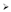An Improved Two-Way Security Authentication Protocol for RFID System
Abstract
:1. Introduction
2. The Proposed Security Protocol
2.1. Initial Conditions and Related Instructions
2.2. Authentication Process
- In the initial state, the tags need to store their own identifiers and the secret value , , and readers only need to store their own identifiers , and backend database store all readers data and tags data .
- The reader generates a random number , and it sends query to the tag as an authentication request.
- After received the reader’s request, the tag generates a random number using its own identification ID. The tag calculates , (where, is the concatenation operator, exclusive OR operation), and the M value is divided into two parts, and .
- The tag sends data , , to the reader.
- The reader calculates after received the message from the tag, and it sends the data , , , , and to the backend server.
- After received the message from the reader, the backend server verifies the legitimacy of the identity of the reader, and then the server verifies the legitimacy of the identity of the tag. If the reader and tag identity are legitimate, the server will update the secret value shared by tag and the server, otherwise the server finishes the authentication process. The detailed process is as follows.
-
- Verify the legitimacy of the reader: the backend server calculates and uses the value of the reader itself to check whether the equation is satisfied. The process continues to the next step if the condition is satisfied, otherwise the verification process is terminated.
-
- Verify the legitimacy of the tag: The backend database calculates to check whether the equation is satisfied. The process continues to the next step if the condition is satisfied, otherwise the backend server makes an authentication using the previous retained . The process continues to the next step if the condition is satisfied with retained , otherwise the verification process is terminated.
-
- If the above steps are finished, the backend server calculates according to the tag’s data pair stored by it. If there is , the tag is authenticated, otherwise authentication process is stopped.
-
- The tag’s secret value is updated in this step, let and .
-
- The tag’s secret value remains unchanged.
-
- Finally, the backend server calculates the following two values , and .
-
- The backend server sends the value to the reader.
- The reader calculates that is the tag ID value, and it sends to tag.
- When the tag receives the data, it makes a comparison between and . If equals to , the tag calculates the value as the updated tag’s key, otherwise the authentication process is terminated.
