Application of Systems-of-Systems Theory to Electromagnetic Warfare Intentional Electromagnetic Interference Risk Assessment
Abstract
1. Introduction
2. Literature Review: EW IEMI RA and SoS
2.1. Electromagnetic Spectrum Operations and EW
“Military actions to exploit, attack, protect, and manage the electromagnetic operating environment”.[5]
2.2. Applicability of SoS to EW IEMI RA and Critical Analysis of SoS Types
“A set of systems or system elements that interact to provide a unique capability that none of the constituent systems can accomplish independently. Note 1 to entry: Systems elements can be necessary to facilitate the interaction of the constituent systems in the systems of systems”.[16]
- “The attractiveness of SoS architectures descends from the fact that the SoS collective behavior can achieve goals that would be infeasible by having the constituent systems working in isolation”.
- “In the literature such collective goals are referred to as the SoS missions”.
- “Explicitly identifying and modelling a SoS mission may provide key guidance for SoS design and validation”.
- “A mission conceptual model can help in representing and relating the main elements of the SoS emergent behavior”
- Directed: built and managed to fulfil specific purposes;
- Acknowledged: recognized objectives, and designated management and resources (but constituent systems retain independence);
- Collaborative: no central management with coercive power—elements collaborate voluntarily;
- Virtual: no central management or purposes. Exists deliberately or accidentally (SoS behavior emerges, via informal elemental collaboration & individual element management).
2.3. Harm Identification and Risk Assessment
3. Methodology
3.1. Description of the QRAM
3.2. Case Study Based Approach for the Critical Analysis of the Proposed SoS Type
4. Case Study: EW IEMI QRAM Using an SoS-Derived Model
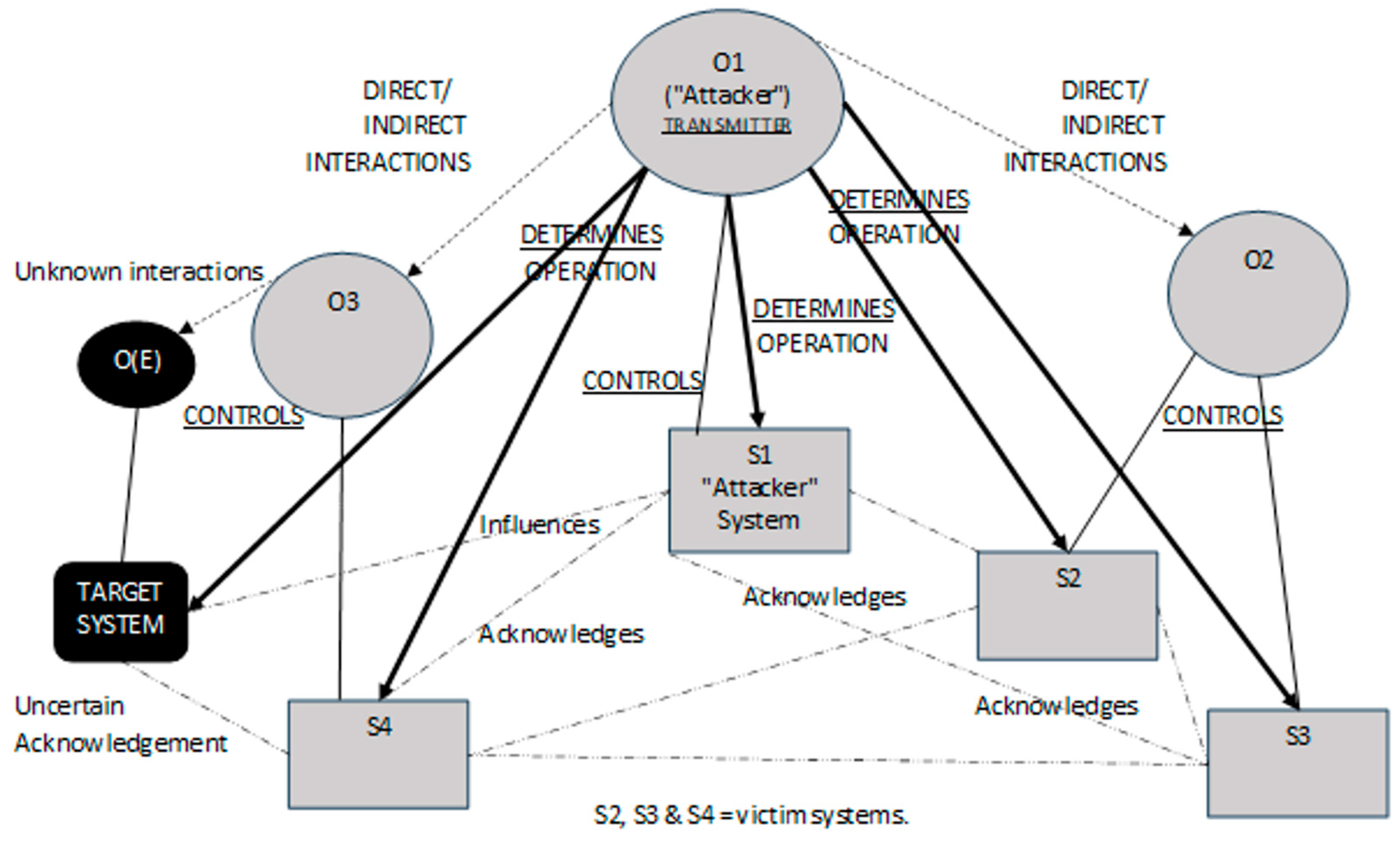
4.1. Description of the Scenario
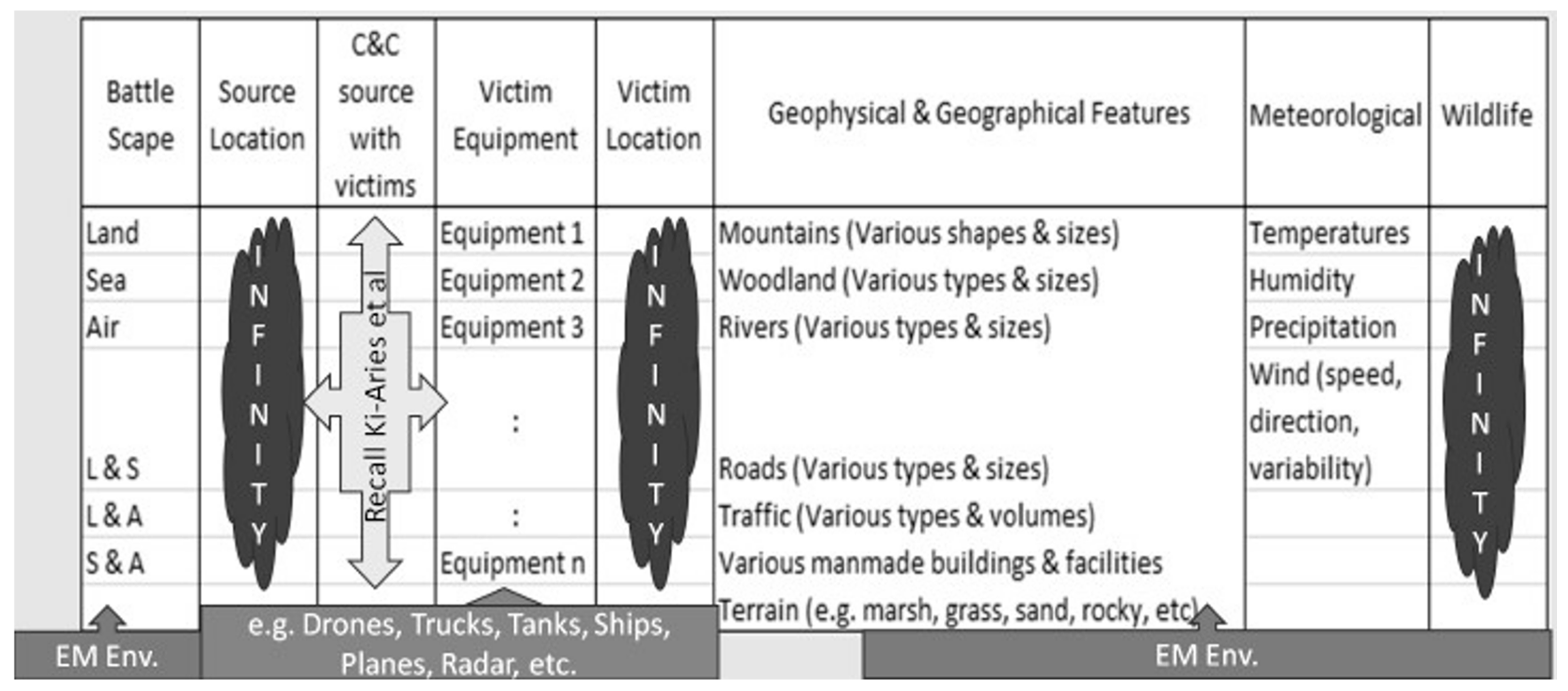
4.2. Data and SoS Elements
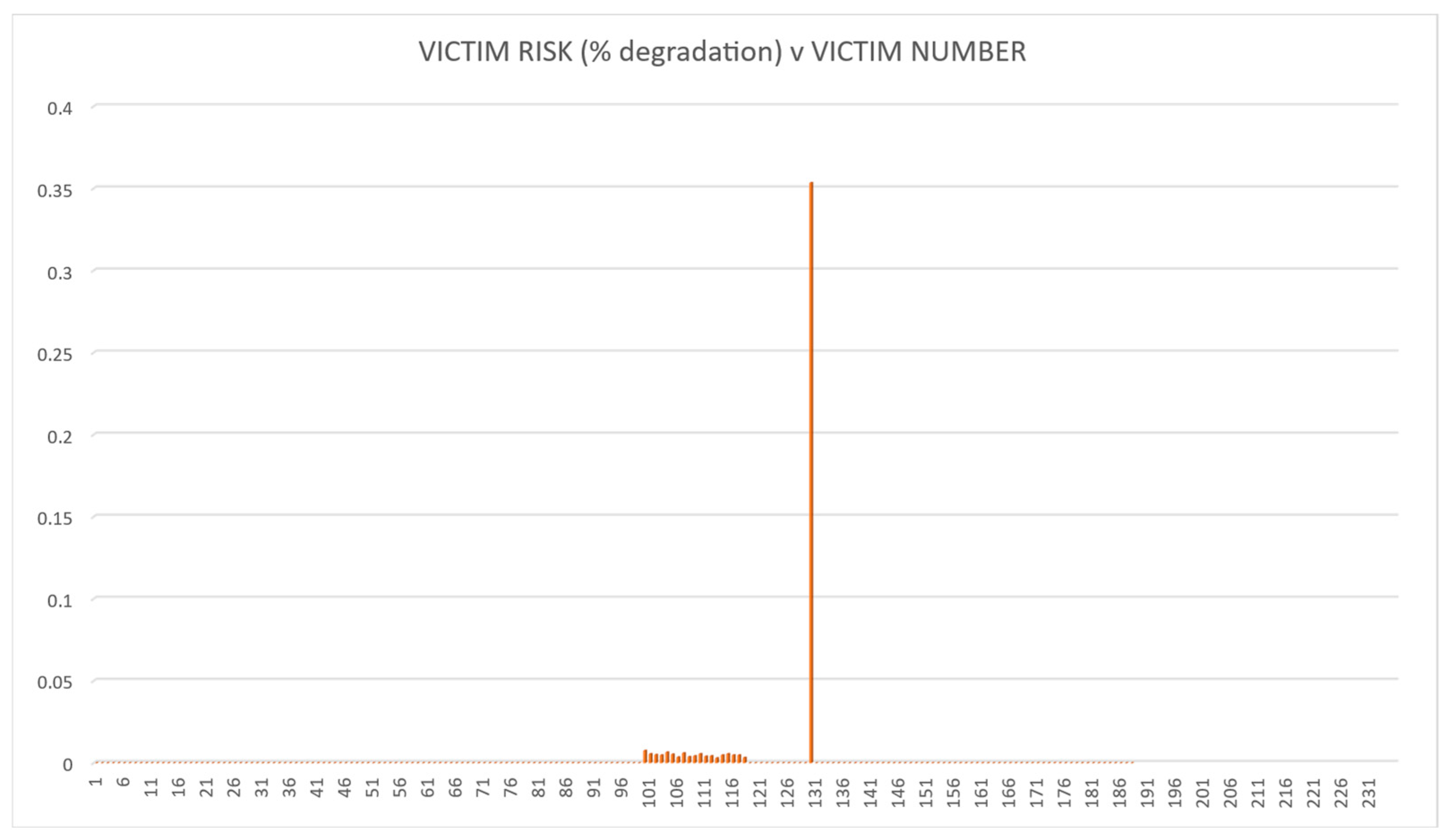
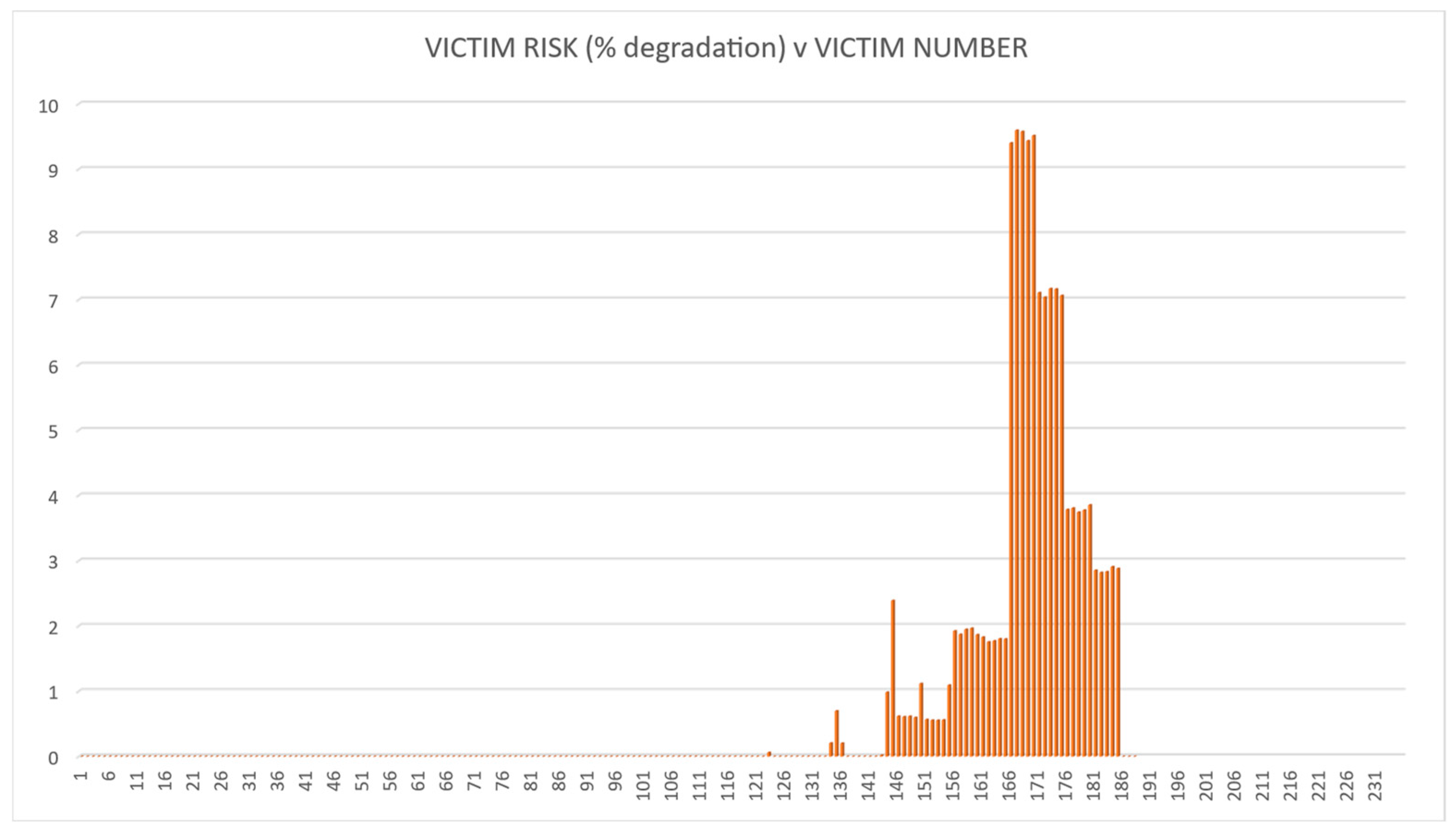
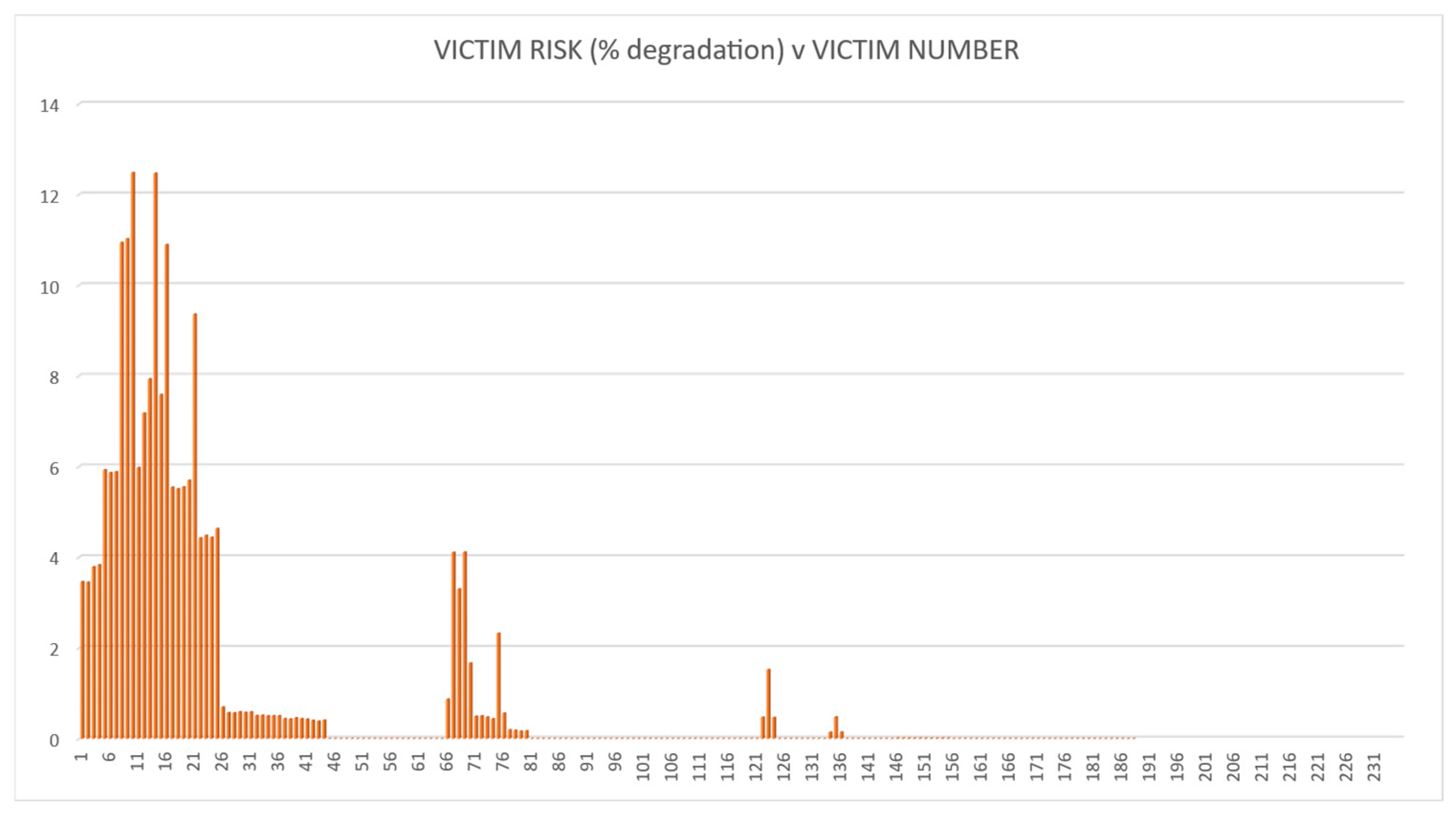
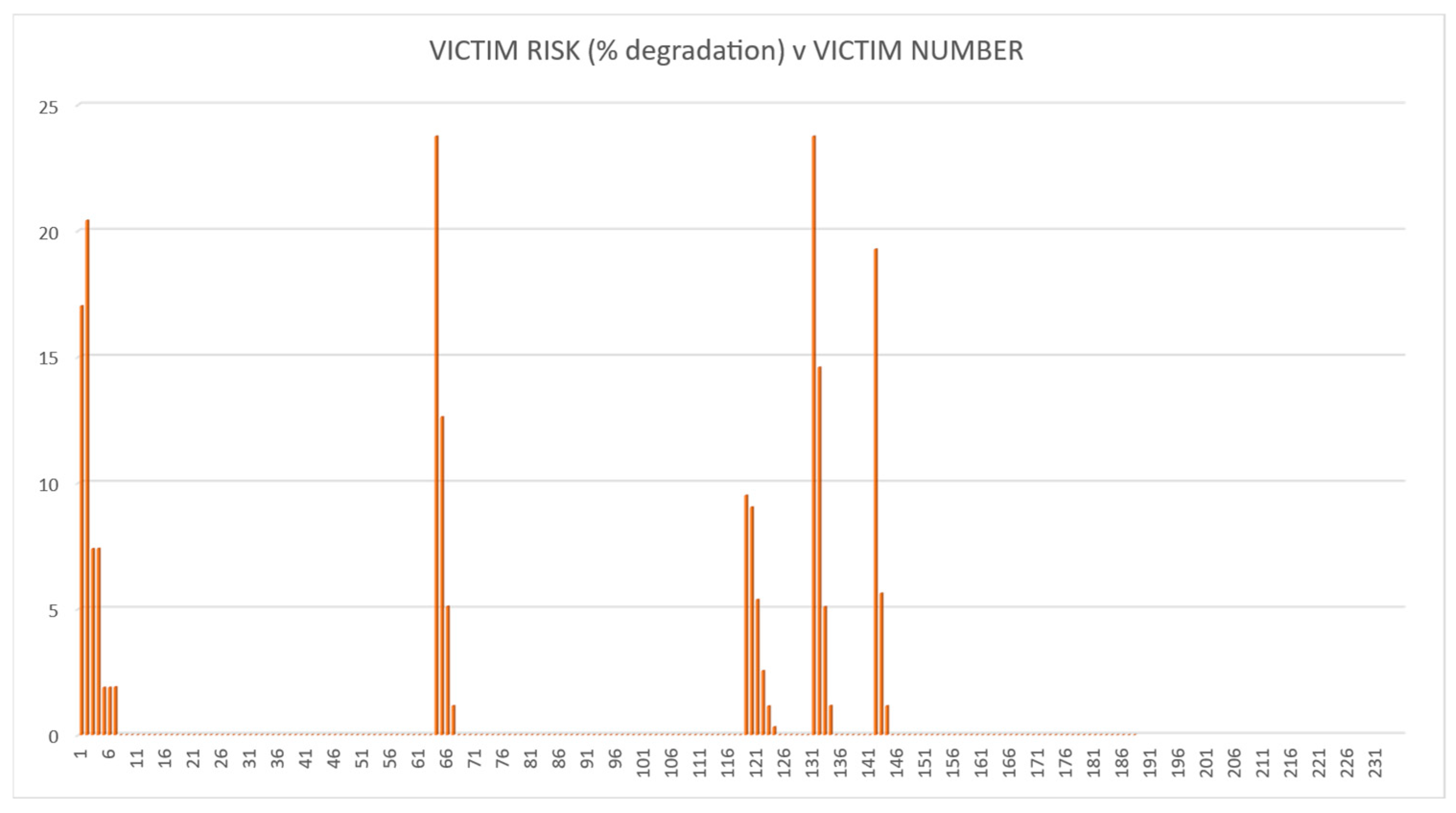
4.3. Results, Validation and Verification
5. Discussion
5.1. Relevance to SoS Types
