Discussion on IoT Security Recommendations against the State-of-the-Art Solutions
Abstract
:1. Introduction
2. Motivation and Related Work
3. Security Recommendations for Internet of Things
3.1. Existing Guidelines
- National Institute of Standards and Technology (NIST),
- European Union Agency for Network and Information Security (ENISA),
- GSM Association (GSMA),
- Internet Engineering Task Force (IETF),
- Internet Research Task Force (IRTF),
- IoT Security Foundation (IoTSF),
- ioXt Alliance,
- International Standard Organization (ISO),
- Institute of Electrical and Electronics Engineers (IEEE),
- International Telecommunication Union (ITU),
- Broadband Internet Technical Advisory Group (BITAG),
- Industrial Internet Consortium (IIC),
- Open Web Application Security Project (OWASP),
- Trusted Computing Group (TCG),
- Cloud Security Alliance (CSA),
- GlobalPlatform,
- Internet Society’s Online Trust Alliance (OTA).
3.2. Evaluation Criteria
- hardware security,
- trust and integrity management,
- data protection and software design,
- device configuration and software update,
- secure interfaces and communication,
- cybersecurity event monitoring and logging,
- cryptography and key management,
- device identification, authentication and strong default security.
4. Review of Existing Solutions
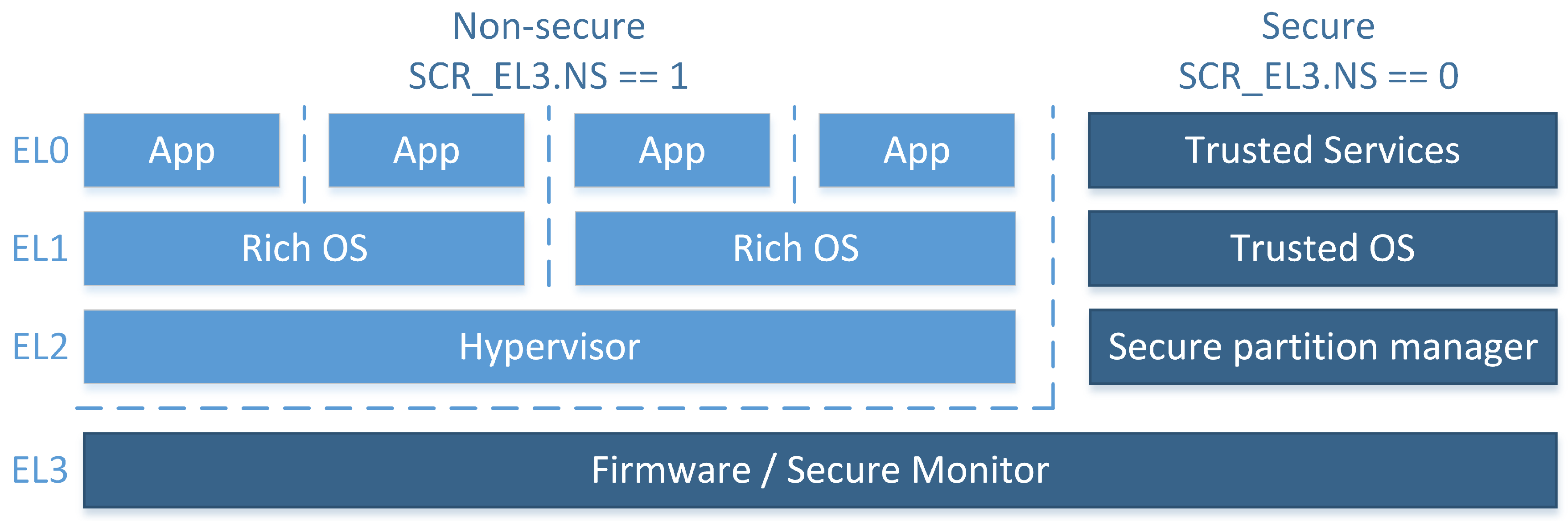
4.1. Arm TrustZone
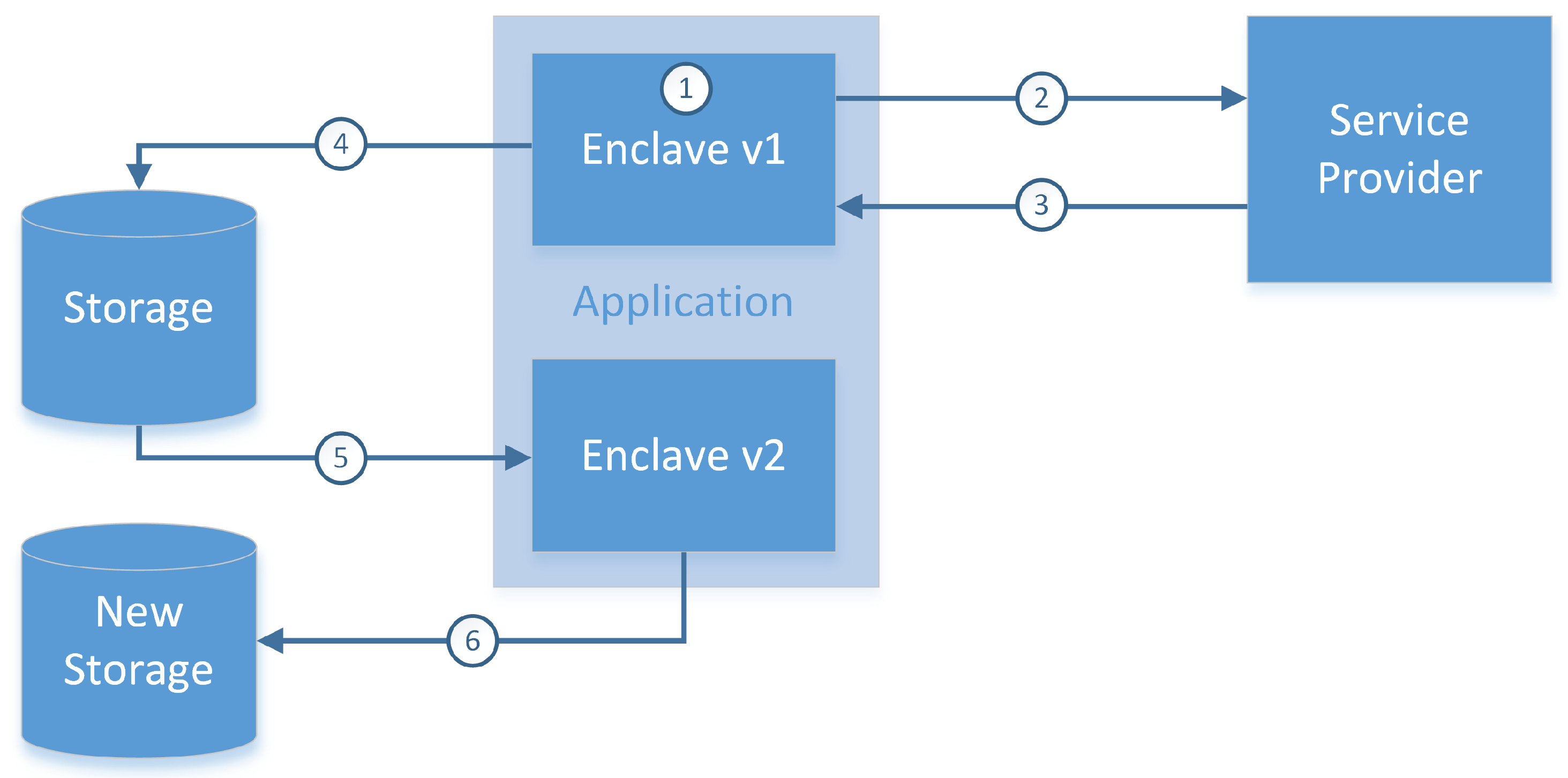
4.2. Intel Software Guard Extensions (SGX) and Security Essentials
- Creating the enclave—an untrusted REE application creates an enclave environment in order to protect the software of the trusted provider, during this process the contents and creation parameters are logged as a measurement,
- Attestation—the enclave informs the software provider about its readiness to receive new software and the device presents the measurement from before,
- Provisioning—a secure channel between the device and provider is created and the data is sent,
- Sealing and unsealing—the enclave uses a cryptographic hardware key for encryption before storing the data in memory. Only an identical enclave will be able to decrypt and use the new program data in the future,
