Individual Security and Network Design with Malicious Nodes
Abstract
1. Introduction
1.1. The Motivation
1.2. Contribution
1.3. Related Work
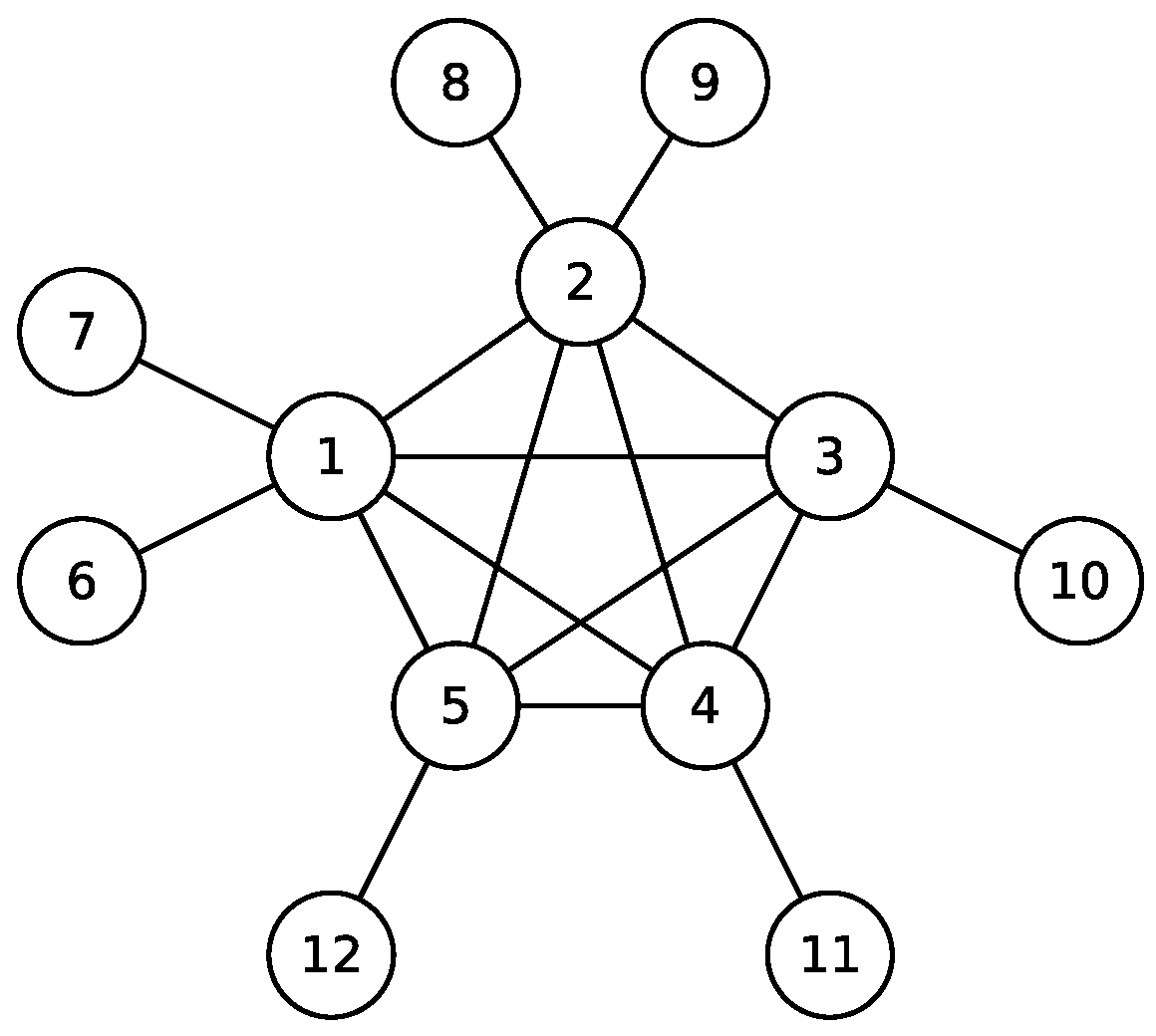
2. The Model
- The types of the nodes are realized.
- D chooses a network , where is the set of all undirected networks over V.
- Nodes from V observe G and choose, simultaneously and independently, whether to protect (what we denote by 1) or not (denoted by 0). This determines the set of protected nodes . The protection of the byzantine nodes is fake and, when attacked, such a node gets infected and transmits the infection to all her neighbors.
- observes the protected network and chooses a subset consisting of nodes to infect. The infection spreads and eliminates all unprotected or byzantine nodes reachable from I in G via a path that does not contain a genuine protected node from . This leads to the residual network obtained from G by removing all the infected nodes.
