Research Challenges for the Internet of Things: What Role Can OR Play?
Abstract
:1. Introduction
2. The Internet of Things
2.1. General Concept of the IoT
2.2. Research Challenges for the Future IoT
- Privacy and data protection;
- Global misinformation systems;
- Big data problems;
- Public attitudes, opinions and behavior;
- Tightly coupled systems;
- Quality of service issues;
- New forms of risk; and
- Linking the IoT to work on responsible innovation
2.3. Development of Standards for the Future IoT
- IPv6 over Low Power Wireless Personal Area Networks which defines IPv6 adaption layer and header compression suitable for constrained radio links;
- Routing over Low Power and Lossy Networks (ROLL), which focusses on routing protocols for constrained-node networks; and
- Constrained Restful Environments which aims to extend Web architecture to most constrained networks and embedded devices.
“An infrastructure of interconnected objects, people, systems and information resources together with intelligent services to allow them to process information of the physical and the virtual world and react.”
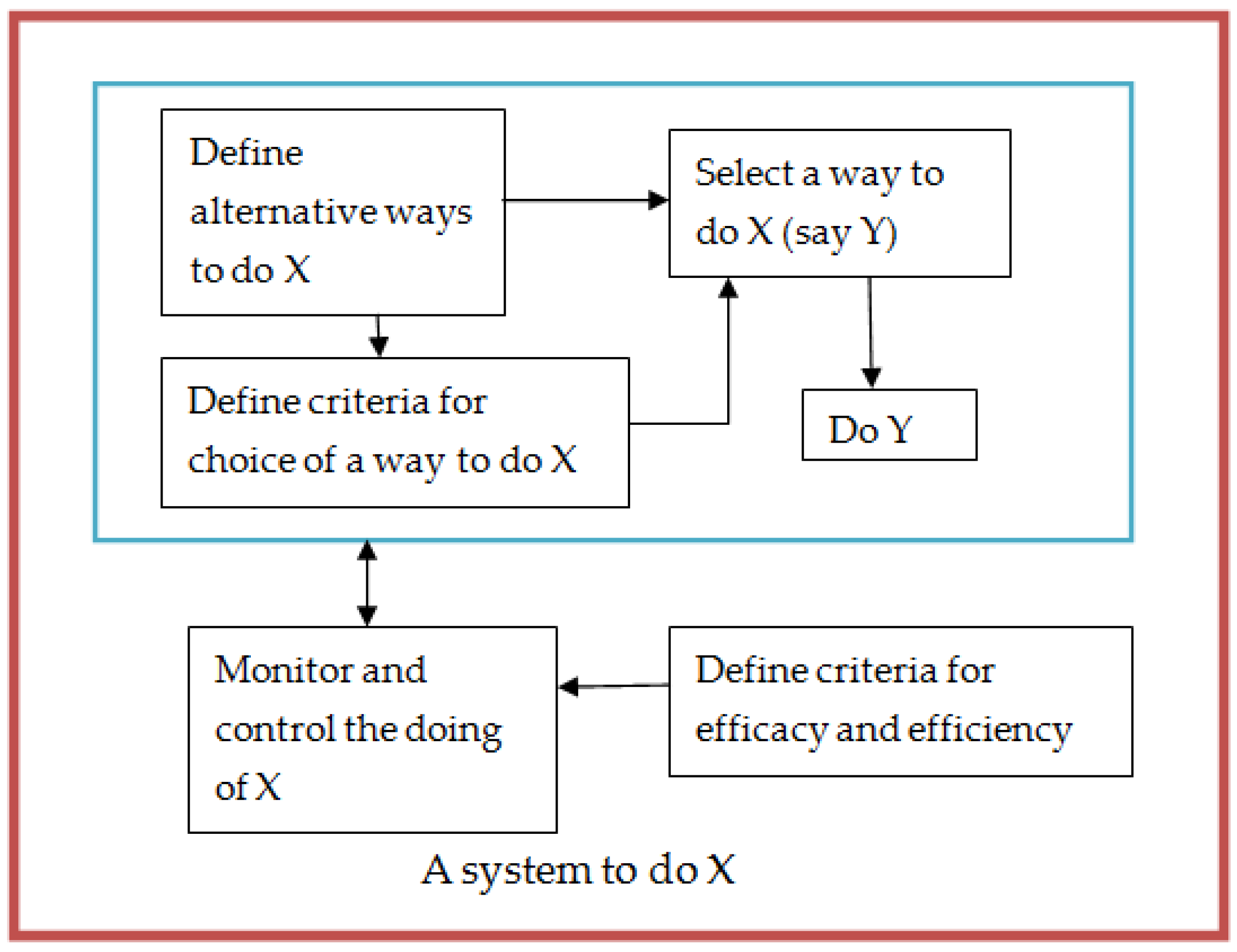
3. How can OR Support the Future IoT?
3.1. The Mathematical Tools and Techniques of OR Which May Support the IoT
3.1.1. Data Analytics/Databases
3.1.2. Decision Analysis/Support Systems Including Analytic Hierarchy Process (AHP), Multi-Criteria Decision Making (MCDM) and Data Envelopment Analysis (DEA)
3.1.3. Game Theory
3.1.4. Simulation
3.1.5. Fuzzy Systems Theory/Artificial Neural Networks
3.1.6. Routing/Scheduling
3.1.7. Reliability Theory
3.1.8. Queuing Theory
3.1.9. Graph Theory
3.1.10. Other OR Techniques
3.1.11. Summary
3.2. Application of General Systems Thinking to the IoT
3.2.1. General Systems Theory (GST)/Complexity Theory
3.2.2. Self-Organizing Systems Theory
3.2.3. Cybernetics/Systems Dynamics
3.2.4. Soft Systems
3.2.5. CST/Multimethodology
4. Detailed Discussion of some IoT Research Challenges Which OR and Systems Thinking May Help Address
4.1. IoT Scalability Studied Using Simulation
4.2. IoT Robustness Studied Using Reliability Theory
4.3. IoT Business Investment Studied Using Game Theory
4.4. Complex Adaptive Systems Theory and the IoT
4.5. Self-Organizing Systems and the IoT
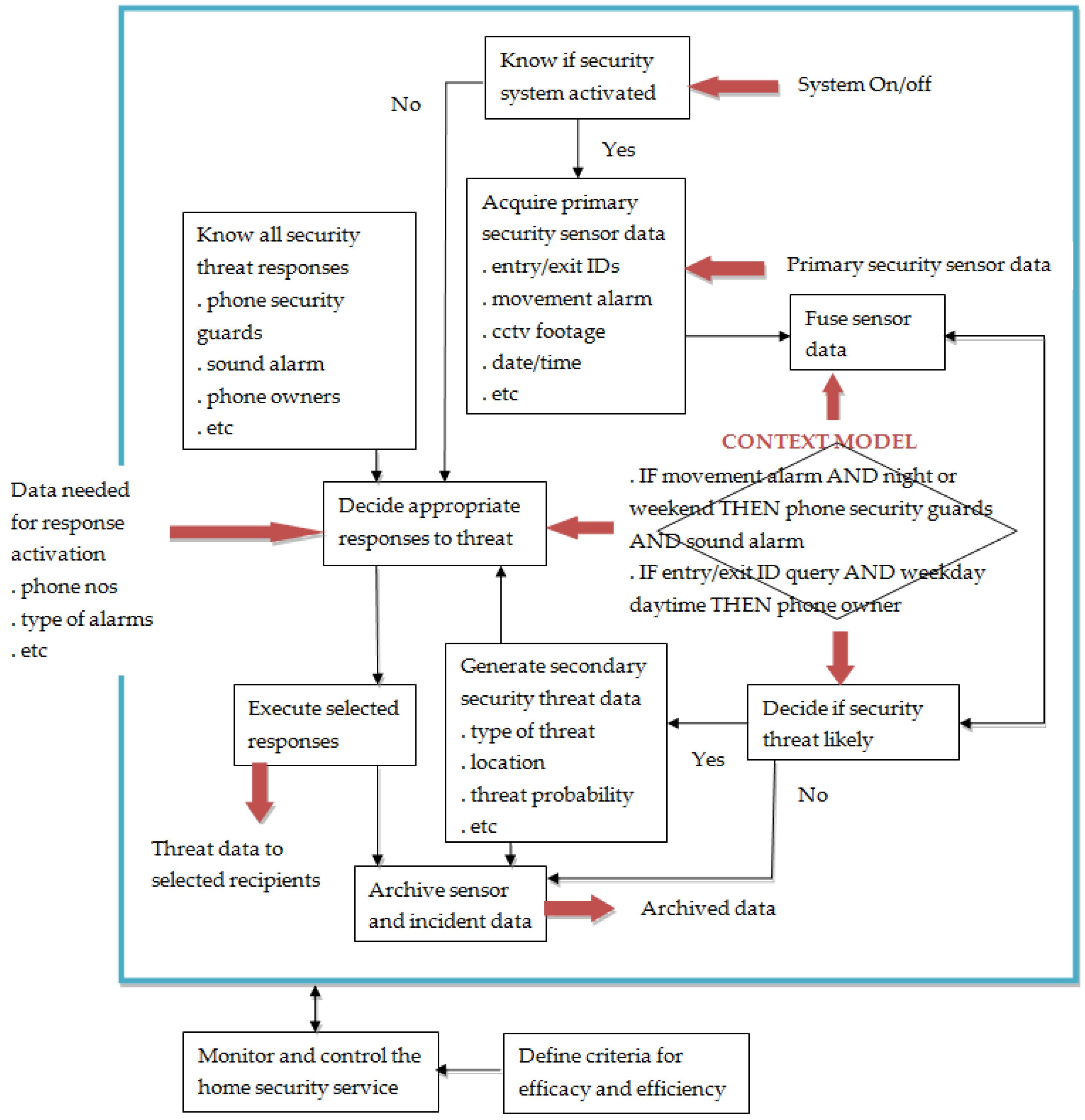
4.6. Intelligence and Context Awareness in the IoT
“A system to provide home security by, when activated, collecting primary security sensor data including entry and exit of people, movements in the property and CCTV images of areas of the property, fusing sensor data, deciding if a security threat is likely, deciding appropriate responses to take to security threats by means of a context model and generated secondary threat data, executing chosen responses, and archiving of sensor and incident data”.
