Cybersecurity for Analyzing Artificial Intelligence (AI)-Based Assistive Technology and Systems in Digital Health
Abstract
1. Introduction
- Providing theoretical and technical foundations for securing AI-based assistive systems that support AI-based AT for digital health.
- Providing practical AI-based security tools for developing the proposed model and applying the tested algorithms and protocols.
2. Literature Review
2.1. AI and Cybersecurity in Healthcare Systems
2.2. Cybersecurity in Emerging Healthcare Technologies
2.3. Cybersecurity for Analyzing AI-Based AT via Digital Healthcare Applications
| Refs. | Scope | Remarks | Details of Cyber Issues | ||
|---|---|---|---|---|---|
| Contributions | Limitations | Summary | Malware | ||
| [51] | Cyber risk insurance for ransomware | Proposes a mixed-method approach for evaluating and reducing risks using cyber risk insurance techniques. Emphasizes the need for proactive risk management. | Limited focus on non-ransomware cyber threats. Lacks a mixed-method procedure and increases the complexity of the space. | Discusses ransomware risks, their financial impact, cyber-insurance modeling, and risk management and mitigation strategies. | R |
| [52] | AI in ophthalmology | Reviews AI-based assistive applications in ophthalmology by focusing on the accuracy of diagnosis and treatment planning. | Lacks secure image management, and does not address data privacy, ethical considerations, or regulatory challenges when using AI in healthcare. | Raises concerns about data security related to the sensitive medical records used by AI systems. Lacks a thorough investigation of different healthcare-specific cyber threats. | R |
| [53] | Mixed reality (MR) and IoT for elderly assistive technology | Integrates mixed reality and IoT for elderly care in smart home environments, enhancing independence, safety, and quality of life. | Technical challenges related to user adoption and system interoperability in MR and IoT integration are not fully addressed. | IoT security concerns, including potential data breaches and unauthorized access. | NR |
| [54] | Assistive robots for autistic children | Explores how robots enhance cognitive abilities and foster learning experiences for children with autism spectrum disorder (ASD), providing evidence from experimental studies. | Widespread adoption might be hindered by high costs and technical challenges in robot deployment. | Limited discussion on cybersecurity risks in robotic systems, despite the reliance on connected devices, which could introduce vulnerabilities such as hacking or the misuse of personal data. | NR |
| [55] | Instructional strategies in assistive technology for learning disabilities | Conducts a meta-synthesis review of effective instructional strategies for assistive technology in learning disabilities, providing insights into best practices and pedagogical approaches. | Strategic AT must be reviewed; lacks empirical studies on long-term effectiveness. | No significant cybersecurity focus, although it highlights the need for secure digital platforms to protect student data. | NR |
| [56] | AI in e-learning systems | Explores AI technologies and applications in e-learning systems, including personalized learning, adaptive assessments, the automation of administrative tasks, and enhanced learner engagement. | Limited practical applications. | Discusses potential data privacy risks and issues related to security and data protection in AI-driven e-learning platforms. | NR |
