Abstract
Radio frequency identification (RFID) is widely used in several contexts, such as logistics, supply chains, asset tracking, and health, among others, therefore drawing the attention of many researchers. This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy. A total of 62,685 records were downloaded from the Web of Science (WoS) and Scopus core databases and processed, reconciling the datasets to remove duplicates, resulting in 40,677 unique elements. Fundamental indicators were extracted and are presented, such as the citation number, average growth rate, and average number of documents per year. We extracted the top topics and reviewed the relevant indicators using a free Python tool, ScientoPy. The results are discussed in the following sections: the first is the Applications Section, whose subsections are the Internet of Things (IoT), Supply Chain Management, Localization, Traceability, Logistics, Ubiquitous Computing, Healthcare, and Access Control; the second is the Security and Privacy section, whose subsections are Authentication, Privacy, and Ownership Transfer; finally, we present the Discussion section. This paper intends to provide the reader with a global view of the current status of trending RFID topics and present different analyses from different perspectives depending on motivations or background.
1. Introduction
It is expected that technology will work for us in more transparent and ubiquitous ways. RFID is implemented in many contexts, such as logistics [1,2], supply chains [3,4], asset tracking [5,6,7], healthcare [8,9], industrial enterprise environments [5,6], and many others, making our lives easier and generating vast quantities of information on many levels.
This review paper describes the most active topics of investigation regarding RFID technology. This information will help researchers in identifying research gaps and trending topics. Additionally, it could be useful for other disciplines and those outside academia, providing a brief overview of the most active investigations into RFID applications and security topics.
Multiple reviews and surveys exploring RFID from various perspectives have been published. From 2007 to 2009, there were reviews on the applications of this technology [10,11], as well as academic literature and historical reviews [12,13]. Additionally, we encountered a review published in 2010 on how RFID is used for tracking in the Internet of Things (IoT) [14]. A review of specific applications such as in postal and courier services was published in 2006 [15]. In the same way, work on its use in the aviation industry was published in 2010 [16]; work on its use in activities such as construction was published in 2015 [17]; there were healthcare-related publications from 2013 to 2018 [18,19,20]; work on supply chain management was published between 2010 and 2016 [21,22]; work on localization in the smart home paradigm was published in 2018 [23]; finally, in 2020, a systematic literature review was published on the applications of RFID in supply chains and its impacts on the competitive advantages of organizations [24], analyzed from corporate, customer, and benefit perspectives. There was also a review of the role of RFID in transportation [25], identifying the advantages of, and barriers to, its adoption. We observed that these reviews tended to focus on one specific topic each year.
This review compiles the most active topics to present the trends in the applications of RFID technology, based on the numbers of citations in papers published from 1996 to 2020 and the activity in the selected topics between 2019 and 2020, contributing an updated overview similar to the reviews of the applications published before [10,11], but also creating eight groups based on the most active topics from 2008 to 2009 [12,13], complementing this with the security, privacy, and ownership transfer topics.
Initially, we describe the process of working with separate datasets and reconciliation to obtain unique dataset entries, and we present the indicators related to the datasets used. We start with the RFID Applications Section, followed by the Security and Privacy section. The first section is subdivided based on the most active subtopics encountered in the analysis. The subsections discuss the Internet of Things (IoT), supply chain management (SCM), applications for localization using RFID, traceability, logistics management, ubiquitous computing, RFID in healthcare, and applications in access control. In the second section, we present the leading security and privacy topics, and in the subsections contained therein, we present authentication and ownership transfer. Finally, we present the Discussion.
2. Materials and Methods
This article collected and used information from the Scopus and Clarivate Web of Science (WoS) databases. To download the raw source datasets, an institutional subscription was needed to access and retrieve the data entries from both databases. Using the requisite web applications to access the databases, we performed the query using the string (“Radio frequency identification” OR “Radio-frequency identification” OR “RFID”) to obtain the data registered in each database. The query was executed on 4 February 2021. Subsequently, the data were processed using the scientometric tool ScientoPy [26].
The process applied to reconcile the datasets obtained from both databases, WoS and Scopus, and to generate the secondary dataset is represented in Figure 1. For more details, see the first three sections of the ScientoPy manual available in the GitHub repository https://github.com/jpruiz84/ScientoPy (accessed on 7 February 2021).
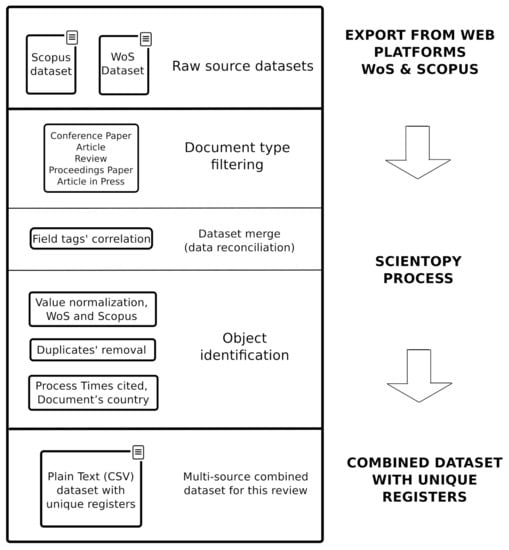
Figure 1.
Data process to remove duplicates and obtain unique entries from the WoS and Scopus datasets, using ScientoPy [26].
Data Description
The raw source dataset used for this work was retrieved on 4 February 2021. It contains 62,685 papers, appending entries from the WoS and Scopus databases. After the data reconciliation [27], we worked with 40,677 individual entries from both databases containing 24,587 unique papers from WoS and 16,090 unique papers from Scopus, removing 360 duplicated papers from WoS and 21,648 from Scopus. The distribution is shown in Figure 2.
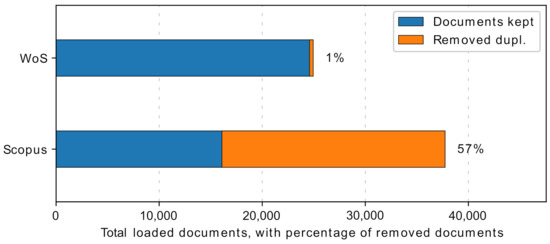
Figure 2.
ScientoPy data preprocessing from datasets downloaded from Clarivate Web of Science and Scopus, showing unique papers in blue and removed duplicates in orange.
Table 1 defines the acronyms for the statistics determined by ScientoPy; the software uses three different topic growth indicators to find trending topics, including relative/absolute growth, and calculates the h-index of each topic.

Table 1.
Topic growth indicators.
3. RFID Applications
RFID technology is making its way into various fields, sometimes keeping a low profile. However, it is becoming more relevant in people’s lives, creating paths to new applications and complementing known ones. In some cases, these applications do not directly interact with people, but RFID supports different processes for realizing products and services used daily. Accordingly, with reason, RFID is sometimes seen as a requirement or core technology for the Internet of things (IoT). This is affirmed by the total documents published on this topic, positioning IoT well above other applications. RFID supports many applications of the Internet of Things due to characteristics such as high volume, non-contact reading, tag features and, more importantly, low price. The situation is clearly reflected in the graphs (a) and (b) in Figure 3, with the more prominent indicators in Table 2. In second place, we have supply chain management, in which RFID is essential for identification and information capture for real-time management, using different methods such as frameworks and protocols. This allows high versatility due to the variety of tags available; all these processes are continually studied to solve security issues and possible vulnerabilities. RFID is also used in localization applications, extending the primary function of the technology, representing the second-largest activity in terms of the percentage of documents in last years (PDLY), as shown in Table 2. For traceability and logistics, RFID supports a variety of applications in supply chains and shop floor deployment. RFID is opening paths to new applications in an ever more ubiquitous fashion, blending into our lives much more, such as in healthcare spaces for ensuring data security and allowing more robust management of patients, equipment, and personnel. Similarly, it is applied to support the control of access to physical spaces and systems or enforcing the control of access to information captured by different sensors along with RFID. All these findings are presented in detail in the following sections and represented graphically in Figure 3. This chapter presents the top research applications identified through the scientometric analysis.
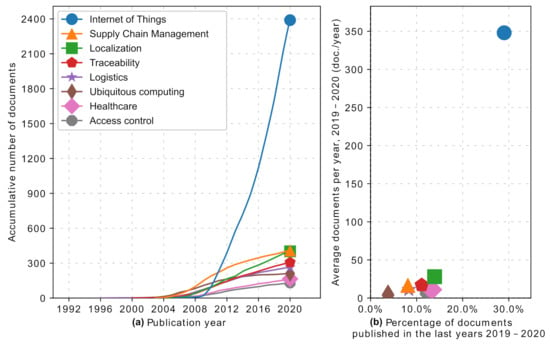
Figure 3.
(a) Top applications, and number of publications by year. (b) Average number of publications per year and percentage of documents published between 2019 and 2020.

Table 2.
Top author keywords for RFID applications.
3.1. Internet of Things (IoT)
With RFID, we can track and securely monitor individual objects worldwide in different environments. The technology offers multiple cost options, depending on the conditions and requirements. For this reason and more, RFID is often seen as a prerequisite for the IoT [28,29,30]. There are multiple studies on communication protocols to improve performance without compromising on security and scalability [31]; strong security and privacy are important when using mutual authentication between the reader and the tags [32]. The existing security attacks, privacy risks, and countermeasures to be applied [33], and identifying the limitations, requirements, and issues to work on for more secure deployment to meet security demands [34,35,36,37] are also being studied. However, there is a demand to search for more lightweight RFID authentication schemes due to the limitations of processing, storage, and power on the RFID tag side [38,39]. Security and privacy communication models are being developed that are better optimized for limited resources, while meeting the security requirements of applications [34,40]. Additionally, investigations are focusing on commercial tags to identify common flaws and possible measures to realize secure applications [41,42]. RFID–IoT investigations are equally analyzing how to enforce security through new policies for fine granularity and context-aware information control [43]. Additionally, to test these new proposals, there is a hardware and software suite for laboratories for emulating tags and readers [44] and analyzing security schemes that aim to provide secure and untraceable communication for end-users [45], allowing flexibility and application in different environments, considering important IoT components such as quality of service (QoS) or message queue telemetry transport (MQTT) [46,47].
RFID plays a role in the industrial enterprise environment, taking into consideration the low-carbon economy [48]. However, its main role is helping in monitoring, traceability and tracking [5], or obtaining more accurate location information by using ultra-wideband (UWB) technology [6]. It also helps to ensure the safety of personnel. For instance, by using wireless sensor networks (WSN) along with RFID, researchers aim to implement an advanced safety system for the hazardous environments in industrial plants [49]. The industrial Internet of Things (IIOT) requires a high level of trust and performance due to the significance of these tasks. Hence, there have been investigations into a general architecture for application program interfaces (APIs) with which to handle the considerable diversity of RFID equipment available for industrial environments [50], and to improve communication speed and reliability for a large population of tags using an estimator to maximize the efficiency of channel usage [51].
RFID communication protocols offer protection against tag tracking, replay attacks, and cloning attacks, among others, enabling a balance between security and high efficiency [52,53]. Alternatively, some protocols tend to be lightweight or ultra-lightweight, such as the mutual authentication protocol, revised to be more secure and enforced using a cache on the reader side [54,55]. However, investigations are going further and defining an address translation protocol enabling RFID to IP for complete IoT communication [56]. Equally, for security, cryptanalysis is applied to ultra-lightweight mutual authentication to ensure untraceability and identify vulnerabilities [57,58,59]. Another concern in RFID protocols is privacy, which, in some cases, limits the use of this technology. Therefore, investigators are working on an anonymous authentication protocol to protect against clandestine tracking [60,61]. Consequently, to test and validate these changes, it is necessary to use a framework to model and simulate new protocols to evaluate their robustness [62].