- Software update—in this step, a new version of a program may ask an older version to unseal the data. After the update process ends, a new seal is created, which renders the old software version (which could be compromised due to flaws patched in the new version) unable to access the new software version data.
4.3. Keystone
- Measures the SM image loaded,
- Generates a new attestation key based on the randomness source,
- Saves the data in a SM memory location isolated by PMP,
- Sends the cryptographically generated metadata via a public key scheme.
- It is programmable,
- It allows control over interrupts and exceptions above the OS level,
- PMP mechanism, which allows the enforcement of access policies.
4.4. OpenTitan
4.5. NXP EdgeLock SE050
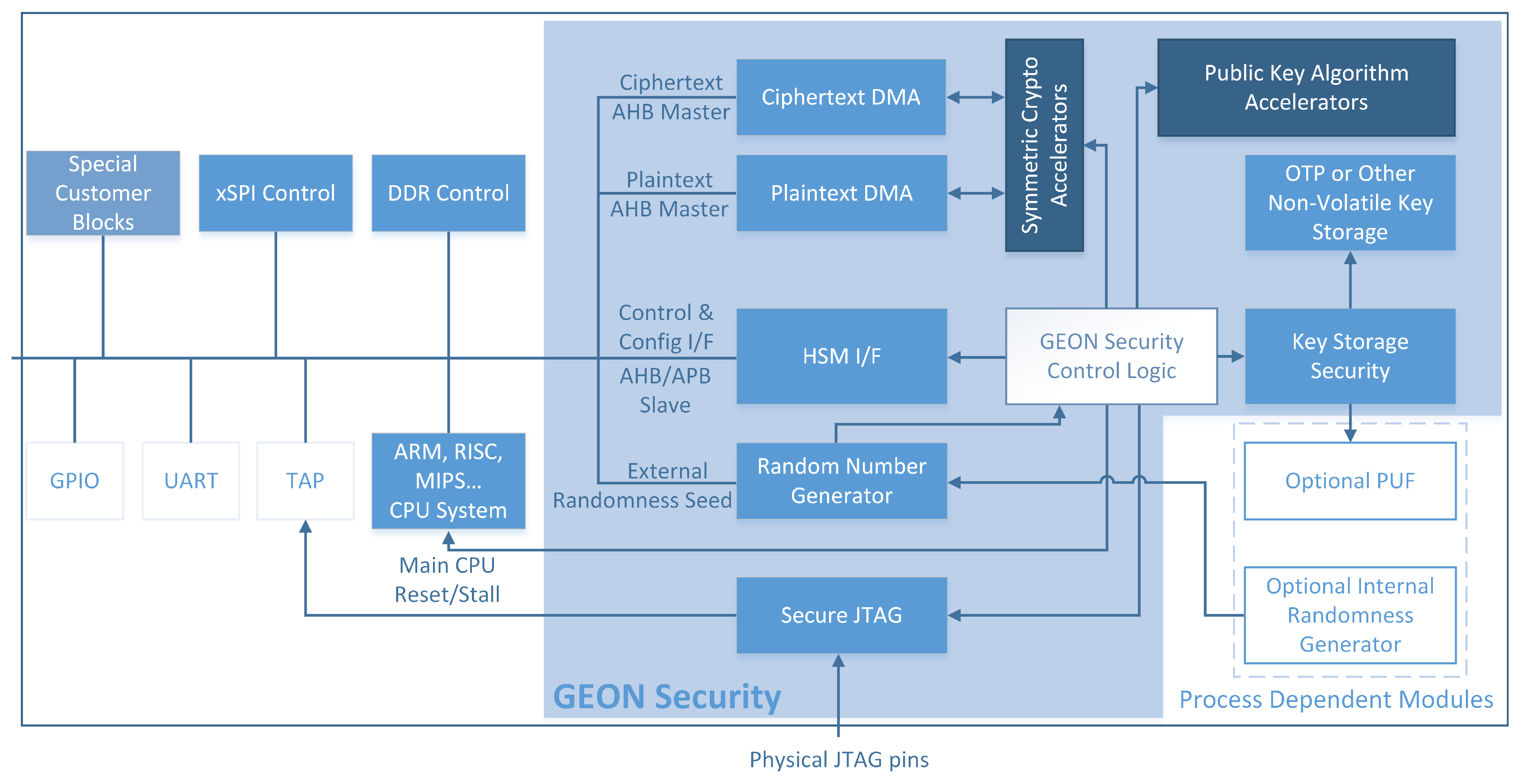
4.6. Beyond Semiconductor GEON SoC Security Platform
4.7. Rambus RT Family
4.8. Summary
- ◯—difficult to satisfy this secure IoT requirement using a particular solution;
- ◖—can be done, but no explicit recommendation nor solution for use in an IoT device is presented, leaving the design decisions open and potentially unsafe;
- ●—strong recommendation or solution which satisfies the requirement.
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AC | Air Conditioning |
| AES | Advanced Encryption Standard |
| AHB | AMBA High-performance Bus |
| AMBA | ARM Advanced Microcontroller Bus Architecture |
| APB | AMBA Advanced Peripheral Bus |
| API | Application Programming Interface |
| AXI | AMBA Advanced eXtensible Interface |
| CCTV | Closed-circuit Television |
| CLI | Command Line Interface |
| CMAC | Cipher-based Message Authentication Code |
| CPU | Central Processing Unit |
| DDoS | Distributed Denial of Service |
| DMA | Direct Memory Access |
| ECC | Elliptic-curve cryptography |
| FW | Firmware |
| GSM | Global System for Mobile Communications |
| HMAC | keyed-Hash Message Authentication Code |
| HW | Hardware |
| HWRoT, RoT | (Hardware) Root of Trust |
| I2C | Inter-Integrated Circuit communication bus |