| [57] | AIoT in assistive technology | A systematic review of AIoT applications in assistive technology, emphasizing innovations in healthcare, mobility aids, and smart living solutions. | No emphasis on challenges related to scalability and integration with existing systems. | Potential cyber issues include AIoT security vulnerabilities, data breaches, unauthorized access, and concerns regarding data integrity. | NR |
| [58] | AI assistive technology in hospital nursing | Designs a 3D human pose estimation system for home care robots, and how AI enhances professional nursing practices, including patient monitoring, diagnostics, workflow optimization, and decision support. | Lacks real-world case studies. | Security concerns related to patient data and medical data privacy. | R + NR |
| [59] | AI in prosthetic and orthotic rehabilitation | Reviews AI’s integration in rehabilitation technologies, including personalized design and functionality enhancements. | Limited cybersecurity perspective | No major cybersecurity risks are discussed, although connected prosthetic devices may be vulnerable to hacking or malfunction due to software flaws. | R + NR |
| [60] | AI in sports training | Explored AI applications in sports training through case studies, including optimizing athlete performance analysis, injury prevention, and training customization. | Lacks discussion of the practical implementation of AI in areas other than sports training. | Limited focus on significant cybersecurity issues, although wearable tech and AI systems used in sports could face threats such as data theft or system tampering. | NR |
| [61] | Emerging technologies in assistive tech | Reviews emerging technologies and their potential for creating new assistive technologies for people with disabilities. | General overview, lacks depth in AT applications and detailed implementation strategies. | Does not specify the types of cyber risks or mitigation strategies associated with emerging technologies. | NR |
3. Research Methodology
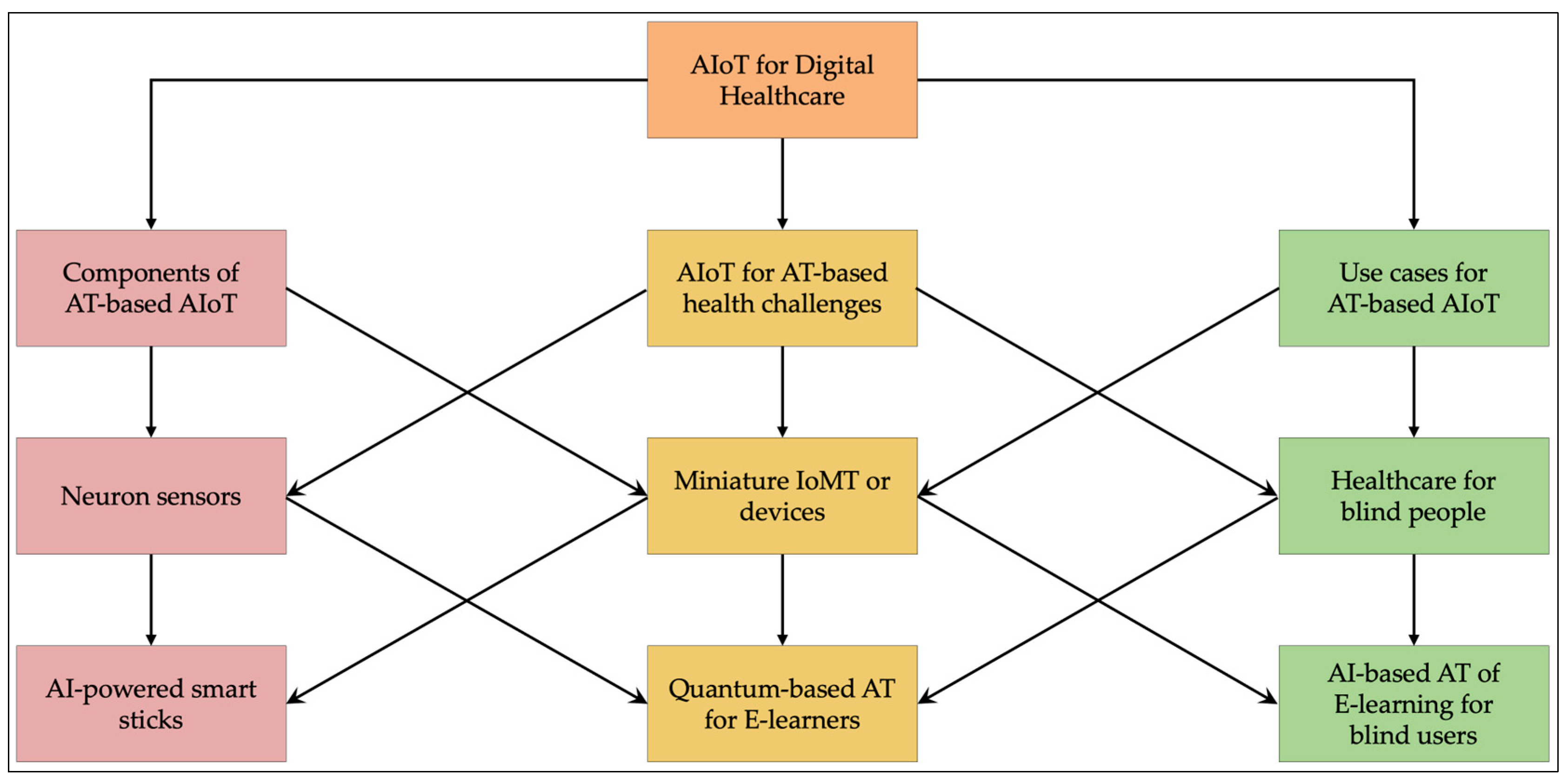
3.1. The Assistive Systems
3.2. Cybersecurity with Digital Healthcare Applications
3.2.1. Assistive Systems for People with Sight Impairments
3.2.2. Assistive Systems for People with Hearing Impairments
3.2.3. Assistive Systems for People with Cognitive Impairments
3.2.4. Assistive Systems for People with Physical Impairments
3.3. Illustrative Use Case: Cyber Risk in AT-Based E-Learning for Blind Users
- Scenario:
- Medical Context in Digital Health:
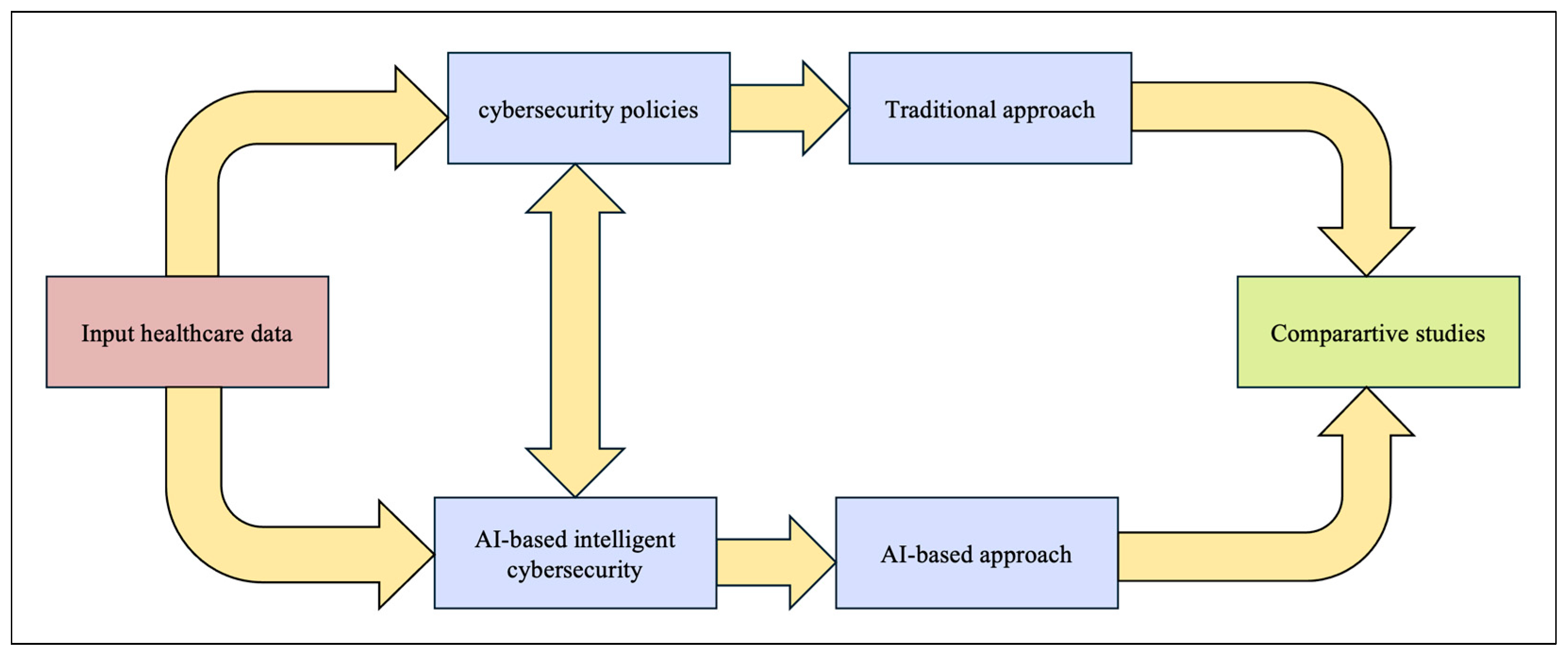
3.4. Theoretical Model
3.5. Methodology
- Learning potential risks, future cyberattacks, and threats with the evolving security issues considered in assistive systems with emerging technologies. The vulnerabilities of assistive systems that damage users’ services, applications, etc., have to be analyzed with the AT.
- Building an efficient model for securing assistive systems and services between the user devices that are fixed for those who use secure facilities, and analyzing the model presented in this study and the use of AT by those with physical disabilities.
- Developing cybersecurity solutions using security algorithms, intelligent techniques, and the latest emerging technology, aiming to increase security and reduce overall cost, depending on the energy consumption and use of low-complexity AT.
- Maintaining the dynamic cybersecurity solution while the services are used by different assistive systems.