3. Protocol Analysis
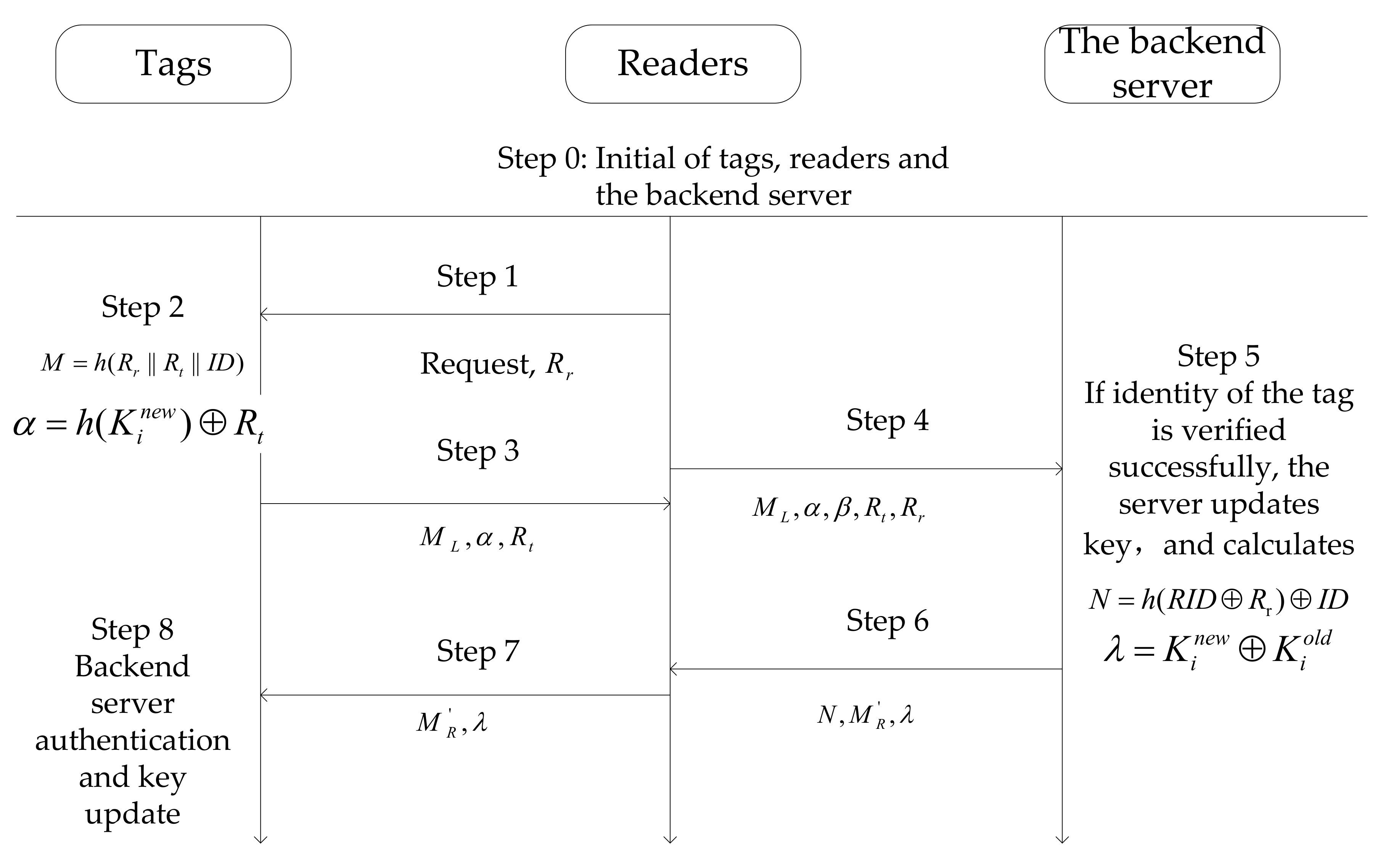
3.1. BAN Logical Analysis and Proof of Security
- message-meaning rules R1: ;
- Fresh rules R2: ;
- Logical community rules R3: ;
- Belief rules R4: ;
3.1.1. Protocol Initialization Hypothesis
3.1.2. Establish an Idealized Protocol Model
3.1.3. The Expectations of the Protocol
3.1.4. Proof of the Authentication Process
3.2. Security Comparisons
- (1)
- Data privacy. Each message in the solution is encrypted using hash function and XOR operation. Because of the unidirectional nature of hash function [21], it is difficult for attackers to obtain confidential information such as ID, RID. In the authentication process, random number is not the same, so the solution can guarantee the security of the label ID information.
- (2)
- Replay attack [22]. Assuming that an attacker has recorded the information sent by the tag in advance, when the reader communicates with the tag again, the attacker is disguised as a legal label to communicate with a reader through the recorded tag information. The value of is associated with the random number of the reader and the tag. Because the random number of each authentication is different, each value of tag response is also not the same, even if the illegal attacker intercepted the previous information, it cannot simulate the value next time. As a result, the tag or reader will not accept the copied information.
- (3)
- Fake attack [23]. It can be seen from above that an attacker cannot obtain private information of a label and a reader, so it cannot disguise as a legitimate label and reader.
- (4)
- Position tracking [24]. The random number of each communication is different, and the transmitted information of the label is different each time, which can effectively prevent the fixed output caused by the location tracking problem.
- (5)
- Asynchronous attack [25]. Because of the static ID security protocol, the label ID information is the same each time, it is impossible to appear asynchronous attack.
- (6)
- Brute-force attack [14]. The hash function SHA3-224 is recommended. When the adversary has acquired , , , , via eavesdropping or meaningless requests, a brute-force attack must be performed in order to obtain , , , via analysis of the messages. If we assume that initially an adversary knows , the complexity of determining and from is 2196. The number of possible pairs of and is 296, and based on the respective values, the number of estimations for the 64 bits ID and the 128 bits is 2192. Therefore, an adversary has requested 2388 estimations of and . Based on above analysis, the scheme proposed is sufficiently secure against the brute-force attack.
