Abstract
Communications, Navigation, Surveillance/Air Traffic Management (CNS/ATM) systems utilize digital technologies, satellite systems, and various levels of automation to facilitate seamless global air traffic management. Automatic Dependent Surveillance-Broadcast (ADS-B), the core component of CNS/ATM, broadcasts important monitoring information, such as the location, altitude, and direction of aircraft, to the ground. However, ADS-B data are transmitted in an unencrypted (or unprotected) communication channel between ADS-B sensors and Air Traffic Control (ATC). Consequently, these data are vulnerable to security threats, such as spoofing, eavesdropping, and data modification. In this paper, we propose a method that protects the ADS-B data transmitted between ADS-B sensors and ATC using Simple Public Key Infrastructure (SPKI) certificates and symmetric cryptography. The SPKI certificates are used to grant transmission authorization to the ADS-B sensors, while symmetric cryptography is used to encrypt/decrypt the ADS-B data transmitted between the ADS-B sensors and ATC. The proposed security framework comprises an ADS-B sensor authentication module, an encrypted data processing module, and an ADS-B sensor information management module. We believe that application of the proposed security framework to CNS/ATM will enable it to effectively obviate security threats, such as ground station flood denial, ground station target ghost injection, and ADS-B data modification.
1. Introduction
Communication, Navigation, Surveillance/Air Traffic Management (CNS/ATM), which is based on the concept that safe aircraft navigation is ensured by the use of satellites, sensors, and data communication technology, is the next-generation Air Traffic Control (ATC) system being promoted by the International Civil Aviation Organization (ICAO) [1]. Automatic Dependent Surveillance-Broadcast (ADS-B), one of the core components of CNS/ATM, broadcasts information about aircraft, such as location, altitude, and speed, in real time [2,3,4]. CNS/ATM uses 4-D Trajectory Modeling [5,6], which can accurately predict the flight path of an aircraft on the basis of ADS-B and aircraft performance data, and therefore ensures safe navigation of more aircraft in limited air space.
However, recently, the number of security issues in the wireless environment has been increasing. As a result, a number of solutions to correspond to consequential security threats have been proposed [7,8,9]. However, even with these proposed measures, data from ADS-B, one of the core components of CNS/ATM are still vulnerable to security threats. ICAO is currently still examining security issues, and has been delaying selection and implementation of effective technologies to countermeasure the threats [10,11,12,13,14,15]. An example of the threats involved was outlined at the 2012 Defcon Hacking Conference [16,17], where it was demonstrated that ADS-B data could be hacked by aircraft target ghost injection. In this scenario, aircraft target ghost injection generates ADS-B data for 50 virtual aircraft and broadcasts the data, which are then received at the surveillance system and displayed at the Controller Working Position (CWP), which may result in hacking at the ATC.
In this paper, we propose a method that protects the ADS-B data transmitted between ADS-B sensors and ATC using Simple Public Key Infrastructure (SPKI) certificates and symmetric cryptography. The proposed security framework periodically authenticates the ADS-B sensors using lightweight SPKI certificate and encrypts the ADS-B data transmitted from the ADS-B sensors to ATC. The remainder of this paper is organized as follows: Section 2 gives an overview of ADS-B, describes the security vulnerabilities present, and discusses the lightweight SPKI certificates utilized in the proposed security framework. Section 3 outlines the proposed ADS-B security framework, which utilize SPKI certificates and XML digital signatures to countermeasure security threats. Section 4 concludes this paper.
2. Related Work
2.1. ADS-B
2.1.1. Overview
ADS-B is the next-generation surveillance system of CNS/ATM that allows the sharing of aircraft information, such as position, altitude, etc., among aircrafts and ATC [2,3,4]. ADS-B features two service modes as shown in Figure 1. “Step 1: ADS-B OUT” provides broadcasting of surveillance information (e.g., position, altitude, velocity, identification, emergency information) [18] from aircrafts to ATC or to other aircrafts. “Step 2: ADS-B IN” displays transmitted ADS-B information to cockpits of the aircrafts and ATC CWP to show identification of other aircrafts [2,3].