3.2. Supply Chain Management (SCM)
RFID for supply chain management (SCM) plays a critical role in connecting the physical world with management systems; RFID collects data to be analyzed and improves the quality of management, which is an area of special interest for large enterprises [63]. For example, by applying a framework for the development of RFID, the operation efficiency can be improved, and competitive advantage can be enhanced [64]. Additionally, in the search for a smarter process [65], researchers are analyzing the effect in e-supply chains for grocery retailing [66]; the benefits, challenges, and effects that RFID applications may bring for retail in the UK [67]; the application in convenience stores in Taiwan [68]; and comparing RFID benefits for USA and Republic of Korea (South Korea) [69]. However, it is important to perform a mean-variance analysis to implement smart shelves [70], with identification at the item level in the retail supply chain, and determine how the cost should be allocated among the partners and its application on a sales floor [3,4]. In the same way, the available software solutions and information systems for supply chain coordination have been investigated [71], assessing the performance gained by implementing RFID [72,73], using methods such as quantitative evaluation [74] or using empirical evidence [75,76]. By contrast, investigators consider different variables in the supply chain, such as the effects of tag orientation and package contents affecting the tag reading, resulting in inconsistencies [77]. There is a drive for increased speed in processes using RFID portable devices in construction supply chains [78]. The supply chain can generate a vast amount of data that need to be processed and managed [79] using an efficient storage scheme and query process on relational databases [80,81], no-relational repository designs in MongoDB [82], or a method for processing massive amounts of data using path encoding [83]. All these data can be either important or not, based on their attributes [84]. For this reason, it is necessary to use a model to quantify the quality of the data [85], according to factors that may affect the economy. Inventory register inaccuracies can have negative consequences [86,87]; on the other hand, the adoption of RFID can help to prevent counterfeiting and fake products [88,89], in critical supply chains such as medicine [90,91,92], where the protection of privacy and security is of utmost importance [93,94,95]. These advantages acquired by using RFID come with economical costs to be considered [96,97,98]. Finally, RFID can be applied in close-loop supply-chains to cut costs in large business applications [99,100,101].
3.3. Localization
RFID technology’s primary function is the identification of objects, but investigations are pushing beyond the limits of this technology to expand its capabilities, allowing localization information to be obtained from specific indoor scenarios where global positioning system (GPS) devices generally do not work. Examples of these applications are real-time location tracking with high precision via RFID tags using commercial off-the-shelf (COTS) devices [7], a standalone positioning system using low-cost passive RFID tags installed to guide the path [102], the location of tags that are not in line of sight (NLOS) for the reader [103,104,105], and navigation for autonomous mobile robots based on passive RFID tags to be applied in indoor environments [106,107,108]. Alternatively, for industrial mobile vehicles and robots, the signal strength indicator from the vehicle’s transponder makes the vehicle move when RFID UHF tags are read [109,110]. In a similar way, it enables the location and approach to a stationary target object using the same principle [111]. Another example is occupancy monitoring for smart buildings and indoor environments, focusing on improving the energy usage in these spaces [112,113]. RFID is even used in the construction of buildings, enforcing management and safety, besides facilitating the location and tracking of people, equipment, and materials in realistic construction environments [114,115,116]. Additionally, RFID is used to enable high accuracy in assisted positioning in vehicular ad hoc networks (VANETS) [117]. The use of ultra-wideband (UWB) is ever advancing, overcoming most of the current limitations of narrowband, such as low area coverage, interference, and limited multiple-access capability [118]. This is enhancing the location applications of RFID, and new propagation models are being tested [119], with alternative location techniques for tags using phase differences, obtaining better accuracy, robustness and sensitivity when integrated with other measurements [120]. Consequently, investigators are finding solutions to this technology’s challenges, such as through millimeter-level ranging based on backscatter RF tags [121] or the usage of phased array antennas to determine the precise angles and positions of small passive RFID tags [122].
3.4. Traceability
Traceability provides information about the event history, locations, or application of tagged elements in the supply chain, including origin and destination. Traceability systems based on RFID are being studied, aiming at a reduction in costs, improving customer service and decision making [72], and allowing different applications, such as traceability in food supply chains [123]; traceability in the context of cattle/beef quality and safety in China [124]; traceability systems incorporating 2D bar codes and RFID for wheat flour mills [125]; the use of RFID, bar codes, and digital weighing technologies in manual fruit harvesting [126]; advanced tracing in aquaculture supply chains, allowing the product to be traced from the farm to the consumer [127]; and performance evaluation. This is relevant not only in intercontinental flesh fish logistics [128], but also in the supply chains of living fish [129]. Lessons have been learned from its application in an aircraft engineering company [130], and the tracing of beef from farm to slaughter in Ireland [131]. Moreover, there have been advances in data analysis using semantic trajectories centering on the behavioral patterns of moving objects, without neglecting the privacy issues that arise due to the semantic aspects of trajectories [132]. Realizing RFID-based traceability improves production scheduling in a job-shop environment [133]; traceability across sovereign, distributed RFID databases [134]; and the automatic tracing of production with mobile and agent-based computing [135]. Moreover, it is important to know the perceived benefits and drawbacks of the technologies used in tracking to identify the factors that influence consumers’ perceptions of these technologies in their lives [136].
3.5. Logistics Management
In logistics, RFID technology is used in acquiring data that allow the visualization and production of analytics, such as on a shop floor, where large quantities of data are generated [1,2], and material tracking for construction logistics [137]. Applications such as these demand the implementation of intelligent network systems for collecting information to be analyzed and deployed in real time [138]. Moreover, studies on the retail sector have led to a contingency model for identifying the most important elements of RFID supply chain projects for application in logistics and manufacturing environments [139]. Similarly, researchers have defined a framework for assessing RFID applications for logistics [140]. There is research on optimizing operations using a distributed simulation platform to design advanced RFID-based freight transportation systems [141]. This will further allow vehicle management in logistics to work along with global positioning systems (GPS) and geographic information systems (GIS) [142]. An architecture for improving terrestrial logistics has also been described [143]. Additionally, researchers have worked on a method based on fuzzy scorecard for logistics management in robust supply chain management (SCM) to evaluate the overall performance in real-time [144]. An analysis and comparison of RFID and Auto-ID for logistics performance were also conducted [145]. Thus, it is possible to extend the functionality in logistics using the simultaneous operation of RFID and bar-codes [146], or the knowledge-based logistics management system (KLMS) design to support service providers in making more contextualized decisions [147].
3.6. Ubiquitous Computing
As mentioned previously and shown in the previous and following sections in this paper, RFID is present in many places and environments. It usually works in a transparent manner. This section describes different examples and utilities for ubiquitous RFID—for example, tracking autonomous entities in indoor environments using RFID, and makes a comparison with other technologies [148]. RFID is ubiquitous by its use, not only in home-health monitoring with context awareness [149], but also in mobile telemedicine systems for perceiving emergencies in older adults [150]. RFID is also applied in the classroom for identifying and obtaining context services, focusing on natural interaction with the system [151]. Alternatively, in large deployments such as the smart cities case, it helps in identification in massive streams of real-time data [152]. On the other hand, it can be present even in a simple game of cards, adding new features using computers [153]. This type of application makes the creation of frameworks to support the process of creation necessary, making the development easier, as shown in [154]. It can be seen that this technology is advancing in every regard; whether this is a good situation can be questioned, considering the impacts of ubiquitous computing from legal and social perspectives [155].
3.7. Healthcare
RFID is important in the Internet of Things (IoT) ecosystem. One can observe the active integration of RFID in healthcare environments, supporting various processes. This section describes some of the solutions implemented or explored for these sensitive environments. For example, in IoT-based healthcare smart spaces, investigators have explored the use of RFID in body-centric systems and for gathering information such as temperature, humidity, and other variables related to the user’s living environment [8]. In addition, RFID is used in devices for managing diabetes therapy in ambient assisted living (AAL) spaces [9]. It is also used to store healthcare events on large HF RFID memory tags and integrated with Twitter services to keep the patient’s relatives up to date [156]. The IoT is applied to healthcare through RFID-enabled asset management to evaluate the advantages and impact obtained [157,158]; there is an IoT hybrid monitoring system for healthcare environments called “CUIDATS”, which integrates RFID and wireless sensor network (WSN) technologies [159]. RFID-IPv6 has been used in healthcare, making the deployment less costly with less maintenance [160].RFID is applied for protecting medical privacy to mitigate the risk of the disclosure of patient data, along with an IoT security infrastructure [161]; an RFID-based security platform for a healthcare environment where the data collected from the patient is extremely sensitive has been developed [162]. A signing platform based on RFID to manage health workers regarding work efficiency in real time has been realized [163]. Other applications can be found in an intelligent warning system to provide real-time visual and auditive warnings to other drivers when an emergency vehicle needs to pass through at an intersection [158].
3.8. Access Control
Access control can limit entry to a physical space or access a tag’s data or backend services through a middle-ware system; as a result, RFID is applied in different ways to control multiple types of systems. One application is protecting people’s privacy by excluding irrelevant information for spaces under video surveillance, by limiting the recording based on RFID [164,165]. This access control can be performed by applying frameworks to stop unauthorized readers from accessing tags that could result in unauthorized access to stored information [166]. In the same way, when the access needs to be limited to the right stakeholders and systems, different methods have been investigated, for example, asymmetric keys for mutual authentication [167], digital signature systems [168], role-based access applied to the readers [169], or using protocols based on the ownership of the tags [170]. In the past, systems have been breached, such as the case of the cloning of MiFare Passes [171]. Therefore, practices such as the reuse of tags by multiple companies can be dangerous [172]. This necessitates the analysis of the security used and fine credential management [173] for data access control [174,175] or document access control [176]. However, in mobile objects, the implementation of security significantly degrades the system’s performance or changes the data capture, affecting the storage of information, which has led to the development of models and policies for improving confidentiality protection and governance for object tracking data [177,178]. There are access control methods based on IPv6 [179], more simple approaches that work without a backend system [180], and hybrid systems that support online and offline modes, to adapt according to the rules [181]. These methods are used, for example, to control access for vehicles [182] and healthcare environments [182]. Equally important are management systems for applying access control and positioning security [183]. The systems offer different authentication and access control methods that need to be analyzed to guarantee their safe application in different environments [184]. In the same way, the GS1 Electronic Product Code Global (EPCglobal) network is designed to provide a common language for supply chains by which to share information in a secure manner [185]. However, new models are sometimes necessary to maintain the level of privacy in the process [186], similarly to the concerns regarding privacy and access control policy implementation to control middle-ware systems [187,188]. Finally, it is observed that investigations tend to focus on futuristic applications such as human microchip implants, making necessary the evaluation of the relationship between risks and rewards [189], analyzing if there exists a more secure method of implementation [190], and exploring the current perceived barriers in these application scenarios [191].
4. Security and Privacy
One of the major concerns in many applications is the security and privacy of data. The main factor is the fast expansion and Internet diversification in the IoT and related services. This has led to various concerns, such as those regarding the security of currently used protocols, such as the mutual authentication protocol. Additionally, it is necessary to analyze existing attacks and their solutions, and evaluate currently used standards such as the EPC Global C1G2, to better protect the main technology users.
Investigations are testing and searching for new methods for RFID readers, tags, middle-ware, and backend systems. The relevance of this situation can be confirmed by the average number of publications per year related to security shown in Figure 4, with the more important indicators shown in Table 3, presenting values close to the IoT topic in the application section in Table 2. Thus, the authentication topic shows the same behavior. The majority of the studies are focused on the authentication between the reader and tags, exploring new methods for protecting this communication against different identified attacks, maintaining a steady AGR as presented in Table 3. Similarly, the ownership transfer topic explores new methods for enforcing security in the actual transfer of tags, protecting the privacy of the parts and exploring the scalability of the process to secondhand markets and circular supply chains. The evolution of these topics is shown in graph (a) on the left in Figure 4, and the topics are presented in more detail below.
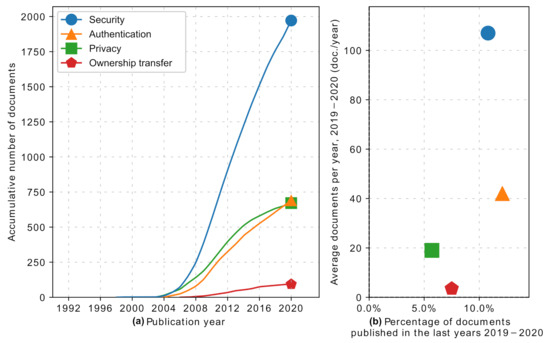
Figure 4.
