SecFedDNN: A Secure Federated Deep Learning Framework for Edge–Cloud Environments
Abstract
1. Introduction
- We propose a multi-layered framework, SecFedDNN, designed to detect and classify cyberattacks (DDoS, DoS, Injection) using federated deep learning (FDL) mechanisms within edge–cloud environments. SecFedDNN enables edge nodes to train models while preserving privacy through decentralized learning collaboratively. Moreover, SecFedDNN performs edge-level pre-aggregation filtering through Layer-Adaptive Sparsified Model Aggregation (LASA) for anomaly detection while supporting balanced multi-class evaluation across federated clients.
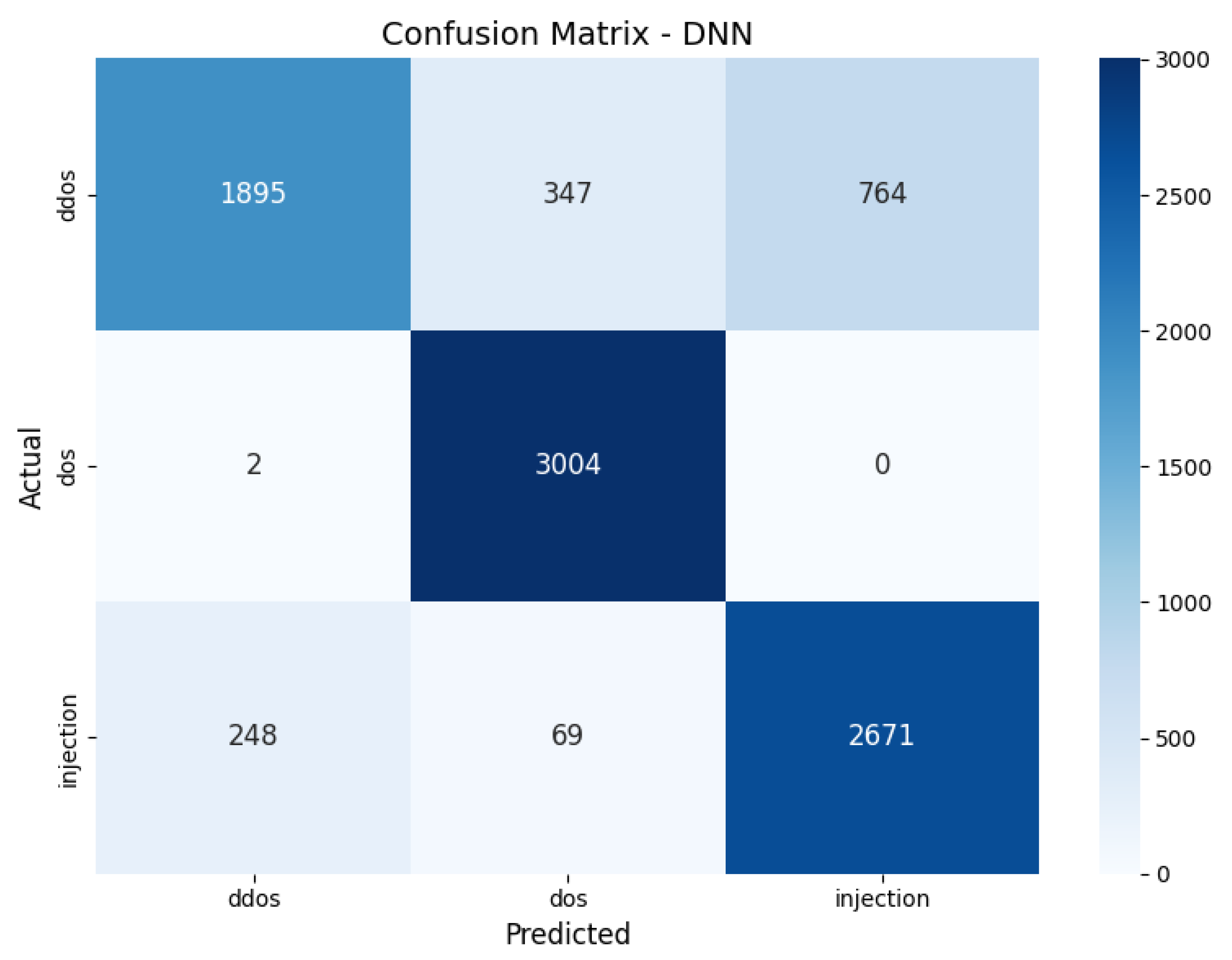
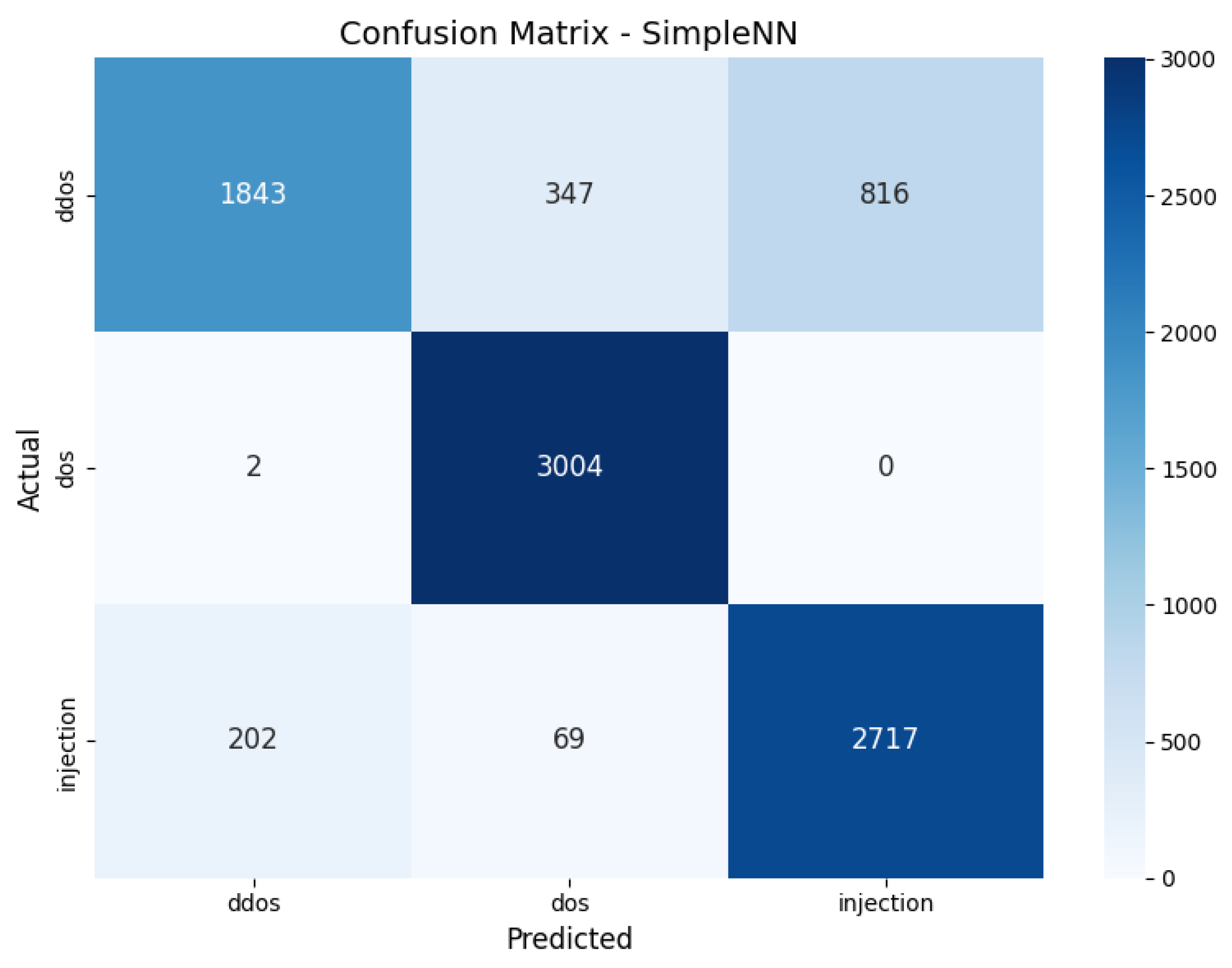
- We further implemented FL-DNN and analyzed its performance using per-client metrics, confusion matrices, and performance curves. The results reveal strong detection performance, especially for DoS and injection attacks.