- Fusion of sensor data;
- Deciding if a security threat is likely; and
- Deciding on appropriate responses to a threat
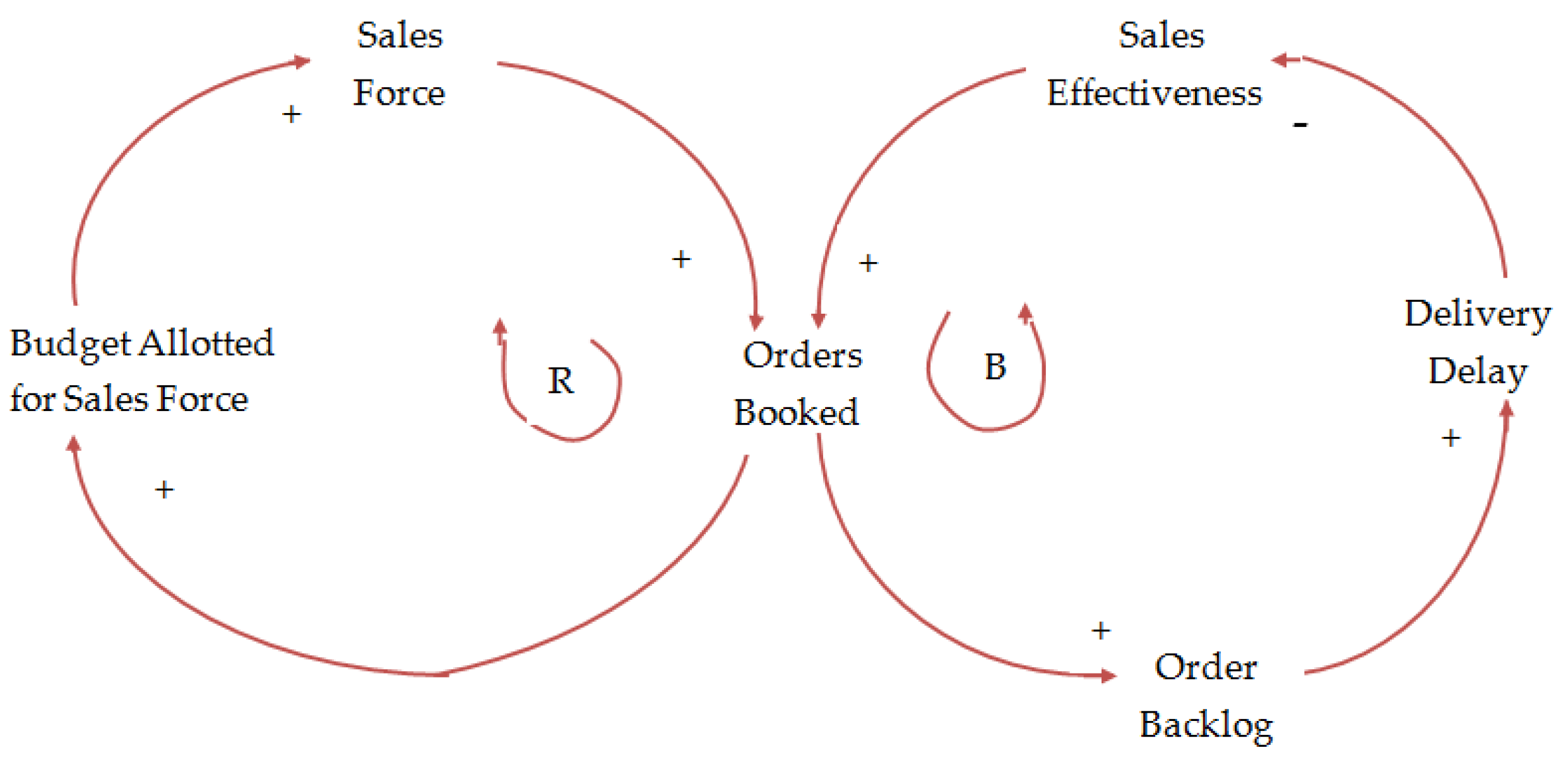
4.7. IoT Software Development—An Application of System Dynamics
- Real-time train and bus schedules
- Smart traffic signalling
- Smart parking
- Autonomous and cooperative vehicles
- “Uber” vehicle sharing
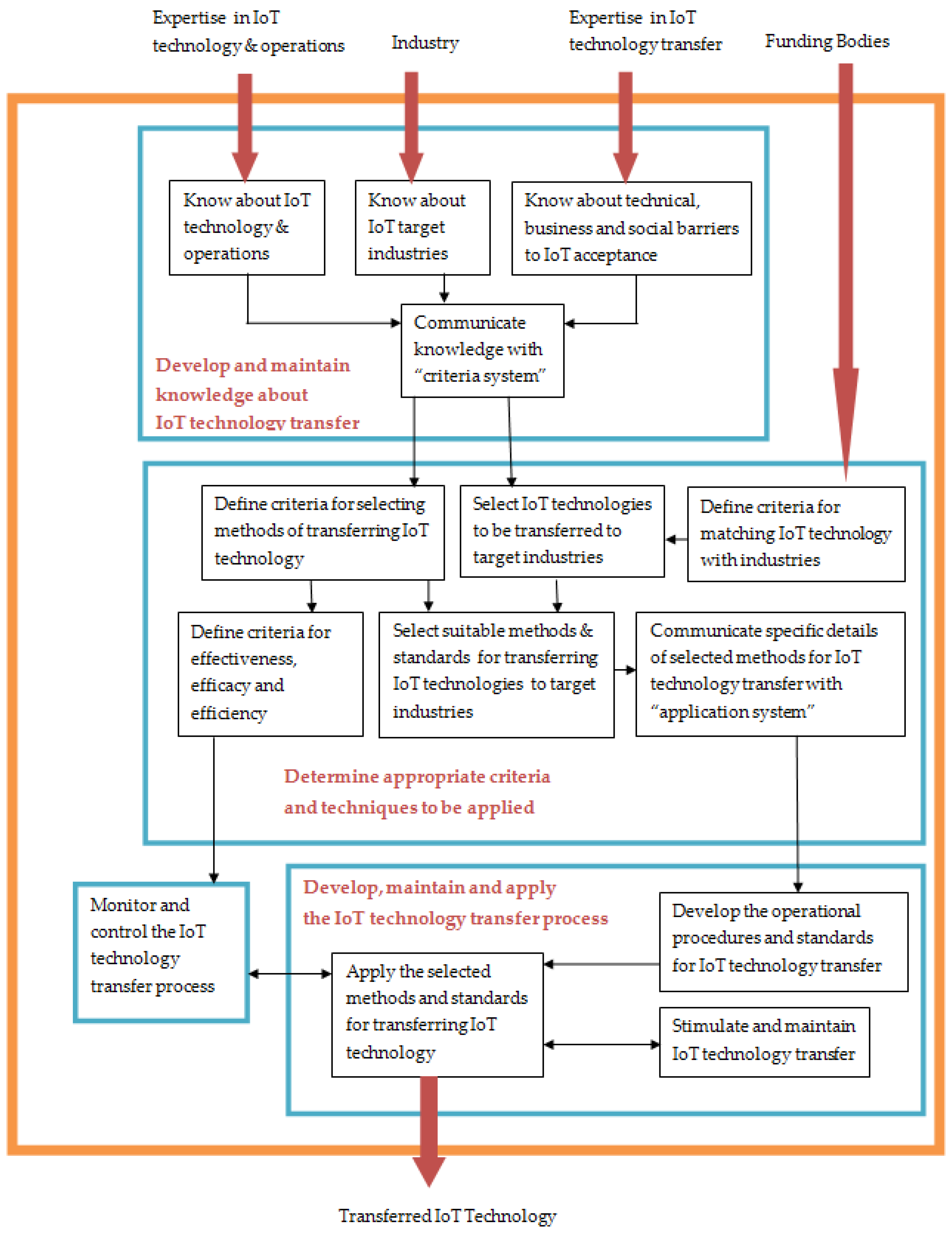
4.8. IoT Technology Transfer—An Application of SSM
“An industry driven system operating within SDOs with the objective of transferring IoT technology by: knowing about IoT technology and operations, knowing the technical, business and social barriers to acceptance, knowing about targeted industries, selecting IoT technology to be transferred, selecting means of transferring IoT technology, applying those means to targeted industries, stimulating the ongoing transfer, and monitoring the success of such transfers; in order to benefit all involved parties, in an environment of standards, industrial competitiveness, and national and international economic development.”