“SoS factors & concepts suitable for eliciting, analyzing, validating security risks using tool-support within the SoS context”.
“alignment with a tool such as CAIRIS provides many benefits for translating operational needs into requirements”.
- Dynamic evolution of the SoS (changing characteristics of victims).
- Changing interoperability needs related to individual victim systems.
- Compounding emergent behaviors within the SoS (i.e., new victim interactions).
5.2. EMSO
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Giri, D.V.; Tesche, F.M. Classification of intentional electromagnetic environments (IEMI). IEEE Trans. Electromagn. Compat. 2004, 46, 322–328. [Google Scholar]
- Radasky, W.A.; Baum, C.A.; Wik, M.W. Introduction to the special issue on high-power electromagnetics (HPEM) and intentional electromagnetic interference (IEMI). IEEE Trans. Electromagn. Compat. 2004, 46, 314–321. [Google Scholar] [CrossRef]
- Sabath, F. What can be learned from documented intentional electromagnetic interference (IEMI) attacks? In Proceedings of the 2011 31th URSI General Assembly and Scientific Symposium, Istanbul, Turkiye, 13–20 August 2011. [Google Scholar]
- Genender, E.; Mleczko, M.; Döring, O.; Garbe, H.; Potthast, S. Fault tree analysis for system modeling in case of intentional EMI. Adv. Radio Science 2011, 9, 297–302. [Google Scholar]
- EMSOPEDIA Electro Magnetic Spectrum Operation (EMSO). Available online: https://www.emsopedia.org/entries/electro-magnetic-spectrum-operation-emso/ (accessed on 2 December 2024).
