Internet Governance in the Context of Global Digital Contracts: Integrating SAR Data Processing and AI Techniques for Standards, Rules, and Practical Paths
Abstract
1. Introduction
2. Formulation of Standards and Rules for Internet Governance
2.1. Formulation of Internet Governance Standards
2.2. Transformer Architecture in SAR Data-Driven Applications
2.3. Formulation of Internet Governance Rules
2.4. Legal and Policy Development
2.4.1. Privacy Protection
2.4.2. Personal Information Protection
3. Practical Path of Internet Governance
3.1. International Cooperation and Multilateral Consultation
3.2. Data Privacy Protection
3.3. Transparency and Accountability
4. Experiments Related to Internet Governance
5. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Liu, J.; Liu, L.Y.; Tu, Y.; Li, S.X.; Li, Z.M. Multi-stage Internet public opinion risk grading analysis of public health emergencies: An empirical study on Microblog in COVID-19. Inf. Process. Manag. 2022, 59, 2–21. [Google Scholar] [CrossRef]
- Li, Z.; Zhang, W.Y.; Zhang, H.T.; Gao, R.; Fang, X.D. Global Digital Compact: A Mechanism for the Governance of Online Discriminatory and Misleading Content Generation. Int. J. Hum.-Comput. Interact. 2024, 3, 1381–1396. [Google Scholar] [CrossRef]
- Mancuso, I.; Petruzzelli, A.M.; Panniello, U. Digital business model innovation in metaverse: How to approach virtual economy opportunities. Inf. Process. Manag. 2023, 60, 103457. [Google Scholar] [CrossRef]
- Putz, B.; Dietz, M.; Empl, P.; Pernul, G. Ether Twin: Blockchain-based Secure Digital Twin Information Management. Inf. Process. Manag. 2021, 58, 102425. [Google Scholar] [CrossRef]