(a) Security and related topics, number of publications by year. (b) Average number of publications per year and percentage of documents published between 2019–2020.

Table 3.
Top author keywords for security- and privacy-related topics.
All the expansion and diversification in Internet-related services are generating new security and privacy challenges [192]. For this reason, the most common issues, practices, and architectures are listed, to mitigate frequent privacy and security issues [193]. “Strong privacy” has been defined, and the definition has been applied to reveal vulnerabilities in proposed privacy-enhancing RFID protocols [194]. Different security threats derived from the implementation of RFID systems in supply chain scenarios have also been explored [195]. Privacy and security have been enhanced using scalable server-less authentication and search protocols for the reader and tag communication for pervasive environments [196]. A customized infrastructure based on smart devices to enforce the privacy of individuals in healthcare scenarios has been developed [197]. Investigators are analyzing existing RFID tags regarding privacy and security aspects, providing an overview of all the types of privacy and security problems and their countermeasures [198]. In addition, the threats and measures for all the types of security threats in the IoT in general are being investigated [199].
One of the most explored topics is the mutual authentication protocol used, which has been analyzed in different ways. For example, investigations have explored possible attacks in mutual authentication protocols and proposed improvements to eliminate them [200]. Equally, there have been advances in research for new mutual agreement protocols to ensure secure communication between mobile RFID-enabled devices and the main server [201,202]. In the same way, cryptanalysis application in lightweight mutual authentication, and ownership transfer for RFID systems [203], or improvements to the hash-based RFID mutual authentication protocol to avoid denial of service (DoS) attacks have been explored [204]. Alternatively, an RFID authentication scheme based on quadratic residues has been implemented to address impersonation and replay attacks [205], and new methods such as chaotic map usage to guarantee a mutually authenticated process using a chaotic cryptosystem have been researched [206]. However, due to the tags’ hardware limitations, there is a search for the most efficient ultra-lightweight authentication protocol [207]. Finally, work is in progress to confirm GS1 EPC Class 1 Generation 2 standards for RFID, including mutual authentication and privacy protection to reduce database loading and ensure user privacy [208].
Robust security and high privacy are necessary for all RFID contexts, including low-cost RFID networks [209]. All the mentioned protocols and security measures will eventually reach the general public in everyday environments. For example, deploying frameworks to preserve privacy in RFID-based healthcare systems is one of the most prominent applications for these technologies [210]. Additionally, the rapid spread of RFID makes security one of the main concerns in the context of the IoT [29].
4.1. Authentication
The flexibility of RFID tags in terms of the forms and variety of working frequencies allows the diverse investigation of adaptations for different and changing environments, such as solutions to guarantee secure and efficient medication for patients [211]. The definition of protocols such as the Chien’s protocol and other ultra-lightweight RFID for authentication allows improvements to ensure security against known vulnerabilities [212,213]. In the same way, a lightweight authentication protocol for low-cost RFID with untraceability in mind has been described [214]. Cryptanalysis has been applied to protocols conforming to the EPC-C1G2 standard, analyzing the security level offered [215]. Similarly, the security implications in RFID and authentication processing frameworks have been analyzed, exploring a robust protocol based on error correction codes (ECC) [166], or the intrinsic usage of physical-layer authentication using integrated circuits to counteract device cloning [216]. Security has been improved by creating efficient techniques with which to monitor missing RFID tags [217]. Correspondingly, a protocol has been defined to provide coexistence proofs for RFID tags to detect tagged elements shown at the same time and in the same place [218].
4.2. Ownership Transfer
In enterprise-level applications and supply-chain environments, RFID tags cross different entities and places; in some cases, it is necessary to transfer control over the RFID tags, raising concerns regarding privacy when the tag travels from A to B [219]. These tasks need to be performed securely using protocols conforming to EPCglobal class-1 generation-2 standards [220,221,222,223], and methods to improve the current protocols to offer enhanced security in ownership transfer operations are needed [224,225]. Ownership transfer is applied on mobile RFIDs, taking into consideration all the components from handheld readers to the backend server [226]. Additionally, protocols implement new methods for ensuring privacy for tag owners, and allowing secure, private, and scalable ownership-transfer [227]. Equally, it is important to ensure a secure, counterfeit-proof transaction for low-cost RFID systems where the tags have very limited resources [228,229]. To enhance the security in the transfer operation, additional measures are used, such as electronic fingerprints [230], group tag ownership transfer [231], and physically unclonable function (PUF)-based transfer for open environments using unique hardware characteristics to replace the pseudorandom generator [232]. The elliptical curve application has been used to provide controlled delegation [233]. Correspondingly, there is a search for methods with which to attack the ownership transfer system using de-synchronization based on quadratic residues [234]. However, in some cases, a protocol is needed to ensure untraceability from the previous owner in a transfer operation; to archive this, a challenge-response mechanism is proposed [235]. Moreover, new optional modes of ownership transfer are created, which let the previous owner maintain control in some specific scenarios [236]. Finally, the post-supply chain scenario has been investigated, exploring potential application in retailer and second-hand transactions or circular supply chains in the near future [237].
5. Discussion
Applications of RFID technologies were found in many contexts, from asset identification to tracking for industrial [5,6] and general [7] public environment applications, for instance, indoor applications [102,103], robot navigation [106,109,110,111], and the positioning of objects, even those not visible [104,112,117]. Ultra-wideband has been used to overcome some of the current problems with narrowband frequencies [114,118]. Additionally, it helps organizations with management and safety for construction [115,116] and pushes the limits of transmission signals’ ability to enhance the quality [119,120,121,122] in different frequencies [6,118].
We found privacy and authenticity to be of utmost concern [209,228,229]. In this review, we focused on the most active RFID applications based on scientometric variables, resulting in eleven groups. The applications characterized for this technology especially concern the IoT, which supports the idea that RFID is a key requirement for the Internet of Things [28,29,30]. We also found RFID to be applied in supply chains [72,73], providing ways to detect counterfeiting [91,92] and keep track of any asset [90,123,127,128,129]. The most active security topics appear to be testing the existing protocols to search for flaws, ways to solve them [93,94,173,177,178,196,198], and balancing privacy and performance for different scenarios [192,193,196,198,199]. It was found that privacy and security are of general concern, almost in all applications. In addition, it was noted that healthcare is a topic that shows a positive AGR in the results, and it includes RFID in different related operations [8,9,149,156,157,158,159,160,161,162,163,182,197,210]. RFID is also used in access control, such as for managing access to spaces and systems [173,174,175,176,177,178], and its use in the human body has also been explored from different perspectives [189,190,191].
Some other recent papers have focused on specific topics, so this paper can serve as an entry point, providing a global view to help researchers to explore the most active topics, trending applications and security work in RFID, information that is valuable to people of different backgrounds and interests. During this research, it was observed that the application of RFID continues to grow, with management of the complexity in security models [34,40,62,85,177,178] and protocols [31,39,51,54,55,56,59,60,61,62,161,196,200,201,202,204,207,212,213,235].
As noted throughout the paper, RFID is used in diverse scenarios and continues to grow in its applications and functionalities, such as working with wireless sensors and IPv6, the new addressing system for the IoT, expanding its frequencies wherein technological advances are permitted (currently to ultra-wideband). Thus, this technology can find emerging utility in RF, electronics, and security, and it is not an exaggeration to state that RFID will be the technology that will allow reaching the point, through the IoT, where every existing object will be able to be connected to the Internet.
We used the centralized and primary databases Clarivate, WoS and Scopus. Further investigations could analyze databases that harvest information rapidly to obtain cutting-edge information on RFID research activity and its relation to emerging and trending technologies.
Author Contributions
C.M.-A., J.R.-R., and G.R.-G. proposed the concept of this research. C.M.-A. and J.R.-R. proposed the used methodology. J.R.-R. and G.R.-G. designed the scientometric analysis. J.R.-R. do review and editing. C.M.-A. wrote the paper. G.R.-G. supervised the process. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing is not applicable to this article.
Acknowledgments
This research was conducted as part of the MSc program in Telematic Engineering at the Universidad del Cauca, Popayán, Colombia, and by the Universidad del Cauca (501100005682).
Conflicts of Interest
The authors declare that they have no known competing financial interests or personal relationships that have, or could be perceived to have, influenced the work reported in this article.
References
- Zhong, R.Y.; Lan, S.; Xu, C.; Dai, Q.; Huang, G.Q. Visualization of RFID-enabled shopfloor logistics Big Data in Cloud Manufacturing. Int. J. Adv. Manuf. Technol. 2016, 84, 5–16. [Google Scholar] [CrossRef]