| IC | Integrated Circuit |
| IoT | Internet of Things |
| IP | Intellectual Property |
| JCOPOS | Java Card OpenPlatform Operating System |
| JTAG | Joint Test Action Group |
| M-mode | RISC-V Machine Mode |
| NIST | National Institute of Standards and Technology |
| OS | Operating System |
| REE | Rich Execution Environment |
| RFID | Radio-frequency Identification |
| ROM | Read-only Memory |
| RSA | Rivest–Shamir–Adleman (public key cryptosystem) |
| S-mode | RISC-V Supervisor Mode |
| SGX | (Intel) Software Guard Extensions |
| SHA-1 | Secure Hash Algorithm 1 |
| SoC | System-on-Chip |
| SW | Software |
| TCB | Trusted Computing Base |
| TEE | Trusted Execution Environment |
| TLS | Transport Layer Security |
| TPM | Trusted Platform Module |
| U-mode | RISC-V User Mode |
References
- Ericsson. IoT Connections Outlook. Available online: https://www.ericsson.com/en/mobility-report/dataforecasts/iot-connections-outlook (accessed on 24 June 2021).
- Lueth, K.L. State of the IoT 2020: 12 billion IoT Connections, Surpassing Non-IoT for the First Time. Available online: https://iot-analytics.com/state-of-the-iot-2020-12-billion-iot-connections-surpassing-non-iot-for-the-first-time/ (accessed on 24 June 2021).
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21. [Google Scholar] [CrossRef]
- Greenberg, A. Hackers Remotely Kill a Jeep on the Highway—With Me in It. Available online: https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/ (accessed on 24 June 2021).
- Graff, G.M. How a Dorm Room Minecraft Scam Brought down the Internet. Available online: https://www.wired.com/story/mirai-botnet-minecraft-scam-brought-down-the-internet/ (accessed on 24 June 2021).
- Ben Herzberg, I.Z.; Bekerman, D. Breaking Down Mirai: An IoT DDoS Botnet Analysis. Available online: https://www.imperva.com/blog/malware-analysis-mirai-ddos-botnet/ (accessed on 24 June 2021).
- Green, A. The Mirai Botnet Attack and Revenge of the Internet of Things. Available online: https://www.varonis.com/blog/the-mirai-botnet-attack-and-revenge-of-the-internet-of-things/ (accessed on 24 June 2021).
