Bridging Policy and Practice: Integrated Model for Investigating Behavioral Influences on Information Security Policy Compliance
Abstract
1. Introduction
2. Literature Review
2.1. Information Security Policy Compliance
2.2. Theoretical Background
2.2.1. Operant Conditioning Theory (OCT)
2.2.2. Protection Motivation Theory (PMT)
2.2.3. Theory of Planned Behavior (TPB)
2.3. Hypothesis Development
2.3.1. The Relationship Between Perceived Severity and Intention to Comply with ISPs
2.3.2. The Relationship Between Perceived Vulnerability and Intention to Comply with ISPs
2.3.3. The Relationship Between Rewards and Intention to Comply with ISPs
2.3.4. The Relationship Between Punishment and Intention to Comply with ISPs
2.3.5. The Relationship Between Attitude and Intention to Comply with ISPs
2.3.6. The Relationship Between Subjective Norms and Intention to Comply with ISPs
2.3.7. The Relationship Between Perceived Behavioral Control and Intention to Comply with ISPs
2.3.8. The Relationship Between Intention to Comply with ISP and Actual Compliance Behavior with ISPs
2.4. Conceptual Model
3. Methodology
3.1. Research Design
3.2. Research Instrument
3.3. Sample and Data Collection
3.4. Ethical Considerations
4. Results
4.1. Demographic Profile
4.2. Measurement Model
4.3. Reliability and Validity of the Measurement Model
4.3.1. Convergent Validity
4.3.2. Discriminant Validity
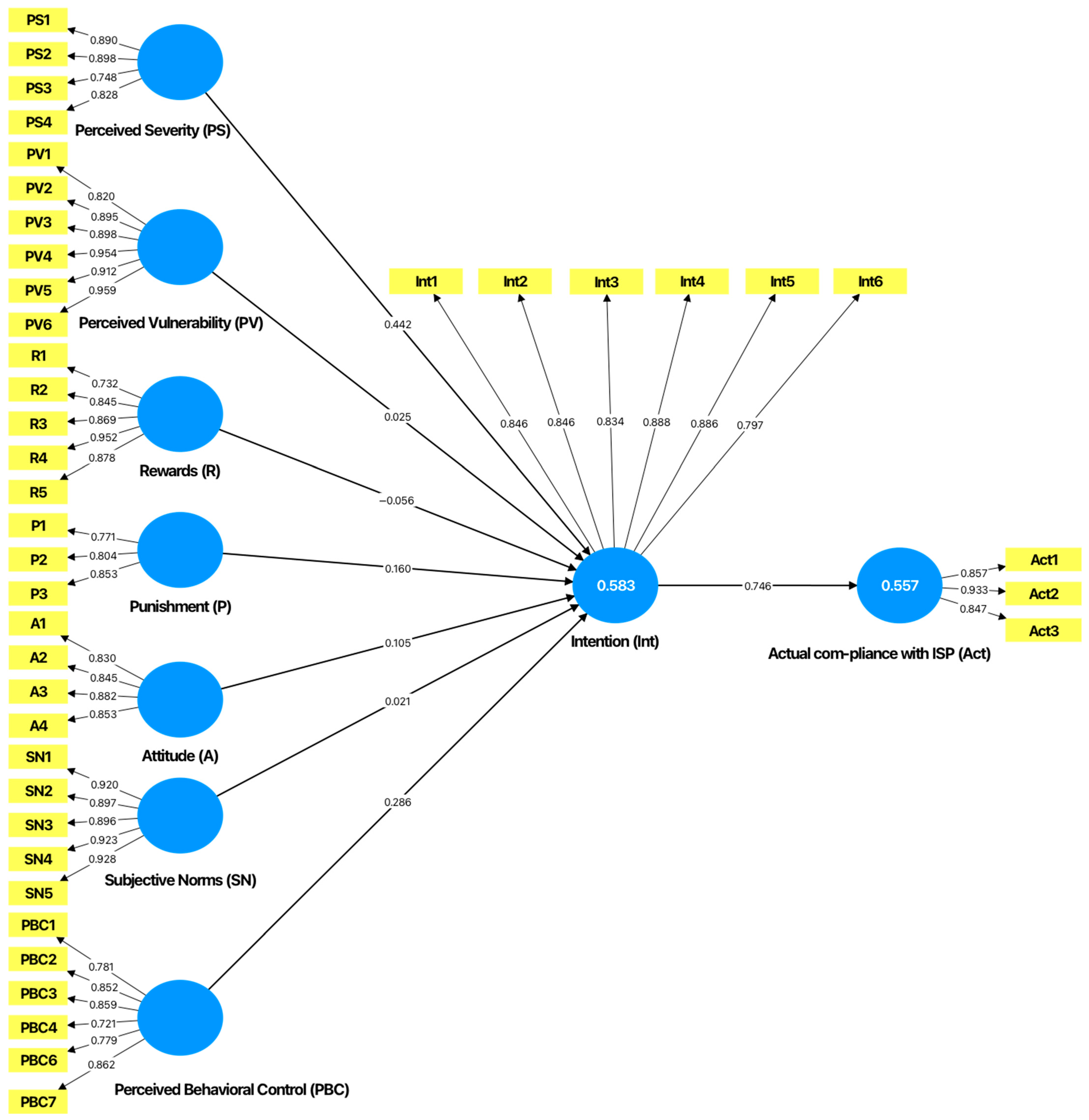
4.4. Structural Model
5. Discussion
6. Implications
6.1. Theoretical Implications
6.2. Practical Implications
7. Limitations and Directions for Future Research
8. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Measurement Items
| Constructs | Items | Reference |
| Perceived Severity (PS) | PS1: I believe that complying with information security policies strengthens the security of information stored on organizational computers. PS2: I believe that complying with information security policies improves protection against potential security incidents. PS3: I believe that adherence to information security policies and measures supports the productivity of the organization and its employees. PS4: I believe that strong compliance with information security practices helps safeguard the profitability of organizations. | [26] |
| Perceived Vulnerability (PV) | PV1: I understand that adhering to my organization’s information security policy helps prevent security breaches. PV2: I believe that by following the information security policy, I can protect myself from security incidents. PV3: I believe that complying with the Information Security Policy (ISP) significantly reduces the risk of unauthorized access to sensitive information. PV4: By following the Information Security Policy (ISP) guidelines, I help protect my organization’s data and systems from potential harm. PV5: I believe that when the Information Security Policy (ISP) is followed, the likelihood of security violations at my organization is minimized. PV6: By complying with the Information Security Policy (ISP), I actively contribute to protecting myself and the organization from security threats. PV7: Adhering to the Information Security Policy (ISP) ensures that I am helping to safeguard my organization from security risks. | [57,66] |
| Rewards (R) | R1: I comply with the requirements of the Information Security Policy (ISP) to receive rewards. R2: My pay raises and/or promotions depend on whether I comply with the ISP. R3: I receive personal mention in oral or written assessment reports if I comply with the ISP. R4: I am given monetary or non-monetary rewards if I comply with the ISP. R5: If I comply with information security policies, I receive appreciation. | [20,34] |
