1. Introduction
Adapting to new market demands forces organizations of all sizes, from small businesses to large corporations, to continually renew their revenue-generating mechanisms through product/service innovations, better strategies, and innovative business models [
1]. The digital age requires companies to invest in value-added projects rather than routine activities to leverage innovation as a competitive edge and business success [
2]. Process management must be designed around these business and compliance requirements, which are subject to a compromise between IT systems and business practices. Business Process Management (BPM) includes methods, techniques, and technologies to continually adapt and improve business processes by identifying, prioritizing, analyzing, and iteratively monitoring [
2]. In this context, characteristic improvement goals include reducing costs, shortening execution times, and reducing error rates [
3]. BPM is at the intersection of IT and business, enabling companies to manage digital innovations and transformations. While changing technology, they also pose challenges in the context of BPM [
1]. An identified problem with current BPM solutions is that they need to leverage the amount of data to understand the most challenging aspects of a BPM system, what task to execute, when the task must be completed, and who will solve it. Researchers and practitioners suggest that BPM should be progressively optimized and automated [
4].
Speed is one of the most critical factors to staying competitive in today’s challenging business conditions. The commissioning of software robots with Robotic process automation (RPA) has become one of the most essential and fastest-growing technologies in recent years [
5,
6]. RPA is a technology for performing routine business processes by automating how people interact with multiple applications or analytics through a user interface and following simple decision-making rules [
7]. RPA can benefit from artificial intelligence and machine learning capabilities to tackle high-volume, repeatable tasks that previously required only humans to perform [
4,
8]. It uses software bots that can be considered digital workers, each using its computer station, username, and password, similar to a human worker [
9].
The acceleration in the business context makes it even more challenging to predict what changes will occur and how they might affect the technological solutions used in increasingly automated business processes. It has been argued that immature or poorly trained models can eventually reduce productivity and increase errors due to unsupported or wrong decisions [
4,
10]. RPA has been widely adopted in many industries to automate well-defined and repetitive tasks [
6]. Gartner forecasted RPA software end-user spending to reach USD 2.9 billion in 2022, up 19.5% from 2021 [
11]. Because of its ease of use, the RPA revolution is taking place in the business operation groups of many companies active in financial services, healthcare, telecommunications, higher education, and energy [
12]. Regarding RPA adoption, a survey of the top 25 global RPA service providers benefiting from 5800 customer deployments revealed that finance and accounting are the leading areas of RPA application, accounting for 36 percent of all RPA use cases [
13]. Early adopters of RPA see that automation can radically transform the back office, improving service quality, increasing compliance, and reducing lead times while delivering much lower costs [
14].
To understand the importance of RPA risk assessment, one can also look at it in the context of Industry 4.0, a popular topic in recent years. In Industry 4.0, creating efficient, intelligent, and interconnected systems is essential. One of these systems is the automation of processes using RPA technology. Assessing the potential risks and vulnerabilities of the developed systems is as important as developing the systems. Companies assess risks such as process stability, data security, and integration difficulties through various methods (one of which is discussed in this study). This can ensure that RPA improves operational efficiency and seamlessly connects with other advanced I4.0 technologies such as IoT, AI, and big data analytics. This combination will better prepare firms for the complexity of autonomous systems while maximizing the benefits of automation and reducing unintended disruptions [
15].
Despite the widespread adoption of RPA worldwide, RPA adoption challenges are multidimensional in their technical, strategic, operational, and human aspects [
16]. According to EY research, 30% to 50% of first RPA projects fail. For example, robots used in the complaint process caused a pile of complaints due to coding errors, and robots used in the accrual process caused significant under-reporting of accruals due to incorrect rule set definitions in bots [
17]. As automation is rolled out across the industry, many examples of non-performance issues are a gray area for the deployment and investigation of technology causes [
18]. Because of this, potential risks need to be considered.
This study applied decomposed fuzzy failure mode and effect analysis (DFS-FMEA) to compute the risk assessment of RPA. Failure mode and effect analysis (FMEA) is one of the most widely used risk assessment methods. In this study, risk assessment was carried out for the first time by integrating the FMEA method with decomposed fuzzy sets (DFSs). According to the logic of DFSs, a question is asked to the decision-maker for evaluation. The answer received from the decision-maker may change depending on whether the question is optimistic or pessimistic. That is, a question with the same meaning can be asked in two different ways: optimistic or pessimistic, and the decision-maker’s answer may change accordingly. With DFS-FMEA integration, questions about the three primary parameters of FMEA (Severity, Occurrence, and Detectability) are asked of the decision-makers from an optimistic and pessimistic perspective, and a more accurate assessment is carried out by obtaining more information from the user.
The remaining part of this paper is as follows:
Section 2 summarizes the background of RPA and its benefits, and
Section 3 identifies potential risks in detail with a fishbone diagram.
Section 4 explains the methodology, including the decomposed fuzzy sets and decomposed fuzzy set-based FMEA.
Section 5 presents a case study of six processes executed by RPA. It evaluates the risk assessment of digital robots’ implementation with the DFS-FMEA method.
Section 6 discusses the results of the DFS-FMEA method over the selected six processes. Finally,
Section 7 concludes the paper.