- Zhong, R.Y.; Xu, C.; Chen, C.; Huang, G.Q. Big Data Analytics for Physical Internet-based intelligent manufacturing shop floors. Int. J. Prod. Res. 2017, 55, 2610–2621. [Google Scholar] [CrossRef]
- Gaukler, G.M.; Seifert, R.W.; Hausman, W.H. Item-level RFID in the retail supply chain. Prod. Oper. Manag. 2007, 16, 65–76. [Google Scholar] [CrossRef]
- Loebbecke, C.; Huyskens, C.; Gogan, J. Emerging technologies in the service sector: An early exploration of item-level RFID on the fashion sales floor. In Proceedings of the International Working Conference on Information Technology in the Service Economy—Challenges and Possibilities for the 21st Century, Toronto, ON, Canada, 10–13 August 2008; Springer: Berlin/Heidelberg, Germany, 2008; Volume 267, pp. 189–198. [Google Scholar] [CrossRef]
- Velandia, D.M.S.; Kaur, N.; Whittow, W.G.; Conway, P.P.; West, A.A. Towards industrial internet of things: Crankshaft monitoring, traceability and tracking using RFID. Robot.-Comput.-Integr. Manuf. 2016, 41, 66–77. [Google Scholar] [CrossRef]
- Zhai, C.; Zou, Z.; Zhou, Q.; Mao, J.; Chen, Q.; Tenhunen, H.; Zheng, L.; Xu, L. A 2.4-GHz ISM RF and UWB hybrid RFID real-time locating system for industrial enterprise Internet of Things. Enterp. Inf. Syst. 2017, 11, 909–926. [Google Scholar] [CrossRef]
- Yang, L.; Chen, Y.; Li, X.Y.; Xiao, C.; Li, M.; Liu, Y. Tagoram: Real-Time Tracking of Mobile RFID Tags to High Precision Using COTS Devices. In Proceedings of the 20th ACM Annual International Conference on Mobile Computing and Networking (MobiCom), Maui, HI, USA, 7–11 September 2014; Association for Computing Machinery Learned Society: New York, NY, USA, 2014; pp. 237–248. [Google Scholar] [CrossRef]
- Amendola, S.; Lodato, R.; Manzari, S.; Occhiuzzi, C.; Marrocco, G. RFID Technology for IoT-Based Personal Healthcare in Smart Spaces. IEEE Internet Things J. 2014, 1, 144–152. [Google Scholar] [CrossRef]
- Jara, A.J.; Zamora, M.A.; Skarmeta, A.F.G. An internet of things-based personal device for diabetes therapy management in ambient assisted living (AAL). Pers. Ubiquitous Comput. 2011, 15, 431–440. [Google Scholar] [CrossRef]
- Nambiar, A.N. RFID Technology: A Review of its Applications. In Proceedings of the World Congress on Engineering and Computer Science, San Francisco, CA, USA, 20–22 October 2009; International Association of Engineers: Hong Kong, China, 2009; pp. 1253–1259. [Google Scholar]
- Thakare, Y.; Musale, S.; Ganorkar, S. A technological review of RFID & applications. In Proceedings of the IET Conference on Wireless, Mobile and Multimedia Networks, Mumbai, India, 11–12 January 2008; pp. 65–70. [Google Scholar] [CrossRef]
- Ngai, E.W.T.; Moon, K.K.L.; Riggins, F.J.; Yi, C.Y. RFID research: An academic literature review (1995–2005) and future research directions. Int. J. Prod. Econ. 2008, 112, 510–520. [Google Scholar] [CrossRef]
- Chao, C.C.; Yang, J.M.; Jen, W.Y. Determining technology trends and forecasts of RFID by a historical review and bibliometric analysis from 1991 to 2005. Technovation 2007, 27, 268–279. [Google Scholar] [CrossRef]
- Khoo, B. RFID—From tracking to the internet of things: A review of developments. In Proceedings of the 2010 IEEE/ACM Int’l Conference on Green Computing and Communications & Int’l Conference on Cyber, Physical and Social Computing, Hangzhou, China, 18–20 December 2010; pp. 533–538. [Google Scholar] [CrossRef]
- Zhang, X.D.; Yue, S.J.; Wang, W.M. The review of RFID applications in global postal and courier services. J. China Univ. Posts Telecommun. 2006, 13, 106–110. [Google Scholar] [CrossRef]
- Mishra, A.; Mishra, D. Application of RFID in Aviation Industry: An exploratory review. Promet-Traffic Transp. 2010, 22, 363–372. [Google Scholar] [CrossRef]
- Valero, E.; Adan, A.; Cerrada, C. Evolution of RFID Applications in Construction: A Literature Review. Sensors 2015, 15, 15988–16008. [Google Scholar] [CrossRef]
- Gulcharan, N.F.B.I.; Daud, H.; Nor, N.M.; Ibrahim, T.; Nyamasvisva, E.T. Limitation and Solution for Healthcare Network Using RFID Technology: A Review. In Proceedings of the 4th International Conference on Electrical Engineering and Informatics (ICEEI), Bangi, Malaysia, 24–25 June 2013; Elsevier: Amsterdam, The Netherlands, 2013; Volume 11, pp. 565–571. [Google Scholar] [CrossRef]
- Kolokathi, A.; Rallis, P. Radio Frequency Identification (RFID) in Healthcare: A Literature Review. In Proceedings of the 11th International Conference on Informatics, Management, and Technology in Healthcare (ICIMTH), Athens, Greece, 5–7 July 2013; IOS PRESS: Amsterdam, The Netherlands, 2013; Volume 190, pp. 157–159. [Google Scholar] [CrossRef]
- Haddara, M.; Staaby, A. RFID Applications and Adoptions in Healthcare: A Review on Patient Safety. In Proceedings of the International Conference on Health and Social Care Information Systems and Technologies (HCIST), Lisbon, Portugal, 21–23 November 2018; Elsevier: Amsterdam, The Netherlands, 2018; Volume 138, pp. 80–88. [Google Scholar] [CrossRef]
- Sarac, A.; Absi, N.; Dauzere-Peres, S. A literature review on the impact of RFID technologies on supply chain management. Int. J. Prod. Econ. 2010, 128, 77–95. [Google Scholar] [CrossRef]
- Musa, A.; Dabo, A.A. A Review of RFID in Supply Chain Management: 2000–2015. Glob. J. Flex. Syst. Manag. 2016, 17, 189–228. [Google Scholar] [CrossRef]
- Labbi, Z.; Senhadji, M.; Maarof, A.; Belkasmi, M. IoT smart homes based on RFID technology: Localization systems review. Association for Computing Machinery. In Proceedings of the 4th International Conference on Engineering and MIS, Istanbul, Turkey, 19–20 June 2018. [Google Scholar] [CrossRef]
- Chanchaichujit, J.; Balasubramanian, S.; Charmaine, N.S.M. A systematic literature review on the benefit-drivers of RFID implementation in supply chains and its impact on organizational competitive advantage. Cogent Bus. Manag. 2020, 7. [Google Scholar] [CrossRef]
- Sharma, D.; Mahto, R.; Harper, C.; Alqattan, S. Role of RFID technologies in transportation projects: A review. Int. J. Technol. Intell. Plan. 2020, 12, 349–377. [Google Scholar] [CrossRef]
- Ruiz-Rosero, J.; Ramirez-Gonzalez, G.; Viveros-Delgado, J. Software survey: ScientoPy, a scientometric tool for topics trend analysis in scientific publications. Scientometrics 2019, 121, 1165–1188. [Google Scholar] [CrossRef]
- Jarke, M.; Lenzerini, M.; Vassiliou, Y.; Vassiliadis, P. Fundamentals of Data Warehouses; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Jia, X.; Feng, Q.; Fan, T.; Lei, Q. RFID technology and its applications in Internet of Things (IoT). In Proceedings of the 2012 2nd International Conference on Consumer Electronics, Communications and Networks, Yichang, China, 21–23 April 2012; pp. 1282–1285. [Google Scholar] [CrossRef]
- Aggarwal, R.; Das, M. RFID security in the context of internet of things. In Proceedings of the 1st International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012; pp. 51–56. [Google Scholar] [CrossRef]
- Chen, B.; Dai, Y.; Jin, B.; Zou, X.; Zhou, L. The RFID-based electronic identity security platform of the Internet of Things. In Proceedings of the 2011 International Conference on Mechatronic Science, Electric Engineering and Computer, Jilin, China, 19–22 August 2011; pp. 246–249. [Google Scholar] [CrossRef]
- Ray, B.R.; Abawajy, J.; Chowdhury, M. Scalable RFID security framework and protocol supporting Internet of Things. Comput. Netw. 2014, 67, 89–103. [Google Scholar] [CrossRef]
- Das, M.L. Strong Security and Privacy of RFID System for Internet of Things Infrastructure. In Proceedings of the 3rd International Conference on Security, Privacy, and Applied Cryptography Engineering (SPACE), Kharagpur, India, 19–23 October 2013; Springer: Berlin/Heidelberg, Germany, 2013; Volume 8204, pp. 56–69. [Google Scholar]
- Khan, W.Z.; Zangoti, H.M.; Aalsalem, M.Y.; Zahid, M.; Arshad, Q. Mobile RFID in Internet of Things: Security Attacks, Privacy Risks, and Countermeasures. In Proceedings of the International Conference on Radar, Antenna, Microwave, Electronics, and Telecommunications (ICRAMET), Jakarta, Indonesia, 3–5 October 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 36–41. [Google Scholar]
- Chamekh, M.; Hamdi, M.; El Asmi, S.; Kim, T.H. Security of RFID Based Internet of Things Applications: Requirements and Open Issues. In Proceedings of the 15th International Multi-Conference on Systems, Signals and Devices (SSD), Hammamet, Tunisia, 19–22 March 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 699–703. [Google Scholar]
- Shao, X. Study on security issue of internet of things based on RFID. In Proceedings of the 4th International Conference on Computational and Information Sciences, Chongqing, China, 17–19 August 2012; pp. 566–569. [Google Scholar] [CrossRef]
- Singh, N.; Hans, A.; Kaur, S. Layer and RFID Based Security Issues of Internet of Things. Int. J. Grid Distrib. Comput. 2016, 9, 301–310. [Google Scholar] [CrossRef]
- Jin, H.Y.; Tian, M. Research on security issues of RFID technology in IOT. In Proceedings of the 2012 National Conference on Information Technology and Computer Science, Lanzhou, China, 16–18 November 2012; pp. 52–54. [Google Scholar]
- Fan, K.; Li, J.; Li, H.; Liang, X.; Shen, X.; Yang, Y. ESLRAS: A lightweight RFID authentication scheme with high efficiency and strong security for internet of things. In Proceedings of the 2012 4th International Conference on Intelligent Networking and Collaborative Systems, Bucharest, Romania, 19–21 September 2012; pp. 323–328. [Google Scholar] [CrossRef]
- Sharma, V.; Vithalkar, A.; Hashmi, M. Lightweight Security Protocol for Chipless RFID in Internet of Things (IoT) Applications. In Proceedings of the 10th International Conference on Communication Systems and Networks (COMSNETS), Bangalore, IN, USA, 3–7 January 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 468–471. [Google Scholar]
- Zhu, W.; Yu, J.; Wang, T. A Security and Privacy Model for Mobile RFID Systems in the Internet of Things. In Proceedings of the 14th IEEE International Conference on Communication Technology (ICCT), Chengdu, China, 9–11 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 726–732. [Google Scholar]
- Fernandez-Carames, T.M.; Fraga-Lamas, P.; Suarez-Albela, M.; Castedo, L. Reverse Engineering and Security Evaluation of Commercial Tags for RFID-Based IoT Applications. Sensors 2017, 17, 28. [Google Scholar] [CrossRef]
- Bendavid, Y.; Bagheri, N.; Safkhani, M.; Rostampour, S. IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors 2018, 18, 4444. [Google Scholar] [CrossRef]
- Rekleitis, E.; Rizomiliotis, P.; Gritzalis, S. How to protect security and privacy in the IoT: A policy-based RFID tag management protocol. Secur. Commun. Netw. 2014, 7, 2669–2683. [Google Scholar] [CrossRef]