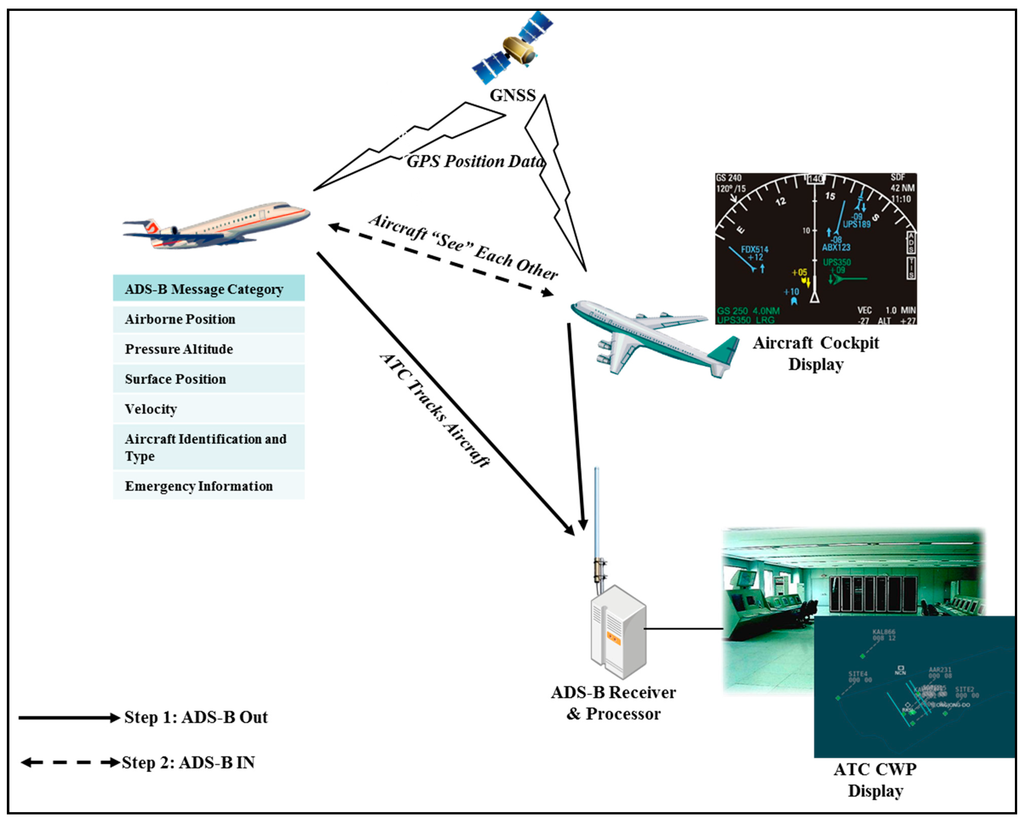
Figure 1.
ADS-B Service Scenario.
ADS-B features higher accuracy of identification than current Primary Surveillance Radar (PSR) provides because Global Positioning System (GPS) is used in acquisition of the aircraft position. Therefore, superior air traffic control featuring higher degree of accuracy, safety, and efficiency is possible in a controlled airspace [2,3,4].
2.1.2. Security Threats
Because ADS-B does not contain a suitable security countermeasure, anyone can view aircraft flight information using ADS-B data receiver occurred to possible security threats [10,11,12,13,14,15,16,17]. [10] shows the analysis of the security vulnerability of ADS-B data in the ADS-B data link.
- -
- Eavesdropping
- -
- Jamming
- -
- Message Injection
- -
- Message Modification
- -
- Message Deletion
Particularly, there is strong possibility of increase of security vulnerability concerning Message Injection and Message Modification. Message Injection can interfere air traffic control by using Ground Station Flood Denial, Ground Station Target Inject, Ground Station Multiple Ghost Inject, and Message Modification can be used in Virtual Aircraft Hijacking [10,11]. An example, Ground Station Target Inject and Aircraft Target Ghost Inject were demonstrated in 2012 Defcon Hacking Conference [16,17].
2.2. SPKI
Public Key Infrastructure (PKI) generates security tokens to provide encrypted signatures using a public key algorithm. More specifically, it authenticates users and encrypts data using a public/private key pair for encryption/decryption. Because PKI can only be applied to sensor groups and resource groups, rather than specific users, a universal user authentication/authorization mechanism is used in grid environments instead [19]. The most recently presented mobile network anonymous authentication mechanism [20] satisfies the low-volume data and fast processing speed of ADS-B, but it does not yet clearly recognize ADS-B. As a consequence, we adopted the lightweight SPKI certificate for out proposed method.
The SPKI certificate is the standard proposed for the application of the PKI certificate. An SPKI certificate binds the authority of a user with the public key and provides access control. An SPKI certificate is also called an “authority certificate”. It is published by a server to a client, who is then permitted to use the resources provided by a server in accordance with the access policy granted to the SPKI certificate it possesses. An SPKI certificate has the following features, which contrast those possessed by an X.509 user certificate [21,22].