2. Background
RPA is the technological revolution that aims to take mundane and repetitive tasks from people’s daily workloads [
19]. It frees up employees from tedious tasks and enables them to focus on more diverse, challenging, and valuable work [
14]. It makes human creativity and ingenuity available for higher-value tasks that require decision making [
4]. Much has been predicted about the effects of automation on the nature of human work. Some experts feel that automation will leave people with few tasks besides lawn mowing and hairdressing [
12].
RPA benefits companies, customers, and employees in many departments, such as purchasing, manufacturing, human resources, sales, and marketing [
15]. Many large and small companies appreciate that RPA reduces human labor needs, shortens transaction times, and easily interfaces with foreign systems, which is valuable for their profitability [
11]. According to the Deloitte 2017 global robotics survey of over 400 responses, 85% of respondents reported that RPA continues to exceed their expectations in non-financial benefits such as accuracy, timeliness, flexibility, and improved compliance. In addition, 61% reported meeting cost reduction expectations, emphasizing that it moves people to higher-value activities that lead to higher job satisfaction [
20].
RPA works well with identifiable, repeatable, and rule-based processes in all industries. It allocates significant work hours to tasks performed by software robots. Automation tracks and documents every IT or business process step within an automated system. This way, the company can better comply with industry and audit regulations. A software robot can work twenty-four hours a day, seven days a week, 365 days a year, thus increasing productivity. It enables better decision making when the data of each task the robot executes are analyzed. As software robots take care of repetitive, tedious tasks in a business, employees can engage in more value-added activities [
11]. According to Lacity et al. [
14], one of automation technology’s main benefits is increasing work accuracy and efficiency. Automation technology has the ability to increase productivity and make the business process more efficient and accurate [
21]. When a process is adequately optimized, and all its sub-processes are mapped correctly, software robots do not make mistakes that their employees can make, so they can completely eliminate them [
11]. The fact that all actions for RPA are standardized ensures consistency [
22].
The alleged benefit of RPA’s ease of implementation leads firms to adopt RPA to generate a rapid return on investment (ROI) [
23]. While traditional IT projects take months or even years, a standard RPA implementation happens faster. Therefore, the return on investment is much faster [
5]. According to the case study results of Lacity et al. [
12], it automates approximately 20 to 25 percent of back-office work related to meter management, customer invoicing, account management, consumption management, and segmentation, resulting in a return on investment in an average of 200 percent in 12 months.
Based on the literature about RPA process selection, the challenges encountered are summarized as selecting the right processes to automate; lack of RPA professional talent; reputational damage to the organization, both outside and within itself; and security. Figueiredo and Pinto [
24] conducted semi-structured interviews with RPA project managers to address robotization’s main challenges and implications in shared service centers. The findings indicate that the main challenges in implementing RPA are concentrated in two main areas: (1) lack of resources, such as software management and development, to perform robotization tasks, and (2) insufficient internal training to develop these solutions. Flechsig et al. [
25] studied using RPA in purchasing and supply management. In-depth, semi-structured expert interviews were conducted with experts from different levels in purchasing and IT departments, covering 19 organizations from the public and private sectors. The findings indicate that barriers to using RPA in purchasing and supply management include technical, organizational, and environmental factors such as internal communication, financial resources, top management support, infrastructure, human resources, organizational structures, supplier issues, and government regulations. Wagar et al. [
26] studied the primary economic, technological, regulatory, privacy, and resource constraints to using RPA for tall-building safety management. Data were collected from tall-building experts through semi-structured interviews and surveys. The findings of the analysis showed that all factors, except resources, significantly influence RPA adoption. According to the path analysis findings, legislation was the most influential factor, followed by concerns about privacy, technological advancements, and economic factors.
As for risk assessment, Gotthardt et al. [
27] conducted literature-based and case study-based research on the challenges encountered in successfully implementing RPA in accounting and auditing. The risk categories determined from implementing RPA systems evaluated with artificial intelligence were evaluated under two headings: business and automation risks. Business risks were categorized as technical, functional, operational, executive, and change management, while automation risks were categorized as center of excellence, proof of concept, backward compatibility, implementation, and business case. Patri [
28] investigated banks’ main challenges in adopting RPA and provided suggestions for avoiding these challenges. Gao and Kuang [
7] investigated how RPA technology for Risk Data Analysis can be used in customs post-clearance auditing. They discussed the challenges and benefits of its integration into customs management and explained RPA’s application values within the scope of a framework model. Eulerich et al. [
29] interviewed 26 experts to identify the risks and challenges associated with RPA, and the findings were verified with the company’s external auditors. Five main challenges were identified regarding using RPA: implementation as a band-aid, control and security issues, cost, management, and the loss of information it causes. Yendluri et al. [
30] explored RPA risk management, highlighting the challenges, trends, and strategies organizations need to integrate RPA successfully into their operations. Risks in RPA are explained under three headings: technical, operational, and business risks. Additionally, explanations regarding risk assessment were presented. Schlegel et al. [
31] used data from 20 subject matter experts to rate the impact and controllability of risks associated with key factors in RPA projects and investigated the risks associated with RPA projects. A two-dimensional risk severity matrix was used to assess risk factors. The factors with the highest impact on the success of RPA projects were rated as “RPA development” and “process management”.
