Predicting Dependent Edges in Nonequilibrium Complex Systems Based on Overlapping Module Characteristics
Abstract
1. Introduction
1.1. Research on the Robustness of Interdependent Networks
1.2. Study on Dependency Patterns of Interdependent Networks
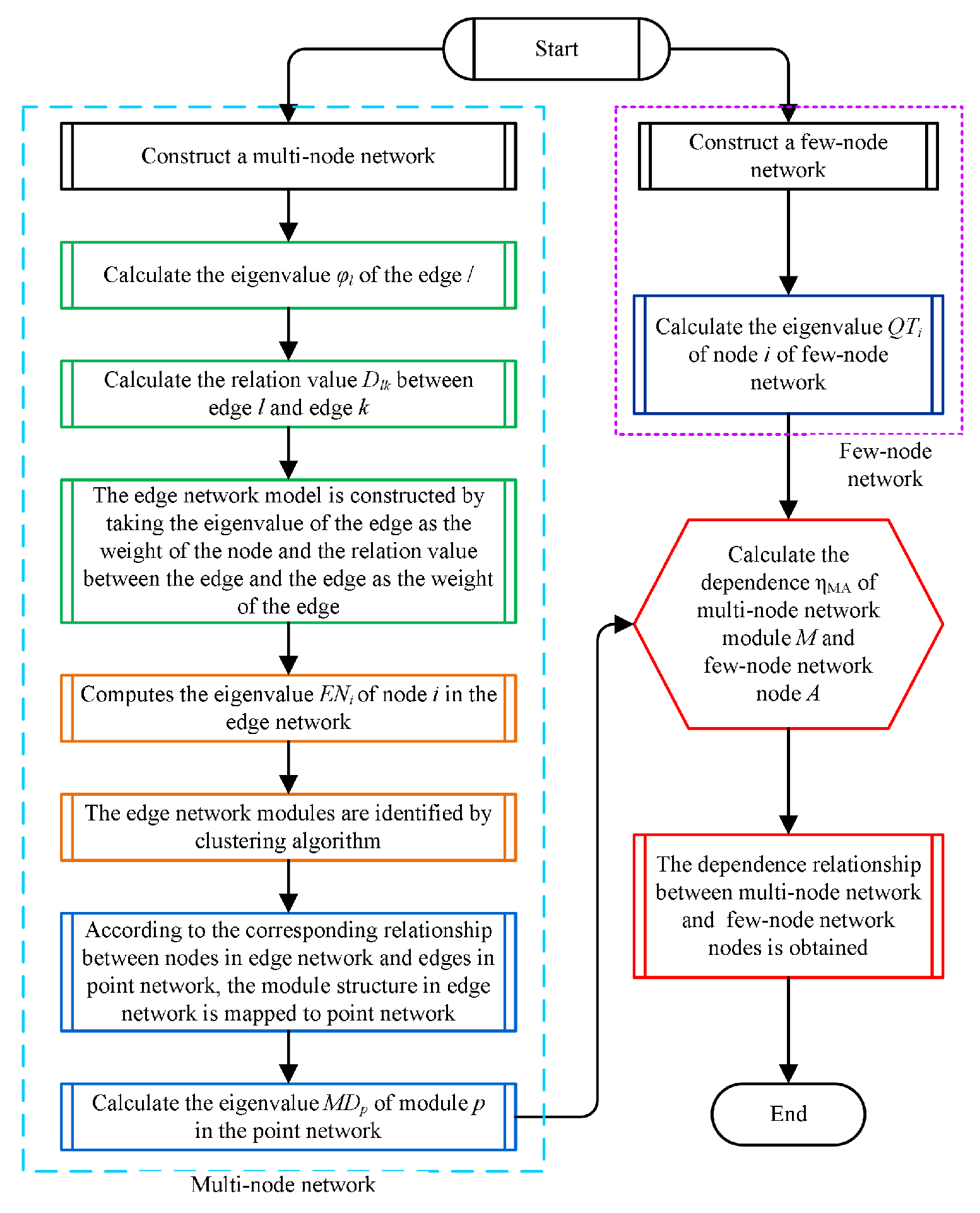
2. Materials and Methods
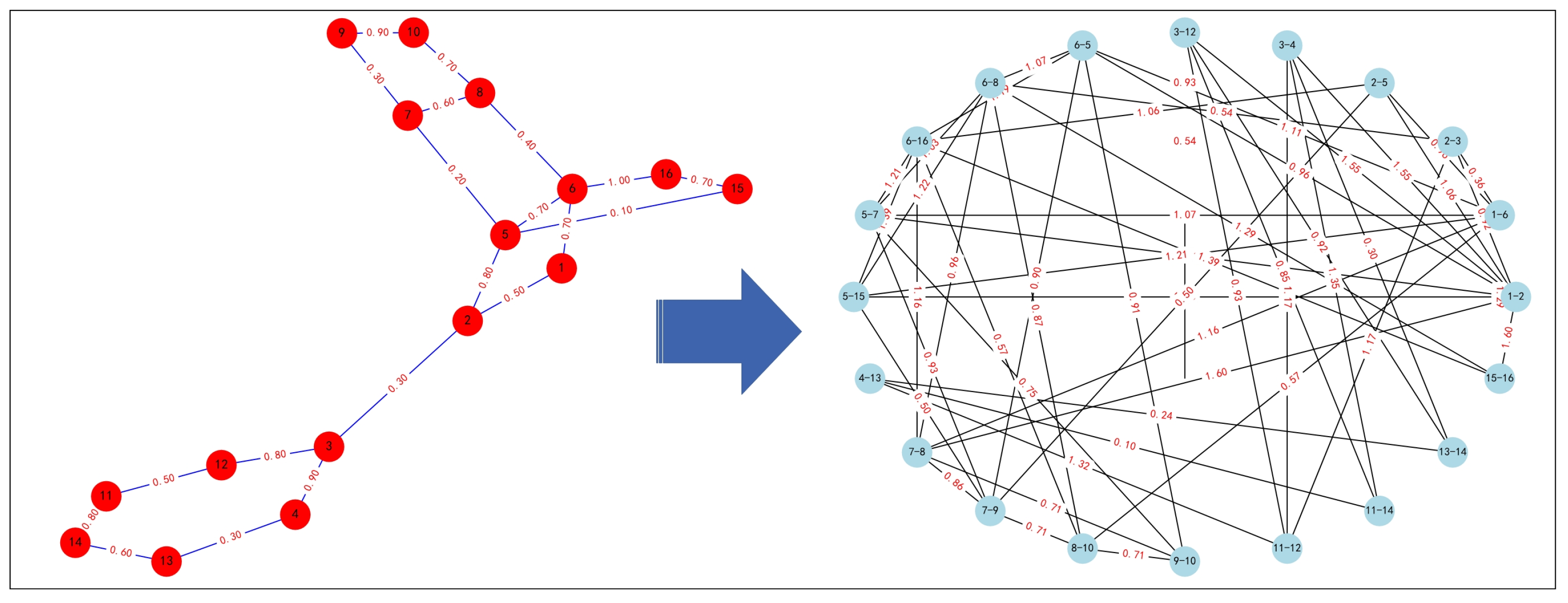
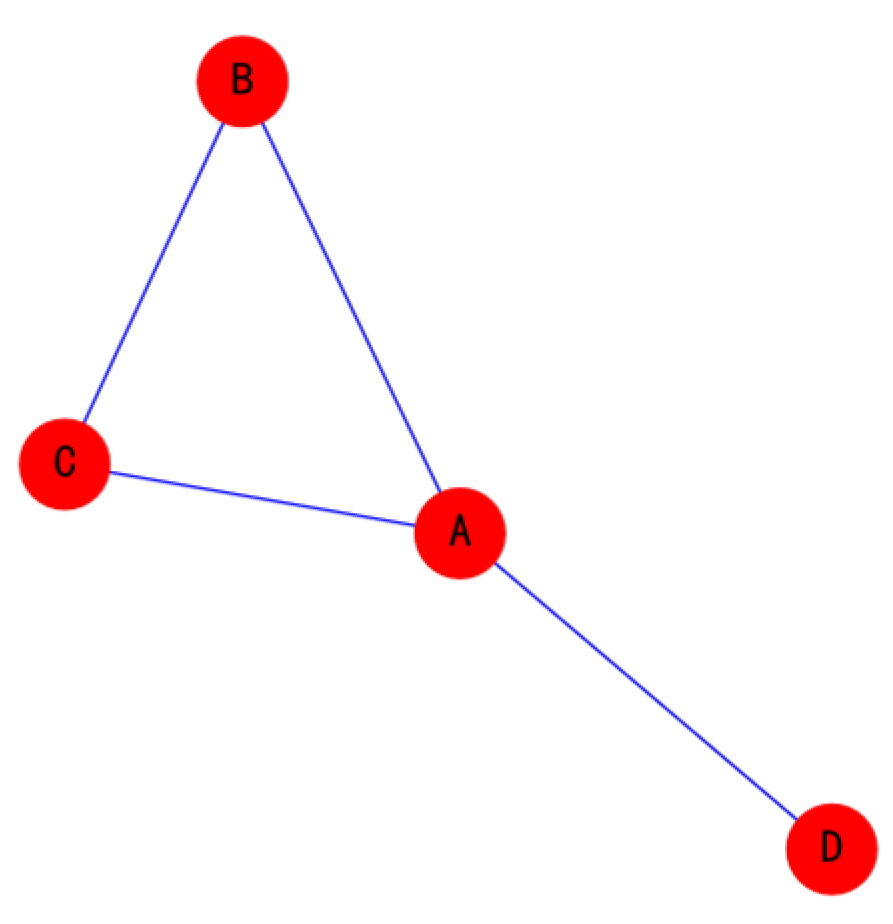
2.1. Edge-Based Model of Multi-Node Network
2.1.1. Edge Feature Values
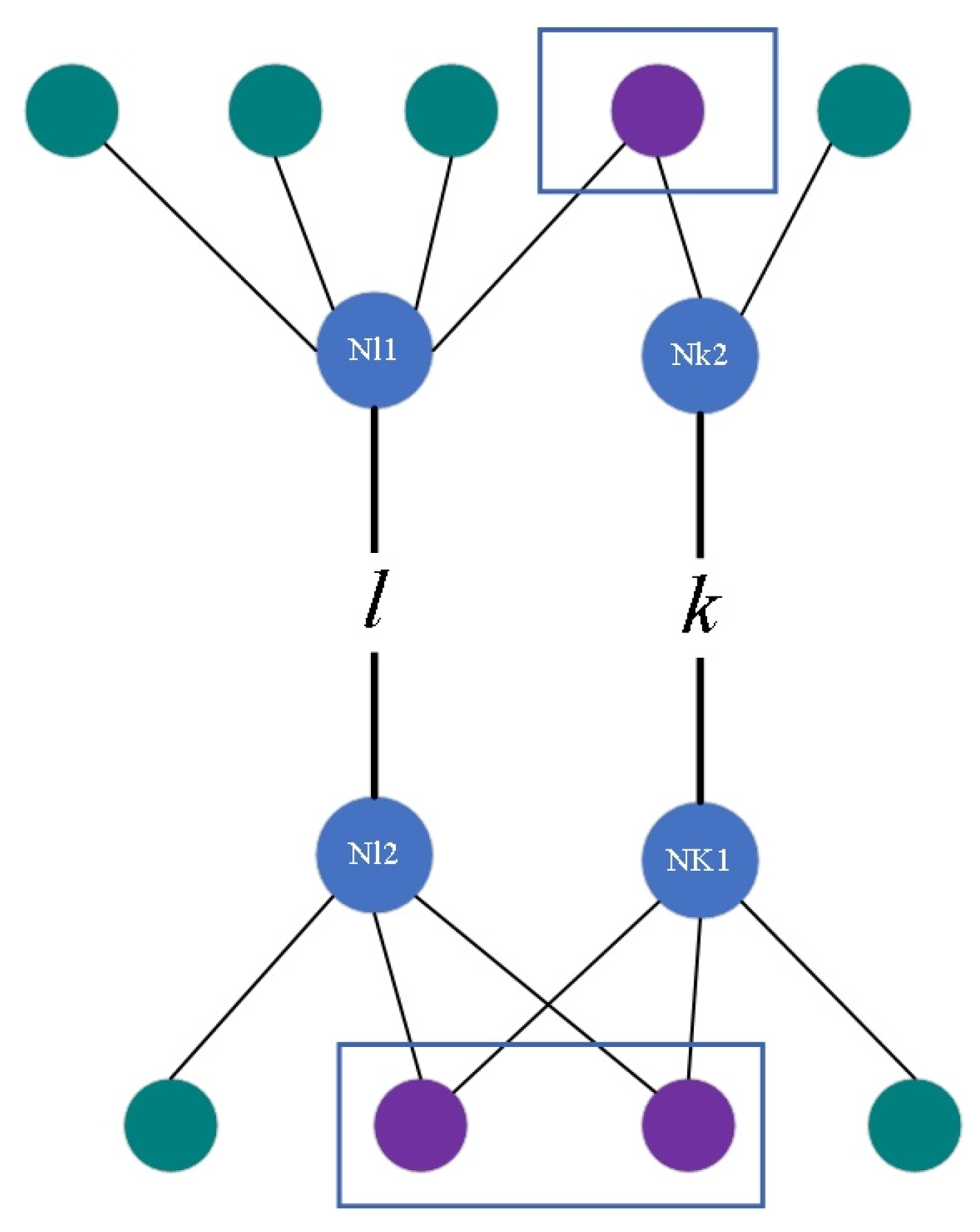
2.1.2. The Value of the Relationship between Edges