| Punishment (P) | P1: The organization promotes accountability by encouraging employees to comply with information security policies. P2: My organization demonstrates a strong commitment to information security by appropriately addressing repeated policy violations. P3: By complying with the organization’s information security policies, I can help maintain a secure environment and avoid potential consequences. | [26] |
| Attitude (A) | A1: I feel that compliance with the Information Security Policy (ISP) is a positive thing. A2: I feel that compliance with the ISP is reasonable. A3: I feel that compliance with the ISP is important. A4: Following the Information Security Policy is a good idea. A5: Following the Information Security Policy is pleasant. A6: The preventive measures available to me to protect organizational information are adequate. | [20,66] |
| Subjective Norms (SNs) | SN1: Top management believes I should comply with the organization’s information security policies. SN2: My boss believes I should comply with the organization’s information security policies. SN3: My colleagues believe I should comply with the organization’s information security policies. SN4: The information security department in my organization believes I should comply with information security policies. SN5: Other technical computer specialists in the organization believe I should comply with information security policies. | [26] |
| Perceived Behavioral Control (PBC) | PBC1: I have the necessary skills to comply with the organization’s Information Security Policy (ISP). PBC2: I have the expertise to implement preventive measures, in line with the ISP, to protect my confidential information. PBC3: I have the skills to apply preventive measures outlined in the ISP to protect organizational computers from harm. PBC4: I believe it is within my control to comply with the Information Security Policy (ISP). PBC5: I can enable ISP-related security measures on organizational computers, but only when I have manuals or guidance for reference. PBC6: For me, following the security procedures described in the Information Security Policy (ISP) is easy. PBC7: My ability to comply with the Information Security Policy (ISP) and prevent security violations is adequate. | [66] |
| Intention (Int) | Int1: I am likely to comply with my organization’s information security policies. Int2: It is possible that I will follow information security policies to help protect the organization’s information systems. Int3: I am certain that I will act in accordance with the organization’s information security policies. Int4: I intend to comply with the requirements of my organization’s Information Security Policy (ISP) in the future. Int5: I intend to safeguard information and technology resources in alignment with my organization’s ISP. Int6: I intend to carry out my assigned responsibilities as outlined in the ISP when using organizational information and technology. | [26,34] |
| Actual compliance with the Information Security Policy (ISP) (Act) | Act1: I comply with the Information Security Policy (ISP). Act2: I recommend that others comply with the Information Security Policy (ISP). Act3: I assist others in complying with the Information Security Policy (ISP). | [20] |
References
- Ogbanufea, O.; Kim, D.J.; Jones, M.C. Informing Cybersecurity Strategic Commitment through Top Management Perceptions: The Role of Institutional Pressures. Inf. Manag. 2021, 58, 103507. [Google Scholar] [CrossRef]
- Kim, N.; Lee, S. Cybersecurity Breach and Crisis Response: An Analysis of Organizations’ Official Statements in the United States and South Korea. Int. J. Bus. Commun. 2021, 58, 560–581. [Google Scholar] [CrossRef]
- Verizon. Dbir2023 Data Breach Investigations Report. 2023. Available online: https://www.verizon.com/business/en-nl/resources/reports/2023/dbir/2023-data-breach-investigations-report-dbir.pdf (accessed on 24 July 2025).