- -
- AN SPKI certificate indicates the issuer and subject using the hash-value of the public key or the public key. Therefore, user anonymity is guaranteed.
- -
- An SPKI certificate operates without modifying the server database; authorization is easily delegated to the user.
- -
- An SPKI certificate can operate independently of any specific service.
- -
- Publication and management of SPKI certificates are relatively easy. Therefore, maintenance cost is expensive.
- -
- Restrictions and multiple delegations can be easily applied using an SPKI certificate.
In this paper, two versions of SPKI certificates are used for ADS-B sensor identification and authorization, respectively [22].
2.2.1. ADS-B Sensor Identification Certificate
An ADS-B sensor identification certificate is used to get an ADS-B sensor authorized by ATC and connects the unique identification codes of the ADS-B sensor to its public keys.
- <Issuer, Localname (Public Key Info), Subject (ADS-B ID), Validity (10/OCT/2014) > Signature (Issuer)
- - Issuer: The SPKI certificate issuer; the issuer signs the SPKI certificate with private keys.
- - Localname: This comprises the SPKI certificate issuer’s public key and one or more identifiers.
- - Subject: The subject of the SPKI certificates issue, including the unique identifiers of the ADS-B sensor.
- - Validity: Indicates the expiration date of the SPKI certificate.
2.2.2. ADS-B Sensor Authorization Certificate
An ADS-B sensor authorization certificate is used to receive ADS-B sensor authorization from ATC. This certificate grants authorization to transmit ADS-B data received by the ADS-B sensor to ATC. The ADS-B sensor authorization certificate comprises the following six tuples:
- <Issuer, Subject (ADS-B ID), SubjectPublicKeyInfo, Delegation, Authorization, Validity (10/Oct/2014)>Signature (Issuer)
- - SubjectPublicKeyInfo: SPKI certificate subject public key information.
- - Delegation: Indicates the existence of authorization to transmit ADS B-data with a value of True/False.
- - Authorization: Specifies the authorization granted by ATC to the ADS-B sensor.
3. Proposed ADS-B Security Framework
3.1. ADS-B Sensor Authorization and Symmetric Keys Exchange Using the Proposed ADS-B Framework
The structure of the ADS-B security framework proposed in this paper is depicted in Figure 2. For the messages exchanged between the ADS-B sensor and ATC in Steps 1–5, an XML signature is used.
- -
- Step 1: The ADS-B sensor generates a private/public key pair, and generates ADS-B sensor identification certificates signed with the private key in the data, and including ADS-B sensor identification information and the public key, then transmits them to ATC. An examples of the SPKI four tuple certificate generated in Figure 3 shown below:
- <ADS-B Sensor 1, ADS-B Sensor 1’s Public Key Info, ADS-B Sensor ID, 10/Oct/2014> Signature (ADS-B Sensor 1’s Private Key)
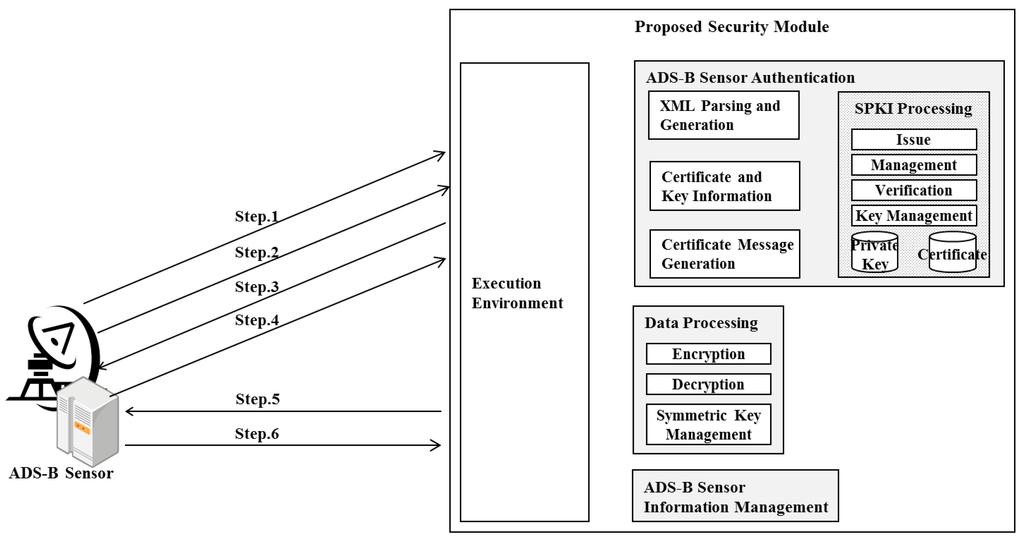
Figure 2.