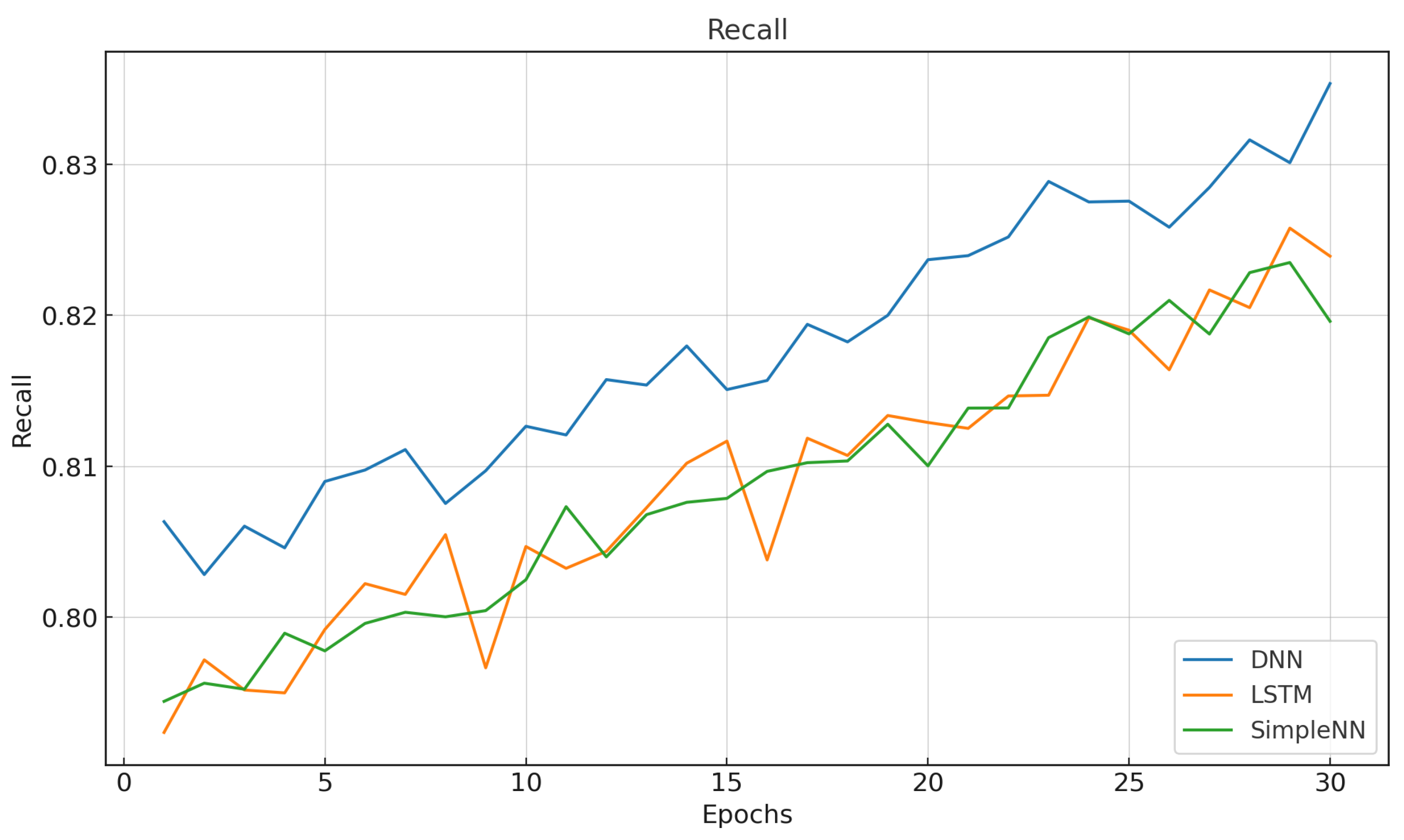
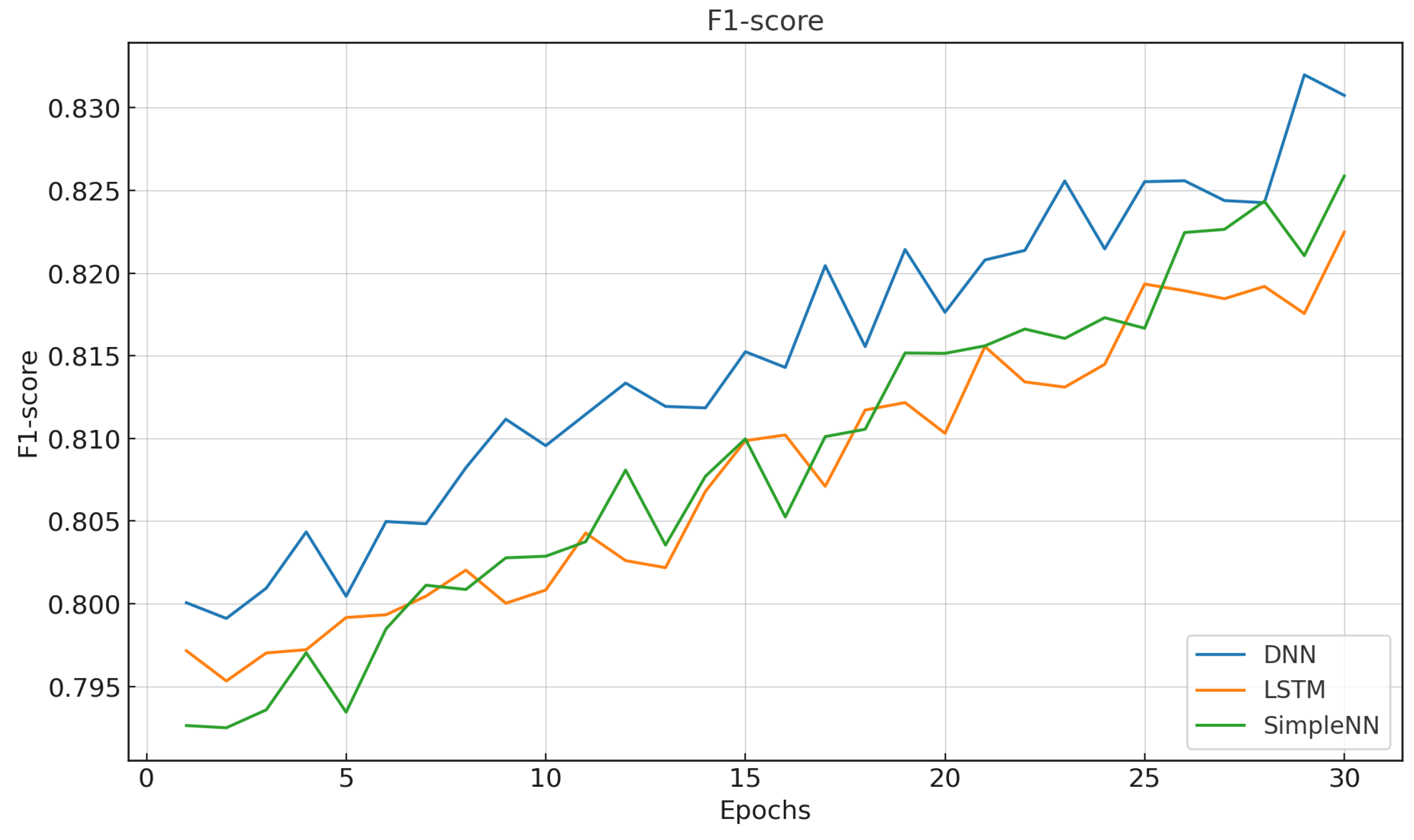
- To validate the proposed framework, we performed a comprehensive comparison between DNN, LSTM, and SimpleNN under centralized settings. Based on performance metrics such as accuracy, precision, recall, and F1-score, the DNN model was selected as the most robust for FL adaptation.
2. Related Work
2.1. Federated Learning for Intrusion Detection
2.2. Deep Learning in Edge Environments
2.3. Hybrid and Privacy-Preserving Federated Learning Approaches
2.4. Reinforcement Learning and Resource Optimization in Federated Learning
2.5. Secure Aggregation and Poisoning Defense Mechanisms
2.6. Adversarial Threats and Adaptive Federated Learning in DDoS Detection
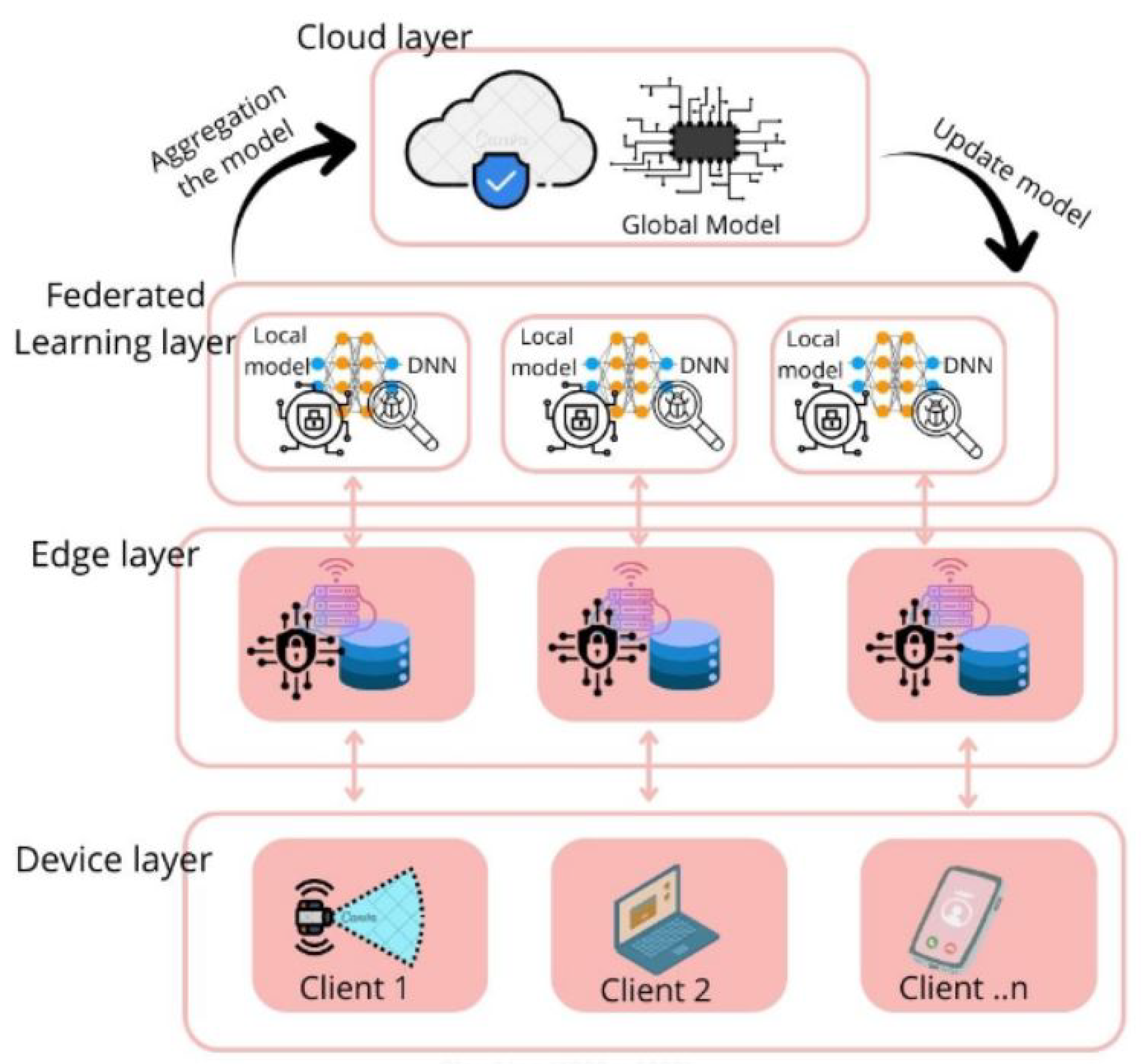
3. SecFedDNN Framework Architecture
3.1. Device Layer
3.2. Edge Layer
3.3. Federated Learning Layer
3.4. Cloud Layer
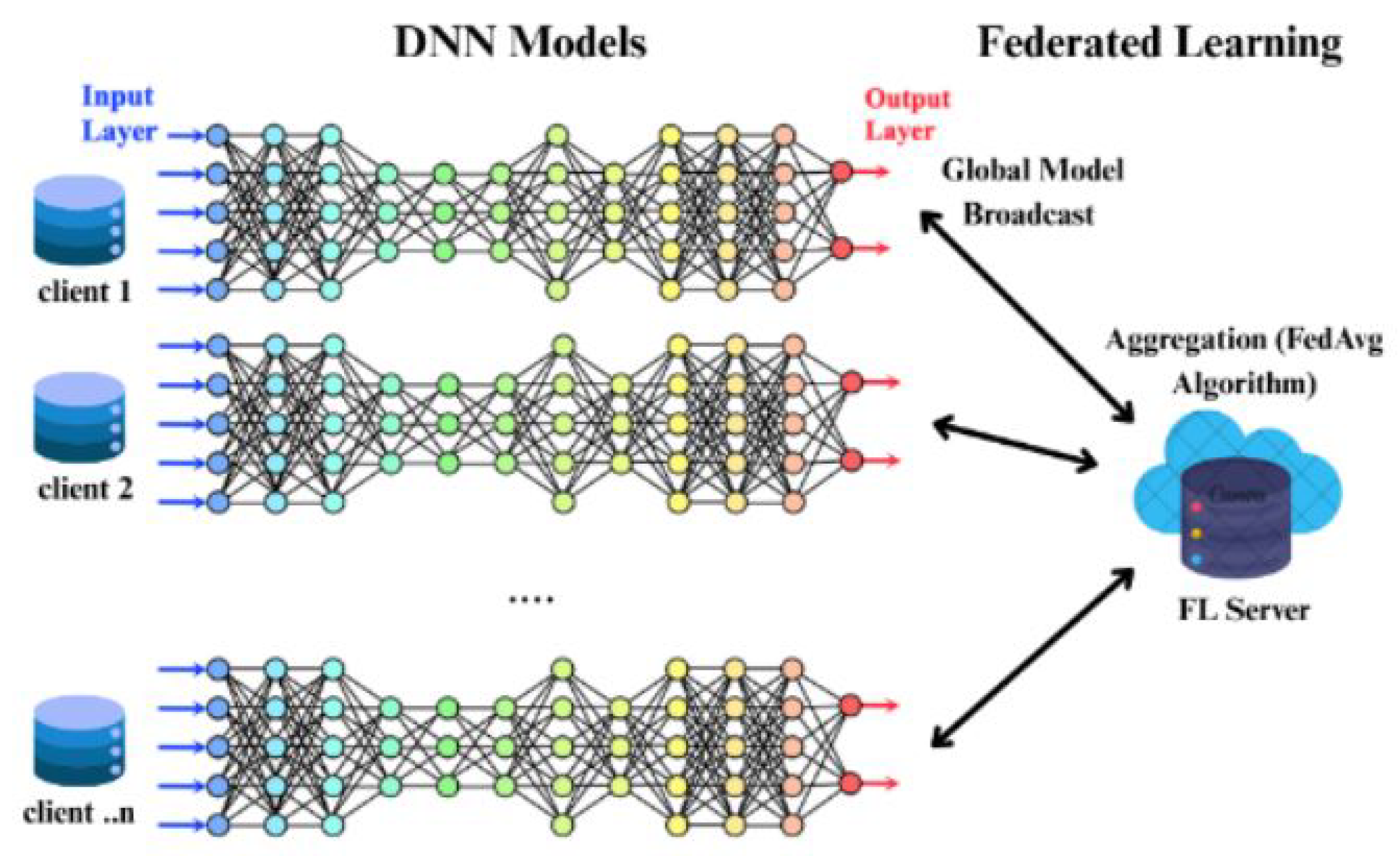
4. FL-DNN Model
5. Implementation
5.1. Environment and Tools
5.2. Dataset
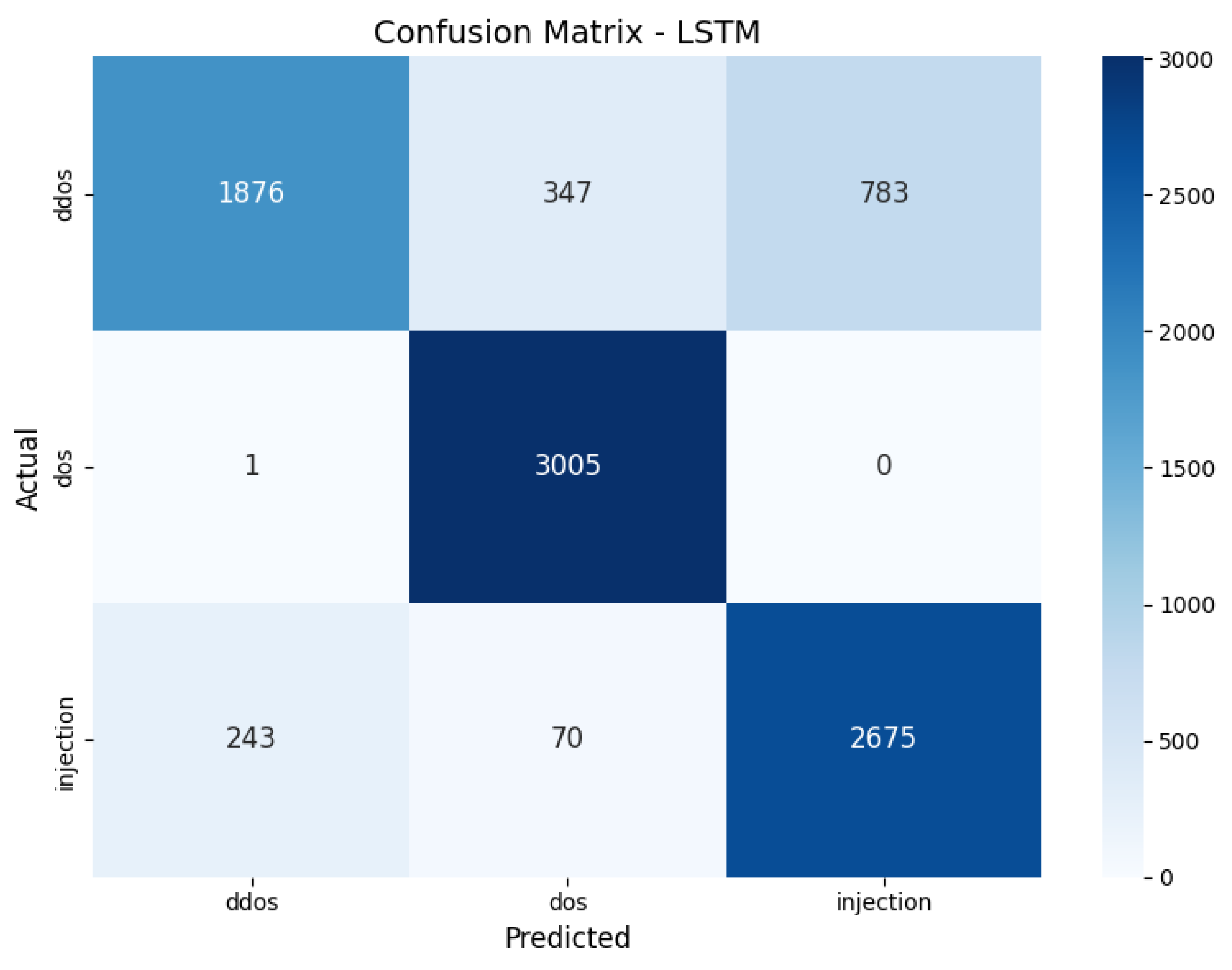
- Distributed Denial of Service (DDoS) Attacks: They use numerous hijacked devices that direct massive traffic volumes at a target system all at once. The TON_IoT-extracted DDoS records show distributed packet flooding patterns, which include fast connection attempts along with high source IP entropy and packet bursts. The model faces significant challenges when detecting distributed attacks across fragmented edge data due to these characteristics, which makes this attack category critical for evaluating FL resilience in collaborative settings.
- Denial of Service (DoS) Attacks: They originate from a single source and work by bombarding a service with multiple requests to create system overload. The TON_IoT dataset reveals DoS attack characteristics through repeated protocol requests, excessive request frequency, and service timeout anomalies. The experimental subset contains DoS samples to enable the model to detect localized high-frequency attacks, which frequently occur in resource-limited edge systems.