- Khan, S.D.; Basalamah, S. Multi-Branch Deep Learning Framework for Land Scene Classification in Satellite Imagery. Remote Sens. 2023, 15, 3408. [Google Scholar] [CrossRef]
- Wang, J.S.; Yang, G.H. Data-driven methods for stealthy attacks on TCP/IP-based networked control systems equipped with attack detectors. IEEE Trans. Cybern. 2018, 49, 3020–3031. [Google Scholar] [CrossRef]
- White, P.A. Cyberpeace: Why Internet Governance Matters for Global Peace and Stability. Peace Change 2019, 44, 441–467. [Google Scholar] [CrossRef]
- Tjahja, N.; Trisha, M.; Jamal, S. Who do you think you are? Individual stakeholder identification and mobility at the Internet Governance Forum. Telecommun. Policy 2022, 46, 102410–102411. [Google Scholar] [CrossRef]
- Flonk, D.; Markus, J.; Anke, S.O. Authority conflicts in internet governance: Liberals vs. sovereigntists? Glob. Const. 2020, 9, 364–386. [Google Scholar] [CrossRef]
- Malcic, S. Proteus online: Digital identity and the Internet governance industry. Convergence 2016, 24, 205–225. [Google Scholar] [CrossRef]
- Guan, S.; Xie, Y.; Zhai, Y.M. The Model Selection and Optimization of Global Internet Governance—Based on Reflection on the Multi stakeholder Model. Gov. Res. 2018, 35, 112–113. [Google Scholar]
- Zhang, J.W. How to Regulate Digital Financial Assets: Cryptocurrency and Smart Contracts—Review of the Draft Law on Digital Financial Assets of the Russian Federation. J. Shanghai Univ. Political Sci. Law Rule Law Ser. 2018, 33, 14–23. [Google Scholar]