- C
- Industry that can benefit from IoT technology transfer
- A
- SDO researchers who wish to promote IoT technology
- T
- Untransferred IoT technology becomes transferred technology
- W
- Transfer of IoT technology is desirable
- O
- Industry (that has the power to accept or reject transferred IoT technology)
- E
- International SDOs/Industrial Competitiveness/National and International Economies
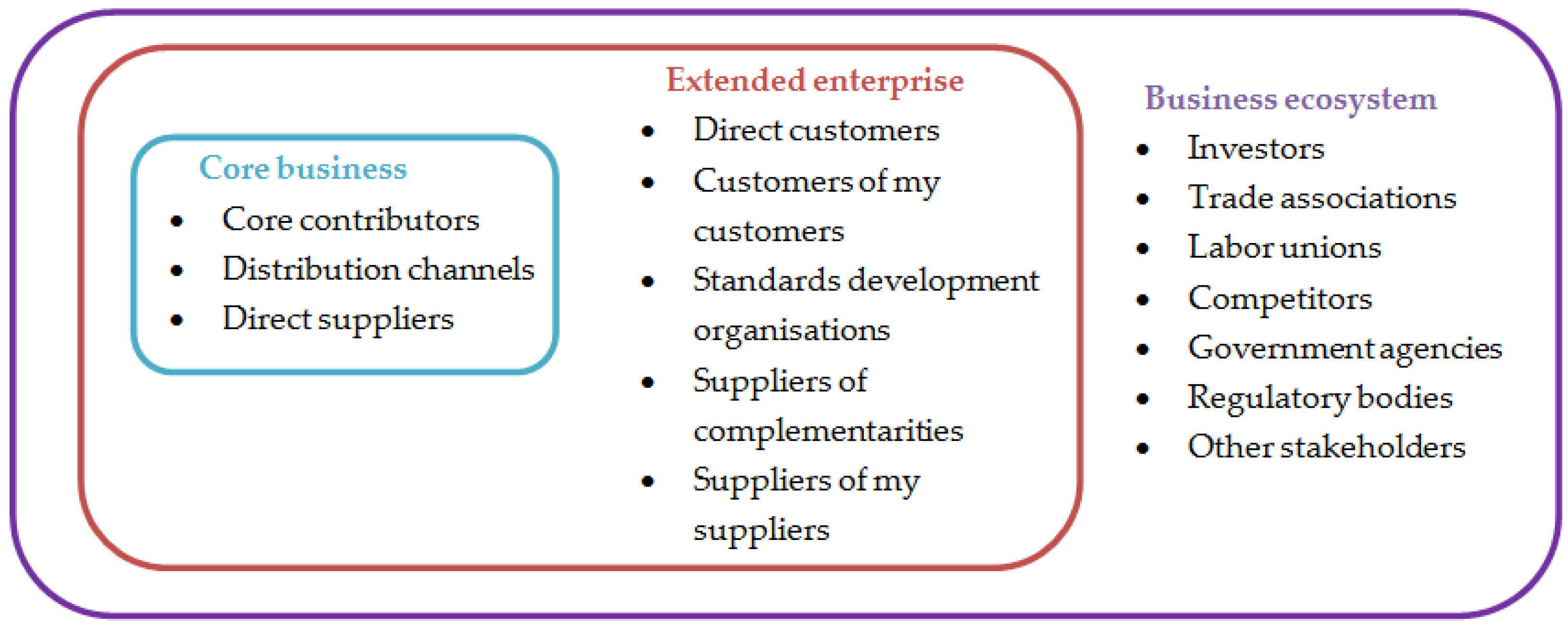
4.9. Industry Investment in IoT—An Application of the Multimethodology Approach
“A composition of systems in which its constituent systems are individually discovered, selected, and composed possibly at run-time to build a more complex system. The constituent systems are managed (at least in part) for their own purposes rather than the purposes of the whole and maintain a continuing operational existence independent of the collaborative system. The resulting composed system (the SoS) is more complex and offers more functionality and performance than simply the sum of its constituent systems.”
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Mortenson, M.J.; Doherty, N.F.; Robinson, S. Operational research from Taylorism to Terabytes: A research agenda for the analytics age. Eur. J. Oper. Res. 2015, 241, 583–595. [Google Scholar] [CrossRef]
- Mingers, J.; White, L. A review of the recent contribution of systems thinking to operational research and management science. Eur. J. Oper. Res. 2010, 207, 1147–1161. [Google Scholar] [CrossRef]
- IEEE. P2413—Standard for an Architectural Framework for the Internet of Things (IoT). 2016. Available online: https://standards.ieee.org/develop/project/2413.html (accessed on 12 March 2017).
- Borgia, E. The Internet of Things vision: Key features, applications and open issues. Comput. Commun. 2014, 54, 1–31. [Google Scholar] [CrossRef]
- Jain, R. Internet of Things: Challenges and Issues. In Proceedings of the 20th Annual Conference on Advanced Computing and Communications (ADCOM 2014), Bangalore, India, 19–22 September 2014.
- Stankovic, J.A. Research directions for the internet of things. IEEE Internet Things J. 2014, 1, 3–9. [Google Scholar] [CrossRef]
- Mattern, F.; Floerkemeier, C. From the Internet of Computers to the Internet of Things. In From Active Data Management to Event-Based Systems and More; Springer: Berlin, Germany, 2010; pp. 242–259. [Google Scholar]
- Elkhodr, M.; Shahrestani, S.; Cheung, H. The Internet of Things: Vision & Challenges. In Proceedings of the TENCON Spring Conference, Sydney, Australia, 17–19 April 2013; pp. 218–222.