- Injection Attacks: Attackers use input fields at the application layer to execute harmful scripts or database queries through injection attacks. The dataset TON_IoT features different injection attack types such as command injection and SQL injection. The samples demonstrate unorthodox string formations and abnormal parameter values along with command-line sequence patterns. Federated systems need precise anomaly detection because identifying subtle irregularities locally can stop malicious data from corrupting global model updates.
6. Experimentation and Result
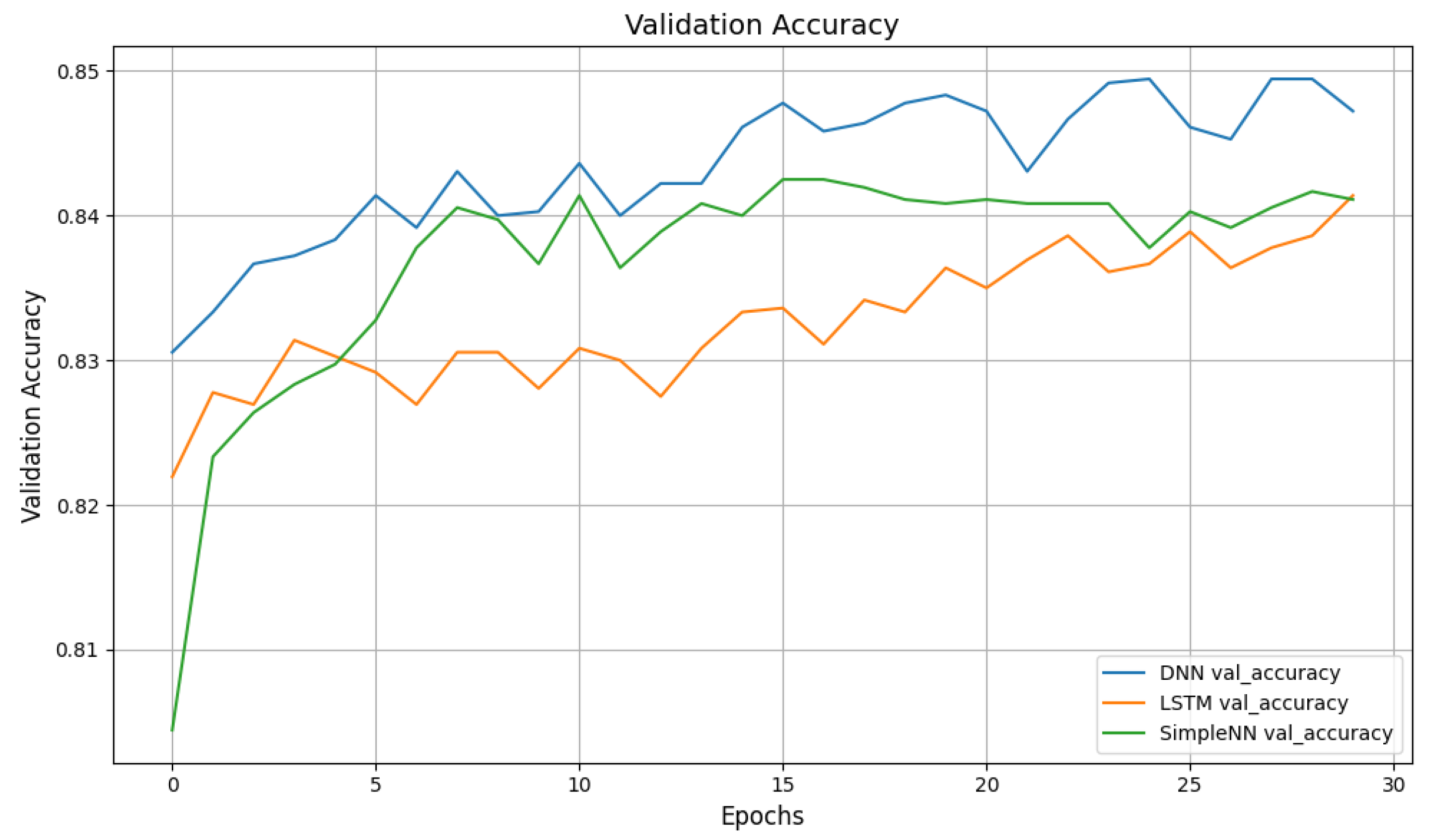
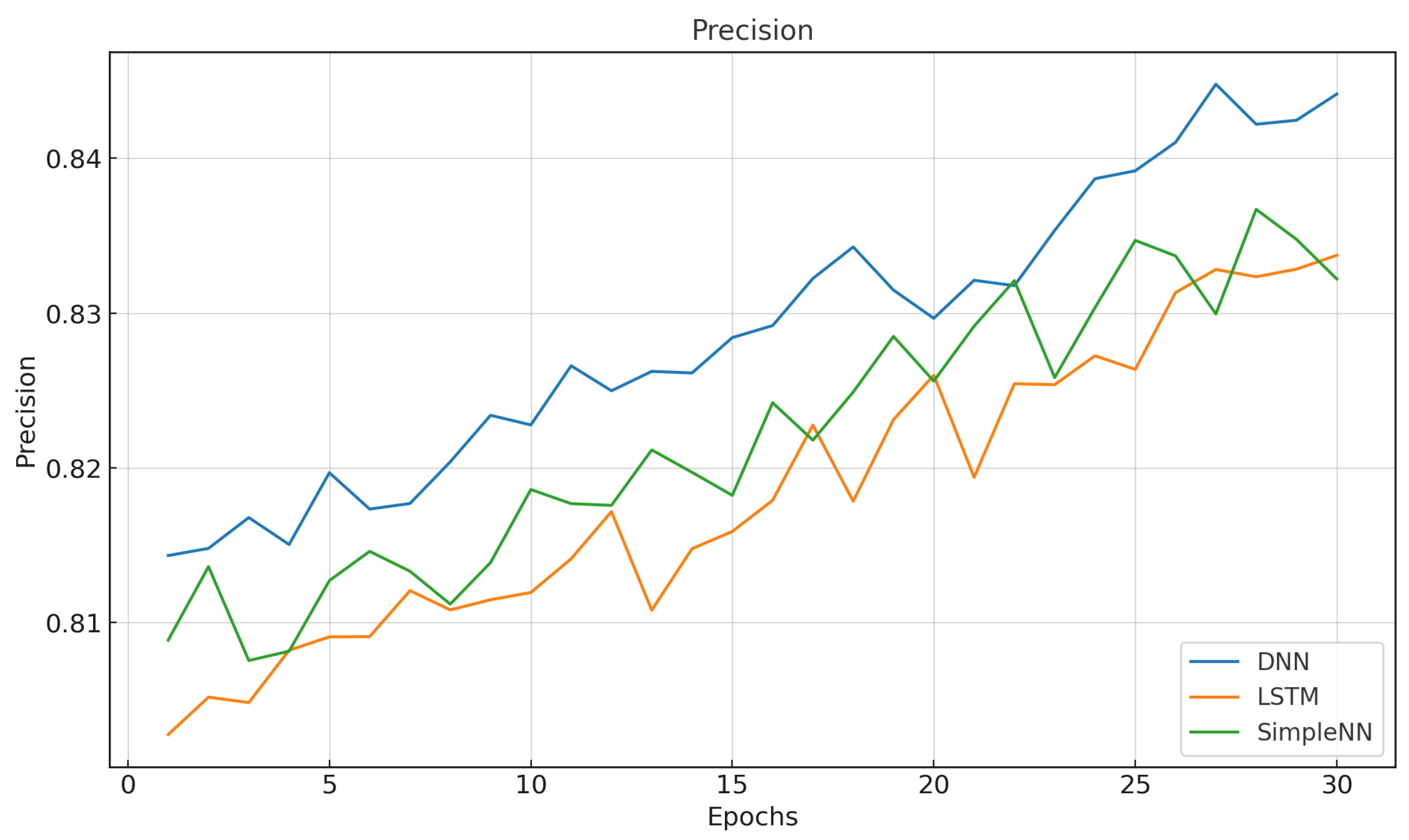
6.1. Baseline Evaluation of Centralized Models
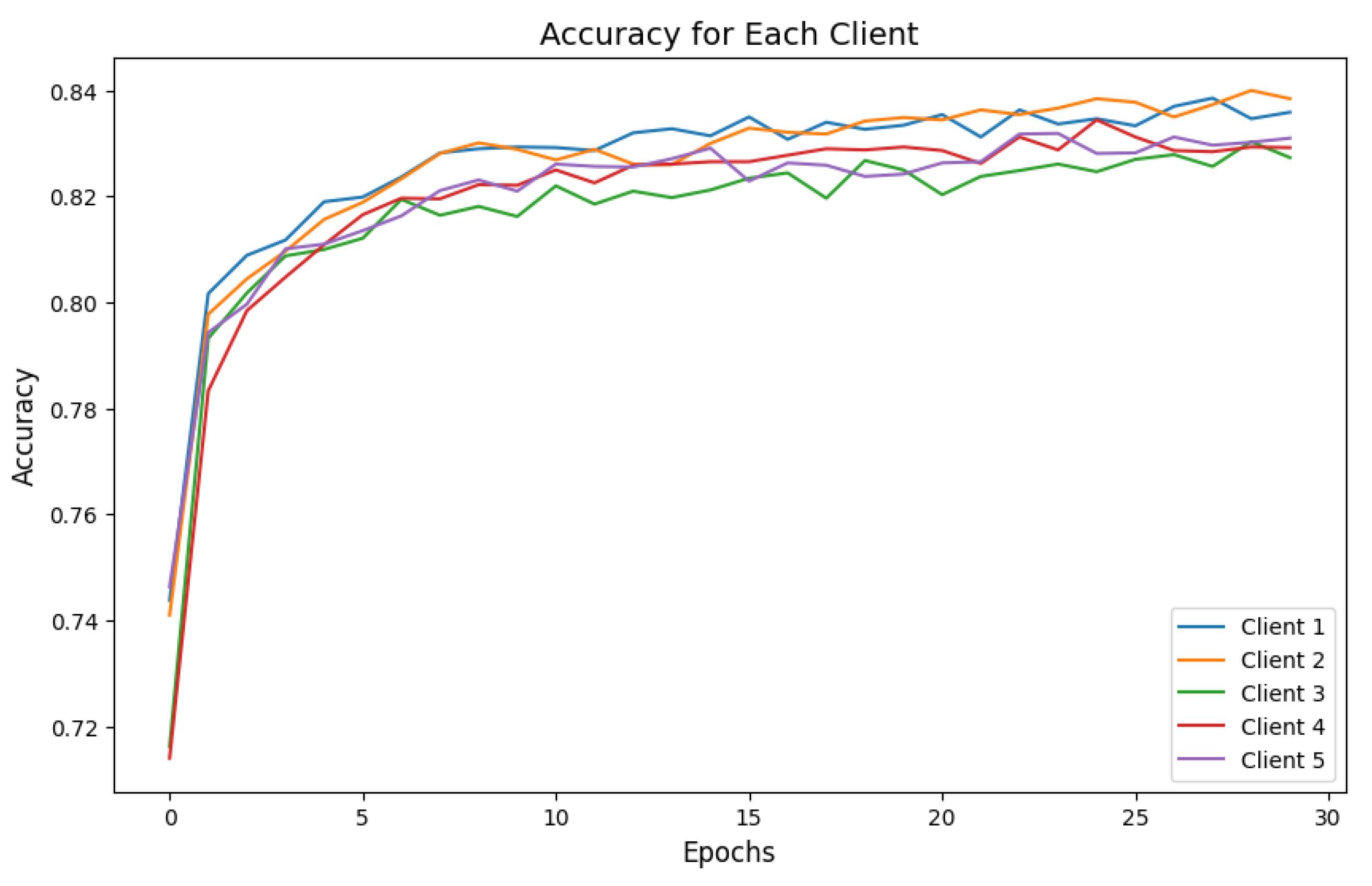
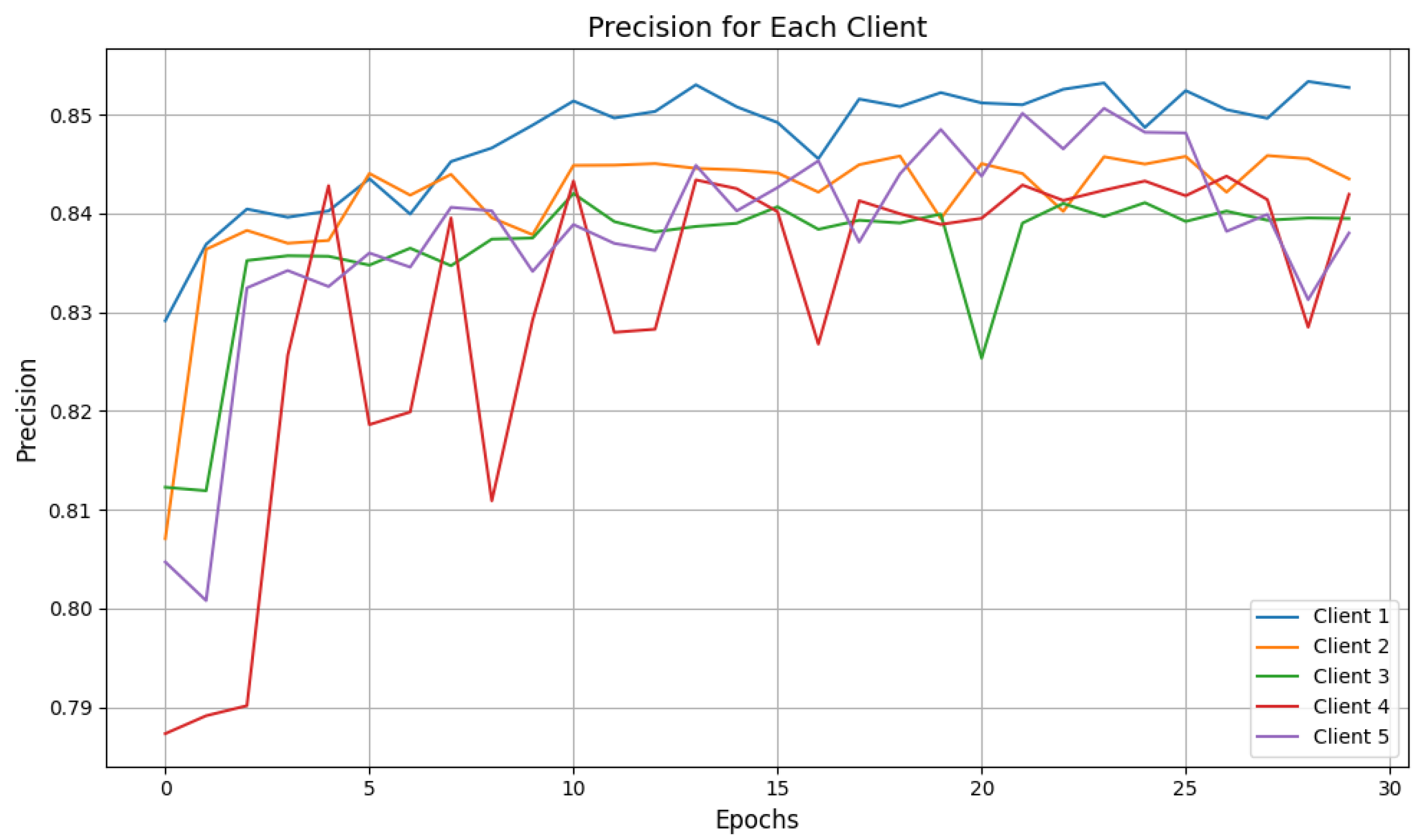
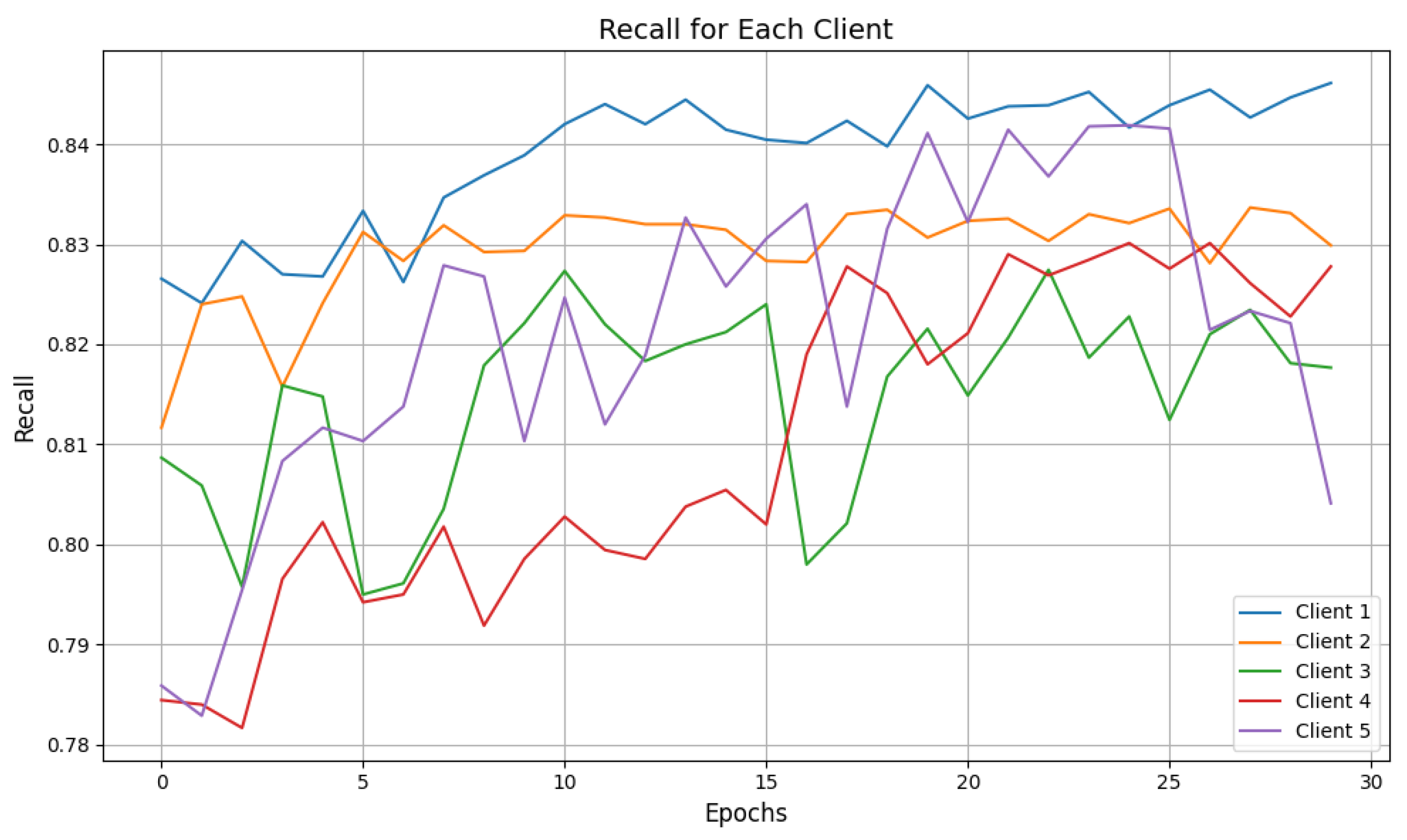
6.2. Experimental Results and Evaluation
7. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ficili, I.; Giacobbe, M.; Tricomi, G.; Puliafito, A. From sensors to data intelligence: Leveraging IoT, cloud, and edge computing with AI. Sensors 2025, 25, 1763. [Google Scholar] [CrossRef] [PubMed]
- Noor, A.; Noor, T.H. Federated intelligence for intrusion detection and unifying health prediction in IoHT. In Proceedings of the 4th International Conference on Distributed Sensing and Intelligent Systems (ICDSIS 2023), Dubai, UAE, 21–23 December 2023; Volume 2023, pp. 556–566. [Google Scholar]
- Trigka, M.; Dritsas, E. Edge and Cloud Computing in Smart Cities. Future Internet 2025, 17, 118. [Google Scholar] [CrossRef]
- Mothukuri, V.; Parizi, R.M.; Pouriyeh, S.; Huang, Y.; Dehghantanha, A.; Srivastava, G. A survey on security and privacy of federated learning. Future Gener. Comput. Syst. 2021, 115, 619–640. [Google Scholar] [CrossRef]
- Sharma, A.; Marchang, N. A review on client-server attacks and defenses in federated learning. Comput. Secur. 2024, 140, 103801. [Google Scholar] [CrossRef]
- Zhukabayeva, T.; Zholshiyeva, L.; Karabayev, N.; Khan, S.; Alnazzawi, N. Cybersecurity Solutions for Industrial Internet of Things–Edge Computing Integration: Challenges, Threats, and Future Directions. Sensors 2025, 25, 213. [Google Scholar] [CrossRef]
- Alotaibi, B. A survey on industrial Internet of Things security: Requirements, attacks, AI-based solutions, and edge computing opportunities. Sensors 2023, 23, 7470. [Google Scholar] [CrossRef]