- Jiang, L. New Trends and Policy Implications for Global Digital Economy Regulation. J. Beijing Norm. Univ. Soc. Sci. Ed. 2023, 3, 58–65. [Google Scholar]
- Wylde, A. The UN Global Digital Compact (GDC), Achieving a trusted, free, open, and Secure Internet: Trust-building. Eur. Conf. Cyber Warf. Secur. 2023, 22, 544–551. [Google Scholar] [CrossRef]
- Saravistha, D.B.; Sukadana, I.K.; Suryana, K.D. Urgency of Contract Model Settings in the Global Digital Market Related to Tourism Business: A Study on Consumer Protection and Electronic Information and Transactions. Bp. Int. Res. Crit. Inst.-J. BIRCI-J. 2022, 5, 4549–4556. [Google Scholar]
- Ong, J.P. The Enforceability of Digital Contract: A Comparative Analysis on Indonesia and New Zealand Law. Lawpreneurship J. 2021, 1, 30–42. [Google Scholar] [CrossRef]
- Tjahja, N.; Meyer, T.; Shahin, J. What is civil society and who represents civil society at the IGF? An analysis of civil society typologies in internet governance. Telecommun. Policy 2021, 45, 102141. [Google Scholar] [CrossRef]
- Cheung, M.; Chen, Z.T. Power, Freedom, and Privacy on a Discipline-and-Control Facebook, and the Implications for Internet Governance. IEEE Trans. Prof. Commun. 2022, 65, 467–484. [Google Scholar] [CrossRef]
- Abood, A.M.; Hussein, M.S.; Faisal, Z.G.; Tawfiq, Z.H. Design and simulation of video monitoring structure over TCP/IP system using MATLAB. Indones. J. Electr. Eng. Comput. Sci. 2021, 24, 1840–1845. [Google Scholar] [CrossRef]
- Wang, L.M. Harmony but Difference: The Rule Boundary and Application of Privacy and Personal Information. Leg. Rev. 2021, 39, 15–24. [Google Scholar]