4. Evaluation
4.1. Experimental Environment
- Hardware sectionProcessor: Intel Core i5-3230M CPU @ 2.60GHZ RAM: 4GBTag: The passive MIFARE Plus IC card
- Software sectionOS: Windows 7 ProfessionalSimulation tools: Eclipse Java EE IDE for Web Developers (Version: 4.6.3), Java SE Development Kit 8 (Version: 1.8), Network simulator-2, MySQL (Version: 10.1.2531.0, for Win32)
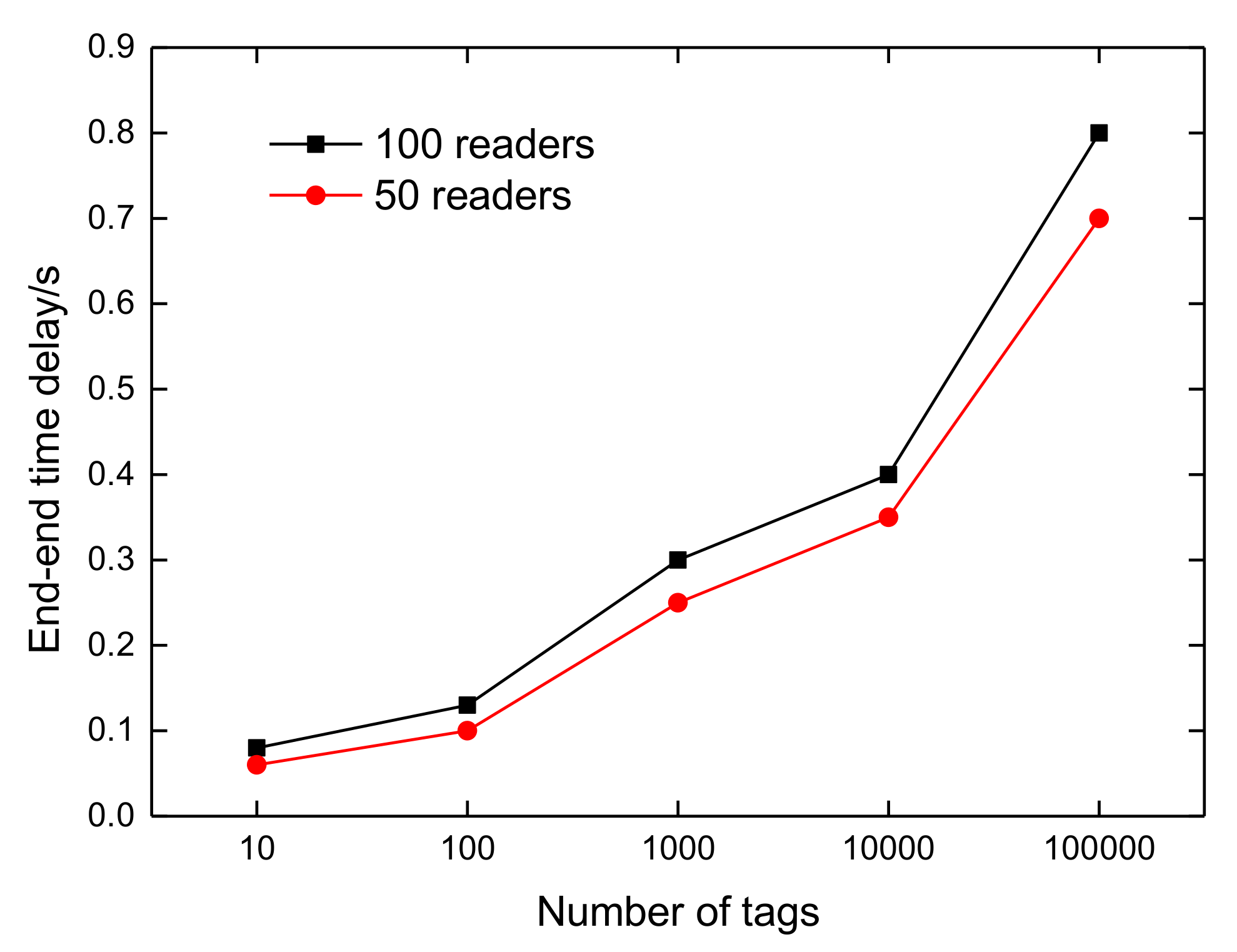
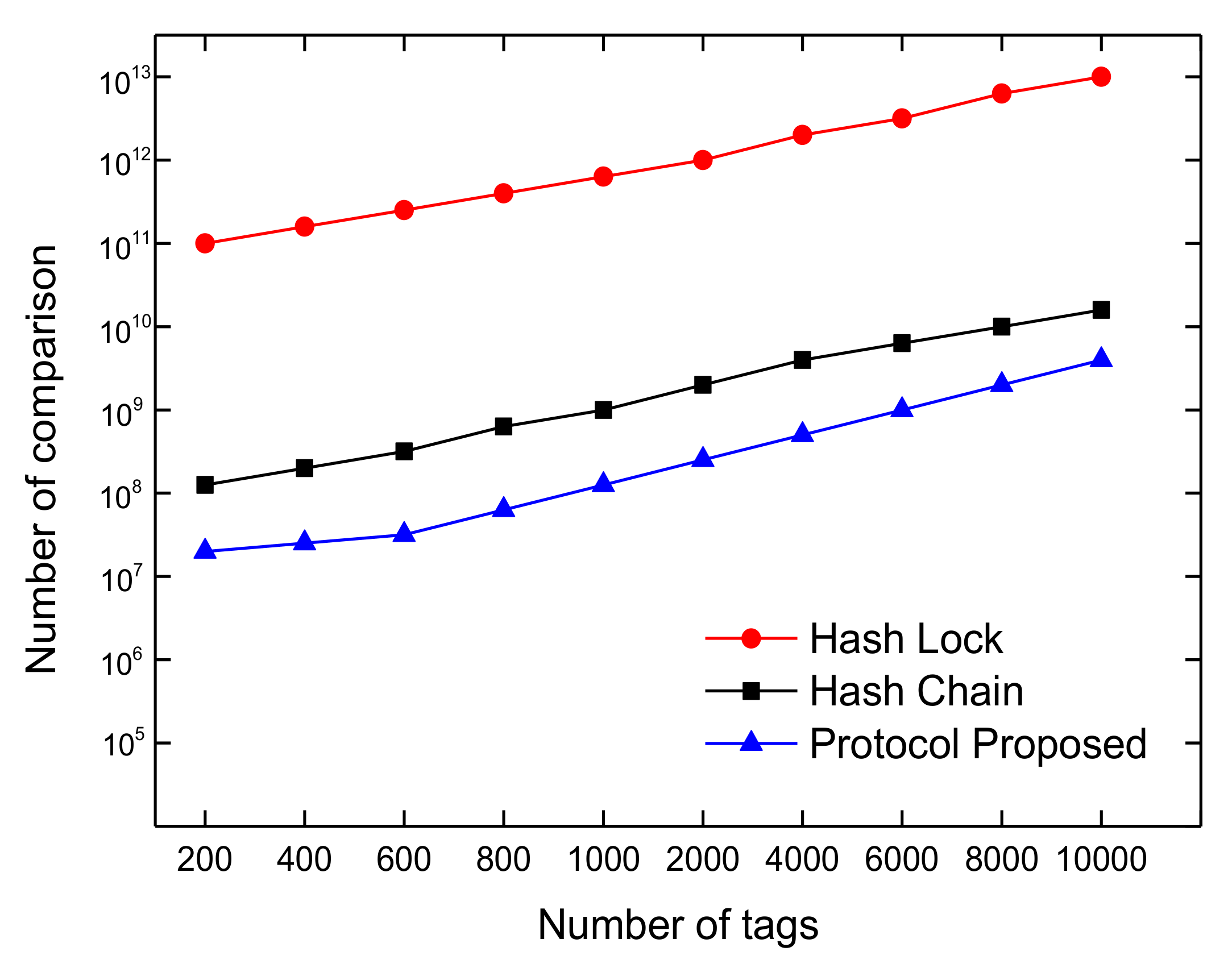
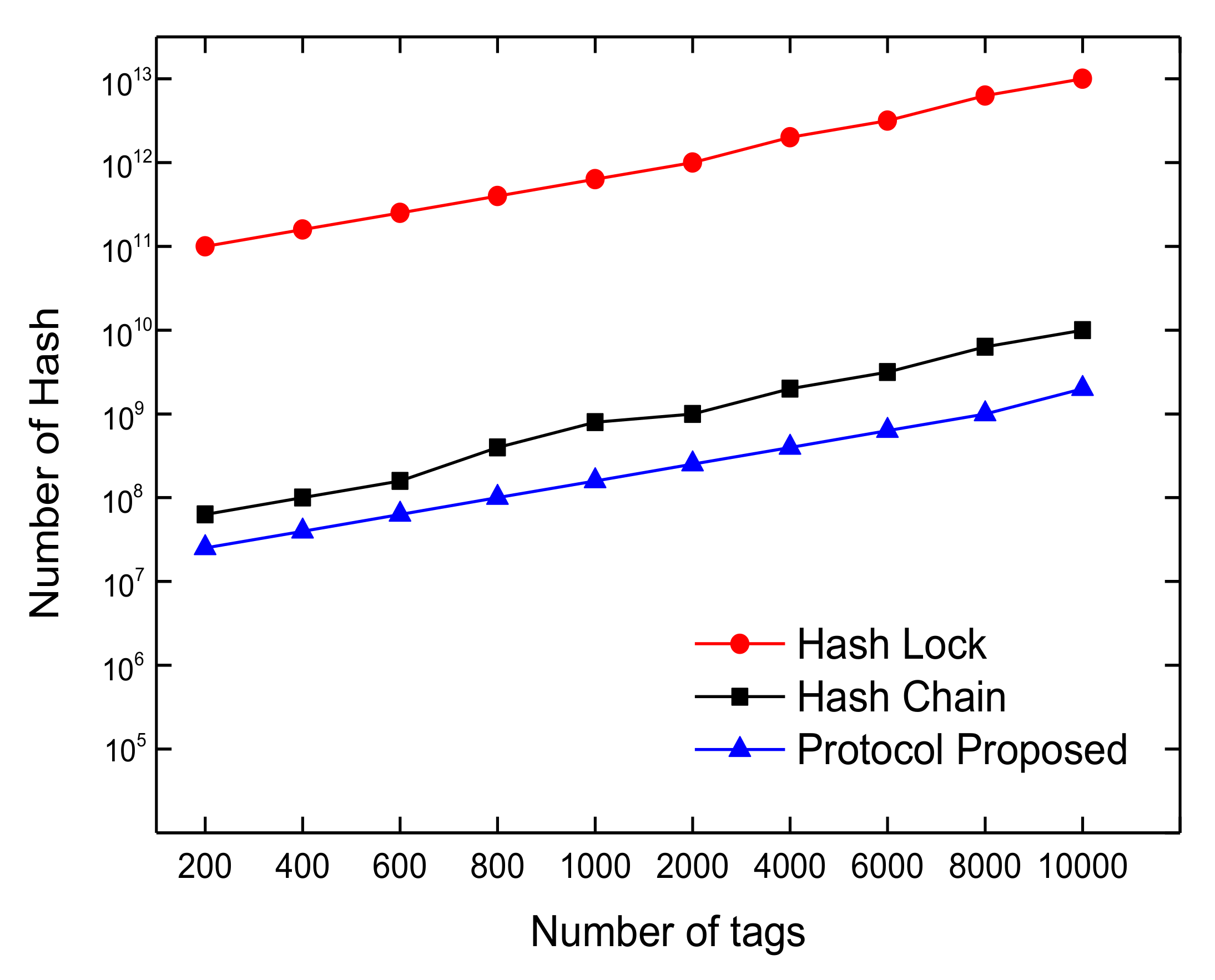
4.2. Scalability
4.3. Performance Efficiency
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sarma, S.A.; Weis, S.E.; Engels, D.W. RFID systems and security and privacy implications. In Proceedings of the 4th International Workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002; pp. 454–469. [Google Scholar] [CrossRef]
- Weis, S.A.; Sarma, S.E.; Rivest, R.L. Security and privacy aspects of low-cost radio frequency identification systems. In Proceedings of the First International Conference on Security in Pervasive Computing, Boppard, Germany, 12–14 March 2003; Lecture Notes in Computer Science. Springer: Berlin/Heidelberg, Germany, 2003; Volume 2802, pp. 201–212. [Google Scholar]
- Ohkubo, M.; Suzuki, K.; Kinoshta, S. Hash-chain based forward-secure privacy protection scheme for low-cost RFID. In Proceedings of the 2004 Symposium on Cryptography and Information Security, Sendai, Japan, 27–30 January 2004; pp. 719–724. [Google Scholar]
- Prosanta, G.; Tzonelih, H. A realistic lightweight authentication protocol preserving strong anonymity for securing RFID system. Comput. Secur. 2015, 55, 271–280. [Google Scholar]
