Batch Attribute-Based Encryption for Secure Clouds
Abstract
:1. Introduction
1.1. Our Contribution
1.2. Related Work
1.3. Paper Organization
2. Modeling BABE
2.1. The System Framework
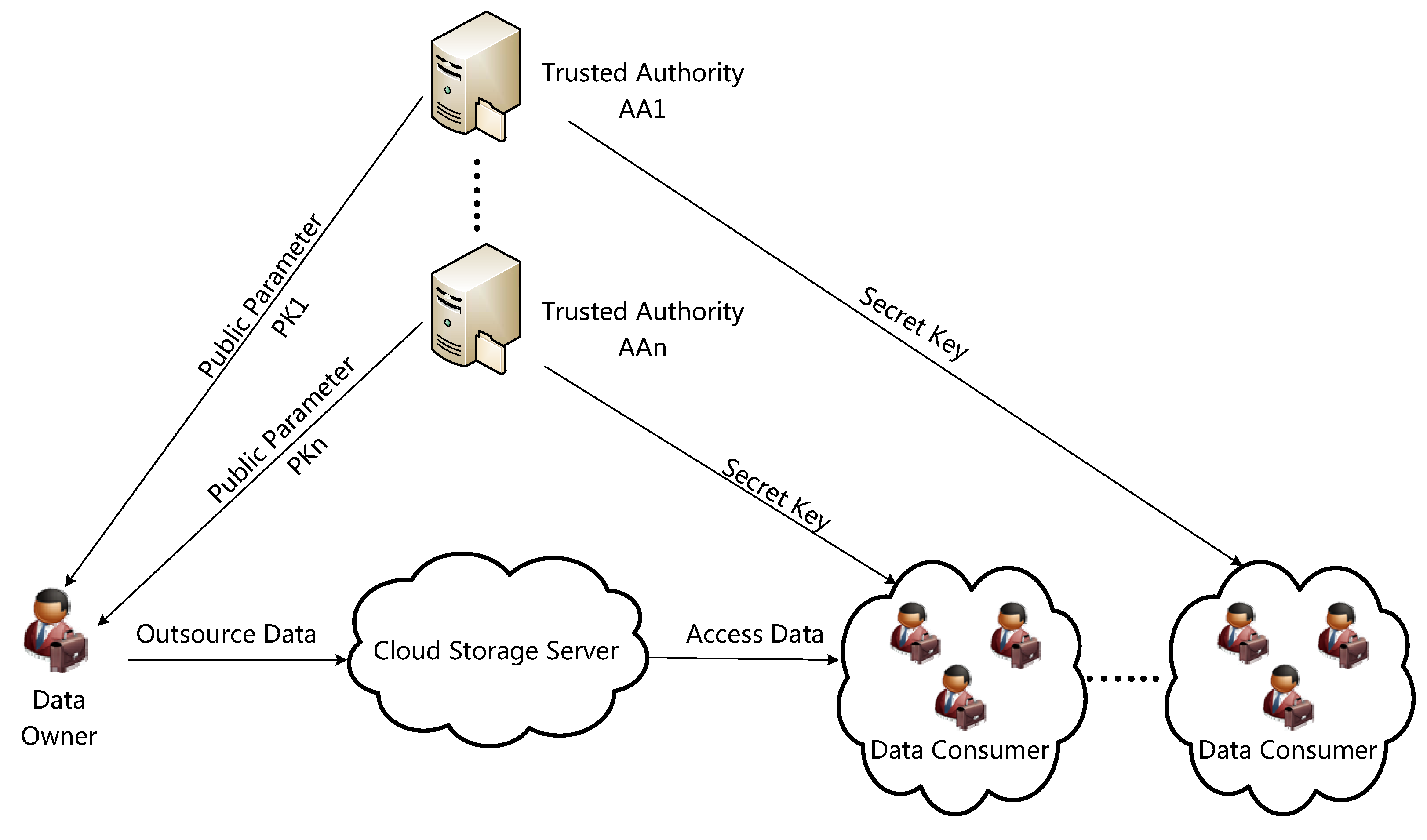
2.2. Defining BABE
- Setup()→(). This is a randomized algorithm run by an authority . It takes as inputs the security parameter λ and an attribute universe , which defines the set of allowed attributes in different underlying ABE subsystems. The authority outputs the public parameters and the mater keys .
- Encrypt()→. Assume that the data owner wants to share data with the data requestors of the systems . This is a randomized algorithm that takes as inputs the public parameters vector , a message vector , which contain different messages , and a series of attribute sets , which contains attribute sets . It outputs ciphertext associated with the attribute sets .
- KeyGen()→ SK. Assume that a data requestor belongs to the i-th subsystem. Then, is used to generate the secret key . This is a randomized algorithm that takes as inputs the master secret key and an access structure and outputs a secret key .
- Decrypt (). The decryption algorithm takes as inputs a secret key associated with the access structure and a ciphertext associated with attribute set . It outputs the message if satisfies or the error message ⊥ otherwise.
2.3. The Adversary Model
- Initialize.
