Standard Compliant Hazard and Threat Analysis for the Automotive Domain
Abstract
:1. Introduction
1.1. Requirements Analysis
1.2. ISO 26262
1.3. The ISO 27000 Series of Standards
1.4. The ISO 27001 Standard
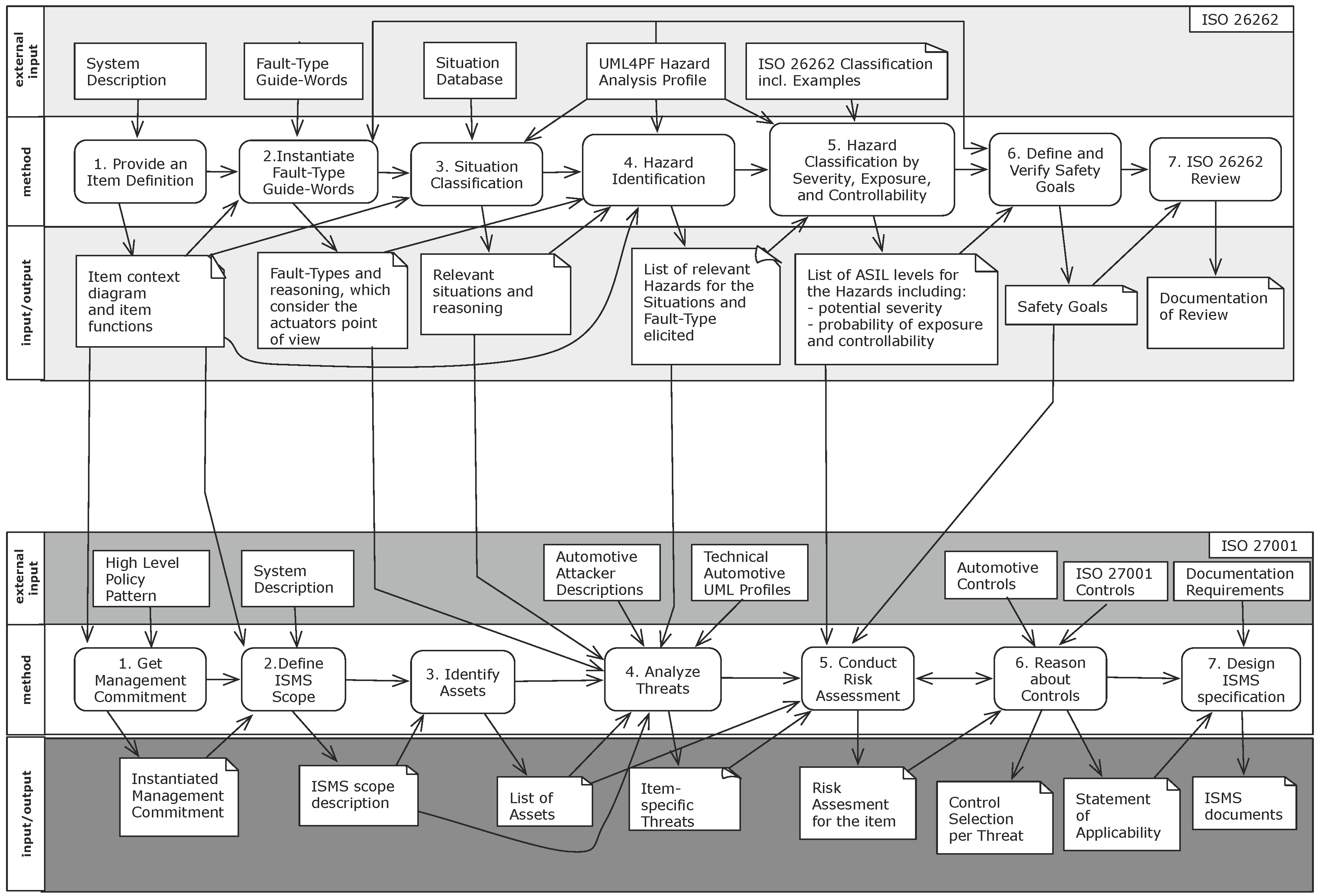
2. Methodology
2.1. Hazard Analysis and Risk Management Compliant to ISO 26262
2.1.1. Safety-Step 1: Provide an Item Definition
2.1.2. Safety-Step 2: Instantiate Fault-Type Guide-Words
2.1.3. Safety-Step 3: Situation Classification
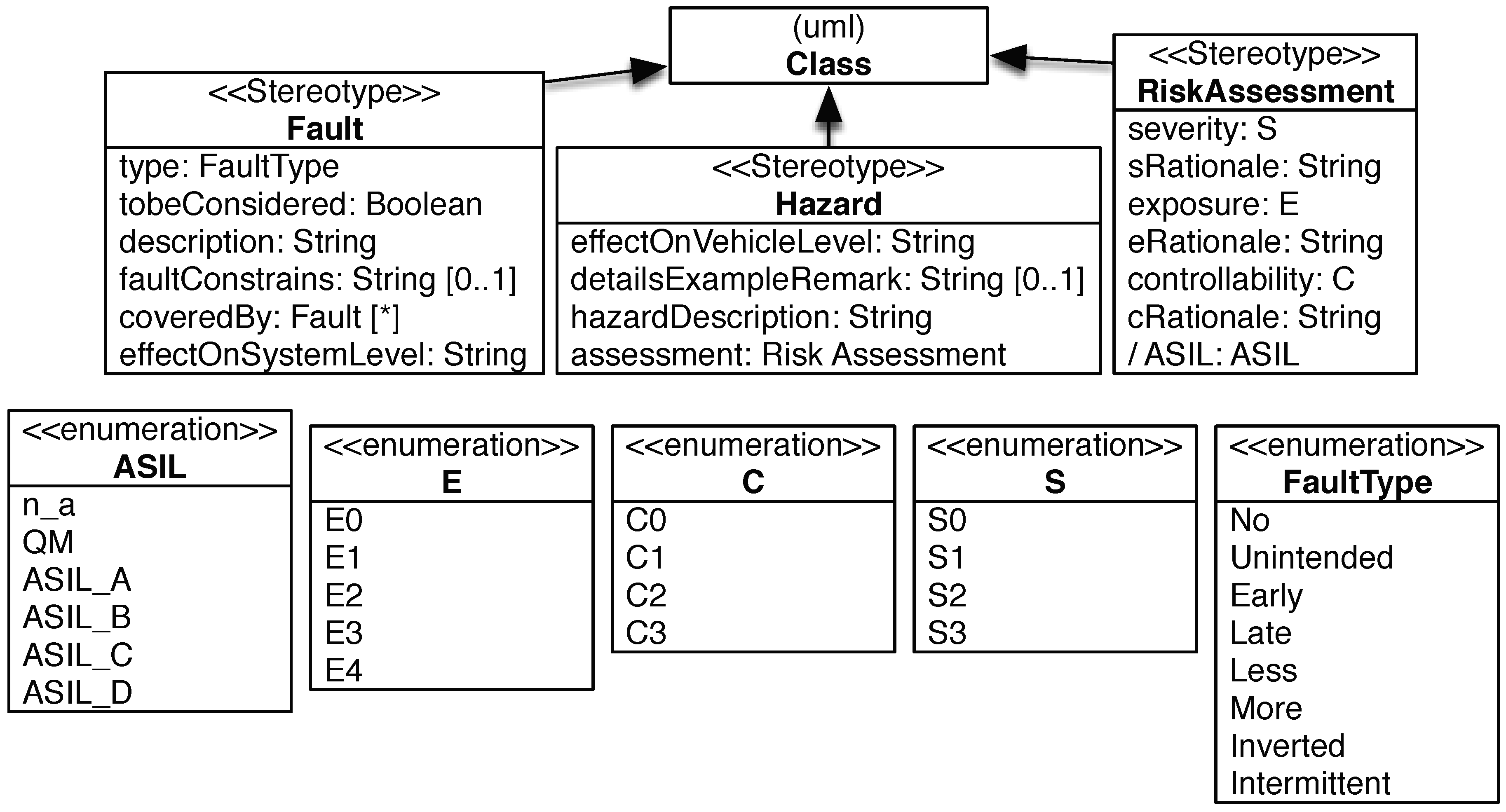
2.1.4. Safety-Step 4: Hazard Identification
2.1.5. Safety-Step 5: Hazard Classification by Severity, Exposure, and Controllability
- Estimate the potential severity and provide a rationale. ISO 26262 classifies the potential severity with the classes S0 (no injuries), S1 (light and moderate injuries), S2 (severe and life-threatening injuries, survival probable), and S3 (life-threatening injuries, fatal injuries).
- Estimate the probability of exposure and provide a rationale. ISO 26262 classifies the exposure with the classes E0 (incredible, e.g., earthquake), E1 (very low probability, e.g., vehicle being towed), E2 (low probability, e.g., snow and ice on road), E3 (medium probability, e.g., heavy traffic with stop and go), E4 (high probability, e.g., highway).
- Estimate the controllability and provide a rationale. ISO 26262 classifies the controllability with the classes C0 (controllable in general, e.g., maintain intended driving path in case of unexpected radio volume increase), C1 (simply controllable, e.g., brake to slow down/stop the vehicle in case of blocked steering column when starting the vehicle), C2 (normally controllable, e.g., maintain intended driving path in case of failure of ABS during emergency braking, C3 (difficult to control or uncontrollable, e.g., stay in lane in case of failure of ABS when braking on low friction road surface while executing a turn).