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Chen, S.; Xu, H.; Liu, D.; Hu, B.; Wang, H. A vision of IoT: Applications, challenges, and opportunities with China perspective. IEEE Internet Things J. 2014, 1, 349–359. [Google Scholar] [CrossRef]
- Muralidharan, S.; Roy, A.; Saxena, N. An Exhaustive Review on Internet of Things from Korea’s Perspective. Wirel. Pers. Commun. 2016, 90, 1463–1486. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Borgia, E. Special Issue on Ïnternet of Things: Research Challenges and Solutions (editorial). Comput. Commun. 2016, 89, 1–4. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernandez-Carames, T.M.; Suarez-Albela, M.; Castedo, L.; Gonzalez-Lopez, M. A review on internet of things for defense and public safety. Sensors 2016, 16, 1644. [Google Scholar] [CrossRef] [PubMed]
- Dijkman, R.M.; Sprenkels, B.; Peeters, T.; Janssen, A. Business models for the Internet of Things. Int. J. Inf. Manag. 2015, 35, 672–678. [Google Scholar] [CrossRef]
- Kim, S.; Kim, S. A multi-criteria approach toward discovering killer IoT application in Korea. Technol. Forecast. Soc. Chang. 2016, 102, 143–155. [Google Scholar] [CrossRef]
- Lee, I.; Lee, K. The Internet of Things (IoT): Applications, investments, and challenges for enterprises. Bus. Horiz. 2015, 58, 431–440. [Google Scholar] [CrossRef]
- Mazhelis, O.; Luoma, E.; Warma, H. Defining an internet-of-things ecosystem. In Internet of Things, Smart Spaces, and Next Generation Networking; Springer: Berlin, Germany, 2012; pp. 1–14. [Google Scholar]
- Westerlund, M.; Leminen, S.; Rajahonka, M. Designing business models for the internet of things. Technol. Innov. Manag. Rev. 2014, 4, 5. [Google Scholar]
- Mishra, D.; Gunasekaran, A.; Childe, S.J.; Papadopoulos, T.; Dubey, R.; Wamba, S. Vision, applications and future challenges of Internet of Things: A bibliometric study of the recent literature. Ind. Manag. Data Syst. 2016, 116, 1331–1355. [Google Scholar] [CrossRef]
- UK Technology Strategy Board (TSB). A Roadmap for Interdisciplinary Research on the Internet of Things; Internet of Things Special Interest Group: London, UK, 2012. [Google Scholar]
- Dutton, W.H.; Capra, L.; Ciaraldi, M.; Evans, D.; Furness, A.; Graham, I.; Jirotka, M.; Kupai, A.; Maguire, M.; Matthews, N.; et al. A Roadmap for Interdisciplinary Research on the Internet of Things: Social Sciences; Internet of Things Special Interest Group, Technology Strategy Board: London, UK, 2013. [Google Scholar]
- Innovate UK. IoT Special Interest Group, Internet of Things (IoT) and Machine to Machine Communications (M2M) Challenges and Opportunities; Innovate UK: London, UK, 2013. [Google Scholar]
- Rose, K.; Eldridge, S.; Chapin, L. The internet of things: An overview. In Understanding the Issues and Challenges of a More Connected World; The Internet Society (ISOC): Washington, DC, USA, 2015; pp. 1–50. [Google Scholar]
- Dutton, W. Putting Things to Work: Social and Policy Challenges for the Internet of Things. In Internet of Things Meetup; Culham Science Centre, Culham: Abingdon, UK, 2014. [Google Scholar]
- Dutton, W.H. The Internet of Things. Oxford Institute, 2013. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2324902 (accessed on 12 March 2017).
- European Research Cluster on the Internet of Things (IERC). Available online: http://www.internet-of-things-research.eu/documents.htm (accessed on 12 March 2017).
- Ishaq, I.; Carels, D.; Teklemariam, G.K.; Hoebeke, J.; Van den Abeele, F.; De Poorter, E.; Moerman, I.; Demeester, P. IETF Standardization in the field of the internet of things (IoT): A survey. J. Sens. Actuator Netw. 2013, 2, 235–287. [Google Scholar] [CrossRef]
- Internet Society. Internet of Things: Standards and Guidance from the IETF. 2016. Available online: https://www.internetsociety.org/publications/ietf-journal-april-2016/internet-things-standards-and-guidance-ietf (accessed on 12 March 2017).
- ISO/IEC JTC1. Resolutions Adopted at the 28th Meeting of ISO/IEC JTC1 (N11894). In ISO/IEC JTC1 Plenary; ISO/IEC: Perros-Guirec, France, 2013. [Google Scholar]
- ISO/IEC JTC1. Internet of Things Preliminary Report (2014); ISO/IEC: Geneva, Switzerland, 2014. [Google Scholar]
- ISO/IEC JTC1. ISO/IEC JTC1 N13119 Text of CD 30141 Information Technology; ISO/IEC: Geneva, Switzerland, 2016. [Google Scholar]
- ISO/IEC JTC1. Resolutions Adopted at the 31st Meeting of ISO/IEC JTC1 (N13270). In ISO/IEC JTC1 Plenary; ISO/IEC: Lillehammer, Norway, 2016. [Google Scholar]
- IEEE. IEEE Internet of Things. 2016. Available online: http://iot.ieee.org/ (accessed on 12 March 2017).
- ITU. Internet of Things Global Standards Initiative. 2016. Available online: http://www.itu.int/en/ITU-T/gsi/iot/Pages/default.aspx (accessed on 12 March 2017).
- Gustavsson, P.; Serbinski, M. The Internet of Things and the Future of M&S—Where are We Going and What are the Opportunities? In Proceedings of the 2015 Fall Simulation Interoperability Workshop, Orlando, FL, USA, 31 August–4 September 2015.
- Lessman, K.; Riecken, M.; O’Connor, M.J. Modeling & Simulation of the Internet of Things and Cyber Physical Systems for Cybersecurity. In Proceedings of the Simulation Innovation Workshop, Orlando, FL, USA, 11–16 September 2016.
- Kondepudi, S. IOT Standards Wars. In Forum on Internet of Things: Empowering the New Urban Agenda; ITU: Geneva, Switzerland, 2015. [Google Scholar]
- Brown, B.R. What the Internet of Things Needs: Systems Engineering. International Council on Systems Engineering News. 2016. Available online: http://www.ecnmag.com/blog/2016/04/what-internet-things-needs-systems-engineering (accessed on 11 March 2017).
- Kljajić, M.; Farr, J.V. Chapter 4: Importance of Systems Engineering in the Development of Information Systems. In Emerging Systems Approaches in Information Technologies; Paradice, D., Ed.; Information Science Reference (an Imprint of IGI Global): New York, NY, USA, 2010. [Google Scholar]
- O’Connor, R.V.; Laporte, C.Y. The Evolution of the ISO/IEC 29110 Set of Standards and Guides. Int. J. Inf. Technol. Syst. Approach 2017, 10, 1–21. [Google Scholar] [CrossRef]
- White, B. A complex adaptive systems engineering (CASE) methodology—The ten-year update. In Proceedings of the 2016 Annual IEEE Systems Conference (SysCon), Orlando, FL, USA, 18–21 April 2016; pp. 1–8.
- Xue, R.; Baron, C.; Esteban, P.; Sahraoui, A. Aligning systems engineering and project management standards to improve the management of processes. In Progress in Systems Engineering; Springer: Heidelberg, Germany, 2015; pp. 547–553. [Google Scholar]
- Daellenbach, H.G.; Flood, R.L. The Informed Student Guide to Management Science; Thomson Learning: London, UK, 2002. [Google Scholar]
- Cooper, J.; James, A. Challenges for database management in the internet of things. IETE Tech. Rev. 2009, 26, 320–329. [Google Scholar] [CrossRef]
- Ma, M.; Wang, P.; Chu, C.H. Data Management for Internet of Things: Challenges, Approaches and Opportunities. In Proceedings of the Green Computing and Communications (GreenCom), 2013 IEEE and Internet of Things (iThings/CPSCom), IEEE International Conference on and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 1144–1151.
- Petkov, D.; Petkova, O.; Andrews, T.; Nepal, T. Mixing multiple criteria decision making with soft systems thinking techniques for decision support in complex situations. Decis. Support Syst. 2007, 43, 1615–1629. [Google Scholar] [CrossRef]
- Haghighi, M.; Maraslis, K.; Tryfonas, T.; Oikonomou, G.; Burrows, A.; Woznowski, P.; Piechocki, R. Game Theoretic approach towards Optimal Multi-tasking and Data-distribution in IoT. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 406–411.