2.1.3. Constructing the Edge-Based Model
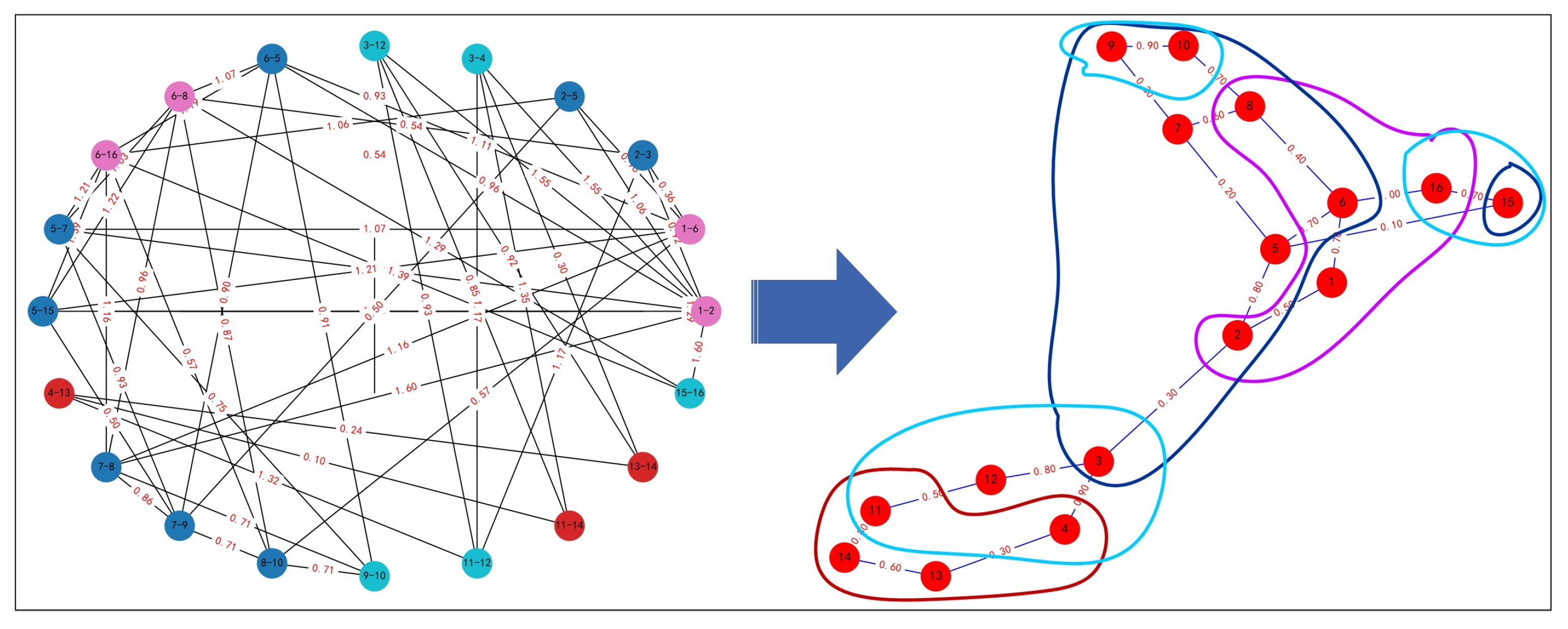
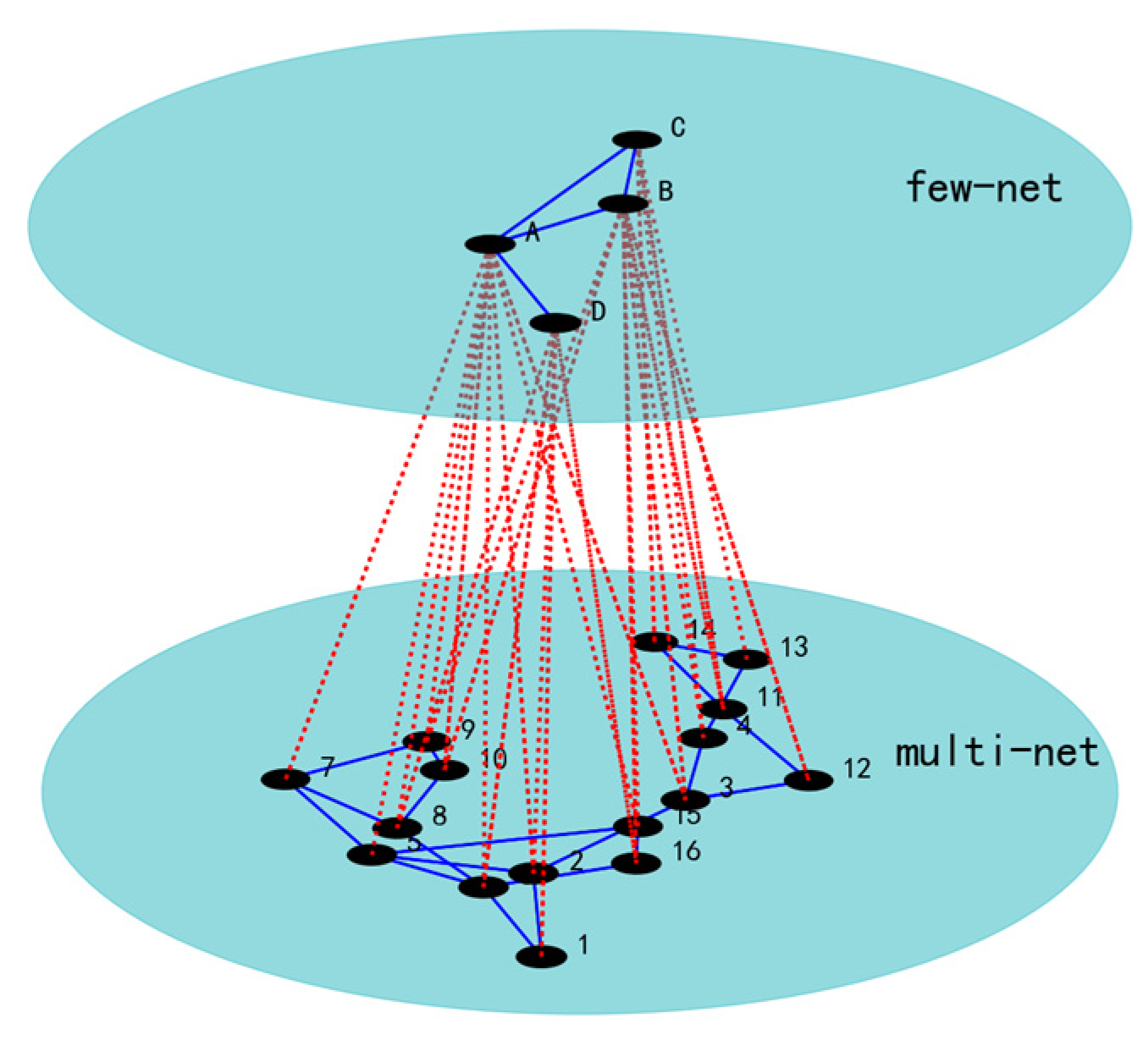
2.2. Network Module Identification in Edge-Based Models
2.2.1. Edge-Based Model Node Eigenvalues
2.2.2. Edge-Based Model Clustering
- Randomly select K nodes in the edge-based model as the initial cluster centers;
- Assign each node to the nearest cluster center;
- Recalculate the center of each cluster as the mean of all nodes assigned to it;
- Repeat steps 2 and 3 until the cluster centers stabilize.