- Alqattan, D.; Ojha, V.; Habib, F.; Noor, A.; Morgan, G.; Ranjan, R. Modular neural network for edge-based detection of early-stage IoT botnet. High-Confid. Comput. 2025, 5, 100230. [Google Scholar] [CrossRef]
- Li, Q.; Huang, H.; Li, R.; Lv, J.; Yuan, Z.; Ma, L.; Han, Y.; Jiang, Y. A comprehensive survey on DDoS defense systems: New trends and challenges. Comput. Netw. 2023, 233, 109895. [Google Scholar] [CrossRef]
- Kerkouche, R.; Ács, G.; Castelluccia, C. Federated learning in adversarial settings. arXiv 2020, arXiv:2010.07808. [Google Scholar]
- Almukhalfi, H.; Noor, A.; Noor, T.H. Traffic management approaches using machine learning and deep learning techniques: A survey. Eng. Appl. Artif. Intell. 2024, 133, 108147. [Google Scholar] [CrossRef]
- Kocher, G.; Kumar, G. Machine learning and deep learning methods for intrusion detection systems: Recent developments and challenges. Soft Comput. 2021, 25, 9731–9763. [Google Scholar] [CrossRef]
- Akgun, D.; Hizal, S.; Cavusoglu, U. A new DDoS attacks intrusion detection model based on deep learning for cybersecurity. Comput. Secur. 2022, 118, 102748. [Google Scholar] [CrossRef]
- Kasyap, H.; Tripathy, S. Privacy-preserving decentralized learning framework for healthcare system. ACM Trans. Multimed. Comput. Commun. Appl. (TOMM) 2021, 17, 1–24. [Google Scholar] [CrossRef]
- Noor, T.H.; Almars, A.M.; El-Sayed, A.; Noor, A. Deep learning model for predicting consumers’ interests of IoT recommendation system. Int. J. Adv. Comput. Sci. Appl. 2022, 13, 161–170. [Google Scholar] [CrossRef]
- Feng, Y.; Guo, Y.; Hou, Y.; Wu, Y.; Lao, M.; Yu, T.; Liu, G. A survey of security threats in Federated Learning. Complex Intell. Syst. 2025, 11, 165. [Google Scholar] [CrossRef]
- Liu, Z.; Guo, J.; Yang, W.; Fan, J.; Lam, K.Y.; Zhao, J. Privacy-preserving aggregation in federated learning: A survey. IEEE Trans. Big Data 2022, 14, 1–20. [Google Scholar] [CrossRef]
- Khraisat, A.; Alazab, A.; Singh, S.; Jan, T.; Gomez, A., Jr. Survey on federated learning for intrusion detection system: Concept, architectures, aggregation strategies, challenges, and future directions. ACM Comput. Surv. 2024, 57, 1–38. [Google Scholar] [CrossRef]