The main contribution of this work to the literature is based on the assessment of risks in RPA by integrating discretized fuzzy sets (DFSs) with failure mode and effect analysis (FMEA). Considering the similar studies summarized, it is evident that there are many previous studies involving RPA applications. However, despite the many positive outcomes of RPA, there may be some risks involved. For a successful RPA implementation, it is necessary to assess the risks as well as the benefits of RPA. The proposed unique risk assessment methodology addresses both the optimistic and pessimistic perspectives of decision-makers, enabling a more detailed and precise assessment of risks. To test the method, 13 potential risks were identified in six automated processes in the context of smart university studies.
3. Potential Risks
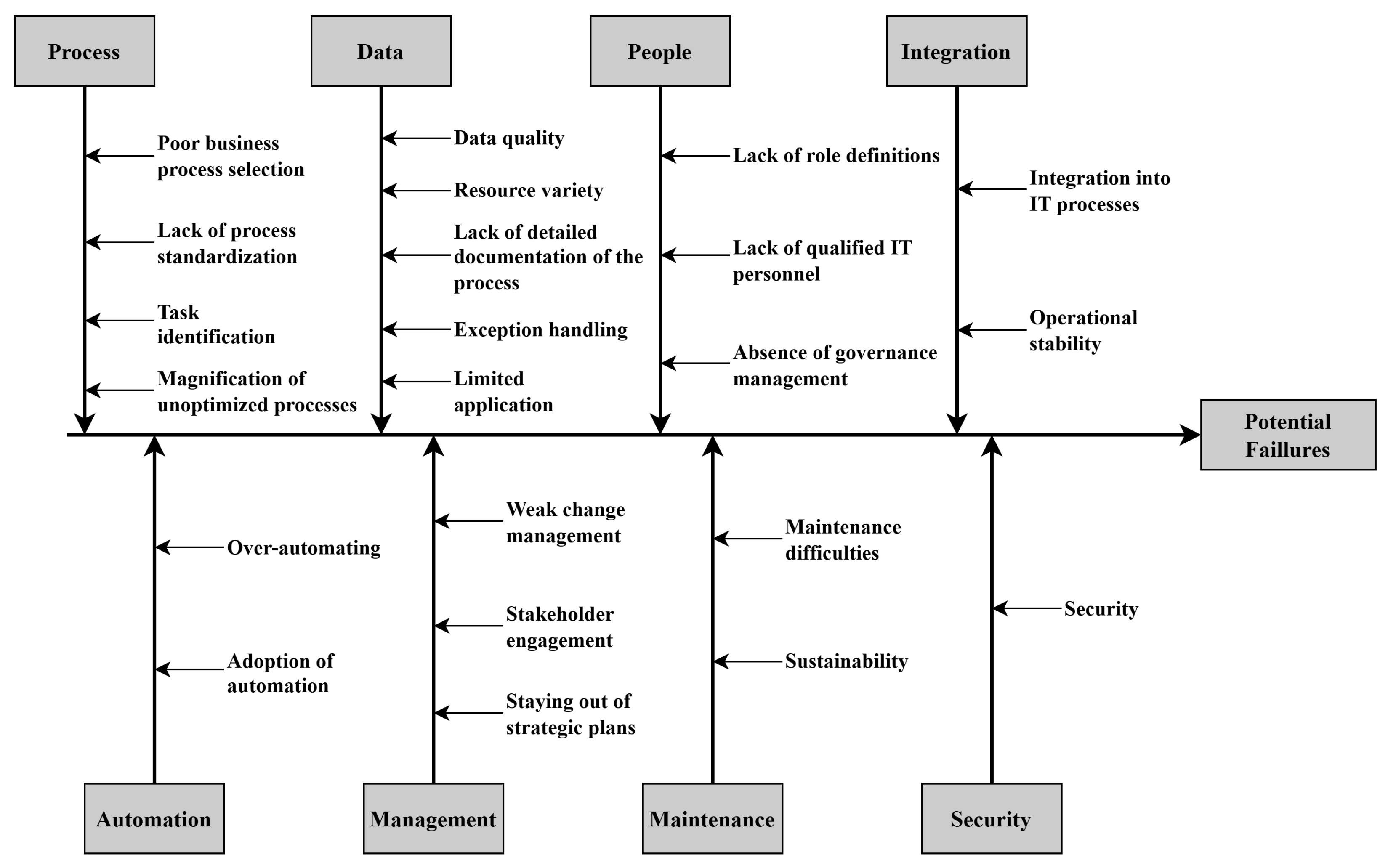
Implementing RPA may require significant changes to an organization’s business processes, which can be disruptive and costly. Additionally, the lack of standardization and detailed documentation of the process may lead to difficulties in designing and implementing RPA. Regarding automation, over-automating or automating poor processes can result in suboptimal automation that fails to deliver the desired outcomes. RPA may decrease job opportunities, particularly for roles that involve repetitive, rule-based tasks. Regarding data, RPA can cause data security and privacy concerns if the bots are not developed and managed appropriately. Also, the standardization of data from various sources may pose challenges during implementation. Change management can be another potential risk. RPA may require significant investment in time, money, and human resources, which can challenge organizations needing more skills and expertise. Furthermore, stakeholder engagement, staying aligned with strategic plans, and weak change management can hinder successful RPA implementation. People-related risks include a lack of qualified IT personnel, an absence of governance management, and a lack of role definitions. These issues can lead to ineffective RPA implementation, poor maintenance, and suboptimal performance. Maintenance and integration are other potential risks, as RPA requires consistent monitoring and maintenance to ensure it continues functioning effectively. Moreover, integration into IT processes can be complex and require significant effort. Finally, RPA may expose an organization to security risks, including the risk of cyber-attacks, data breaches, and other vulnerabilities. Thus, ensuring that RPA implementation is secure and well protected is crucial.
