A Systematic Literature Review on Cyber Security and Privacy Risks in MaaS (Mobility-as-a-Service) Systems
Abstract
:1. Introduction
- Unlike previous SLRs that relied on keywords such as “privacy” or “data privacy” in their search strategies, we deliberately excluded these terms and instead applied carefully designed inclusion and exclusion criteria to identify relevant papers. This approach allowed us to capture a broader and more diverse set of studies, including those where security and privacy concerns were discussed but not the central focus;
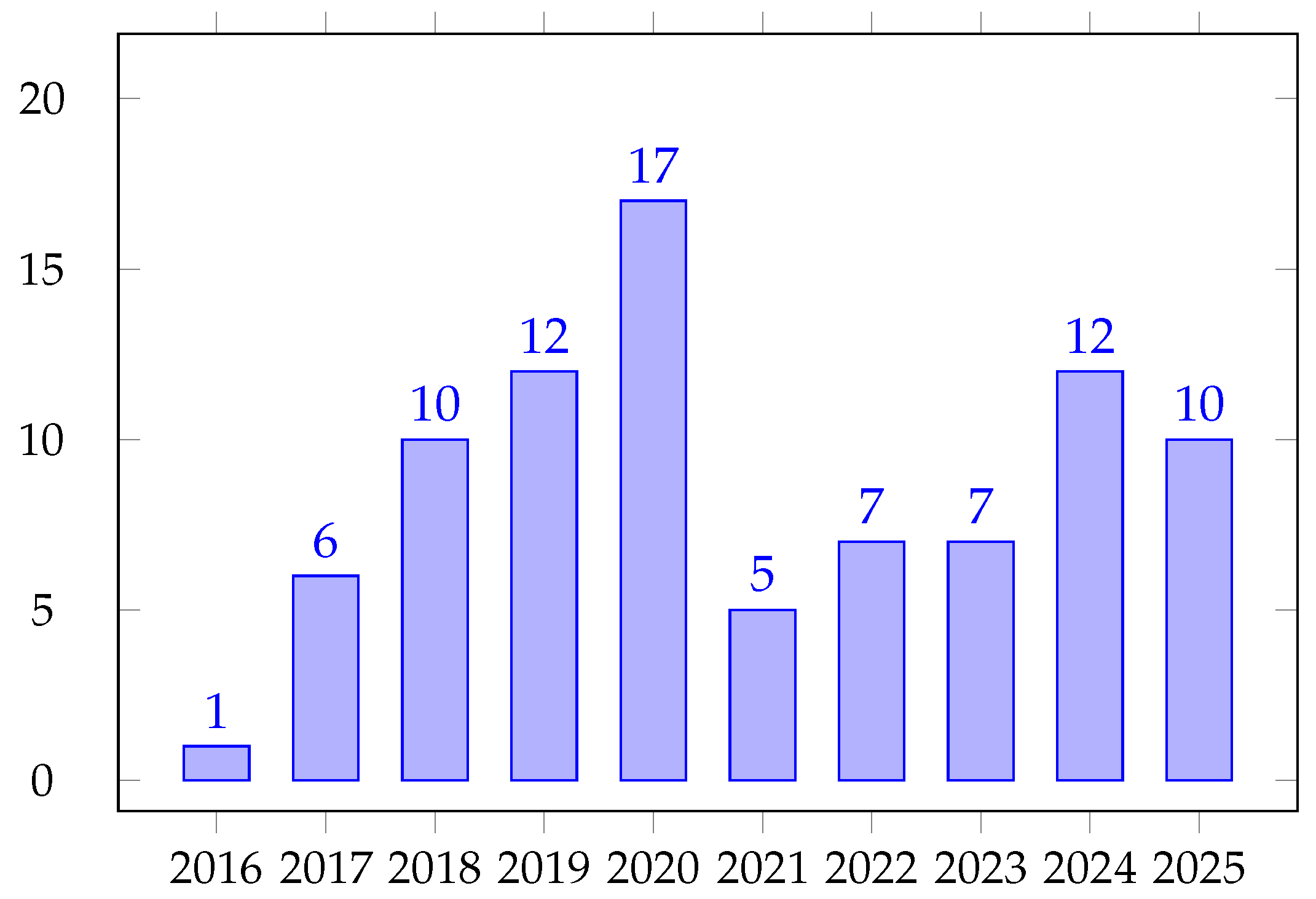
- A Higher Volume of Reviewed Literature: We reviewed 87 publications, substantially more than most previous SLRs, providing a more comprehensive and nuanced understanding of the field;
- Differentiation Between Researcher and User Perspectives: Our review is the first to explicitly compare risks highlighted by MaaS researchers with those identified by end users, exposing a gap between the technical focus and users’ concerns. This comparison lays the foundation for future research on privacy awareness, trust, and technology acceptance among MaaS users;
- Consideration of Driver Privacy: In contrast to most prior studies that focus exclusively on passengers, we also acknowledge and analyze privacy risks for drivers, recognizing their vulnerabilities within the MaaS ecosystem;
- Coverage of Non-Technical Issues: In addition to technical threats, our review includes non-technical concerns, such as regulatory gaps, standardization challenges, and governance issues, which are often overlooked in technical SLRs.
2. Materials and Methods
- Identification of relevant records and removal of duplicate records and non-English records;
- Screening the identified records based on the inclusion and exclusion criteria and conducting further eligibility assessment;
- Final selection of eligible records to be included in the final study.