2.2.3. Module Eigenvalues in the Node-Based Network
2.3. Characteristic Values of Few-Node Network Nodes
2.4. Dependency Edge Prediction
3. Results and Discussion
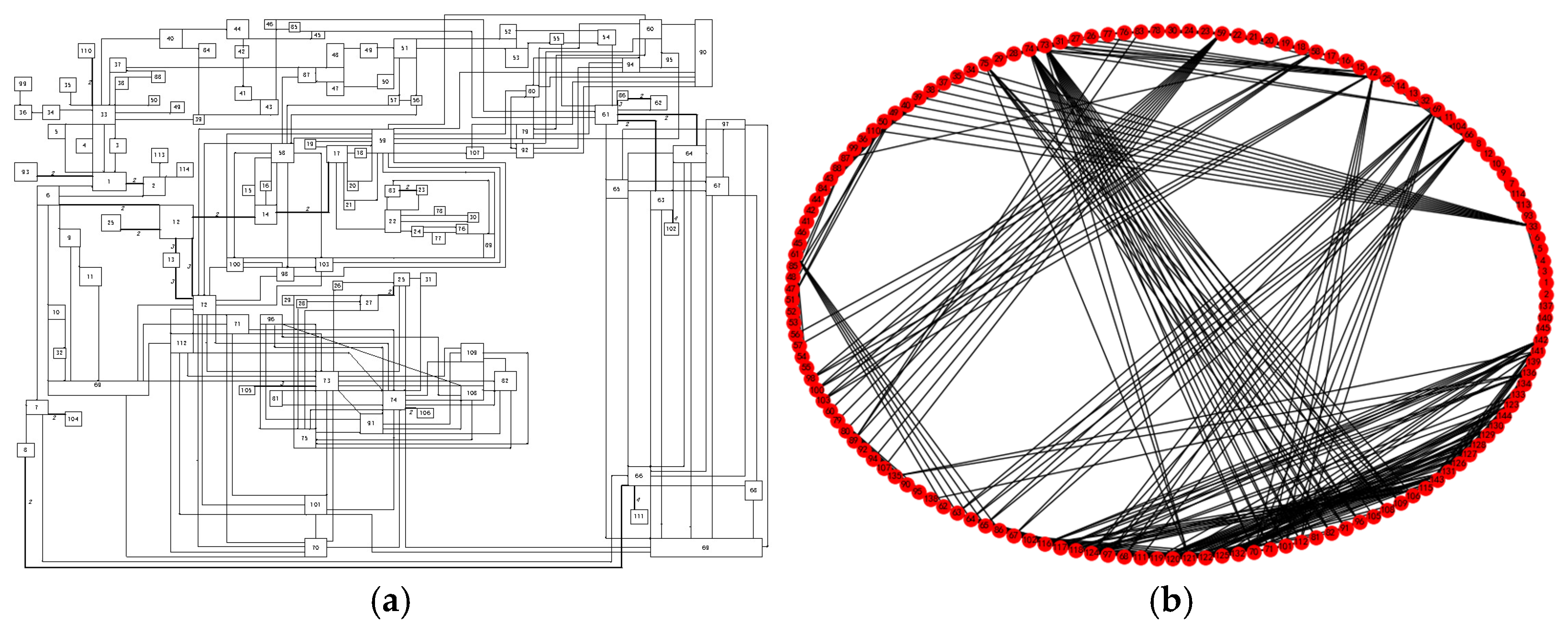
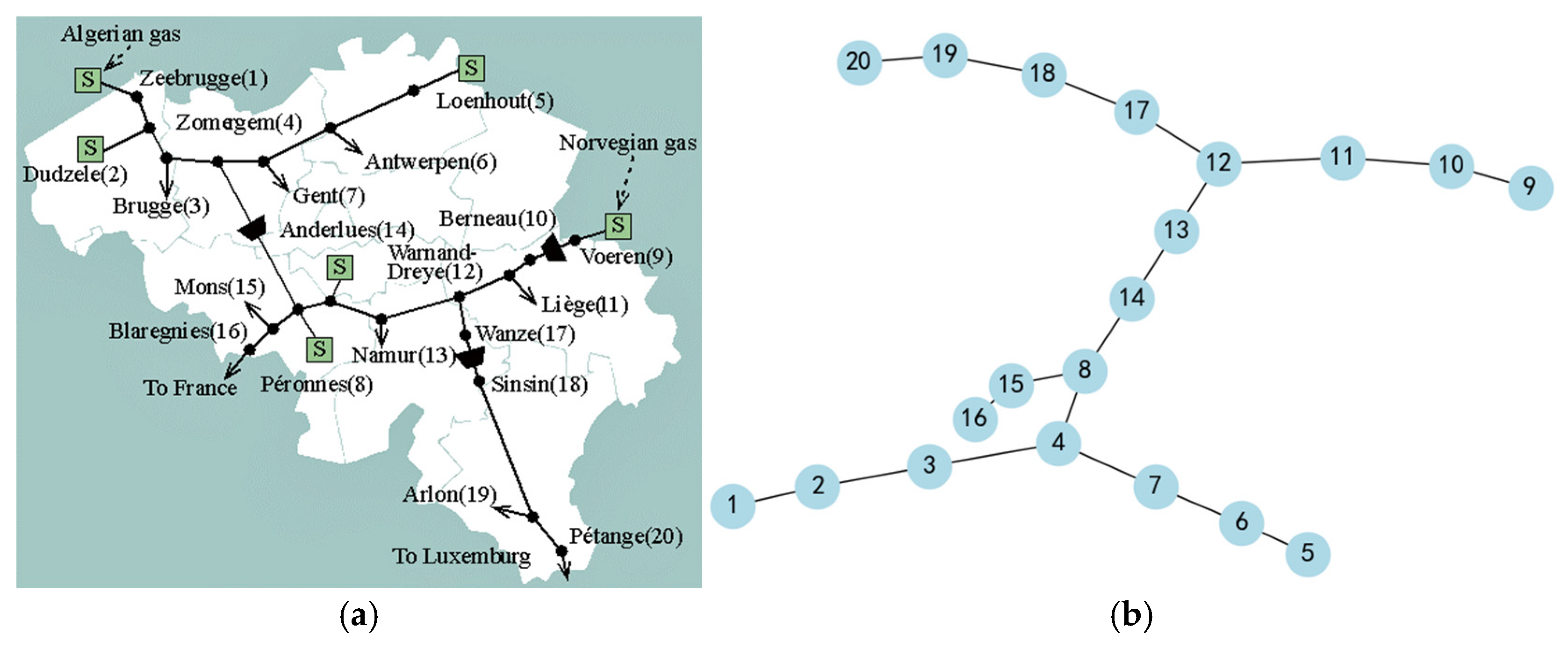
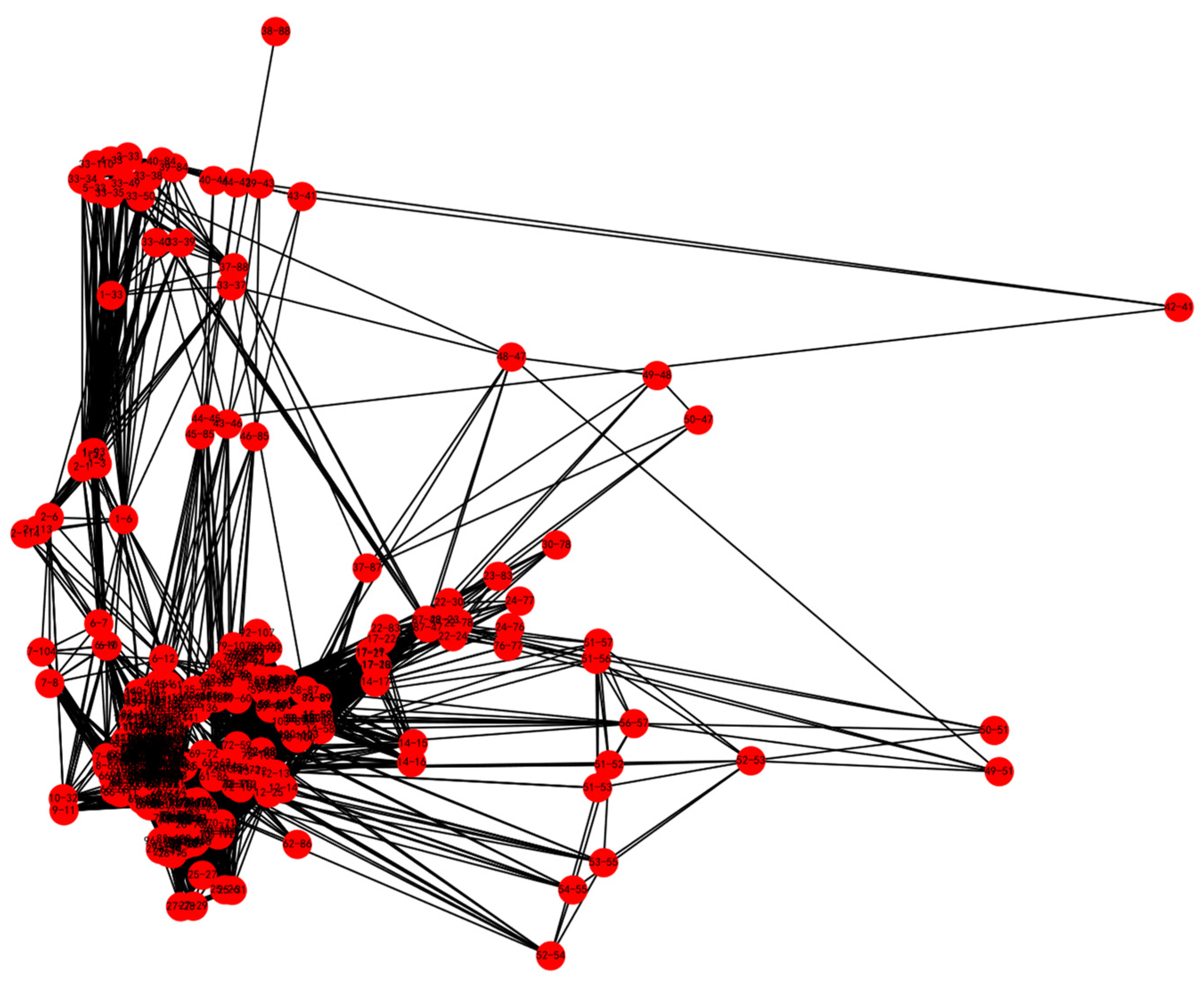
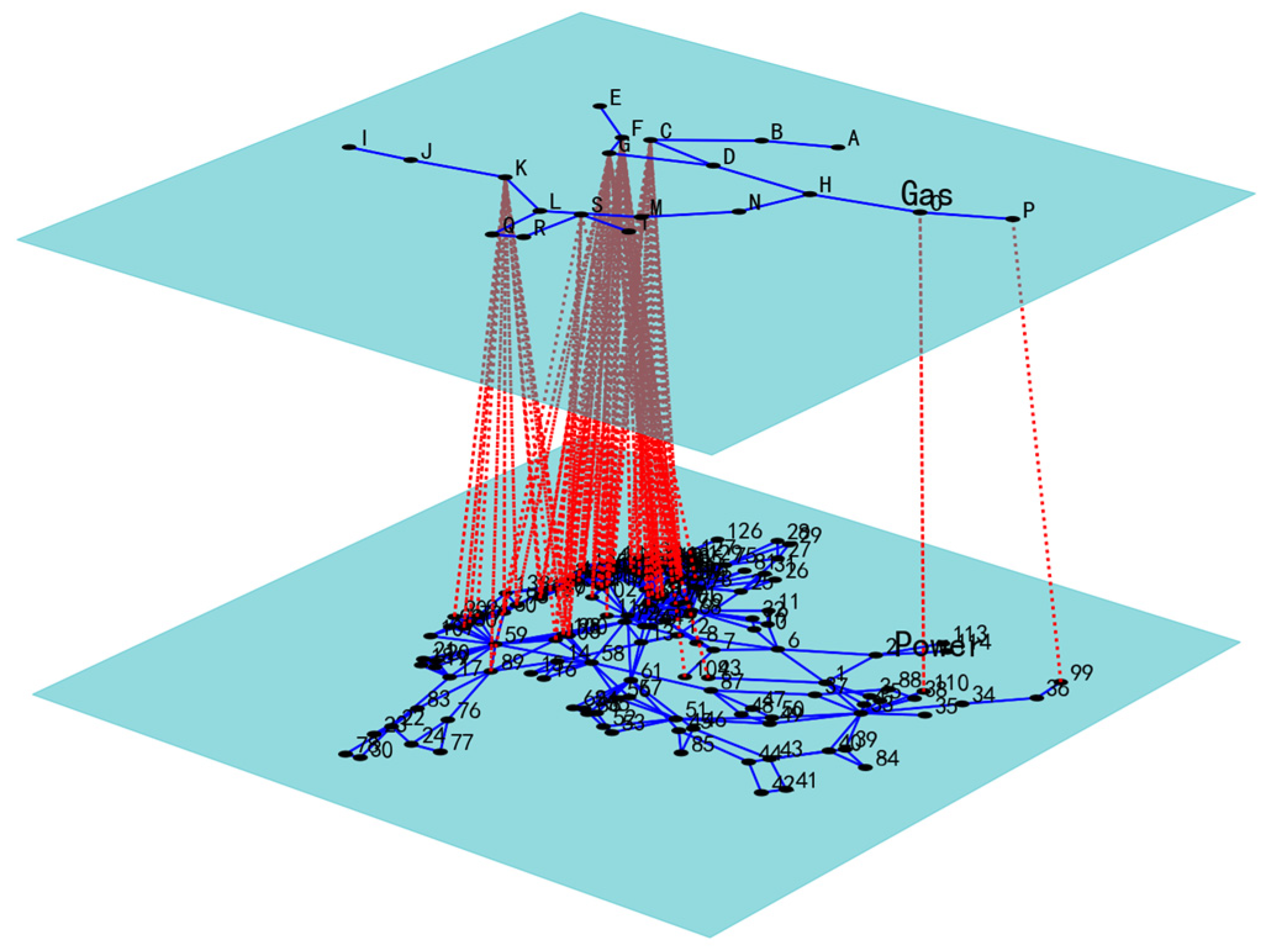
3.1. Power–Gas Network
3.1.1. Power Network Model
- All transmission lines are unique;
- The attribute vector of nodes includes two values: voltage magnitude and voltage phase angle;
- The weight of the transmission line is its reactance value.