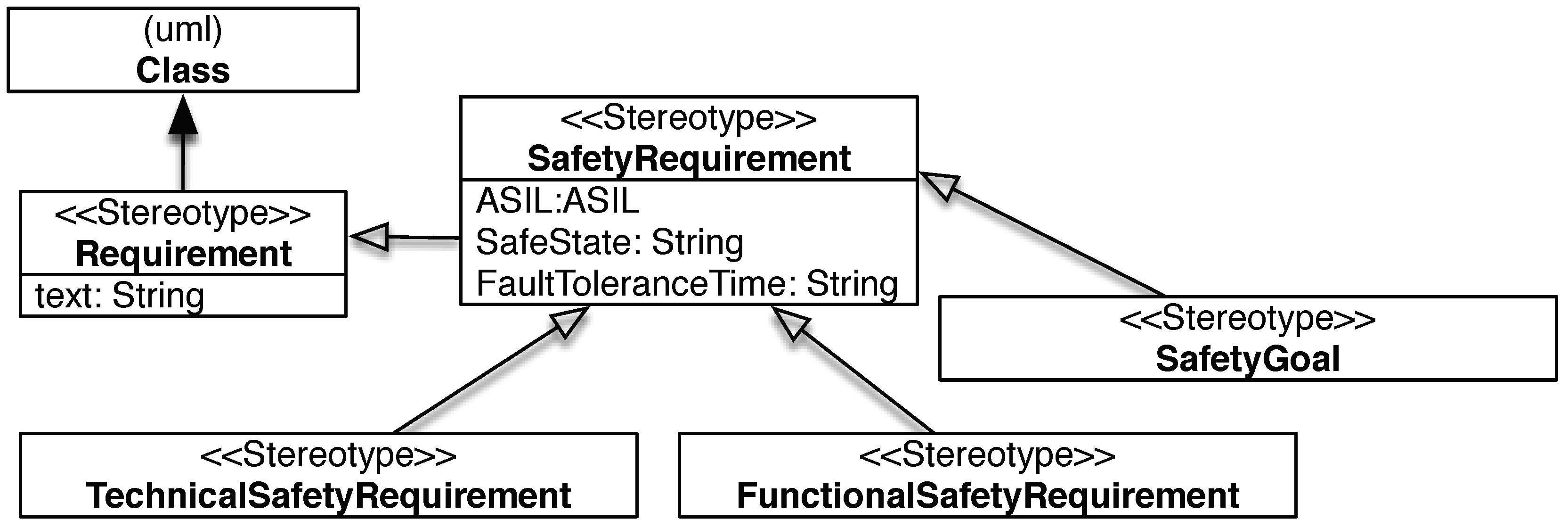
2.1.6. Safety-Step 6: Define and Verify Safety Goals
2.1.7. Safety-Step 7: ISO 26262 Review
2.2. Threat Analysis and Risk Management Compliant to ISO 27001
2.2.1. Security-Step 1: Get Management Commitment
2.2.2. Security-Step 2: Define ISMS Scope
2.2.3. Security-Step 3: Identify Assets
2.2.4. Security-Step 4: Analyze Threats
2.2.5. Security-Step 5: Conduct Risk Assessment
2.2.6. Security-Step 6: Reason about Controls
2.2.7. Security-Step 7: Design ISMS Specification
3. Foundations for Automotive Threat Analysis
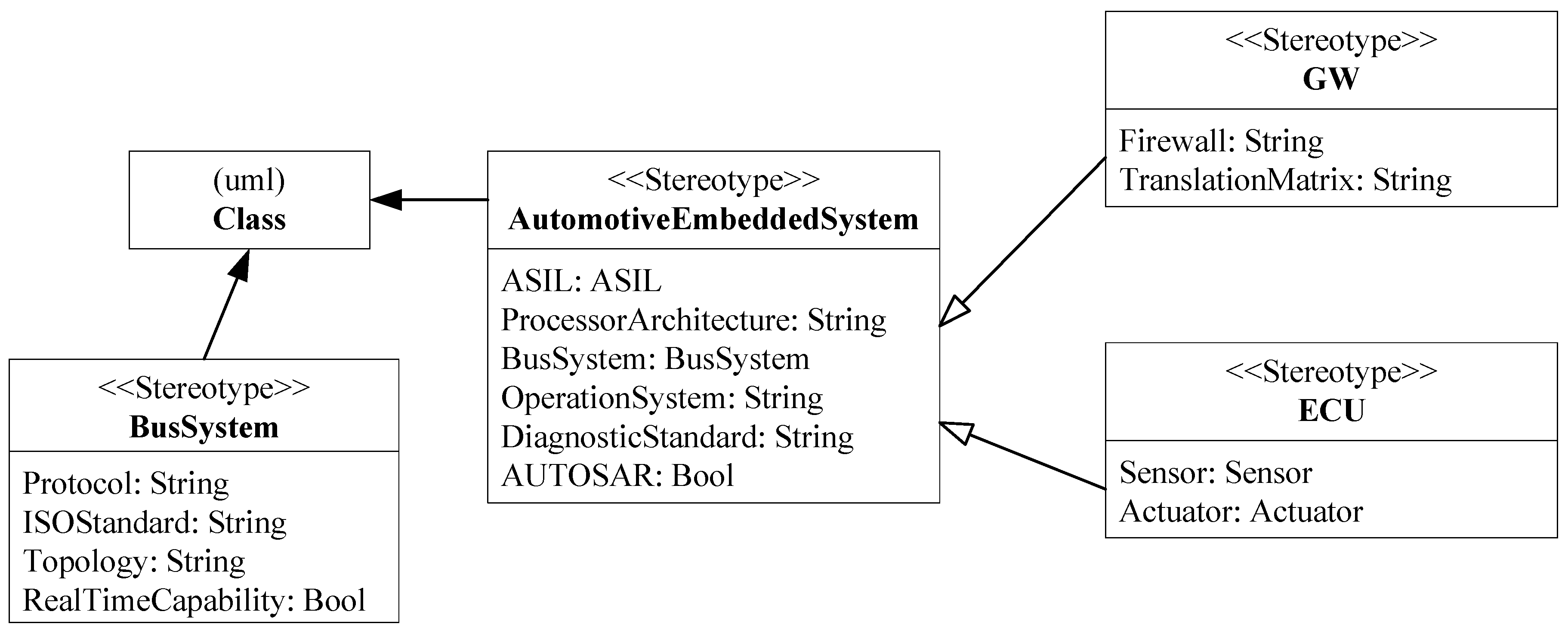
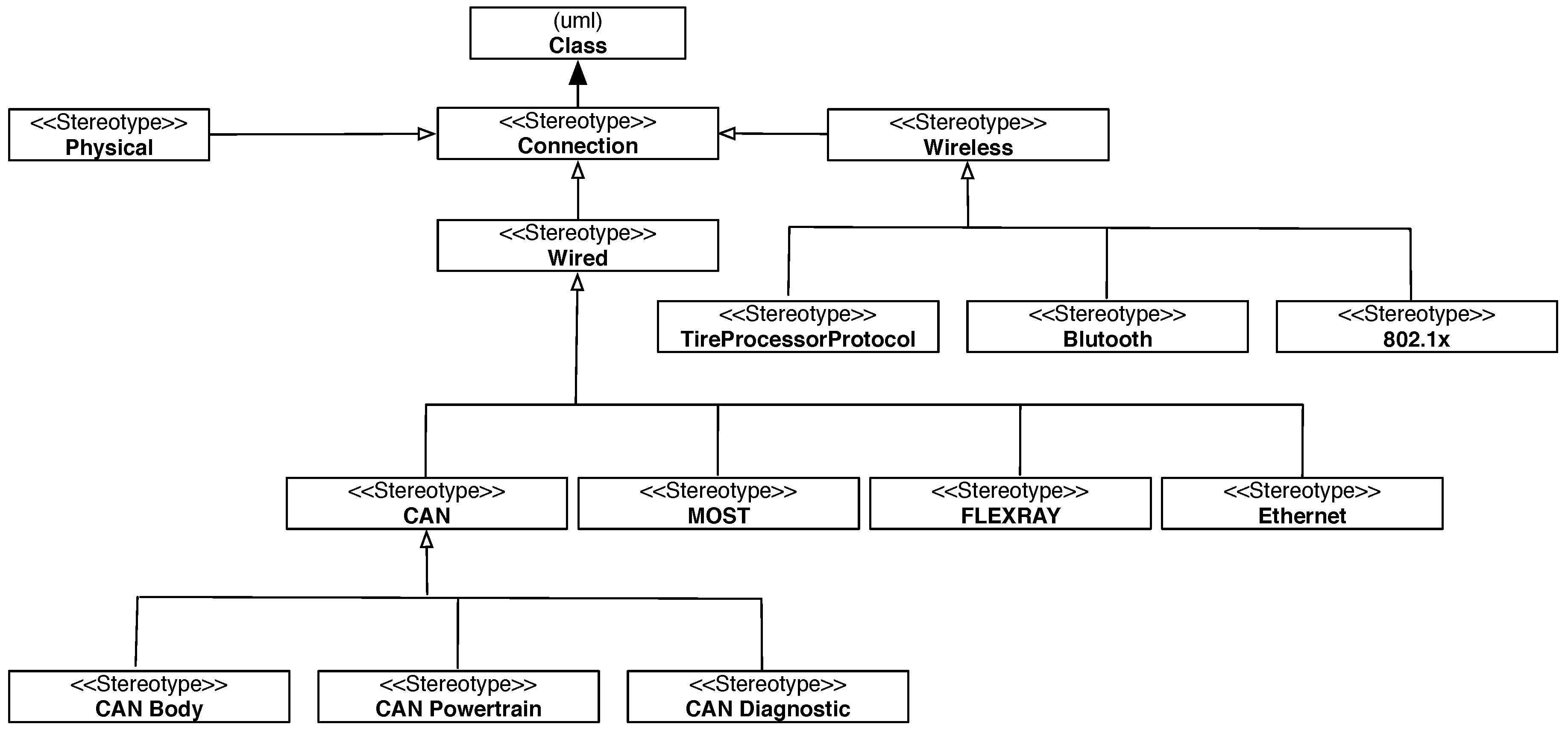
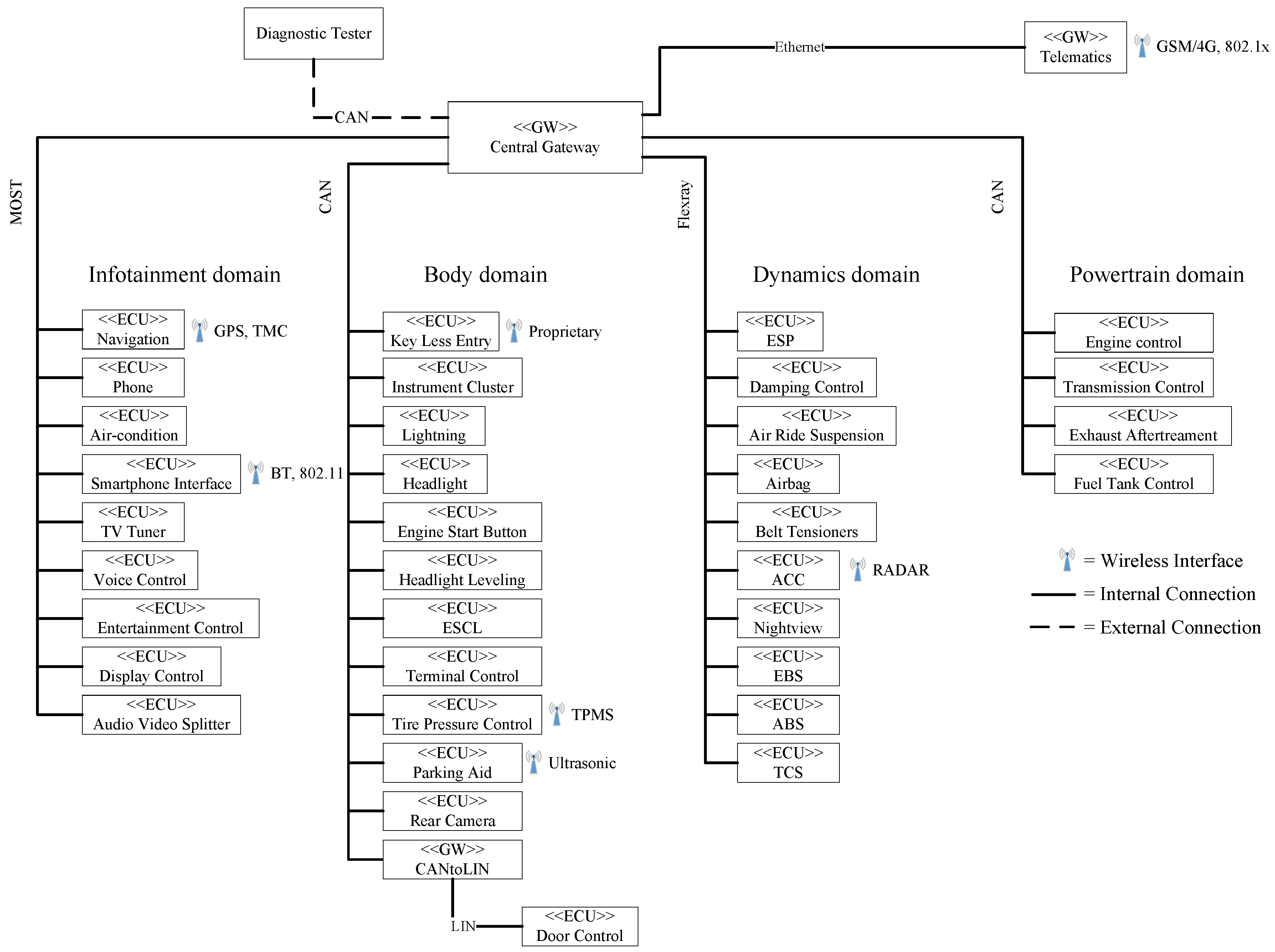
3.1. Conceptual Automotive Architecture
3.2. Automotive Attacker Model
3.3. Automotive Controls
3.3.1. Plausibility Checks
3.3.2. Cryptographic Counters
3.3.3. Firewall Based on CAN Matrix
4. Application of our Methodology
4.1. Hazard Analysis Compliant to ISO 26262
4.1.1. Safety-Step 1: Provide an Item Definition
4.1.2. Safety-Step 2: Instantiate Fault-Type Guide-Words
4.1.3. Safety-Step 3: Situation Classification
4.1.4. Safety-Step 4: Hazard Identification
4.1.5. Safety-Step 5: Hazard Classification by Severity, Exposure, and Controllability