2.1. Databases
2.2. Keywords
2.3. Inclusion and Exclusion Criteria
2.4. Final Paper Selection
2.5. Encoding Data Items
3. Results
3.1. Description of Main Themes and Subthemes
3.2. Cyber Security and/or Privacy Risks of MaaS Systems
3.2.1. Privacy Risks
- Subtheme 1: Profiling and inference
- Subtheme 2: Third-party access and data sharing
3.2.2. Security Risks
- Subtheme 1: Technical security threats/risks
- Subtheme 2: Non-technical security threats/risks
3.2.3. Existing Cyber Security Solutions for MaaS Systems
Blockchain-Based Solutions
Non-Blockchain-Based Solutions for Privacy Preservation
3.3. Users’ Cyber Security and Privacy Concerns and Their Impacts on the Willingness to Adopt MaaS
3.3.1. Users’ Cyber Security and Privacy Concerns
3.3.2. Impacts of Privacy/Security Concerns on MaaS Adoption
Negative Impacts on MaaS Adoption
No Impact on MaaS Adoption
3.4. Policies and Regulations
3.4.1. Privacy Regulations
GDPR
Overview of Other Privacy Laws and Regulations in MaaS
Implications of Privacy Laws and Regulations for MaaS Service Providers
3.4.2. Organizational Policies
- The company has a policy to protect users’ data privacy;
- The company shares or sells sensitive private data without users’ consent or transparency;
- The company uses and processes sensitive private data without users’ consent or users’ access to the data’s content and purposes;
- The company’s use of private data complies with local laws;
- If no regulation exists, the company does not collect, process, share, store, resell, or use sensitive data;
- The company has a PDCA process in place to exceed the minimum legal standard;
- The company has established a grievance mechanism.
4. Further Discussion
4.1. Cyber Security and Privacy Risks Associated with the Use of MaaS Systems and Solutions Proposed to Address Them (RQ1 and RQ3)
- Systematically investigating the scale and landscape of cyber security and privacy risks of MaaS systems;
- Further clarifying the relationship between cyber security and privacy in the context of MaaS;
- Establishing a more comprehensive understanding of the technical requirements for mitigating cyber security and privacy risks of MaaS systems.
4.2. Cyber Security and Privacy Concerns That Users Have Regarding the Use of MaaS Systems (RQ2)
- Systematically defining and comparing cyber security and privacy concerns from different stakeholders’ perspectives;
- Conducting privacy awareness studies among MaaS users to assess and improve their awareness;
- Investigating the impacts of cyber security and privacy concerns on MaaS adoption in a more comprehensive and nuanced approach, considering both technical and user-related aspects.
4.3. Legal Issues Regarding the Privacy of Personal Data Processed Using MaaS Systems (RQ4)
- Systematically examining the GDPR compatibility of MaaS systems, considering all the elements of the GDPR, with a particular focus on data subjects’ rights;
- Exploring the components essential for an organizational policy dedicated to addressing cyber security and privacy issues specific to MaaS;
- Researching sharing policies that encourage innovation while also ensuring the security of service providers and users;
- Researching indicators to be used to assess data privacy practices of MaaS service providers.
4.4. Limitations
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| MaaS | Mobility as a Service |
| SLR | Systematic Literature Review |
| ICT | Information and Communication Technology |
| GDPR | General Data Protection and Regulation |
References
- Newman, P.W.; Kenworthy, J.R. The land use—Transport connection: An overview. Land Use Policy 1996, 13, 1–22. [Google Scholar] [CrossRef]
- Butler, L.; Yigitcanlar, T.; Paz, A. Barriers and risks of Mobility-as-a-Service (MaaS) adoption in cities: A systematic review of the literature. Cities 2021, 109, 103036. [Google Scholar] [CrossRef]
- Hietanen, S. Mobility as a Service. New Transp. Model 2014, 12, 2–4. [Google Scholar]
- Goodall, W.; Dovey, T.; Bornstein, J.; Bonthron, B. The rise of mobility as a service. Deloitte Rev. 2017, 20, 112–129. [Google Scholar]
- Pagoni, I.; Gatto, M.; Tsouros, I.; Tsirimpa, A.; Polydoropoulou, A.; Galli, G.; Stefanelli, T. Mobility-as-a-service: Insights to policymakers and prospective MaaS operators. Transp. Lett. 2022, 14, 356–364. [Google Scholar] [CrossRef]
- Audouin, M.; Finger, M. The development of Mobility-as-a-Service in the Helsinki metropolitan area: A multi-level governance analysis. Res. Transp. Bus. Manag. 2018, 27, 24–35. [Google Scholar] [CrossRef]