A comprehensive literature review was conducted to identify potential failures in RPA implementation using keywords such as “RPA failures”, “RPA risks”, and “RPA implementation challenges”. The studies obtained examined general challenges and risks in RPA implementations. By evaluating the common points of the studies, the risks were categorized under eight main headings: “Process”, “Data”, “People”, “Integration”, “Automation”, “Management”, “Maintenance”, and “Security”. This categorization reflects the general trends in the literature and provides a better understanding of the complex structure of RPA applications.
Figure 1 shows a fishbone diagram of RPA implementation failures. The failures in each category are similar in terms of the underlying issue that caused them.
The process category includes failures related to the process itself, such as poor selection, lack of standardization, and difficulty identifying tasks.
Poor business processes selection: One of the biggest challenges of RPA projects is to choose the most suitable automation processes [
32]. So, business executives need to understand that RPA cannot automate all processes. Therefore, choosing the right processes for RPA can be challenging. RPA is best suited for routine, rule-based, and uniform processes. It is also suitable for tasks without much judgment and with low exception rates. Additionally, RPA can be used to carry out control activities that employees currently perform due to time or resource constraints. Processes that do not meet these criteria will not be appropriate for RPA and will not provide enough benefits to justify the investment [
22].
Lack of process standardization: Standardized processes play a significant role in the high-performance operation of units. It is essential to have clear rules and ideal sub-processes for automation. RPA needs precise instructions and regulations. According to Lacity et al. [
12], RPA works best on standard processes. Not standardizing the processes well is one of the difficulties in implementing RPA [
33].
Task identification: Task definition provides complete stability to RPA’s workflow and workload. Some processes to be selected for automation require specific conditions. For example, for an RPA application to be used in the audit process, well-defined procedures are structured and not subjective. In this way, the RPA application can complete tasks based on clear, rule-based instructions [
6].
Magnification of unoptimized processes: The idea may seem obvious, but it is important to emphasize that optimizing inadequate processes will result in unsatisfactory automation. RPA should not only be utilized to automate repetitive and rule-based processes but also to enhance processes through automation. To achieve this, inefficiencies, gaps, and wastage should be carefully examined and resolved during the design phase of the RPA candidates. The RPA project must produce durable, top-notch automation that will not constantly fail and diminish the anticipated business value it will provide.
The automation category includes failures related to automation, such as over-automating and failure to adopt automation properly.
Over-automating: In today’s world, organizations are increasingly pushing for automation to improve operational efficiency and reduce costs. The pandemic and the associated surges in supply and demand intensified this desire. Automation was seen as a primary solution to manage this volatility. However, the haste to automate has resulted in a common pitfall when design and development are rushed—brittle automation is prone to breaking. To prevent this, automation requires a deliberate and thoughtful design approach that prioritizes process improvement before delivery. Additionally, the process must be linked to all relevant dependencies to enable better governance and change management.
Adoption of automation: The sustainability and success of automation, which has an important place in today’s world, are directly related to the adoption of this technology. RPA enables businesses to increase productivity by automating their routine work. However, considering the human factor and its benefits, its adoption can cause difficulties. Considering the costs, the system working improperly places operating efficiency and profitability at risk. Employees’ fear of losing their jobs hinders the adoption of automation [
33].
The data category includes failures related to data, such as poor data quality, limited resources, and lack of documentation or handling of exceptions.
Data quality: Data accuracy is essential in the automation process, as in all systems. Incorrect data that RPA will use will produce erroneous results. This will cause businesses to make wrong decisions. At the same time, problems in the data source can slow down the RPA process. Robots can operate unexpectedly when data contain logical or semantic errors [
34].
Resource variety: Using data from different sources for RPA can cause data compatibility issues. Data diversity requires the necessary integrations for RPA to process these data. The need to standardize data from various sources is one of the challenges [
19]. RPA’s ability to process data from different sources can pose a risk depending on the infrastructure and integrations required.
Lack of detailed documentation of the process: Detailed process documentation of businesses provides detailed information about business processes. The RPA lifecycle begins with the analysis phase, in which a clear understanding of the process documentation is obtained [
9]. Failure to present the processes in detail may cause RPA robots to execute incomplete or faulty processes. A complete design of RPA robots can be achieved with detailed process documentation.