- HQ Department of the Army. Techniques for Spectrum Management Operations, ATP 6-02.70; HQ Department of the Army: Washington, DC, USA, 2015. [Google Scholar]
- O’Donohue, D. Joint Electromagnetic Spectrum Operations. Joint Publication 3-85; U.S. Department of the Army: Washington, DC, USA, 2022. [Google Scholar]
- Crawley, F.; Tyler, B. Hazard Identification Methods; Institute of Chemical Engineers: Rugby, UK, 2003. [Google Scholar]
- Deshmukh, L.M. Industrial Safety Management: Hazard Identification and Risk Control; McGraw-Hill Education LLC: New York, NY, USA, 2005. [Google Scholar]
- Mannan, S. Lees’ Process Safety Essentials: Hazard Identification, Assessment and Control; Butterworth-Heinemann: Amsterdam, The Netherlands, 2014. [Google Scholar]
- British Standard BS: IEC61882:2016 Hazard and Operability Studies (HAZOP Studies)—Application Guide. Available online: https://shop.bsigroup.com/ProductDetail/?pid=000000000030309555 (accessed on 29 January 2024).
- IEC 60812:2018 Failure Modes and Effects Analysis (FMEA and FMECA). Available online: https://webstore.iec.ch/publication/26359 (accessed on 29 January 2024).
- IEC61025:2006 Fault Tree Analysis (FTA). Available online: https://webstore.iec.ch/publication/4311 (accessed on 29 January 2024).
- IEC 62502:2010 Analysis Techniques for Dependability—Event Tree Analysis (ETA). Available online: https://webstore.iec.ch/publication/7131 (accessed on 29 January 2024).
- UK Civil Aviation Authority. Introduction to Bowtie. Available online: https://www.caa.co.uk/Safety-initiatives-and-resources/Working-with-industry/Bowtie/About-Bowtie/Introduction-to-bowtie/ (accessed on 29 January 2024).
- ISO/IEC/IEEE 21839:2019 Systems and Software Engineering—System of Systems (SoS) Considerations in Life Cycle Stages of a System. Available online: https://www.iso.org/obp/ui/#iso:std:iso-iec-ieee:21839:ed-1:v1:en (accessed on 2 December 2024).
- Pan, X.; Wang, H.; Yang, Y.; Zhang, G. Resilience based importance measure analysis for SoS. J. Syst. Eng. Electron. 2019, 30, 920–930. [Google Scholar]
- Olivero, M.A.; Bertolino, A.; Dominguez-Mayo, F.J.; Escalona, M.J.; Matteucci, I. Security Assessment of Systems of Systems. In Proceedings of the IEEE/ACM 7th International Workshop on Software Engineering for Systems-of-Systems (SESoS) and 13th Workshop on Distributed Software Development, Software Ecosystems and Systems-of-Systems (WDES), Montreal, QC, Canada, 28 May 2019; pp. 62–65. [Google Scholar]
- Silva, E.; Batista, T.; Oquendo, F. A mission-oriented approach for designing system-of-systems. In Proceedings of the 10th SoSE Conference, San Antonio, TX, USA, 17–20 May 2015; pp. 346–351. [Google Scholar] [CrossRef]
- Chiprianov, V.; Falkner, K.; Gallon, L.; Munier, M. Towards modelling and analysing non-functional properties of systems of systems. In Proceedings of the 9th Int. Conference on SOSE, Adelaide, Australia, 9–13 June 2014; pp. 289–294. [Google Scholar]
- Ki-Aries, D. Security Risk Assessment in Systems of Systems. Ph.D. Thesis, Bournemouth University, Bournemouth, UK, 2020. [Google Scholar]
- Systems of Systems Characterization and Types, Dr. Judith S. Dahmann, (STO-EN-SCI-276). Available online: https://www.sto.nato.int/publications/STO%20Educational%20Notes/STO-EN-SCI-276/EN-SCI-276-01.pdf (accessed on 2 December 2024).
- Moon, D.C.; Moon, J.; Keagy, A. Direct and Indirect Interactions. Nat. Educ. Knowl. 2010, 3, 50. [Google Scholar]
- Xiao, Y.; Watson, M. Guidance on Conducting a Systematic Literature Review. J. Plan. Educ. Res. 2019, 39, 93–112. [Google Scholar]
- PRISMA. Welcome to the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) Website. Available online: http://prisma-statement.org/ (accessed on 2 December 2024).
- Fourie, W. Leadership and risk: A review of the literature. Leadersh. Organ. Dev. J. 2022, 43, 550–562. [Google Scholar] [CrossRef]
- Shukla, A.; Katt, B.; Nweke, L.O.; Yeng, P.K.; Weldehawaryat, G.K. System security assurance: A systematic literature review. Comput. Sci. Rev. 2022, 45, 100496. [Google Scholar] [CrossRef]
- Syafitri, W.; Shukur, Z.; Mokhtar, A.U.; Sulaiman, R.; Ibrahim, M.A. Social Engineering Attacks Prevention: A Systematic Literature Review. IEEE Access 2022, 10, 39325–39343. [Google Scholar] [CrossRef]
- Alouffi, B.; Hasnain, M.; Alharbi, A.; Alsosaimi, W.; Alyami, H.; Ayaz, M. A Systematic Literature Review on Cloud Computing Security: Threats and Mitigation Strategies. IEEE Access 2021, 9, 57792–57807. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar]
- Lisova, E.; Šljivo, I.; Čaušević, A. Safety and Security Co-Analyses: A Systematic Literature Review. IEEE Syst. J. 2019, 13, 2189–2200. [Google Scholar]
- Nelson, B.; Olovsson, T. Security and Privacy for Big Data: A Systematic Literature Review. In Proceedings of the 2016 IEEE International Conference on Big Data (Big Data), Washington, DC, USA, 5–8 December 2016; pp. 3693–3702. [Google Scholar]
- Harvard Countway Library. Systematic Reviews and Meta Analysis. Available online: https://guides.library.harvard.edu/meta-analysis/GettingStarted (accessed on 29 January 2024).