- Sochor, J.; Arby, H.; Karlsson, I.M.; Sarasini, S. A topological approach to Mobility as a Service: A proposed tool for understanding requirements and effects, and for aiding the integration of societal goals. Res. Transp. Bus. Manag. 2018, 27, 3–14. [Google Scholar] [CrossRef]
- Pham, H.D.; Shimizu, T.; Nguyen, T.V. A Literature Review on Interactions Between Stakeholders Through Accessibility Indicators Under Mobility as a Service Context. Int. J. Intell. Transp. Syst. Res. 2021, 19, 468–476. [Google Scholar] [CrossRef]
- Arias-Molinares, D.; García-Palomares, J.C. The Ws of MaaS: Understanding mobility as a service from a literature review. J. Int. Assoc. Traffic Saf. Sci. (IATSS) 2020, 44, 253–263. [Google Scholar] [CrossRef]
- Jittrapirom, P.; Marchau, V.; van der Heijden, R.; Meurs, H. Dynamic adaptive policymaking for implementing Mobility-as-a Service (MaaS). Res. Transp. Bus. Manag. 2018, 27, 46–55. [Google Scholar] [CrossRef]
- Mulley, C.; Kronsell, A. Workshop 7 report: The “uberisation” of public transport and mobility as a service (MaaS): Implications for future mainstream public transport. Res. Transp. Econ. 2018, 69, 568–572. [Google Scholar] [CrossRef]
- Kayikci, Y.; Kabadurmus, O. Barriers to the adoption of the mobility-as-a-service concept: The case of Istanbul, a large emerging metropolis. Transp. Policy 2022, 129, 219–236. [Google Scholar] [CrossRef]
- Gebhart, J.; Schlick, S.; Marvell, A. Analysing Barriers in the Business Ecosystem of European MaaS Providers: An Actor-Network Approach. EPiC Ser. Comput. 2023, 93, 68–81. [Google Scholar] [CrossRef]
- Maas, B. Literature Review of Mobility as a Service. Sustainability 2022, 14, 8962. [Google Scholar] [CrossRef]
- Zhang, Y.; Kamargianni, M. A review on the factors influencing the adoption of new mobility technologies and services: Autonomous vehicle, drone, micromobility and mobility as a service. Transp. Rev. 2023, 43, 407–429. [Google Scholar] [CrossRef]
- Natvig, M.K.; Stav, E.; Vennesland, A. Systematic mapping of scientific publications on maas. Manag. Rev. Q. 2025, 75, 83–118. [Google Scholar] [CrossRef]
- Anthony, B.; Sarshar, S. Enhancing data sovereignty to improve intelligent mobility services in smart cities. Urban Gov. 2025, 5, 20–31. [Google Scholar] [CrossRef]
- Garroussi, Z.; Legrain, A.; Gambs, S.; Gautrais, V.; Sansò, B. Data privacy for Mobility as a Service. arXiv 2023. [Google Scholar] [CrossRef]
- Garroussi, Z.; Legrain, A.; Gambs, S.; Gautrais, V.; Sansò, B. A systematic review of data privacy in Mobility as a Service (MaaS). Transp. Res. Interdiscip. Perspect. 2025, 31, 101254. [Google Scholar] [CrossRef]
- Ekpo, O.; Casola, V.; De Benedictis, A. Security and Privacy Issues in Mobility-as-a-Service (MaaS): A Systematic Review. In Proceedings of the 2024 19th Annual System of Systems Engineering Conference (SoSE), Tacoma, WA, USA, 23–26 June 2024; pp. 300–307. [Google Scholar]
- Kaur, H.; Pannu, H.S.; Malhi, A.K. A Systematic Review on Imbalanced Data Challenges in Machine Learning: Applications and Solutions. ACM Comput. Surv. 2019, 52, 1–36. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. Syst. Rev. 2021, 10, 1–11. [Google Scholar] [CrossRef] [PubMed]
- Bar-Ilan, J. Tale of three databases: The implication of coverage demonstrated for a sample query. Front. Res. Metrics Anal. 2018, 3, 6. [Google Scholar] [CrossRef]
- Haddaway, N.R.; Collins, A.M.; Coughlin, D.; Kirk, S. The Role of Google Scholar in Evidence Reviews and its Applicability to Grey Literature Searching. PLoS ONE 2015, 10, e0138237. [Google Scholar] [CrossRef]
- Yasin, A.; Fatima, R.; Wen, L.; Afzal, W.; Azhar, M.; Torkar, R. On Using Grey Literature and Google Scholar in Systematic Literature Reviews in Software Engineering. IEEE Access 2020, 8, 36226–36243. [Google Scholar] [CrossRef]
- Cottrill, C.D. MaaS surveillance: Privacy considerations in mobility as a service. Transp. Res. Part A Policy Pract. 2020, 131, 50–57. [Google Scholar] [CrossRef]
- Barreto, L.; Amaral, A.; Baltazar, S. Urban Mobility Digitalization: Towards Mobility as a Service (MaaS). In Proceedings of the 2018 International Conference on Intelligent Systems, Madeira, Portugal, 25–27 September 2018; pp. 850–855. [Google Scholar] [CrossRef]
- Costantini, F.; Archetti, E.; Di Ciommo, F.; Ferencz, B. IoT, Intelligent Transport Systems and MaaS (Mobility as a Service). Jusletter IT 21. 2019. Available online: https://cambiamo.net/wp-content/uploads/2019/07/Costantini-et-al.-2019-IoT-intelligent-transport-systems-and-MaaS-mobility-as-a-service.pdf (accessed on 5 June 2025).