3.1.2. Gas Network Model
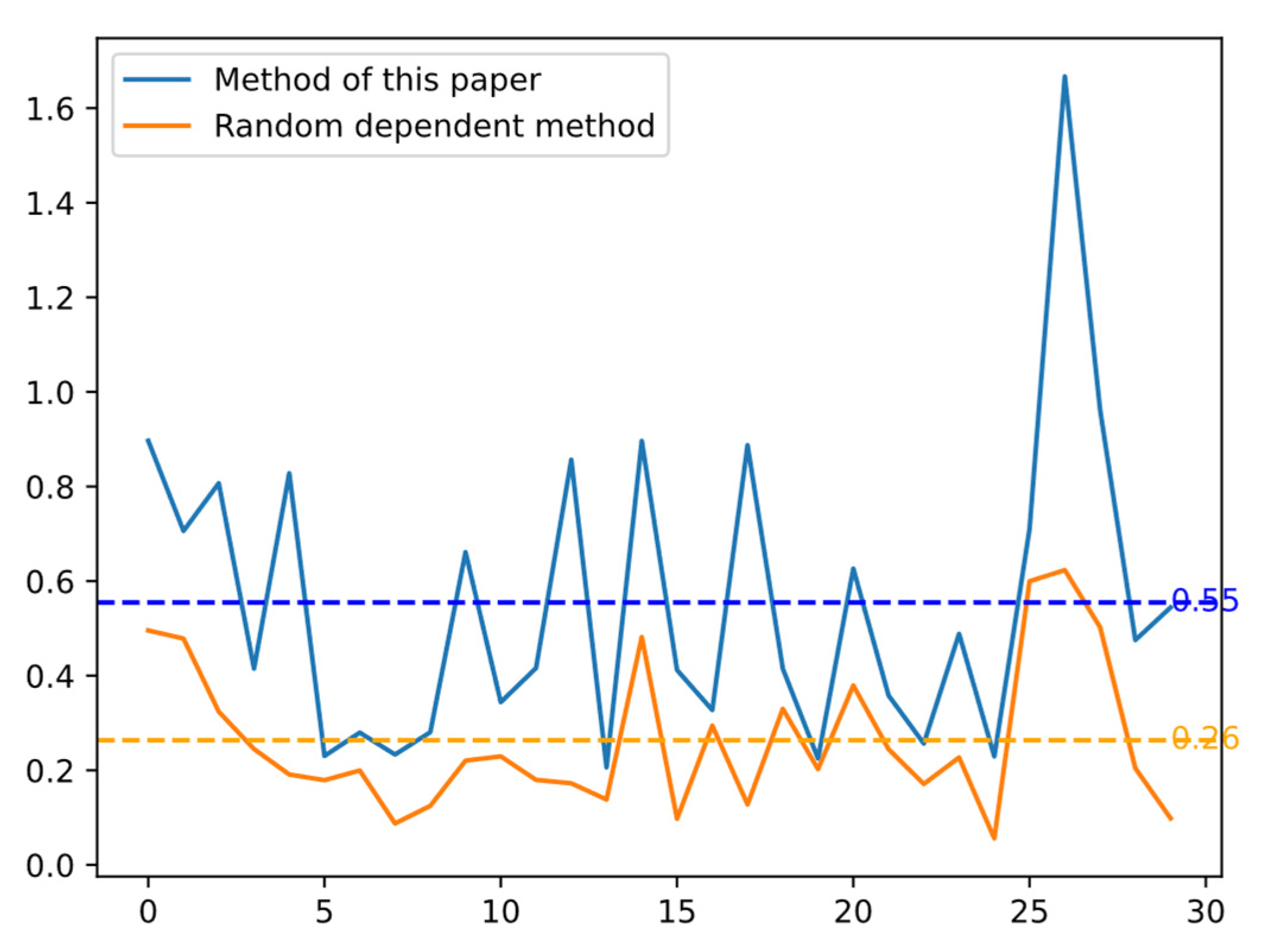
3.1.3. Prediction Result of Power-Gas Network Dependent Edge
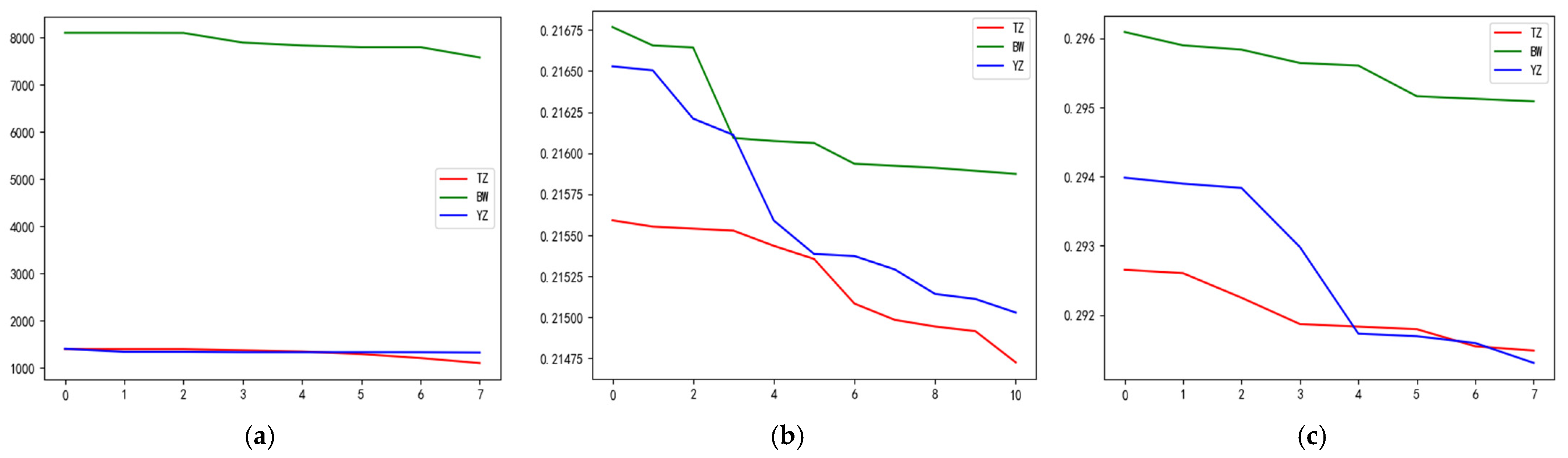
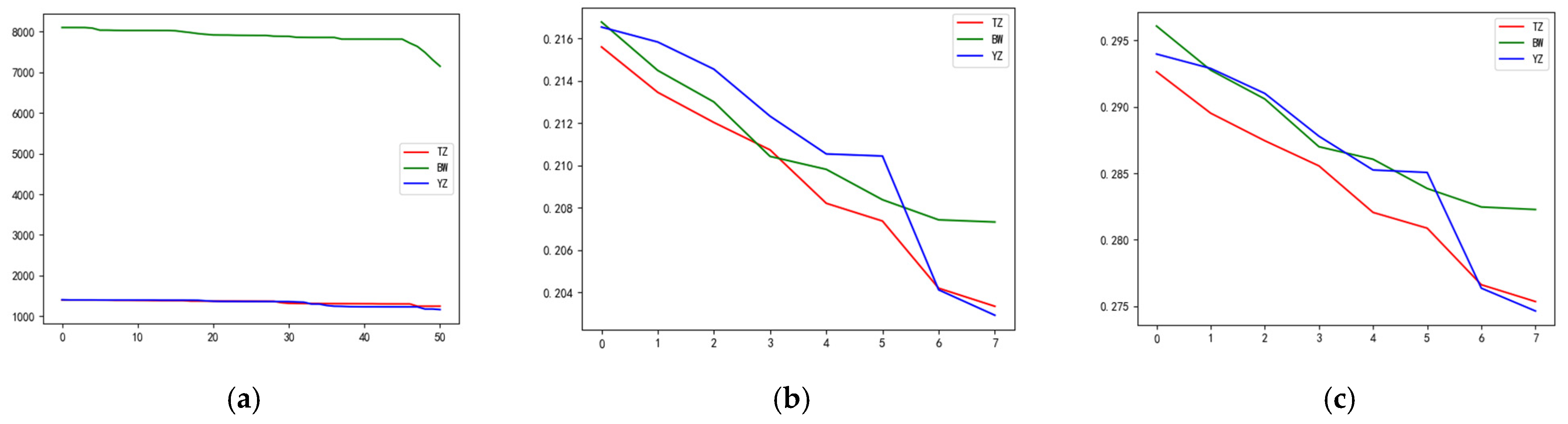
3.1.4. Comparison of Robustness Evaluation Results
Network Evaluation Metrics
- 1.
- Natural Connectivity Metric
- 2.
- Geodesic Vulnerability Index (GVI)
- 3.
- Network Efficiency Metric
Random Edge Attacks
High-Betweenness Edge Attacks
3.2. Course–Competency Network
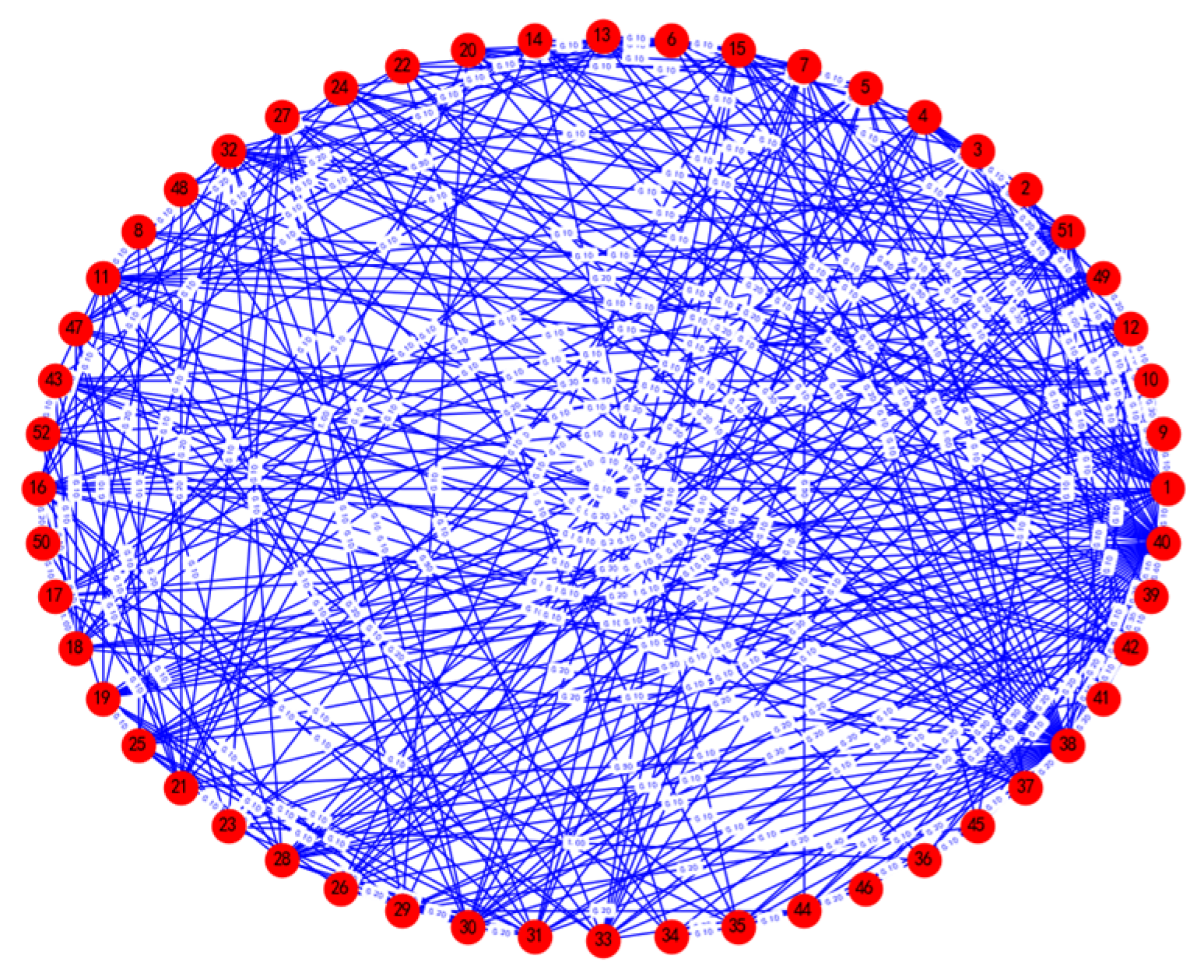
3.2.1. Course Network Model Construction
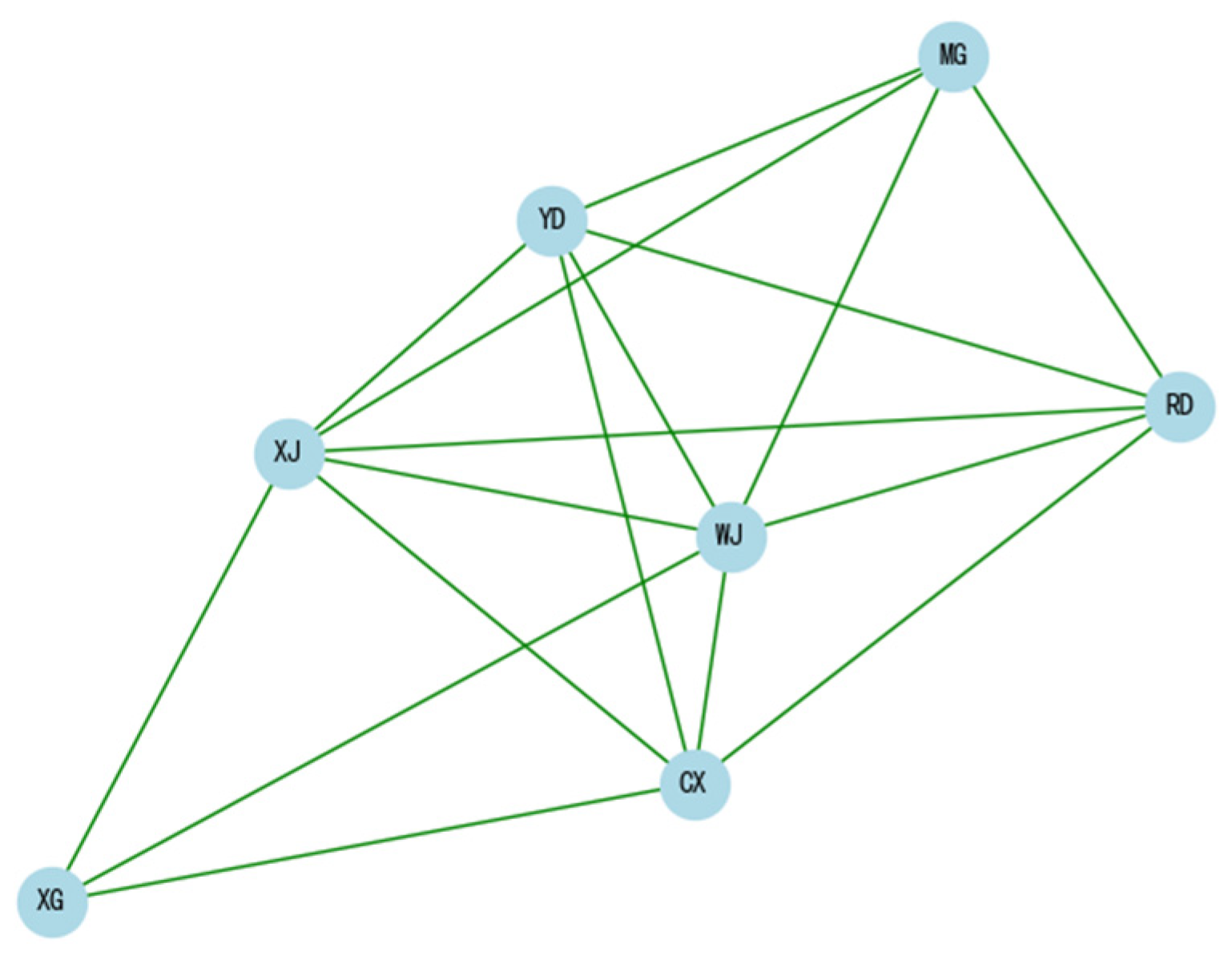
3.2.2. Competency Network Model Construction
- Modeling competency: the ability to abstract and generalize the essence of engineering problems, establish mathematical and physical models of systems, and determine system performance indicators.