- Bonomi, F.; Milito, R. Fog Computing and its Role in the Internet of Things. Proc. MCC Workshop Mob. Cloud Comput. 2012. [Google Scholar] [CrossRef]
- Gupta, N.; Rodrigues, J.J.P.C.; Dauwels, J. (Eds.) Augmented Intelligence toward Smart Vehicular Application; CRC Press: Boca Raton, FL, USA, 2020; pp. 7–13. [Google Scholar] [CrossRef]
- Park, H.; Zhai, S.; Lu, L.; Lin, F.X. StreamBox-TZ: Secure Stream Analytics at the Edge with TrustZone. In Proceedings of the 2019 USENIX Annual Technical Conference (USENIX ATC 19), Renton, WA, USA, 10–12 July 2019; pp. 537–554. [Google Scholar]
- Fournaris, A.P.; Alexakos, C.; Anagnostopoulos, C.; Koulamas, C.; Kalogeras, A. Introducing Hardware-Based Intelligence and Reconfigurability on Industrial IoT Edge Nodes. IEEE Des. Test 2019, 36, 15–23. [Google Scholar] [CrossRef]
- Mahmoud, R.; Yousuf, T.; Aloul, F.; Zualkernan, I. Internet of things (IoT) security: Current status, challenges and prospective measures. In Proceedings of the 2015 10th International Conference for Internet Technology and Secured Transactions, London, UK, 8–10 December 2016; pp. 336–341. [Google Scholar] [CrossRef]
- Binti Mohamad Noor, M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V.; Sikdar, B.; Choo, K.K.R. Consumer IoT: Security Vulnerability Case Studies and Solutions. IEEE Consum. Electron. Mag. 2020, 9, 17–25. [Google Scholar] [CrossRef]
- Tsiropoulou, E.E.; Baras, J.S.; Papavassiliou, S.; Qu, G. On the Mitigation of Interference Imposed by Intruders in Passive RFID Networks. In Decision and Game Theory for Security; Zhu, Q., Alpcan, T., Panaousis, E., Tambe, M., Casey, W., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 62–80. [Google Scholar]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Zhu, Q.; Başar, T. Game-Theoretic Approach to Feedback-Driven Multi-stage Moving Target Defense. In Decision and Game Theory for Security; Das, S.K., Nita-Rotaru, C., Kantarcioglu, M., Eds.; Springer International Publishing: Cham, Switzerland, 2013; pp. 246–263. [Google Scholar]
- Fagan, M.; Megas, K.N.; Scarfone, K.; Smith, M. IoT device cybersecurity capability core baseline. In Technical Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [Google Scholar] [CrossRef]
- Fortino, G.; Savaglio, C.; Spezzano, G.; Zhou, M. Internet of Things as System of Systems: A Review of Methodologies, Frameworks, Platforms, and Tools. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 223–236. [Google Scholar] [CrossRef]
- Tournier, J.; Lesueur, F.; Mouël, F.L.; Guyon, L.; Ben-Hassine, H. A survey of IoT protocols and their security issues through the lens of a generic IoT stack. Internet Things 2020, 100264. [Google Scholar] [CrossRef]
- Sinche, S.; Raposo, D.; Armando, N.; Rodrigues, A.; Boavida, F.; Pereira, V.; Silva, J.S. A Survey of IoT Management Protocols and Frameworks. IEEE Commun. Surv. Tutor. 2020, 22, 1168–1190. [Google Scholar] [CrossRef]
- Babun, L.; Denney, K.; Celik, Z.B.; McDaniel, P.; Uluagac, A.S. A survey on IoT platforms: Communication, security, and privacy perspectives. Comput. Netw. 2021, 192, 108040. [Google Scholar] [CrossRef]
- Ammar, M.; Russello, G.; Crispo, B. Internet of Things: A survey on the security of IoT frameworks. J. Inf. Secur. Appl. 2018, 38, 8–27. [Google Scholar] [CrossRef] [Green Version]
- Macedo, E.L.; De Oliveira, E.A.; Silva, F.H.; Mello, R.R.; Franca, F.M.; Delicato, F.C.; De Rezende, J.F.; De Moraes, L.F. On the security aspects of Internet of Things: A systematic literature review. J. Commun. Netw. 2019, 21, 444–457. [Google Scholar] [CrossRef]
- Abdul-Ghani, H.A.; Konstantas, D. A comprehensive study of security and privacy guidelines, threats, and countermeasures: An IoT perspective. J. Sens. Actuator Netw. 2019, 8, 22. [Google Scholar] [CrossRef] [Green Version]
- Maene, P.; Götzfried, J.; De Clercq, R.; Müller, T.; Freiling, F.; Verbauwhede, I. Hardware-Based Trusted Computing Architectures for Isolation and Attestation. IEEE Trans. Comput. 2018, 67, 361–374. [Google Scholar] [CrossRef]
- European Union Agency for Network and Information Security. Baseline Security Recommendations for IoT in the Context of Critical Information Infrastructures. Available online: https://op.europa.eu/en/publication-detail/-/publication/c37f8196-d96f-11e7-a506-01aa75ed71a1/language-en (accessed on 30 June 2021).
- GSM Association. IoT Security Guidelines Overview Document—Version 2.2. Available online: https://www.gsma.com/iot/wp-content/uploads/2020/05/CLP.11-v2.2-GSMA-IoT-Security-Guidelines-Overview-Document.pdf (accessed on 30 June 2021).
- GSM Association. IoT Security Guidelines for IoT Service Ecosystem—Version 2.2. Available online: https://www.gsma.com/iot/wp-content/uploads/2020/05/CLP.12-v2.2-GSMA-IoT-Security-Guidelines-for-Service-Ecosystems.pdf (accessed on 30 June 2021).
- GSM Association. IoT Security Guidelines for Endpoint Ecosystem—Version 2.2. Available online: https://www.gsma.com/iot/wp-content/uploads/2020/05/CLP.13-v2.2-GSMA-IoT-Security-Guidelines-for-Endpoint-Ecosystems.pdf (accessed on 30 June 2021).
- Moore, K.; Barnes, R.; Tschofenig, H. Best Current Practices for Securing Internet of Things (IoT) Devices. Internet-Draft draft-moore-iot-security-bcp-01. Internet Eng. Task Force 2017. Work in Progress. [Google Scholar]
- Wang, B.; Liu, S.; Wan, L.; Li, J.; Wang, X.T. Technical Requirements for Secure Access and Management of IoT Smart Terminals. Internet-Draft draft-wang-secure-access-of-iot-terminals-01. Internet Eng. Task Force 2021. Work in Progress. [Google Scholar]
- Garcia-Morchon, O.; Kumar, S.; Sethi, M. Internet of Things (IoT) Security: State of the Art and Challenges. Available online: https://www.rfc-editor.org/info/rfc8576 (accessed on 30 June 2021).