- Cooper, P.; Tryfonas, T.; Crick, T.; Marsh, A. Electric vehicle mobility-as-a-service: Exploring the “Tri-Opt” of novel private transport business models. J. Urban Technol. 2019, 26, 35–56. [Google Scholar] [CrossRef]
- Kong, Q.; Lu, R.; Yin, F.; Cui, S. Blockchain-based Privacy-preserving Driver Monitoring for MaaS in the Vehicular IoT. IEEE Trans. Veh. Technol. 2021, 70, 3788–3799. [Google Scholar] [CrossRef]
- Belletti, F.; Bayen, A.M. Privacy-preserving MaaS fleet management. Transp. Res. Procedia 2017, 23, 1000–1024. [Google Scholar] [CrossRef]
- Callegati, F.; Giallorenzo, S.; Melis, A.; Prandini, M. Cloud-of-Things meets Mobility-as-a-Service: An insider threat perspective. Comput. Secur. 2018, 74, 277–295. [Google Scholar] [CrossRef]
- Pitera, K.; Marinelli, G. Autonomous E-Mobility as a Service-Final Report; Technical Report Report 3/2017 NTNU IBM; NTNU: Trondheim, Norway, 2017. [Google Scholar]
- He, B.Y.; Chow, J.Y.J. Gravity Model of Passenger and Mobility Fleet Origin–Destination Patterns with Partially Observed Service Data. Transp. Res. Rec. 2021, 2675, 235–253. [Google Scholar] [CrossRef]
- Merkert, R.; Bushell, J.; Beck, M.J. Collaboration as a service (CaaS) to fully integrate public transportation–Lessons from long distance travel to reimagine mobility as a service. Transp. Res. Part A Policy Pract. 2020, 131, 267–282. [Google Scholar] [CrossRef]
- Mukhtar-Landgren, D.; Smith, G. Perceived action spaces for public actors in the development of Mobility as a Service. Eur. Transp. Res. Rev. 2019, 11, 32. [Google Scholar] [CrossRef]
- Araghi, Y.; Larco, N.; Bouma, G.; Doll, C.; Vonk Noordegraaf, D.; Krauß, K. Drivers and Barriers of Mobility-as-a-Service in urban areas. In Proceedings of the 8th Transport Research Arena Conference (TRA) 2020, Helsinki, Finland, 27–30 April 2020. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhang, N. A Novel Development Scheme of Mobility as a Service: Can It Provide a Sustainable Environment for China? Sustainability 2021, 13, 4233. [Google Scholar] [CrossRef]
- Utriainen, R.; Pöllänen, M. Review on mobility as a service in scientific publications. Res. Transp. Bus. Manag. 2018, 27, 15–23. [Google Scholar] [CrossRef]
- Thai, J.; Yuan, C.; Bayen, A.M. Resiliency of Mobility-as-a-Service Systems to Denial-of-Service attacks. IEEE Trans. Control Netw. Syst. 2018, 5, 370–382. [Google Scholar] [CrossRef]
- Vaidya, B.; Mouftah, H.T. Security for Shared Electric and Automated Mobility Services in Smart Cities. IEEE Secur. Priv. 2020, 19, 24–33. [Google Scholar] [CrossRef]
- Callegati, F.; Delnevo, G.; Melis, A.; Mirri, S.; Prandini, M.; Salomoni, P. I want to ride my bicycle: A microservice-based use case for a MaaS architecture. In Proceedings of the 2017 IEEE Symposium on Computers and Communications, Heraklion, Greece, 3–6 July 2017; pp. 18–22. [Google Scholar] [CrossRef]
- Callegati, F.; Giallorenzo, S.; Melis, A.; Prandini, M. Insider Threats in Emerging Mobility-as-a-Service Scenarios. In Proceedings of the 50th Hawaii International Conference on System Science, Waikoloa, HI, USA, 4–7 January 2017; University of Hawaii: Manoa, HI, USA, 2017. [Google Scholar]
- Mouhibbi, L.; Elhozmari, M.; Ettalbi, A. Sorting and persisting REST and SOAP client for MaaS based architecture. In Proceedings of the 2018 6th International Conference on Multimedia Computing and Systems, Rabat, Morocco, 10–12 May 2018. [Google Scholar] [CrossRef]
- Carvalho, G.; Cabral, B.; Pereira, V.; Bernardino, J. A Case for Machine Learning in Edge-Oriented Computing to Enhance Mobility as a Service. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems, Santorini Island, Greece, 29–31 May 2019; pp. 530–537. [Google Scholar] [CrossRef]
- Cruz, C.O.; Sarmento, J.M. “Mobility as a service” Platforms: A Critical Path towards Increasing the Sustainability of Transportation Systems. Sustainability 2020, 12, 6368. [Google Scholar] [CrossRef]
- Alyavina, E.; Nikitas, A.; Njoya, E.T. Mobility as a service and sustainable travel behaviour: A thematic analysis study. Transp. Res. Part F Traffic Psychol. Behav. 2020, 73, 362–381. [Google Scholar] [CrossRef]
- Nguyen, T.H.; Partala, J.; Pirttikangas, S. Blockchain-Based Mobility-as-a-Service. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks, Valencia, Spain, 29 July–1 August 2019. [Google Scholar] [CrossRef]
- Chinaei, M.H.; Hossein Rashidi, T.; Waller, T. Digitally transferable ownership of mobility-as-a-service systems using blockchain and smart contracts. Transp. Lett. 2022, 20, 54–61. [Google Scholar] [CrossRef]
- Bothos, E.; Magoutas, B.; Arnaoutaki, K.; Mentzas, G. Leveraging Blockchain for Open Mobility-as-a-Service Ecosystems. In Proceedings of the 2019 IEEE/WIC/ACM International Conference on Web Intelligence—Companion Volume, Thessaloniki, Greece, 14–17 October 2019; pp. 292–296. [Google Scholar] [CrossRef]
- Casady, C.B. Customer-led mobility: A research agenda for Mobility-as-a-Service (MaaS) enablement. Case Stud. Transp. Policy 2020, 8, 1451–1457. [Google Scholar] [CrossRef]
