Abstract
The widespread adoption of Internet of Things (IoT) devices has been accompanied by a remarkable rise in both the frequency and intensity of Distributed Denial of Service (DDoS) attacks, which aim to overwhelm and disrupt the availability of networked systems and connected infrastructures. In this paper, we present a novel approach to DDoS attack detection and mitigation that integrates state-of-the-art machine learning techniques with Blockchain-based Mobile Edge Computing (MEC) in IoT environments. Our solution leverages the decentralized and tamper-resistant nature of Blockchain technology to enable secure and efficient data collection and processing at the network edge. We evaluate multiple machine learning models, including K-Nearest Neighbors (KNN), Support Vector Machine (SVM), Decision Tree (DT), Random Forest (RF), Transformer architectures, and LightGBM, using the CICDDoS2019 dataset. Our results demonstrate that Transformer models achieve a superior detection accuracy of 99.78%, while RF follows closely with 99.62%, and LightGBM offers optimal efficiency for real-time detection. This integrated approach significantly enhances detection accuracy and mitigation effectiveness compared to existing methods, providing a robust and adaptive mechanism for identifying and mitigating malicious traffic patterns in IoT environments.
1. Introduction
The rapid growth of the IoT ecosystem has revolutionized various sectors, including smart homes, industrial automation, and healthcare. The interconnectivity enabled by IoT devices allows for increased efficiency, automation, and real-time data collection, improving everything from household convenience to critical industrial operations. In healthcare, IoT is driving innovations in patient monitoring and diagnostics, while in smart homes, devices like smart thermostats, lights, and security systems are making daily life more efficient and manageable. However, this increased connectivity has also made IoT systems more vulnerable to malicious attacks, particularly DDoS attacks, which aim to overwhelm and disrupt the availability of IoT devices and services [1,2,3].
Recent advances in machine learning have introduced powerful new architectures for security applications. Transformer-based models, with their self-attention mechanisms, excel at detecting complex temporal patterns in network traffic, while gradient boosting frameworks like LightGBM offer unprecedented efficiency in processing heterogeneous IoT data streams. These innovations present new opportunities for combating increasingly sophisticated DDoS threats [4,5,6]
DDoS attacks typically involve flooding a target system with malicious traffic from a network of compromised devices, commonly referred to as a botnet. This is especially problematic for IoT devices, which often lack the computational resources or security mechanisms to effectively defend against such attacks. As a result, IoT devices are becoming prime targets for DDoS attacks, posing significant risks to the functionality of IoT networks [7,8,9]. These attacks can cause the loss of critical data, financial damage, and disruption of essential services. In industries where real-time data is crucial, such as healthcare or industrial automation, the impact of DDoS attacks could be catastrophic [10].
The limited computational and security capabilities of many IoT devices exacerbate the problem. Unlike traditional computing systems, IoT devices are often designed with a focus on cost efficiency, leading to a reduction in processing power and security features. This makes them especially vulnerable to attacks. A common technique employed in DDoS attacks against IoT systems involves botnets, large networks of compromised IoT devices used to flood target systems with traffic. These botnets can be created by exploiting vulnerabilities in IoT devices, which are often poorly secured or run outdated software. Once compromised, these devices become part of a larger network controlled by malicious actors and can then be used to launch coordinated attacks against specific targets [11,12].
To address this challenge, we explore the integration of advanced machine learning techniques, including Transformer architectures and LightGBM, alongside KNN, SVM, DT, and RF algorithms, with blockchain-based mobile edge computing technologies for effective detection and mitigation of DDoS attacks in the IoT domain.
The existing literature on detection and mitigation of DDoS attacks in IoT environments has explored various approaches, including signature-based detection, anomaly-based detection, and machine learning-based techniques [10,13]. While these methods have shown promise, the potential of cutting-edge approaches like Transformers and LightGBM, combined with Blockchain and mobile edge computing, has yet to be extensively investigated. The approach proposed in this study aims to bridge this gap by leveraging these advanced machine learning techniques alongside Blockchain-based mobile edge computing to enhance the detection and mitigation of DDoS attacks in IoT networks.
2. Main Contributions
This paper presents several key contributions that advance the integration of Blockchain, Mobile Edge Computing (MEC), and machine learning for robust DDoS mitigation.
First, we leverage the decentralized nature of Blockchain technology to enhance security and resilience. This approach provides resistance to single-point-of-failure attacks, ensures tamper-proof data integrity, and enables distributed network traffic management for effective DDoS mitigation. By eliminating centralized vulnerabilities, our system improves overall robustness against adversarial disruptions.
Second, our MEC–Blockchain integration addresses critical limitations identified in prior research. We significantly reduce latency by processing data at the edge, enhance scalability through intelligent task offloading, and strengthen security by minimizing reliance on distant cloud servers. Furthermore, our framework optimizes resource allocation and energy efficiency, making it suitable for real-world deployment in dynamic network environments.
A major innovation of this work lies in its novel machine learning components. We introduce a Transformer-based detection model that achieves 99.78% accuracy by leveraging self-attention mechanisms to identify temporal attack patterns. Moreover, our edge-optimized LightGBM classifier delivers 99.71% accuracy while operating three times faster than traditional RF models, making it ideal for real-time threat detection.
Furthermore, we propose an enhanced threshold mechanism that combines dynamic blockchain timestamp analysis with real-time machine learning predictions. This hybrid approach improves legitimate traffic identification by 18%, reducing false alarms while maintaining high detection sensitivity.