- Hardware design competency: the ability to design hardware systems that meet requirements based on product needs and solve various problems encountered in the hardware design process.
- Software development competency: the ability to write high-quality code, implement product functions, and debug and optimize software.
- System integration competency: the ability to effectively integrate hardware and software to ensure the normal operation of the system.
- Project management competency: the ability to effectively organize and manage the development process of projects, ensuring that projects are completed on time and with quality.
- Innovation competency: the ability to continuously propose new ideas and solutions, promoting technological development and product innovation.
- Problem-solving competency: the ability to quickly and accurately analyze and solve various technical and engineering problems.The edges in the network represent the relationships between various competencies.
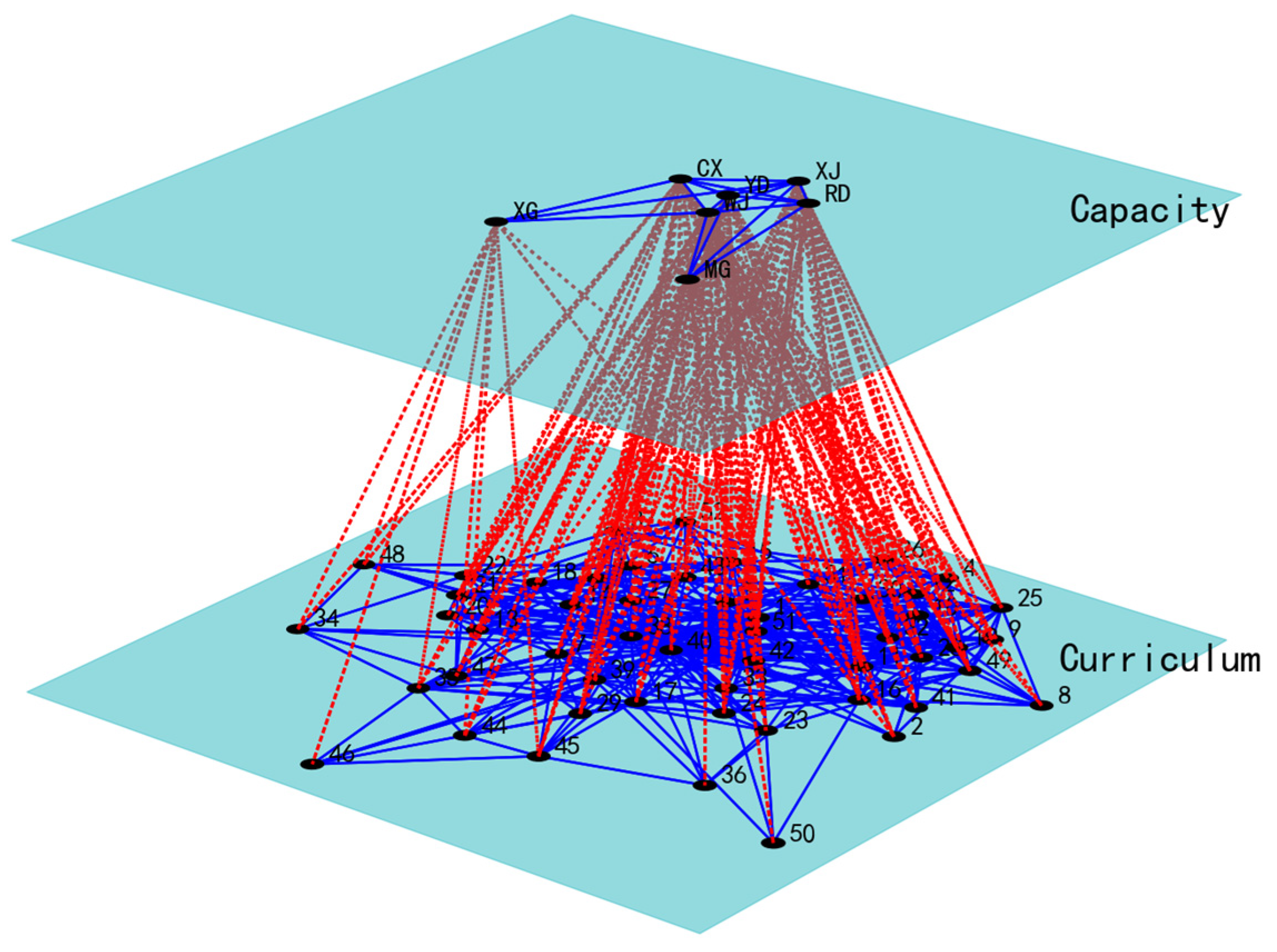
3.2.3. Dependency Edge Prediction Results
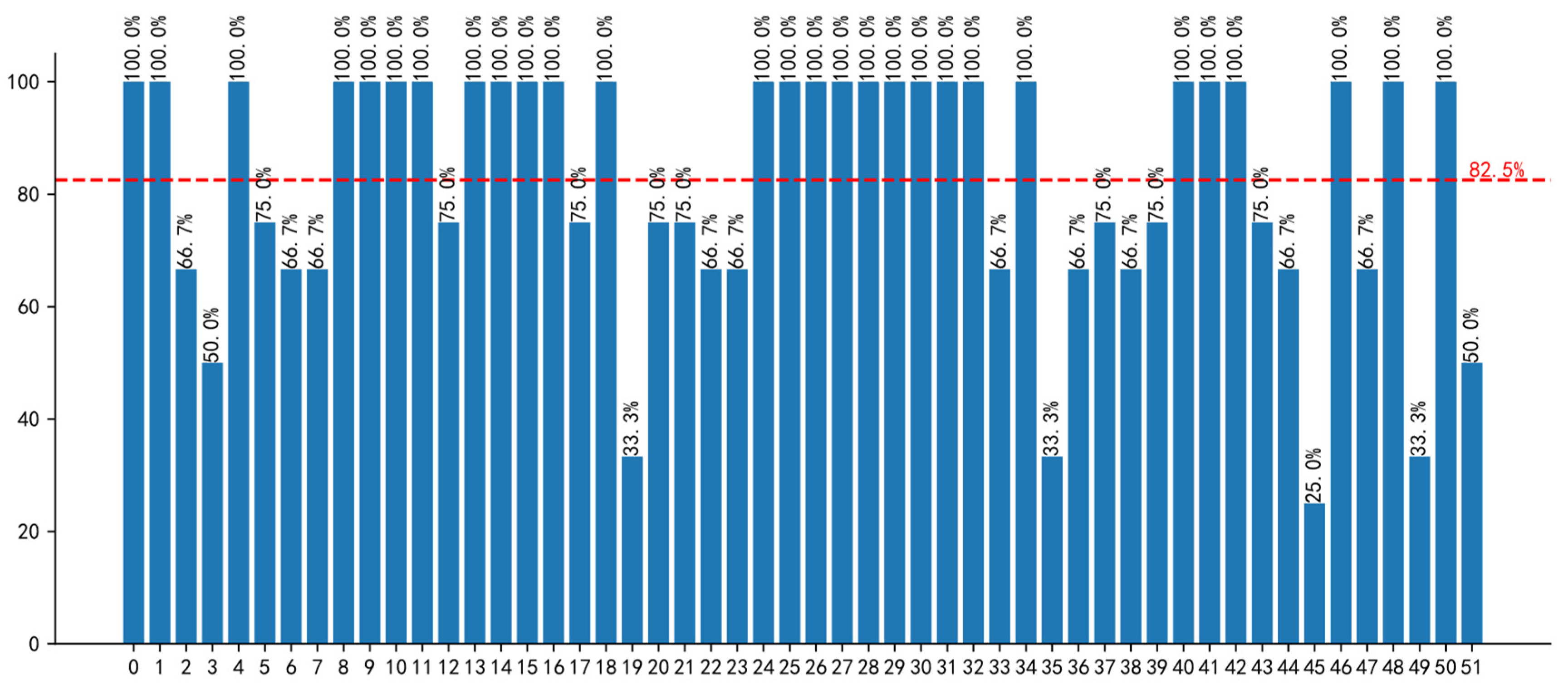
3.2.4. Comparison and Evaluation with Training Programs
Accuracy of Course and Competency Objectives
Accuracy of Competency-Supporting Courses
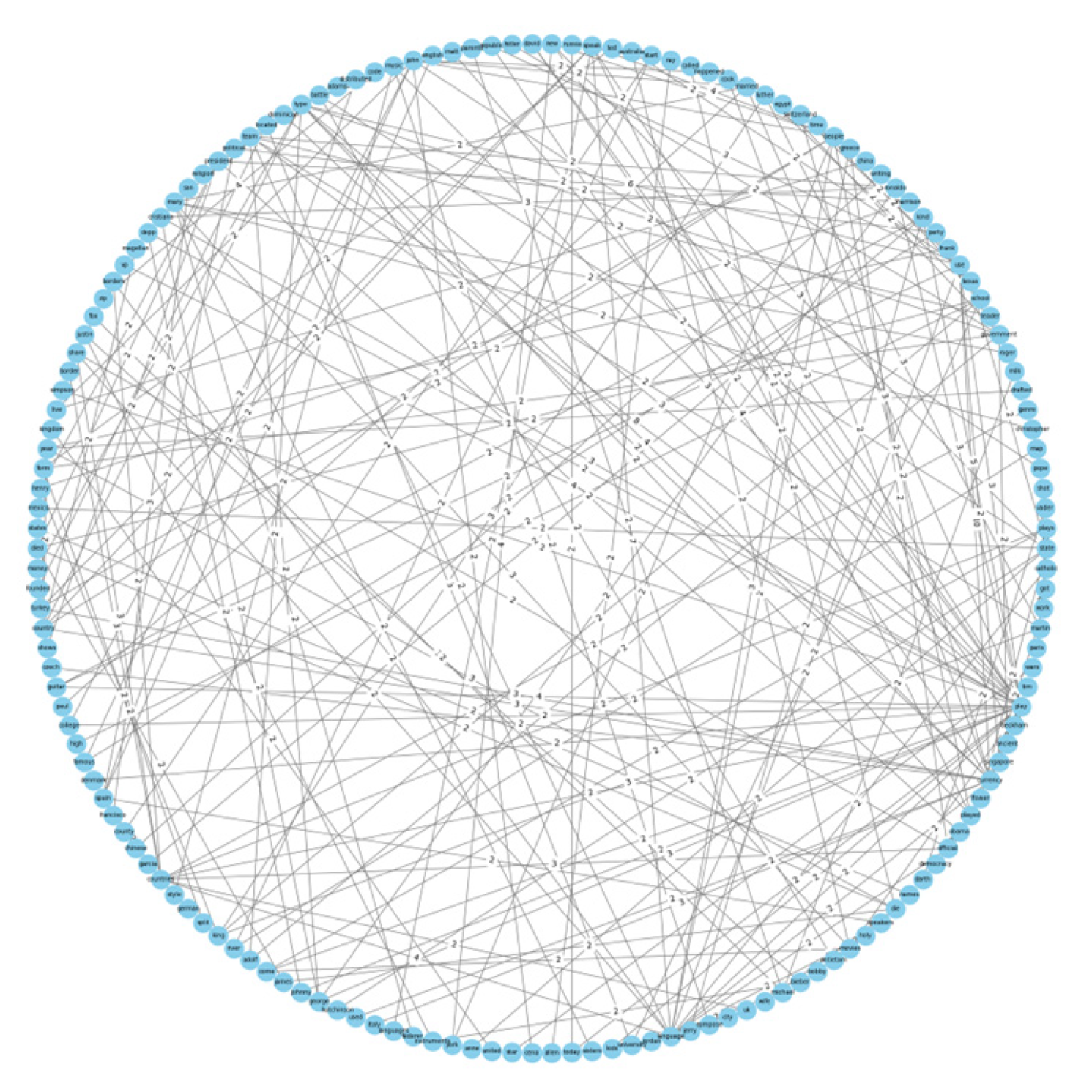
3.3. Text–Question Network
3.3.1. Word Attribute Vectors
3.3.2. Network Model Construction
3.3.3. Dependent Edge Prediction Results
3.3.4. Experimental Comparison Results
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Amini, M.H.; Boroojeni, K.G.; Iyengar, S.S.; Blaabjerg, F.; Pardalos, P.M.; Madni, A.M. (Eds.) A Panorama of Future Interdependent Networks: From Intelligent Infrastructures to Smart Cities. In Sustainable Interdependent Networks: From Theory to Application; Springer: Cham, Switzerland, 2018; Volume 145, pp. 1–10. [Google Scholar]
- Sarwat, A.I.; Sundararajan, A.; Parvez, I.; Moghaddami, M.; Moghadasi, A. Toward a Smart City of Interdependent Critical Infrastructure Networks. In Sustainable Interdependent Networks: From Theory to Application; Amini, M.H., Boroojeni, K.G., Iyengar, S.S., Pardalos, P.M., Blaabjerg, F., Madni, A.M., Eds.; Springer International Publishing Ag: Cham, Switzerland, 2018; Volume 145, pp. 21–45. [Google Scholar]
- Buldyrev, S.V.; Parshani, R.; Paul, G.; Stanley, H.E.; Havlin, S. Catastrophic cascade of failures in interdependent networks. Nature 2010, 464, 1025–1028. [Google Scholar] [CrossRef] [PubMed]
- Zhang, C.; Lei, Y.; Shen, X.; Li, Q.; Yao, H.; Cheng, D.; Xie, Y.; Yu, W. Fragility Induced by Interdependency of Complex Networks and Their Higher-Order Networks. Entropy 2022, 25, 22. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.-Y.; Zhao, Y.; Gao, J.; Stanley, H.E. Nonlinear model of cascade failure in weighted complex networks considering overloaded edges. Sci. Rep. 2020, 10, 13428. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Z.; Yin, Y.; Zhang, X.; Liu, L. Optimization of robustness of interdependent network controllability by redundant design. PLoS ONE 2018, 13, e0192874. [Google Scholar] [CrossRef] [PubMed]
- Chen, D.B.; Lü, L.Y.; Shang, M.S.; Zhang, Y.C.; Zhou, T. Identifying influential nodes in complex networks. Phys. A-Stat. Mech. Its Appl. 2012, 391, 1777–1787. [Google Scholar] [CrossRef]
- Wang, X.; Cao, J.; Li, R.; Zhao, T. A preferential attachment strategy for connectivity link addition strategy in improving the robustness of interdependent networks. Phys. A-Stat. Mech. Its Appl. 2017, 483, 412–422. [Google Scholar] [CrossRef]
- Beygelzimer, A.; Grinstein, G.E.; Linsker, R.; Rish, I. Improving network robustness by edge modification. Phys. A-Stat. Mech. Its Appl. 2005, 357, 593–612. [Google Scholar] [CrossRef]
- Jiang, Z.Y.; Liang, M.G.; Guo, D.C. Enhancing network performance by edge addition. Int. J. Mod. Phys. C 2011, 22, 1211–1226. [Google Scholar] [CrossRef]
- Sydney, A.; Scoglio, C.; Gruenbacher, D. Optimizing algebraic connectivity by edge rewiring. Appl. Math. Comput. 2013, 219, 5465–5479. [Google Scholar] [CrossRef]
- Cao, X.B.; Hong, C.; Du, W.B.; Zhang, J. Improving the network robustness against cascading failures by adding links. Chaos Solitons Fractals 2013, 57, 35–40. [Google Scholar] [CrossRef]
- Ji, X.; Wang, B.; Liu, D.; Chen, G.; Tang, F.; Wei, D.; Tu, L. Improving interdependent networks robustness by adding connectivity links. Phys. A-Stat. Mech. Its Appl. 2016, 444, 9–19. [Google Scholar] [CrossRef]
- Chen, C.Y.; Zhao, Y.; Qin, H.; Meng, X.; Gao, J. Robustness of interdependent scale-free networks based on link addition strategies. Phys. A-Stat. Mech. Its Appl. 2022, 604, 127851. [Google Scholar] [CrossRef]
- Lao, S.; Wang, J.; Bai, L. Review of the interdependent networks. J. Natl. Univ. Def. Technol. 2016, 38, 122–128. [Google Scholar]
- Gao, J.X.; Barzel, B.; Barabasi, A.L. Universal resilience patterns in complex networks. Nature 2016, 530, 307–312. [Google Scholar] [CrossRef]
- Valdez, L.D.; Shekhtman, L.; La Rocca, C.E.; Zhang, X.; Buldyrev, S.V.; Trunfio, P.A.; Braunstein, L.A.; Havlin, S.; Estrada, E. Cascading failures in complex networks. J. Complex Netw. 2020, 8, cnaa013. [Google Scholar] [CrossRef]
- Son, S.-W.; Bizhani, G.; Christensen, C.; Grassberger, P.; Paczuski, M. Percolation theory on interdependent networks based on epidemic spreading. Epl 2012, 97, 16006. [Google Scholar] [CrossRef]
- Min, B.; Do Yi, S.; Lee, K.-M.; Goh, K.I. Network robustness of multiplex networks with interlayer degree correlations. Phys. Rev. E 2014, 89, 042811. [Google Scholar] [CrossRef] [PubMed]
- Watanabe, S.; Kabashima, Y. Cavity-based robustness analysis of interdependent networks: Influences of intranetwork and internetwork degree-degree correlations. Phys. Rev. E 2014, 89, 012808. [Google Scholar] [CrossRef]
- Min, B.; Lee, S.; Lee, K.-M.; Goh, K.I. Link overlap, viability, and mutual percolation in multiplex networks. Chaos Solitons Fractals 2015, 72, 49–58. [Google Scholar] [CrossRef][Green Version]
- Cellai, D.; Dorogovtsev, S.N.; Bianconi, G. Message passing theory for percolation models on multiplex networks with link overlap. Phys. Rev. E 2016, 94, 032301. [Google Scholar] [CrossRef]