- Bailey, T.; Kolo, B.; Rajagopalan, K.; Ware, D. Insider Threat: The Human Element of Cyberrisk; McKinsey & Company: New York, NY, USA, 2018; pp. 1–8. [Google Scholar]
- Hong, Y.; Furnell, S. Understanding Cybersecurity Behavioral Habits: Insights from Situational Support. J. Inf. Secur. Appl. 2021, 57, 102710. [Google Scholar] [CrossRef]
- Da Veiga, A. An Approach to Information Security Culture Change Combining Adkar and the Isca Questionnaire to Aid Transition to the Desired Culture. Inf. Comput. Secur. 2018, 26, 584–621. [Google Scholar] [CrossRef]
- ENISA. Raising Awareness of Cybersecurity. 2021. Available online: https://www.enisa.europa.eu/publications/raising-awareness-of-cybersecurity (accessed on 29 November 2021).
- Elifoglu, I.H.; Abel, I.; Tasseven, O. Minimizing Insider Threat Risk with Behavioral Monitoring. Rev. Bus. 2018, 38, 61–73. [Google Scholar]
- CERT. Unintentional Insider Threats: A Foundational Study. Software Engineering Institute. 2013. Available online: https://insights.sei.cmu.edu/library/unintentional-insider-threats-a-foundational-study/ (accessed on 1 August 2013).
- Shandler, R.; Gomez, M.A. The Hidden Threat of Cyber-Attacks—Undermining Public Confidence in Government. J. Inf. Technol. Politics 2023, 20, 359–374. [Google Scholar] [CrossRef]
- Ali, R.F.; Dominic, P.D.D.; Ali, S.E.A.; Rehman, M.; Sohail, A. Information security behavior and information security policy compliance: A systematic literature review for identifying the transformation process from noncompliance to compliance. Appl. Sci. 2021, 11, 3383. [Google Scholar] [CrossRef]
- Donalds, C.; Osei-Bryson, K.M. Cybersecurity compliance behavior: Exploring the influences of individual decision style and other antecedents. Int. J. Inf. Manag. 2020, 51, 102056. [Google Scholar] [CrossRef]
- Cram, W.A.; D’arcy, J.; Proudfoot, J.G. Seeing the forest and the trees. MIS Q. 2019, 43, 525–554. [Google Scholar] [CrossRef]
- Delso-Vicente, A.T.; Diaz-Marcos, L.; Aguado-Tevar, O.; de Blanes-Sebastián, M.G. Factors influencing employee compliance with information security policies: A systematic literature review of behavioral and technological aspects in cybersecurity. Future Bus. J. 2025, 11, 28. [Google Scholar] [CrossRef]
- Boss, S.R.; Galletta, D.F.; Lowry, P.B.; Moody, G.D.; Polak, P. What Do Systems Users Have to Fear? Using Fear Appeals to Engender Threats and Fear That Motivate Protective Security Behaviors. MIS Q. 2015, 39, 837–864. [Google Scholar] [CrossRef]
- Ifinedo, P. Understanding Information Systems Security Policy Compliance: An Integration of the Theory of Planned Behavior and the Protection Motivation Theory. Comput. Secur. 2012, 31, 83–95. [Google Scholar] [CrossRef]
- Rogers, R.W. Cognitive and Physiological Processes in Fear Appeals and Attitude Change: A Revised Theory of Protection Motivation. In Social Psychology; Guilford: New York, NY, USA, 1983; pp. 153–177. [Google Scholar]
- Arachchilage, N.A.G.; Love, S. Security awareness of computer users: A phishing threat avoidance perspective. Comput. Hum. Behav. 2014, 38, 304–312. [Google Scholar] [CrossRef]
- Diana, L.; Dini, P.; Paolini, D. Overview on intrusion detection systems for computers networking security. Computers 2025, 14, 87. [Google Scholar] [CrossRef]
- Siponen, M.; Mahmood, M.A.; Pahnila, S. Employees’ Adherence to Information Security Policies: An Exploratory Field Study. Inf. Manag. 2014, 51, 217–224. [Google Scholar] [CrossRef]
- Puhakainen, P.; Siponen, M. Improving employees’ compliance through information systems security training: An action research study. MIS Q. 2010, 34, 757–778. [Google Scholar] [CrossRef]
- Prümmer, J.; van Steen, T.; van den Berg, B. A systematic review of current cybersecurity training methods. Comput. Secur. 2024, 136, 103585. [Google Scholar] [CrossRef]