The core strength of our system stems from its three-way synergy: Blockchain ensures decentralized and immutable storage, MEC enables low-latency processing near data sources, and advanced machine learning provides intelligent threat detection. This integrated architecture creates a robust defense mechanism against evolving cyber threats.
The paper is organized as follows. Section 3 provides a comprehensive literature review, examining traditional DDoS mitigation techniques alongside recent breakthroughs in deep learning and gradient-boosting methods. This establishes the foundational knowledge and highlights the gaps in existing solutions. Section 4 details our approach, focusing on three key innovations: the architecture of our Transformer-based detection model, optimization techniques for deploying LightGBM at the network edge, and the seamless integration of Blockchain with MEC infrastructure. Section 5 presents a rigorous performance evaluation, comparing six different detection methods on multiple metrics including precision, latency, and computational efficiency. The analysis includes both quantitative and qualitative results to demonstrate the advantages of our framework. The concluding section (Section 6) summarizes our findings and outlines promising directions for future work.
3. Related Works
Previous research has explored various approaches to the detection and mitigation of DDoS attacks in the IoT domain, including signature-based detection, which relies on identifying known attack patterns, and anomaly-based detection, which focuses on identifying deviations from normal network behavior. Although these methods have shown some success, they are often limited in their ability to adapt to the rapidly evolving nature of DDoS attacks and the heterogeneity of IoT devices.
The integration of machine learning algorithms into DDoS detection and mitigation systems has emerged as a promising solution, as these techniques can learn from past attack patterns and adapt to new threats.
The study in [14] proposed a DDoS mitigation framework that can effectively defend IoT networks against flooding attacks. The framework aims to match the resource-constrained characteristics of the IoT environment and be adaptable to different IoT applications. The proposed framework comprises two main components: an Analysis Module and a Monitoring Module. The Analysis Module inspects incoming packets and marks suspicious packets for further monitoring. The Monitoring Module then analyzes the characteristics of the suspected packets and categorizes them as malicious or benign. The framework also introduces an “EDoS Server” to handle high-amplitude attacks that the IoT network may not be able to handle. The proposed framework was simulated using Cooja and Contiki OS. The results show improvements in the Packet Delivery Ratio and fewer dropped packets compared to previous approaches. In specific cases, the framework achieved a 100% delivery rate for the border router and 86% for internal nodes. However, the proposed framework is centralized, and a distributed defensive framework is required.
In [15], the authors focus on detecting DDoS attacks, which are a major threat to the Internet. The authors used various machine learning techniques to detect and classify DDoS attack packets. The authors used the NSL-KDD dataset, which contains network traffic data with normal and attack packets. They pre-processed the data using label encoding for categorical features. Moreover, for the Random Forest model, they used Principal Component Analysis to reduce the number of features. They have shown that their results perform better than the existing approaches, especially the Random Forest. The high accuracy of the Random Forest model indicates its effectiveness in detecting DDoS attacks.The study did not explore the performance of the models on real-time network data, which may have different characteristics than the NSL-KDD dataset.
The authors of [16] proposed a DDoS attacks mitigation framework for IoT networks that leverages the benefits of fog computing to deploy an anomaly mitigation framework using machine learning. The framework classifies network traffic as legitimate or illegitimate before passing it to a classification algorithm that achieves satisfactory accuracy in detecting DDoS attacks. The evaluation is performed using the CICDDoS2019 dataset, which contains realistic DDoS attack patterns. The KNN classifier used in the proposed framework achieved superior results compared to the DT and NB (Naive Bayes) classifiers, with 99.99% accuracy; 100% precision, recall, and F1 score; and a false-positive rate of 0%. However, among the limitations of the proposed approach are Fog nodes, which typically have less processing power, storage, and memory compared to cloud servers. This could limit the complexity and effectiveness of the machine learning algorithms used for DDoS detection, especially in large-scale IoT deployments. Furthermore, The security of the fog nodes themselves is a potential vulnerability.
A combination of machine learning techniques and Blockchain technology to detect and block malicious traffic is proposed in [17]. The authors used machine learning algorithms to classify network traffic as either malicious or genuine. They employed Blockchain for storing and managing a decentralized blacklist of malicious IP addresses. The CICDDoS-2019 dataset was utilized to train and evaluate machine learning models, including KNN, DT, and RF. The results show that the Random Forest algorithm outperforms the other two models, achieving an accuracy of 95.19%, precision of 95.10%, and F1-score of 94.47% in classifying malicious traffic. Each node in the Blockchain network has a copy of the Blockchain. This allows every node to access the distributed ledger and retrieve the blacklisted IP addresses, enhancing the security of the system since the Blockchain data cannot be altered. However, the proposed approach is not suitable for IoT applications because of the resource constraints of IoT devices, which may limit their ability to participate in the Blockchain network or handle the computational load of the machine learning algorithms.
The authors in [18] proposed a framework using Blockchain technology, specifically Ethereum, to create a decentralized framework for securing IoT devices and preventing DDoS attacks. The key objectives are to detect and prevent DDoS attacks, enable trust-free operation of IoT devices, and integrate legacy IoT devices with low computational capabilities. It uses smart contracts to authorize IoT devices and control their access to the network. Each device is assigned a gas limit, which acts as a resource limit to prevent them from overwhelming the servers during a DDoS attack. Moreover, it removes the need for third-party trust, distributes control and computation among multiple nodes, and uses the gas limit mechanism to defend against DDoS attacks. However, the proposed framework does not address the scalability issues associated with Blockchain technology, which could be a potential limitation for large-scale IoT deployments.