- Wang, J.; Liao, J.; Li, T.; Wang, J. Game-theoretic model of asymmetrical multipath selection in pervasive computing environment. Pervasive Mob. Comput. 2016, 27, 37–57. [Google Scholar] [CrossRef]
- Brandenburger, A.M.; Nalebuff, B.J. The right game: Use game theory to shape strategy. Harvard Bus. Rev. 1995, 73, 57–71. [Google Scholar]
- Dyk, M.; Najgebauer, A.; Pierzchala, D. SenseSim: An agent-based and discrete event simulator for Wireless Sensor Networks and the Internet of Things. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 345–350.
- Musznicki, B.; Zwierzykowski, P. Survey of simulators for wireless sensor networks. Int. J. Grid Distrib. Comput. 2012, 5, 23–50. [Google Scholar]
- Wightman, P.M.; Labrador, M.A. Atarraya: A simulation tool to teach and research topology control algorithms for wireless sensor networks. In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, Rome, Italy, 2–6 March 2009.
- Korkalainen, M.; Sallinen, M.; Karkkainen, N.; Tukeva, P. Survey of Wireless Sensor Networks Simulation Tools for Demanding Applications. In Proceedings of the 2009 Fifth International Conference on Networking and Services, Valencia, Spain, 20–25 April 2009.
- Ribeiro, R.A.; Falcao, A.; Mora, A.; Fonseca, J.M. FIF: A fuzzy information fusion algorithm based on multi-criteria decision making. Knowl.-Based Syst. 2014, 58, 23–32. [Google Scholar] [CrossRef]
- Nakamura, E.F.; Loureiro, A.A.; Frery, A.C. Information fusion for wireless sensor networks: Methods, models, and classifications. ACM Comput. Surv. 2007, 39, 9. [Google Scholar] [CrossRef]
- De Coninck, E.; Verbelen, T.; Vankeirsbilck, B.; Bohez, S.; Simoens, P.; Demeester, P.; Dhoedt, B. Distributed neural networks for Internet of Things: The Big-Little approach. In Proceedings of the 2nd EAI International Conference on Software Defined Wireless Networks and Cognitive Technologies for IoT, Rome, Italy, 26–27 October 2015; pp. 1–9.
- Chen, D.; Chang, G.; Sun, D.; Li, J.; Jia, J.; Wang, X. TRM-IoT: A trust management model based on fuzzy reputation for internet of things. Comput. Sci. Inf. Syst. 2011, 8, 1207–1228. [Google Scholar] [CrossRef]
- Dhumane, A.; Prasad, R.; Prasad, J. Routing Issues in Internet of Things: A Survey. In Proceedings of the International MultiConference of Engineers and Computer Scientists, Hong Kong, China, 16–18 March 2016; pp. 16–18.
- Yong-Fei, L.; Li-Qin, T. Comprehensive evaluation method of Reliability of Internet of Things. In Proceedings of the 2014 Ninth International Conference on P2P, Parallel, Grid, Cloud and Internet Computing (3PGCIC), Guangzhou, China, 8–10 November 2014; pp. 262–266.
- Mneimneh, S. Computer Networks A Gentle Introduction to Queuing Theory; Hunter College of CUNY: New York, NY, USA, 2013. [Google Scholar]
- Mahamure, S.; Railkar, P.N.; Mahall, N. Communication Protocol and Queueing Theory-based Modelling for the Internet of Things. J. ICT 2016, 3, 157–176. [Google Scholar]
- Euler, L. Leonhard Euler and the Königsberg bridges. Sci. Am. 1953, 189, 66–70. [Google Scholar] [CrossRef]
- Yao, B.; Liu, X.; Zhang, W.; Chen, X.; Zhang, X.; Yao, M.; Zhao, Z. Applying Graph theory to the Internet of Things. In Proceedings of the 2013 IEEE 10th International Conference on High Performance Computing and Communications & 2013 IEEE International Conference on Embedded and Ubiquitous Computing, Zhangjiajie, China, 13–15 November 2013.
- Pirzada, S. Applications of graph theory. PAMM 2007, 7, 2070013. [Google Scholar] [CrossRef]
- Shirinivas, S.; Vetrivel, S.; Elango, N. Applications of graph theory in computer science an overview. Int. J. Eng. Sci. Technol. 2010, 2, 4610–4621. [Google Scholar]
- Holland, J.H. Adaptation in natural and artificial systems. In An Introductory Analysis with Application to Biology, Control, and Artificial Intelligence; University of Michigan Press: Ann Arbor, MI, USA, 1975. [Google Scholar]
- Esmaeili, M.; Jamali, S. A Survey: Optimization of Energy Consumption by using the Genetic Algorithm in WSN based Internet of Things. Wirel. Commun. 2016, 8, 65–73. [Google Scholar]
- Singh, K.; Aggarwal, A. Survey on Optimization Techniques of RFID for Internet of Things. Int. J. Comput. Appl. 2016, 148, 9. [Google Scholar] [CrossRef]
- Fortino, G.; Russo, W.; Savaglio, C. Simulation of Agent-oriented Internet of Things Systems. In Proceedings of the 17th Workshop” From Objects to Agents, Catania, Italy, 29–30 July 2016.
- Houston, C.; Gooberman-Hill, S.; Mathie, R.; Kennedy, A.; Li, Y.; Baiz, P. Case Study for the Return on Investment of Internet of Things Using Agent-Based Modelling and Data Science. Systems 2017, 5, 4. [Google Scholar] [CrossRef]
- Jackson, M.C.; Keys, P. Towards a system of systems methodologies. J. Oper. Res. Soc. 1984, 35, 473–486. [Google Scholar] [CrossRef]
- Von Bertalanffy, L. General Systems Theory: Foundations, Development, Applications. JAMA 1968, 208, 870. [Google Scholar]
- Courtney, J.; Merali, Y.; Paradice, D.; Wynn, E. On the study of complexity in information systems. Int. J. Inf. Technol. Syst. Approach 2008. [Google Scholar] [CrossRef]
- Holland, J.H. Hidden Order: How Adaptation Builds Complexity; Basic Books: New York, NY, USA, 1995. [Google Scholar]
- Bar-Yam, Y. Dynamics of Complex Systems; Addison-Wesley: Reading, MA, USA, 1997. [Google Scholar]
- Banzhaf, W. Self-organizing Systems. In Encyclopedia of Complexity and Systems Science; Springer: Heidelberg, Germany, 2009; pp. 8040–8050. [Google Scholar]
- Ashby, W.R. Principles of the self-organizing dynamic system. J. Gener. Psychol. 1947, 37, 125–128. [Google Scholar] [CrossRef] [PubMed]
- Mingers, J. Self-Producing Systems: Implications and Applications of Autopoiesis; Springer Science & Business Media: New York, NY, USA, 1994. [Google Scholar]
- Wiener, N. Cybernetics; Hermann: Paris, France, 1948. [Google Scholar]
- Beer, S. The viable system model: Its provenance, development, methodology and pathology. J. Oper. Res. Soc. 1984, 35, 7–25. [Google Scholar] [CrossRef]
- Watson, R.B.; Smith, R. A Macro Analysis of the RAAF Logistics System. In Proceedings of the Australian Society for Operations Research 7th National Conference, Adelaide, Australia, 26–28th August 1985.
- Watson, R.B. Suggestions for new application areas for soft systems methodology in the information age. Syst. Pract. Action Res. 2012, 25, 441–456. [Google Scholar] [CrossRef]
- Ulrich, W. Operational research and critical systems thinking—an integrated perspective Part 1: OR as applied systems thinking. J. Oper. Res. Soc. 2012, 63, 1228–1247. [Google Scholar] [CrossRef]
- Mingers, J.; Brocklesby, J. Multimethodology: Towards a framework for mixing methodologies. Omega 1997, 25, 489–509. [Google Scholar] [CrossRef]
- Howick, S.; Ackermann, F. Mixing OR methods in practice: Past, present and future directions. Eur. J. Oper. Res. 2011, 215, 503–511. [Google Scholar] [CrossRef]
- D’Angelo, G.; Ferretti, S.; Ghini, V. Simulation of the Internet of Things. In Proceedings of the IEEE 2016 International Conference on High Performance Computing and Simulation (HPCS 2016), Innsbruck, Austria, 18–22 July 2016.