- Shao, S.; Huang, X.; Stanley, H.E.; Havlin, S. Robustness of a partially interdependent network formed of clustered networks. Phys. Rev. E 2014, 89, 032812. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Pan, L.; Stanley, H.E.; Gao, J. Multiple phase transitions in networks of directed networks. Phys. Rev. E 2019, 99, 012312. [Google Scholar] [CrossRef] [PubMed]
- Li, W.; Bashan, A.; Buldyrev, S.V.; Stanley, H.E.; Havlin, S. Cascading Failures in Interdependent Lattice Networks: The Critical Role of the Length of Dependency Links. Phys. Rev. Lett. 2012, 108, 228702. [Google Scholar] [CrossRef]
- Kleineberg, K.-K.; Buzna, L.; Papadopoulos, F.; Boguna, M.; Serrano, M.A. Geometric Correlations Mitigate the Extreme Vulnerability of Multiplex Networks against Targeted Attacks. Phys. Rev. Lett. 2017, 118, 218301. [Google Scholar] [CrossRef]
- Danziger, M.M.; Bonamassa, I.; Boccaletti, S.; Havlin, S. Dynamic interdependence and competition in multilayer networks. Nat. Phys. 2019, 15, 178–185. [Google Scholar] [CrossRef]
- Xu, X.; Fu, X. Analysis on Cascading Failures of Directed-Undirected Interdependent Networks with Different Coupling Patterns. Entropy 2023, 25, 471. [Google Scholar] [CrossRef]
- Zhou, L.; Yin, J.; Tan, F.; Liao, H. Robustness analysis of edge-coupled interdependent networks under different attack strategies. Phys. A-Stat. Mech. Its Appl. 2023, 632, 129338. [Google Scholar] [CrossRef]
- Peng, H.; Zhao, Y.; Zhao, D.; Zhong, M.; Hu, Z.; Han, J.; Li, R.; Wang, W. Robustness of higher-order interdependent networks. Chaos Solitons Fractals 2023, 171, 113485. [Google Scholar] [CrossRef]
- Modarresi, A.; Symons, J. Modeling Technological Interdependency in IoT—A Multidimensional and Multilayer Network Model for Smart Environments; IEEE: New York, NY, USA, 2019; pp. 1–7. [Google Scholar]
- Tu, H.; Xia, Y.; Wu, J.; Zhou, X. Robustness assessment of cyber-physical systems with weak interdependency. Phys. A-Stat. Mech. Its Appl. 2019, 522, 9–17. [Google Scholar] [CrossRef]
- Zhou, S.H.; Ng, S.T.; Yang, Y.F.; Xu, F.J.; Li, D.Z. A Data-Driven and Physics-Based Approach to Exploring Interdependency of Interconnected Infrastructure; The American Society of Civil Engineers: New York, NY, USA, 2019; pp. 82–88. [Google Scholar]
- Cao, Y.-Y.; Liu, R.-R.; Jia, C.-X.; Wang, B.-H. Percolation in multilayer complex networks with connectivity and interdependency topological structures. Commun. Nonlinear Sci. Numer. Simul. 2021, 92, 105492. [Google Scholar] [CrossRef]
- Guimera, R.; Sales-Pardo, M.; Amaral, L.A.N. Module identification in bipartite and directed networks. Phys. Rev. E 2007, 76, 036102. [Google Scholar] [CrossRef] [PubMed]
- Gonzalez, M.C.; Barabasi, A.-L. Complex networks—From data to models. Nat. Phys. 2007, 3, 224–225. [Google Scholar] [CrossRef] [PubMed]
- Shi, D.; Shang, F.; Chen, B.; Expert, P.; Lue, L.; Stanley, H.E.; Lambiotte, R.; Evans, T.S.; Li, R. Local dominance unveils clusters in networks. Commun. Phys. 2024, 7, 170. [Google Scholar] [CrossRef]
- Xie, J.; Meng, F.; Sun, J.; Ma, X.; Yan, G.; Hu, Y. Detecting and modelling real percolation and phase transitions of information on social media. Nat. Hum. Behav. 2021, 5, 1161–1168. [Google Scholar] [CrossRef]
- Stella, M.; De Domenico, M. Distance Entropy Cartography Characterises Centrality in Complex Networks. Entropy 2018, 20, 268. [Google Scholar] [CrossRef] [PubMed]
- Gao, Z.; Jin, N.; IEEE. Detecting community structure in complex networks based on K-means clustering and data field theory. In Proceedings of the 2008 Chinese Control and Decision Conference, Yantai, China, 2–4 July 2008; pp. 4411–4416. [Google Scholar]
- Jiang, W.-J.; Liu, R.-R.; Fan, T.-L.; Liu, S.-S.; Lu, L.-Y. Overview of precaution and recovery strategies for cascading failures in multilayer networks. Acta Phys. Sin. 2020, 69, 81–91. [Google Scholar] [CrossRef]
- Sun, J.; Feng, L.; Xie, J.; Ma, X.; Wang, D.; Hu, Y. Revealing the predictability of intrinsic structure in complex networks. Nat. Commun. 2020, 11, 574. [Google Scholar] [CrossRef] [PubMed]
- Liu, C.; Shahidehpour, M.; Wang, J. Coordinated scheduling of electricity and natural gas infrastructures with a transient model for natural gas flow. Chaos 2011, 21, 1. [Google Scholar] [CrossRef]
- Rosas-Casals, M. Power Grids as Complex Networks. Topology and Fragility. In Proceedings of the 2010 Complexity in Engineering: Compeng, Roma, Italy, 22–24 February 2010; pp. 21–26. [Google Scholar]
- Zaibin, J.; Feng, M.; Zongbo, L. Study on Combined Operation of Gas-electricity Coupling System and Emergency Overload Control Considering the Characteristics of Natural Gas. Proc. CSEE 2019, 39, 77–83. [Google Scholar]
- Ban, W.; Runnian, M.; Gang, W. Research on Invulnerability of Complex Networks Based on Natural Connectivity. Comput. Simul. 2015, 32, 315–322. [Google Scholar]
- Jun, W.; Suoyi, T.; Yuejin, T.; Hongzhong, D. Analysis of Invulnerability in Complex Networks Based on Natural Connectivity. Complex Syst. Complex. Sci. 2014, 11, 77–86. [Google Scholar]
- Beyza, J.; Garcia-Paricio, E.; Ruiz, H.F.; Yust, J.M. Geodesic Vulnerability Approach for Identification of Critical Buses in Power Systems. J. Mod. Power Syst. Clean Energy 2021, 9, 37–45. [Google Scholar] [CrossRef]
- Kang, W.J.; Zhu, P.D.; Zhang, J.X.; Zhang, J.Y. Critical Nodes Identification of Power Grids Based on Network Efficiency. Ieice Trans. Inf. Syst. 2018, E101D, 2762–2772. [Google Scholar] [CrossRef]
- Zou, Q.Y.; Sun, X.; Zhou, Z.X. Relationship Recognition between Knowledge and Ability Based on the Modularity of Complex Networks. Sustainability 2023, 15, 20. [Google Scholar] [CrossRef]
- Mu, J. Cognitive Development, Cognitive Process and Knowledge Support: A three-dimensional construction of Chinese textbooks. Chin. Constr. 2020, 8, 19–24. [Google Scholar]
- Hancock, M.; Stiers, J.; Higgins, T.; Swarr, F.; Shrider, M.; Sood, S. A Hierarchical Characterization of Knowledge for Cognition. In Proceedings of the 13th International Conference on Augmented Cognition (AC) Held as Part of the 21st International Conference on Human-Computer Interaction (HCII), Orlando, FL, USA, 26–31 July 2019; pp. 58–73. [Google Scholar]
- Qingyu, Z.; Lin, Y. Research on the Core Competence Model of Engineering and Technical Personnel. Adult High. Educ. 2022, 4, 16–23. [Google Scholar]