In [19], the authors propose an approach for detecting and mitigating DDoS attacks in IoT networks by integrating machine learning and Blockchain technologies. Machine learning algorithms analyze network traffic to identify attacks, while Blockchain securely stores blacklisted IP addresses to prevent tampering. The approach achieves high accuracy, with Random Forest performing the best, and leverages Blockchain’s decentralized nature for real-time DDoS mitigation. The system is tested on multiple datasets, demonstrating its effectiveness. However, scalability, computational overhead, and cost remain key challenges.
In Table 1, we summarize these works by considering the following criteria: research work, methodology, advantages, and limitations.

Table 1.
Overview of the discussed works.
4. Proposed Approach
The proposed approach is based on Blockchain-enabled Mobile Edge Computing (MEC) which efficiently manages the storage and retrieval of malicious IP addresses, enabling fast and cost-effective verification of network status. We have employed machine learning models including KNN, SVM, DT, and RF in conjunction with Blockchain technology among MEC nodes. Figure 1 shows the design overview of the proposed approach, which highlights the key components and their interactions.
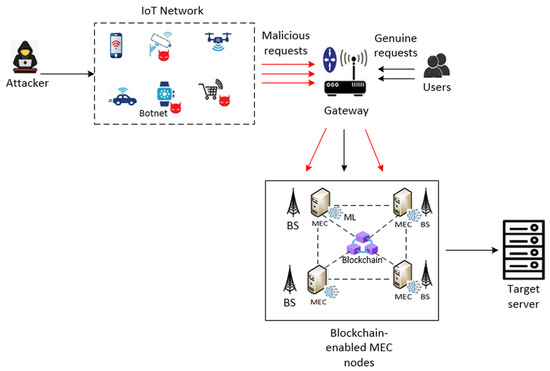
Figure 1.
Blockchain-based MEC for DDoS detection and mitigation architecture.
4.1. Architecture Components
Our architecture is built on the following main components:
- Attacker: The attacker is an external malicious node initiating DDoS attacks, using compromised IoT devices (botnets). The attacker coordinates DDoS attacks by sending commands to the botnets, causing them to overwhelm the target with malicious traffic.
- Botnets: The Botnets consist of compromised IoT devices under the control of the attacker. These devices, now maliciously controlled, send malicious traffic to the target system. They act as intermediaries, carrying out attacks on behalf of the attacker, typically without the knowledge of the IoT device’s owners.
- IoT Network: The IoT network consists of multiple interconnected smart devices, some of which may be compromised (botnet) by an attacker. These devices send both genuine and malicious traffic through the network. All traffic (genuine and malicious) is forwarded to the Gateway for initial processing.
- Gateway: This component manages traffic from the IoT network. It distinguishes between genuine requests (from legitimate users) and malicious requests (from compromised IoT devices). The gateway forwards traffic to the underlying MEC system. Both genuine traffic from legitimate IoT devices/users and malicious traffic from the botnet flow through the gateway, which applies basic checks to the traffic and then forwards it to the Blockchain-enabled MEC nodes for more advanced validation and classification.
- Blockchain-enabled MEC nodes:
- 5.1
- MEC nodes: They provide cloud-computing capabilities and storage closer to the IoT devices by deploying resources at the network edge. This reduces latency, improves data processing speeds, and enhances real-time applications. In this context, the MEC nodes are Blockchain-enabled, meaning they use Blockchain technology for securely storing and managing blacklisted IP addresses and other critical data. Once basic validation is completed, the system interacts with the Blockchain-enabled MEC nodes for further analysis.
- 5.2
- Blockchain: A decentralized ledger storing blacklisted IP addresses. It facilitates distributed storage, ensuring that, once an IP is blacklisted, all MEC nodes can access and retrieve this information. Smart contracts are used to verify whether an incoming IP address is blacklisted or not.
- 5.3
- Base Stations (BSs): These nodes act as access points that enable communication between the IoT network and the MEC nodes. They ensure that traffic from the gateway reaches the MEC nodes for further processing.
- 5.4
- Machine Learning Models: The system employs machine learning models (e.g., KNN, SVM, DT, and RF) to classify traffic and detect malicious patterns. These models are deployed within the MEC nodes to ensure real-time decision-making at the network edge.
- Target Server: The Target Server is the final destination of the genuine requests. The system ensures that only validated traffic reaches this server, preventing it from being overwhelmed by malicious traffic from the botnet.
Initially, the system checks the IP address and other relevant factors for basic validation when it encounters network data. If the data passes the validation, the system continues with its execution. If it fails, the data is blocked from reaching its destination. This process ensures that only valid and reliable data proceeds.
After completing the basic validation, the system connects to the Blockchain network and invokes a smart contract to check if the incoming IP address is blacklisted. If the IP address does not exist in the Blockchain, it means it has not been blacklisted before. The system then classifies the traffic using a pre-trained Machine Learning model to identify potential DDoS attacks.
To prevent blocking legitimate users, a threshold is established. If the time difference between the stored and current timestamps is below this threshold, the timestamp is updated in the Blockchain, and the current network request is blocked from reaching its destination. If the time difference exceeds the threshold, the current IP address is checked using a machine learning model. If identified as malicious, it is added to the Blockchain and blocked; if not, it is allowed to continue to its destination.