2.1. Remarks on the Model
3. The Analysis
3.1. Centralized Defense
- (i)
- G has at most three connected components.
- (ii)
- If and , then G is a generalized k-star with protected core and unprotected periphery.
- (iii)
- If and , then G is composed of a generalized k-star of size with protected core and unprotected periphery and a single unprotected node.
- (iv)
- If and , then G has two connected components of size and, if , a single unprotected node.
- (v)
- If and , then G either has the structure described in Proposition 1 or G is composed of three components of size , depending on the term achieving the maximum in Equation (4).
- (vi)
- If , then G is composed of a generalized 2-star with protected core and unprotected periphery, an unprotected component of size and, possibly, a single unprotected node. The size q is the number achieving maximum in Equation (6). The existence of a single unprotected node depends on the term achieving maximum in Equation (5).
3.2. Decentralized Defense
- all genuine nodes use pure strategies,
- if , then all genuine nodes are protected,
- if , then all genuine core nodes are protected and all genuine periphery nodes are not protected,
- if , then all genuine nodes are not protected.
4. Extensions of the Model
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Appendix A. Characterization of Equilibria in the Centralized Defense Model

- Case I:
- Suppose that . We then have by the inequality
- Case II:
- Case III:
- Suppose that and . Let , where and . If , then we have , which is impossible for . Hence, and we have . Note that the open interval contains an integer number if and only if . This condition is satisfied only for and . Hence, we have and for some . We want to prove that or, equivalently,If , then this inequality takes form . If , then we have and hence .

Appendix B. Characterization of Equilibria in the Centralized Defense Model
References
- Laszka, A.; Felegyhazi, M.; Buttyán, L. A survey of interdependent information security games. ACM Comput. Surv. 2015, 47, 23. [Google Scholar] [CrossRef]
- Böhme, R.; Schwartz, G. Modeling cyber-insurance: Towards a unifying framework. In Proceedings of the 9th Workshop on the Economics of Information Security (WEIS 2010), Cambridge, MA, USA, 7–8 June 2010. [Google Scholar]
- Cerdeiro, D.; Dziubiński, M.; Goyal, S. Individual security and network design. In Proceedings of the 15th ACM Conference on Economics and Computation (EC’14), Stanford, CA, USA, 9–12 June 2014; pp. 205–206. [Google Scholar] [CrossRef]
- Cerdeiro, D.; Dziubiński, M.; Goyal, S. Individual security, contagion, and network design. J. Econom. Theory 2017, 170, 182–226. [Google Scholar] [CrossRef]
- Weaver, N.; Paxson, V.; Staniford, S.; Cunningham, R. A taxonomy of computer worms. Proceedings of Tenth ACM Conference on Computer and Communications Security 2003, Washington, DC, USA, 27–30 October 2003; pp. 11–18. [Google Scholar]
- Zou, C.; Gong, W.; Towsley, D. Code red worm propagation modeling and analysis. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 138–147. [Google Scholar]
- Chen, Z.; Gao, L.; Kwiat, K. Modeling the spread of active worms. In Proceedings of the Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies (IEEE INFOCOM’03), San Francisco, CA, USA, 30 March–3 April 2003; pp. 1890–1900. [Google Scholar]
- Dainotti, A.; Pescape, A.; Ventre, G. Worm Traffic Analysis and Characterization. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, Scotland, 24–28 June 2007; pp. 1435–1442. [Google Scholar]
- Shapiro, C.; Varian, H. Information Rules: A Strategic Guide to the Network Economy; Harvard Business School Press: Boston, MA, USA, 2000. [Google Scholar]
- Moscibroda, T.; Schmid, S.; Wattenhofer, R. When selfish meets evil: Byzantine players in a virus inoculation game. In Proceedings of the 25th ACM Symposium on Principles of Distributed Computing (PODC 2006), Denver, CO, USA, 23–26 July 2006; pp. 35–44. [Google Scholar]
- Moscibroda, T.; Schmid, S.; Wattenhofer, R. The price of malice: A game-theoretic framework for malicious behavior. Int. Math. 2009, 6, 125–156. [Google Scholar] [CrossRef]
- Baccarelli, E.; Naranjo, P.; Shojafar, M.; Scarpiniti, M. Q*: Energy and delay-efficient dynamic queue management in TCP/IP virtualized data centers. Comput. Commun. 2017, 102, 89–106. [Google Scholar] [CrossRef]
