasure
5. Related Work
5.1. CPU Side-Channel Attack against KASLR
5.2. Memory Deduplication Attack
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Snow, K.Z.; Monrose, F.; Davi, L.; Dmitrienko, A.; Liebchen, C.; Sadeghi, A.R. Just-In-Time Code Reuse: On the Effectiveness of Fine-Grained Address Space Layout Randomization. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 574–588. [Google Scholar] [CrossRef]
- Bletsch, T.; Jiang, X.; Freeh, V.W.; Liang, Z. Jump-oriented programming: A new class of code-reuse attack. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; pp. 30–40. [Google Scholar]
- Dai Zovi, D. Practical return-oriented programming. Source Boston. 2010. Available online: https://repository.root-me.org/Exploitation%20-%20Syst%C3%A8me/Microsoft/EN%20-%20Practical%20Return%20Oriented%20Programming.pdf (accessed on 5 May 2010).
- Davi, L.; Dmitrienko, A.; Sadeghi, A.R.; Winandy, M. Return-Oriented Programming without Returns on ARM; Technical Report, Technical Report HGI-TR-2010-002; Ruhr-University Bochum: Bochum, Germany, 2010. [Google Scholar]
- Roemer, R.; Buchanan, E.; Shacham, H.; Savage, S. Return-oriented programming: Systems, languages, and applications. ACM Trans. Inf. Syst. Secur. (TISSEC) 2012, 15, 1–34. [Google Scholar] [CrossRef]
- Checkoway, S.; Davi, L.; Dmitrienko, A.; Sadeghi, A.R.; Shacham, H.; Winandy, M. Return-oriented programming without returns. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 559–572. [Google Scholar]
- Gruss, D.; Maurice, C.; Fogh, A.; Lipp, M.; Mangard, S. Prefetch side-channel attacks: Bypassing SMAP and kernel ASLR. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 368–379. [Google Scholar]
- Hund, R.; Willems, C.; Holz, T. Practical timing side channel attacks against kernel space ASLR. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 191–205. [Google Scholar]
- Lipp, M.; Schwarz, M.; Gruss, D.; Prescher, T.; Haas, W.; Fogh, A.; Horn, J.; Mangard, S.; Kocher, P.; Genkin, D.; et al. Meltdown: Reading Kernel Memory from User Space. In Proceedings of the 27th USENIX Security Symposium, Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Gregg, B. KPTI/KAISER Meltdown Initial Performance Regressions. 2018. Available online: https://www.linux.com/news/kptikaiser-meltdown-initial-performance-regressions/ (accessed on 12 February 2018).
- Suzaki, K.; Iijima, K.; Yagi, T.; Artho, C. Memory deduplication as a threat to the guest OS. In Proceedings of the Fourth European Workshop on System Security—EUROSEC’11, Salzburg, Austria, 10 April 2011; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Arcangeli, A.; Eidus, I.; Wright, C. Increasing memory density by using KSM. In Proceedings of the Linux Symposium. Citeseer; 2009; pp. 19–28. Available online: http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.454.5113 (accessed on 1 January 2009).
- Waldspurger, C.A. Memory resource management in VMware ESX server. ACM Sigops Oper. Syst. Rev. 2002, 36, 181–194. [Google Scholar] [CrossRef]
- Venkitachalam, G.; Cohen, M. Transparent Page Sharing on Commodity Operating Systems. 2009. Available online: https://patents.google.com/patent/US7500048B1/en (accessed on 3 March 2009).