- Feng, W.B.; Hong, Z.; Wu, L.F.; Fu, M.L. Overview of Network Protocol Recognition Technology. Comput. Appl. 2019, 39, 3604–3605. [Google Scholar]
- Zharova, A. Ensuring the information security of information communication technology users in Russia. Int. J. Cyber Criminol. 2019, 13, 255–269. [Google Scholar]
- Joseph, I.; Ituabhor, O.; Zhimwang, J.T.; Ikechi, R. Achievable Throughput over Mobile Broadband Network Protocol Layers: Practical Measurements and Performance Analysis. Int. J. Adv. Netw. Appl. 2022, 13, 5037–5044. [Google Scholar] [CrossRef]
- Raha, A.; Hajdini, I. Franchisees with multiple stakeholder roles: Perceptions and conflict in franchise networks. J. Strateg. Mark. 2022, 30, 160–179. [Google Scholar] [CrossRef]
- Daigo, E.; Kevin, F. Exploring the value sponsors co-create at a charity sport event: A multiple stakeholder perspective of sport value. Sport Manag. Rev. 2022, 25, 656–678. [Google Scholar] [CrossRef]
- Dai, L. On the Protection of Personal Privacy Rights in the Context of Digital Trade. Contemp. Law 2020, 34, 148–160. [Google Scholar]
- Isaak, J.; Hanna, M.J. User data privacy: Facebook, Cambridge Analytica, and privacy protection. Computer 2018, 51, 56–59. [Google Scholar] [CrossRef]
- Cheng, S. Multilateralism: A New Phenomenon in International Politics. J. Soc. Sci. Jilin Univ. 2020, 60, 127–133. [Google Scholar]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential privacy techniques for cyber physical systems: A survey. IEEE Commun. Surv. Tutor. 2019, 22, 746–789. [Google Scholar] [CrossRef]