- The adversary declares the different underlying ABE schemes upon which he or she wants to be challenged, indexed by . The adversary also declares the attribute set of different ABE schemes upon which he or she wished to be challenged upon.
- Setup.
- The challenger runs the Setup algorithm to set up the BABE system and sends the public parameters, , to the adversary.
- Phase 1.
- For the i-th underlying ABE subsystem, the challenger initializes for an empty table , an empty set and an integer counter . The adversary can repeatedly make the following queries:
- Create():
- The challenger sets . It runs the key generation algorithm on to obtain the secret key and stores it in table , forming the entry .
- Corrupt():
- The adversary queries for the secret key corresponding to the κ-th entry in Table i. If there exists such an entry in table , the challenger obtains the entry (), sets and returns the secret key to the adversary. Else, it returns ⊥.
- Challenge.
- The adversary submits two equal-length messages, vector and , with each vector having message and . In addition, the adversary gives a set of attributes , such that for all , the set does not satisfy the access structure . The challenger chooses randomly and encrypts under . The resulting ciphertext is given to the adversary.
- Phase 2.
- Phase 1 is repeated with the restriction that the adversary cannot obtain any secret key that can be used to decrypt the challenge ciphertext. This means that it cannot issue a Corrupt query that would result in an access structure that satisfies being added to . Of course, the adversary cannot issue a decryption query on the challenge ciphertext .
- Guess.
- The adversary outputs a guess bit of b. The output of the experiment is one if and only if .
3. The Proposed BABE Scheme
3.1. Mathematical Background
- Share:
- This takes as input , which is to be shared. It chooses , and let . It outputs as the vector of the shares. The share belongs to party , where is the i-th row of W.
- Recon:
- This takes as input an access set . Let . It outputs a set of constants , such that .
- (1)
- Bilinearity: for all and , we have .
- (2)
- Non-degeneracy: .
3.2. The Proposal
- Setup.
- This algorithm, run by the authority , takes as inputs a system parameter λ and an attribute universe . It generates a bilinear group G of prime order p, with generator . It selects random values . It further chooses a distinct for each i. Finally, for each i, it outputs the public key and master secret key as:
- Encrypt.
- The data owner chooses the organizations that he or she wants to communicate with, denoted by . Then, he or she asks the authority , for the public key and chooses a series of attributes , where , a series of messages . The data owner chooses a random . The ciphertext component used by i-th subsystem is where:After the encryption, the data owner sends the encrypted data to the cloud server.
- KeyGen.
- For each i, the authority takes as inputs the master secret key and an LSSS access structure represented by . Let W be an matrix. The function f is associated with the rows of W. Let β denote the set of distinct attributes appearing in the access structure matrix W, i.e., . This algorithm chooses a random vector . Here, these values will be used to share the master secret , and are random numbers. For to l, it calculates , where is the vector corresponding to the τ-th row of W. The algorithm chooses random integers , .It outputs the secret key as:In the above, means the set β excluding x.
- Decrypt.
- The data requestor requests the encrypted data from the cloud server. The requestor runs the decryption algorithm with his/her secret key for access structure () and the ciphertext for set . Let W be an matrix. The function f is associated with some rows of W. If does not satisfy the access structure, the decryption algorithm outputs ⊥.If satisfies the access structure, we let I be a set of indices and be a set of constants, such that and for all . Note that can be found in polynomial time.We represent the attributes satisfying the access structure as . I is the set of indices corresponding to the rows used to decrypt the ciphertext, and γ is the set of distinct attributes associated with these rows. In fact, there are multiple I’s that satisfy the constraints above. Typically, the smaller the size of I, the better. Observe that , where is the attribute set used to encrypt the ciphertext and , the set of attributes used to create the secret key.To recover the value , we define a function v, which transforms a set of attributes into an element of G in the way . For each , the data requestor computes the value . For the ciphertext, the data requestor computes the value .Finally, the data requestor recovers the value by computing:Note that . Hence, the data requestor can obtain from . From the computation process, it can be seen that the decryption algorithm requires only two pairing operations.
3.3. Security Analysis
3.4. Efficiency Analysis

4. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3494, pp. 457–473. [Google Scholar]
- Hohenberger, S.; Waters, B. Attribute-based encryption with fast decryption. In Public-Key Cryptography–PKC 2013, Proceedings of the 16th International Conference on Practice and Theory in Public-Key Cryptography, Nara, Japan, 26 February–1 March 2013; Springer: Berlin/Heidelberg, Germany, 2013. Lecture Notes in Computer Science. Volume 7778, pp. 162–179. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandri, VA, USA, 30 October–3 November 2006; pp. 89–98.
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the SP’07 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 20–23 May 2007; pp. 321–334.
- Waters, B. Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization. In Public Key Cryptography (PKC) 2011, Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011. Lecture Notes in Computer Science. Volume 6571, pp. 53–70. [Google Scholar]
- Yu, S.; Wang, C.; Ren, K.; Lou, W. Achieving secure, scalable, and fine-grained data access control in cloud computing. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9.
