2. The Related Grouping-Proof Protocols for RFID Systems
The first grouping-proof protocol only involves two tags and it is proposed by A. Juels [
2], which is called the Yoking-proofs protocol for RFID Tags. “Yoking” means the co-existence of two tags. The protocol gives a proof that a pair of RFID tags has been scanned simultaneously in the range of a reader. It utilizes a timeout mechanism to guarantee the validity of co-existence proofs. The protocol assumes that tags have ability to perform basic cryptographic operations such as Hash operation,
functions and pseudorandom number generator. The Yoking-proofs protocol involves two tags
and
. These tags are identified by their identifiers
and
respectively. Their secret keys are
and
. The minimalist version of the “Yoking-proofs” protocol is described as follows.
(1) The reader sends the message to .
(2) generates a random nouce and sends the message to the reader.
(3) The reader sends to .
(4) uses function and its secret key to sign . It gets . Then it generates a random nouce and sends to the reader. The reader sends to .
(5) signs with its secret key and calculates and sends to the reader.
(6) The reader generates as the evidence and sends to the verifier.
(7) The verifier judges the validity of co-existence proof . If is generated within a reasonable and pre-defined time period it is valid. Otherwise, the protocol will be terminated and the generated proof is viewed as an invalid one.
As described above, the identifiers of the tags
and
is transferred with plaintext. So the Yoking-proofs protocol is not anonymous. J. Saito and K. Sakurai [
6] analyzed the Yoking proofs protocol and they indicated the yoking-proofs protocol is not immune to replay attack because a malicious attacker can separately gather proof elements
and
within different proof sessions and combine them later to form a counterfeit proof. This vulnerability is caused by the independent generating process of
and
in the Yoking-proofs protocol [
5]. Mike Burmester et al. [
3] also analyzed the Yoking-proofs protocol and they pointed out other several weaknesses. The first is the Yoking-proofs protocol does not check each other’s computation result so that some unrelated tags can participate in a joking session. Sometimes, some proofs generated by the reader are meaningless. However, these proofs are still transferred to the verifier. The grouping-proof failure is finally detected by the verifier. This will result in a late response time. Another weakness is that the proof
cannot state two tags are scanned simultaneously, especially in the presence of a rogue reader. A corrupted tag can impersonate a legal tag (
or
) to generate and replay
.
Huang and Ku [
7] proposed an online grouping-proof protocol for Class-1 Gen-2 standard tags. Their protocol is used to check the accuracy of the association of drug and patient information so as to enhance medication safety. The protocol only uses a cyclic redundancy check (CRC) function and a pseudorandom number generator (PRNG). P. Peris-Lopez et al. [
4] analyzed the protocol. They found that an attacker can exploit the linearity property of CRC function and the tag’s EPC transferred by plaintext to get the private information related to the objective tag. Then it can impersonate this tag in the future grouping-proof. So the protocol proposed by Huang and Ku cannot resist forgery attack. Otherwise, P. Peris-Lopez et al., pointed out that the protocol proposed by Huang H-H et al., cannot resist de-synchronization attack and replay attack.
HY Chien et al. [
8] proposed two grouping-proof protocols conforming to the EPC Class-1 Gen-2 standard to enhance medication safety for two different scenarios: online and offline. For these protocols, the operations on the tags are very simple, which are limited to 16-bit PRNG and bitwise XOR operation. Peris-Lopez et al. [
4] analyzed the online protocol. They found the protocol cannot resist forgery attack and subset replay attack. If an adversary detects that the random numbers generated by the tag and the reader are equal, he can use XOR operation to generate a fixed session message unrelated with the random numbers. Later he can use the message to impersonate a target tag to generate some false grouping proofs. Otherwise, the protocol assumed the reader is trusted and the tags have to store the secret keys of the readers so as to consume more storage resource of the tags.