- Feng, D.; Zhang, M.; Ye, Y. Research on location trajectory publishing technology based on differential Privacy Model. J. Electron. Inf. Technol 2020, 42, 74–88. [Google Scholar]
- Qiao, Z.; Yang, Q.; Zhou, Y.; Zhang, M. Improved secure transaction scheme with certificateless cryptographic primitives for IoT-based mobile payments. IEEE Syst. J. 2021, 16, 1842–1850. [Google Scholar] [CrossRef]
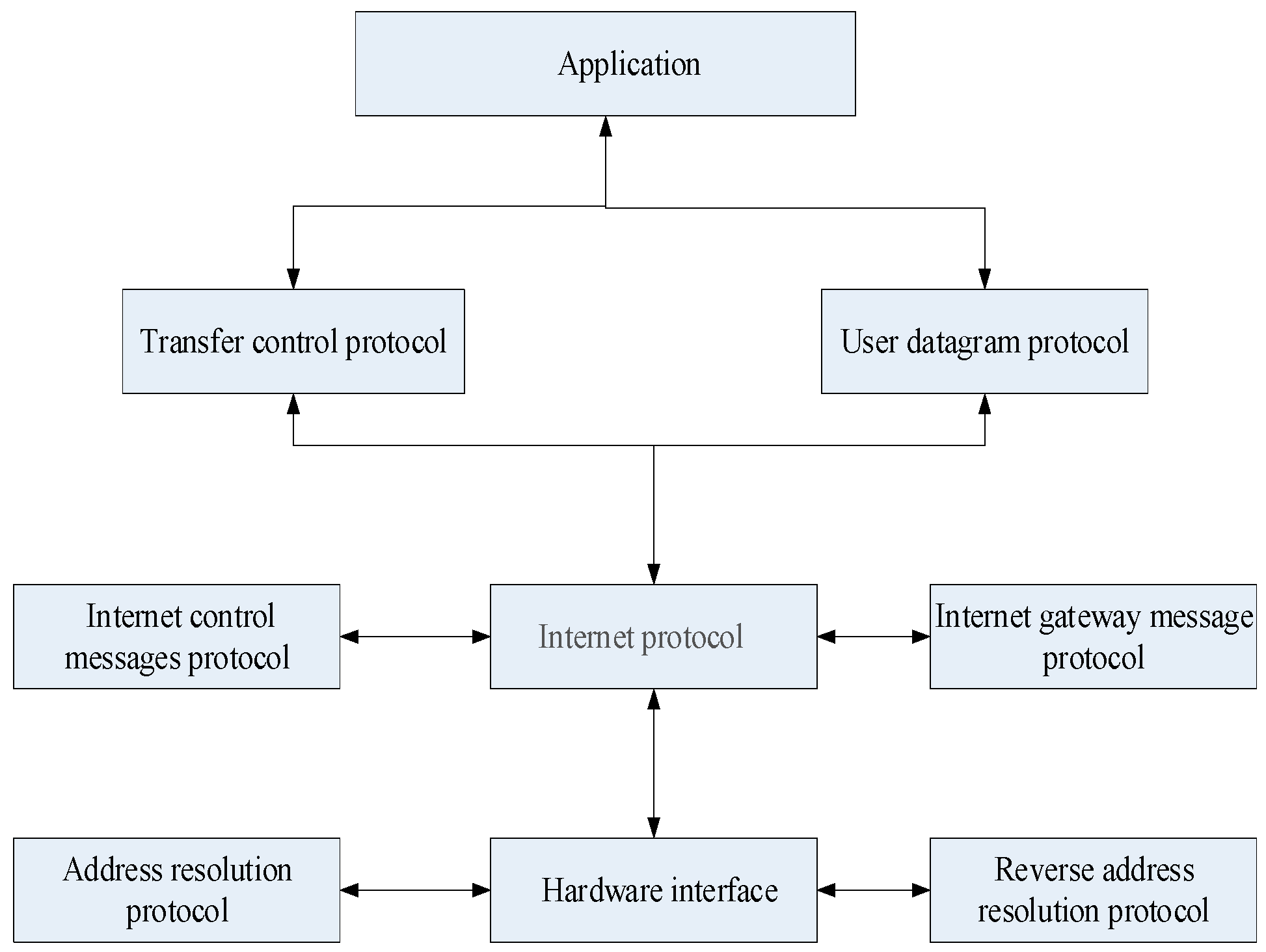
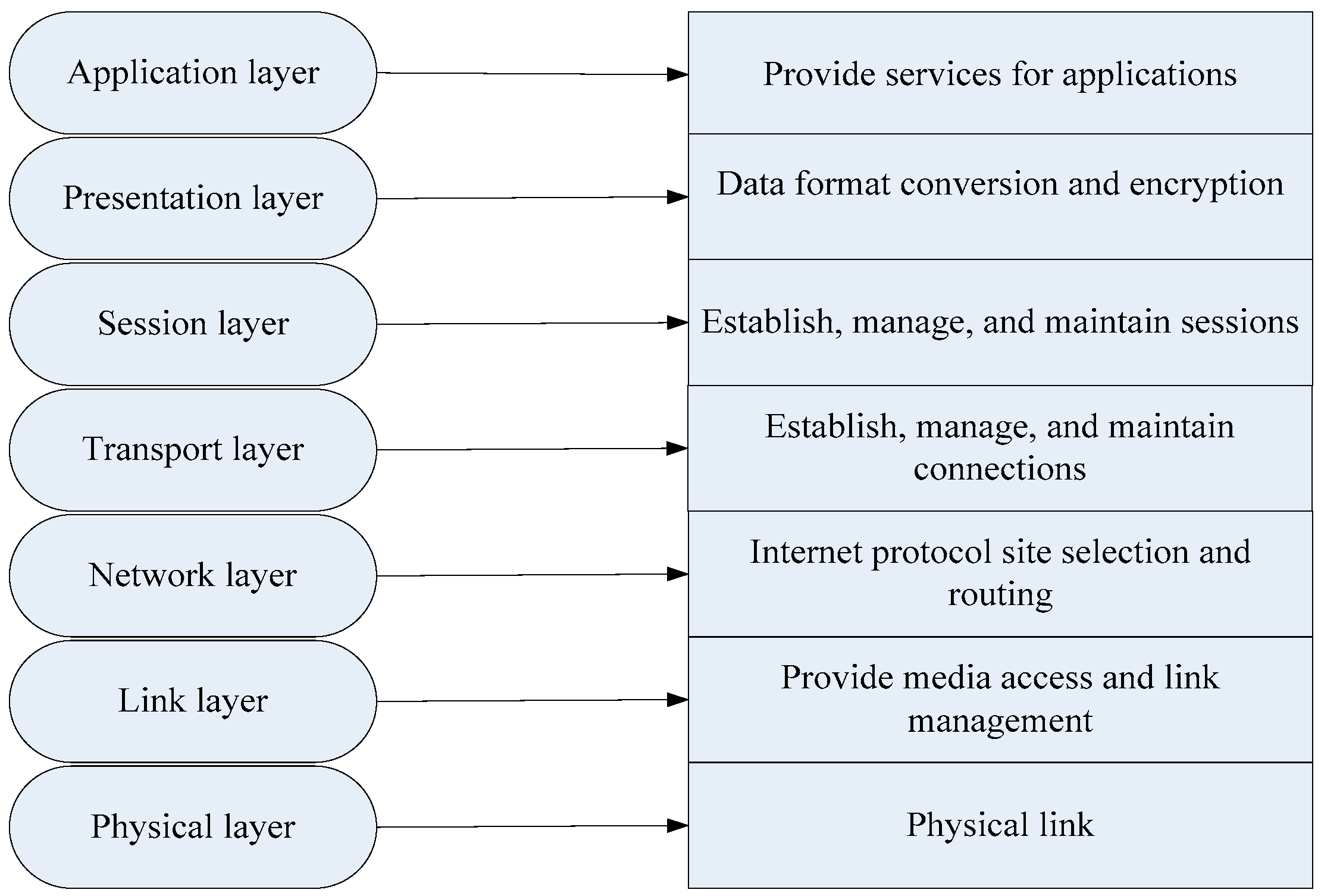
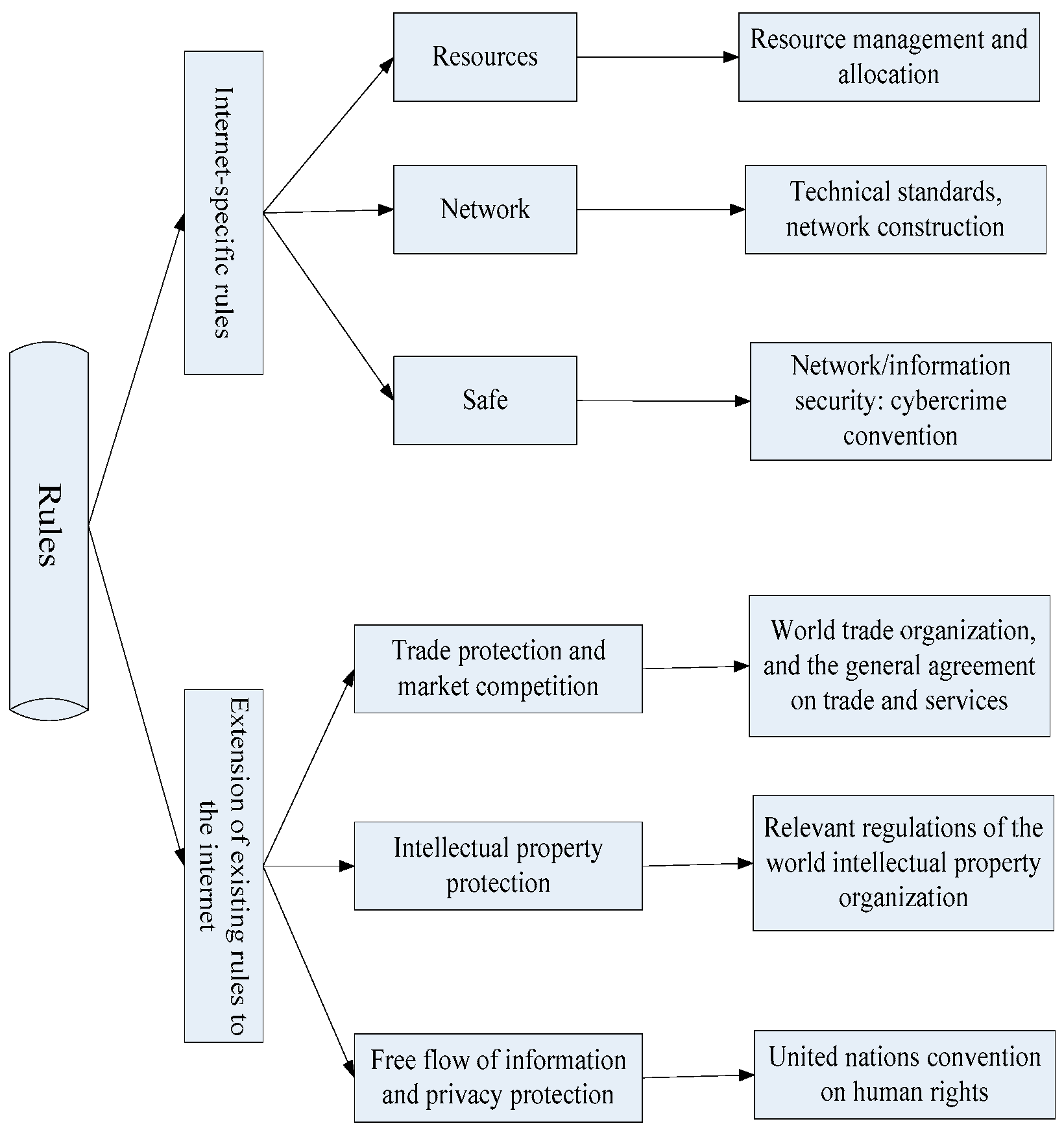
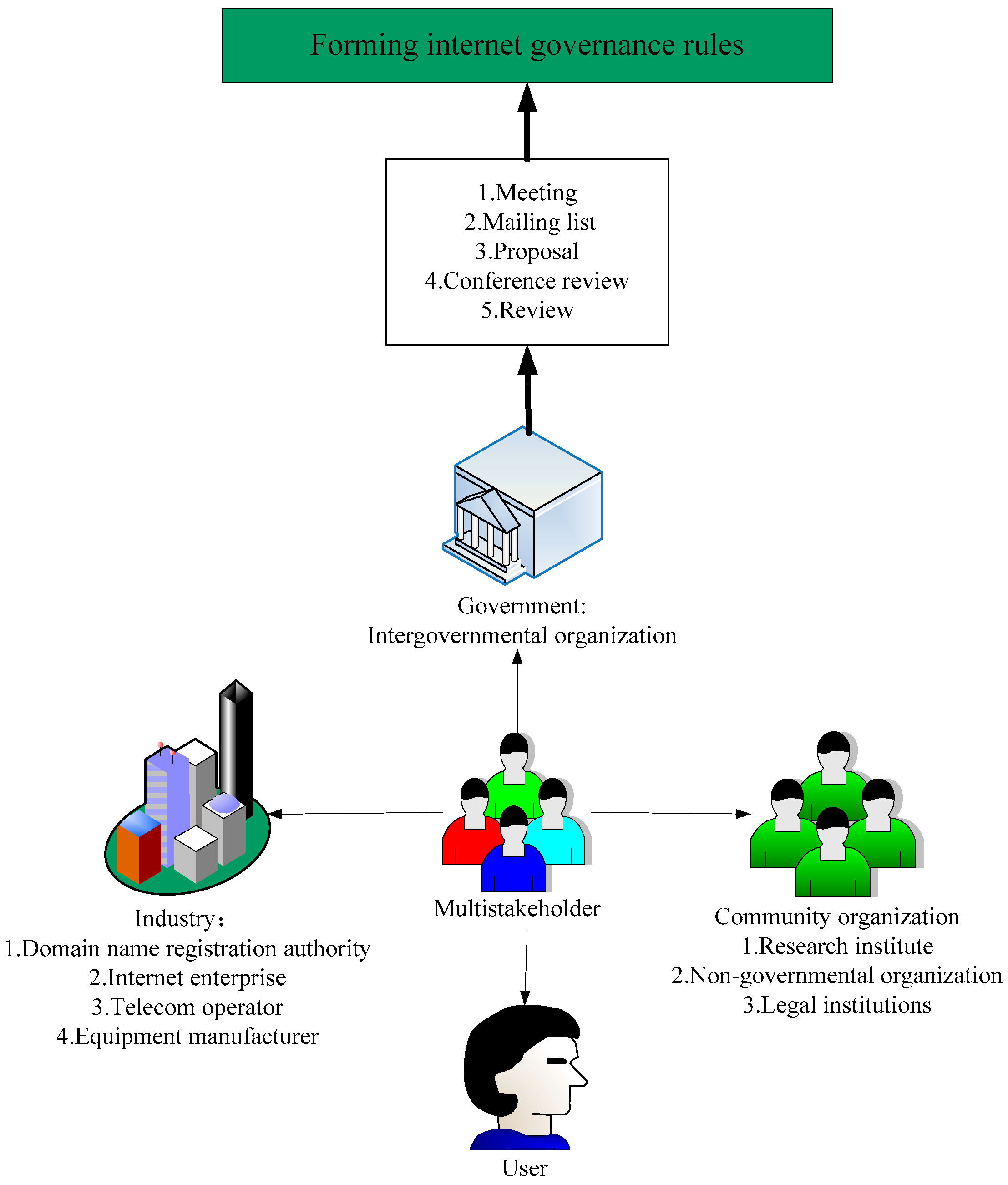
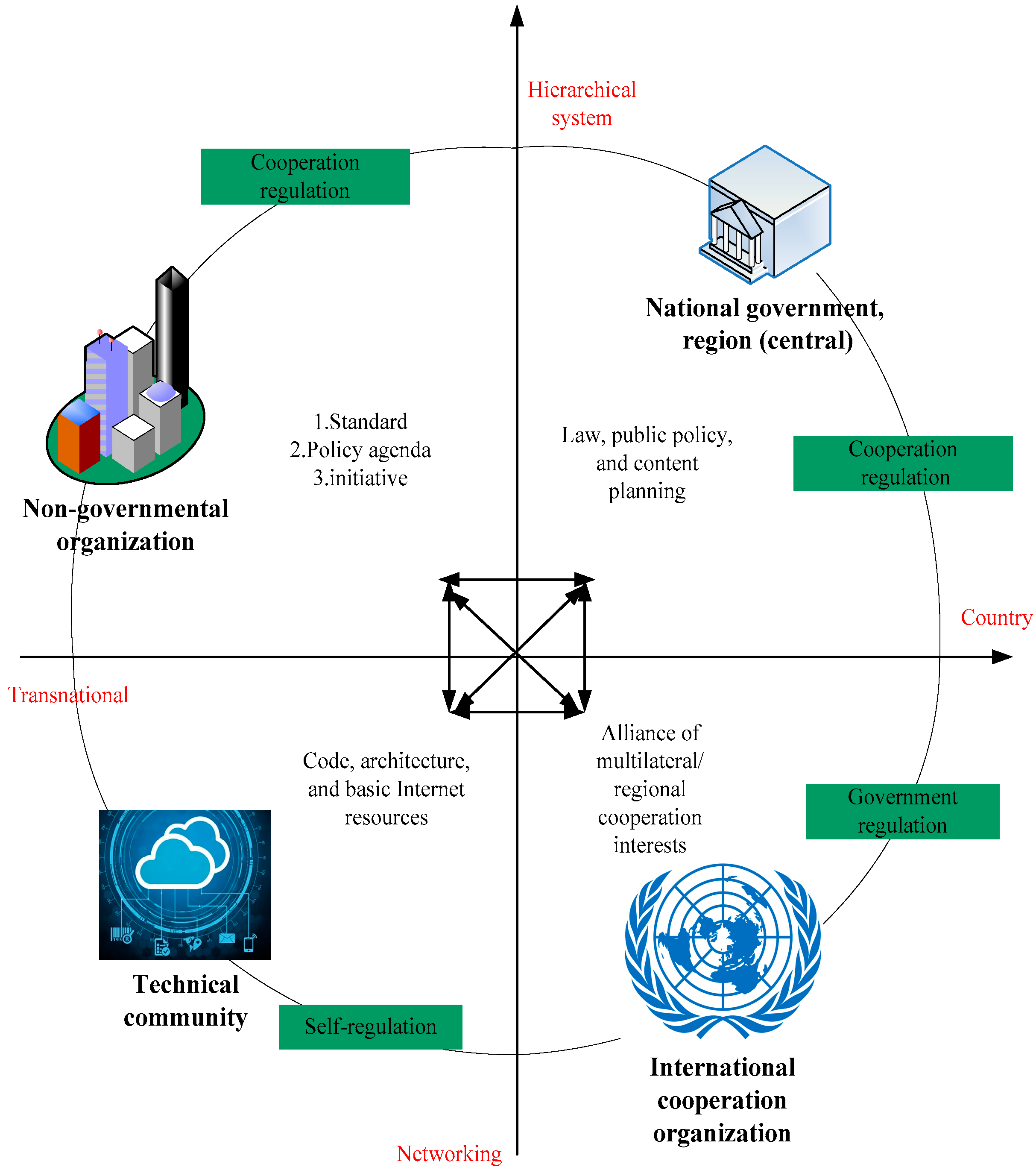
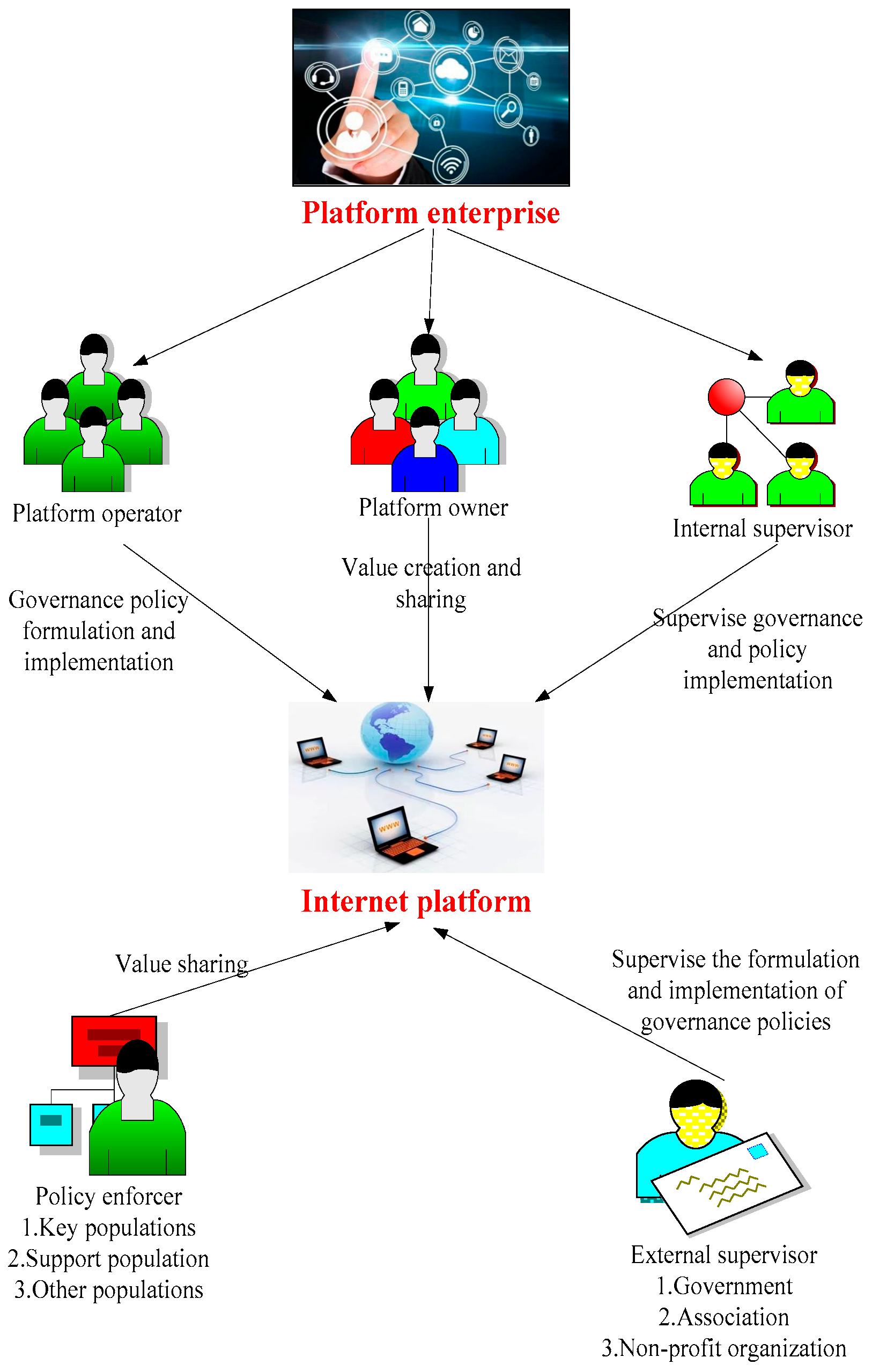

| Functional Area | Task | Main Behavior Subject |
| Key internet resources | Central supervision of domain names and addresses | Number internet name and word address allocation agency, the internet number administration |
| Technology and design of IP addresses | Internet engineering task force | |
| Domain name allocation | Internet registration authority | |
| Automatic digital distribution system | Internet numbering authority and regional internet registration | |
| IP address allocation | Regional internet registration, local internet registration, internet numbering authority | |
| Setting up internet standards | Protocol number distribution | Internet numbering authority |
| Core internet standard design | Internet engineering task force | |
| Core web page standard design | Internet alliance | |
| Access and connection coordination | Multi-layer network interconnection | Internet exchange center and network operator |