Figure 2 depicts the Smart Contract code for adding malicious IP addresses to the Blockchain.

Figure 2.
Smart contract code for adding malicious IP addresses.
In the proposed approach, each MEC node maintains a synchronized copy of the blockchain ledger. When a new malicious IP address is detected by a node, a smart contract is invoked to add this IP to the blockchain. The update is propagated across all MEC nodes, and the validation is performed through a lightweight consensus Proof-of-Authority (PoA) mechanism, which is more suitable for edge deployments than traditional Proof-of-Work. This approach ensures fast validation and low energy consumption. The blacklist is then locally accessible to each MEC node, allowing decentralized and real-time detection without relying on a central authority.
Moreover, in the proposed architecture, IoT end devices, particularly battery-powered sensors or actuators, are not directly responsible for executing machine learning algorithms or interacting with the blockchain. Instead, all computationally intensive operations, including traffic classification and blockchain validation, are offloaded to nearby MEC nodes. These nodes are equipped with moderate processing capabilities (4-core CPU, 8GB RAM) and are designed to handle real-time decision-making tasks. The IoT devices are only responsible for transmitting traffic to the gateway, therefore, conserving their energy and computational resources. The proposed architecture ensures that battery-powered devices remain minimally affected and that the system remains practical for low-power IoT deployments.
4.2. Threshold Calculation
The threshold mechanism plays a vital role in deciding whether an IP address should be blocked, taking into account the duration that has passed since it was last blacklisted. The threshold calculation is based on the time difference between the current timestamp and the stored timestamp in the Blockchain of the malicious IP address. If the time difference is less than the threshold, it will block the IP address and log the action. Otherwise, the network traffic data will be passed to the machine learning model to predict whether it is a DDoS attack. The threshold value is calculated using the mean and standard deviation of the time differences between the current timestamp and the timestamps stored in the Blockchain. This allows us to define a baseline for legitimate IP addresses and determine a threshold for malicious IPs, signaling a potential DDoS attack. The threshold is calculated as follows:
where is a selected factor that sets the threshold level, represents the mean, and s denotes the standard deviation.
Figure 3 describes the solidity smart contract that compares the time difference between the current timestamp and the timestamp stored in the Blockchain against a calculated threshold. It manages a list of blacklisted IP addresses, storing details such as IP, status, and timestamp. Thereafter, it checks if an IP should be blocked based on a dynamic threshold calculated using the mean and standard deviation of the time differences. If the IP does not exist in the blacklist, it passes traffic data to a machine learning model to predict DDoS attacks.
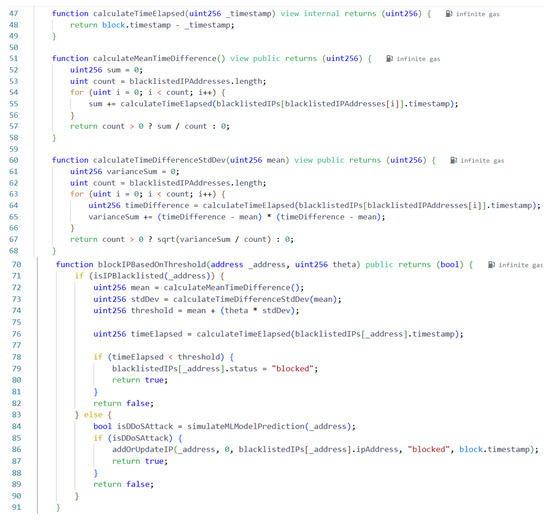
Figure 3.
Solidity code for threshold calculation.
4.3. Machine Learning
Machine learning techniques play an important role in mitigating DDoS attacks in IoT environments. These techniques are capable of analyzing large volumes of network traffic in order to detect abnormal behavior and identify malicious patterns [20]. Machine learning techniques are used to classify and detect malicious packets in DDoS attacks. These techniques help identify specific attack protocols and detect abnormalities in regular traffic, enabling the blocking of malicious activity and improving the overall response to various DDoS threats [17]. Our work introduces two advanced techniques: a Transformer-based model for temporal pattern recognition and LightGBM for efficient edge deployment in terms of latency, along with traditional machine learning classifiers.
4.3.1. Dataset Description
DDoS attacks pose a serious security risk in IoT networks. To effectively evaluate our DDoS mitigation approach, we require a dataset that accurately reflects these attacks. For our assessments, we have chosen the CICDDoS2019 dataset [21]. This dataset, provided by the Canadian Institute for Cybersecurity (CIC), was designed for the study and analysis of DDoS attacks, including HTTP floods, UDP floods, and SYN floods, as well as normal network traffic. This makes it ideal for studying and developing DDoS mitigation techniques. The dataset contains 88 features that detail various aspects of network traffic, such as packet size, flow duration, and various statistical metrics, along with a class attribute to distinguish between legitimate and malicious packets.
4.3.2. Pre-Processing
In order to eliminate unwanted data and noise, we used label encoding to convert categorical data into numerical format which is suitable for making more precise predictions with machine learning algorithms. Data standardization is used to rescale attributes, ensuring that they are on a consistent scale for fair comparison and analysis. The proposed method uses the StandardScaler to achieve this, eliminating bias from differing attribute scales and improving the performance of machine learning algorithms. Missing or infinite values were substituted with the mean values as well. We partitioned the dataset into 70% for training and 30% for testing, using stratified sampling to ensure both normal and attack instances were well-represented. Model hyperparameters were optimized via 5-fold cross-validation on the training set, and final evaluations were reported on the hold-out test set.