- Ajzen, I. The Theory of Planned Behavior. Organ. Behav. Hum. Decis. Process. 1991, 50, 179–211. [Google Scholar] [CrossRef]
- Johnston, A.C.; Warkentin, M. Fear Appeals and Information Security Behaviors: An Empirical Study. MIS Q. 2010, 34, 549–566. [Google Scholar] [CrossRef]
- Skinner, B.F. Science and Human Behavior; Macmillan: New York, NY, USA, 1953. [Google Scholar]
- Herath, T.; Rao, H.R. Protection motivation and deterrence: A framework for security policy compliance in organisations. Eur. J. Inf. Syst. 2009, 18, 106–125. [Google Scholar] [CrossRef]
- Wall, J.D.; Lowry, P.B.; Barlow, J.B. Organizational violations of externally governed privacy and security rules: Explaining and predicting selective violations under conditions of strain and excess. J. Assoc. Inf. Syst. 2016, 17, 4. [Google Scholar] [CrossRef]
- Harris, M.L.; Furnell, S. Routes to Security Compliance: Be Good or Be Shamed? Comput. Fraud Secur. 2012, 12, 12–20. [Google Scholar] [CrossRef]
- Help Net Security. 2020. Available online: https://www.helpnetsecurity.com/2020/08/05/4-in-10-organizations-punish-staff-for-cybersecurity-errors/ (accessed on 5 August 2020).
- Cheng, L.; Li, Y.; Li, W.; Holm, E.; Zhai, Q. Understanding the violation of IS security policy in organizations: An integrated model based on social control and deterrence theory. Comput. Secur. 2013, 39, 447–459. [Google Scholar] [CrossRef]
- Li, H.; Zhang, J.; Sarathy, R. Understanding compliance with internet use policy from the perspective of rational choice theory. Decis. Support Syst. 2010, 48, 635–645. [Google Scholar] [CrossRef]
- Vasileiou, I.; Furnell, S. (Eds.) Cybersecurity Education for Awareness and Compliance; IGI Global: New York, NY, USA, 2019. [Google Scholar]
- Moody, G.; Moody, G.D.; Siponen, M.; Pahnila, S. Toward a Unified Model of Information Security Policy Compliance. MIS Q. 2018, 42, 285–311. [Google Scholar] [CrossRef]
- Bulgurcu, B.; Cavusoglu, H.; Benbasat, I. Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Q. 2010, 34, 523–548. [Google Scholar] [CrossRef]
- Eisenhardt, K.M. Building theories from case study research. Acad. Manag. Rev. 1989, 14, 532–550. [Google Scholar] [CrossRef]
- Posey, C.; Roberts, T.L.; Lowry, P.B.; Hightower, R.T. Bridging the divide: A qualitative comparison of information security thought patterns between information security professionals and ordinary organizational insiders. Inf. Manag. 2014, 51, 551–567. [Google Scholar] [CrossRef]
- Laybats, C.; Tredinnick, L. Information security. Bus. Inf. Rev. 2016, 33, 76–80. [Google Scholar] [CrossRef]
- Hobbs, T.R.; Holt, M.M. The Effects of Token Reinforcement on the Behavior of Delinquents in Cottage Settings. J. Appl. Behav. Anal. 1976, 9, 189–198. [Google Scholar] [CrossRef]
- Sturdy, C.B.; Nicoladis, E. How Much Lang. Acquis. Does Operant Cond. Explain? Front. Psychol. 2017, 8, 1918. [Google Scholar] [CrossRef]
- Miguel, A.Q.C.; Yamauchi, R.; Simões, V.; da Silva, C.J.; Laranjeira, R.R. From Theory to Treatment: Understanding Addiction from an Operant Behavioral Perspective. J. Mod. Educ. Rev. 2015, 5, 778–787. [Google Scholar] [CrossRef]
- Niechoy, A.; Masuch, K.; Trang, S. How Do Employees Learn Security Behavior? An Integrated Perspective on Social Learning and Rational Decision Making. In Digital Transformation and Human Behavior: Innovation for People and Organisations; Springer International Publishing: Cham, Switzerland, 2020; pp. 149–164. [Google Scholar]
- Workman, M.; Bommer, W.H.; Straub, D. Security lapses and the omission of information security measures: A threat control model and empirical test. Comput. Hum. Behav. 2008, 24, 2799–2816. [Google Scholar] [CrossRef]