Peris-Lopez et al., proposed an RFID-based grouping-proof scheme to enhance inpatient medication safety [
9]. They use some low-cost RFID tags which can only perform PRNG function and bitwise XOR operation. Their scheme automatically finishes the matching operation between the unit-dose packages and the inpatient to avoid human error. In addition, digital evidence generated by their scheme can be used for medication tracking and auditing. Their scheme assumes that a physician utilizes a Personal Digital Assistant (PDA) equipped with an RFID reader to issue prescriptions and a nurse utilizes a PDA with an RFID reader to verify drugs for inpatients. Every inpatient wears a wristband with an RFID tag. Every unit-dose drug package is labeled with an RFID tag. After these tags are justified to be the same group, the unit-dose drug package can be dispatched to the inpatient. Yen et al. [
10] found that the digital evidence generated by the scheme is only signed by the nurse, not including the inpatient’s signature. If a medication dispute occurs, the hospital can re-generate counterfeit evidence without inpatient’s awareness to cover up their medication errors. In order to overcome the shortcoming described above, Yi-Chung Yen et al. [
10] proposed an online solution and an offline solution to secure medication administration, which are suitable to areas in a hospital environment where wireless communication is available or not. Their protocol involves four entities: the backend server, nurse’s PDA, the inpatient’s wristband with a tag and unit-dose drug packages. Nurse’s PDA and inpatient’s tag have the computing ability to complete digital signatures. Each unit-dose package is attached with a low-cost tag which only has a PRNG function. By analyzing, we found that for each grouping-proof protocol proposed by Yi-Chung Yen et al., if the inpatient and unit-dose tags receive the challenge
from the nurse’s PDA many times, the inpatient will return the same response messages
, and the unit-dose tags will return the same messages
and
to the nurse’s PDA. An adversary can locate the inpatient and his/her unit-dose package by repeatedly sending the same message
to inpatients and unit-dose packages. Therefore, the adversary can acquire the relationship of the inpatient with unit-dose package and he can find which unit-dose packages belong to the same group. So the grouping-proof protocol cannot resist tracing attack and it is easy to leak the privacy information of the inpatient and his/her unit-dose packages. The keys of the inpatient wristband’s tag and the unit-dose package’s tags are fixed and the protocol cannot provide forward security.
Hong Liu et al. [
11] found that some previous protocols only involves the single reader and the single tag group, which limits the diverse application of RFID systems. Then they proposed a grouping-proof protocol which adopts the distributed authentication mode with independent subgrouping proofs. They claimed that their protocol can resist major attacks such as replay, forgery, tracking and denial of proof. Later, Jian Shen et al. [
12] proposed an enhanced grouping-proof protocol for multiple readers and tag groups, which involves the mutual authentication and grouping proof between multiple readers and multiple tag groups. They claimed that their protocol can resist information leakage and replay attack. However, we found that their protocol use the plaintext of the tag’s identifier
, the tag group’s identifier
and the reader’s identifier
to communicate. Moreover, these identifiers are fixed during the period of grouping proof. So their protocol seriously exposes the privacy information of the RFID system and it cannot resist tracing attack. Their protocol involves multiple readers. However, it does not describe how to authorize a reader to finish grouping proof.
Daisuke Moriyama [
13] analyzed some previous grouping-proof protocols and found that their communication complexity increase rapidly with the number of the tags. Then he proposed a provably secure two-round grouping-proof protocol. His protocol is a parallel protocol and it only uses two-round communication so that the number of the sessions for the protocol is independent of the number of the tags. However, his protocol can only resist impersonation attack. Otherwise, the transferred sessions include the redundant information, e.g., the random nonce
. Moreover, the verifier cannot judge the validness of the grouping-proof evidences because the timestamp is generated by the reader.
Ping Huang and Haibing Mu [
14] proposed a high-security RFID grouping-proof protocol. Their protocol introduces a new method of the key distribution by means of distributing the points on straight lines to different entities. The protocol attempts to complete two important targets for RFID grouping proof: the dependency between tags and the scalability of the RFID system. In order to reduce computing cost, the protocol does not use the Hash function to encrypt the sessions. However, the protocol makes a big mistake, which is that a tag updates its secret key twice during the authentication process. After a tag completes the first updating of its secret key
, the reader uses the previous
to generate
and send the result to the tag, which will make the tag not to authenticate the reader because of their different
. Hence DoS attack occurs. So the protocol cannot resist de-synchronization attack.