- Foundation, I.S. Secure Design—Best Practice Guides—Release 2. Internet of Things (IoT) Security: State of the Art and Challenges. Available online: https://www.iotsecurityfoundation.org/wp-content/uploads/2019/12/Best-Practice-Guides-Release-2_Digitalv3.pdf (accessed on 30 June 2021).
- ioXt Alliance. ioXt Pledge—The Global Standard for IoT Security. Available online: https://static1.squarespace.com/static/5c6dbac1f8135a29c7fbb621/t/5fb43a05bda7c3689ea5bd32/1605646853608/ioXt+Pledge+Book_Secure.pdf (accessed on 30 June 2021).
- International Organization for Standardization. Cybersecurity—IoT Security and Privacy—Guidelines. Available online: https://www.iso.org/standard/44373.html (accessed on 30 June 2021).
- Trusted Computing Group. Trusted Computing Group Glossary. Version 1.1. Available online: https://trustedcomputinggroup.org/wp-content/uploads/TCG-Glossary-V1.1-Rev-1.0.pdf (accessed on 30 June 2021).
- GlobalPlatform, Inc. GlobalPlatform Security Task Force Root of Trust Definitions and Requirements. Available online: https://globalplatform.org/wp-content/uploads/2018/06/GP_RoT_Definitions_and_Requirements_v1.0.1_PublicRelease_CC.pdf (accessed on 30 June 2021).
- Arm. Arm® Platform Security Requirements 1.0. Available online: https://developer.arm.com/documentation/den0106/latest/ (accessed on 30 June 2021).
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A comprehensive survey. ACM Comput. Surv. 2019, 51, 36. [Google Scholar] [CrossRef]
- Arm. Learn the Architecture: TrustZone for AArch64. Available online: https://developer.arm.com/documentation/102418/0100 (accessed on 24 June 2021).
- Zhao, S.; Zhang, Q.; Hu, G.; Qin, Y.; Feng, D. Providing Root of Trust for ARM TrustZone using On-Chip SRAM. In Proceedings of the 4th International Workshop on Trustworthy Embedded Devices—TrustED ’14, Scottsdale, AZ, USA, 3 November 2014; pp. 25–36. [Google Scholar]
- Arm. CryptoCell-300 Family. Available online: https://developer.arm.com/ip-products/security-ip/cryptocell-300-family (accessed on 24 June 2021).
- Arm. CryptoCell-700 Family. Available online: https://developer.arm.com/ip-products/security-ip/cryptocell-700-family (accessed on 24 June 2021).
- Wallace, J. Arm CryptoCell-312: Simplifying the Design of Secure IoT Systems. 2016. Available online: https://community.arm.com/developer/ip-products/system/b/embedded-blog/posts/arm-trustzone-cryptocell-312-simplifying-the-design-of-secure-iot-systems (accessed on 24 June 2021).
- Nordic Semiconductor. CRYPTOCELL—ARM® TrustZone® CryptoCell 310. 2021. Available online: https://infocenter.nordicsemi.com/index.jsp?topic=%2Fps_nrf52840%2Fcryptocell.html (accessed on 24 June 2021).
- Anati, I.; Gueron, S.; Johnson, S.; Scarlata, V. Innovative technology for CPU based attestation and sealing. In Proceedings of the 2nd International Workshop on Hardware and Architectural Support for Security and Privacy; ACM: New York, NY, USA, 2013; Volume 13, p. 7. [Google Scholar]
- Intel SGX-Remote Attestation. Available online: https://software.intel.com/content/www/us/en/develop/topics/software-guard-extensions/attestation-services.html (accessed on 30 June 2021).
- Costan, V.; Devadas, S. Intel SGX Explained. Available online: https://eprint.iacr.org/2016/086.pdf (accessed on 30 June 2021).
- Intel SGX—Security Essentials Solution Brief. Available online: https://www.intel.com/content/dam/www/public/us/en/documents/solution-briefs/intel-security-essentials-solution-brief.pdf (accessed on 30 June 2021).
- Intel SGX—IoT Edge Devices. Available online: https://software.intel.com/content/www/us/en/develop/topics/software-guard-extensions.html (accessed on 30 June 2021).
- Brasser, F.; Müller, U.; Dmitrienko, A.; Kostiainen, K.; Capkun, S.; Sadeghi, A.R. Software Grand Exposure:{SGX} Cache Attacks are Practical. Available online: https://www.usenix.org/conference/woot17/workshop-program/presentation/brasser (accessed on 30 June 2021).
- Van Bulck, J.; Minkin, M.; Weisse, O.; Genkin, D.; Kasikci, B.; Piessens, F.; Silberstein, M.; Wenisch, T.F.; Yarom, Y.; Strackx, R. Foreshadow: Extracting the keys to the intel {SGX} kingdom with transient out-of-order execution. In Proceedings of the 27th {USENIX} Security Symposium ({USENIX} Security 18), Baltimore, MD, USA, 15–17 August 2018; pp. 991–1008. [Google Scholar]
- Chen, G.; Chen, S.; Xiao, Y.; Zhang, Y.; Lin, Z.; Lai, T.H. Sgxpectre: Stealing intel secrets from sgx enclaves via speculative execution. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 142–157. [Google Scholar]
- Murdock, K.; Oswald, D.; Garcia, F.D.; Van Bulck, J.; Gruss, D.; Piessens, F. Plundervolt: Software-based fault injection attacks against Intel SGX. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 17–21 May 2020; pp. 1466–1482. [Google Scholar]
- Lee, D.; Kohlbrenner, D.; Shinde, S.; Asanović, K.; Song, D. Keystone: An open framework for architecting trusted execution environments. In Proceedings of the Fifteenth European Conference on Computer Systems, Heraklion, Greece, 27–30 April 2020; pp. 1–16. [Google Scholar]
- OpenTitan—Open Source Silicon Root of Trust. Available online: https://opentitan.org/ (accessed on 30 June 2021).