- D’Angelo, G.; Ferretti, S.; Ghini, V. Multi-level simulation of Internet of Things on smart territories. Simul. Model. Pract. Theory 2016. [Google Scholar] [CrossRef]
- Zola, E.; Martin-Escanola, I.; Barcelo-Arroyo, F. Discrete Event Simulation of Wireless Cellular Networks. In Discrete Event Simulations; Goti, A., Ed.; InTech: Vienna, Austria, 2010. [Google Scholar]
- Kempf, J.; Arkko, J.; Beheshti, N.; Yedavalli, K. Thoughts on reliability in the internet of things. In Proceedings of the Interconnecting Smart Objects with the Internet Workshop, Prague, Czech, 25–26 March 2011; pp. 1–4.
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, Helsinki, Finland, 13–17 August 2012.
- Madsen, H.; Burtschy, B.; Albeanu, G.; Popentiu-Vladicescu, F. Reliability in the utility computing era: Towards reliable fog computing. In Proceedings of the 2013 20th International Conference on Systems, Signals and Image Processing (IWSSIP), Bucharest, Romania, 7–9 July 2013.
- Niyato, D.; Lu, X.; Wang, P.; Kim, D.I.; Han, Z. Economics of Internet of Things: An information market approach. IEEE Wirel. Commun. 2016, 23, 136–145. [Google Scholar] [CrossRef]
- Turk, M. Internet of Things: Are We There Yet? (The 2016 IoT Landscape). 2016. Available online: http://mattturck.com/2016/03/28/2016-iot-landscape/ (accessed on 12 March 2017).
- Lee, K.-H.; Baldick, R. Solving three-player games by the matrix approach with application to an electric power market. IEEE Trans. Power Syst. 2003, 18, 1573–1580. [Google Scholar]
- Mitleton-Kelly, E. Ten principles of complexity and enabling infrastructures. In Complex Systems and Evolutionary Perspectives on Organisations: The Application of Complexity Theory to Organisations; Elsevier Science: Oxford, UK, 2003; pp. 23–50. [Google Scholar]
- Anish, S.; Gupta, A. Insights from Complexity Theory: Understanding Organizations Better. ISSUES 2010. Available online: http://tejas.iimb.ac.in/articles/12.php (accessed on 11 March 2017).
- Chan, S. Complex adaptive systems. In ESD. 83 Research Seminar in Engineering Systems; MIT: Cambridge, MA, USA, 2001. [Google Scholar]
- Rupert, M.; Hassas, S.; Rattrout, A. The web and complex adaptive systems. In Proceedings of the 20th International Conference on Advanced Information Networking and Applications (AINA’06), Vienna, Austria, 18–20 April 2006; pp. 200–204.
- Grisogono, A.-M.; Ryan, A. Designing complex adaptive systems for defence. In Proceedings of the Systems Engineering Test and Evaluation Conference, Canberra, Australia, 27–29 October 2003.
- Ryan, A.; Grisogono, A.-M. Hybrid complex adaptive engineered systems: A case study in defence. In Proceedings of the International Conference on Complex Systems, Boston, MA, USA, 16–21 May 2004.
- Yan, C.; Ji-Hong, Q. Application analysis of complex adaptive systems for WSN. In Proceedings of the 2010 International Conference on Computer Application and System Modeling (ICCASM 2010), Taiyuan, China, 22–24 October 2010.
- Haghnevis, M.; Askin, R.G. A modeling framework for engineered complex adaptive systems. IEEE Syst. J. 2012, 6, 520–530. [Google Scholar] [CrossRef]
- Batool, K.; Niazi, M.A.; Sadik, S.; Shakil, A.R.R. Towards modeling complex wireless sensor networks using agents and networks: A systematic approach. In Proceedings of the TENCON 2014 IEEE Region 10 Conference, Bangkok, Thailand, 22–25 October 2014; pp. 1–6.
- Hernandez-Bravo, A.; Carretero, J. Approach to manage Complexity in Internet of Things. Procedia Comput. Sci. 2014, 36, 210–217. [Google Scholar] [CrossRef]
- Andrus, D.C. The wiki and the blog: Toward a complex adaptive intelligence community. Stud. Intell. 2005, 49, 3. [Google Scholar]
- Liu, W.; Li, X. A study of the application of self-organizing networks in designing appliances of Internet of Things. In Proceedings of the 2013 3rd International Conference on Consumer Electronics, Communications and Networks (CECNet), Xianning, China, 20–22 November 2013; pp. 45–48.
- Yamamoto, Y.; Kawabe, T.; Tsuruta, S.; Damiani, E.; Yoshitaka, A.; Mizuno, Y.; Knauf, R. Towards Self-Organizing Internet of Things-Aware Systems for Online Sales. In Proceedings of the 2015 11th International Conference on Signal-Image Technology & Internet-Based Systems (SITIS), Bangkok, Thailand, 23–27 November 2015; pp. 208–215.
- Athreya, A.P.; Tague, P. Network self-organization in the internet of things. In Proceedings of the 2013 10th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), New Orleans, LA, USA, 24–27 June 2013.
- Hong, J.-Y.; Suh, E.-H.; Kim, S.-J. Context-aware systems: A literature review and classification. Expert Syst. Appl. 2009, 36, 8509–8522. [Google Scholar] [CrossRef]
- Achilleos, A.; Yang, K.; Georgalas, N. Context modelling and a context-aware framework for pervasive service creation: A model-driven approach. Pervasive Mob. Comput. 2010, 6, 281–296. [Google Scholar] [CrossRef]
- Jameson, A. Modelling both the Context and the User. Pers. Ubiquitous Comput. 2001, 5, 29–33. [Google Scholar] [CrossRef]
- Baek, S.; Lee, H.; Lim, S.; Huh, J. Managing mechanism for service compatibility and interaction issues in context-aware ubiquitous home. IEEE Trans. Consum. Electron. 2005, 51, 524–528. [Google Scholar] [CrossRef]
- Mingers, J. The what/how distinction and conceptual models: A reappraisal. J. Appl. Syst. Anal. 1990, 17, 21–28. [Google Scholar]
- Checkland, P.; Poulter, J. Learning for Action: A Short Definitive Account of Soft Systems Methodology and Its Use, for Practitioners, Teachers and Students; John Wiley and Sons Ltd.: Chichester, UK, 2006. [Google Scholar]
- Wang, F.; Hu, L.; Hu, J.; Zhou, J.; Zhou, K. Recent Advances in the Internet of Things: Multiple Perspectives. IETE Tech. Rev. 2016. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Context aware computing for the internet of things: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 414–454. [Google Scholar] [CrossRef]
- Olsson, C.M.; Henfridsson, O. Designing context-aware interaction: An action research study. In Designing Ubiquitous Information Environments: Socio-Technical Issues and Challenges; Springer: Boston, MA, USA, 2005; pp. 233–247. [Google Scholar]
- Strang, T.; Linnhoff-Popien, C. A context modeling survey. In Proceedings of the Workshop Proceedings, Nottingham, UK, 22–23 January 2004.
- Imen, J.; Raoudha, B.D.; Hanene, B.A. Proposal for a Generic Context Metamodel. World Acad. Sci. Eng. Technol. Int. J. Comput. Electr. Autom. Control Inf. Eng. 2015, 8, 408–414. [Google Scholar]
- Ploesser, K. A Design Theory for Context-Aware Information Systems. Ph.D. Thesis, School of Information Systems, Science & Engineering Faculty, Queensland University of Technology, Brisbane, Australia, 2013; p. 302. [Google Scholar]
- Stowell, F. Towards client-led development of information systems. Inf. Syst. J. 1991, 1, 173–189. [Google Scholar] [CrossRef]
- Dutta, A.; Roy, R. System Dynamics Tutorial provides a primer on a set of tools and techniques aimed at improving decision-making in integrated value chain. OR MS TODAY 2002, 29, 30–35. [Google Scholar]
- Forrester, J.W. System dynamics—a personal view of the first fifty years. Syst. Dyn. Rev. 2007, 23, 345–358. [Google Scholar] [CrossRef]
- Dutta, A.; Roy, R. Internet diffusion in India and China-comparison based on feedback loop dominance. In Proceedings of the 37th Annual Hawaii International Conference on System Sciences, Big Island, HI, USA, 5–8 January 2004; p. 10.
