Abstract
The digital transformation age introduces cybersecurity threats into the hospitality industry by increasing the exposure and vulnerability of hospitality firms’ data and systems to hackers. The hospitality industry is a diverse segment of the service sector dedicated to the provision of services in areas such as accommodation, food and beverage, travel and tourism, and recreation, including hotels, restaurants, bars, travel agencies, and theme parks. Cybersecurity risks in the hospitality industry affect the data and systems of businesses such as accommodation, food, travel, and entertainment, primarily enabled by the industry’s increasing digitization. This study aims to map the principal cybersecurity risks to the main stakeholders by proposing a novel Picture Fuzzy Sets (PFSs)-based Matrix of Alliances and Conflicts: Tactics, Objectives, and Recommendations (MACTOR) approach. The purpose here is to examine each stakeholder’s position towards handling cybersecurity attacks and estimate the uncertain nature of personal judgments of industry representatives when stating their point of view. The research aimed to extract the triggering positions of the defined cybercrime risks to reach the root cause of these risks, as the point to try to mitigate first. Thus, this paper contributes to the literature in both theoretical and practical ways by proposing a new approach and by providing real industry officials’ perspectives to solve the challenges. A hospitality practitioner can easily understand their position in this service network and take action to prevent such cybercrimes.
1. Introduction
Hospitality is the act of welcoming and treating guests with kindness and respect in order to provide services in hotels, restaurants, and bars, using a set of universal and cross-cultural values to enable high levels of human connection [1]. The hospitality industry is of paramount importance due to its contributing position to the global economy and employment. Accordingly, the World Travel and Tourism Council reports that the industry generated 7.6% of the global GDP and supported 272 million jobs in 2022 [2]. Particularly, the hotel and resort industry has a market size of USD 1.21 trillion worldwide [3], and restaurants (food and beverage services) have a USD 975.9 billion market size online in the US [4]. Moreover, the industry provides services and experiences that satisfy the needs and desires of customers, such as leisure, entertainment, comfort, and convenience, in order to enhance the quality of life and well-being of people [5]. It connects people from different backgrounds, cultures, and countries, and promotes mutual understanding, respect, and tolerance to foster cultural diversity and social inclusion. Moreover, it adapts to the changing needs and expectations of customers and adopts new technologies, practices, and standards that improve its efficiency, quality, and environmental impact; hence, it directly drives innovation and sustainability as well [6].
The literature on hospitality focuses on history, culture, and business to investigate different academic perspectives [7]. However, challenges and opportunities in the hospitality industry are always one of the main research questions [8]. In other words, both the challenges and the opportunities of this industry have been widely researched, and the literature presents several research questions. Particularly, globalization, sustainability, innovation, and technology are the most important fields of study that entail both the advantages and disadvantages of the industry [9].
The technology of the digital transformation era brings new cybersecurity risks to this sector by increasing the exposure and vulnerability of the data and systems of hospitality businesses to cyberattacks. Cybersecurity risks in the industry are the potential threats that can compromise the data and systems of businesses that provide services such as lodging, food, travel, and entertainment as key outputs [10,11]. All service network members, such as suppliers, distributors, service providers, and customers, are threatened by cybersecurity risks [12,13]. Technology can also enable cybercriminals to launch more sophisticated and targeted attacks, such as phishing, ransomware, DDoS (distributed denial-of-service), DarkHotel hacking, etc. [14]. For example, there have been the following hospitality industry cyberattacks: the Hilton case in 2015 [15], the Wyndham case between 2008 and 2010 [16], DarkHotel hacking [17], and the Starwood and Marriott case in 2018 [14]. These all caused serious damage to the industry and frightened people. Here, a data breach is defined as a main security threat [18] in the industry reports. Also, the Marriott data breach (Nov 2018) is listed as one of the most important cases, with severe consequences for 500 million guests [19].
Thus, this valuable background knowledge motivates this study to further investigate cybersecurity in this sector. Since the existing literature (see Section 2) is very limited in terms of analyzing cybersecurity risks, this study is motivated to examine both the risks and the stakeholders so that industry practitioners can understand their roles and duties in handling such challenges.
In addition, the background knowledge also directs this study to find a way to handle imprecise, uncertain, and inconsistent subjective judgments by industry representatives. As the most well-known and widely used approach, fuzzy sets are the most suitable way to deal with such uncertainties. As a particular type of fuzzy set, Picture Fuzzy Sets enable a “refusal” decision by the participants, similar to real-world scenarios.
The goal of this study is to discover how each stakeholder deals with the identified cybersecurity threats. To achieve this goal, a list of stakeholders is initially determined, followed by a clarification of the risks related to cybersecurity in the hospitality industry. Following that, a Picture Fuzzy Sets Fuzzy MACTOR (“Matrix of Alliances and Conflicts: Tactics, Objectives, and Recommendations”) approach is applied to systematically determine the interactions between each of these risks and stakeholders’ contributions to each of these risks.
The decision to choose the MACTOR approach is based on its capacity to conduct potential stakeholder assessments [20]. The MACTOR approach proposes a “participants investigative framework” that accounts for the breadth and depth of interactions among those making decisions. The technique allows for the analysis of each of the interests of stakeholders and their unavoidable alignments and expected perspectives by characterizing the position of every participant in regard to the indicated dangers and their power connections. Finally, it contributes to a set of significant and strategic recommendations for improving the financial sustainability of a manufacturing system [21].
Picture Fuzzy Sets (PFSs) are employed owing to their advantages in terms of imprecise, uncertain, and inconsistent data arising from the subjective judgments of people [22]. PFSs also accommodate required information about the sample, representing the field of study, and provide the reliability of the information expressed by refusal membership [23]. Here, tactics refer to the stakeholders’ actions in order to realize their particular objectives via some result-oriented recommendations. The objectives depend on the problem to be solved, and sometimes they can be the kind of challenges or barriers that can be handled, while sometimes they can be the key purposes of the service networks to be fulfilled. Recommendations are not mandatory but provide an idea to solve problems or fulfill the objectives.