- Figueroa, S.; Anorga, J.; Hernantes, J.; Francisco Carias, J.; Arrizabalaga, S. A RFID-based IoT Cybersecurity Lab in Telecommunications Engineering. In Proceedings of the 13th Technologies Applied to Electronics Teaching Conference (TAEE), La Laguna, Spain, 20–22 June 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar] [CrossRef]
- Abdolmaleki, B.; Baghery, K.; Khazaei, S.; Aref, M.R. Game-Based Privacy Analysis of RFID Security Schemes for Confident Authentication in IoT. Wirel. Pers. Commun. 2017, 95, 5057–5080. [Google Scholar] [CrossRef]
- Kypus, L.; Vojtech, L.; Kvarda, L. Qualitative And Security Parameters Inside Middleware Centric Heterogeneous RFID/IoT Networks, On-Tag Approach. In Proceedings of the 38th International Conference on Telecommunications and Signal Processing (TSP), Prague, Czech Republic, 9–11 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 21–25. [Google Scholar]
- Haenel, T.; Bothe, A.; Helmke, R.; Gericke, C.; Aschenbruck, N. Adjustable Security for RFID-Equipped IoT Devices. In Proceedings of the IEEE International Conference on RFID Technology and Application (RFID-TA), Warsaw, Poland, 20–22 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 208–213. [Google Scholar]
- Li, Z.; Wang, X. The Framework of Security Mechanism on the Internet of Things Based on RFID Boosting Low-Carbon Economy. In Proceedings of the International Conference on Low-carbon Transportation and Logistics, and Green Buildings (LTLGB), Beijing, China, 12–13 October 2012; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1007–1013. [Google Scholar] [CrossRef]
- Petracca, M.; Bocchino, S.; Azzara, A.; Pelliccia, R.; Ghibaudi, M.; Pagano, P. WSN and RFID integration in the IoT scenario: An advanced safety system for industrial plants. J. Commun. Softw. Syst. 2013, 9, 104–113. [Google Scholar] [CrossRef]
- Liu, Y.; Li, G.W.; Gao, S. The Design of RFID Middleware Architecture for Application in the Advanced Manufacturing Industry and the Internet of Things. In Proceedings of the International Conference on Industrial Technology and Management Science (ITMS), Tianjin, China, 27–28 March 2015; Volume 34, pp. 1482–1487. [Google Scholar]
- de Barros Filho, I.E.; Silva, I.; Viegas, C.M.D. An Effective Extension of Anti-Collision Protocol for RFID in the Industrial Internet of Things (IIoT). Sensors 2018, 18, 4426. [Google Scholar] [CrossRef]
- Gao, H.; Guo, Y.; Cui, J.; Hao, H.; Shi, H. A communication protocol of RFID systems in internet of things. Int. J. Secur. Its Appl. 2012, 6, 91–102. [Google Scholar]
- Zhang, Z.; Xu, Q.L. Universal composable grouping-proof protocol for RFID tags in the internet of things. Jisuanji Xuebao/Chinese J. Comput. 2011, 34, 1188–1194. [Google Scholar] [CrossRef]
- Yin, Y.; Xu, M.; Zhang, Q.; Chen, J. Cryptanalysis of A New Lightweight RFID Mutual Authentication Protocol with Cache in Reader for IoT. In Proceedings of the IEEE 2nd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 December 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 909–913. [Google Scholar]
- Fan, K.; Gong, Y.; Liang, C.; Li, H.; Yang, Y. Lightweight and ultralightweight RFID mutual authentication protocol with cache in the reader for IoT in 5G. Secur. Commun. Netw. 2016, 9, 3095–3104. [Google Scholar] [CrossRef]
- Toumi, K.; Ayari, M.; Azouz, S.L.; Bouet, M.; Pujolle, G. HAT: HIP address translation protocol for hybrid RFID/IP internet of things communication. In Proceedings of the International Conference on Wireless and Ubiquitous Systems, Sousse, Tunisia, 8–10 October 2010. [Google Scholar] [CrossRef]
- Tewari, A.; Gupta, B.B. Cryptanalysis of a novel ultra-lightweight mutual authentication protocol for IoT devices using RFID tags. J. Supercomput. 2017, 73, 1085–1102. [Google Scholar] [CrossRef]
- Khalid, M.; Mujahid, U.; Najam-ul Islam, M. Cryptanalysis of ultralightweight mutual authentication protocol for radio frequency identification enabled Internet of Things networks. Int. J. Distrib. Sens. Netw. 2018, 14. [Google Scholar] [CrossRef]
- Xu, D.; Chen, Y. A safe RFID authentication protocol for Internet of Things. J. Theor. Appl. Inf. Technol. 2013, 48, 359–364. [Google Scholar]
- Asadpour, M.; Dashti, M.T. Scalable, privacy preserving radio-frequency identification protocol for the internet of things. Concurr.-Comput.-Pract. Exp. 2015, 27, 1932–1950. [Google Scholar] [CrossRef]
- Zhu, W.L.; Yu, J.P. A privacy preserving three-party authentication protocol for RFID systems in the internet of things. Shenzhen Daxue Xuebao (Ligong Ban)/J. Shenzhen Univ. Sci. Eng. 2012, 29, 95–99. [Google Scholar] [CrossRef]
- Olaleye, O.G.; Ali, A.; Perkins, D.; Bayoumi, M. Modeling and Performance Simulation of PULSE and MCMAC Protocols in RFID-based IoT Network Using OMNeT plus. In Proceedings of the IEEE International Conference on RFID (RFID), Orlando, FL, USA, 10–12 April 2018; IEEE: Piscataway, NJ, USA, 2018. [Google Scholar]
- Xu, L.D. Information architecture for supply chain quality management. Int. J. Prod. Res. 2011, 49, 183–198. [Google Scholar] [CrossRef]
- Lin, L.C. An integrated framework for the development of radio frequency identification technology in the logistics and supply chain management. Comput. Ind. Eng. 2009, 57, 832–842. [Google Scholar] [CrossRef]
- Butner, K. The smarter supply chain of the future. Strategy Leadersh. 2010, 38, 22–31. [Google Scholar] [CrossRef]
- Prater, E.; Frazier, G. Future impacts of RFID on e-supply chains in grocery retailing. Supply Chain.-Manag.- Int. J. 2005, 10, 134–142. [Google Scholar] [CrossRef]
- Jones, P.; Clarke-Hill, C.; Hillier, D.; Comfort, D. The benefits, challenges and impacts of radio frequency identification technology (RFID) for retailers in the UK. Mark. Intell. Plan. 2005, 23, 395–402. [Google Scholar] [CrossRef]
- Hong, I.H.; Dang, J.F.; Tsai, Y.H.; Liu, C.S.; Lee, W.T.; Wang, M.L.; Chen, P.C. An RFID application in the food supply chain: A case study of convenience stores in Taiwan. J. Food Eng. 2011, 106, 119–126. [Google Scholar] [CrossRef]
- Kim, E.Y.; Ko, E.; Kim, H.; Koh, C.E. Comparison of benefits of radio frequency identification: Implications for business strategic performance in the US and Korean retailers. Ind. Mark. Manag. 2008, 37, 797–806. [Google Scholar] [CrossRef]
- Zhu, L.; Wang, P.; Xi, S. Mean-Variance Analysis of Retailers Deploying RFID-Enabled Smart Shelves. Information 2018, 9, 40. [Google Scholar] [CrossRef]
- Helo, P.; Szekely, B. Logistics information systems—An analysis of software solutions for supply chain co-ordination. Ind. Manag. Data Syst. 2005, 105, 5–18. [Google Scholar] [CrossRef]
- Sahin, E.; Dallery, Y.; Gershwin, S. Performance evaluation of a traceability system: An application to the radio frequency identification technology. In Proceedings of the 2002 IEEE International Conference on Systems, Man and Cybernetics, Yasmine Hammamet, Tunisia, 6–9 October 2002; Volume 3, pp. 647–650. [Google Scholar]
- Zelbst, P.J.; Green Kenneth, W., Jr.; Sower, V.E.; Baker, G. RFID utilization and information sharing: The impact on supply chain performance. J. Bus. Ind. Mark. 2010, 25, 582–589. [Google Scholar] [CrossRef]
- Hou, J.L.; Huang, C.H. Quantitative performance evaluation of RFID applications in the supply chain of the printing industry. Ind. Manag. Data Syst. 2006, 106, 96–120. [Google Scholar] [CrossRef]
- Visich, J.K.; Li, S.; Khumawala, B.M.; Reyes, P.M. Empirical evidence of RFID impacts on supply chain performance. Int. J. Oper. Prod. Manag. 2009, 29, 1290–1315. [Google Scholar] [CrossRef]
- Lin, C.Y.; Ho, Y.H. RFID technology adoption and supply chain performance: An empirical study in China’s logistics industry. Supply Chain.-Manag.- Int. J. 2009, 14, 369–378. [Google Scholar] [CrossRef]
- Clarke, R.; Twede, D.; Tazelaar, J.; Boyer, K. Radio frequency identification (RFID) performance: The effect of tag orientation and package contents. Packag. Technol. Sci. 2006, 19, 45–54. [Google Scholar] [CrossRef]
- Wang, L.C.; Lin, Y.C.; Lin, P.H. Dynamic mobile RFID-based supply chain control and management system in construction. Adv. Eng. Inform. 2007, 21, 377–390. [Google Scholar] [CrossRef]
- Melski, A.; Thoroe, L.; Schumann, M. Managing RFID data in supply chains. Int. J. Internet Protoc. Technol. 2007, 2, 176–189. [Google Scholar] [CrossRef]
- Lee, C.H.; Chung, C.W. Efficient storage scheme and query processing for supply chain management using RFID. In Proceedings of the 2008 ACM SIGMOD International Conference on Management of Data 2008, Vancouver, BC, Canada, 9–12 June 2008; pp. 291–302. [Google Scholar] [CrossRef]
- Fan, H.; Wu, Q.; Lin, Y.; Zhang, J. A Split-Path Schema-Based RFID Data Storage Model in Supply Chain Management. Sensors 2013, 13, 5757–5776. [Google Scholar] [CrossRef]
- Kang, Y.S.; Park, I.H.; Rhee, J.; Lee, Y.H. MongoDB-Based Repository Design for IoT-Generated RFID/Sensor Big Data. IEEE Sens. J. 2016, 16, 485–497. [Google Scholar] [CrossRef]
- Lee, C.H.; Chung, C.W. RFID Data Processing in Supply Chain Management Using a Path Encoding Scheme. IEEE Trans. Knowl. Data Eng. 2011, 23, 742–758. [Google Scholar] [CrossRef]
- Sellitto, C.; Burgess, S.; Hawking, P. Information quality attributes associated with RFID-derived benefits in the retail supply chain. Int. J. Retail Distrib. Manag. 2007, 35, 69–87. [Google Scholar] [CrossRef]
- Kelepouris, T.; McFarlane, D.; Parlikad, A. Developing a model for quantifying the quality and value of tracking information on supply chain decisions. In Proceedings of the 12th International Conference on Information Quality, Cambridge, MA, USA, 9–11 November 2007. [Google Scholar]
- Fan, T.; Tao, F.; Deng, S.; Li, S. Impact of RFID technology on supply chain decisions with inventory inaccuracies. Int. J. Prod. Econ. 2015, 159, 117–125. [Google Scholar] [CrossRef]
- Cannella, S.; Dominguez, R.; Framinan, J.M. Inventory record inaccuracy—The impact of structural complexity and lead time variability. Omega-Int. J. Manag. Sci. 2017, 68, 123–138. [Google Scholar] [CrossRef]
- Li, L. Technology designed to combat fakes in the global supply chain. Bus. Horiz. 2013, 56, 167–177. [Google Scholar] [CrossRef]
- Rahman, F.; Ahamed, S.I. Efficient detection of counterfeit products in large-scale RFID systems using batch authentication protocols. Pers. Ubiquitous Comput. 2014, 18, 177–188. [Google Scholar] [CrossRef]
- Wyld, D. Genuine medicine?: Why safeguarding the pharmaceutical supply chain from counterfeit drugs with RFID is vital for protecting public health and the health of the pharmaceutical industry. Compet. Rev. 2008, 18, 206–216. [Google Scholar] [CrossRef]
- Coustasse, A.; Arvidson, C.; Rutsohn, P. Pharmaceutical counterfeiting and the RFID technology intervention. J. Hosp. Mark. Public Relat. 2010, 20, 100–115. [Google Scholar] [CrossRef]
- Taylor, D. RFID in the Pharmaceutical Industry: Addressing Counterfeits with Technology. J. Med Syst. 2014, 38. [Google Scholar] [CrossRef]
- Li, Y.; Ding, X. Protecting RFID communications in supply chains. In Proceedings of the 2nd ACM Symposium on Information, Computer and Communications Security, Singapore, 20–22 March 2007; pp. 234–241. [Google Scholar] [CrossRef]