- Cao, L.; Ramesh, B.; Abdel-Hamid, T. Modeling dynamics in agile software development. ACM Tran. Manag. Inf. Syst. 2010, 1, 5. [Google Scholar] [CrossRef]
- White, A. An Agile Project System Dynamics Simulation Model. Int. J. Inf. Technol. Syst. Approach 2014, 7, 55–79. [Google Scholar] [CrossRef]
- Lyneis, J.M.; Ford, D.N. System dynamics applied to project management: A survey, assessment, and directions for future research. Syst. Dyn. Rev. 2007, 23, 157–189. [Google Scholar] [CrossRef]
- Kljajić, M.; Borstnar, M.K.; Skraba, A.; Kofjac, D. System approach to MIS and DSS and its modeling within SD. Res. Methodol. Innov. Philos. Softw. Syst. Eng. Inf. Syst. 2012. [Google Scholar] [CrossRef]
- Madachy, R.; Boehm, B.; Lane, J.A. Assessing hybrid incremental processes for SISOS development. Softw. Process Improv. Pract. 2007, 12, 461–473. [Google Scholar] [CrossRef]
- Milojicic, D.; Nikolich, P.; Leiba, B. Standards for Tomorrow: The Internet of Things (Ubiquity symposium); Ubiquity: Copenhagen, Denmark, 2015; p. 1. [Google Scholar]
- Cowling, J.A.; Ivins, W.K. Assessing the Potential Improvement an Open Systems Development Perspective Could Offer to the Software Evolution Paradigm. Int. J. Inf. Technol. Syst. Approach 2016, 9, 68–87. [Google Scholar] [CrossRef]
- Sood, K.; Yu, S.; Xiang, Y. Software-Defined Wireless Networking Opportunities and Challenges for Internet-of-Things: A Review. IEEE Internet Things J. 2016, 3, 453–463. [Google Scholar] [CrossRef]
- Marshall, P. System dynamics modeling of the impact of Internet-of-Things on intelligent urban transportation. In Proceedings of the 2015 Regional Conference of the International Telecommunications Society (ITS), Los Angeles, CA, USA, 25–28 October 2015.
- Qu, T.; Thurer, M.; Wang, J.; Wang, Z.; Fu, H.; Li, C.; Huang, G.Q. System dynamics analysis for an Internet-of-Things-enabled production logistics system. Int. J. Prod. Res. 2016. [Google Scholar] [CrossRef]
- Hsu, A.P.; Lee, W.T.; Trappey, A.J.C.; Chang, A.-C.; Trappey, C.V. Using System Dynamics Analysis for Performance Evaluation of IoT Enabled One-Stop Logistic Services. In Proceedings of the 2015 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Hong Kong, China, 9–12 October 2015.
- Chevillard, S.V.; Guri, G.; Frete, O.; Clari, F.; Gluhak, A.; Vermesan, O.; Bahr, R.; Moretto, P. Report on the factors of user’s acceptance framework and societal and education stakeholders, H2020—UNIFY-IoT Project. 2016. European Research Cluster on the Internet of Things. Available online: http://www.internet-of-things-research.eu/index.html (accessed on 12 March 2017).
- Finegan, A. A methodology to design an expert system for remote sensing technology management. Int. Arch. Photogarmm. Remote Sens. 1993, 29, 982. [Google Scholar]
- Gil-Garcia, J.R.; Pardo, T.A. Multimethod Approaches to Understanding the Complexity of e-Government. Int. J. Comput. Syst. Signal 2006, 7, 3–17. [Google Scholar]
- Mingers, J. The paucity of multimethod research: A review of the information systems literature. Inf. Syst. J. 2003, 13, 233–249. [Google Scholar] [CrossRef]
- Delicato, F.C.; Pires, P.F.; Batista, T.; Cavalcante, E.; Costa, B.; Barros, T. Towards an IoT ecosystem. In Proceedings of the First International Workshop on Software Engineering for Systems-of-Systems, Montpellier, France, 1 July 2013; pp. 25–28.
- Peltoniemi, M. Business ecosystem: A conceptual model of an organisation population from the perspectives of complexity and evolution. In Research Reports 18; e-Business Research Center: Tampere, Finland, 2005. [Google Scholar]
- Fleisch, E. What is the internet of things? An economic perspective. Econ. Manag. Financ. Markets 2010, 2, 125–157. [Google Scholar]
- Dowling, A.M.; MacDonald, R.H.; Richardson, G.P. Simulation of systems archetypes. In Proceedings of the 1995 International System Dynamics Conference, Tokyo, Japan, 30 July–4 August 1995.
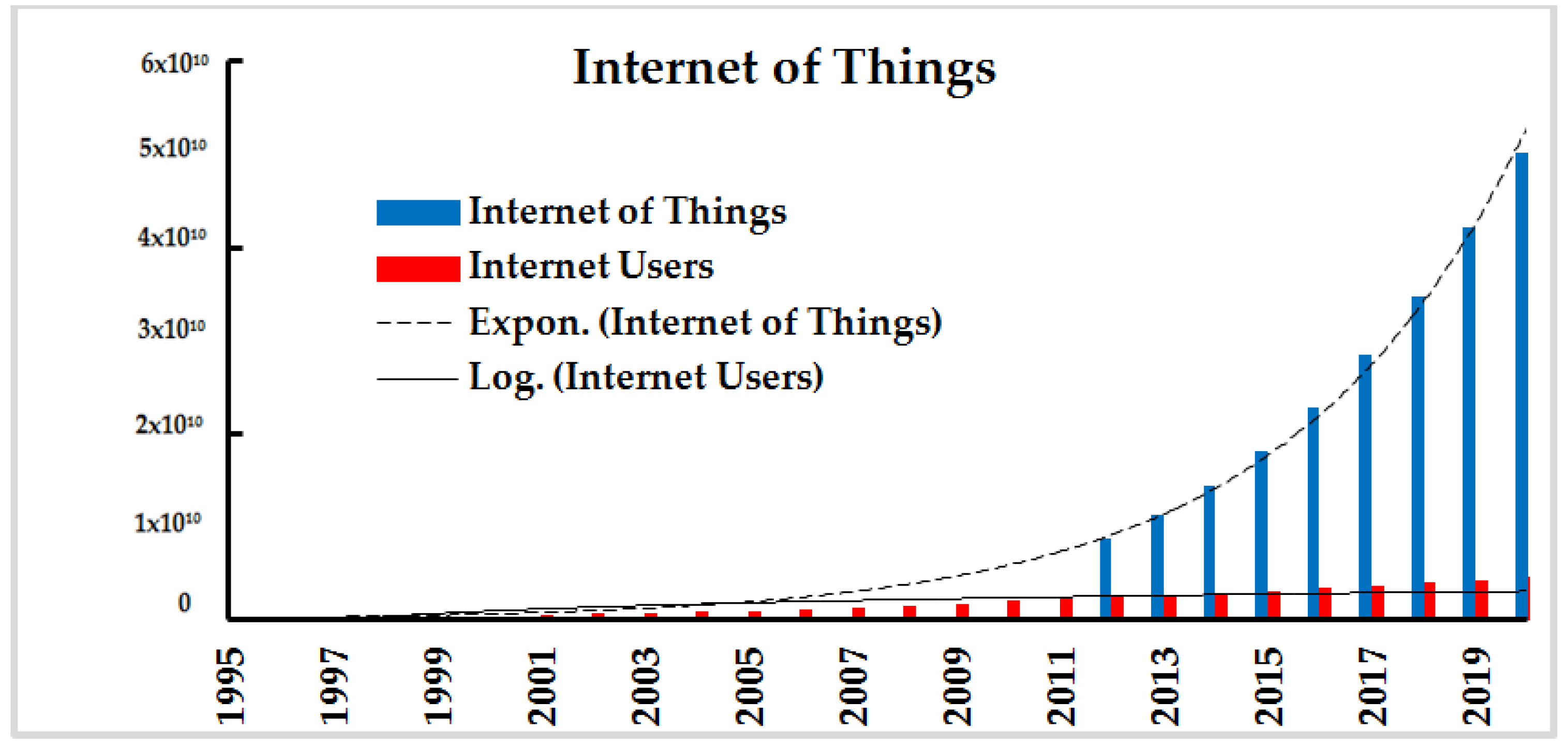
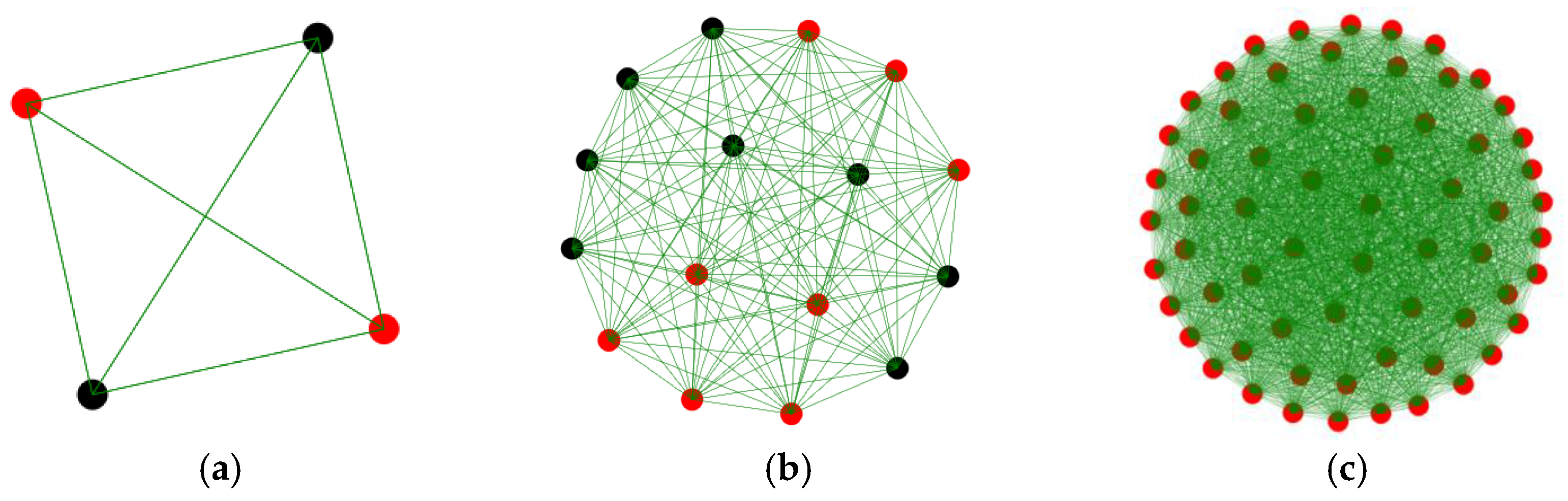

| Papers Mentioning | Borgia 2014 | Jain 2014 | Stankovic 2014 | Mattern 2010 | Elkhodr 2013 | Gubbi 2013 | Chen 2014 | Muralidharan 2016 | Al-Fuqaha 2015 |
|---|---|---|---|---|---|---|---|---|---|
| Design | |||||||||
| Architecture | x | x | x | x | x | x | |||
| Interoper-ability | x | x | x | x | x | x | |||
| Scalability | x | x | x | x | |||||
| Mobility | x | x | x | ||||||
| Security/Privacy | x | x | x | x | x | x | x | x | x |
| Scientific/Engineering | |||||||||
| Energy Efficiency/Power | x | x | x | x | x | ||||
| Reliability/Robustness | x | x | x | x | |||||
| Management/Operations | |||||||||
| Software Development | x | x | |||||||
| Availability | x | ||||||||
| Data Management/Information Fusion | x | x | x | x | x | x | |||