The findings of the analysis reveal that regulations should be enhanced to protect people from cybersecurity attacks, and individuals should be trained in a more frequent way to educate people on the latest methods of cybercrime. For example, phishing can be avoided by an increased awareness and consciousness of all hospitality industry stakeholders. Hence, these avoided phishing attacks also blocks other types of cyberattacks such as data breaches and ransomware. In a similar manner, strengthened vulnerabilities prevent ransomware and data breaches as well. Denial-of-service crimes, on the other hand, necessitate improved IT infrastructure and server capabilities in order for users to access online services.
Next, this manuscript presents a literature review on cybersecurity risks and the stakeholders of the industry, preliminaries of PFSs, and the proposed MACTOR approach. Then, the analysis, findings, and conclusions are presented.
2. Literature Review
Cybersecurity-oriented hospitality sector papers focus on the human factor, human resources [10], confidentiality, awareness [11], digital transformation, IT strategies [24], blockchain, information security [25], data vulnerability [26], hacking, malware, data breach [27], cyberattacks, cybercrime [28], technology integration, incident responses [29], and training [28].
A review of the literature, including hospitality and cybersecurity keywords, was conducted by searching the titles, abstracts, and keywords of the papers in the Scopus database on 13 June 2024, which resulted in only 17 documents. The first papers appeared in 2017 and reached the highest level in 2023, with five papers in that year. Moreover, 42% of these papers are articles, 32% of them are conference papers, and 16% of them are book chapters, and the remaining part includes conference reviews. In addition, the contributing field of studies are computer science (31%), engineering (18%), business and management (16%), decision science (13%), social sciences (7%), economics (4%), mathematics (4%), energy (2%), and the remaining fields are environmental science and medicine. (The statistics are derived from Scopus Analyze Search Results section.)
Table 1 summarizes the literature on papers related to cybersecurity risks and the hospitality industry, including the methodology and details on the findings.

Table 1.
Literature review of papers related to cybersecurity risks and hospitality industry.
The following part of the literature review includes the details of stakeholders and cybersecurity risks in the hospitality industry.
2.1. Stakeholders of Hospitality Industry
A group of individuals possessing the same interest or having an impact is defined as the stakeholders of a system. These stakeholders might impact the systems or be impacted by the outcomes of any decision, action, or strategy in the system. Thus, it is critical for the hospitality industries to identify, understand, and interact with its stakeholders since they may have a substantial effect on their success, reputation, and sustainability [33]. (St: Stakeholder).
According to the detailed review of the literature and industry reports, the stakeholders of hospitality industry can be listed as follows:
- St1. Customers/consumers [34,35,36];
- St2. Employees/operators/internal stakeholders [34,35,36,37];
- St3. Suppliers [35,38,39];
- St4. Shareholders/investors/owners [35];
- St5. Regulators/government authorities [40];
- St6. Competitors [41,42,43];
- St7. Media/social media [42,44].
The following section will define the cybersecurity risks and will then examine the inter-relations of the stakeholders and those risks.
2.2. Cybersecurity Risks in Hospitality Industry
Cybersecurity risks in the hospitality industry refer to potential threats and vulnerabilities that might jeopardize the security and privacy of data and systems utilized by firms [14]. Cybersecurity risks can arise as a consequence of cyberattacks by malicious individuals attempting to steal, damage, or disrupt hospitality firms’ data and systems; human mistakes; system breakdowns; or natural catastrophes that may expose or distort data [45]. Hence, the following in-depth review of both the literature and industry reports is conducted to highlight the cybersecurity risks. (CR: Cybersecurity Risk).
- CR1.
Phishing: Seeking out hospitality staff or customers and abusing their confidence, curiosity, or concern by sending fake emails to deceive them into disclosing personally identifiable data, clicking on dangerous links, or downloading malicious files. Phishing might result in data breaches, malware infections, account hijacking, or financial fraud [10].
- CR2.
Data breaches: Unauthorized acquisition of confidential customer or company data, such as individual data, credit card numbers, booking tracks, loyalty scheme information, and so on [10,27,28,29].
- CR3.
Ransomware: A sort of malware that encrypts hospitality firms’ data or systems and then asks for a ransom or fee to unlock them. Ransomware may interrupt hospitality firms’ services and operations, prohibit access to their data or systems, and demand money from them. Ransomware may potentially expose or damage data or systems and also the reputation if the ransom is not paid or the decryption fails [46].
- CR4.
Denial-of-service (DoS) attacks: A sort of cyberattack in which the network or system of the hospitality company is overwhelmed with excessive traffic or requests, causing it to slow down or become inaccessible. DoS attacks can disrupt the performance and availability of hospitality firms’ online services and platforms, such as websites, booking systems, payment systems, and so on. DoS attacks can also result in consumer disappointment, loss of income, and higher operating expenses [25,26,32].
- CR5.
Vulnerabilities: Defects or weaknesses in either the hardware or software of devices or systems employed by hospitality firms, for example, property administration systems, payment systems, digital door locks, WiFi connections, and so on. Hackers may take advantage of vulnerabilities to obtain unauthorized entry, obtain data, or endanger the appliances, devices or systems [26,31,47].
The following section proposes a novel approach to analyze the field outlined above.
3. Methodology
This section proposes a Picture Fuzzy Sets (PFSs) MACTOR analysis to interpret the stakeholders’ cybersecurity risks and their perspectives on how such stakeholders prefer the risks be handled.
3.1. Preliminaries of Picture Fuzzy Sets (PFSs)
Since Zadeh’s [48] introduction of fuzzy sets, innovative theories understanding uncertainty and theories that expand fuzzy set theory have been proposed. This study focuses on the Picture Fuzzy Sets (PFSs) proposed by Cuong and Kreinovich [49] as an extension of Atanassov’s (1983) [50] fuzzy sets. PFSs are employed in case of individuals having different points of views. Particularly, the PFS decisions are 4-fold: (1) support of the decision, (2) votes against, (3) abstentions, and (4) refusals. There are clear advantages of PFSs such as the capability to identify the imprecise, unclear, and inconsistent dissemination of information of individuals in decision-making processes, due to the uncertain nature of subjective assessments [22], and it ensures the confidence of the information given by refusal of membership [23].