Proposed ADS-B security framework structure and operation.
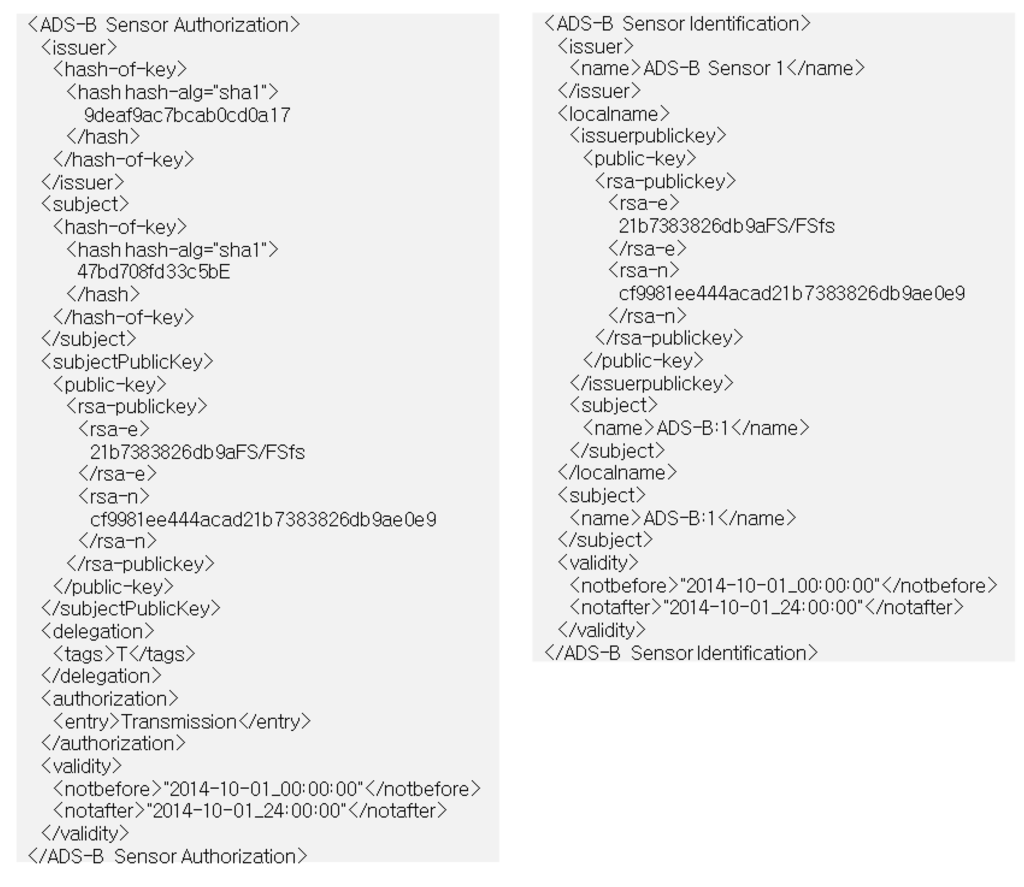
Figure 3.
SPKI four tuple certificate and SPKI six tuple certificate.
- -
- Step 2: To verify the authorization for the transmission of the received ADS-B data, the ADS-B sensor requests ADS-B sensor identification information from ATC.
- -
- Step 3: ATC validates the ADS-B sensor authorization using the ADS-B sensor identification certificates saved in Step 1 and ADS-B sensor identification information in Step 2. It then generates the ADS-B sensor authorization certificates for the ADS-B sensor whose authorization for transmission was validated, and transmits them to the ADS-B sensor. An example of the SPKI six tuple certificates generated in Figure 3 is shown below:
- <ATC, ADS-B Sensor 1, ADS-B Sensor 1’s Public Key Info, T, Transmission, 10/Oct/2014>Signature (ATC’s Private Key)
- -
- Step 4: The ADS-B that receives the ADS-B sensor authorization certificates requests symmetric keys for encryption from ATC in order to transmit the received ADS-B data.
- -
- Step 5: ATC generates symmetric keys for encrypting/decrypting the ADS-B data, signs the generated symmetric keys, encrypts the public keys of the ADS-B sensor, and then transmits them to the ADS-B sensor. Advanced Encryption Standard-128 (AES-128), for example, can be used as the symmetric cryptography algorithm.