- Bournemouth University. Systematic Reviews—Searching for Literature: Introduction. Available online: https://libguides.bournemouth.ac.uk/c.php?g=471700&p=3225871 (accessed on 29 January 2024).
- Mao, C.; Canavero, F. System-Level Vulnerability Assessment for EME: From Fault Tree Analysis to Bayesian Networks-Part I: Methodology Framework. IEEE Trans. Electromagn. Compat. 2016, 58, 180–187. [Google Scholar]
- Genender, E.; Garbe, H.; Sabath, F. Probabilistic risk analysis technique of intentional electromagnetic interference at system level. IEEE Trans. Electromagn. Compat. 2014, 56, 200–207. [Google Scholar]
- Liu, Y.; Du, P.; Han, F.; Xia, H.; Wang, J. A Bayesian Estimation of Confidence Limits for Multi-state System Vulnerability Assessment With IEMI. IEEE Trans. Electromagn. Compat. 2022, 64, 1219–1229. [Google Scholar]
- Liu, Y.; Han, F.; Wang, J.; Qi, H. Vulnerability assessment of a multistate component for IEMI based on a Bayesian method. IEEE Trans. Electromagn. Compat. 2019, 61, 467–475. [Google Scholar] [CrossRef]
- Houret, T.; Besnier, P.; Vauchamp, S.; Pouliguen, P. Probability of Failure Using the Kriging-Controlled Stratification Method and Statistical Inference. In Proceedings of the 2020 International Symposium on Electromagnetic Compatibility—EMC EUROPE, EMC EUROPE 2020, Online, 23–25 September 2020; p. 9245860. [Google Scholar]
- Sabath, F. EMI risk management with the threat scenario, effect, and criticality analysis. In Ultra-Wideband Short-Pulse Electromagnetics; Springer: New York, NY, USA, 2014; Volume 10, pp. 265–278. [Google Scholar]
- Mondal, S.K.; Tan, T.; Khanam, S.; Kabir, H.M.D.; Ni, K. Security Quantification of Container-Technology-Driven E-Government Systems. Electronics 2023, 12, 1238. [Google Scholar] [CrossRef]
- Peikert, T.; Garbe, H.; Potthast, S. A fuzzy approach for IEMI risk analysis of IT-Systems with respect to transient disturbances. In Proceedings of the IEEE International Symposium on Electromagnetic Compatibility, Dresden, Germany, 16–22 August 2015; pp. 1077–1082. [Google Scholar]
- Peikert, T.; Garbe, H.; Potthast, S. Risk analysis with a fuzzy-logic approach of a complex installation. Adv. Radio Sci. 2016, 14, 91–96. [Google Scholar]
- Peikert, T.; Garbe, H.; Potthast, S. Fuzzy-Based Risk Analysis for IT-Systems and Their Infrastructure. IEEE Trans. Electromagn. Compat. 2017, 59, 1294–1301. [Google Scholar]
- Liwang, H.; Ericson, M.; Bang, M. An examination of the implementation of risk-based approaches in military operations. J. Mil. Stud. 2014, 5, 38–64. [Google Scholar]
- Paltrinieria, N.; Comfort, L.; Reneirs, G. Learning about risk: Machine learning for risk assessment. Saf. Sci. 2019, 118, 475–486. [Google Scholar] [CrossRef]
- Pasman, J.; Rogers, W.J.; Mannan, M.S. Risk assessment: What is it worth? Shall we just do away with it, or can it do a better job? Saf. Sci. 2017, 99, 140–155. [Google Scholar]
- Rawson, A.; Brito, M.; Sabeur, Z.; Tran-Thanh, L. From Conventional to Machine Learning Methods for Maritime Risk Assessment. Int. J. Mar. Navig. Saf. Sea Transp. 2021, 15, 757–764. [Google Scholar] [CrossRef]
- Choi, S.; Kwon, O.-J.; Oh, H.; Shin, D. Method for effectiveness assessment of electronic warfare systems in cyberspace. Symmetry 2020, 12, 2107. [Google Scholar] [CrossRef]
- Devaraj, L.; Ruddle, A.R.; Duffy, A.P. EMI Risk Estimation for System-Level Functions Using Probabilistic Graphical Models. In Proceedings of the Joint IEEE International Symposium on Electromagnetic Compatibility Signal and Power Integrity, and EMC Europe, EMC/SI/PI/EMC Europe 2021, Virtual, 26 July–20 August 2021; pp. 851–856. [Google Scholar]
- Mansson, D.; Thottappillil, R.; Backstrom, M. Methodology for classifying facilities with respect to intentional EMI. IEEE Trans. Electromagn. Compat. 2009, 51, 46–52. [Google Scholar] [CrossRef]
- Ruddle, A.R. Risk Analysis for Automotive EMC: Scope, Approaches and Challenges. In Proceedings of the 2020 International Symposium on Electromagnetic Compatibility—EMC EUROPE 2020, Online, 23–25 September 2020; p. 9245774. [Google Scholar]