- Singh, M.; Li, X.; Li, Z. Security and privacy protection in RFID-enabled supply chain management. Int. J. Radio Freq. Identif. Technol. Appl. 2011, 3, 294–318. [Google Scholar] [CrossRef]
- Dai, H.; Li, J.; Yan, N.; Zhou, W. Bullwhip effect and supply chain costs with low- and high-quality information on inventory shrinkage. Eur. J. Oper. Res. 2016, 250, 457–469. [Google Scholar] [CrossRef]
- Ustundag, A.; Tanyas, M. The impacts of Radio Frequency Identification (RFID) technology on supply chain costs. Transp. Res. Part E-Logist. Transp. Rev. 2009, 45, 29–38. [Google Scholar] [CrossRef]
- Bensel, P.; Gunther, O.; Tribowski, C.; Vogeler, S. Cost-benefit sharing in cross-company RFID applications: A case study approach [Partager les couts et les benefices des applications RFID impliquant plusieurs partenaires: Une approche par etudes de cas]. In Proceedings of the 29th International Conference on Information Systems, Paris, France, 14–17 December 2008. [Google Scholar]
- Ustundag, A. Evaluating RFID investment on a supply chain using tagging cost sharing factor. Int. J. Prod. Res. 2010, 48, 2549–2562. [Google Scholar] [CrossRef]
- Lee, C.K.M.; Chan, T.M. Development of RFID-based Reverse Logistics System. Expert Syst. Appl. 2009, 36, 9299–9307. [Google Scholar] [CrossRef]
- Kumar, S.; Dieveney, E.; Dieveney, A. Reverse logistic process control measures for the pharmaceutical industry supply chain. Int. J. Product. Perform. Manag. 2009, 58, 188–204. [Google Scholar] [CrossRef]
- Mladenow, A.; Novak, N.M.; Strauss, C. Internet of Things Integration in Supply Chains—An Austrian Business Case of a Collaborative Closed-Loop Implementation. In Proceedings of the 10th IFIP WG 8.9. Working Conference on Research and Practical Issues of Enterprise Information Systems (CONFENIS), Vienna, Austria, 13–14 December 2016; Volume 268, pp. 166–176. [Google Scholar] [CrossRef]
- Saab, S.S.; Nakad, Z.S. A Standalone RFID Indoor Positioning System Using Passive Tags. IEEE Trans. Ind. Electron. 2011, 58, 1961–1970. [Google Scholar] [CrossRef]
- Ma, Y.; Zhou, L.; Liu, K.; Wang, J. Iterative Phase Reconstruction and Weighted Localization Algorithm for Indoor RFID-Based Localization in NLOS Environment. IEEE Sens. J. 2014, 14, 597–611. [Google Scholar] [CrossRef]
- Wang, J.; Katabi, D. Dude, Where’s My Card? RFID Positioning That Works with Multipath and Non-Line of Sight. ACM SIGCOMM Comput. Commun. Rev. 2013, 43, 51–62. [Google Scholar] [CrossRef]
- Faseth, T.; Winkler, M.; Arthaber, H.; Magerl, G. The influence of multipath propagation on phase-based narrowband positioning principles in UHF RFID. In Proceedings of the 2011 1st IEEE-APS Topical Conference on Antennas and Propagation in Wireless Communications, Torino, Italy, 12–16 September 2011; pp. 1144–1147. [Google Scholar] [CrossRef]
- Han, S.; Lim, H.; Lee, J. An efficient localization scheme for a differential-driving mobile robot based on RFID system. IEEE Trans. Ind. Electron. 2007, 54, 3362–3369. [Google Scholar] [CrossRef]
- Park, S.; Hashimoto, S. Autonomous Mobile Robot Navigation Using Passive RFID in Indoor Environment. IEEE Trans. Ind. Electron. 2009, 56, 2366–2373. [Google Scholar] [CrossRef]
- Choi, B.S.; Lee, J.W.; Lee, J.J.; Park, K.T. A Hierarchical Algorithm for Indoor Mobile Robot Localization Using RFID Sensor Fusion. IEEE Trans. Ind. Electron. 2011, 58, 2226–2235. [Google Scholar] [CrossRef]
- Park, S.; Lee, H. Self-Recognition of Vehicle Position Using UHF Passive RFID Tags. IEEE Trans. Ind. Electron. 2013, 60, 226–234. [Google Scholar] [CrossRef]
- Catarinucci, L.; Tedesco, S.; Tarricone, L. Customized Ultra High Frequency Radio Frequency Identification Tags and Reader Antennas Enabling Reliable Mobile Robot Navigation. IEEE Sens. J. 2013, 13, 783–791. [Google Scholar] [CrossRef]
- Kim, M.; Chong, N.Y. RFID-based mobile robot guidance to a stationary target. Mechatronics 2007, 17, 217–229. [Google Scholar] [CrossRef]
- Akkaya, K.; Guvenc, I.; Aygun, R.; Pala, N.; Kadri, A. IoT-based Occupancy Monitoring Techniques for Energy-Efficient Smart Buildings. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), New Orleans, LA, USA, 9–12 March 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 58–63. [Google Scholar]
- Wang, H.T.; Jia, Q.S.; Song, C.; Yuan, R.; Guan, X. Estimation of Occupancy Level in Indoor Environment Based on Heterogeneous Information Fusion. In Proceedings of the 49th IEEE Conference on Decision and Control (CDC), Atlanta, GA, USA, 15–17 December 2010; IEEE: Piscataway, NJ, USA, 2010; pp. 5086–5091. [Google Scholar] [CrossRef]
- Saidi, K.S.; Teizer, J.; Franaszek, M.; Lytle, A.M. Static and dynamic performance evaluation of a commercially-available ultra wideband tracking system. Autom. Constr. 2011, 20, 519–530. [Google Scholar] [CrossRef]
- Fang, Y.; Cho, Y.K.; Zhang, S.; Perez, E. Case Study of BIM and Cloud-Enabled Real-Time RFID Indoor Localization for Construction Management Applications. J. Constr. Eng. Manag. 2016, 142. [Google Scholar] [CrossRef]
- Lee, H.S.; Lee, K.P.; Park, M.; Baek, Y.; Lee, S. RFID-Based Real-Time Locating System for Construction Safety Management. J. Comput. Civ. Eng. 2012, 26, 366–377. [Google Scholar] [CrossRef]
- Lee, E.K.; Oh, S.Y.; Gerla, M. RFID assisted vehicle positioning in VANETs. Pervasive Mob. Comput. 2012, 8, 167–179. [Google Scholar] [CrossRef]
- Dardari, D.; D’Errico, R.; Roblin, C.; Sibille, A.; Win, M.Z. Ultrawide Bandwidth RFID: The Next Generation? Proc. IEEE 2010, 98, 1570–1582. [Google Scholar] [CrossRef]
- Brchan, J.; Zhao, L.; Wu, J.; Williams, R.; Perez, L. A real-time RFID localization experiment using propagation models. In Proceedings of the 2012 6th IEEE International Conference on RFID, Orlando, FL, USA, 3–5 April 2012; pp. 141–148. [Google Scholar] [CrossRef]
- Hekimian-Williams, C.; Grant, B.; Liu, X.; Zhang, Z.; Kumar, P. Accurate localization of RFID tags using phase difference. In Proceedings of the 4th Annual IEEE International Conference on RFID, Orlando, FL, USA, 14–15 April 2010; pp. 89–96. [Google Scholar] [CrossRef]
- Zhou, C.; Griffin, J.D. Accurate Phase-Based Ranging Measurements for Backscatter RFID Tags. IEEE Antennas Wirel. Propag. Lett. 2012, 11, 152–155. [Google Scholar] [CrossRef]
- Kronberger, R.; Knie, T.; Leonardi, R.; Dettmar, U.; Cremer, M.; Azzouzi, S. UHF RFID Localization System Based on a Phased Array Antenna. In Proceedings of the IEEE International Symposium on Antennas and Propagation (APSURSI)/USNC/URSI National Radio Science Meeting, Spokane, WA, USA, 3–8 July 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 525–528. [Google Scholar]
- Kelepouris, T.; Pramatari, K.; Doukidis, G. RFID-enabled traceability in the food supply chain. Ind. Manag. Data Syst. 2007, 107, 183–200. [Google Scholar] [CrossRef]
- Feng, J.; Fu, Z.; Wang, Z.; Xu, M.; Zhang, X. Development and evaluation on a RFID-based traceability system for cattle/beef quality safety in China. Food Control. 2013, 31, 314–325. [Google Scholar] [CrossRef]
- Qian, J.P.; Yang, X.T.; Wu, X.M.; Zhao, L.; Fan, B.L.; Xing, B. A traceability system incorporating 2D barcode and RFID technology for wheat flour mills. Comput. Electron. Agric. 2012, 89, 76–85. [Google Scholar] [CrossRef]
- Ampatzidis, Y.G.; Vougioukas, S.G. Field experiments for evaluating the incorporation of RFID and barcode registration and digital weighing technologies in manual fruit harvesting. Comput. Electron. Agric. 2009, 66, 166–172. [Google Scholar] [CrossRef]
- Parreno-Marchante, A.; Alvarez-Melcon, A.; Trebar, M.; Filippin, P. Advanced traceability system in aquaculture supply chain. J. Food Eng. 2014, 122, 99–109. [Google Scholar] [CrossRef]
- Abad, E.; Palacio, F.; Nuin, M.; Gonzalez de Zarate, A.; Juarros, A.; Gomez, J.M.; Marco, S. RFID smart tag for traceability and cold chain monitoring of foods: Demonstration in an intercontinental fresh fish logistic chain. J. Food Eng. 2009, 93, 394–399. [Google Scholar] [CrossRef]
- Hsu, Y.C.; Chen, A.P.; Wang, C.H. A RFID-Enabled Traceability System for the Supply Chain of Live Fish. In Proceedings of the IEEE International Conference on Automation and Logistics, Qingdao, China, 1–3 September 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 81–86. [Google Scholar]
- Ngai, E.W.T.; Cheng, T.C.E.; Lai, K.H.; Chai, P.Y.F.; Choi, Y.S.; Sin, R.K.Y. Development of an RFID-based traceability system: Experiences and lessons learned from an aircraft engineering company. Prod. Oper. Manag. 2007, 16, 554–568. [Google Scholar] [CrossRef]
- Shanahan, C.; Kernan, B.; Ayalew, G.; McDonnell, K.; Butler, F.; Ward, S. A framework for beef traceability from farm to slaughter using global standards: An Irish perspective. Comput. Electron. Agric. 2009, 66, 62–69. [Google Scholar] [CrossRef]
- Parent, C.; Spaccapietra, S.; Renso, C.; Andrienko, G.; Andrienko, N.; Bogorny, V.; Damiani, M.L.; Gkoulalas-Divanis, A.; Macedo, J.; Pelekis, N.; et al. Semantic Trajectories Modeling and Analysis. ACM Comput. Surv. 2013, 45. [Google Scholar] [CrossRef]
- Chongwatpol, J.; Sharda, R. RFID-enabled track and traceability in job-shop scheduling environment. Eur. J. Oper. Res. 2013, 227, 453–463. [Google Scholar] [CrossRef]
- Agrawal, R.; Cheung, A.; Kailing, K.; Schonauer, S. Towards traceability across sovereign, distributed RFID databases. In Proceedings of the 10th International Database Engineering and Applications Symposium (IDEAS 2006), Delhi, India, 11–14 December 2006; pp. 174–184. [Google Scholar]
- Cimino, M.G.C.A.; Marcelloni, F. Autonomic tracing of production processes with mobile and agent-based computing. Inf. Sci. 2011, 181, 935–953. [Google Scholar] [CrossRef]
- Chrysochou, P.; Chryssochoidis, G.; Kehagia, O. Traceability information carriers. The technology backgrounds and consumers’ perceptions of the technological solutions. Appetite 2009, 53, 322–331. [Google Scholar] [CrossRef]
- Song, J.H.; Lee, N.S.; Yoon, S.W.; Kwon, S.W.; Chin, S.; Kim, Y.S. Material tracker for construction logistics. In Proceedings of the 24th International Symposium on Automation and Robotics in Construction, Kochi, Japan, 19–21 September 2007; pp. 63–67. [Google Scholar]
- Schuh, G. Sm@rt Logistics: Intelligent networked systems. Cirp-Ann.-Manuf. Technol. 2006, 55, 505–508. [Google Scholar] [CrossRef]
- Wamba, S.F.; Chatfield, A.T. A contingency model for creating value from RFID supply chain network projects in logistics and manufacturing environments. Eur. J. Inf. Syst. 2009, 18, 615–636. [Google Scholar] [CrossRef]
- Baars, H.; Gille, D.; Strueker, J. Evaluation of RFID applications for logistics: A framework for identifying, forecasting and assessing benefits. Eur. J. Inf. Syst. 2009, 18, 578–591. [Google Scholar] [CrossRef]
- Zacharewicz, G.; Deschamps, J.C.; Francois, J. Distributed simulation platform to design advanced RFID based freight transportation systems. Comput. Ind. 2011, 62, 597–612. [Google Scholar] [CrossRef]