- -
- Step 6: The ADS-B sensor validates the cryptography token received from ATC using its own private keys, acquires the symmetric keys and encryption algorithm, and encrypts and transmits the ADS-B data to ATC.
- -
- Step 7: Steps 1–6 are repeated over a predetermined period to authorize ADS-B continuously. To change the symmetric keys used to encrypt the ADS-B data, only Steps 4–6 need be repeated.
3.2. XML Signature Module
The XML signature module is the core module used to authenticate the ADS-B sensor, and is installed in both the ADS-B sensor and ATC. As illustrated in Figure 4, the XML signature module is composed of a unit or parsing and creation of XML signatures, a key and certificate status verification unit, and a unit for certificate request message creation. Data flow and the data in each module are controlled in the execution environment.
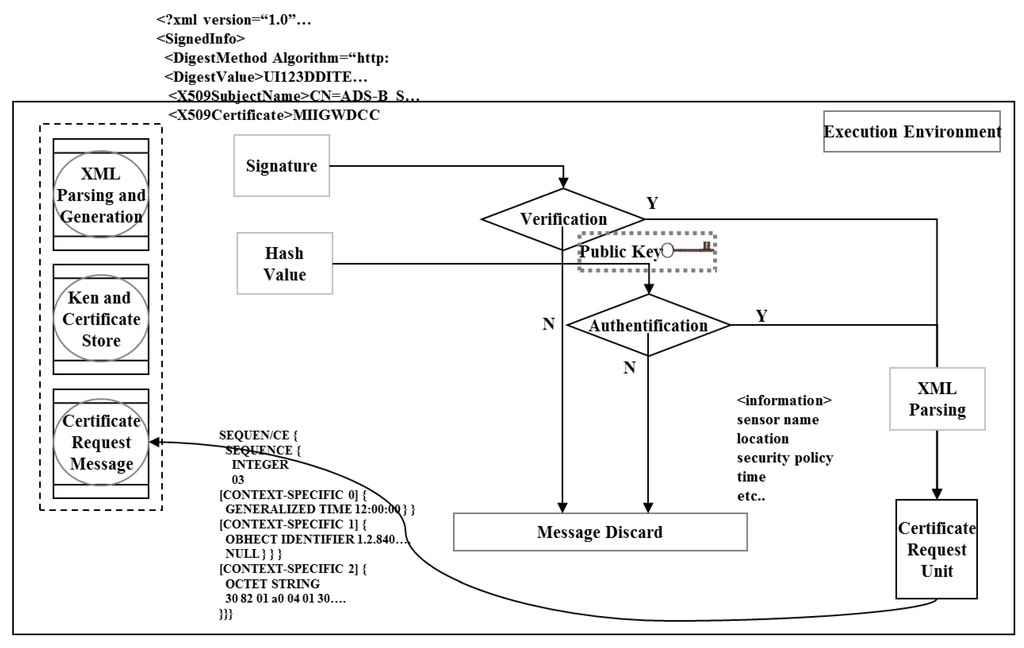
Figure 4.
Structure and operation of the authentication module.
3.2.1. XML Signature Creation and Verification for Authentication
Figure 5 depicts the XML signature generation module, which generates signatures using the ADS-B sensor data (the ADS-B sensor data includes ADS-B sensor identification certificates, SPKI four tuple ADS-B sensor identification certificates and SPKI six tuple sensor authorization certificates) and certificate. The ADS-B sensor data are used to create a value for verification through hashing and then combined with the XML signature value and the encrypted private key of the sensor to from the authentication request in the XML signature generation process. The series of steps executed in the process is outlined below.
- (1)
- Create document by collecting ADS-B sensor data.
- (2)
- Sign with private key of ADS-B sensor certificate and add digest value.
- (3)
- Public key data for signature verification creates <KeyInfo> which includes SPKI certificate for the ADS-B sensor.
- (4)
- Create XML signature containing the value obtained from the above process.