- Pooranian, Z.; Chen, K.; Yu, C.; Conti, M. RARE: Defeating side channels based on data-deduplication in cloud storage. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 444–449. [Google Scholar]
- Isaac, J.; Zeadally, S.; Cámara, J. Security attacks and solutions for vehicular ad hoc networks. IET Commun. 2010, 4, 894–903. [Google Scholar] [CrossRef]
- Petrillo, A.; Pescapé, A.; Santini, S. A collaborative approach for improving the security of vehicular scenarios: The case of platooning. Comput. Commun. 2018, 122, 59–75. [Google Scholar] [CrossRef]
- Dainotti, A.; Pescapé, A.; Ventre, G. A cascade architecture for DoS attacks detection based on the wavelet transform. J. Comput. Security 2009, 17, 945–968. [Google Scholar] [CrossRef]
- Chen, X.; Makki, K.; Yen, K.; Pissinou, N. Sensor network security: A survey. IEEE Commun. Sur. Tutor. 2009, 11, 52–73. [Google Scholar] [CrossRef]
- Padmavathi, G.; Shanmugapriya, D. A survey of attacks, security mechanisms and challenges in wireless sensor networks. arXiv, 2009; arXiv:0909.0576. [Google Scholar]
- Castiglione, A.; D’Arco, P.; De Santis, A.; Russo, R. Secure group communication schemes for dynamic heterogeneous distributed computing. Future Gener. Compute. Syst. 2017, 74, 313–324. [Google Scholar] [CrossRef]
- Kiskani, M.; Sadjadpour, H. A secure approach for caching contents in wireless ad hoc networks. IEEE Trans. Veh. Tech. 2017, 66, 10249–10258. [Google Scholar] [CrossRef]
- Marti, S.; Giuli, T.; Lai, K.; Baker, M. Mitigating routing misbehavior in mobile ad hoc networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000; pp. 255–265. [Google Scholar]
- Michiardi, P.; Molva, R. Core: A Collaborative reputation mechanism to enforce node cooperation in mobile ad hoc networks. In Advanced Communications and Multimedia Security: IFIP TC6/TC11 Sixth Joint Working Conference on Communications and Multimedia Security; Jerman-Blažič, B., Klobučar, T., Eds.; Springer: Boston, MA, USA, 2002; pp. 107–121. [Google Scholar]
- Zhang, Y.; Lee, W.; Huang, Y.A. Intrusion detection techniques for mobile wireless networks. Wirel. Netw. 2003, 9, 545–556. [Google Scholar] [CrossRef]
- Kargl, F.; Klenk, A.; Schlott, S.; Weber, M. Advanced detection of selfish or malicious nodes in ad hoc networks. In Security in Ad-hoc and Sensor Networks; Castelluccia, C., Hartenstein, H., Paar, C., Westhoff, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2005; pp. 152–165. [Google Scholar]
- Nasser, N.; Chen, Y. Enhanced intrusion detection system for discovering malicious nodes in mobile ad hoc networks. In Proceedings of the 2007 IEEE International Conference on Communications, Glasgow, Scotland, 24–28 June 2007; pp. 1154–1159. [Google Scholar]
- Buttyán, L.; Hubaux, J.P. Stimulating cooperation in self-organizing mobile ad hoc networks. Mob. Netw. Appl. 2003, 8, 579–592. [Google Scholar] [CrossRef]
- Zhong, S.; Chen, J.; Yang, Y. Sprite: A simple, cheat-proof, credit-based system for mobile ad-hoc networks. In Proceedings of the 22nd Annual Joint Conference of the IEEE Computer and Communications Societies, San Francisco, CA, USA, 30 March–3 April 2003; pp. 1987–1997. [Google Scholar]
- Smith, A.; Vorobeychik, Y.; Letchford, J. Multidefender security games on networks. ACM SIGMETRICS Perform. Eval. Rev. 2014, 41, 4–7. [Google Scholar] [CrossRef]
- Lou, J.; Vorobeychik, Y. Equilibrium analysis of multidefender security games. In Proceedings of the 24th International Conference on Artificial Intelligence (IJCAI’15), Buenos Aires, Argentina, 25–31 July 2015; pp. 596–602. [Google Scholar]
- Lou, J.; Smith, A.; Vorobeychik, Y. Multidefender security games. IEEE Intell. Syst. 2017, 32, 50–60. [Google Scholar] [CrossRef]
- Kunreuther, H.; Heal, G. Interdependent security. J. Risk Uncertain. 2003, 26, 231–249. [Google Scholar] [CrossRef]
- Varian, H. System reliability and free riding. In Economics of Information Security; Camp, L.J., Lewis, S., Eds.; Springer: Boston, MA, USA, 2004; pp. 1–15. [Google Scholar] [CrossRef]
- Aspnes, J.; Chang, K.; Yampolskiy, A. Inoculation strategies for victims of viruses and the sum-of-squares partition problem. J. Comput. Syst. Sci. 2006, 72, 1077–1093. [Google Scholar] [CrossRef]