- Neto, H.N.C.; Hribar, J.; Dusparic, I.; Mattos, D.M.F.; Fernandes, N.C. A Survey on Securing Federated Learning: Analysis of Applications, Attacks, Challenges, and Trends. IEEE Access 2023, 11, 41928–41953. [Google Scholar] [CrossRef]
- Beltrán, E.T.M.; Pérez, M.Q.; Sánchez, P.M.S.; Bernal, S.L.; Bovet, G.; Pérez, M.G.; Pérez, G.M.; Celdrán, A.H. Decentralized federated learning: Fundamentals, state of the art, frameworks, trends, and challenges. IEEE Commun. Surv. Tutorials 2023, 25, 2983–3013. [Google Scholar] [CrossRef]
- Uddin, M.P.; Xiang, Y.; Hasan, M.; Bai, J.; Zhao, Y.; Gao, L. A Systematic Literature Review of Robust Federated Learning: Issues, Solutions, and Future Research Directions. Acm Comput. Surv. 2025, 57, 1–62. [Google Scholar] [CrossRef]
- Zhang, C.; Xie, Y.; Bai, H.; Yu, B.; Li, W.; Gao, Y. A survey on federated learning. Knowl.-Based Syst. 2021, 216, 106775. [Google Scholar] [CrossRef]
- Al Razib, M.; Javeed, D.; Khan, M.T.; Alkanhel, R.; Muthanna, M.S.A. Cyber threats detection in smart environments using SDN-enabled DNN-LSTM hybrid framework. IEEe Access 2022, 10, 53015–53026. [Google Scholar] [CrossRef]
- Driss, M.; Almomani, I.; e Huma, Z.; Ahmad, J. A federated learning framework for cyberattack detection in vehicular sensor networks. Complex Intell. Syst. 2022, 8, 4221–4235. [Google Scholar] [CrossRef]
- Alsaleh, S.; Menai, M.E.B.; Al-Ahmadi, S. Federated Learning–Based Model to Lightweight IDSs for heterogeneous IoT Networks: State-of-the-Art, Challenges and Future Directions. IEEE Access 2024, 12, 134256–134272. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Friha, O.; Maglaras, L.; Janicke, H.; Shu, L. Federated Deep Learning for Cyber Security in the Internet of Things: Concepts, Applications, and Experimental Analysis. IEEE Access 2021, 9, 138509–138542. [Google Scholar] [CrossRef]
- Lazaros, K.; Koumadorakis, D.E.; Vrahatis, A.G.; Kotsiantis, S. Federated Learning: Navigating the Landscape of Collaborative Intelligence. Electronics 2024, 13, 4744. [Google Scholar] [CrossRef]
- Wu, D.; Xu, H.; Jiang, Z.; Yu, W.; Wei, X.; Lu, J. EdgeLSTM: Towards Deep and Sequential Edge Computing for IoT Applications. IEEE/ACM Trans. Netw. 2021, 29, 1895–1908. [Google Scholar] [CrossRef]