| Network management | Private network operator | |
| Access management | National government | |
| Network security governance | Network infrastructure security | Operator |
| Encryption standard design | Standard-setting agency | |
| Network security management | National governments and multilateral protocols | |
| Software security vulnerability repair | Software company | |
| Software patch management | End user | |
| Routing and address security | Operator and registrar | |
| Website security certification | Certification body | |
| Information transmission | Commercial trading institutions | E-commerce agency |
| Content review | Search engines and social media | |
| Private policy | Social networks and service providers | |
| Manage privacy and speech | Law and constitution |
| Number | Legal Dilemma | Category | Explain |
|---|---|---|---|
| 1 | The dilemma in legislation | Lawmaking lags behind the development of internet governance | The legal system of network governance is still being improved. |
| Imbalance of rights of the internet governance platform | 1. There is a lack of statutory rules to divide the power of different attributes. 2. The scientific structure of the authority and responsibility of the network platform is lacking. | ||
| 2 | The dilemma of regulatory enforcement | There is a problem with the supervision system of administrative outsourcing | 1. The division of authority within the government is not clear. 2. Regulatory and law enforcement agencies are not scientific enough in setting up. |
| Imperfect regulatory mechanism | The prevention mechanism is not sound. | ||
| Complex regulatory and law enforcement environment | 1. Sufficient culture of the rule of law in cyberspace has not been established. 2. The pattern of collaborative governance of network information content needs to be strengthened. | ||
| 3 | Insufficient privacy protection | Data collection infringes on citizens’ privacy rights | Internet platforms pose a threat to users’ privacy rights during data collection. |
| Governance platform infringes on privacy | With the continuous development of the internet, violations of rights that have brought physical and mental trauma to different groups of people are more common, infringing on the privacy rights of consumers. | ||
| Problems in the data security protection phase | The instability of the internet has led internet companies to infringe on consumer privacy. |
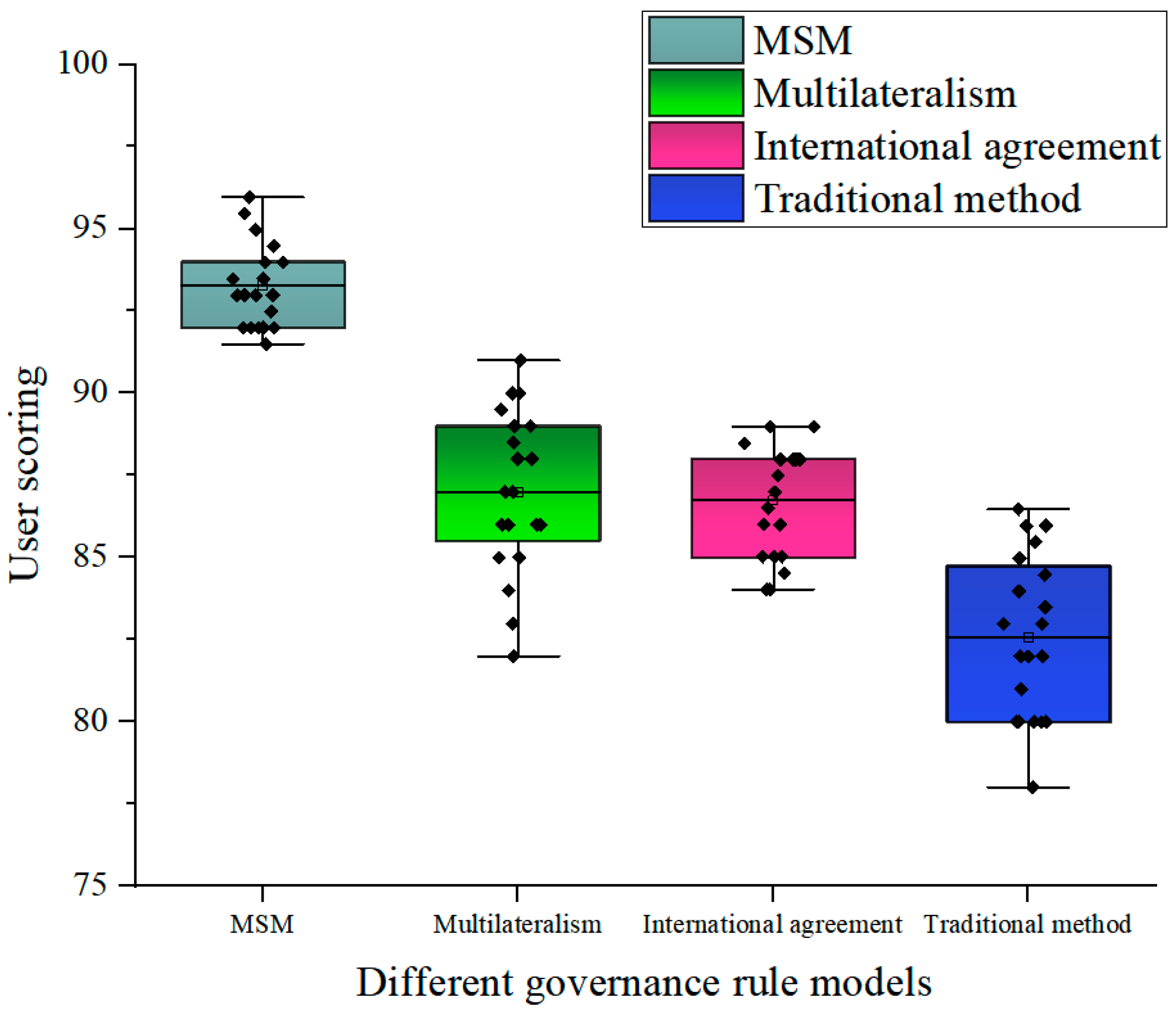
| Number | OSI | Multilateralism | International Protocol | Traditional Method |
|---|---|---|---|---|
| 1 | 9.2 | 8.4 | 8.5 | 8.2 |
| 2 | 9.3 | 8.5 | 8.6 | 8.6 |
| 3 | 9.4 | 8.5 | 8.8 | 8.4 |
| 4 | 9.3 | 8.7 | 8.5 | 8.6 |
| 5 | 9.2 | 8.9 | 8.5 | 8.6 |
| 6 | 9.1 | 8.8 | 8.85 | 8.5 |
| 7 | 9.1 | 8.8 | 8.95 | 8.4 |
| 8 | 9.1 | 8.4 | 8.8 | 8.3 |
| 9 | 9.3 | 8.6 | 8.6 | 8.6 |
| 10 | 9 | 8.7 | 8.75 | 8.4 |
| 11 | 9.1 | 8.7 | 8.85 | 8.5 |
| 12 | 9.2 | 8.6 | 8.4 | 8.5 |
| 13 | 9.2 | 8.5 | 8.65 | 8.6 |
| 14 | 9.3 | 8.5 | 8.45 | 8.7 |
| 15 | 9.2 | 8.4 | 8.7 | 8.3 |
| Average value | 9.2 | 8.6 | 8.66 | 8.48 |
| Evaluation Metrics | Transformer + SAR | CNN | BiLSTM | SVM | RF |