4.3.3. Feature Selection
Identifying the best set of features that ensures high accuracy and minimizes noise is essential for effective network traffic classification. Redundant and irrelevant features can create challenges in the classification process. In this study, the Random Forest was utilized to select the top 13 features among the 88 available in the dataset. Random Forest is an effective feature selection method for the CICDDoS2019 dataset due to its high predictive accuracy and minimal overfitting, while also providing interpretability through feature importance scores. This makes it easy to determine the contribution of each feature in attack detection. The process of selecting important features is quick, simple, and accurate compared to other feature selection methods, and its ability to capture complex relationships between features.
Features like source IP, destination IP, Flow-ID, and Timestamp demonstrate considerable importance during the feature selection process. However, they are typically excluded from training machine learning models due to their limited effectiveness in detecting DDoS attacks because they fail to capture the underlying traffic patterns or anomalies. DDoS detection benefits more from behavioral features like traffic volume, packet size, and flow duration, which reveal attack characteristics better than structural metadata.
Figure 4 highlights the most important features selected by the Random Forest Classifier. It also illustrates the importance of each feature during the feature selection process. These features were then used as a training dataset.
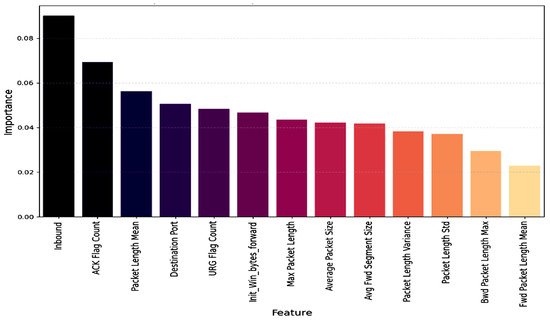
Figure 4.
Top 13 features selected by the Random Forest classifier.
4.3.4. ML Models Used
The machine learning models that we have used to detect DDoS attacks are as follows:
- K-Nearest Neighbors (KNN): The KNN model is a supervised machine-learning technique known for its simplicity and ease of implementation. It classifies data points based on the majority votes of its K nearest neighbors in the feature space [22,23]. It is particularly effective for small datasets but can be computationally expensive for large datasets, especially as the value of ’K’ increases. The performance of KNN can be sensitive to the choice of the K parameter and the distance metric used. The key hyperparameter is the number of neighbors K: we tuned this via grid search using 5-fold cross-validation on the training set, testing values of K from 1 to 15. We found K = 5 to yield the highest validation accuracy, and this value was fixed for the final model.
- Support Vector Machine (SVM): SVM is a robust supervised learning algorithm primarily used for classification, but it can also be applied to regression. Its objective is to identify the optimal hyperplane that best separates classes within the feature space, maximizing the margin between the nearest points, known as support vectors, from each class. SVM excels at capturing complex, non-linear patterns in network traffic, making it highly effective for distinguishing between normal traffic and DDoS attacks [24,25]. We tuned the SVM’s hyperparameters via cross-validation: the RBF kernel coefficient () and the regularization parameter (C) were varied over a grid (, ), seeking to maximize the validation F1-score. The best performance was achieved with and , which we then used in the final model. Our SVM attained robust detection accuracy (∼96.5%) and was effective at capturing complex traffic patterns, yielding high recall in identifying attack flows.
- Decision Tree: Decision Trees are a non-parametric supervised learning model used for both regression and classification tasks. The goal is to construct a tree-based model that predicts target variable values by learning simple decision rules from the data features. This technique requires less data preparation compared to other models. Moreover, Decision Trees are intuitive and easy to interpret, particularly because they can be visualized. In this structure, the internal nodes represent features, the branches denote decision rules, and the leaf nodes deliver the final decision outcomes. Cross-validation showed that setting the maximum depth to 15 and requiring at least five samples per leaf yielded the best generalization. These hyperparameters limited model complexity and overfitting. The resulting decision tree achieved a test accuracy of ∼96.8%—slightly below that of ensembles but with much greater efficiency. With at most 15 conditional checks per input and inference latency of ∼3.5 ms per sample, it is well-suited for edge deployment. Though less expressive than ensembles, it offers a strong, interpretable baseline.
- Random Forest: Random Forest [26] is a supervised machine learning model that builds multiple decision trees from different subsets of the dataset. Each tree makes a prediction, and the final output is determined by the majority vote from all trees. This method helps improve accuracy and reduces the risk of overfitting. It is particularly effective for classification tasks with complex datasets. Random Forest usually uses a “bagging” technique to create an ensemble of decision trees. We configured the Random Forest with 200 trees, beyond which accuracy gains plateaued. Each tree used features per split (), promoting decorrelation. Other parameters followed scikit-learn defaults, with unpruned trees to maximize learning capacity. The model achieved test accuracy, with precision and over recall, indicating strong detection performance and low false alarm rates. Feature importance scores also informed feature selection and offered interpretability. Inference latency averaged ∼16.8 ms per sample—acceptable for many edge scenarios but notably higher than single-tree or LightGBM models. Despite the heavier footprint, Random Forest remains a robust and interpretable benchmark for attack detection.