- Kulla, E.; Barolli, L.; Matsuo, K.; Ikeda, M. Blockchain Applications for Mobility-as-a-Service Ecosystem: A Survey. In Proceedings of the Advances in Internet, Data & Web Technologies: The 11th International Conference on Emerging Internet, Data & Web Technologies (EIDWT-2023), Semarang, Indonesia, 23–25 February 2023; Springer: Berlin/Heidelberg, Germany, 2023; pp. 129–140. [Google Scholar] [CrossRef]
- Campolo, C.; Cuzzocrea, D.; Genovese, G.; Iera, A.; Molinaro, A. An OMA Lightweight M2M-compliant MEC Framework to Track Multi-modal Commuters for MaaS Applications. In Proceedings of the 2019 IEEE/ACM 23rd International Symposium on Distributed Simulation and Real Time Applications, Cosenza, Italy, 7–9 October 2019. [Google Scholar] [CrossRef]
- Katsaros, K.V.; Amditis, A.J.; Trichias, K.; Shagdar, O.; Soua, A.; Requena, J.C.; Santa, J.; Kakes, G.; Almeida, J.; Sousa, E.; et al. Connected and Automated Mobility Services in 5G Cross-Border Environments: Challenges and Prospects. IEEE Intell. Transp. Syst. Mag. 2023, 15, 145–157. [Google Scholar] [CrossRef]
- Campolo, C.; Genovese, G.; Molinaro, A.; Pizzimenti, B. Digital Twins at the Edge to Track Mobility for MaaS Applications. In Proceedings of the 2020 IEEE/ACM 24th International Symposium on Distributed Simulation and Real Time Applications, Prague, Czech Republic, 14–16 September 2020. [Google Scholar] [CrossRef]
- Christiaanse, R. Mobility as a Service. In Proceedings of the Companion Proceedings of the 2019 World Wide Web Conference, San Francisco, CA, USA, 13–17 May 2019; pp. 83–92. [Google Scholar] [CrossRef]
- Polydoropoulou, A.; Pagoni, I.; Tsirimpa, A. Ready for Mobility as a Service? Insights from stakeholders and end-users. Travel Behav. Soc. 2020, 21, 295–306. [Google Scholar] [CrossRef]
- Callegati, F.; Gabbrielli, M.; Giallorenzo, S.; Melis, A.; Prandini, M. Smart mobility for all: A global federated market for mobility-as-a-service operators. In Proceedings of the 2017 IEEE 20th International Conference on Intelligent Transportation Systems, Yokohama, Japan, 16–19 October 2017. [Google Scholar] [CrossRef]
- Breuer, D.; Spichartz, P.; Sourkounis, C. Concept of interlinking mobility services for urban transport towards intermodal mobility including private and shared electromobility. In Proceedings of the 2019 14th International Conference on Ecological Vehicles and Renewable Energies, Monte-Carlo, Monaco, 8–10 May 2019. [Google Scholar] [CrossRef]
- Hoess, A.; Lautenschlager, J.; Sedlmeir, J.; Fridgen, G.; Schlatt, V.; Urbach, N. Toward seamless mobility-as-a-service: Providing multimodal mobility through digital wallets. Bus. Inf. Syst. Eng. 2024, 67, 149–170. [Google Scholar] [CrossRef]
- Miron, R.; Hulea, M.; Muresan, V.; Clitan, I.; Rusu, A. Integrating Blockchain Technology into Mobility-as-a-Service Platforms for Smart Cities. Smart Cities 2025, 8, 9. [Google Scholar] [CrossRef]
- Ekpo, O.; Casola, V.; De Benedictis, A. Towards a Privacy Resilient Mobility-as-a-Service (MaaS): A Threat-driven Approach. In Proceedings of the 2024 International Conference on Smart Systems and Technologies (SST), Osijek, Croatia, 16–18 October 2024. pp. 271–224. [Google Scholar]
- Chu, K.F.; Yuan, H.; Yuan, J.; Guo, W.; Balta-Ozkan, N.; Li, S. A Survey of Artificial Intelligence-Related Cybersecurity Risks and Countermeasures in Mobility-as-a-Service. IEEE Intell. Transp. Syst. Mag. 2024, 16, 37–55. [Google Scholar] [CrossRef]
- Oberoi, K.S. Personalisation in Mobility-as-a-Service: Where We Are and How to Move Forward. In Proceedings of the 10th International Conference on Vehicle Technology and Intelligent Transport Systems (VEHITS 2024), Angers, France, 2–4 May 2024; pp. 352–360. [Google Scholar]
- Peralta, A.A.; Balta-Ozkan, N.; Li, S. The road not taken yet: A review of cyber security risks in mobility-as-a-service (MaaS) ecosystems and a research agenda. Res. Transp. Bus. Manag. 2024, 56, 101162. [Google Scholar]
- Chu, K.F.; Guo, W. Multi-agent reinforcement learning-based passenger spoofing attack on mobility-as-a-service. IEEE Trans. Dependable Secur. Comput. 2024, 21, 5565–5581. [Google Scholar] [CrossRef]
- Kummetha, V.C.; Concas, S.; Staes, L.; Godfrey, J. Mobility on demand in the United States–Current state of integration and policy considerations for improved interoperability. Travel Behav. Soc. 2024, 37, 100867. [Google Scholar] [CrossRef]
- Schwinger, F.; Krempels, K.H. Mobility-oriented Agenda Planning as a Value-adding Feature for Mobility as a Service. In Proceedings of the 11th International Conference on Agents and Artificial Intelligence, Prague, Czech Republic, 19–21 February 2019; pp. 288–294. [Google Scholar] [CrossRef]
- Lopez-Carreiro, I.; Monzon, A.; Lois, D.; Lopez-Lambas, M.E. Are travellers willing to adopt MaaS? Exploring attitudinal and personality factors in the case of Madrid, Spain. Travel Behav. Soc. 2021, 25, 246–261. [Google Scholar] [CrossRef]
- Aman, J.J.C.; Smith-Colin, J. Application of crowdsourced data to infer user satisfaction with Mobility as a Service (MaaS). Transp. Res. Interdiscip. Perspect. 2022, 15, 100672. [Google Scholar] [CrossRef]
- Huang, S. Listening to users’ personal privacy concerns. The implication of trust and privacy concerns on the user’s adoption of a MaaS-pilot. Case Stud. Transp. Policy 2022, 10, 2153–2164. [Google Scholar] [CrossRef]