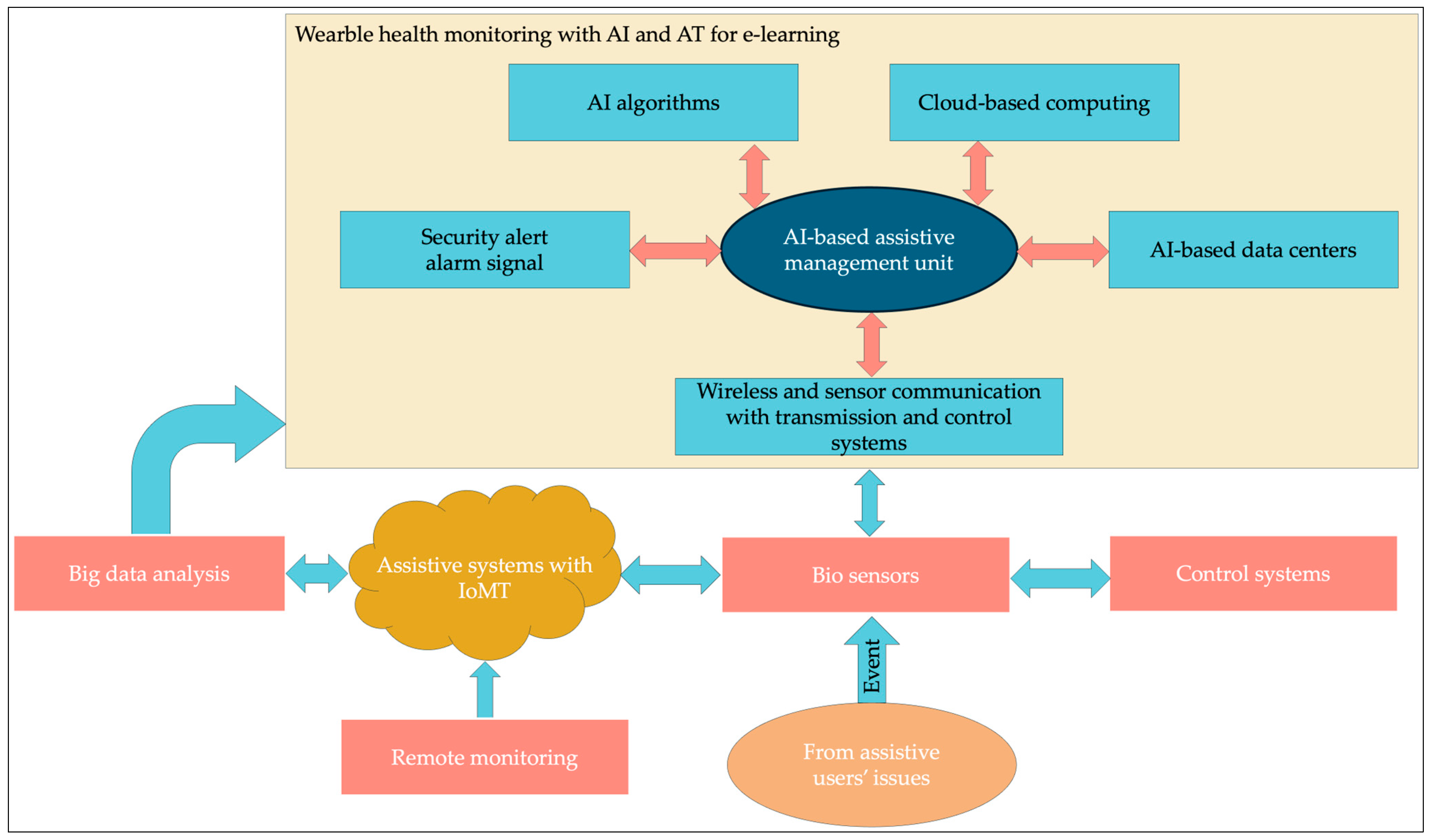
- Biosensors collect the necessary data from assistive users and remote monitoring systems and send them to a wearable health monitoring block.
- Security alarm signals detect all types of cyber-attacks, including ransomware attacks, when data arrive at the AI-based assistive management unit.
- Critical Industry (CI): In digital healthcare and learning environments, hackers install ransomware payloads on the CI’s e-health and e-learning infrastructure using phishing emails and vulnerable online systems. The AI-based assistive management unit (AAMU) identifies and detects ransomware attacks from phishing emails.
- Organization Size (Size): Big data analysis and control systems identify the size of the data and security control issues, such as policies, before AAMU determines the risks through AI-based data centers.
- Digital Intensity (DI): AAMU’s AI algorithms reduce the DI, which refers to the extent of digital technology usage across different levels of operational and strategic activities within a digital healthcare organization. When the proposed model allows us to reduce DI, ransomware attacks can be reduced.
- Network Segmentation (NS): The NS of big data in AI-based data centers helps minimize the occurrence of ransomware attacks.
- Attack Vector (AV): The AI-based security algorithms used in the development of perimeter elements will help prevent ransomware AVs from digital healthcare organizations.
- Privileges Required (PR): AAMU’s proactive approach to vulnerability and ransomware risk assessments depends on the use of AT and PR, which are less exposed to the risk of a ransomware attack.
- Attack Complexity (AC): AI algorithms and control systems identify the AC of IoT and biosensors because the scalability of IoT is increasing in assistive systems and digital healthcare organizations.
- User Interaction (UI): The proposed model’s remote monitoring collects the risks of UI when AT users are involved in e-learning and digital healthcare applications.
- Scope (SC): Cloud-based computing, secure communication channels, and alarm signals can reduce the probability of ransomware attacks. Handling policies, rules, and hypotheses that do not engage the UI and or change the authorization rights affect the SC of the vulnerable. Therefore, ransomware risks can be minimized using vulnerability assessments.
- Confidentiality–Integrity–Availability (CIA): The rules regarding security management in healthcare improve cybersecurity solutions by providing the necessary security algorithms, including CIA policies.
- Cybersecurity Role (CSR): The presence of a CSR within healthcare organizations ensures the proper implementation of IT controls and AT developments, and ensures the systems are used correctly, thereby enhancing cybersecurity.
3.6. Security in Digital Healthcare with E-Learning
- Low = (i): Minimum level of risk.
- Medium = (ii): Medium level of risk.
- High = (iii): Peak, maximum, or dangerous levels of risk.
4. Results
- Theoretical and technical foundations for improving measurements related to cardiac issues using a proposed framework that will encourage researchers to explore the use of AI-based quantum technology in other specific areas involving cardiac issues in digital health.
- Practical AI-based quantum monitoring tools for developing a proposed framework and applying tested AI algorithms and quantum protocols.
- Extensions of existing software-based protocols related to cardiac issues (such as traditional routing and quantum routing protocols) that account for the dynamically changing time response versus risk and security levels in the critical, harsh digital healthcare environment, which could enhance the efficiency of proactive systems.
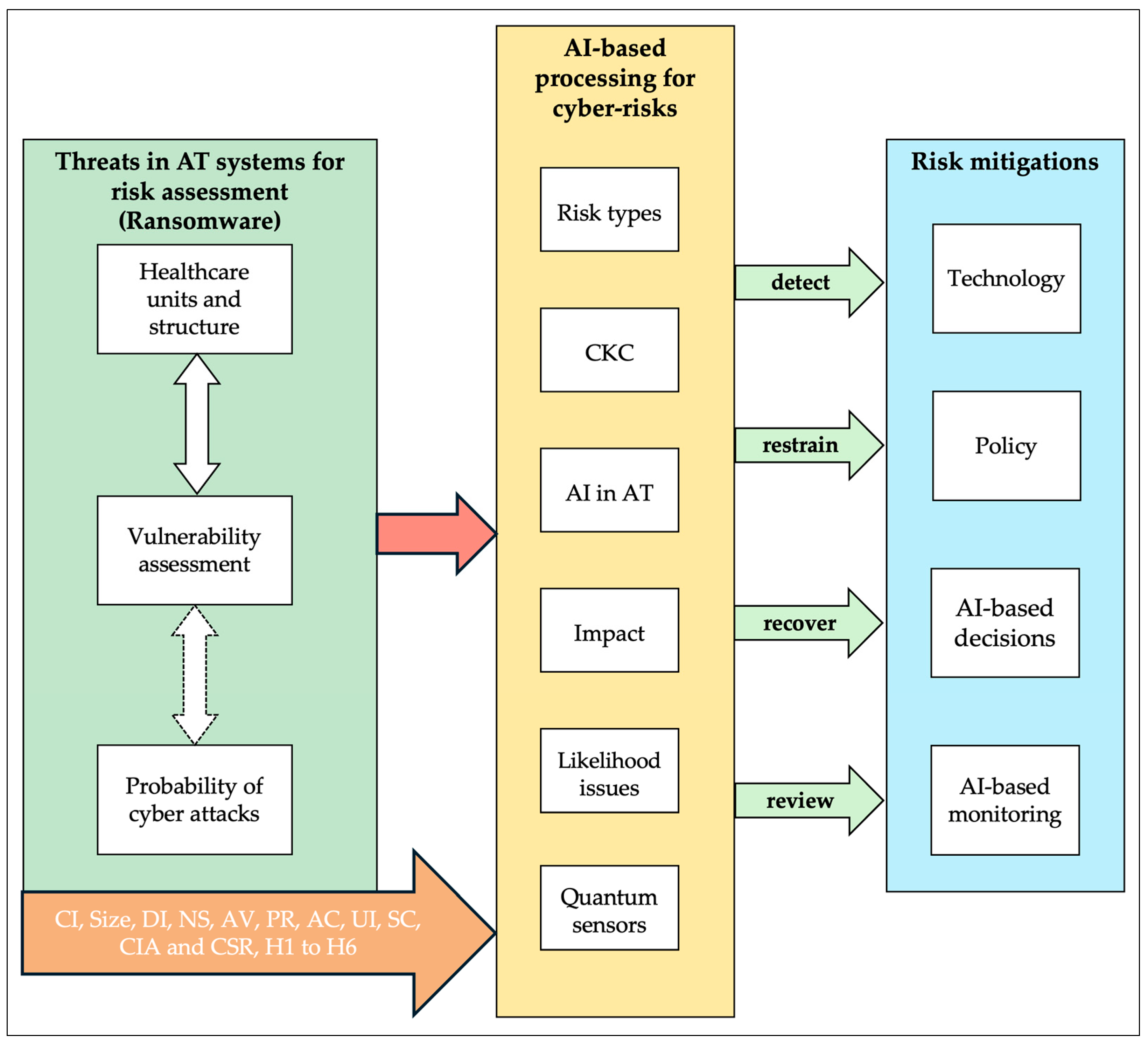
5. Discussion and Analysis
- Assets are assigned a value (asset value (AV)).