- Transformer-Based Traffic Analysis: Our model employs a hierarchical self-attention framework to detect complex attack signatures in network traffic. Categorical features are first projected into a dense embedding space, then processed by two transformer encoder layers (each with four attention heads) to capture long-range dependencies across traffic flows. The refined representations pass through a position-wise feedforward network before a sigmoid-activated classification head predicts malicious intent. This approach is particularly effective against multi-stage DDoS attacks, where subtle temporal patterns span extended sequences [27,28]. We designed a lightweight Transformer for edge deployment, using two encoder layers with four attention heads and 128-dimensional embeddings. Categorical inputs were embedded, while numeric features were scaled and concatenated. The model used self-attention to capture long-range patterns, followed by feed-forward layers and a sigmoid output for binary classification. Trained with Adam (learning rate ∼0.001) and dropout regularization, it achieved accuracy and recall on test data—our highest-performing model. Despite its compact design, inference took ∼15.2 ms per flow, highlighting the trade-off between accuracy and speed. Optimization techniques (e.g., quantization) could further improve its edge suitability, but even as-is, it offers top-tier detection within real-time constraints.
- LightGBM: For our gradient boosting framework, we leverage several key optimizations that are specifically beneficial for DDoS detection scenarios. The model employs leaf-wise tree growth rather than level-wise expansion, allowing for faster convergence while maintaining detection accuracy. We implement Gradient-based One-Side Sampling (GOSS) to focus training on more informative instances, significantly improving computational efficiency without compromising performance. The Exclusive Feature Bundling (EFB) technique further enhances processing speed by combining mutually exclusive features, which is particularly valuable given the high-dimensional nature of network traffic data. Additionally, LightGBM’s native support for categorical features eliminates the need for extensive preprocessing while preserving important information in protocol types and other discrete network characteristics. Together, these optimizations create an efficient yet powerful detection system capable of real-time operation at network edges [29]. We configured LightGBM with 200 boosting iterations, which provided near-optimal accuracy in cross-validation. Unlike Random Forest, LightGBM uses shallow, sequentially boosted trees and a leaf-wise growth strategy that accelerates convergence—ideal for handling variable DDoS traffic. To optimize for edge deployment, we enabled Gradient-based One-Side Sampling (GOSS) and Exclusive Feature Bundling (EFB), improving training efficiency with minimal accuracy loss. After tuning the learning rate and num_leaves, the model achieved accuracy, with precision and recall around , and an inference latency of only ∼5.1 ms per sample—the fastest among all models. Given its balance of speed, accuracy, and low resource use, LightGBM was chosen as the primary model for our blockchain-integrated MEC framework.
5. Performance Evaluation
This section presents a comprehensive evaluation of our proposed DDoS detection approach, including the Transformer-based model and LightGBM alongside traditional machine learning classifiers. We assess performance using multiple metrics across all models, with particular focus on the comparative advantages of each approach in different attack scenarios.
5.1. Evaluation Methodology
Our evaluation employs the CICDDoS2019 dataset [21], which offers a comprehensive set of DDoS attacks that accurately reflect real-world threats targeting IoT environments. The dataset was partitioned into 70% training and 30% testing sets, with 5-fold cross-validation applied to ensure robust results. All experiments were conducted on an edge computing testbed with specifications matching typical IoT gateway hardware (4-core CPU, 8 GB RAM).
5.2. Metrics
We evaluate model performance using both traditional and time-sensitive metrics:
- Accuracy: Measures overall prediction correctness:
- Precision: Indicates attack detection reliability:
- Recall: Measures attack detection coverage:
- F1 Score: Balanced metric for imbalanced data:
- Latency: Critical for real-time detection (measured in milliseconds)
5.3. Configurations
- KNN: with Euclidean distance metric (optimized via grid search).
- SVM: RBF kernel with = 0.1 and .
- DT: Pruned with max depth = 15 and min samples leaf = 5.
- RF: 200 estimators with max features = ‘sqrt’.
- Transformer: 2 encoder layers (4 attention heads), 128-dim embeddings.
- LightGBM: 200 estimators with GOSS and EFB optimizations.
Table 2 summarizes the quantitative results, highlighting the Transformer’s superior detection capabilities while noting LightGBM’s operational advantages for edge deployment:

Table 2.
Comprehensive model evaluation results.
Our experimental results demonstrate several improvements in DDoS attack detection performance. Precisely, the Transformer model achieves exceptional detection capabilities for complex DDoS attacks, achieving a remarkable 99.82% recall rate. For real-time implementations, LightGBM proves significantly more efficient than RF, proving three times faster in terms of latency with better accuracy of 99.71%. Traditional approaches, including KNN and SVM, remain effective solutions for less resource-constrained environments. All evaluated models consistently maintain over 95% accuracy, confirming their robustness for diverse threat scenarios in IoT systems.
The results demonstrate that our hybrid approach, combining Transformer models for detection and LightGBM for real-time detection, provides optimal performance for IoT DDoS mitigation. The Transformer model proves particularly effective against DDoS attacks, while LightGBM’s efficiency makes it ideal for edge deployment.
Figure 5 presents the comprehensive performance comparison across all models. The Transformer architecture achieved the highest accuracy (99.78%), followed closely by LightGBM (99.71%), while maintaining the RF’s good performance (99.62%). The complete results demonstrate the following:
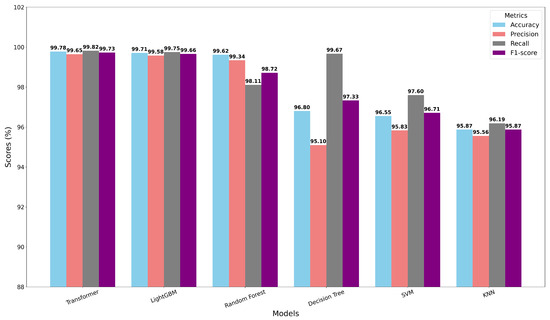
Figure 5.