Jian Shen et al. [
15] proposed a practical grouping authentication protocol. The protocol is divided into four phases: initialization, tag acquisition, main authentication and verification. The protocol only uses some simple operations, not Hash function. It uses the serial signature method to generate the grouping proof. So it costs more time to finish the entire grouping proof. Otherwise, the protocol seriously leaks the privacy of the RFID system. For the tag acquisition phase, an adversary can deduce the group’s key
and the tag’s sequence number
by eavesdropping the sessions between reader and tags. An adversary can eavesdrop the sessions
and
from the reader, the sessions
,
and
. from tags. Then an adversary can deduce
from
and
. Secondly, he can deduce
from
. Because
is known, he can get the group’s key
. Finally he easily deduces the tag’s sequence number
from
, where
is known and it is from the ith tag. Moreover, the protocol cannot provide forward security because the secret information of the RFID system is not updated after each authentication.
Bianqing Yuan and Jiqiang Liu [
16] proposed a universally composable secure grouping-proof protocol for RFID systems with anonymity, privacy preserving, mutual authorized access and anti-replay attack. In general, readers and tags are assumed to be some untrusted entities. They can be impersonated by an adversary. So a reader should not know more information about tags. However, the protocol proposed by Bianqing Yuan and Jiqiang Liu sends the identifier of the tag group to the reader. Thence the reader can know which group it searches. Otherwise, their protocol cannot state how to authenticate between a verifier and readers.
Hongyan Kang [
17] analyzed the grouping-proof protocol proposed by L. Batina et al. [
18] and he found the protocol proposed by L. Batina et al., cannot resist tracking attack and impersonation attack for tags. Then he proposed an improved grouping-proof protocol. However, his protocol still uses ECC mechanism and the computation of EC points means a high overload for low-cost tags. After the initialization of the protocol, its secret information is fixed and it cannot provide forward security. Otherwise, the protocol is a serial protocol and it can only complete grouping-proof for two tags. So it is not suitable for grouping proof of multiple tags.