- Iotzov, V.; Cartolano, F.; Ciccarelli, G.; Durant, T.; Rizzoli, A.E. Integration vs fragmentation: Alternative tactics of local mobility businesses in response to a global wave of market disruptions. In Proceedings of the 7th Transport Research Arena TRA 2018, Vienna, Austria, 16–19 April 2018. [Google Scholar]
- Schikofsky, J.; Dannewald, T.; Kowald, M. Exploring motivational mechanisms behind the intention to adopt mobility as a service (MaaS): Insights from Germany. Transp. Res. Part A Policy Pract. 2020, 131, 296–312. [Google Scholar] [CrossRef]
- Wright, S.; Nelson, J.D.; Cottrill, C.D. MaaS for the suburban market: Incorporating carpooling in the mix. Transp. Res. Part A Policy Pract. 2020, 131, 206–218. [Google Scholar] [CrossRef]
- Caiati, V.; Rasouli, S.; Timmermans, H. Bundling, pricing schemes and extra features preferences for mobility as a service: Sequential portfolio choice experiment. Transp. Res. Part A Policy Pract. 2020, 131, 123–148. [Google Scholar] [CrossRef]
- Casadó, R.G.; Golightly, D.; Laing, K.; Palacin, R.; Todd, L. Children, Young people and Mobility as a Service: Opportunities and barriers for future mobility. Transp. Res. Interdiscip. Perspect. 2020, 4, 100107. [Google Scholar] [CrossRef]
- Ye, J.; Zheng, J.; Yi, F. A study on users’ willingness to accept mobility as a service based on UTAUT model. Technol. Forecast. Soc. Chang. 2020, 157, 120066. [Google Scholar] [CrossRef]
- Kokolakis, S. Privacy attitudes and privacy behaviour: A review of current research on the privacy paradox phenomenon. Comput. Secur. 2017, 64, 122–134. [Google Scholar] [CrossRef]
- Wu, C.; Vine, S.L.; Sivakumar, A. Assessment of the barriers in establishing passenger mobility-as-a-service (MaaS) systems: An analogy with multimodal freight transport. Case Stud. Transp. Policy 2025, 20, 101433. [Google Scholar] [CrossRef]
- Kriswardhana, W.; Esztergár-Kiss, D. Examining university students’ preferences toward MaaS aspects. Transp. Res. Interdiscip. Perspect. 2025, 30, 101348. [Google Scholar] [CrossRef]
- Tang, J.H.C.G.; Liu, J.; Chen, A.; Wang, B.; Zhuge, C.; Yang, X. Exploring the potential adoption of Mobility-as-a-Service in Beijing: A spatial agent-based model. Transp. Res. Part A Policy Pract. 2025, 194, 104430. [Google Scholar] [CrossRef]
- Lopez-Carreiro, I.; Monzon, A.; Lopez, E. Assessing the intention to uptake MaaS: The case of Randstad. Eur. Transp. Res. Rev. 2024, 16, 2. [Google Scholar] [CrossRef]
- Tsirimpa, A.; Karakikes, I.; Tsouros, I.; Mohammed, A.; Tahmasseby, S.; Salam, S.; Alhajyaseen, W.; Polydoropoulou, A. The role of subscription sharing and nationality in MaaS uptake in Qatar. Case Stud. Transp. Policy 2025, 19, 101364. [Google Scholar] [CrossRef]
- Yu, S.; Li, B.; Wang, H.; Liu, Y.; Hu, S. Applying a Modified Technology Acceptance Model to Explore Individuals’ Willingness to Use Mobility as a Service (MaaS): A Case Study of Beijing, China. Systems 2024, 12, 511. [Google Scholar] [CrossRef]
- Tunn, V.; Van Opstal, W.; Athanasopoulou, A. Unlocking Sustainable Mobility: Consumer Preferences and Segments on Mobility-as-A-Service Platforms. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=5168626 (accessed on 5 June 2025).
- Kriswardhana, W.; Esztergár-Kiss, D. University students’ adoption of mobility as a service with respect to user preferences and group differences. J. Public Transp. 2024, 26, 100079. [Google Scholar] [CrossRef]
- Underhill, B.; Knowles, A. Governance Participation Strategies for Mobility as a Service. In Proceedings of the Transportation Association of Canada 2020 Conference and Exhibition-The Journey to Safer Roads, Toronto, ON, Canada, 21 September–8 October 2020. [Google Scholar]
- Knowles, A.; Underhill, B.; Wong, R.; Lightsone, A. Mobility as a Service: Governance Strategies for Impending Disruptions. In Proceedings of the 2019 Canadian Transportation Research Forum 54th Annual Conference-Change, Vancouver, BC, Canada, 26–29 May 2019. [Google Scholar]
- Bevis, K.; Sozcu, O.; Fenner, R. Mobility as a Service. Presented at EEVConvention: Policies and Best Practice, Oslo, Norway, 25 September 2018. [Google Scholar]
- Mitropoulos, L.; Kortsari, A.; Mizaras, V.; Ayfantopoulou, G. Mobility as a Service (MaaS) Planning and Implementation: Challenges and Lessons Learned. Future Transp. 2023, 3, 498–518. [Google Scholar] [CrossRef]
- Murati, E. Mobility-as-a-service (MaaS) digital marketplace impact on EU passengers’ rights. Eur. Transp. Res. Rev. 2020, 12, 62. [Google Scholar] [CrossRef]
- Kamargianni, M.; Goulding, R. The Mobility as a Service Maturity Index: Preparing the Cities for the Mobility as a Service Era. In Proceedings of the 7th Transport Research Arena TRA 2018, Vienna, Austria, 16–19 April 2018. [Google Scholar] [CrossRef]
- Kamargianni, M.; Li, W.; Matyas, M.; Schäfer, A. A Critical Review of New Mobility Services for Urban Transport. Transp. Res. Procedia 2016, 14, 3294–3303. [Google Scholar] [CrossRef]
- Hlubi, N.; Seftel, L. Could Mobility as a Service (MaaS) Have a Role in an Integrated Public Transport Network in South African Cities? In Proceedings of the 38th Annual Southern African Transport Conference 2019, Pretoria, South Africa, 8–11 July 2019. [Google Scholar]