- Tan, X.; Dong, M.; Wu, C.; Ota, K.; Wang, J.; Engels, D. An Energy-Efficient ECC Processor of UHF RFID Tag for Banknote Anti-Counterfeiting. IEEE Access 2017, 5, 3044–3054. [Google Scholar] [CrossRef]
- Sundaresan, S.; Doss, R.; Piramuthu, S.; Zhou, W. A secure search protocol for low cost passive RFID tags. Comput. Netw. 2017, 122, 70–82. [Google Scholar] [CrossRef]
- Yang, J.; Park, J.; Lee, H.; Ren, K.; Kim, K. Mutual authentication protocol for low-cost RFID. In Proceedings of the Workshop on RFID and Lightweight Cryptography, Graz, Austria, 14–15 July 2005; pp. 17–24. [Google Scholar]
- Cai, Q.; Zhan, Y.; Wang, Y. A minima list mutual authentication protocol for RFID system and BAN logic analysis. In Proceedings of the ISECS International Colloquium on Computing, Communication, Control, and Management, Guangzhou, China, 3–4 August 2008; pp. 449–453. [Google Scholar]
- Luo, Z.; Chan, T.; Li, J.S. A lightweight mutual authentication protocol for RFID networks. In Proceedings of the IEEE International Conference on e-Business Engineering (ICEBE’05), Beijing, China, 12–18 October 2005; pp. 620–625. [Google Scholar]
- Tan, C.C.; Sheng, B.; Li, Q. Secure and server-less RFID authentication and search protocols. IEEE Trans. Wirel. Commun. 2008, 7, 1400–1407. [Google Scholar] [CrossRef]
- Dass, P.; Om, H. A Secure Authentication Scheme for RFID Systems. Procedia Comput. Sci. 2016, 78, 100–106. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Islam, S.H.; Kumar, N.; Bhalla, V.K. Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localization services for smart city environment. Future Gener. Comput. Syst. 2017, 83, 629–637. [Google Scholar] [CrossRef]