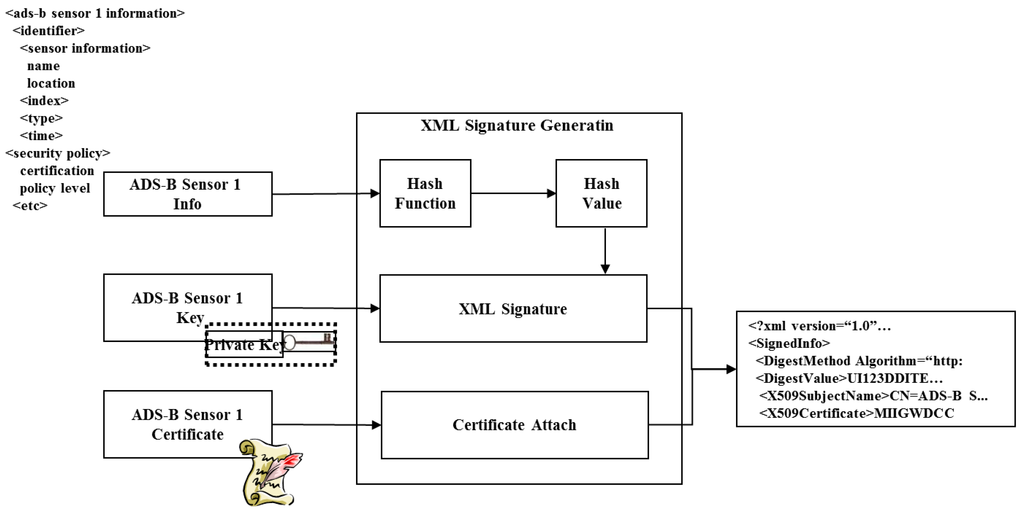
Figure 5.
Creation of XML signature.
Figure 6 depicts the module used to examine the validity of the XML signature and extract the ADS-B sensor data following the request for authentication. The series of steps utilized in the process is as follows:
- (1)
- Separate XML signature of each attribute tag using a parser.
- (2)
- Examine the validity of the certificate contained in the <KeyInfo> tag through communication with the CA and acquire the public key value.
- (3)
- Verify the signature by decoding the signature value contained in the XML signature.
- (4)
- Verify the integrity of the signature by comparing the digest value contained in the XML signature with the hash value created through signature verification.
- (5)
- Acquire the ADS-B sensor data in the request for authentication.
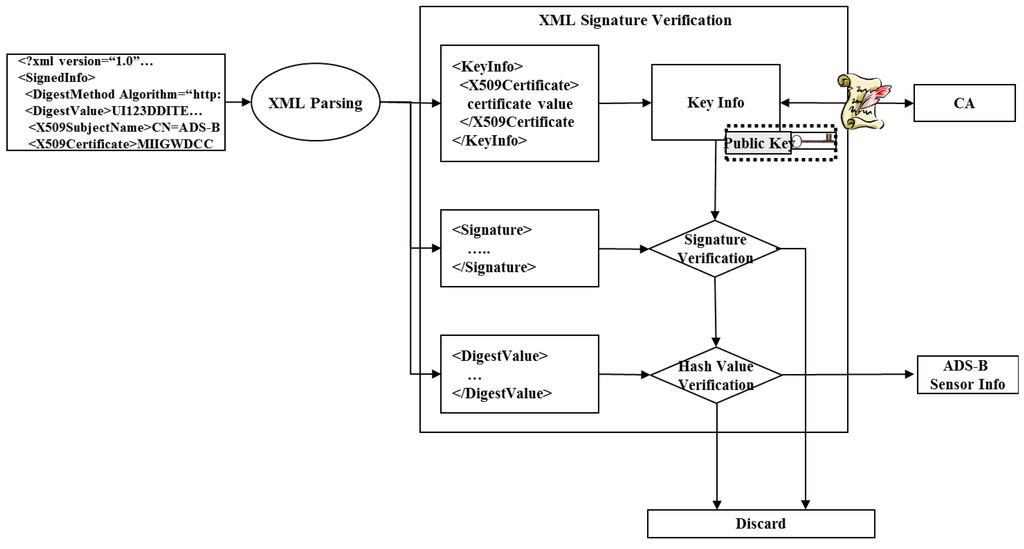
Figure 6.
Verification of XML signature.
3.2.2. Creation and Transmission of SPKI Certificate
Certificate request message creation for the ADS-B sensor is carried out by the communication and encryption module to request/acquire SPKI certificate for the ADS-B to the CA and transmit the created SPKI certificate to each ADS-B sensor. A description of each component illustrated in Figure 7 is given below.
- -
- ASN.1 Parsing Unit: A data structure creation unit that creates data for certification in the international standard regulation certificate request message format.
- -
- Encryption Unit: A unit that encrypts data for the security service for certificate request data.
- -
- Transmission Unit: A send/receive unit for encrypted data.
- -
- Certificate & Private Key: A unit to acquire the created SPKI certificate and private key for ADS-B from CA and transmit them to the ADS-B sensor.