- OpenTitan—Hardware Dashboard. Available online: https://docs.opentitan.org/hw/ (accessed on 30 June 2021).
- OpenTitan—Earl Gray Top Level Specification. Available online: https://docs.opentitan.org/hw/top_earlgrey/doc/ (accessed on 30 June 2021).
- Barker, E.; Kelsey, J.; National Institute of Standards and Technology. NIST Special Publication 800-90A, Revision 1: Recommendation for Random Number Generation Using Deterministic Random Bit Generators. Available online: https://csrc.nist.gov/publications/detail/sp/800-90a/rev-1/final (accessed on 30 June 2021).
- Barker, E.; Kelsey, J.; National Institute of Standards and Technology. NIST Special Publication 800-90C (Second Draft): Recommendation for Random Number Generator (RBG) Constructions. Available online: https://csrc.nist.gov/publications/detail/sp/800-90c/draft (accessed on 30 June 2021).
- OpenTitan—Logical Security Model. Available online: https://docs.opentitan.org/doc/security/logical_security_model/ (accessed on 30 June 2021).
- NXP. SE050 Plug and Trust Secure Element. Available online: https://www.nxp.com/docs/en/data-sheet/SE050-DATASHEET.pdf (accessed on 30 June 2021).
- NXP. AN12413-SE050 APDU Specification—Application Note—Rev. 2.12. Available online: https://www.nxp.com.cn/docs/en/application-note/AN12413.pdf (accessed on 30 June 2021).
- Beyond Semiconductor. GEON SoC Security Platform. 2021. Available online: https://www.beyondsemi.com/116/geon-security-platform/ (accessed on 30 June 2021).
- Beyond Semiconductor. GEON Secure Boot. 2021. Available online: https://www.beyondsemi.com/117/geon-secure-boot/ (accessed on 30 June 2021).
- Beyond Semiconductor. GEON Secure JTAG. 2021. Available online: https://www.beyondsemi.com/119/geon-secure-jtag/ (accessed on 30 June 2021).
- Root of Trust RT-100. Foundational Security for SoCs and FPGAs. Available online: https://go.rambus.com/root-of-trust-rt-100-product-brief (accessed on 30 June 2021).
- Root of Trust RT-130. Foundational Security for SoCs and FPGAs for IoT Servers, Gateways and Edge Devices. Available online: https://go.rambus.com/root-of-trust-rt-130-product-brief (accessed on 30 June 2021).
- Root of Trust RT-140. Foundational Security for SoCs and FPGAs for Cloud-Connected Devices. Available online: https://go.rambus.com/root-of-trust-rt-140-product-brief (accessed on 30 June 2021).
- Root of Trust RT-260. Foundational Security for SoCs and FPGAs for Secure MCU Devices. Available online: https://go.rambus.com/root-of-trust-rt-260-product-brief (accessed on 30 June 2021).




| No. | Requirement | NIST | ENISA | IETF IRTF | GSMA | IoTSF | ioXt |
|---|---|---|---|---|---|---|---|
| Cat. 1 | Hardware Security | ||||||
| 1.1 | Utilization of immutable Hardware Root of Trust (HWRoT—Trust Anchor)—trusted component that extends the chain of trust to other HW, FW, SW components | - | X | X[32] | X | X | - |
| 1.2 | HW provided security features (memory locking, storage for cryptographic keys, secure boot support, device authentication, communication confidentiality and integrity, …) | X | X | X[32] | X | X | - |
| 1.3 | Measures for tamper protection and detection | - | X | - | X | X | - |
| 1.4 | Use of proven/cryptographic quality Random Number Generator (hardware-based if feasible) | - | X | X[31,32] | X | - | - |
| Cat. 2 | Trust and integrity management | ||||||
| 2.1 | Secure boot process based on HWRoT. Boot process initializes the main hardware components, verifies executed code (first-, second-stage bootloader, OS) and results in environment determined to be in an uncompromised state | - | X | - | X | X | X |
| 2.2 | Software (code, applications) must be signed cryptographically and verified upon installation or execution | - | X | - | X | X | X |
| 2.3 | The ability to restore last known secure state (e.g., firmware rollback, when code is verified as damaged or tampered) | - | X | - | X | X | - |
| 2.4 | Software installation control in operating systems (OS), to prevent unauthenticated software and files from being loaded onto it | - | X | - | - | - | - |
| Cat. 3 | Data protection and software design | ||||||
| 3.1 | Encryption of data storage medium. Possibility of locking or erasing device contents remotely | X | X | X[32] | - | X | - |
| 3.2 | Ensuring that data is secure prior to use by the process (input data validation) | - | X | X[32] | - | X | - |
| 3.3 | Process privilege minimization - limited permission of allowed actions, applications must operate at the lowest privilege level possible | - | X | X[31] | X | X | - |
| 3.4 | Utilization of memory compartmentalization to prevent rogue or compromised applications from accessing memory areas that they are not authorized to use, process isolation | - | X | X[31] | X | X | - |
| Cat. 4 | Device configuration and software update | ||||||
| 4.1 | The ability to change the device’s FW and SW configuration by authorized entities | X | - | X[32,33] | X | X | - |
| 4.2 | The ability to update device’s FW and SW through remote or local means by authorized entities | X | X | X[31,32] | X | X | X |
| 4.3 | Update file must be encrypted, signed and device verifies its integrity before application | X | X | X[31,32,33] | X | X | - |
| 4.4 | Automatic update capability (checking at frequent, but irregular intervals), enabled by default | X | X | X[31,33] | X | - | X |