4.1.6. Safety-Step 6: Define and Verify Safety Goals
4.1.7. Safety-Step 7: ISO 26262 Review
- whether each relevant functional requirement in the item definition is considered,
- whether the hazard and risk assessment is aligned with the supplier’s assessment, and
- whether the hazard and risk assessment is consistent with ISO 26262 description.
4.2. Threat Analysis Compliant to ISO 27001
4.2.1. Security-Step 1: Get Management Commitment
4.2.2. Security-Step 2: Define ISMS Scope
- A 1
- The firmware of all ECUs on all buses (including CAN) is secure from tampering by attackers.
- A 2
- Updates to the firmware of ECUs have security guarantees enforced by the update mechanisms concerning their integrity (e.g. they are signed).
- A 3
- The shop and repair garages do not carry out any attacks on the cars while in maintenance. This includes security guarantees towards the tampering of software/hardware used in this maintenance.
- A 4
- Attackers do not have access to any maintenance or diagnosis tool/software typically only available to shop and repair garages.
- A 5
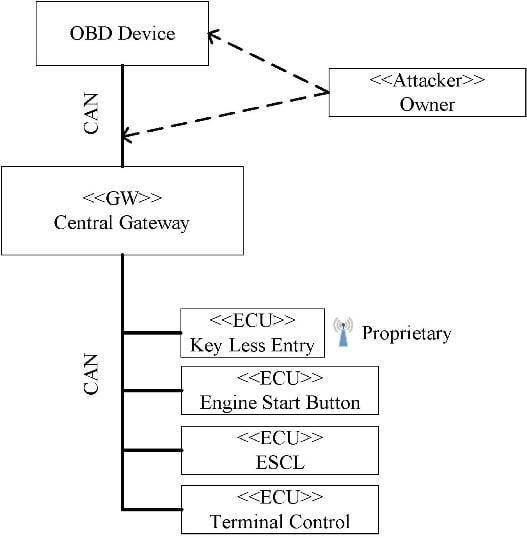
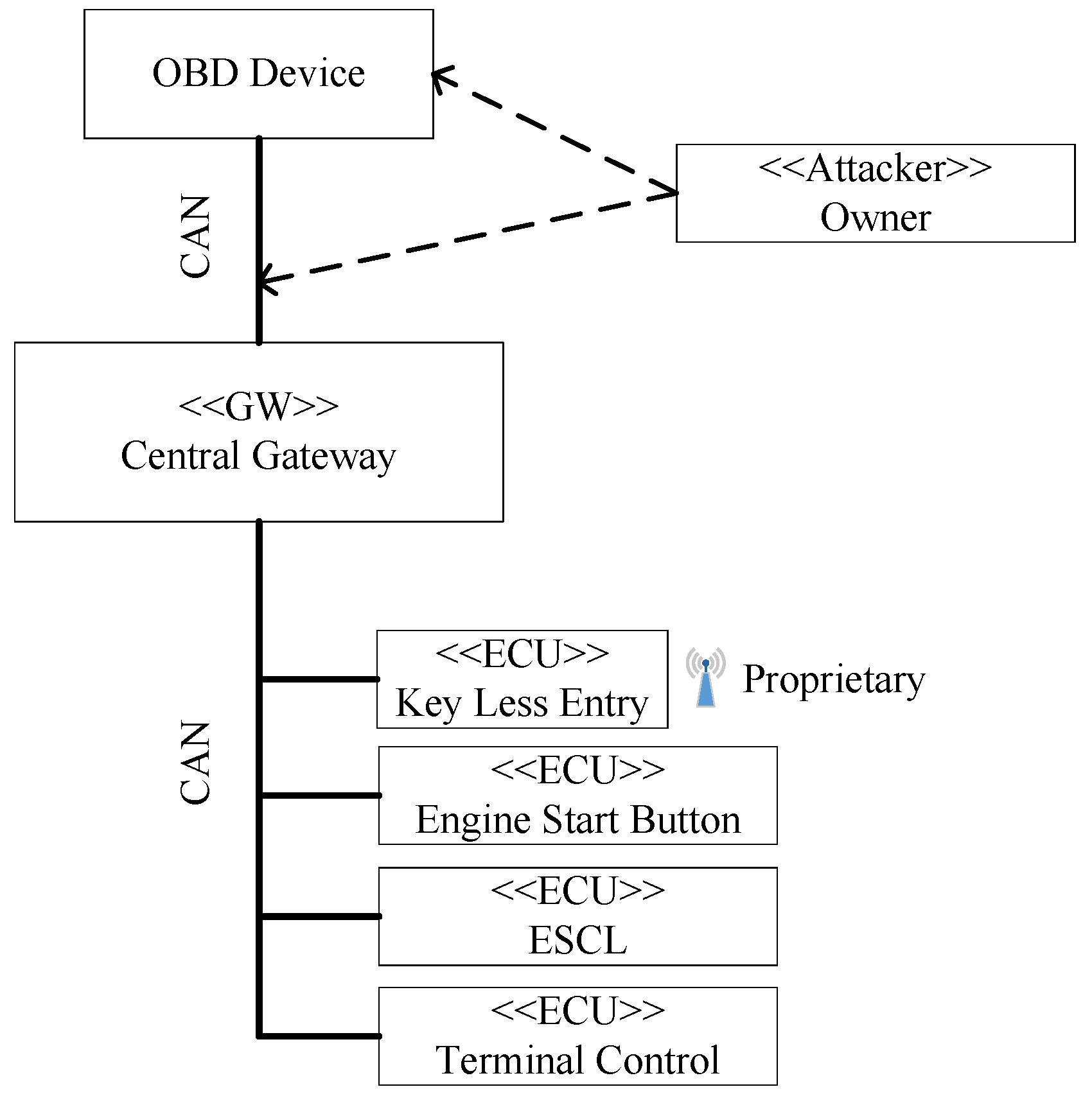
- All signals from other buses (including other bus types) must pass through a dedicated gateway (as shown in Figure 6).