- Each asset is researched and a list is produced of all possible threats to each asset. The exposure factor (EF) and single loss expectancy (SLE) for each listed threat are focused on.
- A threat analysis is conducted to calculate the likelihood of each threat being realized within a single year—the annualized rate of occurrence (ARO).
- The overall loss potential per threat is derived by calculating the annualized loss expectancy (ALE).
- Research the countermeasures for each threat and then calculate the changes to ARO and ALE based on the applied countermeasure.
- Perform a cost/benefit analysis of each countermeasure
- Likelihood = [Very Low, Low, Medium, High, Very High].
- Impact = [None, Low, Medium, High, Critical].
6. Challenges
- Quantum sensing technology enhances the speed of response time which, allows for doctors to see symptoms proactively when diagnosing using miniature devices.
- The first biological quantum-light microscope used squeezed light in an optical tweezer to probe the interior of a living yeast cell.
- The Integrated Quantum Networks (IQN) Hub is a research hub that aims to create a quantum internet.
- Advanced quantum communication protocols can improve medical systems by providing efficient and secure communication and the efficient and secure administration of digital healthcare.
- Quantum routing will upgrade the traditional features integrated with the legacy assistive systems used in digital healthcare.
- Quantum position navigation and timing (PNT) can be used in the prediction models used to diagnose heart diseases through the insertion of miniature devices.
- Miniature microfabricated quantum inertial sensors can be used to examine ex neuron communication within the brain and other organs using specific miniature devices.
- Biomedical Imaging: Quantum sensors that detect minute variations in magnetic fields are being created for a variety of uses, including the early detection of Alzheimer’s disease, cardiovascular disease, and epilepsy. Faster scan speeds to help reduce waiting lists are among the new quantum imaging features being investigated to improve MRI.
- Quantum-Enhanced In Vitro Diagnostics: Spin-enhanced nanodiamond sensors will be used to develop ultra-sensitive blood tests in portable formats, such as basic lateral flow testing. This could allow for the early diagnosis of a variety of diseases, from infections to cancer, by expanding access to testing in GP offices and pharmacies, as well as at-home self-testing. Novel surgical and therapeutic approaches could also be provided for difficult-to-treat and early-stage malignancies. Among these is a novel strategy looking into the treatment of cancer with magnetic nanoparticles.
- To allow for secure digital healthcare and rehabilitation.
- In e-learning paradigms for neural networks and automated medical diagnostics.
- Hardware limitations, such as limitations to its scalability, high error rates in calculation, and cryogenic requirements.
- Quantum algorithms are limited and their integration with AI is still in its infancy.
- Quantum threats to encryption threaten data privacy and security, requiring the adoption of quantum-safe cryptography.
- The expensive infrastructure, resource intensity lead to high costs and resource constraints.
- Data bias in quantum AI and regulatory uncertainty lead to ethical and regulatory concerns.
- The shortage of skilled professionals and collaboration barriers between quantum researchers and healthcare practitioners lead to gaps in interdisciplinary expertise.
- There is uncertainty in its practical applications due to the limited real-world use cases and long development timelines.
- Its integration with existing systems faces compatibility issues that require hybrid solutions.
- Examinations of public perception and trust suggest a lack of awareness of many healthcare stakeholders, as well as trust issues and implications regarding its reliability, transparency, and ethical use.
- The use of AIoT with IQN will lead to many new challenges when a priority approach is considered in digital healthcare and AI-based AT.
- Miniature microfabricated quantum inertial sensors and PNT will enhance the proactiveness of the prediction models. Quantum routing in neuron sensor communication will allow doctors to monitor the weakest neuron behaviors, which lead to health data showing risks that were found in the organs.
7. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| APT | Advanced Persistent Threat |
| AAMU | AI-based Assistive Management Unit |
| AHC | AI-based Healthcare Communication |
| ALE | Annualized Loss Expectancy |
| ARO | Annualized Rate of Occurrence |
| AI | Artificial Intelligence |
| AIoT | Artificial Intelligence of Things |
| AV | Asset Value |
| AT | AT |
| AC | Attack Complexity |
| AV | Attack Vector |
| ASD | Autism Spectrum Disorder |
| BICS-AI | Blockchain-Integrated Cybersecurity Approach Based on AI |
| CIA | Confidentiality–Integrity–Availability |
| CKC | Cyber Kill Chain |
| CI | Critical Industry |
| CSR | Cybersecurity Role |
| DoS | Denial-of-Service |
| DI | Digital Intensity |
| EPS | End-Point Security |
| EF | Exposure Factor |
| GDPR | General Data Protection Regulation |
| H | Hazards |
| HIPAA | Health Insurance Portability and Accountability Act |
| IQN | Integrated Quantum Networks |
| IoMT | Internet of Medical Things |
| IoT | Internet of Things |
| L | Likelihood |
| LGE-HES | Lionized Golden Eagle-based Homomorphic Elapid Security |
| LR | Logistic Regression |
| ML | Machine Learning |
| MD | Miniature Detectors |
| MR | Mixed Reality |
| MEC | Multi-Access Edge Computing |
| NLP | Natural Language Processing |
| N | Negligence |
| NS | Network Segmentation |
| NGT | Nominal Group Technique |
| Size | Organization Size |
| PNT | Position Navigation and Timing |
| PR | Privileges Required |
| P | Probability |
| PMT | Protection Motivation Theory |
| Q-BIOMED | Quantum-based biomedicine |
| R | Ransomware |
| NR | Non-Ransomware |
| RT | Risk Type |
| R | Risk |
| SC | Scope |
| SLE | Single Loss Expectancy |
| T | Threat |
| UI | User Interaction |
| V | Vulnerability |
References
- WHO. 2023. Available online: https://www.who.int/health-topics/assistive-technology#tab=tab_1 (accessed on 4 March 2025).