| Cloud Computing | x | x | |||||||
| Performance | x | x | x | ||||||
| ANSI/EIA-632 | IEEE-1220 | ISO/IEC-15288 | INCOSE HANDBOOK | SEBoK | |
|---|---|---|---|---|---|
| Content | 13 processes 34 requirements | 8 processes | 25 processes | 25 processes | 26 processes |
| Focus of systems life cycle | Conception and development | all systems | all systems | all systems | all systems |
| Pages | 110 | 70 | 70 | 400 | 850 |
| Level of details | 2/5 | 2/5 | 2/5 | 4/5 | 5/5 |
| Context of applications | Program and project environment | Program and project environment | Enterprise environment | Enterprise environment | External environment |
| Publication Year | 1998 | 2005 | 2008 | 2010 | 2013 |
| Reversion frequency | 2/5 | 2/5 | 5/5 | 3/5 | 1/5 |
| No. SEMPS | 3 | 1 | 12 | 12 | 12 |
| SEMP’s proportion | 3/13 | 1/14 | 12/25 | 12/25 | 12/26 |
| Method | Application |
|---|---|
| Game Theory | Multi-tasking, data distribution |
| Math programming—Linear, nonlinear, integer, dynamic | Network design |
| Simulation | Environmental effects on IoT |
| Neural Nets | Security; sensor data analysis |
| Stochastic (Markov) Processes | Reliability/robustness |
| Graph Theory | Network flow; Routing |
| Queueing Theory | Network response; |
| Critical Path Method | Network |
| Decision Analysis—Multi criteria, analytic hierarchy | Assessing business models for IoT |
| Genetic algorithms | Energy consumption |
| Optimization approaches | RFID |
| Agent-based modelling | Traffic load; protocol selection; smart object interaction |
| IoT Challenge | OR Tools/Techniques Applicable | Examples; Notes |
|---|---|---|
| Design | ||
| Architecture | Data analytics, optimization, game theory | Wang et al. [49] use GT to study architectures |
| Interoperability (Addressing/Naming Objects) | ||
| Scalability | Simulation | Musznicki and Zwierzykowski [52] |
| Mobility | Simulation | |
| Security/Privacy | Data analytics; fuzzy systems; graph theory | Chen et al. [58]; Yao et al. [64]; Shirinivas et al. [66] |
| Scientific/Engineering | ||
| Energy Efficiency/Power | Simulation; Game theory; decision analysis | Haghighi et al. [48]—GT; Kim et al. [16]—decision analysis |
| Reliability/Robustness | Reliability theory | Yong-fei et al. [60]—RT |
| Management/Operations | ||
| Software Development | Expect simulation to help? | Musznicki et al. [52] |
| Availability | Reliability theory; simulation should apply | |
| Data Management/Information Fusion | Game theory; data analytics | Cooper and James [45] Petkov et al. [47] |
| Cloud Computing | Decision analysis; data analytics | Cooper and James [45] Petkov et al. [47] |
| Performance (Quality of Service) | Optimisation; reliability theory; queuing theory; math programming; stochastic processes | |
| Business | ||
| Business Models | Decision analysis; Game theory; Agent-based modelling; Data analytics | Dijkman et al. [15]; Westurland et al. [19]; Houston et al. [71] |
| Use cases (e.g., Korea/China); killer apps (e.g., medical) | Decision analysis; MCDM | Kim et al. [16]; healthcare, energy |
| Systems Thinking Approach → | GST/Complexity Theory | Self-Organizing Systems Theory | Cybernetics/System Dynamics | Soft Systems | CST/Multimethodology |
|---|---|---|---|---|---|
| Network Design | x | x | x | x | |
| Complex Adaptive System | x | x | x | x | |
| Self Organizing System | x | x | x | x | |
| Intelligence & Context Awareness | x | x | x | x | x |
| Software Development | x | x | x | ||
| Network Management/Operations | x | x | x | x | |
| Technology Transfer | x | x | x | ||
| Politics/Cross Border Data Flows | x | x | |||
| Work Restructuring | x | x | |||
| Industry Investment in IoT | x | x | x | ||
| Ethical & Legal Framework of IoT | x | x | |||
| Security & Privacy | x | x |
| Company | Specialty | Potential Investment Area |
|---|---|---|
| Company A | Internal systems | External systems |
| Company B | External systems | Internal systems |
| Company C | Security systems | All non security systems |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ryan, P.J.; Watson, R.B. Research Challenges for the Internet of Things: What Role Can OR Play? Systems 2017, 5, 24. https://doi.org/10.3390/systems5010024
Ryan PJ, Watson RB. Research Challenges for the Internet of Things: What Role Can OR Play? Systems. 2017; 5(1):24. https://doi.org/10.3390/systems5010024
Chicago/Turabian StyleRyan, Peter J., and Richard B. Watson. 2017. "Research Challenges for the Internet of Things: What Role Can OR Play?" Systems 5, no. 1: 24. https://doi.org/10.3390/systems5010024
APA StyleRyan, P. J., & Watson, R. B. (2017). Research Challenges for the Internet of Things: What Role Can OR Play? Systems, 5(1), 24. https://doi.org/10.3390/systems5010024