Exception handling: Exception handling is essential in scripting at all stages of the RPA lifecycle [
35]. Unexpected errors or problems during the RPA process pose a risk to RPA. These errors can prevent the system from working correctly and cause a waste of time.
Limited application: The automation decision depends on the cost–benefit analysis of the specific process and its requirements. Some documents, including complex data such as images, audio, and video, require partial automation. Putting cost and time into partial automation may not be reasonable.
The management category includes failures related to managing human resources and change, such as weak change management, poor stakeholder engagement, and not considering strategic plans.
Weak change management: Insufficient change management can negatively impact the successful implementation of RPA within an organization. The integration of new software and technology necessitates the transformation of employee roles and business processes. Proper communication with employees about the inevitable changes in workflows and processes is essential to avoid confusion. Business leaders must recognize that RPA will have varying effects on different employees, potentially resulting in differing levels of job satisfaction. Additionally, employees may require additional training and skill development to adapt to RPA. Failure to adequately support and understand employees during the implementation process may lead to an inability to keep up with the changes [
36].
Stakeholder engagement: Stakeholders play an essential role in all processes, from the analysis to the implementation of the RPA process. Without stakeholder participation, RPA cannot be adequately designed, and problems are encountered during the implementation phase. At the same time, not adopting RPA applications disrupts business processes.
Staying out of strategic plans: Although RPA has the potential to enhance innovation and improve competitiveness, organizations often set unrealistic goals and misuse them for isolated areas, resulting in RPA failing to deliver on its promise. Instead of using RPA to innovate and improve work, some organizations solely use it to cut down spending by reducing FTE headcount, lacking any strategic intent or end-point design in their RPA projects. This under-resourcing of RPA initiatives can lead to risks associated with the RPA strategy. To mitigate these risks, organizations must implement a solid, future-proof target operating model and intelligent process automation tools.
The people category includes failures related to people, such as lack of role definitions, qualified personnel, and governance management.
Lack of role definitions: Operational risks in RPA implementation can arise if proper operating models are not defined. Rushing into training without defining roles can blur responsibilities when the bots go into production, leaving human RPA supervisors confused about their actual roles. To mitigate such risks, enterprises must have a well-defined operating model and clear role definitions [
37].
Lack of qualified IT personnel: IT personnel is one of the most important stakeholders involved in all processes, from the construction of RPA applications to their implementation. IT staff support is required at every stage of the process. Employees engaged in RPA processes are available as those who build and maintain it and those who use the implementation results [
38]. The lack of qualified IT personnel here can cause problems such as lodging, maintaining, and managing RPA applications.
Absence of governance management: A well-defined governance model is crucial for effective automation design. To this end, many organizations have established their own RPA Centers of Excellence, which are responsible for defining the governance model. To minimize risk downstream, it is important to have defined processes for identifying, assessing, validating, and prioritizing RPA opportunities. The standardization of automation work is also essential through templates and guidelines that follow best practices [
9]. This ensures continuous improvement through lessons learned and avoids costly mistakes being repeated.
The maintenance category includes failures related to maintenance, such as sustainability problems and difficulties with maintenance.
Maintenance difficulties: The maintenance of RPA solutions is an essential aspect that must be considered to ensure the long-term sustainability of the implementation. As RPA solutions are designed to perform repetitive and rule-based tasks, they require regular maintenance to ensure optimal performance. Failure to initiate maintenance protocols can result in technical issues and difficulties that may become more challenging to resolve over time. Therefore, organizations must establish maintenance protocols and schedules to keep their RPA solutions up to date and functioning effectively. This includes regular monitoring, updates, and upgrades to ensure that the RPA solutions are aligned with any changes in business processes and technology.
Sustainability: Sustainability risks can also arise due to a lack of maintenance and support for the RPA system. As organizations continue to scale up their RPA deployments, maintenance and support become critical factors for ensuring the continued success of automation initiatives. Without proper maintenance and support, the RPA system can become outdated and fail to meet changing business needs, resulting in decreased efficiency and productivity. To mitigate these risks, organizations should establish clear processes for ongoing maintenance and support of the RPA system, including regular updates and upgrades to the software, as well as the continuous monitoring of system performance and user feedback. Additionally, having a dedicated team responsible for managing and maintaining the RPA system can help ensure that the system remains up to date and effective in meeting business needs.
The integration category includes failures related to integration, such as problems with integrating into IT processes and lack of operational stability.
Integration into IT processes: The complete integration of RPA applications into IT processes prevents problems in business processes. Integration is critical in ensuring data security. Data integrity provided by integration into IT processes increases the security of sensitive data processed by RPA. Management and maintenance problems may arise if RPA applications do not integrate with IT processes. This problem risks the stability and correct operation of RPA applications.
Operational stability: Operational instability can be caused by factors such as improperly designed, misconfigured, or poorly tested RPA applications and integrating RPA applications into business processes. The incompatibility of RPA applications with other systems may cause interruptions to processes. Lost link principles in RPA processes appear to be a challenge to be considered for operational stability [
39].