- Cai, S.; Li, Y.; Li, T.; Deng, R. Attacks and improvements to an RFID mutual authentication protocol. In Proceedings of the 2nd ACM Conference on Wireless Network Security (WiSec’09), Zurich, Switzerland, 16–18 March 2009; pp. 51–58. [Google Scholar]
- Cho, J.-S.; Jeong, Y.-S.; Park, S. Consideration on the Brute-force attack cost and retrieval cost: A hash-based radio-frequency identification (RFID) tag mutual authentication protocol. Comput. Math. Appl. 2015, 69, 58–65. [Google Scholar] [CrossRef]
- Piramuthu, S. RFID mutual authentication protocols. Decis. Support Syst. 2011, 50, 387–393. [Google Scholar] [CrossRef]
- Safkhani, M.; Peris-Lopez, P.; Hernandez-Castro, J.C.; Bagheri, N. Cryptanalysis of the Cho et al. protocol: A hash-based RFID tag mutual authentication protocol. J. Comput. Appl. Math. 2014, 259, 571–577. [Google Scholar] [CrossRef]
- Seo, S.; Won, J.; Sultana, S.; Bertino, E. Effective Key Management in Dynamic Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 371–383. [Google Scholar]
- Levi, A.; Sarimurat, S. Utilizing hash graphs for key distribution for mobile and replaceable interconnected sensors in the IoT context. Ad Hoc Netw. 2017, 57, 3–18. [Google Scholar] [CrossRef]
- Castiglione, A.; Santis, A.; Masucci, B. Hierarchical and Shared Key Assignment. In Proceedings of the 2014 International Conference on Network-Based Information Systems, Salerno, Italy, 10–12 September 2014; pp. 263–270. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Li, Z.; Zhong, X.; Chen, X. A Lightweight Hash-Based Mutual Authentication Protocol for RFID. In Proceedings of the International Workshop on Management of Information, Processes and Cooperation, Hangzhou, China, 23 September 2016; pp. 87–98. [Google Scholar]