- Shrestha, R.; Mohammadi, M.; Sinaei, S.; Salcines, A.; Pampliega, D.; Clemente, R.; Sanz, A.L.; Nowroozi, E.; Lindgren, A. Anomaly detection based on LSTM and autoencoders using federated learning in smart electric grid. J. Parallel Distrib. Comput. 2024, 193, 104951. [Google Scholar] [CrossRef]
- Huang, J.; Chen, Z.; Liu, S.Z.; Zhang, H.; Long, H.X. Improved Intrusion Detection Based on Hybrid Deep Learning Models and Federated Learning. Sensors 2024, 24, 4002. [Google Scholar] [CrossRef] [PubMed]
- Belarbi, O.; Spyridopoulos, T.; Anthi, E.; Mavromatis, I.; Carnelli, P.; Khan, A. Federated Deep Learning for Intrusion Detection in IoT Networks. In Proceedings of the GLOBECOM 2023-2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 237–242. [Google Scholar] [CrossRef]
- Kumar, A.; Singh, D. Detection and prevention of ddos attacks on edge computing of IOT devices through reinforcement learning. Int. J. Inf. Technol. 2023, 16, 1365–1376. [Google Scholar] [CrossRef]
- Zheng, J.; Li, K.; Mhaisen, N.; Ni, W.; Tovar, E.; Guizani, M. Exploring Deep-Reinforcement-Learning-Assisted Federated Learning for Online Resource Allocation in Privacy-Preserving EdgeIoT. IEEE Internet Things J. 2022, 9, 21099–21110. [Google Scholar] [CrossRef]
- Kotecha, P.; Dhoka, T.; Bhatia, J.; Kumhar, M.; Gupta, R.; Tanwar, S.; Jadav, N.K. Performance Evaluation of Federated Learning in Edge Computing Environment. Procedia Comput. Sci. 2024, 235, 2955–2964. [Google Scholar] [CrossRef]
- Ren, J.; Yu, G.; Ding, G. Accelerating DNN Training in Wireless Federated Edge Learning Systems. IEEE J. Sel. Areas Commun. 2021, 39, 219–232. [Google Scholar] [CrossRef]
- Kanagavelu, R.; Li, Z.; Samsudin, J.; Yang, Y.; Yang, F.; Mong Goh, R.S.; Cheah, M.; Wiwatphonthana, P.; Akkarajitsakul, K.; Wang, S. Two-Phase Multi-Party Computation Enabled Privacy-Preserving Federated Learning. In Proceedings of the 2020 20th IEEE/ACM International Symposium on Cluster, Cloud and Internet Computing (CCGRID), Melbourne, VIC, Australia, 11–14 May 2020; pp. 410–419. [Google Scholar] [CrossRef]