By assuming that is the positive membership degree (md), is the neutral md, and is the negative md, PFSs are the mathematical object of , by meeting the condition. In addition, the refusal md is defined as . Additionally, in case of having case, the PFS turns into an intuitionistic fuzzy set, and in case of having case, the PFS turns into the fuzzy set [51]. Here, by assuming that and are two Picture Fuzzy Numbers (PFNs), then the addition operation is defined as (Equation (1)), and multiplication operation is defined as (Equation (2)) [52]. Moreover, a score function and accuracy function are employed in defuzzification and comparison procedures with the use of defined (Equation (3)) and (Equation (4)) formulations [49]. Indeed, a linguistic scale (see Table 2) is suggested and widely used in gathering the decision maker’s opinions on a particular field of research.

Table 2.
Linguistic expressions for PFNs [53].
These tentative descriptions will be utilized in the suggested methodology and analysis sections.
3.2. Proposed Picture Fuzzy Sets (PFSs) Based MACTOR Approach
The MACTOR technique allows stakeholders to select how to implement a certain policy based on alliances and disputes. This method improves data processing for all stakeholders, particularly their comprehension of strategic goals. The technique identifies power relationships among stakeholders to define dominant relationships and autonomous stakeholders. It assesses vital relationships to determine the key stakeholders among supply chain actors. The study’s scope includes the creation of a direct influence matrix and the description and organization of stakeholders based on their position in the system. A stakeholder risk matrix is then used to determine a stakeholder’s position in relation to the risks and the possibility of forming partnerships to achieve it. Finally, a stakeholder convergence graph is generated [54].
MACTOR is utilized in a number of academic fields such as stakeholders of art market [55], sustainable agriculture [56], wastewater management [57,58], fashion supply chains [59], urban railway [60], hospitality [61], and tourism [62,63]. The MACTOR method addresses the stakeholders’ convergence and divergence in terms of handling the risks. It facilitates the identification of stakeholder relationships and their impact and authority on the target risk. This is an analytical approach that examines stakeholders’ activities, risks, power balance, and position in relation to project implementation [59].
The proposed “Picture Fuzzy Sets based-MACTOR” approach contains the followings steps:
- Identifying the cyber security risks.
- Identifying the hospitality industry stakeholders playing important roles.
- Creating stakeholder × stakeholder matrix using PFSs to evaluate the inter-relationships of these stakeholders by asking the hospitality industry officials for their mutual understanding. Here, Matrix of Direct Influences (MDI) is generated by aggregating these hospitality industry officials’ decisions via Delphi technique.
- Applying the score function equation (see Preliminaries of PFSs) to defuzzify the input values.
- Describing the indirect linkages and taking the square of the MDI matrix to obtain the Matrix of Direct and Indirect Influences (MDII).
- Implementing the and computations to present the balance of power coefficients. Here, represents the direct and indirect influence of ith stakeholder, n means total number of stakeholders, represents direct and indirect dependence of ith stakeholder, and coefficient is the power balance of those stakeholders.
Balance of power coefficients represent the relative power of different actors involved in a strategic analysis. These coefficients help to quantify the influence and power each actor holds within the system being studied. The balance of power is calculated based on several factors, including resources, influence, alliances, and conflicts. By analyzing these coefficients, stakeholders can better understand the dynamics of power and influence within the system, which can inform strategic decisions and actions.
- 7.
- Stakeholder positioning map generation.
- 8.
- Stakeholder × risk matrix the Matrix of Stakeholder and Risks (MSR) is created by using PFSs again to assess the inter-relationships of these stakeholders with cybersecurity risks by again asking the hospitality industry officials for their mutual understanding, and again, aggregating them via the Delphi technique. The defuzzification is also repeated in here with a score function.
- 9.
- MSR and balance of power coefficients matrices multiplication to present the weighted matrix.
- 10.
- Generating the convergence and divergence graphs and offering strategic advice to the hospitality industry stakeholders.
Here, stakeholder × risk matrix MSR refers to which stakeholder is responsible for solving or dealing with which risk encountered in hospitality cybersecurity. The assessment phase also involves the degree of risk that can be assigned to this stakeholder-to-risk relationship. For example, a stakeholder might be responsible for handling a risk with very high level.
The Delphi technique was used to obtain participant perspectives on the correlations between the stated criteria. The Delphi approach is a predictive framework that uses the findings of numerous rounds of interviews with panels of individuals. Participants are shown an aggregate assessment summary, allowing them to change their replies based on the group reaction. This technique combines the advantages of participant analysis with collective knowledge [64,65]. In the next part, the suggested approach will be applied to the hospitality service network to emphasize the unique responsibilities required to manage cybersecurity threats.
4. Examination and Findings
In the previous literature review, the first phase described the risks, and the second listed the stakeholders. Thus, the third stage is examining stakeholder connections and assigning input values as PFSs. The participants were interviewed in June 2024 and asked to identify direct relationships to build MDI and MSR matrices as inputs (refer to Table 3).

Table 3.
Participant profiles.
Next, these individuals were contacted in June 2024 via Instagram and LinkedIn to gather decision matrices. The decision makers were informed about the research’s purpose and scope. A total of 141 individuals were requested to participate in the study, and 19 of them did so. All of the participants attended a two-hour remote meeting in Turkish; a midday event was most convenient for all of them. Personal assessments were available at the very beginning of the meeting since participants had been briefed about the meeting’s scope in advance.
Moreover, this kind of cross-impact matrix-oriented study requires 10–12 experts in general, while this study reached 19 industry representatives. It is accepted that these numbers are enough to generalize the findings in cross-impact matrix-oriented studies [63].