- Bandeira, J.M.; Macedo, E.; Teixeira, J.; Cicarelli, G.; Niculescu, M.; Fischer, N.; Gather, M. Multidimensional indicator of MaaS systems performance. Transp. Res. Procedia 2022, 62, 491–500. [Google Scholar] [CrossRef]
- Gompf, K.; Traverso, M.; Hetterich, J. Towards social life cycle assessment of mobility services: Systematic literature review and the way forward. Int. J. Life Cycle Assess. 2020, 25, 1883–1909. [Google Scholar] [CrossRef]
- Mohammed, A.; Salam, S.; Tahmasseby, S.; Alhajyaseen, W. Governance as Success Factor for Implementing MaaS in Countries with High Share of Expatriates: Qatar’s Case Study. Transp. Res. Procedia 2025, 82, 547–562. [Google Scholar] [CrossRef]
- Nikitas, A.; Cotet, C.; Vitel, A.E.; Nikitas, N.; Prato, C. Transport stakeholders’ perceptions of Mobility-as-a-Service: A Q-study of cultural shift proponents, policy advocates and technology supporters. Transp. Res. Part Policy Pract. 2024, 181, 103964. [Google Scholar] [CrossRef]
- Chu, K.F.; Guo, W. Privacy-preserving federated deep reinforcement learning for mobility-as-a-service. IEEE Trans. Intell. Transp. Syst. 2023, 25, 1882–1896. [Google Scholar] [CrossRef]
- Finnish Ministry of Justice. Personal Data Act (1999). Finnish law, Finlex 523/1999. Available online: https://natlex.ilo.org/dyn/natlex2/r/natlex/fe/details?p3_isn=73914 (accessed on 1 May 2025).
- Andrews, E.S.; Barthel, L.P.; Tabea, B.; Benoît, C.; Ciroth, A.; Cucuzzella, C.; Gensch, C.O.; Hébert, J.; Lesage, P.; Manhart, A.; et al. Guidelines for Social Life Cycle Assessment of Products; Technical Report; United Nations Environment Programme: Nairobi, Kenya, 2022. [Google Scholar]
- Goedkoop, M.J.; de Beer, I.M.; Harmens, R.; Saling, P.; Morris, D.; Florea, A.; Hettinger, A.L.; Indrane, D.; Visser, D.; Morao, A.; et al. Product Social Impact Assessment Handbook. 2020. Available online: https://ciraig.org/index.php/project/product-social-impact-assessment-handbook/ (accessed on 1 May 2025).
- Jing, Q.; Vasilakos, A.V.; Wan, J.; Lu, J.; Qiu, D. Security of the Internet of Things: Perspectives and challenges. Wirel. Netw. 2014, 20, 2481–2501. [Google Scholar] [CrossRef]
- Jain, P.; Gyanchandani, M.; Khare, N. Big data privacy: A technological perspective and review. J. Big Data 2016, 3, 25. [Google Scholar] [CrossRef]
- Lyons, G.; Hammond, P.; Mackay, K. The importance of user perspective in the evolution of MaaS. Transp. Res. Part A Policy Pract. 2019, 121, 22–36. [Google Scholar] [CrossRef]
- Landolfi, G.; Bami, A.; Izzo, G.; Montini, E.; Bettoni, A.; Vujasinovic, M.; Gugliotta, A.; Soares, A.L.; Diogo Silva, H. An Ontology Based Semantic Data Model Supporting A Maas Digital Platform. In Proceedings of the 2018 International Conference on Intelligent Systems, Funchal, Portugal, 25–27 September 2018; pp. 896–904. [Google Scholar] [CrossRef]
- Yazdizadeh, A.; Farooq, B. Smart Mobility Ontology: Current Trends and Future Directions. In Handbook of Smart Cities; Springer: Berlin/Heidelberg, Germany, 2021; pp. 803–838. [Google Scholar] [CrossRef]

| RQ1 | What cyber security and privacy risks associated with the use of MaaS systems have been reported in past research? |
| RQ2 | What cyber security and privacy concerns of users regarding the use of MaaS systems have been reported in past research? |
| RQ3 | What is the current state of research on technical considerations and solutions, as identified in prior investigations, for improving the cyber security and privacy of MaaS ecosystems? |
| RQ4 | How have researchers addressed legal issues regarding the privacy of personal data processed by MaaS systems, e.g., which regulations and what kind of policies have been considered on regulating MaaS systems? |
| Exclusion Criteria |
| → Published before 2017. |
| → Were not properly or sufficiently peer reviewed, including pre-prints, book chapters, white papers, technical reports, and other forms of gray literature. |
| → Published in languages other than English. |
| → Discussing ride sharing (private, like Uber or Lyft, or public, like bus sharing) when ride sharing is not intended as an integrated part of a MaaS System. |
| → Focusing on automated vehicles when automated vehicles are not integrated with a MaaS System. |
| → Discussing one or more transport systems that involve only one mode of transport. |
| Inclusion Criteria |
| → Have at least brief discussions on the roles played by cyber security and/or privacy risks in the development of MaaS. |
| → Have cyber security and/or privacy discussions on MaaS (which is considered as a system with shared mobility/ticketing and multimodal travel options). A multimodal travel option involves at least one transfer between more than or equal to two transport modes per single trip. |
| → Have considerable discussions on the policy governance of privacy and data sharing/protection and security. |
| Theme | Papers |
|---|---|
| Theme 1: Cyber security and/or privacy risks of MaaS systems and proposed solutions | : [2,18,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67] |
| Theme 2: Impacts of cyber security and/or privacy concerns/risks on the adoption of MaaS systems | : [7,28,47,57,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86] |