- Doku, R.; Rawat, D.B. Mitigating Data Poisoning Attacks On a Federated Learning-Edge Computing Network. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Dehghantanha, A.; Karimipour, H.; Srivastava, G.; Parizi, R.M. A Robust Privacy-Preserving Federated Learning Model Against Model Poisoning Attacks. IEEE Trans. Inf. Forensics Secur. 2024, 19, 6693–6708. [Google Scholar] [CrossRef]
- Ye, P.; Jiang, Z.; Wang, W.; Li, B.; Li, B. Feature Reconstruction Attacks and Countermeasures of DNN Training in Vertical Federated Learning. IEEE Trans. Dependable Secur. Comput. 2024, 22, 2659–2669. [Google Scholar] [CrossRef]
- Doriguzzi-Corin, R.; Siracusa, D. FLAD: Adaptive Federated Learning for DDoS attack detection. Comput. Secur. 2024, 137, 103597. [Google Scholar] [CrossRef]
- Xu, J.; Zhang, Z.; Hu, R. Achieving byzantine-resilient federated learning via layer-adaptive sparsified model aggregation. In Proceedings of the 2025 IEEE/CVF Winter Conference on Applications of Computer Vision (WACV), Tucson, AZ, USA, 26 February–6 March 2025; pp. 1508–1517. [Google Scholar]
- Li, L.; Zhu, L.; Li, W. Cloud–Edge–End Collaborative Federated Learning: Enhancing Model Accuracy and Privacy in Non-IID Environments. Sensors 2024, 24, 8028. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Friha, O.; Hamouda, D.; Maglaras, L.; Janicke, H. Edge-IIoTset: A New Comprehensive Realistic Cyber Security Dataset of IoT and IIoT Applications for Centralized and Federated Learning. IEEE Access 2022, 10, 40281–40306. [Google Scholar] [CrossRef]
- Lee, Y.C.; Chien, W.C.; Chang, Y.C. FedDB: A Federated Learning Approach Using DBSCAN for DDoS Attack Detection. Appl. Sci. 2024, 14, 10236. [Google Scholar] [CrossRef]
| Attacks | Accuracy | Precision | Recall | F1-Score | Response Time |
|---|---|---|---|---|---|
| DDoS | 0.63 | 0.89 | 0.62 | 0.73 | 29.10 s |
| DoS | 0.97 | 0.87 | 0.98 | 0.93 | 27.12 s |
| Injection | 0.90 | 0.77 | 0.90 | 0.83 | 28.53 s |
| Attacks | Accuracy | Precision | Recall | F1-Score | Response Time |
|---|---|---|---|---|---|
| DDoS | 0.61 | 0.88 | 0.61 | 0.72 | 30.96 s |
| DoS | 0.96 | 0.87 | 0.97 | 0.93 | 29.25 s |
| Injection | 0.87 | 0.76 | 0.89 | 0.82 | 30.15 s |
| Attacks | Accuracy | Precision | Recall | F1-Score | Response Time |