As analyzed above, many grouping-proof protocols only involve a reader and a tag group, not multiple readers and multiple tag groups. The verifier does not know whether the reader is trusted during grouping proof. Many grouping-proof protocols use the serial approach to query each tag and to generate the grouping-proof evidence, which results in the low efficiency of grouping proof. When there exist many tag groups near the reader the verifier does not sense their co-existence. Especially, some grouping-proof protocols are vulnerable to information leakage and some common attacks.
4. The Grouping-Proof Protocol Based on Parallel Mode and DHCP Mechanism
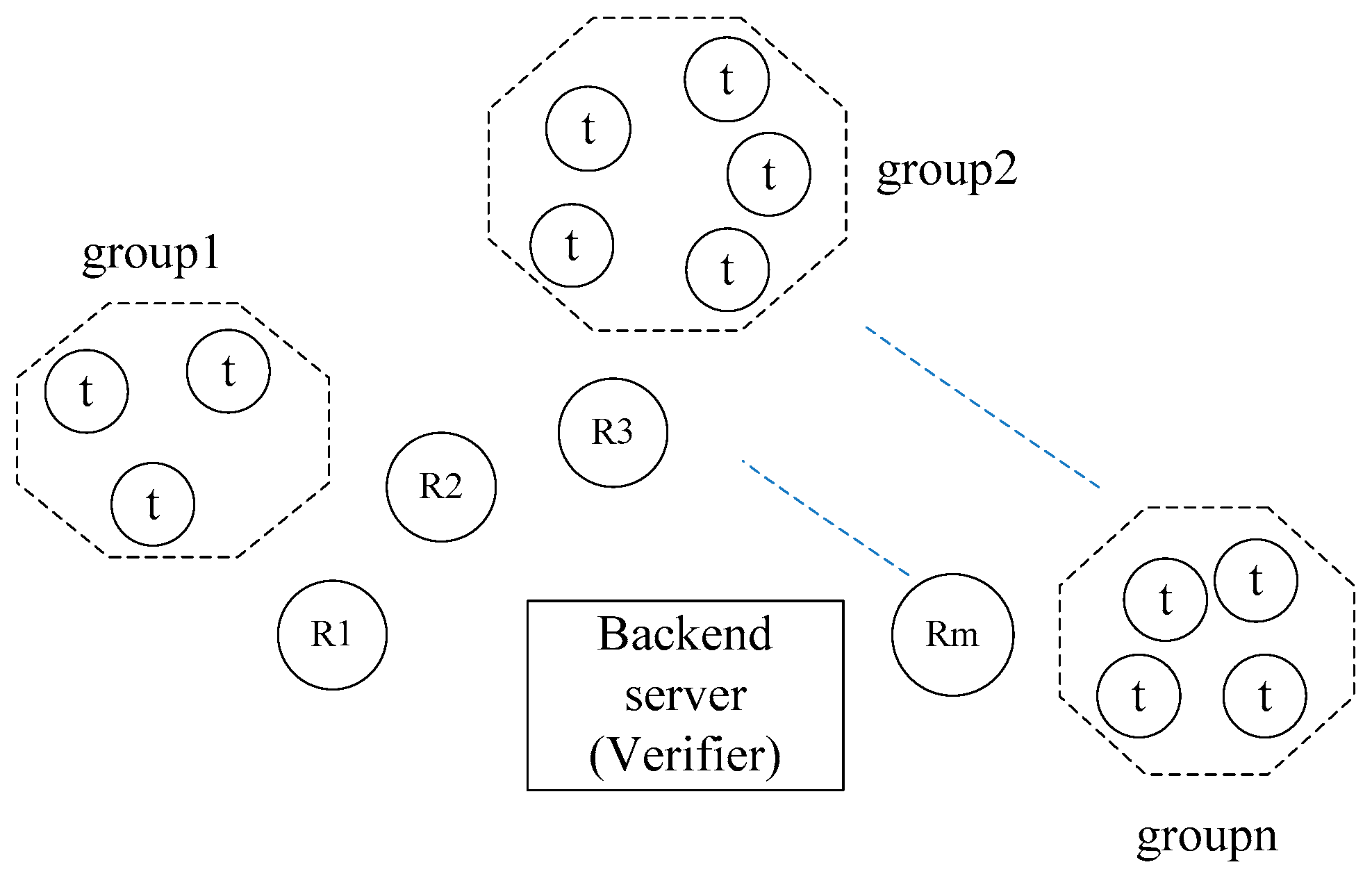
For an RFID System under the grouping proof mode, there are four kinds of entities: verifier, reader, tag and adversary. We assume that there are multiple readers and multiple tag groups for an RFID system. Therefore readers may be represented by . Tags are also represented by , where represents a tag which is the jth tag of the ith group. It is usually assumed that the verifier is a unique trusted entity and the readers are some untrusted entities. The communication channels between verifier and readers are secure and the communication channels between readers and tags are not secure. Before a reader is responsible for grouping proof, it must be authenticated and authorized by the verifier. It is also assumed that an adversary is probabilistic polynomial time algorithm and he can control all communication channels between readers and tags. He can eavesdrop, intercept, tamper, counterfeit and replay each session message transferred between reader and tag. His main attack goal is to counterfeit a grouping-proof evidence which is verified to be valid by the verifier or to obtain the private information of the RFID system, such as the secret keys and identifiers of tags.
For an RFID system under the grouping-proof model, there may be many readers and tag’s groups to be queried simultaneously. They almost give their responses at the same time. Which is chosen? DHCP gives a good approach. Now we utilize DHCP and broadcast mechanism from Internet to propose a novel grouping-proof protocol. Our protocol works under parallel mode and it is independent of reading order to tags. So it is very efficient. It concerns multiple readers and multiple tag groups. Each reader stores its identifier
and its secret key
. Each tag stores its secret key
and its group identifier
. The verifier stores the secret key and identifier
of each reader and the secret information
of each tag. L is the length of the secret information. The symbols used in our protocol are shown in
Table 1.