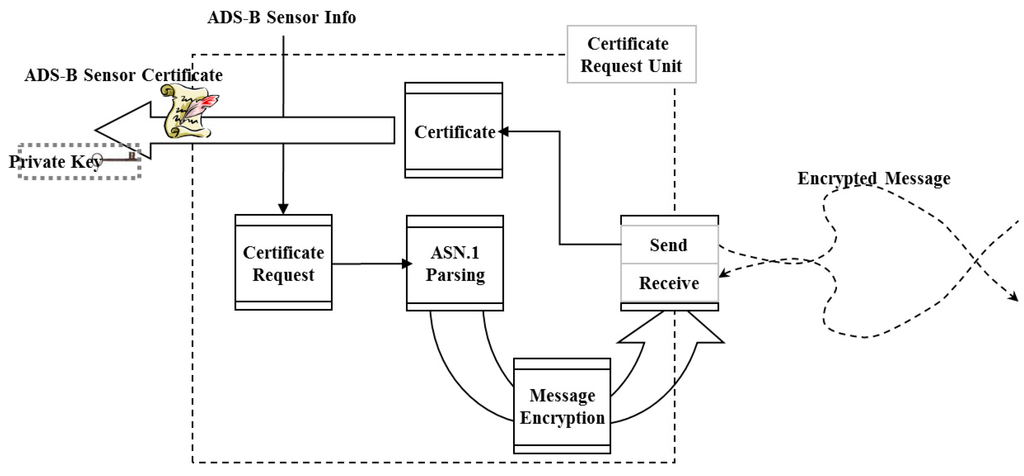
Figure 7.
Composition and operation of SPKI certificate requesting unit.
4. Conclusion
Recently, as a result of the rapid increase in air traffic, the construction of the CNS/ATM next-generation ATC system has been accelerated. To ensure the safe navigation of more aircraft in limited air space, CNS/ATM has to predict accurate traffic flows on the basis of flight plans and accurate positioning of aircraft. ADS-B is able to provide accurate navigation information, such as the location, altitude, and identification information of aircraft; consequently, it is the core technology in CNS/ATM. However the transmission of ADS-B data between ADS-B sensor and ATC is carried out in an unencrypted (or unprotected) communication channel; therefore, it is vulnerable to security threats such as spoofing, eavesdropping, and data modification.
The ideal method of countering this security threat toward ADS-B would be to issue X.509 certificates to all planes and provide a certificate based security service, but this is difficult in reality.
In this paper, we proposed a method that protects the ADS-B data transmitted between the ADS-B sensor and ATC. In the proposed method, the ADS-B sensor is identified using SPKI four tuple certificates and further authorized to transmit ADS-B data to ATC using SPKI six tuple certificates. An authorized ADS-B receives symmetric keys from ATC and utilizes them to encrypt the ADS-B data. We believe that application of the method proposed in this paper to the next-generation ATC system will facilitate an effective response to the security threats to ADS-B data transmitted between ADS-B sensors and ATC, such as spoofing, eavesdropping, and data modification.
Our future research direction is to implement the proposed security framework, improve it through validation at the laboratory level, analyze the benefits of application to CNS/ATM, and ultimately obtain valid test results by linking the actual data with an actual ATC system in operation.
Acknowledgments
This work was supported by the IT R&D program of MISP/IITP. (10041560. A development of anomaly detection and a multi-layered response technology to protect an intranet of a control system for the availability of pipeline facilities.)
Author Contributions
Seoung-Hyeon Lee has initiated the idea of the work and written the manuscript. Yong-Kyun Kim collected the references. Jong-Wook Han conducted the literature review. Deok-Gyu Lee provided critical revisions. All of the authors have developed the research design. All authors have read and approved the final manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Global Air Navigation Plan for CNS/ATM Systems (Doc 9550 AA/963), 2nd ed.; ICAO: Chicago, IL, USA, 2002.
- Wikipedia: Automatic Dependent surveillance-broadcast. Available online: http://en.wikipedia.org/wiki/Automatic_dependent_surveillance-broadcast (accessed on 18 November 2014).
- Vigier, C. Automatic Dependent Surveillance Broadcast (ADS-B): Communication development for Air Traffic Management. AIRBUS FAST 2011, 47, 8–13. [Google Scholar]
- Australian Government Civil Aviation Safety Authority, ADS-B; Civil Aviation Safety Authority: Woden, Australia, 2012.