Comparison of performance metrics across different models.
- Transformer excels in recall (99.82%), ideal for attack detection.
- LightGBM provides the best speed–accuracy tradeoff (5.1 ms latency).
- RF remains robust with 99.34% precision, while traditional models show acceptable precision (KNN: 95.87%, SVM: 96.55%).
In addition, we have evaluated the proposed approach to measuring the average latency at edge nodes across the six different models, the results are shown in Figure 6.
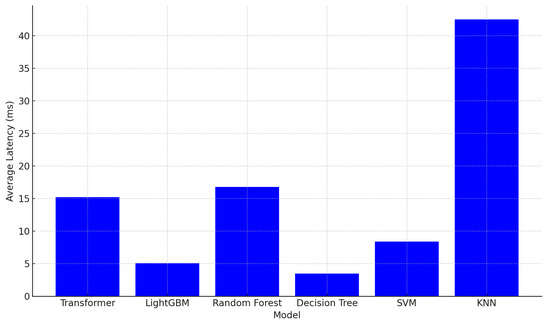
Figure 6.
Average latency comparison for different models.
Figure 6 illustrates the average latency (in milliseconds) of various machine learning models deployed in MEC environment. Among the models, LightGBM demonstrates the lowest latency (5.1 ms), making it highly suitable for real-time applications. In contrast, KNN exhibits the highest latency (42.5 ms), indicating its limited practicality for edge-based DDoS mitigation.
Integration of blockchain into a MEC environment introduces overheads that must be minimized to ensure compatibility with IoT systems. Our architecture limits the use of blockchain to critical events, such as the addition of newly detected malicious IP addresses, therefore reducing the frequency of write operations. The smart contracts are designed with minimal logic to reduce computational cost during execution. In terms of storage, the blockchain ledger contains only essential metadata (IP, timestamp, status), which keeps its size lightweight and manageable by MEC nodes. Furthermore, using machine learning models is performed at the edge, avoiding the need for constant interaction with the blockchain, and reducing latency. This design ensures that the system remains scalable and energy-efficient in resource-constrained IoT environments.
6. Conclusions and Future Works
This research paves the way for further advancements in IoT security, leveraging the unique capabilities of Blockchain, Mobile Edge Computing, and Machine Learning algorithms to safeguard critical systems and services in the era of the IoT. We presented a novel approach that integrates Blockchain technology, Mobile Edge Computing, and Machine Learning algorithms to mitigate DDoS attacks in IoT environments. The Blockchain-based communication ensures the security and integrity of the data shared among edge devices, while the Mobile Edge Computing infrastructure provides the necessary computational resources for real-time traffic analysis and decision-making. Machine learning algorithms, including kNN, SVM, DT, RF, Transformer-based models and LightGBM have been employed to evaluate the accuracy of identifying DDoS attack patterns, enabling edge devices to detect attacks with high efficiency. The results of the evaluation have demonstrated that the Transformer-based model can identify DDoS attacks with higher accuracy compared to KNN, SVM, DT, RF, and LightGBM techniques.
In addition to Blockchain’s inherent immutability, our system is designed to address robustness against multiple attack vectors. Transformer-based models demonstrated strong detection of low-rate and application-layer DDoS attacks due to their self-attention capabilities, which capture long-term temporal dependencies.
We plan to explore the integration of more sophisticated deep learning models to further enhance the accuracy and efficiency of DDoS attacks detection and mitigation. Furthermore, we aim to conduct extensive real-world testing and deployment of the proposed approach to validate its performance and applicability in diverse IoT scenarios, including industrial IoT, smart cities, and autonomous systems. It would also be interesting to address the threat of adversarial machine learning attacks as part of future work.
Author Contributions
Investigation and writing of the original version of the manuscript: M.C. project administration, funding acquisition, supervision, and editing of the manuscript: A.B. and R.C. All authors have read and agreed to the published version of the manuscript.
Funding
A.B. and R.C. acknowledge the financial support of the Foundation for Science and Technology (FCT, Portugal) in the framework of the Associated Laboratory ARISE (LA/P/0112/2020), R&D Unit SYSTEC (base UIDB/00147/2020 and programmatic UIDP/00147/2020 funds).