For example, a café manager is asked to evaluate each individual relationship between stakeholders and then asked to examine each stakeholder’s role in handling each risk. A sample answer here is “customers have very high influence on social media” or “customers have very low influence on dealing with the vulnerabilities risk”. The participants are only giving their perceptions to create decision matrices within the MACTOR technique, and their influence and concerns were measured by the PFS’s linguistic scale, for example, low, very low, high, very high, etc.
The third step yielded the MDI matrix. In the fourth phase, the score function was implemented toward defuzzification mechanisms (see Table 4). The fifth stage uses the square of the MDI matrix to handle the indirect links known as MDII, while the sixth step applied the power coefficient balancing equations. Table 5 handles both the produced MDII matrix and the power coefficient balance.

Table 4.
MDI matrix with score functions.

Table 5.
MDII matrix and balance of power coefficients.
The components in the MDII matrix represent direct and indirect stakeholder influences. The higher the value means the greater the stakeholder’s influence on the other stakeholder. Mi corresponds to the degree of direct and indirect influence of each stakeholder (by summing up the lines of MDII matrix), Di corresponds to the degree of direct and indirect dependence of each stakeholder (by summing up the columns of MDII matrix), and ri is the stakeholder’s competitiveness that takes (i) maximum influences into account, (ii) direct and indirect dependence, and (iii) feedback. ri* corresponds to the balance of power coefficient between every stakeholder. Therefore, the sixth step of the proposed methodology was met, and the competitiveness situation is presented with the “balance of power coefficients” in Figure 1.
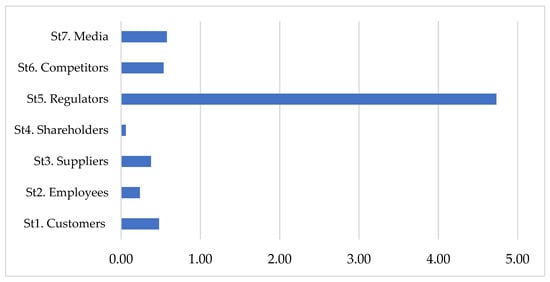
Figure 1.
Stakeholders’ competitiveness levels.
As shown in Figure 1, regulators/governmental authorities dominate power perspectives, while media, competitors, customers, suppliers, and employees have many alternatives in the hospitality market. Moreover, Figure 1 also illustrates that shareholders/owners/investors are the ones can be easily changed in this service network. Next, at the seventh step, a stakeholder’s map of positioning is provided (see Figure 2). Accordingly, St5. Regulators are the influential stakeholders that can easily affect the whole hospitality service network via regulations and obligations. St3. Suppliers, St6. Competitors, and St7. Media are autonomous stakeholders. However, it is a significant detail that Competitors and Media are so closely positioned in all other areas. Therefore, one can easily determine that they can be both influential for the other stakeholders and also dependent on the other stakeholders as well. Their position in the hospitality industry can be easily altered in another way according to the industry dynamics. Moreover, St1. Customers, St2. Employees, and St4. Shareholders are the dependent stakeholders that can be affected easily by any positive or negative condition in this service network. Any bullwhip effect might generate further augmented results from these dependent stakeholders. Finally, the analysis revealed no key player or leading stakeholder dominating the hospitality service network.
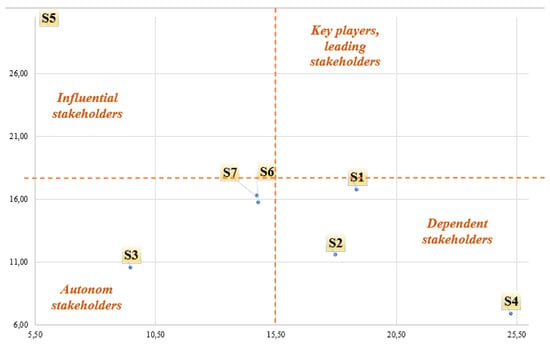
Figure 2.
Stakeholders’ map of positioning.
The eighth phase requires “stakeholder × risk” relationships with PFSs input values. The MSR and “balance of power coefficients” matrices were multiplied here to produce the weighted matrix shown in Table 6.

Table 6.
Weighted matrix.
At the last tenth step, the weighted matrix generates the “convergence” graph, which provides strategic guidance to each stakeholder (see Figure 3). The converged stakeholders and cybersecurity risks graph reveal that the St5. Regulators have the most important problem-solving position in the hospitality industry’s cybersecurity risks. All other stakeholders should be protected by the regulations and preventive mechanisms to avoid negative circumstances.
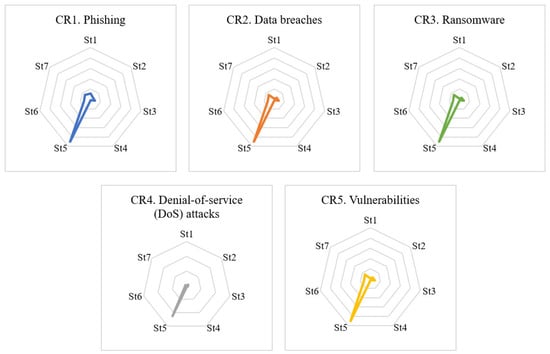
Figure 3.
Stakeholders’ cybersecurity risks convergence.
Furthermore, phishing can be prevented by the awareness and the increased consciousness of all hospitality industry stakeholders. Mitigated phishing attacks also prevent the data breaches and ransomware. Similarly, the reinforced vulnerabilities also solve the ransomware and data breach occurrences as well. However, the denial-of-service attacks require enhanced IT infrastructure and server capabilities to enable individuals to reach the online services.
The following section of the research examines the findings of this article and discusses the alternative solution possibilities suggested by the literature.
5. Discussion and Potential Solutions
As it is clearly indicated in the analysis and findings section, there is no definitive answer to how we can solve the cybersecurity risks in the hospitality industry, and there is also no single authority to solve the cyberattacks; however, all participant industry representatives emphasize that some governmental preventions should be available for all individuals.