- Berant, J.; Chou, A.; Frostig, R.; Liang, P. Semantic Parsing on Freebase from Question-Answer Pairs. In Proceedings of the 2013 Conference on Empirical Methods in Natural Language Processing, Seattle, WA, USA, 18–21 October 2013; ZDavid Yarowsky, Timothy Baldwin, Anna Korhonen, Karen Livescu, Steven Bethard; Association for Computational Linguistics: Seattle, WA, USA, 2013; pp. 1533–1544. [Google Scholar]
- Jain, S. Question Answering over Knowledge Base using Factual Memory Networks. In Proceedings of the NAACL Student Research Workshop; Jacob, A., Eunsol, C., Angeliki, L., Eds.; Association for Computational Linguistics: San Diego, CA, USA, 2016; pp. 109–115. [Google Scholar]
- Mikolov, T.; Chen, K.; Corrado, G.; Dean, J. Efficient Estimation of Word Representations in Vector Space. arXiv 2013, arXiv:1301.3781. [Google Scholar]
- Newman, M.E.J. The structure and function of complex networks. Siam Rev. 2003, 45, 167–256. [Google Scholar] [CrossRef]
- Lippi, M.; Jaeger, M.; Frasconi, P.; Passerini, A. Relational information gain. Mach. Learn. 2011, 83, 219–239. [Google Scholar] [CrossRef]
- Zhang, R.; Tran, T. An information gain-based approach for recommending useful product reviews. Knowl. Inf. Syst. 2010, 26, 419–434. [Google Scholar] [CrossRef]


| Node | Attribute 1 | Attribute 2 | Node | Attribute 1 | Attribute 2 |
|---|---|---|---|---|---|
| 1 | 0.7 | 0.8 | 9 | 1.9 | 0.7 |
| 2 | 0.5 | 1.2 | 10 | 1.1 | 0.5 |
| 3 | 2 | 0.8 | 11 | 1.3 | 1.1 |
| 4 | 0.4 | 0.9 | 12 | 1.6 | 1.9 |
| 5 | 0.5 | 1.3 | 13 | 0.7 | 0.9 |
| 6 | 2.1 | 1.2 | 14 | 0.7 | 1 |
| 7 | 0.8 | 0.9 | 15 | 0.3 | 0.8 |
| 8 | 1.7 | 0.8 | 16 | 2.1 | 1.8 |
| Node | Weights | Node | Weights | Node | Weights | Node | Weights |
|---|---|---|---|---|---|---|---|
| 1–2 | 0.474 | 3–12 | 0.706 | 5–15 | 0.100 | 9–10 | 0.898 |
| 1–6 | 0.662 | 6–5 | 0.542 | 4–13 | 0.291 | 11–12 | 0.493 |
| 2–3 | 0.210 | 6–8 | 0.399 | 7–8 | 0.552 | 11–14 | 0.774 |
| 2–5 | 0.800 | 6–16 | 0.982 | 7–9 | 0.265 | 13–14 | 0.599 |
| 3–4 | 0.645 | 5–7 | 0.187 | 8–10 | 0.700 | 15–16 | 0.613 |
| Module | Node in a Module | Characteristic Values |
|---|---|---|
| 1 | Node 2, 3, 5, 6, 7, 8, 9, 10, 15 | 3.125 |
| 2 | Node 4, 11, 13, 14 | 2 |
| 3 | Node 16, 1, 2, 6, 8 | 3 |
| 4 | Node 3, 4, 9, 10, 11, 12, 15, 16 | 2.2 |
| Module | Node Number in the Module | Average Degree Value |
|---|---|---|
| 1 | 6, 137, 138, 139, 12, 140, 14, 15, 16, 17, 18, 19, 20, 21, 79, 80, 89, 90, 92, 94, 95, 98, 100, 103, 107, 58, 59, 60 | 8.011 |
| 2 | 7, 76, 77, 78, 104, 85, 86, 87, 24, 30, 37, 39, 40, 41, 42, 43, 44, 45, 46, 47, 48, 49, 50, 51, 52, 53, 54, 56, 57, 62 | 3.152 |
| 3 | 128, 129, 130, 131, 133, 134, 135, 136, 9, 10, 11, 138, 139, 141, 142, 144, 143, 145, 32, 61, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 82, 91, 97, 101, 102, 108, 109, 112, 115, 116, 117, 118, 119, 120, 123, 125, 126, 127 | 10.44 |
| 4 | 1, 2, 3, 4, 5, 6, 7, 9, 10, 11, 12, 13, 14, 15, 16, 17, 18, 19, 20, 21, 22, 27, 28, 29, 32, 33, 37, 39, 40, 45, 46, 54, 55, 56, 57, 58, 61, 62, 76, 83, 84, 86, 87, 88, 89, 93, 98, 100, 103 | 4.977 |
| 5 | 7, 8, 12, 13, 25, 26, 27, 28, 29, 31, 58, 59, 60, 61, 63, 66, 68, 70, 71, 72, 73, 74, 75, 81, 82, 91, 95, 96, 98, 100, 101, 102, 103, 105, 106, 108, 109, 111, 112, 117, 135, 136, 137, 138, 139, 140, 145 | 8.636 |
| 6 | 59, 63, 64, 65, 66, 67, 68, 69, 70, 71, 72, 73, 74, 75, 82, 91, 97, 101, 108, 109, 112, 116, 117, 118, 119, 120, 121, 122, 123, 124, 125, 127, 128, 129, 130, 131, 132, 133, 136, 141, 142, 143, 144 | 14.224 |
| 7 | 34, 99, 36, 38, 88 | 1.833 |
| 8 | 2, 3, 4, 5, 6, 7, 8, 22, 23, 24, 30, 33, 34, 35, 37, 38, 39, 40, 43, 44, 45, 46, 47, 48, 49, 50, 53, 54, 55, 56, 57, 77, 78, 83, 87, 110, 113, 114 | 5.016 |
| The Dependence Relationship between Gas Network Nodes and Power Network Modules | ||||||||
|---|---|---|---|---|---|---|---|---|
| Gas network node | C 1 | F 2 | G 3 | K 4 | O 5 | P 6 | S 7 | T 8 |
| Power network module | Module6 | Module3 | Module5 | Module1 | Module8 | Module7 | Module4 | Module2 |
| Tnet | Dnet | Tnet | Dnet | Tnet | Dnet | Tnet | Dnet | Tnet | Dnet | Tnet | Dnet |
|---|---|---|---|---|---|---|---|---|---|---|---|
| C | 67 | C | 144 | F | 116 | G | 137 | C | 132 | P | 99 |
| C | 82 | F | 128 | F | 117 | G | 139 | C | 136 | S | 89 |
| C | 91 | F | 130 | F | 118 | G | 140 | C | 141 | S | 93 |
| C | 97 | F | 131 | F | 119 | G | 145 | C | 142 | S | 98 |
| C | 101 | F | 134 | G | 60 | K | 137 | C | 143 | C | 131 |
| C | 108 | F | 135 | G | 82 | K | 139 | S | 103 | F | 101 |
| C | 109 | F | 136 | G | 91 | K | 140 | F | 102 | G | 109 |
| C | 112 | F | 139 | G | 95 | K | 79 | F | 108 | O | 110 |
| C | 116 | F | 141 | G | 96 | K | 80 | F | 109 | S | 100 |
| C | 117 | F | 142 | G | 98 | K | 89 | F | 112 | C | 130 |
| C | 118 | F | 144 | G | 100 | K | 90 | F | 115 | F | 97 |
| C | 119 | F | 143 | G | 101 | K | 94 | T | 104 | G | 108 |
| C | 121 | F | 145 | G | 102 | K | 95 | G | 111 | K | 60 |
| C | 122 | F | 67 | G | 103 | K | 98 | G | 112 | G | 136 |
| C | 124 | F | 82 | G | 105 | K | 100 | G | 117 | G | 135 |
| C | 128 | F | 91 | G | 106 | K | 103 |
| No. | Course Name | DUA | DAE | No. | Course Name | DUA | DAE |
|---|---|---|---|---|---|---|---|
| 1 | Digital Electronic Technology | 0.8 | 0.2 | 27 | Fundamentals of Computer Simulation | 0.5 | 0.5 |
| 2 | Analog Electronics Experiment | 0.6 | 0.4 | 28 | Sensor Technology | 0.6 | 0.4 |
| 3 | Digital Electronics Experiment | 0.6 | 0.4 | 29 | New Technology Topics | 0.2 | 0.8 |
| 4 | High-Frequency Electronic Technology | 0.9 | 0.1 | 30 | Wireless Sensor Networks | 0.5 | 0.5 |
| 5 | EDA Technology and Applications | 0.7 | 0.3 | 31 | Introduction to IoT | 0.3 | 0.7 |
| 6 | System-on-Chip Design | 0.5 | 0.5 | 32 | RF Identification Technology | 0.8 | 0.2 |
| 7 | Engineering Ethics | 1 | 0 | 33 | FPGA Engineering Applications | 0.5 | 0.5 |
| 8 | Project Management | 0.9 | 0.1 | 34 | Programming Internship | 0.4 | 0.6 |
| 9 | Pattern Recognition and Applications | 0.9 | 0.1 | 35 | Production Internship | 0.2 | 0.8 |
| 10 | Physics | 0.6 | 0.4 | 36 | Computer Network Technology Internship | 0.3 | 0.7 |
| 11 | Circuit Theory | 0.8 | 0.2 | 37 | EDA Course Internship | 0.3 | 0.7 |
| 12 | Analog Electronic Technology | 0.8 | 0.2 | 38 | Comprehensive Professional Internship | 0.1 | 0.9 |
| 13 | Digital Electronics Internship | 0.4 | 0.6 | 39 | Graduation Internship | 0.5 | 0.5 |