The security category includes failures related to security. RPA bots can create, manipulate, and access large amounts of data. However, if the data are not properly secured, they can be accessed and used by unauthorized personnel. Organizations must take steps to ensure that sensitive data are encrypted and that bots can only access data that are necessary to perform their tasks. Lack of proper data governance and management can also lead to errors and inaccuracies in data processing, negatively impacting the organization [
6,
14,
23].
5. Case Study
5.1. Processes
Izmir Bakircay University is a young and visionary university in Turkiye. The smart campus and digital transformation office, one of the university’s coordinatorships, manages intelligent and digital projects. They utilize RPA technology to automate processes under digital transformation projects. The six selected processes for this study were performed at Izmir Bakircay University. Understanding process details enables readers to interpret their risks.
The main reason for choosing a university case study in this study is that universities offer an ideal environment for RPA implementation due to their complex processes, propensity for digital transformation processes, and data richness. Examining the processes in different university units has increased the study’s general validity by revealing the diversity of risks that can be encountered in RPA applications.
Risk assessment in RPA applications is critical for success, as it identifies potential problems in advance. An incorrect risk assessment can lead to severe consequences such as data loss, process interruptions, and security breaches. A systematic approach to risk assessment, such as the DFS method used in this study, helps minimize such risks. In addition, risk assessment results allow managers to make more informed decisions regarding RPA projects, ensuring more efficient use of resources.
Process experts were selected from among those with in-depth knowledge of the processes under study and experience in risk analysis. Criteria such as having worked in the relevant field for at least five years and having participated in more than ten risk analysis projects were considered. In this way, the reliability of the obtained data was increased.
The process of the scholarship payment process (P1): One employee prepares scholarship payment documents. Project coordinators fill out the application form and submit it with a wet signature at the end of each month. In some cases, project coordinators may require memorization to fill in a mandatory field or enter incorrect details, which can lengthen the cycle time of the process. The responsible employee creates three forms from four sources using the application form. Whereas the same fields are placed in each document, some individualized data such as identity number, name and surname, student number, project ID, and project name must also be included. It takes over two working days to prepare 54 documents for 18 scholarships.
The process of course addition and the branch opening process (P2): Courses and course programs are entered into the system at the beginning of each semester at the Graduate Education Institute. The details of the courses are collected from departments in an Excel file. Then, two employees working together define them in the university information system in six days.
The process of reporting the decisions to the board members and their implementation in the university information system (P3): The council at the Graduate Education Institute plans regular weekly meetings to discuss the applications coming from students. Before the meetings, one employee collects the applications in a standard format and prepares agenda items for the board members. After the meetings, each decision is entered into the university information system individually. Some of the council decisions involve the preparation of records for each department regarding the assignment of academic advisors to registered students at the beginning of each semester, as well as any changes made to academic advising based on student requests during the semester, the suspension of registration, the removal of registration, etc. In assuming that approximately 20 decisions are made at each council meeting, it takes two employees working together 140 min to report decisions to the board members and enter the decisions into the university information system for a weekly meeting.
The process of personalized document preparation and mailing (P4): Each department prepares a compulsory internship certificate for students to present to the companies before their internship. The compulsory internship certificate includes personalized data such as the student’s name, surname, number, department, and academic coordinator’s name, surname, and signature. After the department coordinator prepares the certificate they email it to the student. Approximately 240 students in the engineering faculty need internship certificates prepared every semester, leading to the ineffective use of time and human resources and some potential failures.
The process of reporting applications to the ethics committee preparation and archiving decisions (P5): The medical faculty plans regular weekly meetings to discuss researchers’ applications related to personal data use permission for research. One employee collects the three hard copy application forms. Then, they prepare the agenda items for the committee members. After the meetings, each decision is entered into the university information system individually, and the applicant is informed by email with the committee’s decision letter. Finally, each decision is archived with a unique code represented by a timestamp and the applicant’s surname.
The process of accident insurance payments for internship students (P6): Some departments have short- and long-term internships. The faculties must consider the occupational health and safety of students. Because of this, one faculty employee collects student application forms from the departments at least two weeks in advance. They check the information on the application forms from different official websites. If a mistake is found, the student is informed. The student data are entered into the ministry’s system if everything is correct. The responsible employee must check the ministry’s system every Friday to determine whether the students have a medical report because the accident insurance must not be paid for the days the student did not go to work. Otherwise, the faculty must pay a fine. The process is open to mistakes because the internship period is flexible between specific dates.
5.2. DFS-Based FMEA
The evaluation data for the DFS-based FMEA method were obtained through interviews with three process specialists involved in the process design and experienced in risk analysis. For the first step, the process specialists identified potential risks in RPA implementations using the nominal group technique and literature review.
A moderator with expertise in group decision-making and risk analysis managed the data gathering and evaluation process. The nominal group technique is a structured method used to facilitate group decision making and idea generation, ensuring equal participation from all members. The process begins with the facilitator introducing a problem or topic, followed by a phase where participants independently and silently generate ideas. These ideas are then shared in a round-robin format, allowing each participant to contribute without interruption or criticism. After all ideas are presented, the group discusses and clarifies each idea. Participants then individually rank or vote on the ideas, often using a ranking or point system to prioritize them. The highest-ranked ideas are selected for further consideration. The nominal group technique is effective for generating diverse input, avoiding groupthink by fostering independent idea generation, and enabling structured decision making through consensus building. It is commonly used in fields such as risk assessment and strategic planning. The determined potential risks in RPA implementations are given in
Table 2.