- Warkentin, M.; Malimage, N.; Malimage, K. Impact of protection motivation and deterrence on is security policy compliance: A multi-cultural view. In Proceedings of the Seventh Pre-ICIS Workshop on Information Security and Privacy, Orlando, FL, USA, 15 December 2012. [Google Scholar]
- Zhu, N.; Liu, Y.; Zhang, J.; Wang, N. Contingent reward versus punishment and compliance behavior: The mediating role of affective attitude and the moderating role of operational capabilities of artificial intelligence. Humanit. Soc. Sci. Commun. 2023, 10, 590. [Google Scholar] [CrossRef]
- Baron, A.; Galizio, M. Positive and negative reinforcement: Should the distinction be preserved? Behav. Anal. 2005, 28, 85–98. [Google Scholar] [CrossRef]
- Ryan, R.M.; Deci, E.L. Intrinsic and Extrinsic Motivation from a Self-Determination Theory Perspective: Definitions, Theory, Practices, and Future Directions. Contemp. Educ. Psychol. 2020, 61, 101860. [Google Scholar] [CrossRef]
- Ifinedo, P. Critical Times for Organizations: What Should Be Done to Curb Workers’ Noncompliance with Information Systems Security Policies? Comput. Secur. 2016, 63, 98–109. [Google Scholar]
- Rogers, P.R.; Miller, A.; Judge, W.Q. Using Information-Processing Theory to Understand Planning/Performance Relationships in the Context of Strategy. Strateg. Manag. J. 1999, 20, 567–577. [Google Scholar] [CrossRef]
- Gattiker, T.F.; Goodhue, D.L. Understanding the Local-Level Costs and Benefits of Erp through Organizational Information Processing Theory. Inf. Manag. 2004, 41, 431–443. [Google Scholar] [CrossRef]
- Bedi, A.; Alpaslan, C.M.; Green, S. A Meta-Analytic Review of Ethical Leadership Outcomes and Moderators. J. Bus. Ethics 2016, 139, 517–536. [Google Scholar] [CrossRef]
- Domino, M.A.; Wingreen, S.C.; Blanton, J.E. Social Cognitive Theory: The Antecedents and Effects of Ethical Climate Fit on Organizational Attitudes of Corporate Accounting Professionals—A Reflection of Client Narcissism and Fraud Attitude Risk. J. Bus. Ethics 2015, 131, 453–467. [Google Scholar] [CrossRef]
- Alrawhani, E.M.; Romli, A.; Al-Sharafi, M.A. Evaluating the role of protection motivation theory in information security policy compliance: Insights from the banking sector using PLS-SEM approach. J. Open Innov. Technol. Mark. Complex. 2025, 11, 100463. [Google Scholar] [CrossRef]
- Menard, P.; Bott, G.J.; Crossler, R.E. User motivations in protecting information security: Protection motivation theory versus self-determination theory. J. Manag. Inf. Syst. 2017, 34, 1203–1230. [Google Scholar] [CrossRef]
- Mou, J.; Cohen, J.F.; Bhattacherjee, A.; Kim, J. A test of protection motivation theory in the information security literature: A meta-analytic structural equation modeling approach. J. Assoc. Inf. Syst. 2022, 23, 196–236. [Google Scholar] [CrossRef]
- Sharma, S.; Aparicio, E. Organizational and team culture as antecedents of protection motivation among IT employees. Comput. Secur. 2022, 120, 102774. [Google Scholar] [CrossRef]
- Li, L.; He, W.; Xu, L.; Ash, I.; Anwar, M.; Yuan, X. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. Int. J. Inf. Manag. 2019, 45, 13–24. [Google Scholar] [CrossRef]
- Vance, A.; Siponen, M.; Pahnila, S. Motivating IS security compliance: Insights from habit and protection motivation theory. Inf. Manag. 2012, 49, 190–198. [Google Scholar] [CrossRef]
- Posey, C.; Roberts, T.L.; Lowry, P.B. The Impact of Organizational Commitment on Insiders’ Motivation to Protect Organizational Information Assets. J. Manag. Inf. Syst. 2015, 32, 179–214. [Google Scholar] [CrossRef]
- Mamonov, S.; Benbunan-Fich, R. The impact of information security threat awareness on privacy-protective behaviors. Comput. Hum. Behav. 2018, 83, 32–44. [Google Scholar] [CrossRef]
- Ogbanufe, O.; Crossler, R.E.; Biros, D. The valued coexistence of protection motivation and stewardship in information security behaviors. Comput. Secur. 2023, 124, 102960. [Google Scholar] [CrossRef]