| 14 | Electronic CAD Internship | 0.5 | 0.5 | 40 | Graduation Thesis | 0.3 | 0.7 |
| 15 | Electronic Circuit Internship | 0.6 | 0.4 | 41 | Microcontroller Principles and Interface Technology | 0.8 | 0.2 |
| 16 | Signals and Systems | 0.7 | 0.3 | 42 | Microcontroller Systems Internship | 0.5 | 0.5 |
| 17 | DSP Technology and Applications | 0.7 | 0.3 | 43 | Electronic Process Internship | 0.5 | 0.5 |
| 18 | DSP Course Internship | 0.3 | 0.7 | 44 | Electronic System Design | 0.6 | 0.4 |
| 19 | Communication Principles | 0.8 | 0.2 | 45 | Innovation and Quality Development Elective | 0.2 | 0.8 |
| 20 | Embedded Systems and Applications | 0.7 | 0.3 | 46 | Electronic Systems Internship | 0.2 | 0.8 |
| 21 | Embedded Systems Internship | 0.6 | 0.4 | 47 | Fundamentals of University Computing | 0.8 | 0.2 |
| 22 | Programming | 0.5 | 0.5 | 48 | Computer Programming | 0.5 | 0.5 |
| 23 | Computer Network Technology | 0.8 | 0.2 | 49 | Fundamentals of Microelectronic System Integration | 0.9 | 0.1 |
| 24 | Digital Signal Processing | 0.8 | 0.2 | 50 | Data Structures | 0.9 | 0.1 |
| 25 | Electromagnetic Fields and Waves | 0.7 | 0.3 | 51 | Image Processing Technology | 0.1 | 0.9 |
| 26 | RF Electronic Circuits | 0.7 | 0.3 | 52 | Basic Manufacturing Technology Internship | 0.5 | 0.5 |
| Number of Nodes | Number of Edges | Density | Average Degree | Average Betweenness | Average Betweenness | Average Clustering Coefficient | |
|---|---|---|---|---|---|---|---|
| Before | 356 | 62873 | 0.995 | 353.22 | 1.417 | 0.995 | 0.995 |
| After | 349 | 25132 | 0.4139 | 144.02 | 0.0017 | 0.645 | 0.755 |
| Capability Node | Module | Node Number in the Module | Average Degree Value |
|---|---|---|---|
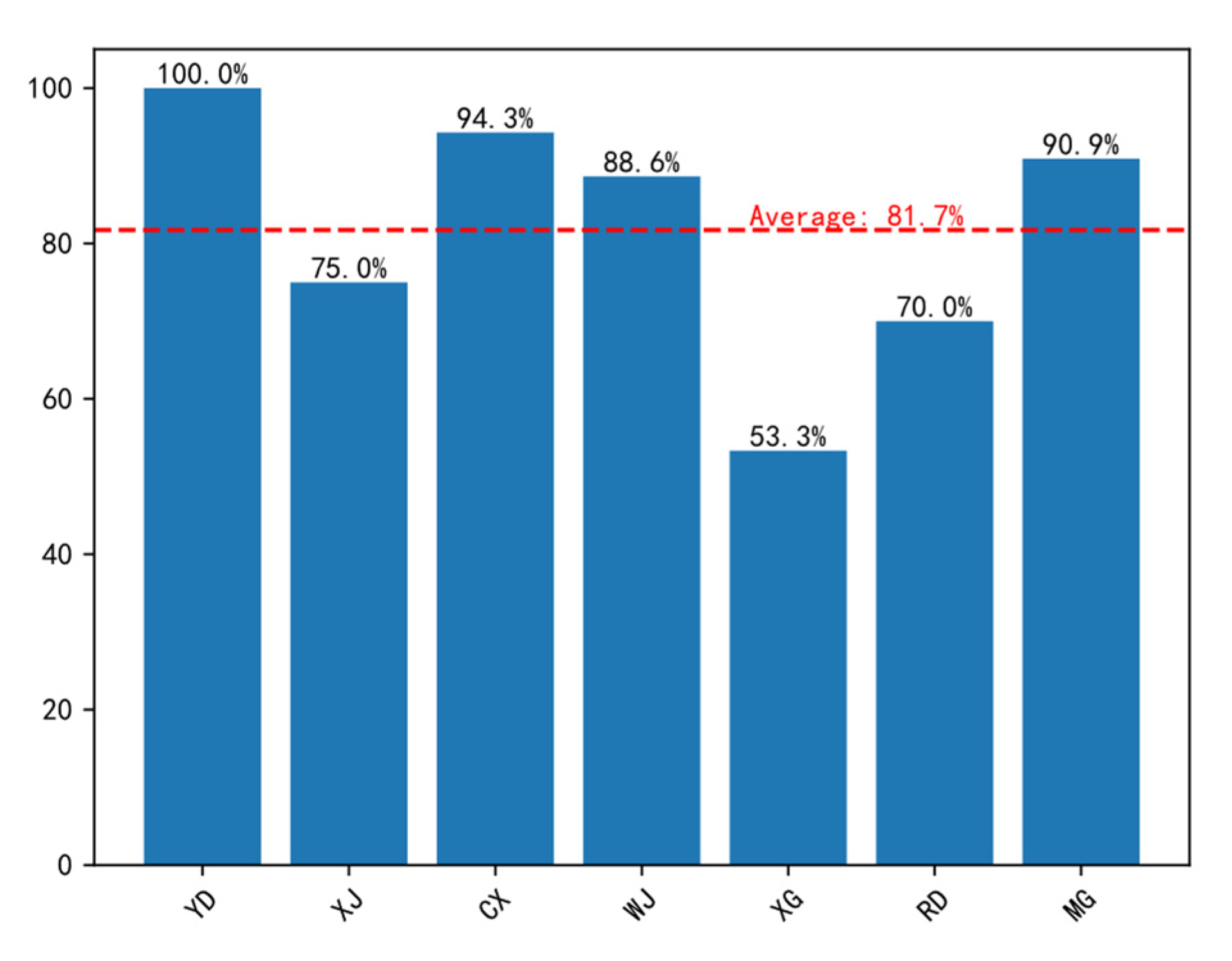
| YD | 1 | 1, 5, 6, 7, 9, 10, 11, 12, 13, 14, 15, 17, 18, 19, 22, 23, 24, 26, 27, 28, 29, 31, 32, 33, 41, 42, 43, 45, 49, 51 | 14.519 |
| XJ | 12 | 1, 5, 6, 7, 11, 12, 14, 15, 16, 17, 19, 25, 26, 27, 28, 30, 31, 32, 33, 38, 39, 40, 42, 49, 51 | 30.41 |
| RD | 17 | 3, 4, 5, 9, 11, 14, 15, 16, 17, 18, 24, 25, 26, 28, 29, 33, 39, 41, 42, 43, 49 | 13.688 |
| XG | 5 | 2, 35, 34, 9, 44, 45, 46, 48, 22 | 7.357 |
| CX | 9 | 1, 2, 4, 5, 6, 10, 11, 12, 13, 15, 16, 19, 21, 22, 25, 27, 28, 29, 30, 31, 32, 33, 34, 35, 37, 38, 39, 40, 44, 47, 48, 49, 51, 52 | 19.53 |
| WJ | 3 | 1, 3, 7, 8, 9, 10, 11, 12, 14, 16, 17, 18, 19, 20, 21, 22, 23, 24, 26, 27, 28, 29, 30, 31, 32, 35, 36, 37, 38, 39, 40, 41, 42, 43, 44, 45, 47, 49, 51 | 24.134 |
| MG | 15 | 2, 8, 10, 42, 44, 13, 45, 47, 50, 21, 23, 29 | 9.429 |
| Module | Node in the Module | Average Degree Value |
|---|---|---|
| 1 | official, borders, share, team, ronaldo, countries, plays, martin, languages, genre, spain, border, uk, new, george, german, cristiano, york, speak, democracy, played | 5.2 |
| 2 | mary, bobby, wife, mexico, roger, die, battle, anne, sisters, flower, federer, hutchinson, called, state, christopher, texas, paris | 4.1 |
| 3 | died, king, adolf, school, james, government | 4.2 |
| 4 | vp, catholic, today, official, borders, greece, holy, type, simpson, matt, currency, married, speak, denmark, kids, new, college, people, language, share, city, play, played | 11.7 |
| 5 | writing, river, shot, zip, united, star, got, map, jordan, wars, chinese, francisco, states, kingdom, fox, darth, code, start, michael, ray, allen, vader, names, located, founded, milk, san, parents | 1.5 |
| 6 | year, harrison, frank, drafted, die, battle, henry, time, texas, antietam | 2.6 |
| 7 | greece, beckham, official, russia, college, johnny, government, depp, david, married, john, kind, today | 3.9 |
| 8 | president, justin, start, party, famous, county, shows, bieber, obama, instruments | 2.2 |
| 9 | use, republic, type, music, country, singapore, currency, john, australia, adolf, school, money, people, government, religion, speak, guitar, switzerland | 7.2 |
| 10 | university, president, died, led, political, split, party, james, die, located, form | 2.8 |
| 11 | use, team, ronaldo, type, george, cristiano, language, speak, guitar, currency, play, played | 16.8 |
| 12 | university, mary, school, movies, luther, king, high, martin | 3.8 |
| 13 | compose, year, style, garcia, music, plays, country, jerry, magellan, kind, come | 3.1 |
| 14 | died, mary, school, married, form, luther, government, ancient, hitler, egypt | 4.5 |
| 15 | cena, pope, new, famous, john, live, happened, state, adams | 5.7 |
| 16 | die, president, died, harrison, henry | 4.2 |
| 17 | turkey, official, borders, share, cook, republic, countries, currency, czech, john, used, guitar, work, dominican, people, speak, tim, switzerland, italy, kind | 7.5 |
| 18 | political, speakers, china, live, king, english, henry, luther, spain, distributed | 3.0 |
| 19 | paul, new, team, movies, ronaldo, george, people, cristiano, york, leader, married, australia, come | 4.0 |
| 20 | beckham, use, team, type, countries, music, country, currency, johnny, movies, people, language, depp, speak, david, play, come, kind, played | 13.7 |
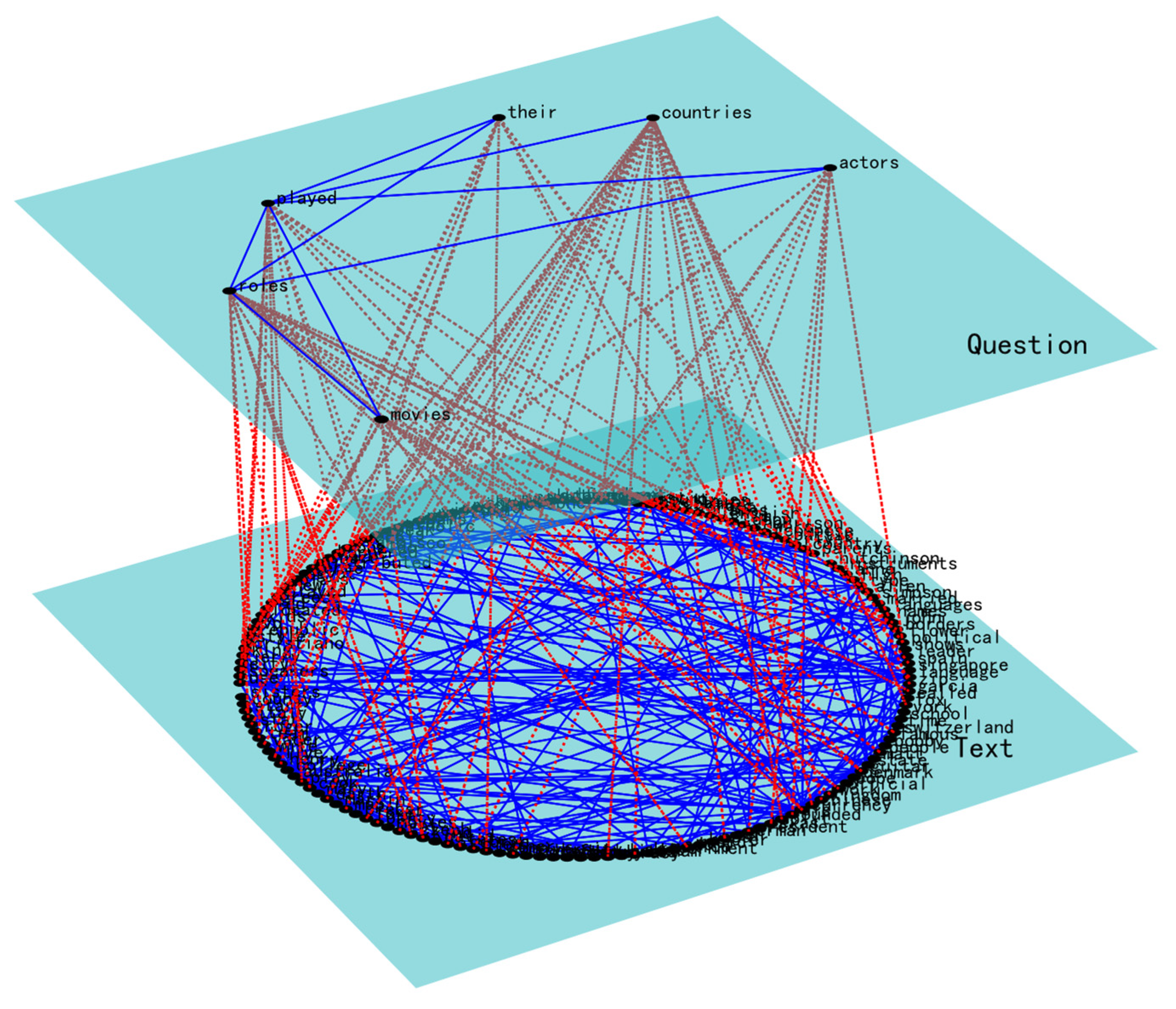
| Dependency Relationship between Competency Network Nodes and Course Network Modules | ||||||
|---|---|---|---|---|---|---|
| Problem Network Nodes | roles | movies | countries | their | actors | played |
| Text Network Modules | Module 28 | Module 11 | Module 1 | Module 5 | Module 30 | Module 25 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zou, Q.; Yan, L.; Gong, Y.; Hou, J. Predicting Dependent Edges in Nonequilibrium Complex Systems Based on Overlapping Module Characteristics. Systems 2024, 12, 433. https://doi.org/10.3390/systems12100433
Zou Q, Yan L, Gong Y, Hou J. Predicting Dependent Edges in Nonequilibrium Complex Systems Based on Overlapping Module Characteristics. Systems. 2024; 12(10):433. https://doi.org/10.3390/systems12100433
Chicago/Turabian StyleZou, Qingyu, Lin Yan, Yue Gong, and Jingfei Hou. 2024. "Predicting Dependent Edges in Nonequilibrium Complex Systems Based on Overlapping Module Characteristics" Systems 12, no. 10: 433. https://doi.org/10.3390/systems12100433
APA StyleZou, Q., Yan, L., Gong, Y., & Hou, J. (2024). Predicting Dependent Edges in Nonequilibrium Complex Systems Based on Overlapping Module Characteristics. Systems, 12(10), 433. https://doi.org/10.3390/systems12100433