- Wang, Y.; Ho, O.; Huang, G.; Li, D. Study on vehicle management in logistics based on RFID, GPS and GIS. Int. J. Internet Manuf. Serv. 2008, 1, 294–304. [Google Scholar] [CrossRef]
- Castro, M.; Jara, A.J.; Skarmeta, A. Architecture for Improving Terrestrial Logistics Based on the Web of Things. Sensors 2012, 12, 6538–6575. [Google Scholar] [CrossRef] [PubMed]
- Chen, S.G. Fuzzy-scorecard based logistics management in robust SCM. Comput. Ind. Eng. 2012, 62, 740–745. [Google Scholar] [CrossRef]
- Johansson, O.; Palsson, H. The impact of Auto-ID on logistics performance: A benchmarking survey of Swedish manufacturing industries. Benchmarking 2009, 16, 504–522. [Google Scholar] [CrossRef]
- Schmidt, M.; Thoroe, L.; Schumann, M. RFID and Barcode in Manufacturing Logistics: Interface Concept for Concurrent Operation. Inf. Syst. Manag. 2013, 30, 100–115. [Google Scholar] [CrossRef]
- Chow, K.; Choy, K.; Lee, W. Design of a knowledge-based logistics management system: A case-based RFID approach. Int. J. Enterp. Netw. Manag. 2006, 1, 5–28. [Google Scholar] [CrossRef]
- Tesoriero, R.; Gallud, J.A.; Lozano, M.D.; Penichet, V.M.R. Tracking Autonomous Entities using RFID Technology. IEEE Trans. Consum. Electron. 2009, 55, 650–655. [Google Scholar] [CrossRef]
- Esposito, A.; Tarricone, L.; Zappatore, M.; Catarinucci, L.; Colella, R. A framework for context-aware home-health monitoring. Int. J. Auton. Adapt. Commun. Syst. 2010, 3, 75–91. [Google Scholar] [CrossRef]
- Raad, M. A ubiquitous mobile telemedicine system for the elderly using RFID. Int. J. Secur. Netw. 2010, 5, 156–164. [Google Scholar] [CrossRef]
- Bravo, J.; Hervas, R.; Chavira, G. Ubiquitous Computing in the classroom: An approach through identification process. J. Univers. Comput. Sci. 2005, 11, 1494–1504. [Google Scholar]
- Kim, T.H.; Ramos, C.; Mohammed, S. Smart City and IoT. Future Gener. Comput.-Syst.- Int. J. Escience 2017, 76, 159–162. [Google Scholar] [CrossRef]
- Roemer, K.; Domnitcheva, S. Smart Playing Cards: A Ubiquitous Computing Game. Pers. Ubiquitous Comput. 2002, 6, 371–377. [Google Scholar] [CrossRef]
- Romer, K.; Schoch, T.; Mattern, F.; Dubendorfer, T. Smart identification frameworks for ubiquitous computing applications. Wirel. Netw. 2004, 10, 689–700. [Google Scholar] [CrossRef]
- Friedewald, M.; Raabe, O. Ubiquitous computing: An overview of technology impacts. Telemat. Inform. 2011, 28, 55–65. [Google Scholar] [CrossRef]
- Lopez-de Ipina, D.; Diaz-de Sarralde, I.; Garcia-Zubia, J. An Ambient Assisted Living Platform Integrating RFID Data-on-Tag Care Annotations and Twitter. J. Univers. Comput. Sci. 2010, 16, 1521–1538. [Google Scholar]
- Wamba, S.; Ngai, E. Internet of things in healthcare: The case of RFID-enabled asset management. Int. J. Biomed. Eng. Technol. 2013, 11, 318–335. [Google Scholar] [CrossRef]
- Liu, C.F.; Gu, Y.M. The Research of Intelligent Medical Devices Management System Based on RFID Technology. In Proceedings of the International Conference on Information System and Artificial Intelligence (ISAI), Hong Kong, China, 24–26 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 29–33. [Google Scholar] [CrossRef]
- Adame, T.; Bel, A.; Carreras, A.; Melia-Segui, J.; Oliver, M.; Pous, R. CUIDATS: An RFID-WSN hybrid monitoring system for smart health care environments. Future Gener. Comput.-Syst.- Int. J. Escience 2018, 78, 602–615. [Google Scholar] [CrossRef]
- Tsirbas, H.; Giokas, K.; Koutsouris, D. “Internet of Things”, an RFID—IPv6 scenario in a healthcare environment. In Proceedings of the 12th Mediterranean Conference on Medical and Biological Engineering and Computing, Chalkidiki, Greece, 27–30 May 2010; Volume 29, pp. 808–811. [Google Scholar] [CrossRef]
- Fan, K.; Jiang, W.; Li, H.; Yang, Y. Lightweight RFID Protocol for Medical Privacy Protection in IoT. IEEE Trans. Ind. Inform. 2018, 14, 1656–1665. [Google Scholar] [CrossRef]
- Jisha, S.; Philip, M. Rfid based security platform for internet of things in health care environment. In Proceedings of the Online International Conference on Green Engineering and Technologies (IC-GET), Coimbatore, India, 19 November 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Ai, L.; Jun, D.Z.; Yun, S.; Ling, W.X. The intelligent signing system of internet of things about environmental health workers based on RFID. In Proceedings of the 6th International Conference on Electronics and Information Engineering (ICEIE), Dalian, China, 26–27 September 2015; 2015; Volume 9794. [Google Scholar] [CrossRef]
- Wickramasuriya, J.; Datt, M.; Mehrotra, S.; Venkatasubramanian, N. Privacy protecting data collection in media spaces. In Proceedings of the ACM Multimedia 2004—Proceedings of the 12th ACM International Conference on Multimedia, New York, NY, USA, 10–16 October 2004; Association for Computing Machinery (ACM): New York, NY, USA, 2004; pp. 48–55. [Google Scholar] [CrossRef]
- Wickramasuriya, J.; Alhazzazi, M.; Datt, M.; Mehrotra, S.; Venkatasubramanian, N. Privacy-protecting video surveillance. In Proceedings of the Conference on Real-Time Imaging IX, San Jose, CA, USA, 18–20 January 2005; Volume 5671, pp. 64–75. [Google Scholar] [CrossRef]
- Ayoade, J. Security implications in RFID and authentication processing framework. Comput. Secur. 2006, 25, 207–212. [Google Scholar] [CrossRef]
- Li, M.; Poovendran, R.; Falk, R.; Koepf, A.; Braun, M.; Sampigethaya, K.; Robinson, R.; Lintelman, S.; Seuschek, H. Multi-domain rfid access control using asymmetric key based tag-reader mutual authentication. In Proceedings of the 26th Congress of International Council of the Aeronautical Sciences 2008, Anchorage, AK, USA, 14–19 September 2008; Volume 2, pp. 2841–2850. [Google Scholar]
- Larchikov, A.; Panasenko, S.; Pimenov, A.V.; Timofeev, P. Combining RFID-Based Physical Access Control Systems with Digital Signature Systems to Increase Their Security. In Proceedings of the 22nd International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 17–19 September 2014; IEEE: Piscataway, NJ, USA, 2014. [Google Scholar]
- Chen, B.C.; Yang, C.T.; Yeh, H.T.; Lin, C.C. Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID. Appl. Sci. 2016, 6, 215. [Google Scholar] [CrossRef]
- Xie, W.; Xie, L.; Zhang, C.; Wang, Q.; Wang, C.; Tang, C. TOA: A tag-owner-assisting RFID authentication protocol toward access control and ownership transfer. Secur. Commun. Netw. 2014, 7, 934–944. [Google Scholar] [CrossRef]
- Courtois, N.T. The dark side of security by obscurity and cloning Mifare Classic rail and building passes, anywhere, anytime. In Proceedings of the International Conference on Security and Cryptography, Milan, Italy, 7–10 July 2009; pp. 331–338. [Google Scholar]
- Chen, Y.Y.; Huang, D.C.; Tsai, M.L.; Jan, J.K. A Design of Tamper Resistant Prescription RFID Access Control System. J. Med Syst. 2012, 36, 2795–2801. [Google Scholar] [CrossRef]
- Henseler, M.; Rossberg, M.; Schaefer, G. Credential Management for Automatic Identification Solutions in Supply Chain Management. IEEE Trans. Ind. Inform. 2008, 4, 303–314. [Google Scholar] [CrossRef][Green Version]
- Qi, S.; Zheng, Y.; Li, M.; Liu, Y.; Qiu, J. Scalable Industry Data Access Control in RFID-Enabled Supply Chain. IEEE-ACM Trans. Netw. 2016, 24, 3551–3564. [Google Scholar] [CrossRef]
- Deng, H.F.; Deng, W.; Li, H.; Yang, H.J. Authentication and access control in RFID based logistics-customs clearance service platform. Int. J. Autom. Comput. 2010, 7, 180–189. [Google Scholar] [CrossRef]
- Nowicki, T.; Kiedrowicz, M.; Waszkowski, R.; Chodowska, A.; Lach, A. Access control system for RFID-tagged documents in supply chain management. Logforum 2017, 13, 91–101. [Google Scholar] [CrossRef]
- Kerschbaum, F. An Access Control Model for Mobile Physical Objects. In Proceedings of the 15th ACM Symposium on Access Control Models and Technologies, Pittsburgh, PA, USA, 9–11 June 2010; pp. 193–202. [Google Scholar] [CrossRef]
- Atluri, V.; Shin, H.; Vaidya, J. Efficient security policy enforcement for the mobile environment. J. Comput. Secur. 2008, 16, 439–475. [Google Scholar] [CrossRef]
- Jensen, S.E.H.; Jacobsen, R.H. Access Control with RFID in the Internet of Things. In Proceedings of the IEEE 27th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Barcelona, Spain, 25–28 March 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 554–559. [Google Scholar] [CrossRef]
- Al-Zewairi, M.; Alqatawna, J.; Al-Kadi, O. Privacy and security for RFID Access Control Systems: RFID Access Control Systems without back-end database. In Proceedings of the 2011 1st IEEE Jordan Conference on Applied Electrical Engineering and Computing Technologies, Amman, Jordan, 6–8 December 2011. [Google Scholar] [CrossRef]
- Al-Zewairi, M.; Alqatawna, J.; Atoum, J. Risk adaptive hybrid RFID access control system. Secur. Commun. Netw. 2015, 8, 3826–3835. [Google Scholar] [CrossRef]
- Almanza-Ojeda, D.L.; Hernandez-Gutierrez, A.; Ibarra-Manzano, M.A. Design and implementation of a vehicular access control using RFID. In Proceedings of the 3rd International Conference on Advanced Optoelectronics and Lasers/3rd International Conference on Precision Oscillations in Electronics and Optics/1st International Workshop on Image and Signal Processing (MEP 2006), Guanajuato, MEXICO, 7–11 November 2006; IEEE: Piscataway, NJ, USA, 2006. [Google Scholar]
- Mai, A.; Wei, Z.; Gao, M. An Access Control and Positioning Security Management System Based on RFID. In Proceedings of the 7th International Conference on Intelligent Human-Machine Systems and Cybernetics (IHMSC), Hangzhou, China, 26–27 August 2015; IEEE: Piscataway, NJ, USA, 2015. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Y.; Chen, C. Internet of things’ authentication and access control. Int. J. Secur. Netw. 2012, 7, 228–241. [Google Scholar] [CrossRef]
- Shi, J.; Li, Y.; Deng, R.H. A secure and efficient discovery service system in EPCglobal network. Comput. Secur. 2012, 31, 870–885. [Google Scholar] [CrossRef]
- Tounsi, W.; Cuppens-Boulahia, N.; Cuppens, F.; Garcia-Alfaro, J. Fine-grained privacy control for the RFID middleware of EPCglobal networks. In Proceedings of the 5th International Conference on Management of Emergent Digital EcoSystems, Luxembourg, 28–31 October 2013; pp. 60–67. [Google Scholar] [CrossRef]
- Taesung, K.; Howon, K. Access control for middleware in RFID systems. In Proceedings of the 8th International Conference Advanced Communication Technology, Dublin, Ireland, 20–22 February 2006; Volume 2, pp. 1020–1022. [Google Scholar]
- Tounsi, W.; Cuppens-Boulahia, N.; Cuppens, F.; Pujolle, G. Access and privacy control enforcement in RFID middleware systems: Proposal and implementation on the fosstrak platform. World Wide-Web-Internet Web Inf. Syst. 2016, 19, 41–68. [Google Scholar] [CrossRef]