| 4.5 | Backward compatibility of updates—update should not change network protocol interfaces nor modify user-configured preferences, security and/or privacy settings | - | X | X[31] | - | - | - |
| Cat. 5 | Secure interfaces and communication | ||||||
| Interface security | |||||||
| 5.1 | Ability to disable or logically restrict access (e.g., device/user authentication) to any local and network interfaces | X | X | - | - | X | X |
| 5.2 | Deployed device should never contain debugging, diagnostic or testing interfaces that could be abused by adversary (JTAG, CLI, Telnet, etc.) | - | X | X[32] | X | X | X |
| Protocol security | |||||||
| 5.3 | Ensure that communication security is provided using state-of-the-art, standardized security protocols (e.g., TLS for encryption) | - | X | X[32] | X | X | - |
| 5.4 | Mutual authentication of the devices must be performed before trust can be established (prevent man in the top attack), even when given device leaves and re-joins network | - | X | X[31] | X | X | X |
| 5.5 | Make intentional connections. Prevent unauthorized connections to product or other devices it is connected to, at all levels of the protocols. IoT devices must provide notice and/or request a user confirmation when initially pairing, onboarding, and/or connecting with other devices, platforms or services. | - | X | X[32] | - | X | X |
| Data security | |||||||
| 5.6 | Guarantee different security aspects of the transmitted data—confidentiality, integrity, authenticity | - | X | X[31,32] | X | - | - |
| Cat. 6 | Cybersecurity event monitoring and logging | ||||||
| 6.1 | The ability to log cybersecurity events from device’s HW, FW and SW | X | X | X[32] | X | X | - |
| 6.2 | The ability to record sufficient details for each logged event to facilitate an authorized entity examining the log and determining issue origin | X | - | X[32] | X | X | - |
| 6.3 | The ability to restrict access to the logs so only authorized entities can view them and prevent all entities (authorized or unauthorized) from editing them | X | X | X[32] | - | X | - |
| 6.4 | Avoid security issues when designing error messages. An error message should give/display only the concise information the user needs—it must not expose sensitive information that can be exploited by an attacker, such as an error ID, the version of the web server, etc. | - | X | X[32] | - | X | - |
| 6.5 | Device’s behavior should be monitored and compared with model to detect anomalies (e.g., erratic reboots/resets, (dis)connections, different network fingerprint, repeated malformed messages sent, etc.) | - | - | - | X | - | - |
| Cat. 7 | Cryptography and key management | ||||||
| 7.1 | Use of Standard Cryptographic Algorithms and Security Protocols, which implementations have been independently reviewed | X | X | X[31,32,33] | - | X | X |
| 7.2 | Security protocols should support algorithm agility (lightweight cryptography for resource constrained devices, ability to change algorithm or use it only with longer key in case it is compromised) | X | X | X[31,33] | - | X | - |
| 7.3 | Length of the key should provide strong security, make brute-force attack infeasible | - | X | X[31] | - | X | - |
| 7.4 | Every device must be instantiated with unique private key(s) | - | X | X[31] | X | X | - |
| 7.5 | Secure and scalable management of cryptographic keys (generation, storage, distribution) | - | X | X[31] | X | X | - |
| Cat. 8 | Device identification, authentication, strong default security | ||||||
| 8.1 | Device must have a unique physical identifier only authorized entities can access | X | X | - | X | X | - |
| 8.2 | Device must be provisioned with unique logical identifier | X | X | X[32] | X | - | - |
| 8.3 | Prepare robust authentication and authorization schemes, so device can prove its identity | X | X | - | X | X | - |
| 8.4 | Establish strong, device-individual default passwords that has to be changed by the user during initial setup (weak, null or blank passwords are not allowed) | - | X | X[31,32] | X | X | X |
| 8.5 | Resistance to keyspace-searching, brute-force or other login abusive attacks by limiting number of invalid login attempts or introducing incrementing delays between them | - | X | X[31,32] | X | - | - |
| 8.6 | Availability of two-factor authentication | - | X | X[31] | X | X | - |
| 8.7 | Product security shall be appropriately enabled by default. Strong security controls should be something the consumer has to deliberately disable rather than deliberately enable. | - | X | X[31] | - | X | X |
| No. | Requirement | Arm TrustZone | Intel SGX | Keystone | Open Titan | NXP SE050 | GEON SoC | Rambus RT |
|---|---|---|---|---|---|---|---|---|
| Cat. 1 | Hardware Security | |||||||
| 1.1 | Immutable Hardware Root of Trust | ●* | ● | ◖ | ● | ● | ● | ● |
| 1.2 | HW provided security features | ● | ◖ | ◖ | ● | ● | ● | ● |
| 1.3 | Tamper protection and detection | ●* | ● | ◖ | ● | ● | ◖ | ◖ |
| 1.4 | Random Number Generator (hardware-based if feasible) | ●* | ● | ◖ | ● | ◖ | ● | ● |
| Cat. 2 | Trust and integrity management | |||||||
| 2.1 | Secure boot process based on HWRoT. | ● | ● | ◖ | ◖/● | ◖ | ● | ● |
| 2.2 | Software (code, applications) signed cryptographically and verified upon installation or execution | ●* | ● | ◖ | ◖ | ◖ | ● | ◖ |