- Wong, L.W.; Lee, V.H.; Tan, G.W.H.; Ooi, K.B.; Sohal, A. The role of cybersecurity and policy awareness in shifting employee compliance attitudes: Building supply chain capabilities. Int. J. Inf. Manag. 2022, 66, 102520. [Google Scholar] [CrossRef]
- Li, Y.J.; Hoffman, E. Designing an incentive mechanism for information security policy compliance: An experiment. J. Econ. Behav. Organ. 2023, 212, 138–159. [Google Scholar] [CrossRef]
- Arbin, K.; Frostenson, M.; Helin, S.; Borglund, T. Explaining workers’ resistance against a health and safety programme: An understanding based on hierarchical and social accountability. Saf. Sci. 2021, 136, 105131. [Google Scholar] [CrossRef]
- Prabhu, S.; Kocsis, D.; Lew, T.Y. Beyond the direct impact of sanctions and subjective norms in cybersecurity. Inf. Comput. Secur. 2025. [Google Scholar] [CrossRef]
- Lee, D.; Lallie, H.S.; Michaelides, N. The impact of an employee’s psychological contract breach on compliance with information security policies: Intrinsic and extrinsic motivation. Cognition. Technol. Work. 2023, 25, 273–289. [Google Scholar] [CrossRef]
- Rajab, M.; Eydgahi, A. Evaluating the explanatory power of theoretical frameworks on intention to comply with information security policies in higher education. Comput. Secur. 2019, 80, 211–223. [Google Scholar] [CrossRef]
- Kline, R.B. Principles Practice of Structural Equation Modeling, 4th ed.; Guilford Press: New York, NY, USA, 2015. [Google Scholar]
- Hair, J.; Anderson, R.; Tatham, R.; Black, W. Multivariate Data Analysis, 7th ed.; Prentice Hall: Hoboken, NY, USA, 2010. [Google Scholar]
- Awang, Z. Structural Equation Modeling Using AMOS Graphic; Penerbit Universiti Teknologi MARA: Shah Alam Selangor, Malaysia, 2012. [Google Scholar]
- Hair, J.J.F.; Hult, G.T.; Ringle, C.M. Partial Least Squares; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Alshebami, A.S. Fuelling entrepreneurial success: Unravelling the nexus of financial resources, self-efficacy, outcome expectations and entrepreneurial intentions in Saudi micro and small enterprises. Discov Sustain. 2024, 5, 62. [Google Scholar] [CrossRef]
- Al-Mamary, Y.H. A comprehensive model for AI adoption: Analysing key characteristics affecting user attitudes, intentions and use of ChatGPT in education. Hum. Syst. Manag. 2024, 01672533251340523. [Google Scholar] [CrossRef]
- Sulaiman, N.S.; Fauzi, M.A.; Hussain, S.; Wider, W. Cybersecurity behavior among government employees: The role of protection motivation theory and responsibility in mitigating cyberattacks. Information 2022, 13, 413. [Google Scholar] [CrossRef]
- Crossler, R.E.; Andoh-Baidoo, F.K.; Menard, P. Espoused cultural values as antecedents of individuals’ threat and coping appraisal toward protective information technologies: Study of US and Ghana. Inf. Manag. 2019, 56, 754–766. [Google Scholar] [CrossRef]
- Addae, J.A.; Simpson, G.; Ampong, G.O.A. Factors influencing information security policy compliance behavior. In 2019 International Conference on Cyber Security and Internet of Things (ICSIoT); IEEE: New York, NY, USA, 2019; pp. 43–47. [Google Scholar]
- Yoon, C.; Hwang, J.W.; Kim, R. Exploring factors that influence students’ behaviors in information security. J. Inf. Syst. Educ. 2012, 23, 407–416. [Google Scholar]
- Sommestad, T.; Karlzén, H.; Hallberg, J. The theory of planned behavior and information security policy compliance. J. Comput. Inf. Syst. 2019, 59, 344–353. [Google Scholar] [CrossRef]
- Khatib, R.; Barki, H. How different rewards tend to influence employee non-compliance with information security policies. Inf. Comput. Secur. 2022, 30, 97–116. [Google Scholar] [CrossRef]