- Michael, K.; Michael, M.G. The future prospects of embedded microchips in humans as unique identifiers: The risks versus the rewards. Media Cult. Soc. 2013, 35, 78–86. [Google Scholar] [CrossRef]
- Perakslis, C.; Michael, K. Indian Millennials: Are microchip implants a more secure technology for identification and access control? In Proceedings of the 2012 IEEE Conference on Technology and Society in Asia (T&SA), Singapore, 27–29 October 2012; 2012. [Google Scholar] [CrossRef]
- Perakslis, C.; Michael, K.; Michael, M.G.; Gable, R. Perceived Barriers for Implanting Microchips in Humans: A Transnational Study. In Proceedings of the IEEE Conference on Norbert Wiener in the 21st Century (21CW)—Driving Technology’s Future, Boston, MA, USA, 24–26 June 2014; IEEE: Piscataway, NJ, USA, 2014. [Google Scholar]
- Weber, R. Internet of Things—New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Molnar, D.; Wagner, D. Privacy and security in library RFID issues, practices, and architectures. In Proceedings of the 11th ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 210–219. [Google Scholar]
- Juels, A.; Weis, S.A. Defining strong privacy for RFID (Extended abstract). In Proceedings of the 5th IEEE International Conference on Pervasive Computing and Communications, White Plains, NY, USA, 19–23 March 2007. [Google Scholar] [CrossRef]
- Gao, X.; Xiang, Z.; Wang, H.; Shen, J.; Huang, J.; Song, S. An approach to security and privacy of RFID system for supply chain. In Proceedings of the IEEE International Conference on E-Commerce Technology for Dynamic E-Business, Beijing, China, 13–15 September 2004; pp. 164–168. [Google Scholar]
- Hoque, M.E.; Rahman, F.; Ahamed, S.I.; Park, J.H. Enhancing Privacy and Security of RFID System with Serverless Authentication and Search Protocols in Pervasive Environments. Wirel. Pers. Commun. 2010, 55, 65–79. [Google Scholar] [CrossRef]
- Park, N. Customized Healthcare Infrastructure Using Privacy Weight Level Based on Smart Device. In Proceedings of the 5th International Conference on Convergence and Hybrid Information Technology (ICHIT), Daejeon, Korea, 22–24 September 2011; Volume 206, pp. 467–474. [Google Scholar]
- Shih, D.H.; Lin, C.Y.; Lin, B. RFID tags: Privacy and security aspects. Int. J. Mob. Commun. 2005, 3, 214–230. [Google Scholar] [CrossRef]
- Yang, G.; Geng, G.; Du, J.; Liu, Z.; Han, H. Security threats and measures for the Internet of Things. Qinghua Daxue Xuebao/J. Tsinghua Univ. 2011, 51, 1335–1340. [Google Scholar]
- Cai, S.; Li, Y.; Li, T.; Deng, R. Attacks and improvements to an RFID mutual authentication protocol and its extensions. In Proceedings of the 2nd ACM Conference on Wireless Network Security, Zurich, Switzerland, 16–18 March 2009; pp. 51–58. [Google Scholar] [CrossRef]
- Lo, N.; Yeh, K.H.; Yeun, C. New mutual agreement protocol to secure mobile RFID-enabled devices. Inf. Secur. Tech. Rep. 2008, 13, 151–157. [Google Scholar] [CrossRef]
- Pang, L.; He, L.; Pei, Q.; Wang, Y. Secure and efficient mutual authentication protocol for RFID conforming to the EPC C-1 G-2 Standard. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 1870–1875. [Google Scholar]
- Kardas, S.; Akgun, M.; Kiraz, M.; Demirci, H. Cryptanalysis of lightweight mutual authentication and ownership transfer for RFID systems. In Proceedings of the 2011 Workshop on Lightweight Security and Privacy: Devices, Protocols, and Applications, Istanbul, Turkey, 14–15 March 2011; pp. 20–25. [Google Scholar] [CrossRef]
- Dehkordi, M.H.; Farzaneh, Y. Improvement of the Hash-Based RFID Mutual Authentication Protocol. Wirel. Pers. Commun. 2014, 75, 219–232. [Google Scholar] [CrossRef]
- Yeh, T.C.; Wu, C.H.; Tseng, Y.M. Improvement of the RFID authentication scheme based on quadratic residues. Comput. Commun. 2011, 34, 337–341. [Google Scholar] [CrossRef]
- Cheng, Z.Y.; Liu, Y.; Chang, C.C.; Chang, S.C. Authenticated RFID security mechanism based on chaotic maps. Secur. Commun. Netw. 2013, 6, 247–256. [Google Scholar] [CrossRef]
- Yeh, K.H.; Lo, N.; Winata, E. An efficient ultralightweight authentication protocol for RFID systems. Cryptol. Inf. Secur. Ser. 2010, 4, 49–60. [Google Scholar] [CrossRef]
- Chen, C.L.; Deng, Y.Y. Conformation of EPC Class 1 Generation 2 standards RFID system with mutual authentication and privacy protection. Eng. Appl. Artif. Intell. 2009, 22, 1284–1291. [Google Scholar] [CrossRef]
- David, M.; Prasad, N.R. Providing Strong Security and High Privacy in Low-Cost RFID Networks. In Proceedings of the 1st International ICST Conference, Turin, Italy, 03–05 June 2009; Volume 17, pp. 172–179. [Google Scholar]
- Rahman, F.; Bhuiyan, M.Z.A.; Ahamed, S.I. A privacy preserving framework for RFID based healthcare systems. Future Gener. Comput.-Syst.- Int. J. Escience 2017, 72, 339–352. [Google Scholar] [CrossRef]
- Chien, H.Y.; Yang, C.C.; Wu, T.C.; Lee, C.F. Two RFID-based Solutions to Enhance Inpatient Medication Safety. J. Med. Syst. 2011, 35, 369–375. [Google Scholar] [CrossRef]
- Sun, H.M.; Ting, W.C.; Wang, K.H. On the Security of Chien’s Ultralightweight RFID Authentication Protocol. IEEE Trans. Dependable Secur. Comput. 2011, 8, 315–317. [Google Scholar] [CrossRef]
- Chien, H.Y.; Huang, C.W. Security of ultra-lightweight RFID authentication protocols and its improvements. Acm SIGOPS Oper. Syst. Rev. 2007, 41, 83–86. [Google Scholar] [CrossRef]
- Chien, H.Y.; Laih, C.S. ECC-based lightweight authentication protocol with untraceability for low-cost RFID. J. Parallel Distrib. Comput. 2009, 69, 848–853. [Google Scholar] [CrossRef]
- Peris-Lopez, P.; Hernandez-Castro, J.C.; Estevez-Tapiador, J.M.; Ribagorda, A. Cryptanalysis of a novel authentication protocol conforming to EPC-C1G2 standard. Comput. Stand. Interfaces 2009, 31, 372–380. [Google Scholar] [CrossRef]
- Cobb, W.E.; Laspe, E.D.; Baldwin, R.O.; Temple, M.A.; Kim, Y.C. Intrinsic Physical-Layer Authentication of Integrated Circuits. IEEE Trans. Inf. Forensics Secur. 2012, 7, 14–24. [Google Scholar] [CrossRef]
- Tan, C.C.; Sheng, B.; Li, Q. Efficient Techniques for Monitoring Missing RFID Tags. IEEE Trans. Wirel. Commun. 2010, 9, 1882–1889. [Google Scholar] [CrossRef]
- Lo, N.W.; Yeh, K.H. Anonymous Coexistence Proofs for RFID Tags. J. Inf. Sci. Eng. 2010, 26, 1213–1230. [Google Scholar]
- Xin, W.; Guan, Z.; Yang, T.; Sun, H.; Chen, Z. An efficient privacy-preserving RFID ownership transfer protocol. In Proceedings of the 15th Asia-Pacific Web Conference on Web Technologies and Applications, Sydney, Australia, 4–6 April 2013; Volume 7808 LNCS, pp. 538–549. [Google Scholar] [CrossRef]
- Chen, C.L.; Lai, Y.L.; Chen, C.C.; Deng, Y.Y.; Hwang, Y.C. RFID ownership transfer authorization systems conforming EPCglobal class-1 generation-2 standards. Int. J. Netw. Secur. 2011, 13, 41–48. [Google Scholar]
- Chen, C.L.; Huang, Y.C.; Jiang, J.R. A secure ownership transfer protocol using EPCglobal Gen-2 RFID. Telecommun. Syst. 2013, 53, 387–399. [Google Scholar] [CrossRef]
- Niu, H.; Taqieddin, E.; Jagannathan, S. EPC Gen2v2 RFID Standard Authentication and Ownership Management Protocol. IEEE Trans. Mob. Comput. 2016, 15, 137–149. [Google Scholar] [CrossRef]
- Niu, H.; Jagannathan, S.; Taqieddin, E.S. A Gen2v2 Compliant RFID Authentication and Ownership Management Protocol. In Proceedings of the 39th Annual IEEE Conference on Local Computer Networks (LCN), Edmonton, AB, Canada, 8–11 September 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 331–336. [Google Scholar]
- Jappinen, P.; Hamalainen, H. Enhanced RFID security method with Ownership transfer. In Proceedings of the International Conference on Computational-Intelligence and Security, Suzhou, China, 13–17 December 2008; pp. 943–946. [Google Scholar]
- Gui, Y.Q.; Zhang, J.; Choi, H. An improved RFID security method with ownership transfer. In Proceedings of the 2011 International Conference on ICT Convergence, Seoul, Korea, 28–30 September 2011; pp. 594–596. [Google Scholar] [CrossRef]
- Chen, C.L.; Chien, C.F. An Ownership Transfer Scheme Using Mobile RFIDs. Wirel. Pers. Commun. 2013, 68, 1093–1119. [Google Scholar] [CrossRef]
- Fernandez-Mir, A.; Trujillo-Rasua, R.; Castella-Roca, J.; Domingo-Ferrer, J. A Scalable RFID Authentication Protocol Supporting Ownership Transfer and Controlled Delegation. In Proceedings of the 7th Workshop on RFID Security and Privacy (RFIDSec), Amherst, MA, USA, 26–28 June 2011; Volume 7055, pp. 147–162. [Google Scholar]
- Chen, C.L.; Chen, Y.Y.; Huang, Y.C.; Liu, C.S.; Lin, C.I.; Shih, T.F. Anti-counterfeit ownership transfer protocol for low cost RFID system. WSEAS Trans. Comput. 2008, 7, 1149–1158. [Google Scholar]
- Li, T.; Jin, Z.; Pang, C. Secured ownership transfer scheme for low-cost RFID tags. In Proceedings of the 3rd International Conference on Intelligent Networks and Intelligent Systems, Shenyang, China, 1–3 November 2010; pp. 584–587. [Google Scholar] [CrossRef]
- Chinnappa, S.; Periaswamy, G.; Thompson, D.; Di, J. Ownership transfer of RFID tags based on electronic fingerprint. In Proceedings of the 2008 International Conference on Security and Management, Las Vegas, NV, USA, 14–17 July 2008; pp. 64–67. [Google Scholar]
- Zhang, R.; Zhu, L.; Xu, C.; Yi, Y. An Efficient and Secure RFID Batch Authentication Protocol with Group Tags Ownership Transfer. In Proceedings of the IEEE Conference Collaboration Internet Computing, Hangzhou, China, 28–30 October 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 168–175. [Google Scholar] [CrossRef]
- Li, Q.S.; Xu, X.L.; Chen, Z. PUF-based RFID Ownership Transfer Protocol in an Open Environment. In Proceedings of the 15th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Hong Kong, China, 9–11 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 131–137. [Google Scholar] [CrossRef]
- Cheng, S.; Varadharajan, V.; Mu, Y.; Susilo, W. A secure elliptic curve based RFID ownership transfer scheme with controlled delegation. Cryptol. Inf. Secur. Ser. 2013, 11, 31–43. [Google Scholar] [CrossRef]
- Chien, H.Y. De-synchronization Attack on Quadratic Residues-based RFID Ownership Transfer. In Proceedings of the 10th Asia Joint Conference on Information Security (AsiaJCIS 2015), Kaohsiung City, Taiwan, 24–26 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 42–47. [Google Scholar] [CrossRef]
- Wang, H.; Yang, X.; Huang, Q.; Long, K. A Novel Authentication Protocol Enabling RFID Tags Ownership Transfer. In Proceedings of the 14th IEEE International Conference on Communication Technology (ICCT), Chengdu, China, 09–11 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 855–860. [Google Scholar]
- Zhou, X.; Wang, A.; Xi, T. A new optional ownership transfer mode of RFID tags. J. Inf. Comput. Sci. 2013, 10, 2471–2479. [Google Scholar] [CrossRef]
- Chen, Y.Y.; Tsai, M.L.; Chen, Y.T.; Jan, J.K. A tagged-product ownership transfer mechanism used in retailer and second-hand transaction. Int. J. Radio Freq. Identif. Technol. Appl. 2011, 3, 47–53. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).