In the second step, the process specialists obtained linguistic evaluations of the Occurrence, Severity, and Detectability of the risks separately for each process. In accordance with the DFS logic, the decision-makers were asked two different questions, optimistic and pessimistic. The process specialists’ assessments of potential risks in RPA are given in
Table 3. The linguistic evaluations were transformed into fuzzy triangular numbers using the scale in
Table 1.
In the third step, the analysis process was started after the data collection process. Since each process specialist presents their preferences separately, the DWGM operator given by Equation (
7) was used to aggregate process specialists’ assessments to obtain a co-decision matrix.
Table 4 shows the co-decision matrix. Then, the risk priority numbers of each risk under each process were obtained using the multiplication operator defined in Equation (
3).
Finally, each process’s CI and SI values are calculated utilizing Equations (
8) and (
9), respectively. In using the multiplication operator defined in the DFS in Equation (
2), the three basic parameters of FMEA, the Severity, Occurrence, and Detectability values, are multiplied, and the risks are ordered according to their magnitude.
Table 5 presents the risk priority numbers in fuzzy triangular numbers for each risk under each process.
7. Conclusions
If organizations make appropriate provisions against potential risks, unfavorable effects can be prevented, and the advantages of RPA can be utilized at the highest level. It is an issue that needs to be considered, as RPA solutions require regular maintenance to ensure their long-term sustainability. Lack of maintenance and support poses significant risks to the sustainability of RPA solutions. Transparent processes must be established to mitigate these risks, and its performance constantly monitored, including regular updates and software upgrades. Managing the RPA system through a dedicated team will ensure that the system remains effective. Such measures will help ensure the sustainability and long-term success of RPA solutions. Governance management includes critical processes such as identifying, validating, and prioritizing RPA opportunities. Lack of governance management brings risks such as setting wrong priorities, automating inappropriate processes, and creating security vulnerabilities. A well-defined governance model is essential for the success and sustainability of automation projects.
Process failures such as poor process selection, lack of process standardization, and the magnification of unoptimized processes will cause programming errors, and thus erroneous decisions, as well as increased process inefficiencies. To adopt the RPA approach, process standardization and process maturity rules must be high. Considering the human factor, which is directly influential in the sustainability and success of automation, there may be difficulties in its adoption. Fear that robots will replace workers’ jobs hinders automation adoption. RPA, while capable of handling increased workloads, poses a risk of displacing human workers. Although some vendors argue that RPA eliminates redundant work, the truth is that some employees were previously responsible for those tasks. This can cause concern for those affected and affect the public’s perception of the organization’s business practices.
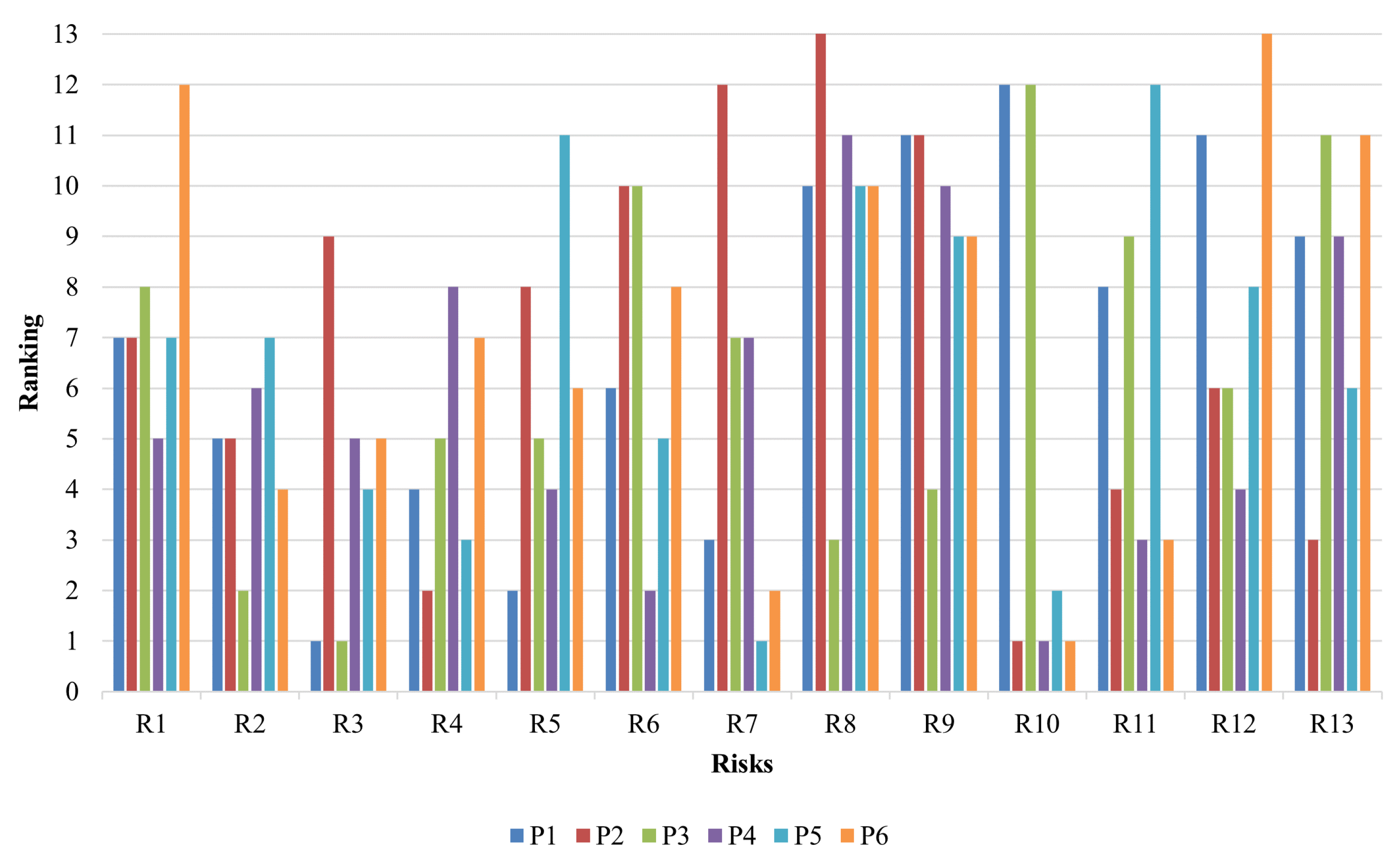