| 2.3 | Restore last known secure state (e.g., firmware rollback, when code is verified as damaged or tampered) | ●* | ◖ | ◖ | ● | ◯ | ● | ◯ |
| 2.4 | Software installation control in OS, to prevent unauthenticated software and files from being loaded onto it | ●* | ◖ | ◖ | ◖ | ◯ | ● | ◖ |
| Cat. 3 | Data protection and software design | |||||||
| 3.1 | Encryption of data storage medium. | ◖ | ● | ◖ | ◖ | ◖ | ◖ | ◖ |
| 3.2 | Input data validation | ◖ | ● | ◖ | ◖ | ◖ | ◖ | ◯ |
| 3.3 | Process privilege minimization | ◖ | ◖ | ● | ◖ | ◯ | ◯ | ◯ |
| 3.4 | Memory compartmentalization, process isolation | ● | ● | ● | ◖ | ◯ | ◯ | ◯ |
| Cat. 4 | Device configuration and software update | |||||||
| 4.1 | Changing the device’s FW and SW configuration by authorized entities | ●* | ● | ◖ | ● | ◖ | ● | ◖ |
| 4.2 | Updating device’s FW and SW through remote or local means by authorized entities | ◖ | ● | ◖ | ● | ◖ | ◖ | ◖ |
| 4.3 | Update file must be encrypted, signed and device verifies its integrity before application | ●* | ● | ◖ | ● | ◖ | ● | ● |
| 4.4 | Automatic update capability | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| 4.5 | Backward compatibility of updates | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| Cat. 5 | Secure interGfaces and commGunication | |||||||
| Interface security | ||||||||
| 5.1 | Ability to disable or logically restrict access to any local and network interfaces | ◖ | ◖ | ◖ | ◖ | ◯ | ◯ | ◯ |
| 5.2 | Deployment without debugging, diagnostic or testing interfaces that could be abused by adversary | ◖ | ◖ | ◖ | ◖ | ◖ | ● | ◖ |
| Protocol security | ||||||||
| 5.3 | Communication security using state-ofthe-art, standardized security protocols (e.g., TLS for encryption) | ●* | ● | ◖ | ◖ | ● | ◖ | ● |
| 5.4 | Mutual authentication of the devices before trust can be established (prevent man in the middle attack) | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| 5.5 | Prevent unauthorized connections to product or other devices it is connected to, at all levels of the protocols. | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◯ |
| Data security | ||||||||
| 5.6 | Confidentiality, integrity and authenticity of the transmitted data | ●* | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| Cat. 6 | Cybersecurity event monitoring and logging | |||||||
| 6.1 | Logging cybersecurity events from device’s HW, FW and SW | ◖ | ◖ | ◖ | ◯/◖ | ◯ | ◖ | ◖ |
| 6.2 | Recording sufficient details for each logged event | ◖ | ◖ | ◖ | ◯/◖ | ◯ | ◖ | ◖ |
| 6.3 | Restricting access to the logs to authorized entities only and prevent all entities from editing them | ◖ | ◖ | ◖ | ◯/◖ | ◖ | ◖ | ◖ |
| 6.4 | Avoid security issues when designing error messages. | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| 6.5 | Device’s behavior should be monitored and compared with model to detect anomalies | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| Cat. 7 | Cryptography and key management | |||||||
| 7.1 | Use of Standard Cryptographic Algorithms and Security Protocols | ●* | ◖ | ◖ | ● | ● | ● | ● |
| 7.2 | Security protocols should support algorithm agility | ●* | ◖ | ◖ | ◖ | ● | ● | ● |
| 7.3 | Length of the key should provide strong security, make brute-force attack infeasible | ◖ | ◖ | ◖ | ● | ◖ | ◖ | ◖ |
| 7.4 | Every device must be instantiated with unique private key(s) | ●* | ◖ | ◖ | ● | ◖ | ◖ | ● |
| 7.5 | Secure and scalable management of cryptographic keys (generation, storage, distribution) | ●* | ◖ | ◖ | ● | ◖ | ● | ● |
| Cat. 8 | Device identification, authentication, strong default security | |||||||
| 8.1 | Unique physical identifier only authorized entities can access | ●* | ◖ | ● | ● | ◖ | ◖ | ◖ |
| 8.2 | Device must be provisioned with unique logical identifier | ◖ | ◖ | ◖ | ● | ◖ | ◖ | ◖ |
| 8.3 | Robust authentication and authorization schemes | ◖ | ◖ | ◖ | ● | ◖ | ◖ | ◖ |
| 8.4 | Strong, device-individual default passwords that has to be changed by the user during initial setup | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| 8.5 | Limiting number of invalid login attempts or introducing incrementing delays between them | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
| 8.6 | Availability of two-factor authentication | ◖ | ◖ | ◖ | ● | ◖ | ◖ | ◖ |
| 8.7 | Product security shall be appropriately enabled by default. | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ | ◖ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chmiel, M.; Korona, M.; Kozioł, F.; Szczypiorski, K.; Rawski, M. Discussion on IoT Security Recommendations against the State-of-the-Art Solutions. Electronics 2021, 10, 1814. https://doi.org/10.3390/electronics10151814
Chmiel M, Korona M, Kozioł F, Szczypiorski K, Rawski M. Discussion on IoT Security Recommendations against the State-of-the-Art Solutions. Electronics. 2021; 10(15):1814. https://doi.org/10.3390/electronics10151814
Chicago/Turabian StyleChmiel, Marta, Mateusz Korona, Fryderyk Kozioł, Krzysztof Szczypiorski, and Mariusz Rawski. 2021. "Discussion on IoT Security Recommendations against the State-of-the-Art Solutions" Electronics 10, no. 15: 1814. https://doi.org/10.3390/electronics10151814
APA StyleChmiel, M., Korona, M., Kozioł, F., Szczypiorski, K., & Rawski, M. (2021). Discussion on IoT Security Recommendations against the State-of-the-Art Solutions. Electronics, 10(15), 1814. https://doi.org/10.3390/electronics10151814