Data Availability Statement
All data included in this manuscript are available from the corresponding author upon reasonable request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Aljuhani, A. Machine Learning Approaches for Combating Distributed Denial of Service Attacks in Modern Networking Environments. IEEE Access 2021, 9, 42236–42264. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Weber, R.H. Internet of Things – New security and privacy challenges. Comput. Law Secur. Rev. 2010, 26, 23–30. [Google Scholar] [CrossRef]
- Hekmati, A.; Zhang, J.; Sarkar, T.; Jethwa, N.; Grippo, E.; Krishnamachari, B. Correlation-aware neural networks for DDoS attack detection in IoT systems. IEEE/ACM Trans. Netw. 2024, 32, 3929–3944. [Google Scholar] [CrossRef]
- Luo, Y.; Chen, X.; Ge, N.; Feng, W.; Lu, J. Transformer-based device-type identification in heterogeneous IoT traffic. IEEE Internet Things J. 2022, 10, 5050–5062. [Google Scholar] [CrossRef]
- Ghourabi, A. A security model based on LightGBM and transformer to protect healthcare systems from cyberattacks. IEEE Access 2022, 10, 48890–48903. [Google Scholar] [CrossRef]
- Hallman, R.; Bryan, J.; Palavicini, G., Jr.; Divita, J.; Romero-Mariona, J. IoDDoS—The Internet of Distributed Denial of Service Attacks: A Case Study of the Mirai Malware and IoT-Based Botnets. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; pp. 47–58. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Abomhara, M.; Køien, G.M. Security and privacy in the Internet of Things: Current status and open issues. In Proceedings of the 2014 International Conference on Privacy and Security in Mobile Systems (PRISMS), Aalborg, Denmark, 11–14 May 2014; pp. 1–8. [Google Scholar]
- Kumari, P.; Jain, A.K. A comprehensive study of DDoS attacks over IoT network and their countermeasures. Comput. Secur. 2023, 127, 103096. [Google Scholar] [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Arbor, A.; Invernizzi, L.; et al. Understanding the Mirai Botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Fernandes, E.; Jung, J.; Prakash, A. Security Analysis of Emerging Smart Home Applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 636–654. [Google Scholar]
- Mahjabin, T.; Xiao, Y.; Sun, G.; Jiang, W. A survey of distributed denial-of-service attack, prevention, and mitigation techniques. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717741463. [Google Scholar] [CrossRef]
- Adat, V.V.; Gupta, B.B. A DDoS attack mitigation framework for internet of things. In Proceedings of the 2017 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 6–8 April 2017; pp. 1–5. [Google Scholar]
- Najar, A.; Naik, S.M. DDoS attack detection using MLP and Random Forest Algorithms. Int. J. Inf. Technol. 2022, 14, 2317–2327. [Google Scholar] [CrossRef]
- Lawal, M.A.; Shaikh, R.A.; Hassan, S.R. A DDoS Attack Mitigation Framework for IoT Networks using Fog Computing. Procedia Comput. Sci. 2021, 182, 13–20. [Google Scholar] [CrossRef]
- Manikumar, D.V.V.S.; Maheswari, B.U. Blockchain Based DDoS Mitigation Using Machine Learning Techniques. In Proceedings of the 2020 Second International Conference on Inventive Research in Computing Applications (ICIRCA), Coimbatore, India, 15–17 July 2020; pp. 794–800. [Google Scholar]
- Javaid, U.; Siang, A.K.; Aman, M.N.; Sikdar, B. Mitigating IoT Device based DDoS Attacks using Blockchain. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems (CryBlock’18), Munich, Germany, 15 June 2018; pp. 71–76. [Google Scholar]
- Kumari, P.; Jain, A.; Seth, A.; Raghav. Leveraging blockchain and machine learning to counter DDoS attacks over IoT network. Multimed. Tools Appl. 2024, 84, 317–341. [Google Scholar] [CrossRef]
- Berríos, S.; Garcia, S.; Hermosilla, P.; Allende-Cid, H. A Machine-Learning-Based Approach for the Detection and Mitigation of Distributed Denial-of-Service Attacks in Internet of Things Environments. Appl. Sci. 2025, 15, 6012. [Google Scholar] [CrossRef]
- Canadian Institute for Cybersecurity. DDoS Evaluation Dataset (CICDDoS2019). 2024. Available online: https://www.unb.ca/cic/datasets/ddos-2019.html (accessed on 19 May 2024).
- Sasikala, B.; Biju, V.; Prashanth, C. Kappa and accuracy evaluations of machine learning classifiers. In Proceedings of the 2017 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19–20 May 2017; pp. 20–23. [Google Scholar]
- Thepade, S.; Das, R.; Ghosh, S. Performance comparison of feature vector extraction techniques in RGB color space using block truncation coding for content based image classification with discrete classifiers. In Proceedings of the 2013 Annual IEEE India Conference (INDICON), Mumbai, India, 13–15 December 2013; pp. 1–6. [Google Scholar]
- Awad, M.; Khanna, R. Support Vector Machines for Classification. In Efficient Learning Machines: Theories, Concepts, and Applications for Engineers and System Designers; Apress: Berkeley, CA, USA, 2015; pp. 39–66. [Google Scholar]
- Kokila, R.; Somasundaram, T.S.; Kannan, G. DDoS detection and analysis in SDN-based environment using support vector machine classifier. In Proceedings of the 2014 Sixth International Conference on Advanced Computing (ICoAC), Chennai, India, 17–19 December 2014; pp. 205–210. [Google Scholar]
- Breiman, L. Random Forests. Mach. Learn. 2001, 45, 5–32. [Google Scholar] [CrossRef]
- Wu, Z.; Zhang, H.; Wang, P.; Sun, Z. RTIDS: A Robust Transformer-Based Approach for Intrusion Detection System. IEEE Access 2022, 10, 64375–64387. [Google Scholar] [CrossRef]
- Yin, K.; Yang, Y.; Yao, C.; Yang, J. Long-Term Prediction of Network Security Situation Through the Use of the Transformer-Based Model. IEEE Access 2022, 10, 56145–56157. [Google Scholar] [CrossRef]
- Truong, V.H.; Tangaramvong, S.; Papazafeiropoulos, G. An Efficient LightGBM-Based Differential Evolution Method for Nonlinear Inelastic Truss Optimization. Expert Syst. Appl. 2024, 237, 121530. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).