- Lee, S.-H.; Kim, Y.-K.; Lee, D.-G. Conformance monitoring method based 4D trajectory modeling using aircraft performance data. J. Converg. 2014, 5, 28–36. [Google Scholar]
- Kim, Y.-K.; Lee, D.-G.; Han, J.-W.; Park, H.-D. Ground speed calculation using wind component information for trajectory prediction. J. Converg. 2013, 4, 1–5. [Google Scholar]
- Singh, R.; Singh, P.; Duhan, M. An effective implementation of security based algorithmic approach in mobile adhoc networks. Hum.-centric Comput. Inf. Sci. 2014, 4. [Google Scholar] [CrossRef]
- Cho, M.; Lee, I.-H. Optical image encryption and decryption considering wireless communication channels. J. Inf. Process. Syst. 2014, 10, 215–222. [Google Scholar]
- Peng, K. A secure network for mobile wireless service. J. Inf. Process. Syst. 2013, 9, 247–258. [Google Scholar] [CrossRef]
- Strohmeier, M.; Lenders, V.; Martinovic, I. Security of ADS-B: State of the art and beyond. 2013; arXiv:1307.3664v1. [Google Scholar]
- McCallie, D.; Butts, J.; Mills, R. Security analysis of the ADS-B implementation in the next generation air transportation system. Int. J. Crit. Infrastruct. Prot. 2011, 4, 78–87. [Google Scholar] [CrossRef]
- Wilhelm, M.; Martinovic, I. Short paper: Reactive jamming in wireless networks: How realistic is the threat? In Proceedings of the Fourth ACM Conference on Wireless Network Security, Hamburg, Germany, 14–17 June 2011; pp. 47–52.
- Schäfer, M.; Lenders, V.; Martinovic, I. Experimental analysis of attacks on next generation air traffic communication. In Applied Cryptography and Network Security, Proceedings of 11th International Conference, ACNS 2013; Banff, Canada, 25–28 June 2013, Jacobson, M., Locasto, M., Mohassel, P., Safavi-Naini, R., Eds.; Lecture Notes in Computer Science, Volume 7954; Springer: Berlin/Heidelberg, Germany, 2013; pp. 253–271. [Google Scholar]
- Pöpper, C.; Tippenhauer, N.O.; Danev, B.; Capkun, S. Investigation of signal and message manipulations on the wireless channel. In Computer Security-ESORICS 2011, Proceedings of 16th European Symposium on Research in Computer Security; Leuven, Belgium, 12–14 September 2011, Atluri, V., Diaz, C., Eds.; Lecture Notes in Computer Science, Volume 6879; Springer: Berlin/Heidelberg, Germany, 2011; pp. 40–59. [Google Scholar]
- Wilhelm, M.; Schmitt, J.B.; Lenders, V. Practical message manipulation attacks in IEEE 802.15.4 wireless networks. In Proceedings of MMB & DFT 2012, Kaiserslautern, Germany, 19–21 March 2012.
- Costin, A.; Francillon, A. Ghost in the Air (Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices. In Proceedings of Black Hat USA 2012, Las Vegas, NV, USA, 21–26 July 2012.
- Renderlab. Hackers + Airplanes = No Good Can Come Of This. In Proceedings of Defcon 20, Las Vegas, NV, USA, 26–29 July 2012.
- Orlando, V.A. Automatic Dependent Surveillance Broadcast (ADS-B). MIT Lincoln Laboratory. Available online: http://adsb.tc.faa.gov/WG3_Meetings/Meeting8/Squitter-Lon.pdf (accessed on 20 November 2014).
- Gnanaraj, J.W.K.; Ezra, K.; Rajsingh, E.B. Smart card based time efficient authentication scheme for global grid computing. Hum-centric Comput. Inf. Sci. 2013, 3, 1–14. [Google Scholar] [CrossRef]
- Chung, Y.; Choi, S.; Won, D. Lightweight anonymous authentication scheme with unlink ability in global mobility networks. J. Converg. 2013, 4, 23–29. [Google Scholar]
- Ellison, C.; Frantz, B.; Lampson, B.; Rivest, R.; Thomas, B.; Ylonen, T. SPKI Certificate Theory (RFC 2693). IETF, 1999. Available online: http://www.ietf.org/rfc/rfc2693.txt (accessed on 20 November 2014).
- Lee, Y.-L.; No, B.-N. SPKI/SDSI HTTP secure server to support role-based access control & confidential communication. J. Korea Inst. Inf. Secur. Cryptol. 2002, 12, 29–46. [Google Scholar]
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).