The literature and industry reports suggest the following actions to help reduce cybersecurity risks in the hospitality industry: encrypting payment card information [14], continuous training programs, implementing a formal process to verify requests for data or funds, securing customer Wi-Fi, establishing cyber safeguards for mobile point-of-sale devices [66], adhering to relevant regulations like Payment Card Industry Data Security Standard (PCI DSS), the General Data Protection Regulation (GDPR), and the California Consumer Privacy Act (CCPA) [67], utilizing cybersecurity measures such as firewalls, network monitoring, anti-malware, and traffic filtering [68] and increasing guest engagement with loyalty apps [46].
Moreover, artificial intelligence (AI) might, in the future, provide tailored cybersecurity strategies by detecting anomalies and threats, enhancing security awareness and training [69], and predicting and preventing attacks [70]. For example, there are AI-powered cybersecurity solutions for hotels such as [66], OneReach.ai [71] and IDeaS [72]. AI can likely help you improve your hotel’s security system by detecting, preventing, and responding to known cyber threats, as well as enhancing your security awareness and training in hospitality through reports from the AI to staff when actions are taken [73,74].
6. Conclusions
The hospitality business is extremely important because of its contribution to the global economy and jobs. It brings together individuals from various origins, cultures, and nations, encouraging mutual understanding, respect, and tolerance in order to develop cultural diversity and social inclusion. Furthermore, it adjusts to changing consumer demands and expectations by implementing new technologies, procedures, and standards that enhance its efficiency, quality, and environmental impact, thus driving innovation and sustainability.
The digital transformation age introduces cybersecurity threats into the hospitality sector by increasing the exposure and vulnerability of hospitality firms’ data and systems to hackers. Cybersecurity risks in the hospitality sector are possible dangers to the data and systems of businesses that provide services such as housing, food, travel, and entertainment. The cybersecurity concerns affect all members of the service network, including suppliers, distributors, service providers, and customers.
As a result, the goal of this study was to discover how each stakeholder prefers to deal with the identified cybersecurity threats. To achieve the goal, stakeholders were first identified, and then the risks associated with cybersecurity in the hospitality industry were described. Following that, a PFSs MACTOR approach was used to systematically analyze the inter-relationships of these risks and stakeholders’ contributions to each of these risks.
The analysis revealed authorities/regulators play the most essential role in mitigating cybersecurity threats in the hospitality business. Regulations and preventative procedures should safeguard all other stakeholders in order to avoid harmful outcomes. Furthermore, phishing may be avoided by raising the knowledge and consciousness among all players in the hospitality business. Blocking phishing attempts also prevents data breaches and malware. Similarly, defended weaknesses prevent ransomware and data breaches. Denial-of-service assaults, on the other hand, necessitate improved IT infrastructure and server capabilities in order for users to access online services.
This paper adds to the literature by (i) identifying engaged stakeholders in hospitality businesses, (ii) defining cybersecurity goals, (iii) recommending a PFSs MACTOR investigation, (iv) comprehending a stakeholder-stakeholder matrix to discover stakeholder positions, and (v) defining a stakeholder-risk structure to indicate the level of convergence of all of these interested parties for every risk.
As a result, a practitioner might comprehend the role they play in the network of services in order to accomplish cybersecurity and build stronger relationships with the companies they serve. A practitioner, an example of a shareholder, could better understand their position in this hospitality service network, recognize their influencing power over the network, understand their role in dealing with the cybersecurity risks, and then take action accordingly. As a management consequence, higher-level executives in a hospitality organization may anticipate possible commercial hurdles and design tactical, operational, and strategic plans to achieve better cybersecurity. For instance, management practitioners can focus on social media or customers due to their high level of influence and importance. Finally, this study makes a methodological advancement by providing a unique PFSs MACTOR, which is an essential instrument to provide insights on the supply chain and service network for the current body of literature.
This study sought to limit potential personal opinions by choosing the most qualified individuals who are committed to contributing to such a study. Furthermore, the consistency of their judgments was carefully reviewed to ensure accuracy. Other study constraint were the total amount of attendees, the diversity of service-oriented demonstrations, and the single nation of residency. Future research should expand the sampling on these three fronts.
Further investigation initiatives could involve using additional fuzzy sets to expand the MACTOR study or including various parties with several distinct objectives. Furthermore, field investigsoftwareations involving comprehensive questionnaires or interviews could possibly be sent to a more significant number of people.
Funding
This research received no external funding.
Data Availability Statement
Detailed data are available upon request.
Conflicts of Interest
The author declares no conflicts of interest.
References
- Merriam-Webster. Hospitality Definition & Meaning; Merriam-Webster: Springfield, MA, USA, 2024. [Google Scholar]
- Hendron, A.; Epos Now. The Importance of the Hospitality Industry & Its Four Sectors. Available online: https://www.eposnow.com/us/resources/importance-of-the-hospitality-industry/ (accessed on 23 January 2024).
- Statista Research Department. Hotel Industry Worldwide. Statista. Available online: https://www.statista.com/topics/1102/hotels/ (accessed on 25 January 2024).
- Statista Research Department. Foodservice and Drinking Place Sales US 2022. Statista. Available online: https://www.statista.com/statistics/239410/us-food-service-and-drinking-place-sales/ (accessed on 25 January 2024).
- EHL Insights. Hospitality Industry: All Your Questions Answered. Available online: https://hospitalityinsights.ehl.edu/hospitality-industry-2031 (accessed on 23 January 2024).
- EHL Insights. Why Hospitality Is Important as a Skill and Not Only as An Industry. Available online: https://hospitalityinsights.ehl.edu/why-hospitality-is-important (accessed on 23 January 2024).