For our protocol, two modes are involved: active mode and passive mode. Under active mode, the verifier knows the identifier of the tag group which it wants to search. When the protocol begins, the verifier sends the identifier of the tag group to the authorized reader. The reader collects the grouping-proof evidence and returns the evidence to the verifier. Under passive mode, the verifier does not know which tag group it wants to search. There may be many tag groups at this time. When the protocol begins, the authorized reader broadcasts the challenge to all tag groups. After tags receive the challenge from the reader, they return their randomized group identifiers to the reader. Then the reader transfers these group identifiers to the verifier. The verifier chooses a tag group by means of DHCP rule and returns the group identifier to the reader. The reader broadcasts the group identifier to all tags and activates the chosen tag group. It is obvious that the protocol under active mode is simpler than under passive mode. So we only describe the grouping-proof protocol under passive mode.
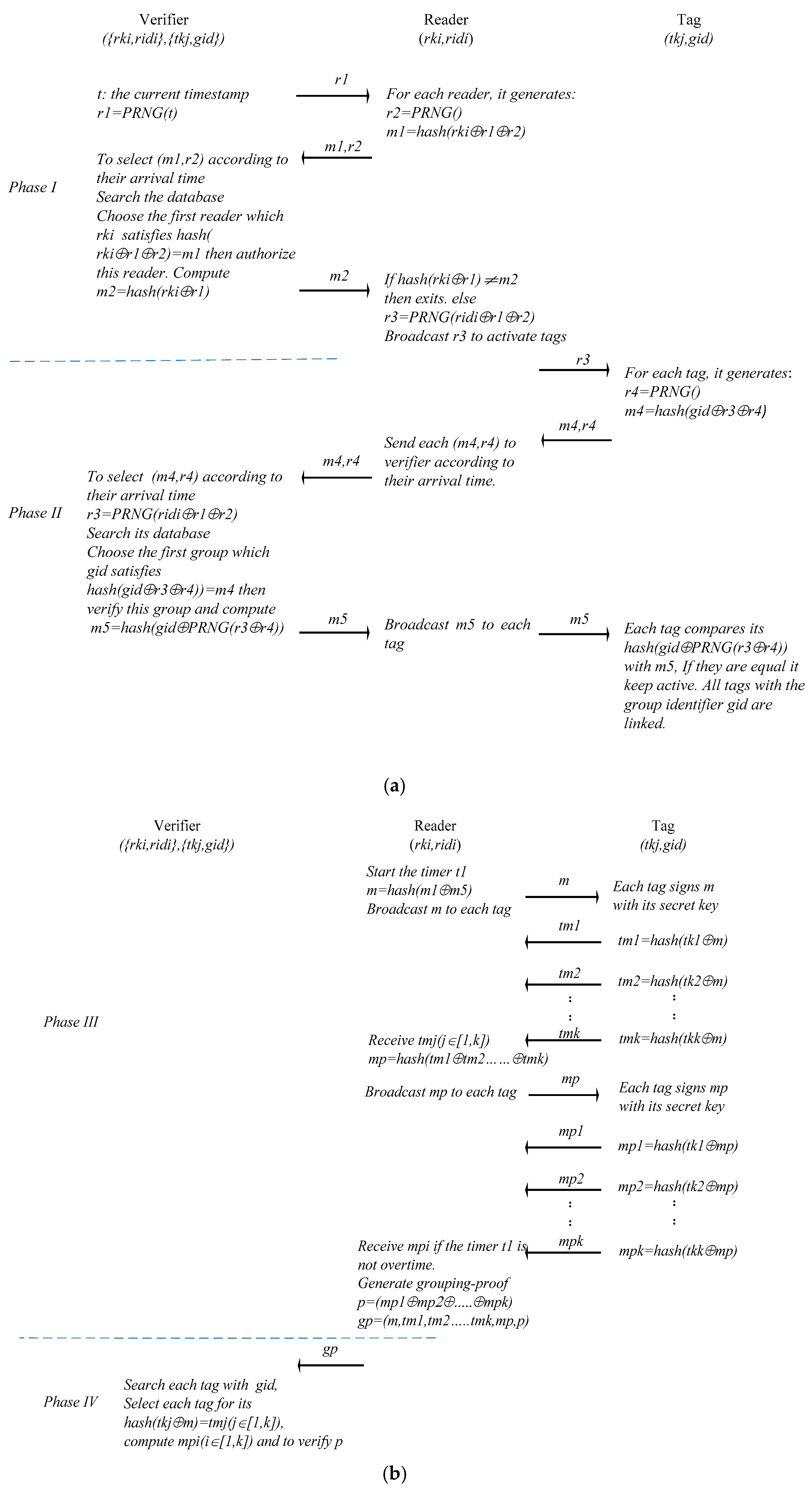
The protocol includes four phases: to authorize a reader, to choose a tag group, to generate a grouping-proof evidence and to verify the grouping-proof evidence, as shown in
Figure 2.