- Liu, Y.; Feng, S. Scalable Lightweight Authentication Protocol with Privacy Preservation. In Proceedings of the Tenth International Conference on Computational Intelligence and Security, Kunming, China, 15–16 November 2014; pp. 474–478. [Google Scholar]
- Jannati, H.; Bahrak, B. Security analysis of an RFID tag search protocol. Inf. Process. Lett. 2016, 116, 618–622. [Google Scholar] [CrossRef]
- Yang, L.; Wu, Q.; Bai, Y.; Zheng, H.; Lin, S. An improved hash-based RFID two-way security authentication protocol and application in remote education. J Intell. Fuzzy Syst. 2016, 31, 2713–2720. [Google Scholar] [CrossRef]
- Zhang, C.; Zhang, W.; Mu, H. A Mutual Authentication Security RFID Protocol Based on Time Stamp. In Proceedings of the 2015 First International Conference on Computational Intelligence Theory, Systems and Applications (CCITSA), Yilan, Taiwan, 10–12 December 2015; pp. 166–170. [Google Scholar]
- Yang, X. Research and Design on Authentication Protocol for RFID. Master Thesis, Xidian University, Shaanxi, China, 2014. [Google Scholar]
- Xiong, W.; Xue, K.; Hong, P. RFID cryptographic protocol based on two-dimensional region Hash chain. J. Univ. Sci. Technol. China 2011, 41, 594–598. [Google Scholar]
- Lei, H.; Song, H.; Tao, Z. An enhanced 2-pass optimistic anonymous RFID authentication protocol with forward security. In Proceedings of the 5th International Conference on Wireless Communications, Networking and Mobile Computing, Beijing, China, 24–26 September 2009; pp. 3692–3695. [Google Scholar]
| Notations | Description |
|---|---|
| Random number generated by reader | |
| Random number generated by tag | |
| ID | The identifier of the tag |