- Pijls-Hoekstra, R.; Groen, B.H.; Galetzka, M.; Pruyn, A.T.H. Experiencing Hospitality: An Exploratory Study on the Experiential Dimensions of Hospitality. In Proceedings of the EuroCHRIE 2015, Manchester, UK, 15–17 October 2015. [Google Scholar]
- Huertas-Valdivia, I.; González-Torres, T.; Nájera-Sánchez, J.-J. Contemporary Leadership in Hospitality: A Review and Research Agenda. Int. J. Contemp. Hosp. Manag. 2022, 34, 2399–2422. [Google Scholar] [CrossRef]
- Seyitoğlu, F.; Costa, C.; Martins, M.; Malta, A.M. The Future of Tourism and Hospitality Labour: Challenges, Requirements, Trends, Skills and the Impact of Technology. Curr. Issues Tour. 2023, 1–15. [Google Scholar] [CrossRef]
- Augustyn, D.; Tick, A. Security Threats in Online Metasearch Booking Services. In Proceedings of the 2020 IEEE 20th International Symposium on Computational Intelligence and Informatics (CINTI), Budapest, Hungary, 5–7 November 2020; pp. 000017–000022. [Google Scholar] [CrossRef]
- Holdsworth, J.; Apeh, E. An Effective Immersive Cyber Security Awareness Learning Platform for Businesses in the Hospitality Sector. In Proceedings of the 2017 IEEE 25th International Requirements Engineering Conference Workshops (REW), Lisbon, Portugal, 4–8 September 2017; pp. 111–117. [Google Scholar] [CrossRef]
- Aravinda, T.; Krishnareddy, K.; Varghese, S.; Chandrika, P.V.; Rao, T.P.; Trofimov, V. Implementation of Facial Recognition (AI) and Its Impact on the Service Sector. In Proceedings of the 2022 International Conference on Applied Artificial Intelligence and Computing (ICAAIC), Salem, India, 9–11 May 2022; pp. 74–80. [Google Scholar] [CrossRef]
- Barda, I. Just about Managing: Dealing with the Threats to Industrial Systems. Comput. Fraud. Secur. 2019, 2019, 11–14. [Google Scholar] [CrossRef]
- Chin, K. Cybersecurity in the Hospitality Industry: Challenges and Solutions. Available online: https://www.upguard.com/blog/cybersecurity-in-the-hospitality-industry (accessed on 23 January 2024).
- Roberts, P. Hilton Was Fined $700K for a Data Breach. Under GDPR It Would Be $420M. Available online: https://www.digitalguardian.com/blog/hilton-was-fined-700k-data-breach-under-gdpr-it-would-be-420m (accessed on 23 January 2024).
- Tymoshchenko, D. Cybersecurity in Hospitality—How to Fix Data Breach Threats. Available online: https://acropolium.com/blog/cybersecurity-and-data-breach-threats-in-hospitality-how-to-fix/ (accessed on 23 January 2024).
- Logsign. The Biggest Cyber-Attacks in 2019. Logsign. Available online: https://www.logsign.com/blog/the-biggest-cyber-attacks-in-2019/ (accessed on 25 September 2024).
- Petrosyan, A.; Statista. Largest Data Breaches Worldwide 2023. Available online: https://www.statista.com/statistics/290525/cyber-crime-biggest-online-data-breaches-worldwide/ (accessed on 25 January 2024).
- Petrosyan, A.U.S. Consumers and Cyber Crime. Statista. Available online: https://www.statista.com/topics/2588/us-consumers-and-cyber-crime/ (accessed on 25 January 2024).
- Fiallos-Cárdenas, M.; Pérez-Martínez, S.; Ramirez, A.D. Prospectives for the Development of a Circular Bioeconomy around the Banana Value Chain. Sustain. Prod. Consum. 2022, 30, 541–555. [Google Scholar] [CrossRef]
- Fetoui, M.; Frija, A.; Dhehibi, B.; Sghaier, M.; Sghaier, M. Prospects for Stakeholder Cooperation in Effective Implementation of Enhanced Rangeland Restoration Techniques in Southern Tunisia. Rangel. Ecol. Manag. 2021, 74, 9–20. [Google Scholar] [CrossRef]
- Wei, G. Picture Fuzzy Cross-Entropy for Multiple Attribute Decision Making Problems. J. Bus. Econ. Manag. 2016, 17, 491–502. [Google Scholar] [CrossRef]
- Singh, P. Correlation Coefficients for Picture Fuzzy Sets. J. Intell. Fuzzy Syst. 2015, 28, 591–604. [Google Scholar] [CrossRef]
- Wynn, M.; Lam, C. Digitalisation and IT Strategy in the Hospitality Industry. Systems 2023, 11, 501. [Google Scholar] [CrossRef]
- Sahu, A.K.; Gutub, A. Improving Grayscale Steganography to Protect Personal Information Disclosure within Hotel Services. Multimed. Tools Appl. 2022, 81, 30663–30683. [Google Scholar] [CrossRef]
- Chen, H.S.; Fiscus, J. The Inhospitable Vulnerability: A Need for Cybersecurity Risk Assessment in the Hospitality Industry. JHTT 2018, 9, 223–234. [Google Scholar] [CrossRef]
- Gwebu, K.; Barrows, C.W. Data Breaches in Hospitality: Is the Industry Different? JHTT 2020, 11, 511–527. [Google Scholar] [CrossRef]