- Devaraj, L.; Ruddle, A.R.; Duffy, A.P. System Level Risk Analysis for Immunity in Automotive Functional Safety Analyses. In Proceedings of the 2020 International Symposium on Electromagnetic Compatibility—EMC EUROPE 2020, Online, 23–25 September 2020; p. 9245692. [Google Scholar]
- Li, K.-J.; Xie, Y.-Z.; Chen, Y.-H.; Zhou, Y.; Hui, Y.-C. Bayesian inference for susceptibility of electronics to transient electromagnetic disturbances with failure mechanism Consideration. IEEE Trans. Electromagn. Compat. 2020, 62, 1669–1677. [Google Scholar]
- Zhou, P.; Lv, Y.; Chen, Z.; Xu, H. System-level EMC assessment for military vehicular communication systems based on a modified four-level assessment model. China Commun. 2018, 15, 39–53. [Google Scholar]
- Xu, T.; Chen, Y.; Wang, Y.; Zhang, D.; Zhao, M. EMI Threat Assessment of UAV Data Link Based on Multi-Task CNN. Electronics 2023, 12, 1631. [Google Scholar] [CrossRef]
- Jang, J.; Kim, K.; Yoon, S.; Lee, S.; Ahn, M.; Shin, D. Mission Impact Analysis by Measuring the Effect on Physical Combat Operations Associated with Cyber Asset Damage. IEEE Access 2023, 11, 45113–45128. [Google Scholar]
- Butt, F.A.; Jalil, M. An overview of electronic warfare in radar systems. In Proceedings of the International Conference on Technological Advances in Electrical, Electronics and Computer Engineering, Konya, Turkey, 9–11 May 2013; pp. 213–217. [Google Scholar]
- Howard, C.; Stumptner, M. Probabilistic reasoning techniques for situation assessments. In Proceedings of the 3rd International Conference on Information Technology and Applications, Sydney, NSW, Australia, 4–7 July 2005; pp. 383–386. [Google Scholar]
- Salnikova, O.; Cherviakova, O.; Sova, O.; Zhyvotovskyi, R.; Petruk, S.; Hurskyi, T.; Shyshatskyi, A.; Nos, A.; Neroznak, Y.; Proshchyn, I. Development of an improved method for finding a solution for neuro-fuzzy expert systems. East.-Eur. J. Enterp. Technol. 2020, 5, 35–44. [Google Scholar]
- Sova, O.; Shyshatskyi, A.; Malitskyi, D.; Zhuk, O.; Gaman, O.; Hordiichuk, V.; Fedoriienko, V.; Kokoiko, A.; Shevchuk, V.; Sova, M. Development of a complex method for finding a solution for neuro-fuzzy expert systems. East.-Eur. J. Enterp. Technol. 2020, 6, 22–31. [Google Scholar]
- Taherdoost, H.; Madanchian, M. Multi-Criteria Decision Making (MCDM) Methods and Concepts. Encyclopedia 2023, 3, 77–87. [Google Scholar] [CrossRef]
- Davies, N.; Williams, C.; Osborne, M.; Dogan, H.; Ki-Aries, D.; Jiang, N. Electromagnetic Warfare Intentional Interference: Victim Risk Assessment. IEEE Trans. EMC, 2025; submitted. [Google Scholar]
- de Vries, J.P. An Outline of Risk-Informed Interference Assessment. Available online: https://ssrn.com/abstract=2564213 (accessed on 2 December 2024).
- Ki-Aries, D.; Faily, S.; Dogan, H.; Williams, C. Assessing System of Systems Security Risk and Requirements with OASoSIS. In Proceedings of the IEEE 5th International Workshop on Evolving Security & Privacy Requirements Engineering (ESPRE), Banff, AB, Canada, 20 August 2018; pp. 14–20. [Google Scholar]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Davies, N.; Dogan, H.; Ki-Aries, D. Application of Systems-of-Systems Theory to Electromagnetic Warfare Intentional Electromagnetic Interference Risk Assessment. Systems 2025, 13, 244. https://doi.org/10.3390/systems13040244
Davies N, Dogan H, Ki-Aries D. Application of Systems-of-Systems Theory to Electromagnetic Warfare Intentional Electromagnetic Interference Risk Assessment. Systems. 2025; 13(4):244. https://doi.org/10.3390/systems13040244
Chicago/Turabian StyleDavies, Nigel, Huseyin Dogan, and Duncan Ki-Aries. 2025. "Application of Systems-of-Systems Theory to Electromagnetic Warfare Intentional Electromagnetic Interference Risk Assessment" Systems 13, no. 4: 244. https://doi.org/10.3390/systems13040244
APA StyleDavies, N., Dogan, H., & Ki-Aries, D. (2025). Application of Systems-of-Systems Theory to Electromagnetic Warfare Intentional Electromagnetic Interference Risk Assessment. Systems, 13(4), 244. https://doi.org/10.3390/systems13040244