4.2.3. Security-Step 3: Identify Assets
4.2.4. Security-Step 4: Analyse Threats
4.2.5. Security-Step 5: Conduct Risk Assessment
4.2.6. Security-Step 6: Reason about Controls
4.2.7. Security-Step 7: Design ISMS Specification
5. Related Work
5.1. Hazard Analysis
5.2. ISO 27001
5.3. Automotive Safety and Security
6. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Evans, L. Traffic Safety; Science Serving Society: Bloomfield, MI, USA, 2004. [Google Scholar]
- ISO. ISO 26262–Road Vehicles–Functional Safety; ISO: Geneva, Switzerland, 2011. [Google Scholar]
- Andy Greenberg. Hackers Remotely Kill a Jeep on the Highway With Me in It. Available online: https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/ (accessed on 17 June 2016).
- Valasek, C.; Miller, C. Adventures in Automotive Networks and Control Units. Available online: http://can-newsletter.org/assets/files/ttmedia/raw/c51e81bf7c09578c37e3f7a1f97c197b.pdf (accessed on 17 June 2016).
- Soja, R. Automotive Security: From Standards to Implementation. Available online: http://cache.nxp.com/files/automotive/doc/white_paper/AUTOSECURITYWP.pdf (accessed on 17 June 2016).
- ISO/IEC. Information Technology–Security Techniques–Information Security Management Systems–Requirements; ISO/IEC: Geneva, Switzerland, 2013. [Google Scholar]
- ISO/IEC. Common Criteria for Information Technology Security Evaluation; ISO/IEC: Geneva, Switzerland, 2012. [Google Scholar]
- ISO statistic in 2014. Available online: http://www.iso.org/iso/iso_survey_executive-summary.pdf (accessed on 15 April 2016).
- Common Criteria statistic in 2014. Available online: http://www.commoncriteriaportal.org/products/stats/ (accessed on 15 April 2016).
- Beckers, K.; Frese, T.; Hatebur, D.; Heisel, M. A Structured and Model-Based Hazard Analysis and Risk Assessment Method for Automotive Systems. In Proceedings of the 24th IEEE International Symposium on Software Reliability Engineering (ISSRE), Pasadena, CA, USA, 4–7 November 2013; pp. 238–247.
- Beckers, K.; Cote, I.; Faßbender, S.; Heisel, M.; Hofbauer, S. A pattern-based method for establishing a cloud-specific information security management system. Requir. Eng. 2013, 18, 343–395. [Google Scholar] [CrossRef]
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T. Comprehensive Experimental Analyses of Automotive Attack Surfaces. In Proceedings of the 20th USENIX Conference on Security, Berkeley, CA, USA, 2011; p. 6.
- Jackson, M. Problem Frames: Analyzing and Structuring Software Development Problems; Addison-Wesley: Boston, MA, USA, 2001. [Google Scholar]
- OMG. OMG Unified Modeling Language: Superstructure; Object Management Group: Needham, MA, USA, 2010. [Google Scholar]
- Hatebur, D.; Heisel, M. A UML Profile for Requirements Analysis of Dependable Software. In Proceedings of the 29th International Conference, SAFECOMP 2010, Vienna, Austria, 14–17 September 2010; Schoitsch, E., Ed.; Lecture Notes in Computer Science. Springer: Cham, Switzerland, 2010; Volume 6351, pp. 317–331. [Google Scholar]
- ISO/IEC. Functional Safety of Electrical/electronic/programmable Electronic Safety-relevant Systems; ISO/IEC: Geneva, Switzerland, 2000. [Google Scholar]
- Calder, A. Implementing Information Security Based on ISO 27001/ISO 27002: A Management Guide; Haren Van Publishing: Zaltbommel, The Netherlands, 2009. [Google Scholar]
- ISO/IEC. Information Technology–Security Techniques–Information Security Management Systems–Overview and Vocabulary; ISO/IEC: Geneva, Switzerland, 2014. [Google Scholar]
- Klipper, S. Information Security Risk Management mit ISO/IEC 27005: Risikomanagement mit ISO/IEC 27001, 27005 und 31010; Vieweg+Teubner: Wiesbaden, Germany, 2010. [Google Scholar]
- IET. Hazard and Operability Studies (HAZOP Studies); IET: Stevenage, UK, 2015. [Google Scholar]
- Deutsches Institut für Normung. Analysetechniken für die Funktionsfähigkeit von Systemen – Verfahren für die Fehlzustandsart- und -auswirkungsanalyse (FMEA); DIN: Berlin, Germany, 2006. (In German) [Google Scholar]
- U. S. Department of Defense. Electronic Reliability Design Handbook; DoD: Arlington County, VA, USA, 1998.
- ISO. Road Vehicles–Controller Area Network (CAN); ISO: Geneva, Switzerland, 2003. [Google Scholar]
- Beckers, K. Pattern and Security Requirements Engineering-based Establishment of Security Standards, 1st ed.; Springer: Cham, Switzerland, 2015. [Google Scholar]
- OWASP. Identify User Roles and Resource Capabilities; OWASP: Baltimore, MD, USA, 2015. [Google Scholar]
- ISMS toolkit. Available online: http://www.iso27001security.com/html/iso27k_toolkit.html (accessed on 16 June 2016).
- HMAC: Keyed-Hashing for Message Authentication. Available online: https://tools.ietf.org/html/rfc2104 (accessed on 17 June 2016).
- ISO/IEC. Information Technology–Security Techniques–Information Security Management Systems–Requirements; ISO/IEC: Geneva, Switzerland, 2013. [Google Scholar]
- ISO/IEC. Information Technology–Security Techniques – Information Security Risk Management; ISO/IEC: Geneva, Switzerland, 2011. [Google Scholar]
- Törner, F.; Johannessen, P.; Öhman, P. Evaluation of Hazard Identification Methods in the Automotive Domain, SAFECOMP 2006; Górski, J., Ed.; Springer: Cham, Switzerland, 2006; pp. 237–260. [Google Scholar]
- Baumgart, S. Investigations on Hazard Analysis Techniques for Safety Critical Product Lines. Available online: http://www.idt.mdh.se/kurser/ct3340/ht12/MINICONFERENCE/FinalPapers/ircse12_submission_14.pdf (accessed on 20 June 2016).
- Safety Management System and Safety Culture Working Group. Available online: https://essi.easa.europa.eu/documents/ECASTSMSWG-GuidanceonHazardIdentification.pdf (accessed on 20 June 2016).
- Jesty, P.H.; Hobley, K.M.; Evans, R.; Kendal, I. Safety analysis of vehicle-based systems. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.114.4318&rep=rep1&type=pdf (accessed on 20 June 2016).
- Papadopoulos, Y.; Grante, C. Evolving car designs using model-based automated safety analysis and optimisation techniques. J. Syst. Softw. 2005, 76, 77–89. [Google Scholar] [CrossRef]
- Li, W.; Zhang, H. A software hazard analysis method for automotive control system. In Proceedings of the 2011 IEEE International Conference on Computer Science and Automation Engineering (CSAE), Shanghai, China, 10–12 June 2011; pp. 744–748.
- Mehrpouyan, H. Model-Based Hazard Analysis of Undesirable Environmental and Components Interaction. Ph.D. Thesis, Linköping Universitet, Linköping, Sweden, 2011. [Google Scholar]
- Zhang, H.; Li, W.; Chen, W. Model-based hazard analysis method on automotive programmable electronic system. In Proceedings of the 3rd International Conference on Biomedical Engineering and Informatics (BMEI), Yantai, China, 16–18 October 2010; pp. 2658–2661.
- Giese, H.; Tichy, M.; Schilling, D. Compositional Hazard Analysis of UML Component and Deployment Models, SAFECOMP; Heisel, M., Liggesmeyer, P., Wittmann, S., Eds.; Springer: Cham, Switzerland, 2004; pp. 166–179. [Google Scholar]
- Hauge, A.A.; Stølen, K. A Pattern-Based Method for Safe Control Systems Exemplified within Nuclear Power Production, SAFECOMP; Springer: Cham, Switzerland, 2012; pp. 13–24. [Google Scholar]
- Kersten, H.; Reuter, J.; Schröder, K.-W. IT-Sicherheitsmanagement nach ISO 27001 und Grundschutz; Vieweg+Teubner: Wiesbaden, Germany, 2011. (In German) [Google Scholar]
- Cheremushkin, D.V.; Lyubimov, A.V. An application of integral engineering technique to information security standards analysis and refinement. In Proceedings of the International Conference on Security of Information and Networks, Taganrog, Russia, 7–11 September 2010; pp. 12–18.
- Lyubimov, A.; Cheremushkin, D.; Andreeva, N.; Shustikov, S. Information security integral engineering technique and its application in ISMS design. In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; pp. 585–590.
- Fabian, B.; Gürses, S.; Heisel, M.; Santen, T.; Schmidt, H. A Comparison of Security Requirements Engineering Methods. Requir. Eng. 2010, 15, 7–40. [Google Scholar] [CrossRef]
- Montesino, R.; Fenz, S. Information security automation: How far can we go? In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; pp. 280–285.
- Beckers, K.; Küster, J.C.; Fabender, S.; Schmidt, H. Pattern-Based Support for Context Establishment and Asset Identification of the ISO 27000 in the Field of Cloud Computing. In Proceedings of the 2011 Sixth International Conference on International Conference on Availability, Reliability and Security (ARES), Vienna, Austria, 22–26 August 2011; pp. 327–333.
- Fenz, S.; Goluch, G.; Ekelhart, A.; Riedl, B.; Weippl, E. Information Security Fortification by Ontological Mapping of the ISO/IEC 27001 Standard. In Proceedings of the 13th Pacific Rim International Symposium on Dependable Computing, Melbourne, Australia, 17–19 December 2007; pp. 381–388.
- Miller, C.; Valasek, C. Adventures in Automotive Networks and Control Units. Available online: http://illmatics.com/car_hacking.pdf (accessed on 17 June 2016).