- Chase, M. Multi-authority attribute based encryption. In Theory of Cryptography, Proceedings of the 4th Theory of Cryptography Conference, TCC 2007, Amsterdam, The Netherlands, 21–24 February 2007; Springer: Berlin/Heidelberg, Germany, 2007. Lecture Notes in Computer Science. Volume 4392, pp. 515–534. [Google Scholar]
- Chase, M.; Chow, S.S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 121–130.
- Yang, K.; Jia, X. Attributed-based access control for multi-authority systems in cloud storage. In Proceedings of the 2012 IEEE 32nd International Conference on Distributed Computing Systems (ICDCS), Macau, China, 18–21 June 2012; pp. 536–545.
- Li, J.; Huang, Q.; Chen, X.; Chow, S.S.; Wong, D.S.; Xie, D. Multi-authority ciphertext-policy attribute-based encryption with accountability. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; pp. 386–390.
- Attrapadung, N.; Libert, B.; de Panafieu, E. Expressive key-policy attribute-based encryption with constant-size ciphertexts. In Public Key Cryptography–PKC 2011, Proceedings of the 14th International Conference on Practice and Theory in Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011. Lecture Notes in Computer Science. Volume 6571, pp. 90–108. [Google Scholar]
- Attrapadung, N.; Herranz, J.; Laguillaumie, F.; Libert, B.; de Panafieu, E.; Ràfols, C. Attribute-based encryption schemes with constant-size ciphertexts. Theor. Comput. Sci. 2012, 422, 15–38. [Google Scholar] [CrossRef]
- Fiat, A. Batch rsa. In Advances in Cryptology CRYPTO 89 Proceedings; Springer: Berlin/ Heidelberg, Germany, 1990; Lecture Notes in Computer Science; Volume 435, pp. 175–185. [Google Scholar]
- Bellare, M.; Garay, J.A.; Rabin, T. Fast batch verification for modular exponentiation and digital signatures. In Advances in Cryptology EUROCRYPT 98, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques Espoo, Finland, 31 May–4 June 1998; Springer: Berlin/Heidelberg, Germany, 1998. Lecture Notes in Computer Science. Volume 1403, pp. 236–250. [Google Scholar]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.H.; Shen, X. An efficient identity-based batch verification scheme for vehicular sensor networks. In Proceedings of the IEEE INFOCOM 2008, the 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008.
- Ferrara, A.L.; Green, M.; Hohenberger, S.; Pedersen, M.Ø. Practical short signature batch verification. In Topics in Cryptology—CT-RSA 2009, Proceedings of the The Cryptographers’ Track at the RSA Conference 2009, San Francisco, CA, USA, 20–24 April 2009; Springer: Berlin/Heidelberg, Germany, 2009. Lecture Notes in Computer Science. Volume 5473, pp. 309–324. [Google Scholar]
- Camenisch, J.; Hohenberger, S.; Pedersen, M.Ø. Batch verification of short signatures. In Advances in Cryptology—EUROCRYPT 2007, Proceedings of the 26th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Barcelona, Spain, 20–24 May 2007; Springer: Berlin/Heidelberg, Germany, 2007. Lecture Notes in Computer Science. Volume 4515, pp. 246–263. [Google Scholar]
- Duan, S.; Cao, Z. Efficient and provably secure multi-receiver identity-based signcryption. In Information Security and Privacy, Proceedings of the 11th Australasian Conference, ACISP 2006, Melbourne, Australia, 3–5 July 2006; Springer: Berlin/Heidelberg, Germany, 2006. Lecture Notes in Computer Science. Volume 4058, pp. 195–206. [Google Scholar]
- Baek, J.; Safavi-Naini, R.; Susilo, W. Efficient multi-receiver identity-based encryption and its application to broadcast encryption. In Public Key Cryptography-PKC 2005, Proceedings of the 8th International Workshop on Theory and Practice in Public Key Cryptography, Les Diablerets, Switzerland, 23–26 January 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3386, pp. 380–397. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution. Ph.D. Thesis, Technion-Israel Institute of Technology, Haifa, Israel, 1996. [Google Scholar]
- Boneh, D.; Boyen, X.; Goh, E.J. Hierarchical identity based encryption with constant size ciphertext. In Advances in Cryptology–EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3494, pp. 440–456. [Google Scholar]
- Boneh, D.; Gentry, C.; Waters, B. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Advances in Cryptology–CRYPTO 2005, Proceedings of the 25th Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3621, pp. 258–275. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, C.; Sun, Y.; Wu, Q. Batch Attribute-Based Encryption for Secure Clouds. Information 2015, 6, 704-718. https://doi.org/10.3390/info6040704
Yang C, Sun Y, Wu Q. Batch Attribute-Based Encryption for Secure Clouds. Information. 2015; 6(4):704-718. https://doi.org/10.3390/info6040704
Chicago/Turabian StyleYang, Chen, Yang Sun, and Qianhong Wu. 2015. "Batch Attribute-Based Encryption for Secure Clouds" Information 6, no. 4: 704-718. https://doi.org/10.3390/info6040704
APA StyleYang, C., Sun, Y., & Wu, Q. (2015). Batch Attribute-Based Encryption for Secure Clouds. Information, 6(4), 704-718. https://doi.org/10.3390/info6040704