- Boto-García, D. Hospitality Workers’ Awareness and Training about the Risks of Online Crime and the Occurrence of Cyberattacks. J. Hosp. Tour. Manag. 2023, 55, 240–247. [Google Scholar] [CrossRef]
- Ogunyebi, O.; Swar, B.; Aghili, S. An Incident Handling Guide for Small Organizations in the Hospitality Sector. In Trends and Advances in Information Systems and Technologies; Rocha, Á., Adeli, H., Reis, L.P., Costanzo, S., Eds.; Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2018; Volume 745, pp. 232–241. [Google Scholar] [CrossRef]
- Cohen, M.C. Big Data and Service Operations. Prod. Oper. Manag. 2018, 27, 1709–1723. [Google Scholar] [CrossRef]
- Shabani, N.; Munir, A. A Review of Cyber Security Issues in Hospitality Industry. In Intelligent Computing; Arai, K., Kapoor, S., Bhatia, R., Eds.; Advances in Intelligent Systems and Computing; Springer International Publishing: Cham, Switzerland, 2020; Volume 1230, pp. 482–493. [Google Scholar] [CrossRef]
- Arcuri, M.C.; Gai, L.; Ielasi, F.; Ventisette, E. Cyber Attacks on Hospitality Sector: Stock Market Reaction. J. Hosp. Tour. Technol. 2020, 11, 277–290. [Google Scholar] [CrossRef]
- Vrontis, D.; Iazzi, A.; Maizza, A.; Cavallo, F. Stakeholder Engagement IN The Hospitality Industry: An Analysis Of Communication In Smes And Large Hotels. J. Hosp. Tour. Res. 2022, 46, 923–945. [Google Scholar] [CrossRef]
- Jin, D.; Chen, H.; Qi, R. Diversity, Equity and Inclusion in Employee-Queer Customer Interactions in the Hospitality Service Setting: Including Multiple Stakeholders’ Perspectives. Int. J. Contemp. Hosp. Manag. 2024, 36, 1991–2010. [Google Scholar] [CrossRef]
- Ozdemir, O.; Dogru, T.; Kizildag, M.; Erkmen, E. A Critical Reflection on Digitalization for the Hospitality and Tourism Industry: Value Implications for Stakeholders. Int. J. Contemp. Hosp. Manag. 2023, 35, 3305–3321. [Google Scholar] [CrossRef]
- Shulga, L.V.; Busser, J.A.; Chang, W. Relational Energy and Co-Creation: Effects on Hospitality Stakeholders’ Wellbeing. J. Hosp. Mark. Manag. 2022, 31, 1026–1047. [Google Scholar] [CrossRef]
- Vasudevan, S.; Kumar, F.J.P. Distance to Distrust: The Dilemma for Internal Stakeholders in Post COVID-19 Hospitality. Int. J. Spa Wellness 2021, 4, 118–137. [Google Scholar] [CrossRef]
- Gouws, E.; Motala, T. Quality of Service Delivered by Alcoholic Beverage Suppliers to Customers in the South African Hospitality Industry. Afr. J. Hosp. Tour. Leis. 2019, 8, 1–16. [Google Scholar]
- Salihoğlu, G.; Gezici, F. Geography of Suppliers in the Hospitality Sector: The Case of Alanya. Tour. Manag. 2018, 65, 41–54. [Google Scholar] [CrossRef]
- Godinho, V. An Industry in Motion: Stakeholders across Hospitality, Tourism Space Share Key Insights. Gulf Business 2022. Available online: https://gulfbusiness.com/an-industry-in-motion-stakeholders-across-hospitality-tourism-space-share-key-insights/ (accessed on 25 January 2024).
- Alghizzawi, M.; Ahmed, E.; Alshaketheep, K.; Alkhlaifat, B.I.; Alnawafleh, H. Rival Influences of Airbnb Digital Platforms on the Jordanian Hotels Market. Migr. Lett. 2023, 20, 134–144. [Google Scholar] [CrossRef]
- ElShafei, R. Managers’ Risk Perception and the Adoption of Sustainable Consumption Strategies in the Hospitality Sector: The Moderating Role of Stakeholder Salience Attributes. Smart Sustain. Built Environ. 2022, 11, 1–18. [Google Scholar] [CrossRef]
- Sondari, T.; Sucherly; Hasan, M.; Soemaryani, I. The Influence of Market Orientation and Competitive Strategy on the Hotel Image. Int. J. Innov. Creat. Chang. 2020, 13, 297–309. [Google Scholar]
- Del Mar Gálvez-Rodriguez, M.; Saraite, L.; Alonso-Cañadas, J.; Del Carmen Caba-Pérez, M. Stakeholder Engagement via Social Media in the Hospitality Sector: The Evidence from BRIC Countries. In Opportunities and Challenges for Tourism and Hospitality in the BRIC Nations; IGI Global: Hershey, PA, USA, 2016; pp. 15–30. [Google Scholar] [CrossRef]
- Boutin, C.; NIST. Cybersecurity Guide Tailored to the Hospitality Industry. Available online: https://www.nist.gov/news-events/news/2021/03/nist-offers-cybersecurity-guide-tailored-hospitality-industry (accessed on 27 January 2024).
- Smith, C.L.; Wipfli. Cybersecurity Risks Shaping Hospitality in 2022. Available online: https://www.wipfli.com/insights/articles/acc-tc-cybersecurity-risks-shaping-hospitality-in-2022 (accessed on 27 January 2024).
- GoldSky Security. Top 5 Cyber Threats in the Hospitality Industry. GoldSky Security. Available online: https://www.goldskysecurity.com/top-5-cyber-threats-in-the-hospitality-industry/ (accessed on 27 January 2024).