- Koscher, K.; Czeskis, A.; Roesner, F.; Patel, S.; Kohno, T.; Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; et al. Experimental Security Analysis of a Modern Automobile. In Proceedings of the 2010 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 16–19 May 2010; pp. 447–462.
- Checkoway, S.; McCoy, D.; Kantor, B.; Anderson, D.; Shacham, H.; Savage, S.; Koscher, K.; Czeskis, A.; Roesner, F.; Kohno, T.; et al. Comprehensive Experimental Analyses of Automotive Attack Surfaces. Available online: http://static.usenix.org/events/sec11/tech/full_papers/Checkoway.pdf (accessed on 20 June 2016).
- Studnia, I.; Nicomette, V.; Alata, E.; Deswarte, Y.; Kaâniche, M.; Laarouchi, Y. Survey on security threats and protection mechanisms in embedded automotive networks. In Proceedings of the 2013 43rd Annual IEEE/IFIP Conference on Dependable Systems and Networks Workshop (DSN-W), Budapest, Hungary, 24–27 June 2013; pp. 1–12.
- Aijaz, A.; Bochow, B.; Dötzer, F.; Festag, A.; Gerlach, M.; Kroh, R.; Leinmüller, T. Attacks on inter vehicle communication systems-an analysis. In Proceedings of the 3rd international workshop on intelligent transportation (WIT 2006), Hamburg, Germany, 14–15 March 2006; pp. 189–194.
- Schröder, H. Analysis of Attack Methods on Car-to-X Communication Using Practical Tests: Analyse Von Angriffsmethoden Auf Die Car-to-X Kommunikation Durch Anwendung Praktischer Tests. Master Thesis, TU Darmstadt, Darmstadt, Germany, 2013. [Google Scholar]
- Martin, R.; Jürgen, D.; Florian, S.; Reiner, K. Survey on Vehicular Attacks–Building a Vulnerability Database. In Proceedings of the 2015 IEEE International Conference on Vehicular Electronics and Safety (ICVES), Yokohama, Janpan, 5–7 November 2015; pp. 208–212.
- Ring, M.; Rensen, T.; Kriesten, R. Evaluation of Vehicle Diagnostics Security: Implementation of a Reproducible Security Access. In Proceedings of The Eighth International Conference on Emerging Security Information, Systems and Technologies (SECURWARE 2014), Lisbon, Portugal, 16–20 November 2014.
- Glas, B.; Gebauer, C.; Hänger, J.; Heyl, A.; Klarmann, J.; Kriso, S.; Vembar, P.; Wörz, P. Automotive Safety and Security Integration Challenges. Available online: http://cs.emis.de/LNI/Proceedings/Proceedings240/13.pdf (accessed on 20 June 2016).
- Klauda, M.; Kriso, S.; Hamann, R.; Schaffert, M. Automotive Safety und Security aus Sicht eines Zulieferers. Available online: https://www.semanticscholar.org/paper/Automotive-Safety-Und-Security-Aus-Sicht-Eines-Klauda-Kriso/f9d2feca0e4c833dcf5e81b90bdd5df84f1d6b27/pdf (accessed on 20 June 2016).
- SAE International. Vehicle Cybersecurity Systems Engineering Committee (SAE. J3061). In Cybersecurity Guidebook for Cyber-Physical Vehicle Systems; SAE International: Warrendale, PA, USA, 2016. [Google Scholar]
| Attacker | System Knowledge | Physical Attack | Non-physical Attack | Complexity of Attack | Scaled Attack |
|---|---|---|---|---|---|
| Owner | L0 | L1 | L1 | L0 | L0 |
| Beginner | L1 | L1 | L1 | L1 | L0 |
| Tuner or thief | L2 | L2 | L1 | L2 | L1 |
| Insider | L3 | L3 | L3 | L2 | L2 |
| Organized group | L3 | L3 | L3 | L3 | L3 |
| ASIL | Requirements |
|---|---|
| QM | Value from local bus and value should be created or measured in the same domain as the plausibility check is done. |
| A | Value from local bus and value has to be checked for integrity. |
| B | Value from local bus and value has to be checked for integrity and authenticity. |
| C | Value from local bus and value has to be checked for integrity and authenticity. Furthermore, a second value from another bus has to be used. |
| D | Value from local bus and value has to be checked for integrity and authenticity. Furthermore, a second value from a local physical source has to be used. |