RPA implementers should consider all these potential risks for more successful implementations because RPA is not a cheap technology like other advantageous applications. This paper proposes a novel method, decomposed fuzzy set-based failure mode effect analysis (DFS-FMEA). A DFS is an extension of the intuitionistic fuzzy set that considers both the optimistic and pessimistic perspectives of the decision-makers. As a result, the decision-maker’s indeterminacy is defined by their response to both the positive and negative inquiries on the same issue, and the approach takes this inconsistency into account while assessing them. It differs from other fuzzy extensions. This study integrated the FMEA method with DFSs, and 13 potential risks were identified and evaluated under six automated business processes. The importance degrees of the considered risks differ considerably in processes based on their vulnerabilities. In P1 and P3, for example, the “absence of governance management” risk (R3) appears to be the greatest risk. On the other hand, the sustainability problem risk (R10) is the most critical risk for P2, P4, and P6. Furthermore, in P5, security risk (R7) is the most important risk. When considering the rankings for all processes, R3 is the most significant risk, while “staying out of strategic plans” (R8) is the least significant risk. The absence of governance management (R3) is followed by sustainability (R10), magnification of unoptimized processes (R2), and over-automating (R4). Risk reduction methods should be used largely for R2, R3, R4, and R10 hazards to manage risks effectively.
Finally, this study emphasizes the critical implications of effective governance management in successfully implementing RPA solutions. Our findings suggest that organizations must prioritize establishing transparent processes to mitigate risks associated with RPA, particularly regarding governance management, which encompasses identifying, validating, and prioritizing RPA opportunities. The results indicate that the absence of governance management is the most significant risk, highlighting organizations’ need to adopt a well-defined governance model to ensure sustainable automation practices.
From a managerial perspective, our research underscores the importance of the regular maintenance and monitoring of RPA systems to prevent unfavorable outcomes and maximize the benefits of automation. Organizations should invest in dedicated teams to oversee RPA performance, ensuring continuous updates and adaptations to changing business needs. By doing so, companies can address concerns regarding employee displacement and the fear of job loss, facilitating a smoother transition to automation.
Moreover, our findings contribute to the discourse on employee–robot substitutability by illustrating that while RPA can enhance operational efficiency, it also poses risks of displacing human workers. This dual nature of RPA necessitates implementers to consider the human factor in their strategies, recognizing the potential resistance to automation driven by fears of job redundancy. Addressing these concerns is crucial for fostering an organizational culture that embraces change rather than fears it.
The integration of the decomposed fuzzy set-based failure mode effect analysis (DFS-FMEA) into our risk assessment framework offers a novel methodological approach for identifying and evaluating risks associated with automation. By considering optimistic and pessimistic perspectives, our DFS extension provides a more nuanced understanding of decision making under uncertainty. Identifying 13 potential risks across six automated business processes lays the groundwork for future research to explore targeted risk reduction strategies.
The proposed study’s limitation is that the scope of our analysis was confined to specific automated business processes, which may limit the generalizability of our findings to other contexts. Additionally, relying on expert judgment in identifying and evaluating risks may introduce subjectivity, warranting further validation through empirical research. Future studies could expand the application of the DFS-FMEA framework to a broader range of industries and processes, enhancing our understanding of RPA risks across various settings.
In conclusion, this study not only highlights the importance of governance and risk management in RPA adoption but also contributes to the understanding of employee–robot substitutability. By articulating these implications clearly, we aim to guide both academic inquiry and practical applications in the automation field.