Phase I: to authorize a reader
(1.1) The verifier uses its current timestamp to generate a pseudorandom number . Then it broadcasts to all readers.
(1.2) After a reader receives , it generates a pseudorandom number and .
(1.3) each reader sends its to the verifier respectively.
(1.4) The verifier chooses a reader according to the arrival time of each . Then the verifier searches its database and finds the reader with which holds. The verifier authenticates the reader. It computes and broadcasts to all readers. Each reader receives and uses its to judge whether equals . If a reader finds that they are equal, it is authorized for the grouping proof.
(1.5) The authorized reader computes and sends to each tag.
Phase II: to choose a tag group
(2.1) After each tag receives , it generates a pseudorandom number and computes . Then they send to the reader respectively.
(2.2) The reader receives each and transfers them to the verifier according to their arrival time.
(2.3) The verifier chooses according to their arrival time and searches its database to find which holds. Then the verifier computes and sends to the reader.
(2.4) The reader receives and broadcasts to all tags.
(2.5) After each tag receives , it uses its to compute . If the result equals , it keeps active. Or it becomes silent. The tags with the same are linked.
Phase III: to generate a grouping-proof evidence
(3.1) The reader starts its timer and computes . It broadcasts to all objective tags.
(3.2) Each objective tag signs with its secret key respectively and sends the signed result to the reader. For the ith tag (), it signs with its secret key tki, gets and sends to the reader.
(3.3) After the reader receives each , it computes , . Then the reader broadcasts to all objective tags.
(3.5) After each objective tag receives , it signs with its secret key respectively and sends the signed result to the reader. For the ith tag, it signs , gets and sends to the reader.
(3.6) The reader receives each until the timer is overtime. Then it computes , . The reader generates the grouping-proof evidence and sends to the verifier.
Phase IV: to verify the grouping-proof evidence
The verifier receives . If the timer is not overtime, the verifier searches its database and gets which holds. Then it uses and to compute . Finally it can verify the validity of .
5. The Efficient and Secure Analysis of the Proposed Protocol
Our proposed protocol works under parallel mode and it is independent of reading order to tags. Each tag signs m and mp almost simultaneously, and return the response to the reader. So our protocol is very efficient. When tags sign, the collision probably happens. However, we assume that the collision among tags is avoided by the low-level protocol. Multi-level timer is taken by the verifier and the readers to control the proof time. For the current grouping-proof protocols, the reader collects the grouping-proof evidence and sends it to the verifier, whether the evidence is valid or not. The verifier finally judges whether it is overtime and the evidence is valid. For our protocol, the reader can judge whether it is overtime and it can find the invalid evidence in time. So our protocol is very efficient. For the computation and storage requirement for tag, our protocol is compared with other protocols, which is shown in
Table 2. It is obvious that our protocol does not require more computation resources than other protocols.