|---|---|---|---|---|---|
| Feature Extraction Accuracy (%) | 96.2 | 90.5 | 88.7 | 82.4 | 89.1 |
| Load Forecast Error (MAE) | 3 | 4.9 | 3.6 | 6.8 | 5.7 |
| Anomaly Warning Response Time (ms) | 16.8 | 28.3 | 23.5 | 40.2 | 34.7 |
| Encryption Compatibility (%) | 91.5 | 78.6 | 75.3 | 62.5 | 73.8 |
| Spatial Feature Long-Distance Correlation Capture Rate (%) | 93.8 | 72.6 | 76.4 | 56.8 | 70.3 |
| Multi-Source Data Fusion Efficiency (GB/s) | 2.6 | 1.7 | 2.1 | 1 | 1.4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fu, X.; Zhang, W.; Li, Z. Internet Governance in the Context of Global Digital Contracts: Integrating SAR Data Processing and AI Techniques for Standards, Rules, and Practical Paths. Information 2025, 16, 697. https://doi.org/10.3390/info16080697
Fu X, Zhang W, Li Z. Internet Governance in the Context of Global Digital Contracts: Integrating SAR Data Processing and AI Techniques for Standards, Rules, and Practical Paths. Information. 2025; 16(8):697. https://doi.org/10.3390/info16080697
Chicago/Turabian StyleFu, Xiaoying, Wenyi Zhang, and Zhi Li. 2025. "Internet Governance in the Context of Global Digital Contracts: Integrating SAR Data Processing and AI Techniques for Standards, Rules, and Practical Paths" Information 16, no. 8: 697. https://doi.org/10.3390/info16080697
APA StyleFu, X., Zhang, W., & Li, Z. (2025). Internet Governance in the Context of Global Digital Contracts: Integrating SAR Data Processing and AI Techniques for Standards, Rules, and Practical Paths. Information, 16(8), 697. https://doi.org/10.3390/info16080697