| Theme 3: Policies and regulations | : [5,10,18,26,28,33,37,54,57,62,71,79,87,88,89,90,91,92,93,94,95,96,97,98] |
| Subtheme | Description | Papers |
|---|---|---|
| Subtheme 1: Profiling and inference | Users’ behavior and mobility patterns can be profiled and inferred based on the personal data collected by MaaS applications/systems | [18,26,27,28,29,30,31,32,62,63] |
| Subtheme 2: Third-party access and data sharing | Third-party access to personal data collected by MaaS, data sharing between stakeholders/mobility providers, data sharing to open platforms, and data sharing to government bodies | [2,26,33,34,35,36,37,38,64,65] |
| Theme | Description | Papers |
|---|---|---|
| Subtheme 1: Technical security risks | Technical security risks or potential cyber attacks (e.g., denial-of-service (DoS) attacks, eavesdropping, ransomware attacks, and fault injection) to MaaS systems | [39,40,41,43,66] |
| Subtheme 2: Non-technical security risks | Security risks are related to the behaviors of end users and stakeholders of MaaS | [27,32,33,38,41,46,47,62] |
| Mitigation Solutions | Brief Description | Papers |
|---|---|---|
| Blockchain-based solutions | Secure ways for the payment and exchange of services and privacy preservation | [18,28,30,46,48,49,50,51,52,61,67] |
| Non-blockchain based solutions | Data security and access control | [18,26,41,44,45,53,54,55,56,57,58,59,60,63,64,99] |
| Year | Research Method(s) | Study Location(s) | Paper | Impact(s) |
|---|---|---|---|---|
| 2020 | Survey (1067 participants) | Germany | [73] | NO |
| 2020 | Questionnaire (1078 participants) | Amsterdam and Eindhoven areas (Netherlands) | [75] | NO |
| 2020 | Survey (600 participants) | Shanghai (China) | [77] | NE |
| 2020 | Workshops (90 participants), focus group (40 participants), survey (106 participants) | Budapest (Hungary) and Manchester (UK) | [57] | NE and NO |
| 2020 | Interactive workshop 1 (9 participants aged 8–13), Interactive workshop 2 (8 participants aged 14–17), and Interactive workshop 3 (3 participants aged 16–18) | North East of the Newcastle region (UK) | [76] | NE and NO |
| 2021 | Survey (1000 participants) | Madrid (Spain) | [69] | NE |
| 2020 | Workshop (20 participants, 8–18 years old) | North East England (UK) | [76] | NO |
| 2020 | Semi-structured interview (40 participants) | London, Birmingham, and Huddersfield (UK) | [47] | NE |
| 2020 | App trial, survey, and focus group (124 participants) | Brussels (Belgium), Edinburgh (Scotland), Canton Ticino (Switzerland), and Ljubljana (Slovenia) | [74] | NO |
| 2022 | Semi-structured interviews (47 participants), survey (23 participants), and survey (187 participants) | Norway | [71] | NO |
| 2024 | Online survey (700 participants) | Budapest University of Technology and Economics | [86] | NO |
| 2025 | Face-to-face survey (402 participants) | Beijing, China | [81] | NO |
| 2025 | Survey (697 participants) | Budapest University of Technology and Economics | [80] | NO |
| 2025 | Survey (1015 participants) | Qatar | [83] | NE |
| 2025 | Survey (1260 participants) | Beijing, China | [84] | NE |
| 2025 | Survey (107 participants) | the Netherlands | [85] | NE and NO |
| Stakeholder Group | Key Takeaways | Recommendations |
|---|---|---|
| Policymakers | - Lack of standardized data-sharing protocols and legal frameworks - Inconsistent enforcement of data protection laws, like the GDPR | - Develop harmonized international policies and data governance models - Mandate privacy-by-design in MaaS platforms |
| Developers/Providers | - Privacy risks include profiling, inference attacks, and third-party data sharing - Security vulnerabilities include DoS, spoofing, and insider threats | - Implement privacy-preserving technologies (e.g., federated learning, anonymization, and encryption) - Use secure architecture standards and blockchain smart contracts for transparency |
| Researchers | - Limited cross-disciplinary analysis on legal, behavioral, and technical risks - Gaps between users’ concerns and proposed solutions | - Focus future research on user-centric security design - Conduct longitudinal studies on risk perceptions and adoption behaviors |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Belen-Saglam, R.; Yuan, H.; Heering, M.S.; Ashraf, R.; Li, S. A Systematic Literature Review on Cyber Security and Privacy Risks in MaaS (Mobility-as-a-Service) Systems. Information 2025, 16, 514. https://doi.org/10.3390/info16070514
Belen-Saglam R, Yuan H, Heering MS, Ashraf R, Li S. A Systematic Literature Review on Cyber Security and Privacy Risks in MaaS (Mobility-as-a-Service) Systems. Information. 2025; 16(7):514. https://doi.org/10.3390/info16070514
Chicago/Turabian StyleBelen-Saglam, Rahime, Haiyue Yuan, Maria Sophia Heering, Ramsha Ashraf, and Shujun Li. 2025. "A Systematic Literature Review on Cyber Security and Privacy Risks in MaaS (Mobility-as-a-Service) Systems" Information 16, no. 7: 514. https://doi.org/10.3390/info16070514
APA StyleBelen-Saglam, R., Yuan, H., Heering, M. S., Ashraf, R., & Li, S. (2025). A Systematic Literature Review on Cyber Security and Privacy Risks in MaaS (Mobility-as-a-Service) Systems. Information, 16(7), 514. https://doi.org/10.3390/info16070514