- Lelarge, M.; Bolot, J. Network externalities and the deployment of security features and protocols in the Internet. ACM SIGMETRICS Perform. Eval. Rev. 2008, 36, 37–48. [Google Scholar] [CrossRef]
- Lelarge, M.; Bolot, J. A local mean field analysis of security investments in networks. In Proceedings of the 3rd International Workshop on Economics of Networked Systems (NetEcon’08), Seattle, WA, USA, 17–22 August 2008; pp. 25–30. [Google Scholar] [CrossRef]
- Chan, H.; Ceyko, M.; Ortiz, L. Interdependent defense games: modeling interdependent security under deliberate attacks. arXiv, 2012; arXiv:1210.4838. [Google Scholar]
- Acemoglu, D.; Malekian, A.; Ozdaglar, A. Network security and contagion. J. Econom. Theory 2016, 166, 536–585. [Google Scholar] [CrossRef]
- Gueye, A.; Walrand, J.; Anantharam, V. Design of network topology in an adversarial environment. In Proceedings of the 2010 Conference on Decision and Game Theory for Security (GameSec 2010), Berlin, Germany, 22–23 November 2010; pp. 1–20. [Google Scholar] [CrossRef]
- Gueye, A.; Walrand, J.C.; Anantharam, V. How to choose communication links in an adversarial environment? In Proceedings of the 2nd International Conference on Game Theory for Networks (GameNets 2011), College Park, MD, USA, 14–15 November 2011; pp. 233–248. [Google Scholar]
- Gueye, A.; Marbukh, V.; Walrand, J. Towards a metric for communication network vulnerability to attacks: A game theoretic approach. In Proceedings of the 3rd International Conference on Game Theory for Networks (GameNets 2012), Budapest, Hungary, 5–6 November 2012; pp. 259–274. [Google Scholar] [CrossRef]
- Laszka, A.; Szeszlér, D.; Buttyán, L. Game-theoretic robustness of many-to-one networks. In Proceedings of the 3rd International Conference on Game Theory for Networks (GameNets 2012), Budapest, Hungary, 5–6 November 2012; pp. 88–98. [Google Scholar] [CrossRef]
- Laszka, A.; Szeszlér, D.; Buttyán, L. Linear loss function for the network blocking game: An efficient model for measuring network robustness and link criticality. In Proceedings of the 3rd International Conference on Game Theory for Networks (GameNets 2012), Budapest, Hungary, 5–6 November 2012; pp. 152–170. [Google Scholar] [CrossRef]
- Goyal, S.; Jabbari, S.; Kearns, M.; Khanna, S.; Morgenstern, J. Strategic network formation with attack and immunization. In Proceedings of the 12th Conference on Web and Internet Economics (WINE 2016), Montreal, QC, Canada, 11–14 December 2016; pp. 429–443. [Google Scholar] [CrossRef]
- Aghassi, M.; Bertsimas, D. Robust game theory. Math. Program. 2006, 107, 231–273. [Google Scholar] [CrossRef]
- Hiriart-Urruty, J.B.; Lemaréchal, C. Convex Analysis and Minimization Algorithms I: Fundamentals; Springer: Berlin/Heidelberg, Germany, 1993. [Google Scholar]
| Notation | Definition |
|---|---|
| n | number of nodes |
| number of byzantine nodes | |
| number of nodes infected by the adversary | |
| f | component value function |
| G | network |
| set of protected nodes | |
| payoff to the designer, the adversary, and a node | |
| pessimistic payoff to the designer and a node |
| 50-star | |||||
| 30-star | 25-star | ||||
| 15-star | 17-star | ||||
| 12-star | 10-star | 13-star | |||
| 6-star | 6-star | 10-star | |||
| 4-star | 5-star | 5-star | |||
| two disconnected components of equal size | two disconnected components of equal size | two disconnected components of equal size | |||
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Janus, T.; Skomra, M.; Dziubiński, M. Individual Security and Network Design with Malicious Nodes. Information 2018, 9, 214. https://doi.org/10.3390/info9090214
Janus T, Skomra M, Dziubiński M. Individual Security and Network Design with Malicious Nodes. Information. 2018; 9(9):214. https://doi.org/10.3390/info9090214
Chicago/Turabian StyleJanus, Tomasz, Mateusz Skomra, and Marcin Dziubiński. 2018. "Individual Security and Network Design with Malicious Nodes" Information 9, no. 9: 214. https://doi.org/10.3390/info9090214
APA StyleJanus, T., Skomra, M., & Dziubiński, M. (2018). Individual Security and Network Design with Malicious Nodes. Information, 9(9), 214. https://doi.org/10.3390/info9090214