- Kuo, K.M.; Talley, P.C.; Lin, D.Y.M. Hospital staff’s adherence to information security policy: A quest for the antecedents of deterrence variables. J. Health Care Organ. Provis. Financ. 2021, 58, 00469580211029599. [Google Scholar] [CrossRef]
- Aigbefo, Q.A.; Blount, Y.; Marrone, M. The influence of hardiness and habit on security behaviour intention. Behav. Inf. Technol. 2022, 41, 1151–1170. [Google Scholar] [CrossRef]
- Pahnila, S.; Siponen, M.; Mahmood, A. Employees’ behavior towards IS security policy compliance. In Proceedings of the 2007 40th Annual Hawaii International Conference on System Sciences (HICSS’07), Waikoloa, HI, USA, 3–6 January 2007; p. 156. [Google Scholar]
- Dong, K.; Ali, R.F.; Dominic, P.D.D.; Ali, S.E.A. The effect of organizational information security climate on information security policy compliance: The mediating effect of social bonding towards healthcare nurses. Sustainability 2021, 13, 2800. [Google Scholar] [CrossRef]
- Smit, T.; van Haastrecht, M.; Spruit, M. The effect of countermeasure readability on security intentions. J. Cybersecur. Priv. 2021, 1, 675–703. [Google Scholar] [CrossRef]
- Farooq, A.; Ndiege, J.R.A.; Isoaho, J. Factors affecting security behavior of kenyan students: An integration of protection motivation theory and theory of planned behavior. In Proceedings of the 2019 IEEE AFRICON, Accra, Ghana, 25–27 September 2019; pp. 1–8. [Google Scholar]
- Hofstede, G. Culture and organizations. Int. Stud. Manag. Organ. 1980, 10, 15–41. [Google Scholar] [CrossRef]
- Aljlayel, N.A.M. Business Process Management Adoption and Culture: A Case of Saudi Arabia. Ph.D. Thesis, RMIT University, Victoria, Australia, 2020. [Google Scholar]
- D’Arcy, J.; Hovav, A.; Galletta, D. User awareness of security countermeasures and its impact on information systems misuse: A deterrence approach. Inf. Syst. Res. 2009, 20, 79–98. [Google Scholar] [CrossRef]

| Items | Scale | Frequency | Percent |
|---|---|---|---|
| Gender | Male | 160 | 53.0 |
| Female | 142 | 47.0 | |
| Education | High School | 26 | 8.6 |
| Diploma | 79 | 26.2 | |
| Bachelor | 114 | 37.7 | |
| Postgraduate | 83 | 27.5 | |
| Age | Less than 30 | 61 | 20.2 |
| 31–40 | 85 | 28.1 | |
| 41–50 | 92 | 30.5 | |
| More than 50 | 64 | 21.2 | |
| Job Experience | Less than 5 Years | 63 | 20.9 |
| 5–10 Years | 133 | 44.0 | |
| Above 10 Years | 106 | 35.1 | |
| Employment Sector | Private | 145 | 48.0 |
| Public | 157 | 52.0 | |
| Total | 302 | 100 |
| Construct | Item | Loading | Cronbach Alpha (≥0.7) | Composite Reliability (≥0.7) | Average Variance Extracted (≥0.5) | Inner VIF |
|---|---|---|---|---|---|---|
| Perceived Severity (PS) | 0.863 | 0.883 | 0.711 | 1.450 | ||
| PS1 | 0.890 | |||||
| PS2 | 0.898 | |||||
| PS3 | 0.748 | |||||
| PS4 | 0.828 | |||||
| Perceived Vulnerability (PV) | 0.959 | 0.965 | 0.824 | 1.159 | ||
| PV1 | 0.820 | |||||
| PV2 | 0.895 | |||||
| PV3 | 0.898 | |||||
| PV4 | 0.954 | |||||
| PV5 | 0.912 | |||||
| PV6 | 0.959 | |||||
| PV7 | Deleted | |||||
| Rewards (R) | 0.918 | 0.933 | 0.736 | 1.070 | ||
| R1 | 0.732 | |||||
| R2 | 0.845 | |||||
| R3 | 0.869 | |||||
| R4 | 0.952 | |||||
| R5 | 0.878 | |||||
| Punishment (P) | 0.751 | 0.810 | 0.656 | 1.694 | ||
| P1 | 0.771 | |||||
| P2 | 0.804 | |||||
| P3 | 0.853 | |||||
| Attitude (A) | 0.874 | 0.876 | 0.727 | 1.047 | ||
| A1 | 0.830 | |||||
| A2 | 0.845 | |||||
| A3 | 0.882 | |||||
| A4 | 0.853 | |||||
| A5 | Deleted | |||||
| A6 | Deleted | |||||
| Subjective Norms (SNs) | 0.950 | 0.964 | 0.833 | 1.172 | ||
| SN1 | 0.920 | |||||
| SN2 | 0.897 | |||||
| SN3 | 0.896 | |||||
| SN4 | 0.923 | |||||
| SN5 | 0.928 | |||||
| Perceived Behavioral Control (PBC) | 0.895 | 0.904 | 0.657 | 1.590 | ||
| PBC1 | 0.781 | |||||
| PBC2 | 0.852 | |||||
| PBC3 | 0.859 | |||||
| PBC4 | 0.721 | |||||
| PBC5 | Deleted | |||||
| PBC6 | 0.779 | |||||
| PBC7 | 0.862 | |||||
| Intention (Int) | 0.923 | 0.925 | 0.723 | 1.000 | ||