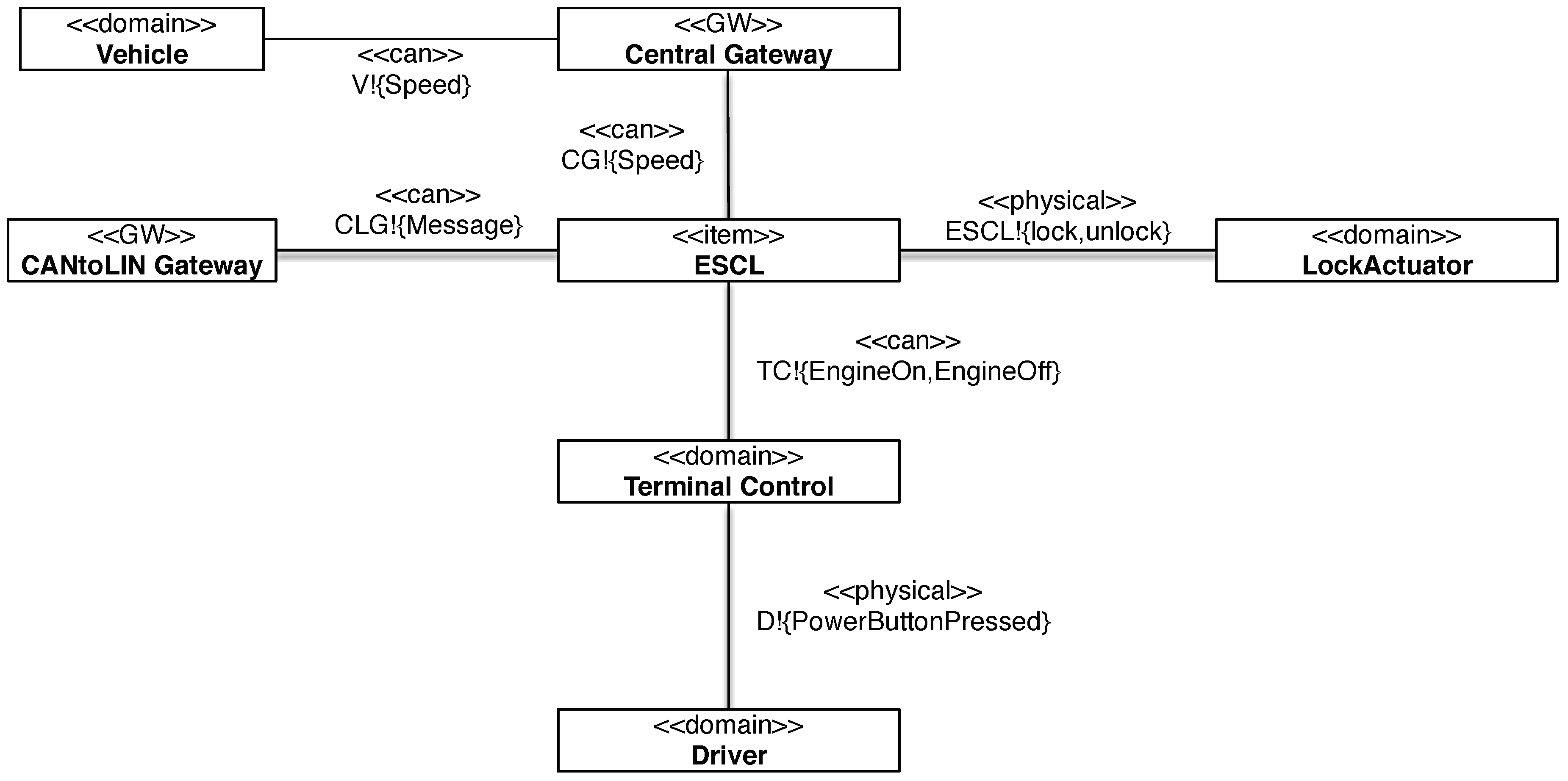
| No | Text | ≪constrains≫ | ≪refersTo≫ |
|---|---|---|---|
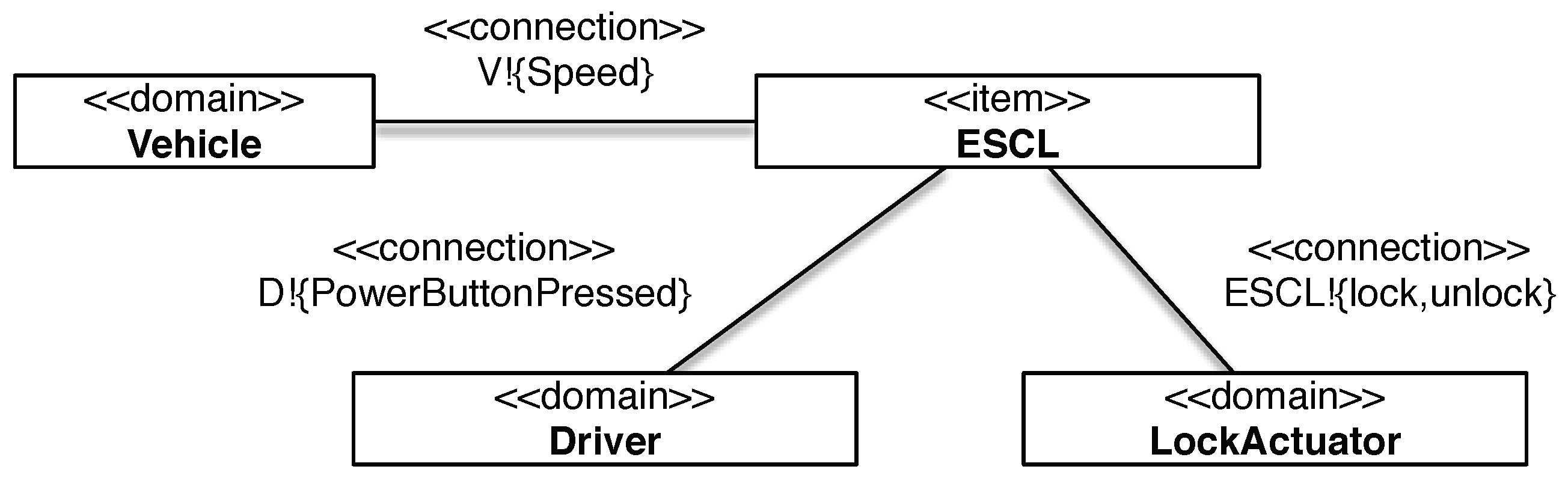
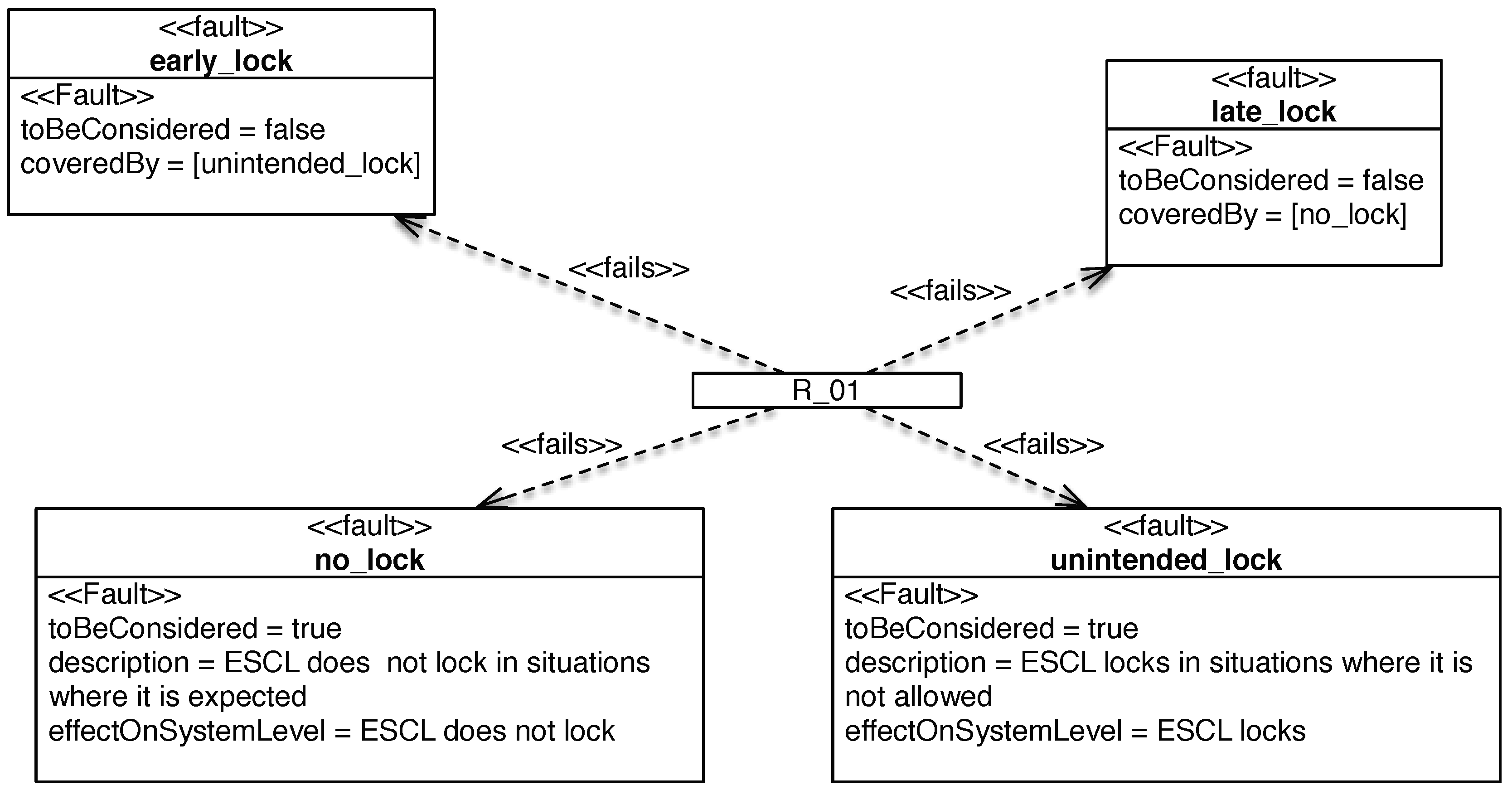
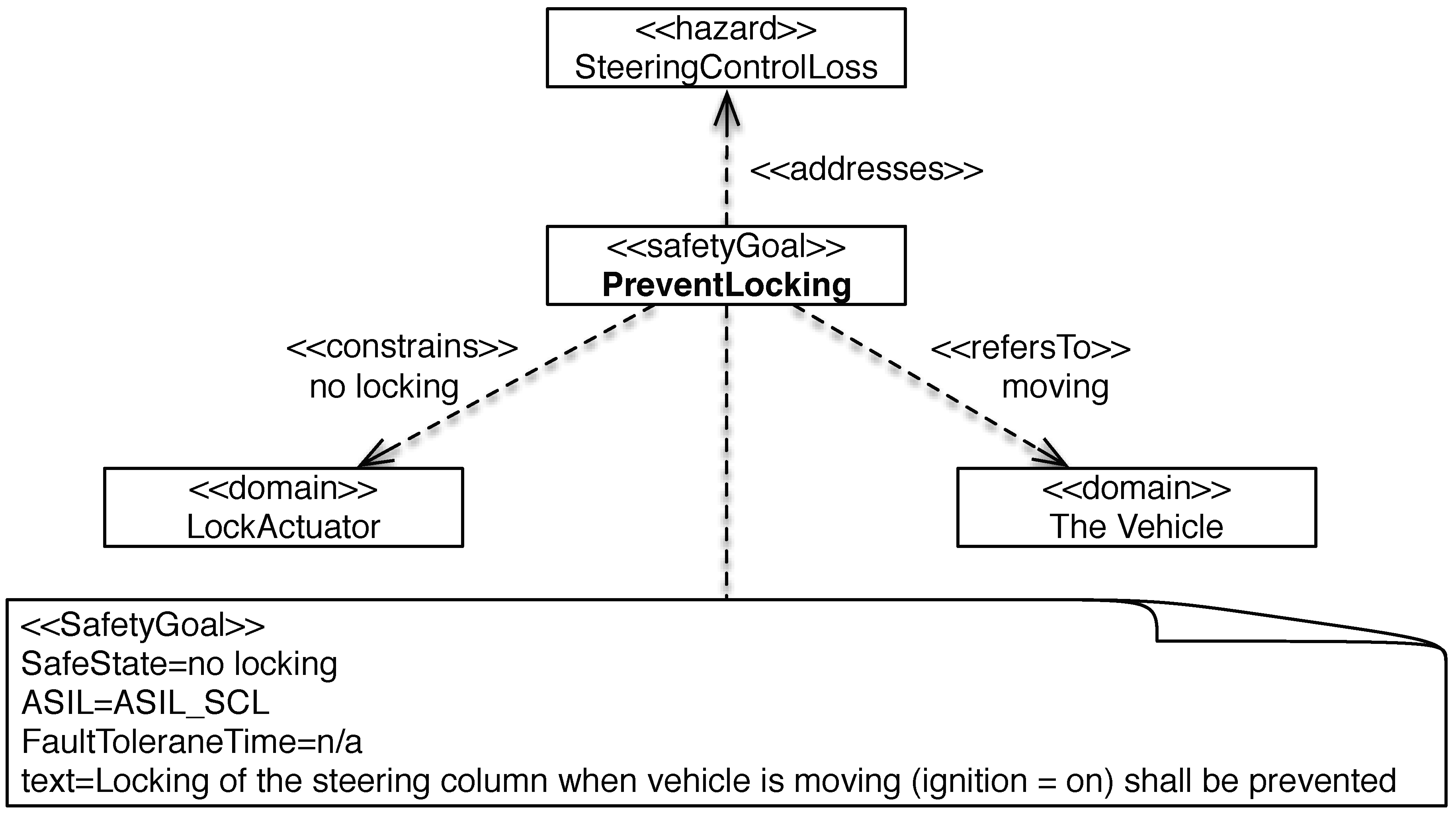
| R01 | The steering column shall be locked, when the driver wants to immobilise the vehicle. | LockActuator | Driver, Vehicle |
| R02 | The steering column shall be unlocked, when the driver wants to drive. | LockActuator | Driver, Vehicle |
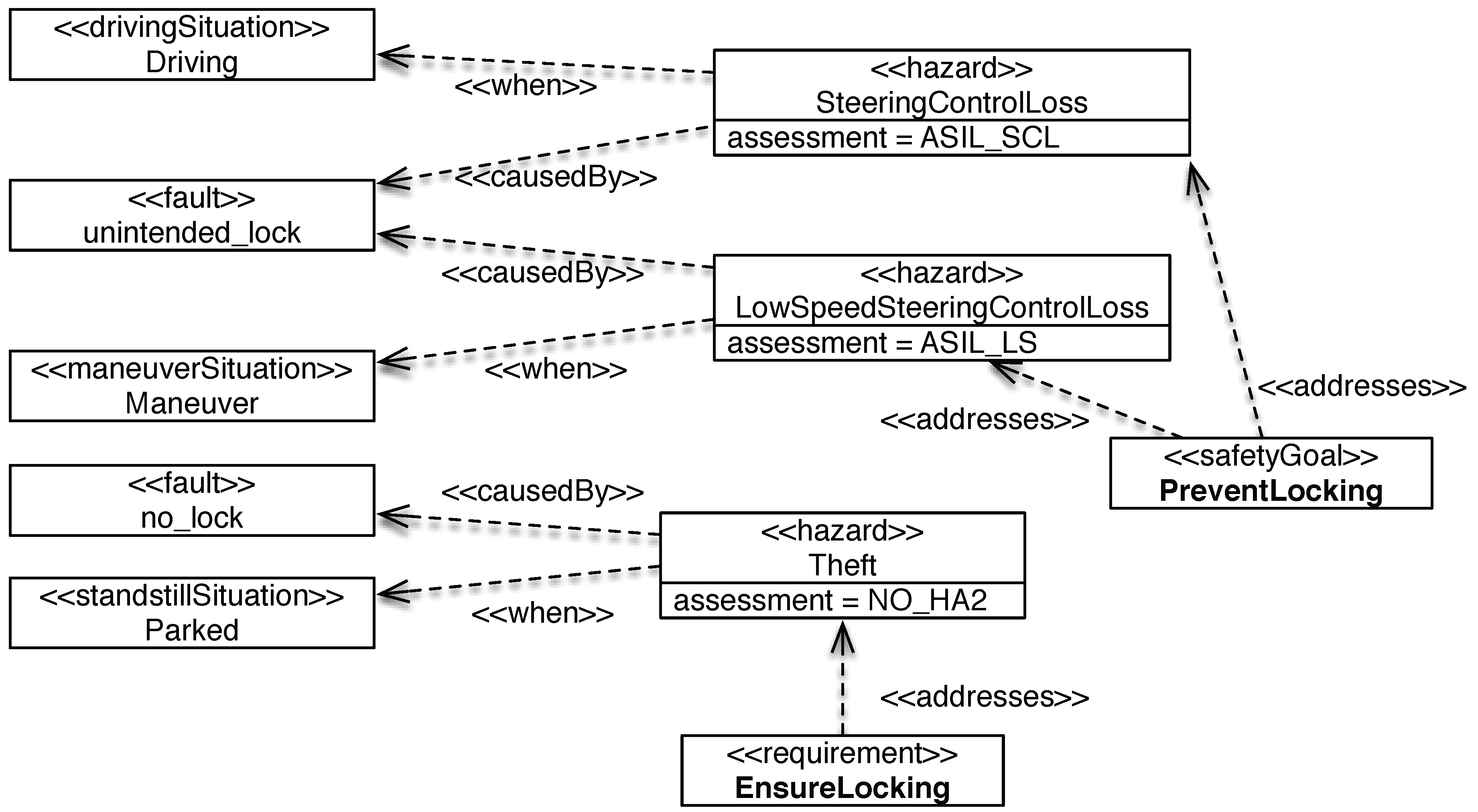
| Fault | Situation | Hazard | Risk Assessment | Safety Goal/Requirement |
|---|---|---|---|---|
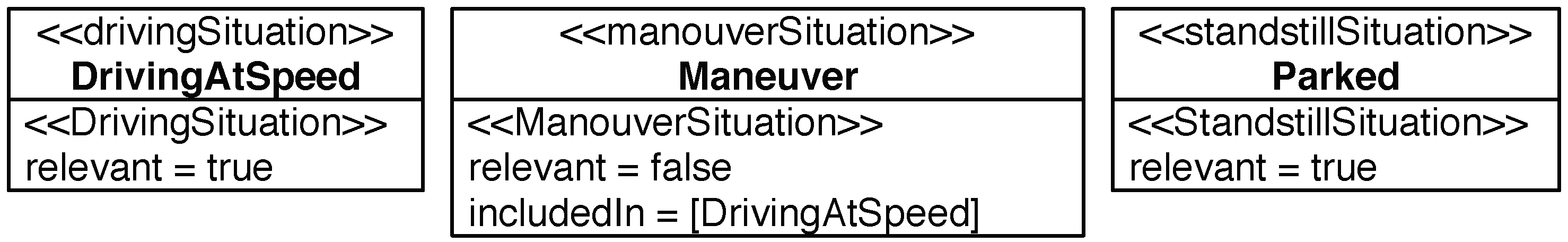
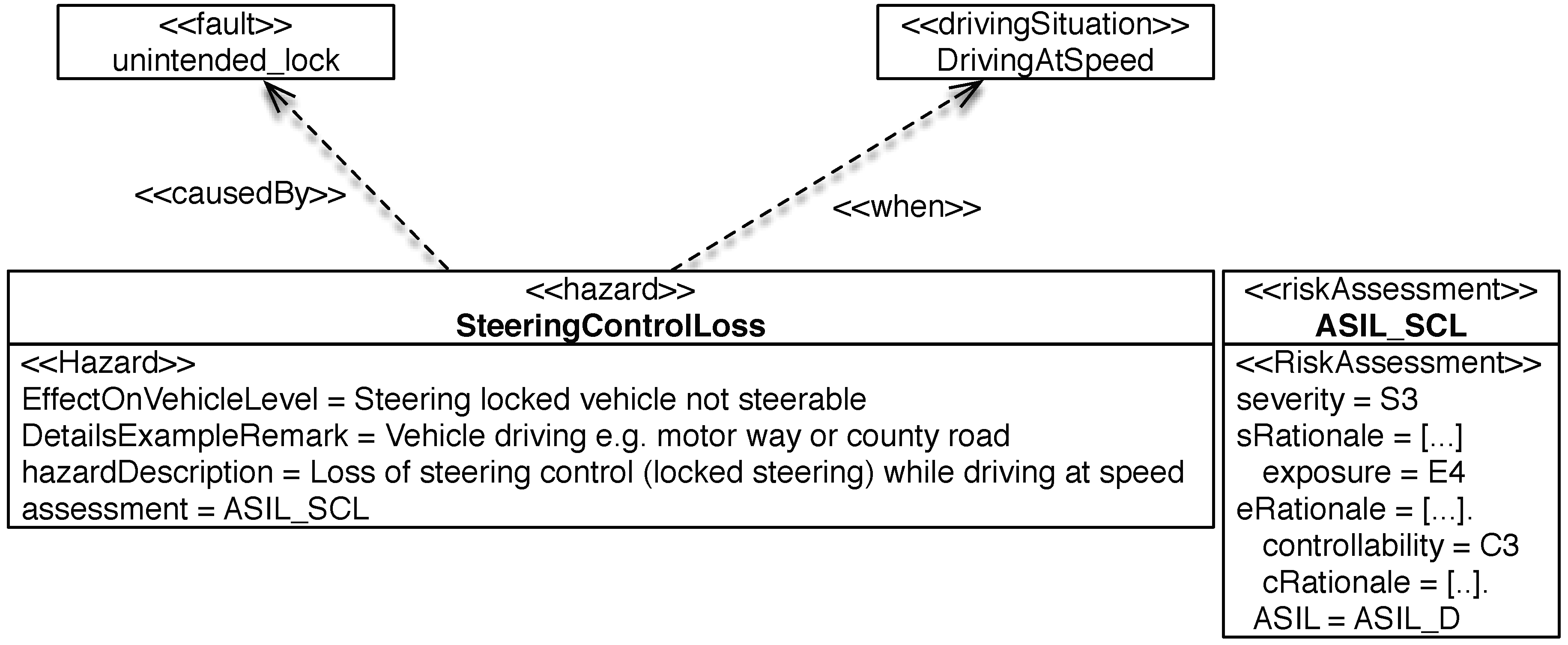
| unintended_lock | Driving | SteeringControlLoss | ASIL_SCL | PreventLocking |
| unintended_lock | Manouver | LowSpeed SteeringControlLoss | ASIL_LS | PreventLocking |
| no_lock | Parked | Theft | NO_HA2 | EnsureLocking |
| Management Commitment | |
|---|---|
| ISMS security goal | The integrity of data transferred to and from the ESCL shall be preserved. The availability of the transaction data shall be preserved. |
| Establish responsibilities | The responsible person for the fulfillment of all security goals is Mr. Jones from the OEM. |
| Communicate importance of security | The employees of the OEM, its subcontractors and maintenance staff receive an education about the consequences to the vehicle caused by a loss of integrity. |
| Criteria for Risk Acceptance | The OEM wants to avoid insolvency. |
| Conduct ISMS Audits | Mr. Jones is responsible for building the ISMS, hence he should not be responsible for hiring or conducting the audits. Mr. Smith is responsible for conducting internal and external audits. |
| ISMS management reviews | Neither Mr. Smith nor Mr. Jones should be responsible for the management reviews, because they are part of it. Instead this tasks is assigned to Mr. Shell. |
| Resource Management | |
| Provided Resources for the ISMS | The ISMS requires external parties to conduct the checking of the data integrity of transaction information using e.g. Hmac a keyed-hashing for message authentication [27]. The resources for these integrity checks have to be provided. |
| Security supports business needs | The integrity checking of the files should not make the transactions impossible or decrease the transaction time significantly. |
| Competent personal | List all resources necessary for conducting integrity checks. These are financial resources for hiring security experts to conduct integrity checks. |
| Provide Training | The training program in this case is for internal auditing and the external party that conducts the integrity checks. The bank institute requires skilled parties to conduct these audits. |
| Effectiveness Evaluation | Have an audit that checks all taken measures. In this case, audit training programs and personal. A specific audit for that case has to be taken. |
| Records of education, training, skills, experience and qualification | Mr. Jones is responsible for fulfilling documentation demands, e.g., which external party was hired and the reasons for hiring this particular party. |
| Scope Element | Is an Asset? | Reasoning when not an Asset |
|---|---|---|
| Vehicle | No | see Assumption A5 |
| Gateway | No | see Assumption A5 |
| ESCL | No | see Assumptions A1-A3 |
| Terminal Control | No | see Assumptions A1-A3 |
| Driver | No | The human is not information in the sense of ISO 27001 / ISO 27005 |
| LockActuator | No | see Assumptions A1-A3 |
| ≪can≫V!{Speed} | Yes | - |
| ≪can≫GW!{Speed} | Yes | - |
| ≪physical≫ESCL!{lock,unlock} | Yes | - |
| ≪can≫TC!{EngineOn,EngineOff} | Yes | - |
| ≪physical≫physical!{PowerButtonPressed} | Yes | - |
| Threat ID | Threat Description | Associated Hazard |