- Fall, C.L.; Gagnon-Turcotte, G.; Dubé, J.F.; Gagné, J.S.; Delisle, Y.; Campeau-Lecours, A.; Gosselin, C.; Gosselin, B. Wireless sEMG-Based Body–Machine Interface for AT Devices. IEEE J. Biomed. Health Inform. 2017, 21, 967–977. [Google Scholar] [CrossRef] [PubMed]
- Tyagi, N.; Sharma, D.; Singh, J.; Sharma, B.; Narang, S. Assistive Navigation System for Visually Impaired and Blind People: A Review. In Proceedings of the 2021 International Conference on Artificial Intelligence and Machine Vision (AIMV), Gandhinagar, India, 24–26 September 2021; pp. 1–5. [Google Scholar]
- Baucas, M.J.; Spachos, P.; Gregori, S. Internet-of-Things Devices and Assistive Technologies for Health Care: Applications, Challenges, and Opportunities. IEEE Signal Process. Mag. 2021, 38, 65–77. [Google Scholar] [CrossRef]
- Hussain Shah, S.J.; Albishri, A.A.; Lee, Y. Deep Learning Framework for Internet of Things for People With Disabilities. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; pp. 3609–3614. [Google Scholar]
- Brilli, D.D.; Georgaras, E.; Tsilivaki, S.; Melanitis, N.; Nikita, K. Airis: An ai-powered wearable assistive device for the visually impaired. In Proceedings of the 2024 10th IEEE RAS/EMBS International Conference for Biomedical Robotics and Biomechatronics (BioRob), Heidelberg, Germany, 1–4 September 2024; pp. 1236–1241. [Google Scholar]
- Bajwa, J.; Munir, U.; Nori, A.; Williams, B. Artificial intelligence in healthcare: Transforming the practice of medicine. Future Health J. 2021, 8, e188–e194. [Google Scholar] [CrossRef]
- Gala, D.; Behl, H.; Shah, M.; Makaryus, A.N. The role of artificial intelligence in improving patient outcomes and future of healthcare delivery in cardiology: A narrative review of the literature. Healthcare 2024, 12, 481. [Google Scholar] [CrossRef]
- Maleki Varnosfaderani, S.; Forouzanfar, M. The role of AI in hospitals and clinics: Transforming healthcare in the 21st century. Bioengineering 2024, 11, 337. [Google Scholar] [CrossRef]
- Davenport, T.; Kalakota, R. The potential for artificial intelligence in healthcare. Future Healthc. J. 2019, 6, 94–98. [Google Scholar] [CrossRef]
- Holmes, J.; Sacchi, L.; Bellazzi, R. Artificial intelligence in medicine. Ann. R. Coll. Surg. Engl. 2004, 86, 334–338. [Google Scholar]
- Jiang, F.; Jiang, Y.; Zhi, H.; Dong, Y.; Li, H.; Ma, S.; Wang, Y.; Dong, Q.; Shen, H.; Wang, Y. Artificial intelligence in healthcare: Past, present and future. Stroke Vasc. Neurol. 2017, 2, 230–243. [Google Scholar] [CrossRef]
- Elnawawy, M.; Hallajiyan, M.; Mitra, G.; Iqbal, S.; Pattabiraman, K. Systematically assessing the security risks of AI/ML-enabled connected healthcare systems. In Proceedings of the 2024 IEEE/ACM Conference on Connected Health: Applications, Systems and Engineering Technologies (CHASE), Wilmington, DE, USA, 19–21 June 2024; pp. 97–108. [Google Scholar]
- Biasin, E.; Kamenjašević, E.; Ludvigsen, K.R. Cybersecurity of AI medical devices: Risks, legislation, and challenges. In Research Handbook on Health, AI and the Law; Edward Elgar Publishing: Cheltenham, UK, 2024; pp. 57–74. [Google Scholar]
- Mirsky, Y.; Mahler, T.; Shelef, I.; Elovici, Y. {CT-GAN}: Malicious tampering of 3d medical imagery using deep learning. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 461–478. [Google Scholar]
- Muley, A.; Muzumdar, P.; Kurian, G.; Basyal, G.P. Risk of AI in Healthcare: A comprehensive literature review and study framework. arXiv 2023, arXiv:2309.14530. [Google Scholar] [CrossRef]
- Kamerer, J.L.; McDermott, D. Cybersecurity: Nurses on the front line of prevention and education. J. Nurs. Regul. 2020, 10, 48–53. [Google Scholar] [CrossRef]
- Jalali, M.S.; Kaiser, J.P. Cybersecurity in hospitals: A systematic, organizational perspective. J. Med. Internet Res. 2018, 20, e10059. [Google Scholar] [CrossRef] [PubMed]
- McLeod, A.; Dolezel, D. Cyber-analytics: Modeling factors associated with healthcare data breaches. Decis. Support Syst. 2018, 108, 57–68. [Google Scholar] [CrossRef]
- Alotaibi, Y.K.; Federico, F. The impact of health information technology on patient safety. Saudi Med. J. 2017, 38, 1173–1180. [Google Scholar] [CrossRef] [PubMed]
- Layode, O.; Naiho, H.N.N.; Adeleke, G.S.; Udeh, E.O.; Labake, T.T. The role of cybersecurity in facilitating sustainable healthcare solutions: Overcoming challenges to protect sensitive data. Int. Med. Sci. Res. J. 2024, 4, 668–693. [Google Scholar] [CrossRef]
- Baker, S.; Xiang, W. Artificial intelligence of things for smarter healthcare: A survey of advancements, challenges, and opportunities. IEEE Commun. Surv. Tutor. 2023, 25, 1261–1293. [Google Scholar] [CrossRef]
- Pistorius, C. Developments in emerging digital health technologies. DeltaHedron Innov. Insight 2017, 1, 1–17. [Google Scholar]
- Algarni, A.M.; Thayananthan, V. Digital Health: The Cybersecurity for AI-based healthcare communication. IEEE Access 2025, 13, 5858–5870. [Google Scholar] [CrossRef]
- Thayananthan, V. Advanced Security Issues of IoT Based 5G Plus Wireless Communication for Industry 4.0. Available online: https://novapublishers.com/shop/advanced-security-issues-of-iot-based-5g-plus-wireless-communication-for-industry-4-0/ (accessed on 4 March 2025).