- Suzaki, K.; Iijima, K.; Yagi, T.; Artho, C. Software side channel attack on memory deduplication. In Proceedings of the ACM Symposium on Operating Systems Principles (SOSP 2011), Cascais, Portugal, 23–26 October 2011; pp. 2–3. [Google Scholar]
- Suzaki, K.; Iijima, K.; Yagi, T.; Artho, C. Implementation of a memory disclosure attack on memory deduplication of virtual machines. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2013, 96, 215–224. [Google Scholar] [CrossRef] [Green Version]
- Jang, Y.; Lee, S.; Kim, T. Breaking Kernel Address Space Layout Randomization with Intel TSX. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 380–392. [Google Scholar]
- Chiappetta, M.; Savas, E.; Yilmaz, C. Real time detection of cache-based side-channel attacks using Hardware Performance Counters. Appl. Soft Comput. 2016, 49, 1162–1174. [Google Scholar] [CrossRef] [Green Version]
- Payer, M. HexPADS: A platform to detect stealth attacks. In International Symposium on Engineering Secure Software and Systems; Springer: Cham, Switzerland, 2016; Volume 9639, pp. 138–154. [Google Scholar] [CrossRef]
- Yarom, Y.; Falkner, K. Flush + Reload: A High Resolution, Low Noise, L3 Cache Side-Channel Attack. In Proceedings of the 23th USENIX Security Symposium, San Diego, CA, USA, 20–22 August 2014; pp. 719–732. [Google Scholar]
- Schwarz, M.; Canella, C.; Giner, L.; Gruss, D. Store-to-Leak Forwarding: Leaking Data on Meltdown-resistant CPUs. arXiv 2019, arXiv:1905.05725. [Google Scholar]
- Canella, C.; Schwarz, M.; Haubenwallner, M.; Schwarzl, M.; Gruss, D. KASLR: Break It, Fix It, Repeat. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security, Taipei, China, 5–9 October 2020; pp. 481–493. [Google Scholar]
- Kim, T.; Shin, Y. Reinforcing Meltdown Attack by using a Return Stack Buffer. IEEE Access 2019, 7, 186065–186077. [Google Scholar] [CrossRef]
- Gruss, D.; Bidner, D.; Mangard, S. Practical memory deduplication attacks in sandboxed javascript. In Proceedings of the European Symposium on Research in Computer Security, Vienna, Austria, 21–25 September 2015; pp. 108–122. [Google Scholar]
- Barresi, A.; Razavi, K.; Payer, M.; Gross, T.R. CAIN: Silently Breaking ASLR in the Cloud. In Proceedings of the 9th USENIX Workshop on Offensive Technologies (WOOT 15), Washington, DC, USA, 10–11 August 2015. [Google Scholar]
| OS | Types | Entropy | #slot | Address Range | Granularity |
|---|---|---|---|---|---|
| Ubuntu | Kernel Text | 9 bit | 512 | 0xffffffff80000000 ∼0xffffffffc0000000 | 2 MB |
| 18.04 | Kernel Module | 10 bit | 1024 | 0xffffffffc0000000 ∼0xffffffffc0400000 | 4 KB |
| Hypervisor | CPU | Guset OS/ Kernel Version | Target | RAM | Times (hr) | Attack | |||
|---|---|---|---|---|---|---|---|---|---|
| Host | Spy | Victim | Text | Module | |||||
| Ubuntu KVM | Intel Core i5-7400 | Ubuntu 18.04 /5.3.7 | Kernel Text/ Module | 16 GB | 4 GB | 4 GB | 0.05 | 0.2 | ✔ |
| Intel Core i7-6700 | 16 GB | 4 GB | 8 GB | 0.05 | 0.2 | ✔ | |||
| Intel Core i7-8700 | 16 GB | 8 GB | 4 GB | 0.05 | 0.2 | ✔ | |||
| Intel Core i9-9900KF | 16 GB | 4 GB | 4 GB | 0.05 | 0.2 | ✔ | |||
| AMD Ryzen7 2700x | 16 GB | 4 GB | 4 GB | 0.05 | 0.2 | ✔ | |||
| VMWare ESXi | Intel Core i5-7400 | Ubuntu 18.04 /5.3.7 | Kernel Text/ Module | 16 GB | 4 GB | 4 GB | 2 | 8 | ✔ |
| Attack Techniques | Prerequisite | Configuration | Breaking KASLR with KPTI | |
|---|---|---|---|---|
| Hund et al. [8] | Double Page Fault | Kernel address space is mapped user address space | Host machine | ✗ |
| Gruss et al. [7] | Software prefetch | ✗ | ||
| Jang et al. [17] | Intel TSX | ✗ | ||
| Lipp et al. [9] | Out-of-order execution | ✗ | ||
| Schwarz et al. [21] | Store-to-load forwarding | ✗ | ||
| Canella et al. [22] | Out-of-order execution | ✗ | ||
| Kim et al. [23] | Return Stack Buffer | ✗ | ||
| Our attack | Memory Deduplication | Memory deduplication is enabled | Cross-VM | ✔ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, T.; Kim, T.; Shin, Y. Breaking KASLR Using Memory Deduplication in Virtualized Environments. Electronics 2021, 10, 2174. https://doi.org/10.3390/electronics10172174
Kim T, Kim T, Shin Y. Breaking KASLR Using Memory Deduplication in Virtualized Environments. Electronics. 2021; 10(17):2174. https://doi.org/10.3390/electronics10172174
Chicago/Turabian StyleKim, Taehun, Taehyun Kim, and Youngjoo Shin. 2021. "Breaking KASLR Using Memory Deduplication in Virtualized Environments" Electronics 10, no. 17: 2174. https://doi.org/10.3390/electronics10172174
APA StyleKim, T., Kim, T., & Shin, Y. (2021). Breaking KASLR Using Memory Deduplication in Virtualized Environments. Electronics, 10(17), 2174. https://doi.org/10.3390/electronics10172174