|---|---|---|
| 1 | OBD device is sending CAN message Engine Off which will be relayed by gateway to ESCL ECU. Thereon ESCL will be locked independently of vehicle’s condition. | Steering control loss |
| 2 | OBD device is sending diagnose message Lock ESCL which will be relayed by gateway to ESCL ECU. Thereon ESCL will be locked independently of vehicle’s condition. Diagnose message is mainly intended for testing ESCL’s actuator in a workshop but can also be triggered while car is moving. | Steering control loss |
| Threat ID | Threat Description | Associated Hazard |
|---|---|---|
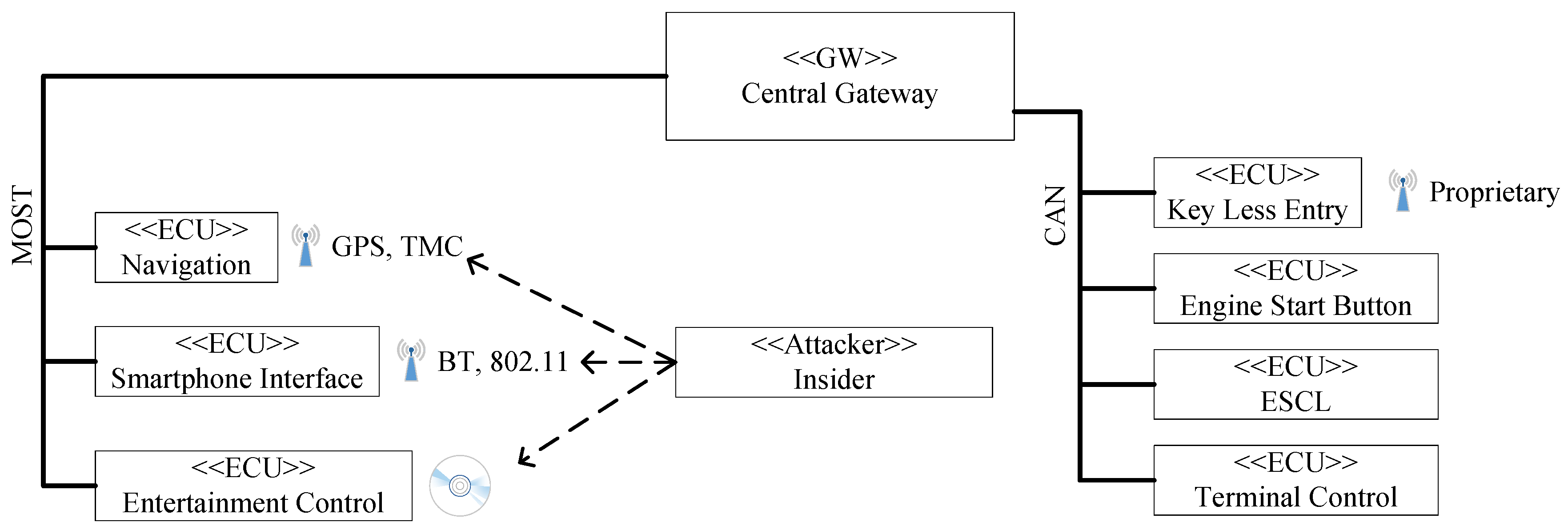
| 3 | Attacker sets up Traffic Message Channel (TMC) transmitter, sending malicious TMC messages which cause buffer overflow in the Navigation ECU. This empowers the attacker to send messages like Engine Off or Lock ESCL, locking ESCL. | Steering control loss |
| 4 | Attacker is able to brute force encryption of 802.11 or Bluetooth connection due to the fact of insufficient password length. Afterwards, he is able to take over the Smart Phone ECU which allows sending messages like Engine Off or Lock ESCL, locking ESCL. | Steering control loss |
| 5 | Attacker creates a malicious audio file which cause a buffer overflow in the Entertainment Control ECU. Afterwards, he is able to send a ESCL Reset message. Consequently, ESCL will reset and default state Locked will be taken which lead to locked ESCL. | Steering control loss |
| Likelihood Value | Description |
|---|---|
| Certain | Owner or beginner can trigger an attack; the attack can occur in more than one third of all driving situations |
| Likely | Beginner can execute the attack; the attack can occur at least at five manoeuvres of all driving situations |
| Possible | A tuner or thief can execute the attack; the attack can occur at least at five manoeuvres of all driving situations |
| Unlikely | An insider can execute the attack; the attack can occur at least at two manoeuvres of all driving situations |
| Rare | A organized group can execute the attack; Never experienced at most driving situations throughout the total lifetime of the Vehicle |
| Consequence | Generic Interpretation |
|---|---|
| Catastrophic | Driver cannot prevent the accident; Has a significant potential harm to drivers, passengers and people in the environment |
| Major | Driver can prevent the accident in a few cases; Has a potential for harm for drivers, passengers and people in the environment |
| Moderate | Driver can prevent the accident in some cases; Can cause limited harm for drivers, passengers and people in the environment |
| Minor | Tolerable if easy to recover from harm caused; Driver can prevent the accident with little effort |
| Insignificant | Generally tolerable and can only cause minimal harm |
| ASIL Exposure | Likelihood Value |
|---|---|
| E4 (high probability, e.g., highway) | Certain |
| E3 (medium probability, e.g., heavy traffic with stop and go) | Likely |
| E2 (low probability, e.g., snow and ice on road) | Possible |
| E1 (very low probability, e.g., vehicle being towed) | Unlikely |
| E0 (incredible, e.g., earthquake) | Rare |
| ASIL Controllability | ASIL Severity | Consequences Value |
|---|---|---|
| C3 (difficult to control or uncontrollable, e.g., stay in lane in case of failure of ABS when braking on low friction road surface while executing a turn) | S3 (life-threatening injuries, fatal injuries) | Catastrophic |
| C2 (normally controllable, e.g., maintain intended driving path in case of failure of ABS during emergency braking | S2 (severe and life-threatening injuries, survival probable) | Major |
| C1 (simply controllable, e.g., brake to slow down/stop the vehicle in case of blocked steering column when starting the vehicle) | S1 (light and moderate injuries) | Moderate |