- Shaikh, R.A.; Thayananthan, V. Patent: Trust Evaluation Wireless Network for Routing Data Packets. U.S. Patent 10225708B2, 5 March 2019. [Google Scholar]
- Algarni, A.; Thayananthan, V. Improvement of 5G transportation services with SDN-based security solutions and beyond 5G. Electronics 2021, 10, 2490. [Google Scholar] [CrossRef]
- Shaikh, R.A.; Thayananthan, V. Risk-based decision methods for vehicular networks. Electronics 2019, 8, 627. [Google Scholar] [CrossRef]
- Chakraborty, C.; Nagarajan, S.M.; Devarajan, G.G.; Ramana, T.V.; Mohanty, R. Intelligent AI-based healthcare cyber security system using multi-source transfer learning method. ACM Trans. Sens. Networks 2023, 19, 14. [Google Scholar] [CrossRef]
- Bertl, M. News analysis for the detection of cyber security issues in digital healthcare: A text mining approach to uncover actors, attack methods and technologies for cyber defense. Young Inf. Sci. 2019, 4, 1–15. [Google Scholar]
- Jalali, M.S.; Razak, S.; Gordon, W.; Perakslis, E.; Madnick, S. Health care and cybersecurity: Bibliometric analysis of the literature. J. Med. Internet Res. 2019, 21, e12644. [Google Scholar] [CrossRef]
- Kelly, B.S.; Quinn, C.; Belton, N.; Lawlor, A.; Killeen, R.P.; Burrell, J. Cybersecurity considerations for radiology departments involved with artificial intelligence. Eur. Radiol. 2023, 33, 8833–8841. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D. Advancing the cybersecurity of the healthcare system with self-optimising and self-adaptative artificial intelligence (part 2). Health Technol. 2022, 12, 923–929. [Google Scholar] [CrossRef]
- Klonoff, A.N.; Lee, W.-A.; Xu, N.Y.; Nguyen, K.T.; DuBord, A.; Kerr, D. Six digital health technologies that will transform diabetes. J. Diabetes Sci. Technol. 2023, 17, 239–249. [Google Scholar] [CrossRef]
- Chintala, S. Data Privacy and Security Challenges in AI-Driven Healthcare Systems in India. J. Data Acquis. Process. 2022, 37, 2769–2778. [Google Scholar]
- Tan, T.F.; Thirunavukarasu, A.J.; Jin, L.; Lim, J.; Poh, S.; Teo, Z.L.; Ang, M.; Chan, R.V.P.; Ong, J.; Turner, A.; et al. Artificial intelligence and digital health in global eye health: Opportunities and challenges. Lancet Glob. Health 2023, 11, e1432–e1443. [Google Scholar] [CrossRef] [PubMed]
- Arafa, A.; Sheerah, H.A.; Alsalamah, S. Emerging digital technologies in healthcare with a spotlight on cybersecurity: A narrative review. Information 2023, 14, 640. [Google Scholar] [CrossRef]
- Vaghela, A.; Shah, V. Cybersecurity Infrastructure and Solutions for Healthcare Systems. In AI and IoT Technology and Applications for Smart Healthcare Systems; Auerbach Publications: Boca Raton, FL, USA, 2024; pp. 358–369. [Google Scholar]
- Messinis, S.; Temenos, N.; Protonotarios, N.E.; Rallis, I.; Kalogeras, D.; Doulamis, N. Enhancing Internet of Medical Things Security with Artificial Intelligence: A Comprehensive Review. Comput. Biol. Med. 2024, 170, 108036. [Google Scholar] [CrossRef]
- Vaisakhkrishnan, K.; Ashok, G.; Mishra, P.; Kumar, T.G. Guarding Digital Health: Deep Learning for Attack Detection in Medical IoT. Procedia Comput. Sci. 2024, 235, 2498–2507. [Google Scholar] [CrossRef]
- Ksibi, S.; Jaidi, F.; Bouhoula, A. A comprehensive study of security and cyber-security risk management within e-Health systems: Synthesis, analysis and a novel quantified approach. Mob. Netw. Appl. 2023, 28, 107–127. [Google Scholar] [CrossRef]
- Thomasian, N.M.; Adashi, E.Y. Cybersecurity in the internet of medical things. Health Policy Technol. 2021, 10, 100549. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.; Liyanage, M. Mec-enabled 5g use cases: A survey on security vulnerabilities and countermeasures. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Musbahi, O.; Syed, L.; Le Feuvre, P.; Cobb, J.; Jones, G. Public patient views of artificial intelligence in healthcare: A nominal group technique study. Digit. Health 2021, 7, 20552076211063682. [Google Scholar] [CrossRef]
- Ramasamy, L.K.; Khan, F.; Shah, M.; Prasad, B.V.V.S.; Iwendi, C.; Biamba, C. Secure smart wearable computing through artificial intelligence-enabled internet of things and cyber-physical systems for health monitoring. Sensors 2022, 22, 1076. [Google Scholar] [CrossRef]
- Ameen, A.H.; Mohammed, M.A.; Rashid, A.N. Dimensions of artificial intelligence techniques, blockchain, and cyber security in the Internet of medical things: Opportunities, challenges, and future directions. J. Intell. Syst. 2023, 32, 20220267. [Google Scholar] [CrossRef]
- Miriam, D.D.H.; Dahiya, D.; Nitin; Robin, C.R.R. Secured Cyber Security Algorithm for Healthcare System Using Blockchain Technology. Intell. Autom. Soft Comput. 2023, 35, 1889–1906. [Google Scholar] [CrossRef]
- Gupta, L.; Salman, T.; Ghubaish, A.; Unal, D.; Al-Ali, A.K.; Jain, R. Cybersecurity of multi-cloud healthcare systems: A hierarchical deep learning approach. Appl. Soft Comput. 2022, 118, 108439. [Google Scholar] [CrossRef]
- Ikharo, B.; Obiagwu, A.; Obasi, C.; Hussein, S.U.; Akah, P. Security for Internet-of-Things Enabled E-Health using Blockchain and Artificial Intelligence: A Novel Integration Framework. In Proceedings of the 2021 1st International Conference on Multidisciplinary Engineering and Applied Science (ICMEAS), Abuja, Nigeria, 15–16 July 2021; pp. 1–4. [Google Scholar]