|---|---|---|---|---|---|
| DDoS | 0.63 | 0.86 | 0.62 | 0.72 | 39.46 s |
| DoS | 0.98 | 0.87 | 97 | 0.93 | 37.13 s |
| Injection | 0.88 | 0.77 | 0.88 | 0.82 | 38.25 s |
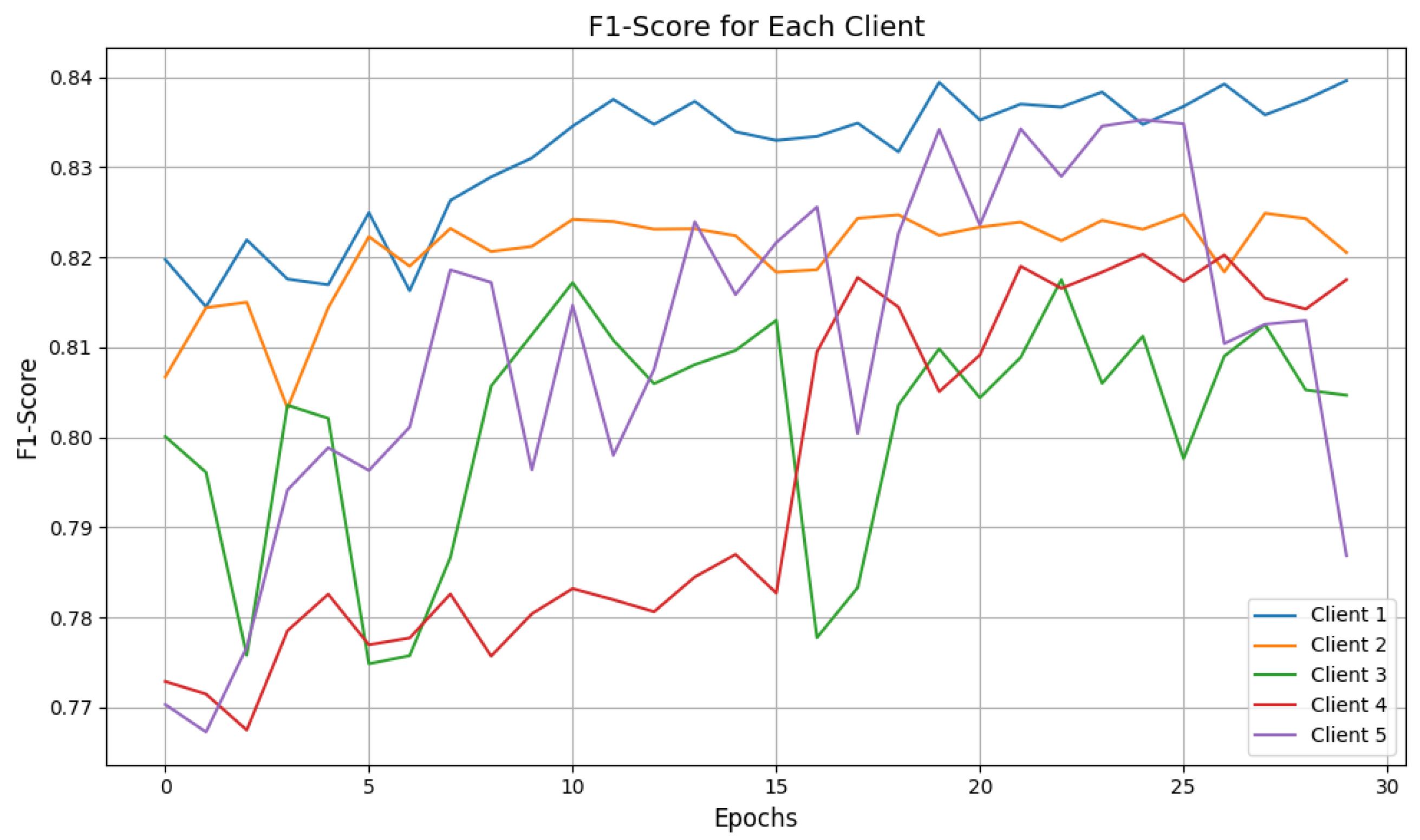
| Clients | Attacks | Accuracy | Precision | Recall | F1-Score | Response Time |
|---|---|---|---|---|---|---|
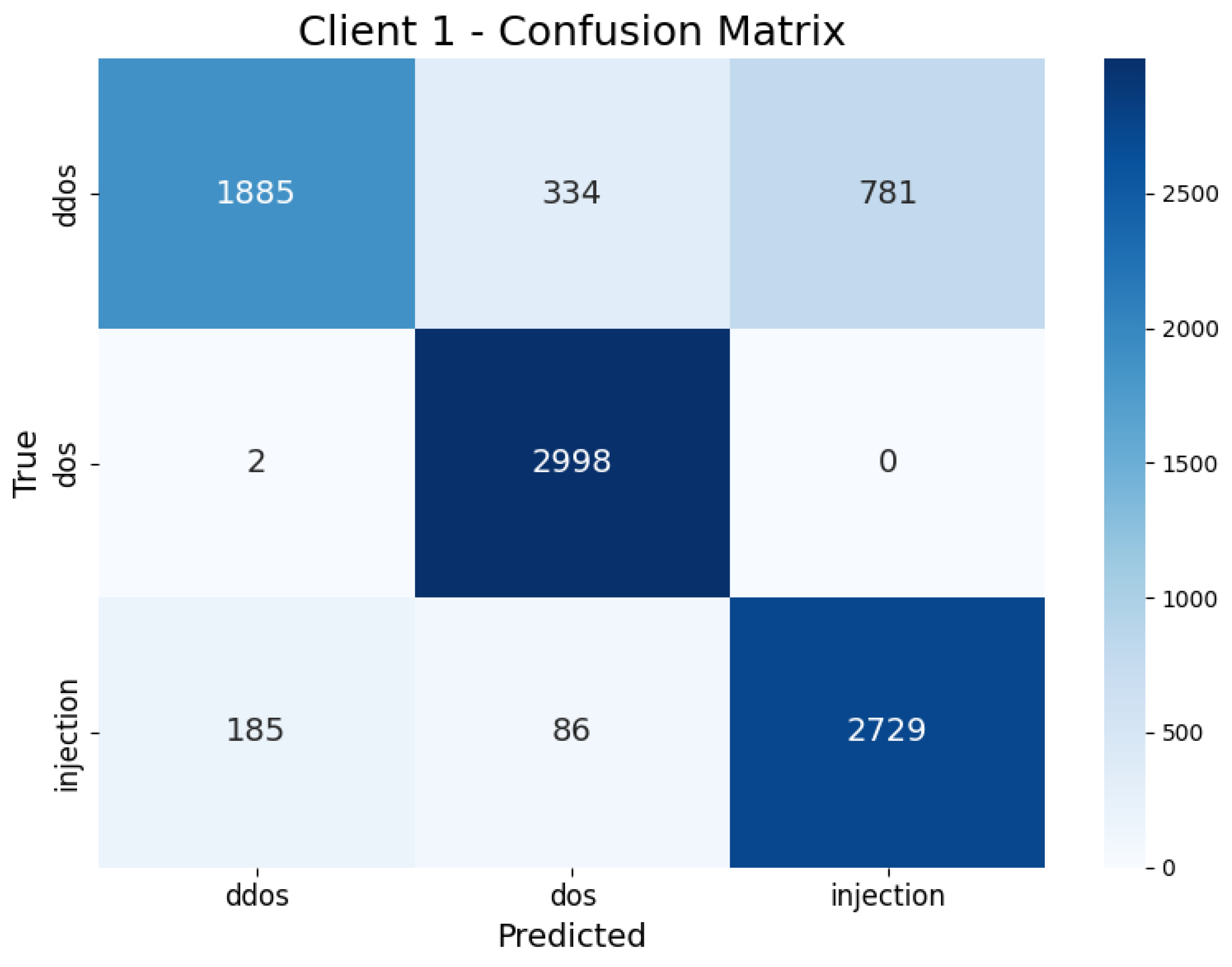
| Client 1 | DDoS | 0.69 | 0.91 | 0.60 | 0.72 | 15.83 s |
| DoS | 1 | 0.88 | 1 | 0.93 | ||
| Injection | 0.91 | 0.76 | 0.92 | 0.83 | ||
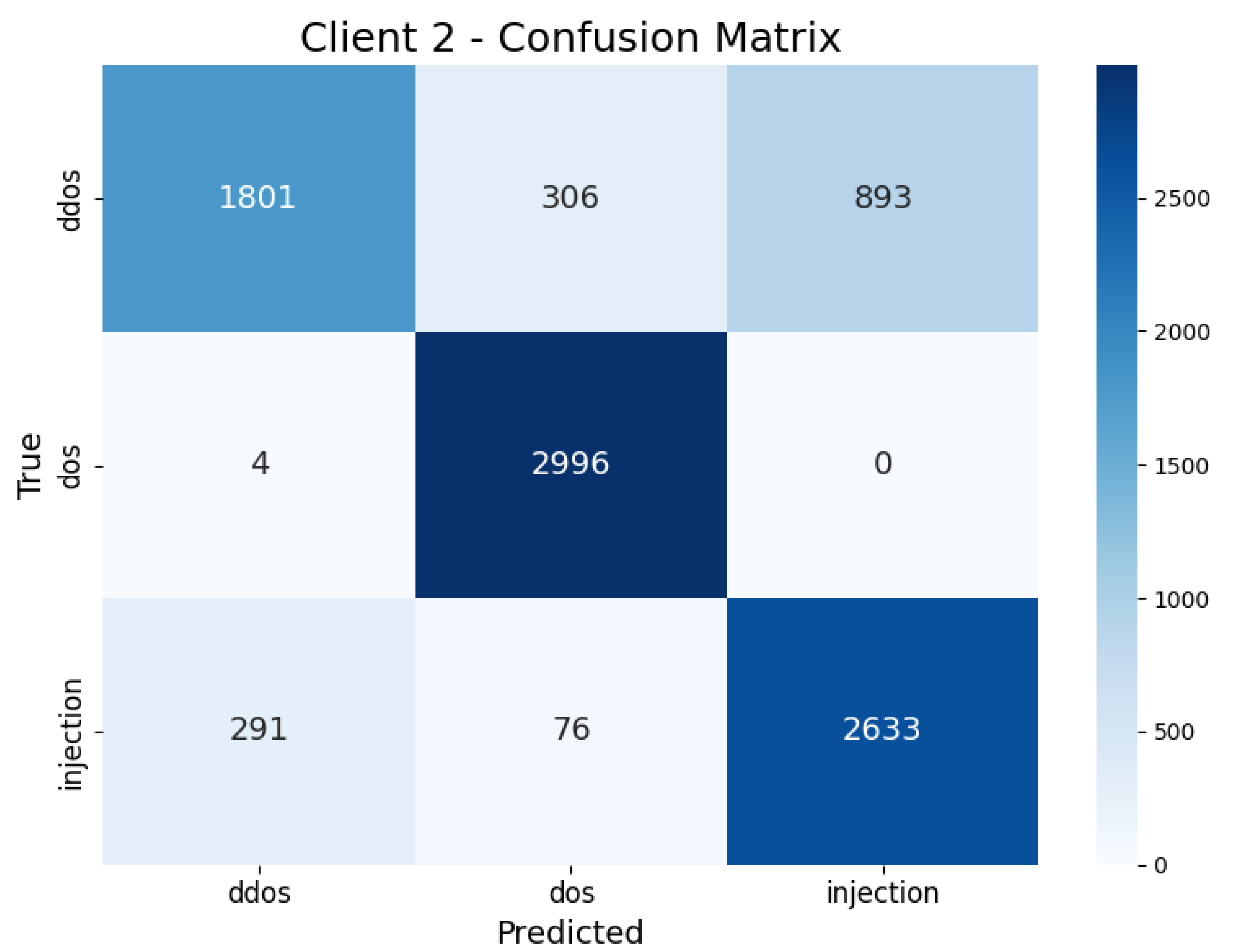
| Client 2 | DDoS | 0.70 | 0.84 | 0.60 | 0.70 | 16.34 s |
| DoS | 0.99 | 0.89 | 0.99 | 0.94 | ||
| Injection | 0.86 | 0.74 | 0.87 | 0.80 | ||
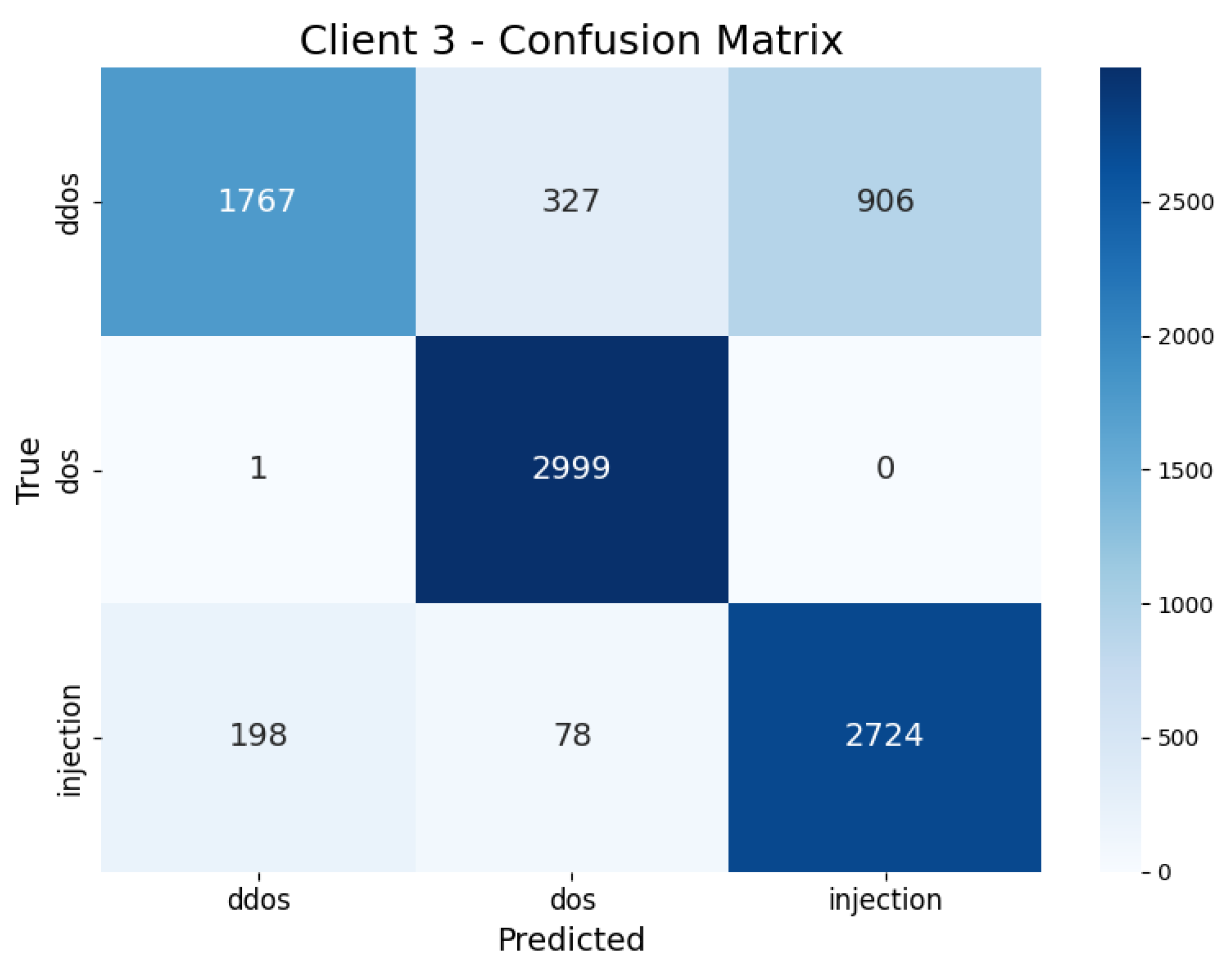
| Client 3 | DDoS | 0.66 | 0.89 | 0.56 | 0.69 | 16.45 s |
| DoS | 0.99 | 0.88 | 0.99 | 0.93 | ||
| Injection | 0.91 | 0.73 | 0.91 | 0.81 | ||
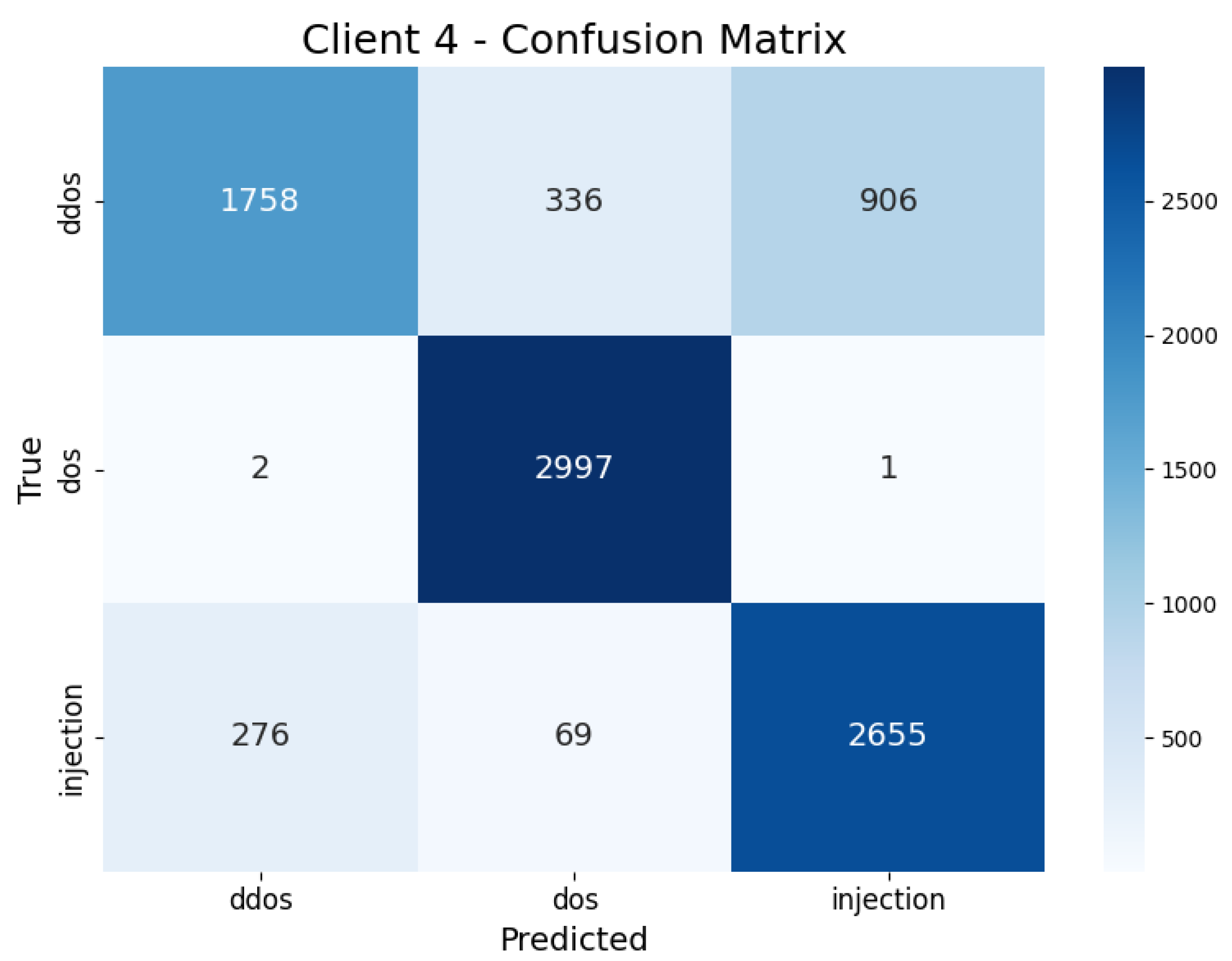
| Client 4 | DDoS | 0.56 | 0.92 | 0.47 | 0.62 | 16.54 s |
| DoS | 1 | 0.88 | 1 | 0.94 | ||
| Injection | 0.93 | 0.69 | 0.94 | 0.79 | ||
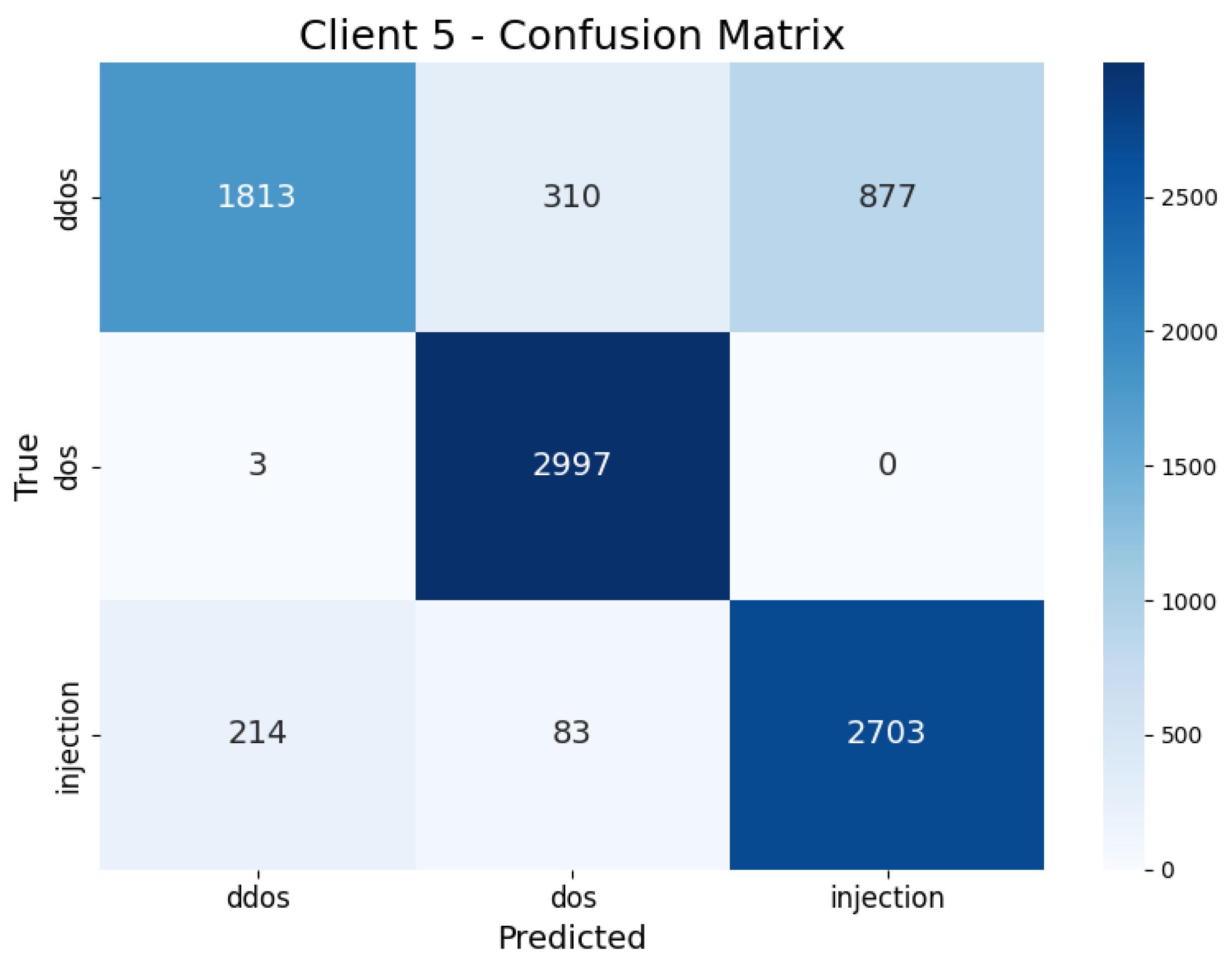
| Client 5 | DDoS | 0.62 | 0.91 | 0.53 | 0.67 | 15.28 s |
| DoS | 0.99 | 0.88 | 1 | 0.94 | ||
| Injection | 0.92 | 0.71 | 0.92 | 0.81 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alamir, R.H.; Noor, A.; Almukhalfi, H.; Almukhlifi, R.; Noor, T.H. SecFedDNN: A Secure Federated Deep Learning Framework for Edge–Cloud Environments. Systems 2025, 13, 463. https://doi.org/10.3390/systems13060463
Alamir RH, Noor A, Almukhalfi H, Almukhlifi R, Noor TH. SecFedDNN: A Secure Federated Deep Learning Framework for Edge–Cloud Environments. Systems. 2025; 13(6):463. https://doi.org/10.3390/systems13060463
Chicago/Turabian StyleAlamir, Roba H., Ayman Noor, Hanan Almukhalfi, Reham Almukhlifi, and Talal H. Noor. 2025. "SecFedDNN: A Secure Federated Deep Learning Framework for Edge–Cloud Environments" Systems 13, no. 6: 463. https://doi.org/10.3390/systems13060463
APA StyleAlamir, R. H., Noor, A., Almukhalfi, H., Almukhlifi, R., & Noor, T. H. (2025). SecFedDNN: A Secure Federated Deep Learning Framework for Edge–Cloud Environments. Systems, 13(6), 463. https://doi.org/10.3390/systems13060463