For the security of an RFID system under the grouping-proof mode, an adversary aims at counterfeiting a valid grouping-proof evidence or revealing the secret information of the RFID system. In order to resist the attacks described above, our protocol uses Hash function to encrypt all sessions transferred among verifier, readers and tags. Because Hash function is a one-way function, an adversary cannot reveal any secret information from the eavesdropped sessions. Therefore the confidentiality and privacy of the RFID system are protected. For different grouping-proof process, all sessions are randomized by different random numbers and the freshness of the sessions is ensured. An adversary cannot trace a tag or a tag group. As an untrusted party, the reader can receive the sessions from the verifier and tags. However, all sessions which the reader receives are encrypted by Hash function and it cannot acquire any secret information about the verifier and tags. So our proposed protocol can ensure the privacy and confidentiality of the RFID system, and it can prevent eavesdropping attack, tracing attack, replay attack and impersonation attack. Now we analyze the security of the proposed protocol as follows.
♦ Eavesdropping: During the grouping-proof period, all session messages transferred between tags and readers are encrypted by Hash function. None of the plaintext messages about the secrecy of the RFID system is transferred. An adversary can intercept all sessions between tags and readers. However, he cannot get any useful information about the tag and the tag group from the intercepted data. Eavesdropping to the communication channel between tags and readers is invalid. The privacy of the RFID system is preserved.
♦ Tracing attack: If a tag or a tag group is traced their privacy may be encroached upon. To resist this type of attack, a pseudorandom number generator is used to ensure that each session between tags and readers is variable so as to make attackers not to distinguish which tag or group sends their received information. For our protocol, an adversary can intercept and in phase II. Then he can repeat to send to tags many times. After the tag receives it will generate a different pseudorandom number to randomize its group identifier . The randomized result is hashed to generate . It is obvious that is different for each different . Our protocol utilizes the parallel mode and all tags send their responses almost at the same time as soon as they receive the challenge from the reader. So it is very difficult for an adversary to distinguish and trace a tag.
♦ Replay attack: This type of attack means that an adversary can compromise an RFID system by replaying sessions intercepted by eavesdropping. In order to prevent replay attack, some pseudorandom number generators and timestamp are utilized. During the grouping-proof period, some pseudorandom numbers , , and are separately generated by the verifier, the reader and the tags. and are dependent on the current time of the verifier. These pseudorandom numbers are utilized to randomize the sessions between tags and readers. The current time of the verifier is not transferred among the system’s components and it is not possible for an adversary to acquire or predict it. If an attacker replays the intercepted session messages in the late grouping-proof period, these messages have not any meanings because a new grouping-proof process uses some new timestamp and pseudorandom numbers.
♦ De-synchronization: In order to reduce the computation and storage load on tags, our protocol does not update the tag’s secrecy, which may result in potential safety hazard to forward security. However, our protocol only reserves the current secrecy of each tag and it saves the time for updating the secrecy. So our protocol can resists de-synchronization attack. It completes the compromise between its secure level and its resource consumption.
♦ Impersonation: The protocol ensures user’s anonymity and privacy by using Hash function to encrypt all sessions transferred between readers and tags. Because Hash function is a one-way function an attacker cannot get the secrecy and identity information of tags or readers, so it cannot impersonate a valid tag or reader to cheat the RFID system.
♦ Counterfeiting attack: Because the communication channel between the verifier and the reader is assumed to be secure, an adversary cannot acquire any secrecy of the RFID system from this channel. Although the communication channel between tags and reader is assumed to be insecure, all sessions transferred between tags and readers are encrypted by Hash function. An adversary cannot also use his intercepted sessions to acquire any secrecy of the RFID system. Therefore he cannot counterfeit any valid grouping-proof. Otherwise, an adversary can abstract some parts of the evidences from the previous grouping-proof period and combine them to generate some new evidences to cheat the RFID system. However, these evidences are dependent on the timestamp of the verifier and different pseudorandom numbers. So it is impossible for the adversary to use these new combined evidences to cheat the RFID system. Counterfeiting attack is resisted by our protocol.
The comparison of our proposed protocol with some typical grouping-proof protocols is shown as
Table 3.