- Alshehri, M. Blockchain-assisted cyber security in medical things using artificial intelligence. Electron. Res. Arch. 2023, 31, 708–728. [Google Scholar] [CrossRef]
- Mukhopadhyay, A.; Jain, S. A framework for cyber-risk insurance against ransomware: A mixed-method approach. Int. J. Inf. Manag. 2024, 74, 102724. [Google Scholar] [CrossRef]
- Hubbard, D.C.; Cox, P.; Redd, T.K. Assistive applications of artificial intelligence in ophthalmology. Curr. Opin. Ophthalmol. 2023, 34, 261–266. [Google Scholar] [CrossRef] [PubMed]
- de Belen, R.A.J.; Bednarz, T.; Favero, D.D. Integrating mixed reality and internet of things as an AT for elderly people living in a smart home. In Proceedings of the 17th International Conference on Virtual-Reality Continuum and Its Applications in Industry, Brisbane, QLD, Australia, 14–16 November 2019; pp. 1–2. [Google Scholar]
- Arshad, N.I.; Hashim, A.S.; Ariffin, M.M.; Aszemi, N.M.; Low, H.M.; Norman, A.A. Robots as AT tools to enhance cognitive abilities and foster valuable learning experiences among young children with autism spectrum disorder. IEEE Access 2020, 8, 116279–116291. [Google Scholar] [CrossRef]
- Thapliyal, M.; Ahuja, N.J. Underpinning implications of instructional strategies on AT for learning disability: A meta-synthesis review. Disabil. Rehabil. Assist. Technol. 2021, 18, 423–431. [Google Scholar] [CrossRef]
- Marmo, R. Artificial Intelligence in E-Learning Systems. In Encyclopedia of Data Science and Machine Learning; IGI Global: Hershey, PA, USA, 2023; pp. 1531–1545. [Google Scholar]
- de Freitas, M.P.; Piai, V.A.; Farias, R.H.; Fernandes, A.M.; de Moraes Rossetto, A.G.; Leithardt, V.R.Q. Artificial Intelligence of Things Applied to AT: A Systematic Literature Review. Sensors 2022, 22, 8531. [Google Scholar] [CrossRef] [PubMed]
- Cai, Y.; Clinto, M.; Xiao, Z. Artificial Intelligence AT in Hospital Professional Nursing Technology. J. Healthc. Eng. 2021, 2021, 1721529. [Google Scholar] [CrossRef]
- Nayak, S.; Das, R.K. Application of artificial intelligence (AI) in prosthetic and orthotic rehabilitation. In Service Robotics; IntechOpen: London, UK, 2020. [Google Scholar]
- Wei, S.; Huang, P.; Li, R.; Liu, Z.; Zou, Y. Exploring the application of artificial intelligence in sports training: A case study approach. Complexity 2021, 2021, 4658937. [Google Scholar] [CrossRef]
- Abdi, S.; Kitsara, I.; Hawley, M.S.; de Witte, L.P. Emerging technologies and their potential for generating new assistive technologies. Assist. Technol. 2021, 33 (Suppl. S1), 17–26. [Google Scholar] [CrossRef]
- Pivato, C.A.; Inversetti, A.; Condorelli, G.; Chieffo, A.; Levi-Setti, P.E.; Latini, A.C.; Busnelli, A.; Messa, M.; Cristodoro, M.; Bragato, R.M.; et al. Cardiovascular safety of assisted reproductive technology: A meta-analysis. Eur. Heart J. 2025, 46, 687–698. [Google Scholar] [CrossRef]
- Wang, K.; Tan, B.; Wang, X.; Qiu, S.; Zhang, Q.; Wang, S.; Yen, Y.T.; Jing, N.; Liu, C.; Chen, X.; et al. Machine learning-assisted point-of-care diagnostics for cardiovascular healthcare. Bioeng. Transl. Med. 2025, 10, e70002. [Google Scholar] [CrossRef]
- Harskamp, R.E.; De Clercq, L. Performance of ChatGPT as an AI-assisted decision support tool in medicine: A proof-of-concept study for interpreting symptoms and management of common cardiac conditions (AMSTELHEART-2). Acta Cardiol. 2024, 79, 358–366. [Google Scholar] [CrossRef]
- Nagrale, M.; Pol, R.S.; Birajadar, G.B.; Mulani, A.O.; Kutubuddin, K.; Liyakat, S. Internet of robotic things in cardiac surgery: An innovative approach. Afr. J. Biol. Sci. 2024, 6, 709–725. [Google Scholar]
- Roy, M.; Barui, S.; Ghosh, A.; Bhattacharjee, S.; Majumdar, A.; Datta, A.; Sadhukhan, D. Assistive Smart Stick: Safe and Independent Mobility for the Visually Disabled Using Sensor Based Technology. In Proceedings of the 2025 AI-Driven Smart Healthcare for Society 5.0, Kolkata, India, 14–15 February 2025; pp. 1–6. [Google Scholar]
- Shashanka, R.; Devi, A.; Gowda, K.L.; Kushal, S.; Kumar, V.R. VisioGuide: An AI for Visually Impaired. In Proceedings of the 2025 4th International Conference on Sentiment Analysis and Deep Learning (ICSADL), Bhimdatta, Nepal, 18–20 February 2025; pp. 1084–1090. [Google Scholar]
- Okolo, G.I.; Althobaiti, T.; Ramzan, N. Smart Assistive Navigation System for Visually Impaired People. J. Disabil. Res. 2025, 4, 20240086. [Google Scholar] [CrossRef]
- Clinical Services Journal. Quantum Research Hub for Healthcare Is Launched. 2024. Available online: https://clinicalservicesjournal.com/story/46904/quantum-research-hub-for-healthcare-is-launched (accessed on 6 March 2024).
- Meikandan, P.V.; Upama, P.B.; Rabbani, M.; Ahamad, M.M.; Ahamed, S.I. Quantum computing for smart healthcare. In Sensor Networks for Smart Hospitals; Elsevier: Amsterdam, The Netherlands, 2025; pp. 525–534. [Google Scholar]
- Osaba, E.; Villar-Rodriguez, E.; Oregi, I. A systematic literature review of quantum computing for routing problems. IEEE Access 2022, 10, 55805–55817. [Google Scholar] [CrossRef]
- Dankan Gowda, V.; Rajalakshmi, J.; Guruprakash, B.; Hariram, V.; Prasad, K.D.V. Integrating IoT, Blockchain, and Quantum Machine Learning: Advancing Multimodal Data Fusion in Healthcare AI. In Multimodal Data Fusion for Bioinformatics Artificial Intelligence; Wiley: Hoboken, NJ, USA, 2025; pp. 103–126. [Google Scholar]