| C1 (simply controllable, e.g., brake to slow down/stop the vehicle in case of blocked steering column when starting the vehicle) | S1 (light and moderate injuries) | Minor |
| C0 (controllable in general, e.g., maintain intended driving path in case of unexpected radio volume increase) | S0 (no injuries) | Insignificant |
| Consequence | ||||||
|---|---|---|---|---|---|---|
| Insignificant | Minor | Moderate | Major | Catastrophic | ||
| Likelihood | Rare | |||||
| Unlikely | ||||||
| Possible | ||||||
| Likely | ||||||
| Certain | ||||||
| Threat | ASIL (Severity, Exposure, Controllability) | Consequence | Likelihood | Reasoning (Attacker Type/Prevention) |
|---|---|---|---|---|
| Threat 1 | Steering control loss ASIL D (S3,E4,C3) | Major | Certain | Owner or beginner/Breaking ESCL lock or decelerate vehicle |
| Threat 2 | Steering control loss ASIL D (S3,E4,C3) | Major | Certain | Beginner/Braking ESCL lock or decelerate vehicle |
| Threat 3 | Steering control loss ASIL D (S3,E4,C3) | Major | Possible | Tuner or Thief/Breaking ESCL lock or decelerate vehicle |
| Threat 4 | Steering control loss ASIL D (S3,E4,C3) | Major | Possible | Tuner or Thief/Breaking ESCL lock or decelerate vehicle |
| Threat 5 | Steering control loss ASIL D (S3,E4,C3) | Major | Unlikely | Insider/Breaking ESCL lock or decelerate vehicle |
| Consequence | ||||||
|---|---|---|---|---|---|---|
| Insignificant | Minor | Moderate | Major | Catastrophic | ||
| Likelihood | Rare | |||||
| Unlikely | T-ID 5 | |||||
| Possible | T-ID 3, 4 | |||||
| Likely | ||||||
| Certain | T-ID 1, 2 | |||||
| Threat | Automotive Countermeasure | ISO 27001 Countermeasure | Prevented Hazard |
|---|---|---|---|
| Threat 1 | Cryptographic counters | A.10.1.1 Policy on the use of cryptographic controls A.10.1.2 Key management | Steering control loss |
| Threat 2 | Plausibility checks, Firewall based on CAN matrix | A.13.1.1 Network controls | Steering control loss |
| Threat 5 | Plausibility checks, Firewall based on CAN matrix | A.13.1.1 Network controls | Steering control loss |
| ISO 27001 Documentation | Support from our Method | Step |
|---|---|---|
| ISMS policies and objectives | Management Approval Template | Step 1 |
| Scope and boundaries of the ISMS | ISMS Scope Definition and Assumptions | Step 2 |
| Procedures and controls | Documentation of Security Controls | Step 6 |
| The risk assessment methodology | Our Risk Methodology | Step 5 |
| Risk assessment report | Asset Identification, Threat Analysis, and Risk Assessment | Steps 2–5 |
| Risk treatment plan | Risk Assessment and Control Selection | Steps 5–6 |
| Information security procedures | Policies | Step 6 |
| Control and protection of records | Security solution concerning the control A.10.7.4 Security of system documentation | Step 6 |
| Statement of Applicability | Reasoning about Controls | Step 6 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Beckers, K.; Dürrwang, J.; Holling, D. Standard Compliant Hazard and Threat Analysis for the Automotive Domain. Information 2016, 7, 36. https://doi.org/10.3390/info7030036
Beckers K, Dürrwang J, Holling D. Standard Compliant Hazard and Threat Analysis for the Automotive Domain. Information. 2016; 7(3):36. https://doi.org/10.3390/info7030036
Chicago/Turabian StyleBeckers, Kristian, Jürgen Dürrwang, and Dominik Holling. 2016. "Standard Compliant Hazard and Threat Analysis for the Automotive Domain" Information 7, no. 3: 36. https://doi.org/10.3390/info7030036
APA StyleBeckers, K., Dürrwang, J., & Holling, D. (2016). Standard Compliant Hazard and Threat Analysis for the Automotive Domain. Information, 7(3), 36. https://doi.org/10.3390/info7030036