| Int1 | 0.846 | |||||
| Int2 | 0.846 | |||||
| Int3 | 0.834 | |||||
| Int4 | 0.888 | |||||
| Int5 | 0.886 | |||||
| Int6 | 0.797 | |||||
| Actual compliance with the Information Security Policy (ISP) (Act) | 0.855 | 0.869 | 0.774 | |||
| Act1 | 0.857 | |||||
| Act2 | 0.933 | |||||
| Act3 | 0.847 |
| PS | PV | R | P | A | SN | PBC | Int | Act | |
|---|---|---|---|---|---|---|---|---|---|
| PS | 0.843 | ||||||||
| PV | 0.019 | 0.908 | |||||||
| R | 0.051 | 0.170 | 0.858 | ||||||
| P | 0.480 | 0.022 | 0.123 | 0.810 | |||||
| A | 0.203 | 0.013 | 0.033 | 0.087 | 0.853 | ||||
| SN | 0.151 | 0.314 | 0.011 | 190 | 0.060 | 0.913 | |||
| PBC | 0.434 | 0.089 | 0.045 | 0.571 | 0.094 | 0.212 | 0.811 | ||
| Int | 0.670 | 0.064 | 0.047 | 0.542 | 0.235 | 0.194 | 0.583 | 0.850 | |
| Act | 0.663 | 0.052 | 0.012 | 0.600 | 0.197 | 0.280 | 0.608 | 0.746 | 0.880 |
| PS | PV | R | P | A | SN | PBC | Int | Act | |
|---|---|---|---|---|---|---|---|---|---|
| PS | - | ||||||||
| PV | 0.036 | - | |||||||
| R | 0.076 | 0.187 | - | ||||||
| P | 0.588 | 0.049 | 0.161 | - | |||||
| A | 0.220 | 0.060 | 0.067 | 0.092 | - | ||||
| SN | 0.160 | 0.341 | 0.042 | 0.208 | 0.071 | - | |||
| PBC | 0.484 | 0.085 | 0.075 | 0.661 | 0.101 | 0.227 | - | ||
| Int | 0.739 | 0.062 | 0.057 | 0.614 | 0.260 | 0.203 | 0.633 | - | |
| Act | 0.760 | 0.047 | 0.063 | 0.720 | 0.225 | 0.309 | 0.690 | 0.827 | - |
| Metric | Saturated Model | Modified Estimated Model |
|---|---|---|
| SRMR | 0.068 | 0.073 |
| d_ULS | 4.974 | 5.695 |
| d_G | 2.451 | 2.515 |
| Chi-square | 4090.296 | 4160.204 |
| NFI | 0.817 | 0.812 |
| Relationship | Path Coefficient | Sample Mean (M) | Standard Deviation (STDEV) | T Statistics (|O/STDEV|) | p Values | Decision |
|---|---|---|---|---|---|---|
| Perceived Severity -> Intention to Comply with ISPs | 0.442 | 0.443 | 0.050 | 8.931 | 0.000 | Supported |
| Perceived Vulnerability -> Intention to Comply with ISPs | 0.025 | 0.027 | 0.049 | 0.510 | 0.610 | Not Supported |
| Rewards -> Intention to Comply with ISPs | −0.056 | −0.050 | 0.054 | 1.046 | 0.296 | Not Supported |
| Punishment -> Intention to Comply with ISPs | 0.160 | 0.159 | 0.052 | 3.094 | 0.002 | Supported |
| Attitude -> Intention to Comply with ISPs | 0.105 | 0.106 | 0.039 | 2.660 | 0.008 | Supported |
| Subjective Norms -> Intention to Comply with ISPs | 0.021 | 0.024 | 0.040 | 0.532 | 0.595 | Not Supported |
| Perceived Behavioral Control -> Intention to Comply with ISPs | 0.286 | 0.283 | 0.062 | 4.613 | 0.000 | Supported |
| Intention to Comply with ISP -> Actual Compliance Behavior with ISPs | 0.746 | 0.746 | 0.036 | 20.975 | 0.000 | Supported |
| R-Square | R-Square Adjusted | |
|---|---|---|
| Intention to Comply with ISPs | 0.583 | 0.574 |
| Actual Compliance Behavior with ISPs | 0.557 | 0.555 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alshammari, M.M.; Al-Mamary, Y.H. Bridging Policy and Practice: Integrated Model for Investigating Behavioral Influences on Information Security Policy Compliance. Systems 2025, 13, 630. https://doi.org/10.3390/systems13080630
Alshammari MM, Al-Mamary YH. Bridging Policy and Practice: Integrated Model for Investigating Behavioral Influences on Information Security Policy Compliance. Systems. 2025; 13(8):630. https://doi.org/10.3390/systems13080630
Chicago/Turabian StyleAlshammari, Mohammad Mulayh, and Yaser Hasan Al-Mamary. 2025. "Bridging Policy and Practice: Integrated Model for Investigating Behavioral Influences on Information Security Policy Compliance" Systems 13, no. 8: 630. https://doi.org/10.3390/systems13080630
APA StyleAlshammari, M. M., & Al-Mamary, Y. H. (2025). Bridging Policy and Practice: Integrated Model for Investigating Behavioral Influences on Information Security Policy Compliance. Systems, 13(8), 630. https://doi.org/10.3390/systems13080630