- Sonavane, A.; Jaiswar, S.; Mistry, M.; Aylani, A.; Hajoary, D. Quantum machine learning models in healthcare: Future trends and challenges in healthcare. In Quantum Computing for Healthcare Data; Elsevier: Amsterdam, The Netherlands, 2025; pp. 167–187. [Google Scholar]
- Gupta, R.S.; Wood, C.E.; Engstrom, T.; Pole, J.D.; Shrapnel, S. Quantum machine learning for digital health? A systematic review. arXiv 2024, arXiv:2410.02446. [Google Scholar] [CrossRef] [PubMed]
- Yuksel Elgin, C. Democratizing Glaucoma Care: A Framework for AI-Driven Progression Prediction Across Diverse Healthcare Settings. J. Ophthalmol. 2025, 2025, 9803788. [Google Scholar] [CrossRef]
- Lakshmi, B.; Sarath, K.; Kumar, K.P.V.; Praveen, G.; Karthik, B.; Bhushan, Y.P. Fuzzy Expert System to Diagnose the Heart Disease Risk Level. In Artificial Intelligence and Cybersecurity in Healthcare; Wiley: Hoboken, NJ, USA, 2025; pp. 273–288. [Google Scholar]
- Menon, U.V.; Kumaravelu, V.B.; Kumar, C.V.; Rammohan, A.; Chinnadurai, S.; Venkatesan, R.; Hai, H.; Selvaprabhu, P. AI-Powered IoT: A Survey on Integrating Artificial Intelligence with IoT for Enhanced Security, Efficiency, and Smart Applications. IEEE Access 2025, 13, 50296–50339. [Google Scholar]
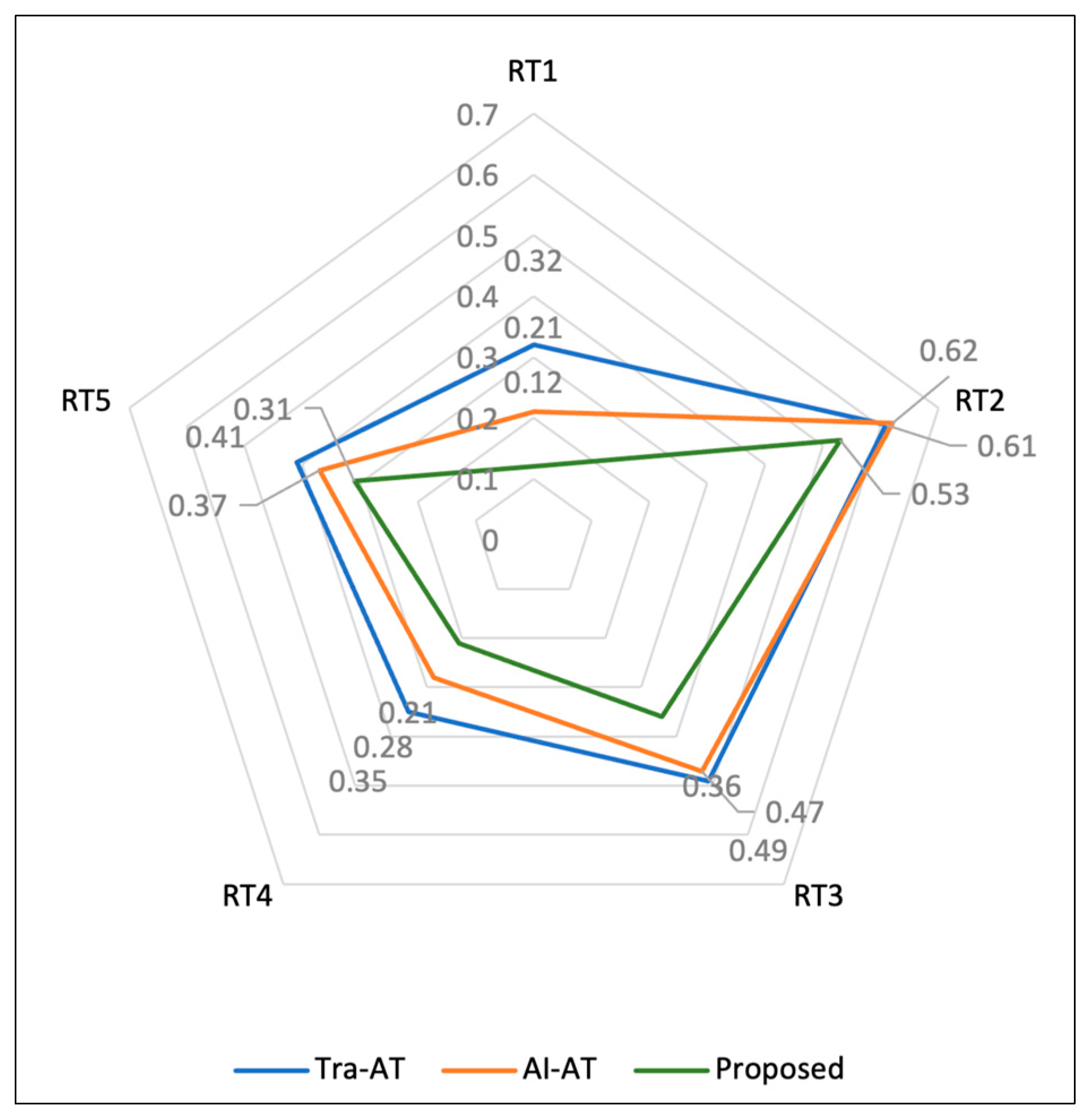
| Without Any Risks | With Various Risks | ||||
|---|---|---|---|---|---|
| Use of AT Tools | Diagnosing Symptoms on Time | Use of HealthcarePolicies | Securing Healthcare | Relying on Power and EE | |
| Digital healthcare (medical) | 1 (ii) | 2 (i) | 3 (ii) | 4 (iii) | 5 (i) |
| Digital healthcare (admin) | 6 (i) | 7 (ii) | 8 (i) | 9 (i) | 10 (ii) |
| Security Parameters for AT Users | Severity Levels of Blindness | |||||
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| Patients’ service failure | Small | Social care (ii) | Assistive System (iii) | Residential care (i) | Vision clinic care (iii) | E-learning care (ii) |
| Medium | Use of the latest tools (i) | Mobility training (i) | Use of AT (iii) | Support with training (i) | Paralympic care (iii) | |
| Maintenance issues of AT (RT1) | Software (ii) | Hardware (iii) | Network issues (ii) | Maintainability (i) | Accessing e-learning (ii) | |
| Use of AI-based eyeglasses (RT2) | Short-sighted (ii) | Long sighted (ii) | Blurry eye (iii) | Permanent eye disease (iii) | Blindness (iii) | |
| Health and safety compliance (RT3) | Reliability (i) | Privacy (ii) | Safeguarding (i) | Health policies (ii) | Physical attacks (iii) | |
| Food safety regulations (RT4) | Warm (ii) | Mild (i) | Cold (ii) | Hot (iii) | Pollen (iii) | |
| Technological obsolescence (RT5) | Internal (i) | Emerging (ii) | External (iii) | Internet (iii) | Advanced (iii) | |
| Digital Healthcare Sources | Remarks of the Results | Methods for Ransomware Risks | |
|---|---|---|---|
| Contributions | Limitations | ||
| Biosensors | Offering secure communication between patients and doctors | Restricted with applications that leads to data breaches | Assessment with malicious intruder |
| Healthcare data | Investigating health risks quickly and accurately | Real-time data handling for proactive issues | AI-based security algorithms in mitigation |
| IoT devices | Handling remote and secure healthcare issues | Wireless risks in IoT networks linked with external devices | Mitigation |
| Assistive users | Availability of digital healthcare information, including e-learning with AT | Privacy of sensitive data should be ensured. | Assessment and phishing attacks |
| Energy | Providing secure power to all digital healthcare devices | High latency and delays experienced during operation | Quantification with AI-based cybersecurity |
| Variables | Risk Types of AT in Digital Health | Likelihood | Impact | Risk for 1 Sample |
|---|---|---|---|---|
| Critical industry (CI) | AT developers | High | Low | 4 × 2 = 8 |
| Organization size (Size) | Number of staff and AT users in any organizations | Medium | None | 3 × 1 = 3 |
| Digital intensity (DI) | AT users’ big data | Very high | Low | 5 × 2 = 10 |
| Network segmentation (NS) | Communication network of AT users | High | Low | 4 × 2 = 8 |
| Attack vector (AV) | Infrastructure with cyberattacks | Very low | Medium | 1 × 3 = 3 |
| Privileges required (PR) | Priorities of AT in digital health | Low | Critical | 2 × 5 = 10 |
| Attack complexity (AC) | IoT sensors network in AT applications | Medium | Low | 3 × 2 = 6 |
| User interaction (UI) | Availability of AT users in peak time | Very high | High | 5 × 4 = 20 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Algarni, A.M.; Thayananthan, V. Cybersecurity for Analyzing Artificial Intelligence (AI)-Based Assistive Technology and Systems in Digital Health. Systems 2025, 13, 439. https://doi.org/10.3390/systems13060439
Algarni AM, Thayananthan V. Cybersecurity for Analyzing Artificial Intelligence (AI)-Based Assistive Technology and Systems in Digital Health. Systems. 2025; 13(6):439. https://doi.org/10.3390/systems13060439
Chicago/Turabian StyleAlgarni, Abdullah M., and Vijey Thayananthan. 2025. "Cybersecurity for Analyzing Artificial Intelligence (AI)-Based Assistive Technology and Systems in Digital Health" Systems 13, no. 6: 439. https://doi.org/10.3390/systems13060439
APA StyleAlgarni, A. M., & Thayananthan, V. (2025). Cybersecurity for Analyzing Artificial Intelligence (AI)-Based Assistive Technology and Systems in Digital Health. Systems, 13(6), 439. https://doi.org/10.3390/systems13060439