| The old secret value shared by the ith tag and the database | |
| The new secret value shared by the ith tag and the database | |
| The identifier of the reader | |
| The left part of the message M | |
| The right part of the message M | |
| Hash function | |
| XOR operation | |
| Connection operator |
| Scheme | [1] | [2] | [3] | [26] | [27] | [28] | Proposed Scheme |
|---|---|---|---|---|---|---|---|
| Data privacy | √ | √ | √ | √ | × | √ | √ |
| Replay attack | × | × | × | √ | √ | √ | √ |
| Fake attack | × | × | × | × | √ | √ | √ |
| Position tracking | × | × | √ | × | × | √ | √ |
| Asynchronous attack | √ | √ | √ | × | × | × | √ |
| Scheme | Reader | Server | Tag | M | C |
|---|---|---|---|---|---|
| [1] | N/A | N/A | 1H | 4 | √ |
| [2] | 2mH | N/A | 1H | 3 | √ |
| [3] | N/A | 2mH | 2H | 2 | √ |
| [26] | 1R | (m + 1)H | 3H, 1R | 3 | √ |
| [27] | 1R | 5H, 1R | 3H | 3 | √ |
| [28] | 1R | (m + 1)H | 2H, 1R | 3 | √ |
| This paper | 1R | 3H | 2H, 1R | 3 | √ |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, B.; Yang, B.; Su, X. An Improved Two-Way Security Authentication Protocol for RFID System. Information 2018, 9, 86. https://doi.org/10.3390/info9040086
Liu B, Yang B, Su X. An Improved Two-Way Security Authentication Protocol for RFID System. Information. 2018; 9(4):86. https://doi.org/10.3390/info9040086
Chicago/Turabian StyleLiu, Baolong, Bing Yang, and Xiaohao Su. 2018. "An Improved Two-Way Security Authentication Protocol for RFID System" Information 9, no. 4: 86. https://doi.org/10.3390/info9040086
APA StyleLiu, B., Yang, B., & Su, X. (2018). An Improved Two-Way Security Authentication Protocol for RFID System. Information, 9(4), 86. https://doi.org/10.3390/info9040086