- Zadeh, L.A. Outline of a New Approach to the Analysis of Complex Systems and Decision Processes. IEEE Trans. Syst. Man Cybern. 1973, SMC-3, 28–44. [Google Scholar] [CrossRef]
- Cuong, B.C.; Kreinovich, V. Picture Fuzzy Sets—A New Concept for Computational Intelligence Problems. In Proceedings of the 3rd World Congress on Information and Communication Technologies, Hanoi, Vietnam, 15–18 December 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Atanassov, K.T. Intuitionistic Fuzzy Sets. Fuzzy Sets Syst. 1986, 20, 87–96. [Google Scholar] [CrossRef]
- Vassilev, P.; Atanassov, K. A Note on Intuitionistic Fuzzy Sets, Interval Valued Intuitionistic Fuzzy Sets and Picture Fuzzy Sets. In Advances in Intelligent Systems and Computing; Springer: Cham, Switzerland, 2021; Volume 1081, pp. 24–28. [Google Scholar] [CrossRef]
- Servin, C.; Martinez, R.; Hanson, P.; Lopez, L.; Kreinovich, V. How to Define “and”-and “or”-Operations for Intuitionistic and Picture Fuzzy Sets. J. Uncertain Syst. 2019, 13, 126–132. [Google Scholar]
- Meksavang, P.; Shi, H.; Lin, S.-M.; Liu, H.-C. An Extended Picture Fuzzy VIKOR Approach for Sustainable Supplier Management and Its Application in the Beef Industry. Symmetry 2019, 11, 468. [Google Scholar] [CrossRef]
- Godet, M. Manuel de Prospective Stratégique, 2nd ed.; Dunod: Paris, France, 2001. [Google Scholar]
- Suasih, N.N.R.; Saskara, I.A.N.; Wijaya, P.Y.; Wibawa, I.P.S.; Santhyasa, I.K.G. Polemic of Stakeholders’ Objectives in the Decision of Revitalization and Relocation of the Sukawati Traditional Market as the Most Distinguished Art Market in Bali, Indonesia. Decis. Sci. Lett. 2024, 13, 211–224. [Google Scholar] [CrossRef]
- Sartika, R.C.; Purwaningsih, Y.; Gravitiani, E.; Nitiyasa, P. The Role of Stakeholders in Achieving Sustainable Agriculture: A Case Study in Sragen Regency, Indonesia. Nat. Environ. Pollut. Technol. 2023, 22, 2181–2188. [Google Scholar] [CrossRef]
- Ben-Daoud, M.; El Mahrad, B.; Moroșanu, G.A.; Elhassnaoui, I.; Moumen, A.; El Mezouary, L.; ELbouhaddioui, M.; Essahlaoui, A.; Eljaafari, S. Stakeholders’ Interaction in Water Management System: Insights from a MACTOR Analysis in the R’Dom Sub-Basin, Morocco. Environ. Manag. 2023, 71, 1129–1144. [Google Scholar] [CrossRef] [PubMed]
- Darmastuti, L.; Rustiadi, E.; Fauzi, A.; Purwanto, Y.J. Stakeholder Analysis of Sustainable Wastewater Management: A Case Study of Bogor, Indonesia. Sustainability 2023, 15, 11826. [Google Scholar] [CrossRef]
- Karadayi-Usta, S. A Novel Neutrosophical Approach in Stakeholder Analysis for Sustainable Fashion Supply Chains. J. Fash. Mark. Manag. 2023, 27, 370–394. [Google Scholar] [CrossRef]
- Wijayanto, Y.; Fauzi, A.; Rustiadi, E.; Wijaya, S. Development of Sustainable Urban Railway Service Model Using Micmac-Mactor: A Case Study in Jabodetabek Mega-Region Indonesia. Int. J. Sustain. Dev. Plan. 2022, 17, 135–146. [Google Scholar] [CrossRef]
- Iskandar; Waridin; Iskandar, D.D. The Potential of Muslim Friendly Hospitality in the Tourism Industry in Central Java. Indones. J. Islam Muslim Soc. 2023, 13, 169–197. [Google Scholar] [CrossRef]
- Suryade, L.; Fauzi, A.; Achsani, N.A.; Anggraini, E. Towards Sustainable Development of the Mandalika Special Economic Zone, Central Lombok, Indonesia: Analysis of Actors. J. Environ. Manag. Tour. 2021, 12, 1729–1740. [Google Scholar] [CrossRef]
- Karadayi-Usta, S. Sustainable Medical Tourism Service Network with a Stakeholder Perspective. Curr. Issues Tour. 2024, 1–20. [Google Scholar] [CrossRef]
- Twin, A. Delphi Method. Available online: https://www.investopedia.com/terms/d/delphi-method.asp (accessed on 25 January 2024).
- Karadayi-Usta, S. A New Servicizing Business Model of Transportation: Comparing the New and Existing Alternatives via Neutrosophic Analytic Hierarchy Process. Neutrosophic Sets Syst. 2022, 48, 56–65. [Google Scholar] [CrossRef]
- Ekran System. Cybersecurity for Hotels: Best Practices & Solutions. Available online: https://www.ekransystem.com/en/blog/cyber-security-in-hotels (accessed on 27 January 2024).
- Wainstein, L. Data Security in Hospitality: Risks and Best Practices. EHL Insights. Available online: https://hospitalityinsights.ehl.edu/data-security-in-hospitality-best-practices (accessed on 27 January 2024).
- Hoover, R.J.; Blount, A. Cybersecurity Risks in Hospitality. Risk Strategies. Available online: https://www.risk-strategies.com/blog/cybersecurity-risks-in-hospitality (accessed on 27 January 2024).
- InnQuest. Cybersecurity for Hospitality Management in the Age of AI. InnQuest Software. Available online: https://www.innquest.com/blog/cybersecurity-for-hospitality-management-in-the-age-of-ai/ (accessed on 27 January 2024).
- Rajagopal, A. As AI in Hotels Advances, So Too Should Cybersecurity Posture. Hospitality Technology. Available online: https://hospitalitytech.com/ai-hotels-advances-so-too-should-cybersecurity-posture (accessed on 27 January 2024).
- Parker, E. Texting Your Hotel—The Next Evolution of Hospitality Customer Service. OneReach. Available online: https://onereach.ai/journal/texting-your-hotel-the-next-evolution-of-hospitality-customer-service/ (accessed on 27 January 2024).
- IDeaS. Hotel Revenue Management Software & Solutions. IDeaS. Available online: https://ideas.com/hotel-rooms/ (accessed on 27 January 2024).
- Bhatia, G.; Mesmer, B. Trends in Occurrences of Systems Engineering Topics in Literature. Systems 2019, 7, 28. [Google Scholar] [CrossRef]
- Wiranatha, A.S.; Suryawardani, I.G.A.O.; Purbanto, I.G.R.; Yudiastina, I.G.B.A.; Bantacut, T. A Conceptual Model of Rural Tourism in Bali to Build Up Global Competitiveness. Systems 2024, 12, 245. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).