A Framework for Blockchain Alignment for Implementing Public Business Registers: A European Perspective
Abstract
1. Introduction
- Introduce the typology of selected public registries (we deliberately omit land, movable property, and civil and focus solely on business entities, for instance, as elaborated in [6]).
- Find common or specific characteristics and requirements for given types of registries.
- Create the framework that would enable one to address (or map) the requirements of selected types of registries by identifying models of the blockchain (architectures) as different classes of blockchain models should be suitable for implementing specific public registers—or not suitable at all.
- Selected state-of-the-art blockchain-based solutions for different kinds of public (legal) registries (mainly land and cadaster) are reviewed.
- A comprehensive list of blockchain system models together with their properties is identified based on the literature.
- A particular set of security concerns that may arise from the suggested switch towards a blockchain-based approach is addressed.
2. Methodology and Related Works
2.1. Research Method
- Concepts: public business registers typology, blockchain types, criteria groups and clusters, and requirements of registry groups;
- Models: a framework for mapping registry requirements to blockchain architecture;
- Methods: a method and set of rules for determining the mapping between registry requirements and specific blockchain types;
- Instances: an adaptation of the framework-based analysis for a specific registry.
2.2. Literature Review
2.3. Blockchain Types Landscape
2.4. Distributed Ledger Taxonomy
2.5. Gap Analysis
3. European Public Business Registers
3.1. Public Registry Types
3.2. The Estonian e-Business Register
3.3. German Shared Handelsregister
3.4. Austrian Firmenbuch
3.5. The Polish National Court Register
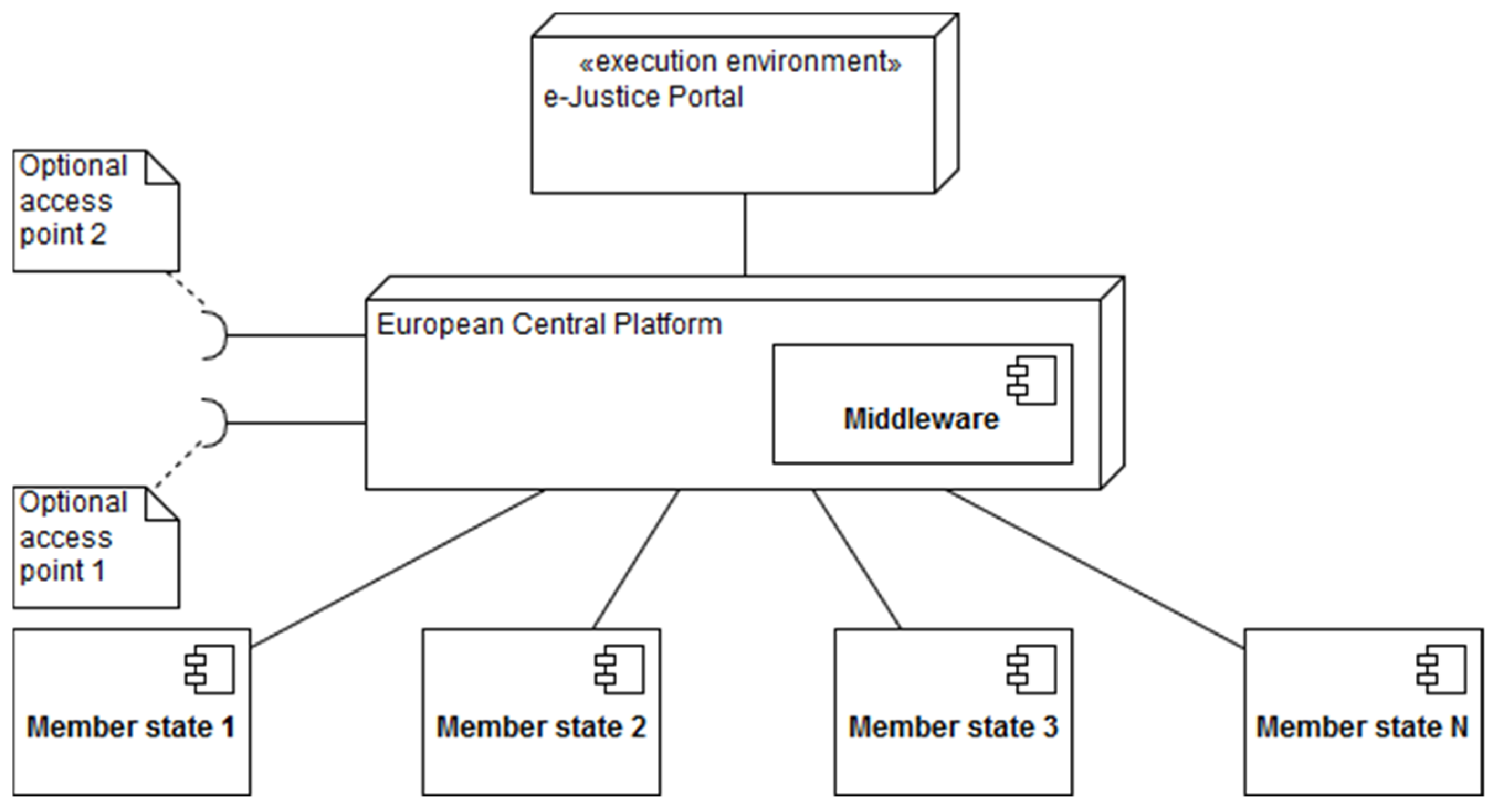
3.6. European Blockchain Services Infrastructure
4. Blockchain Alignment Framework
4.1. The Blockchain-Based Architecture of EU Business Registries
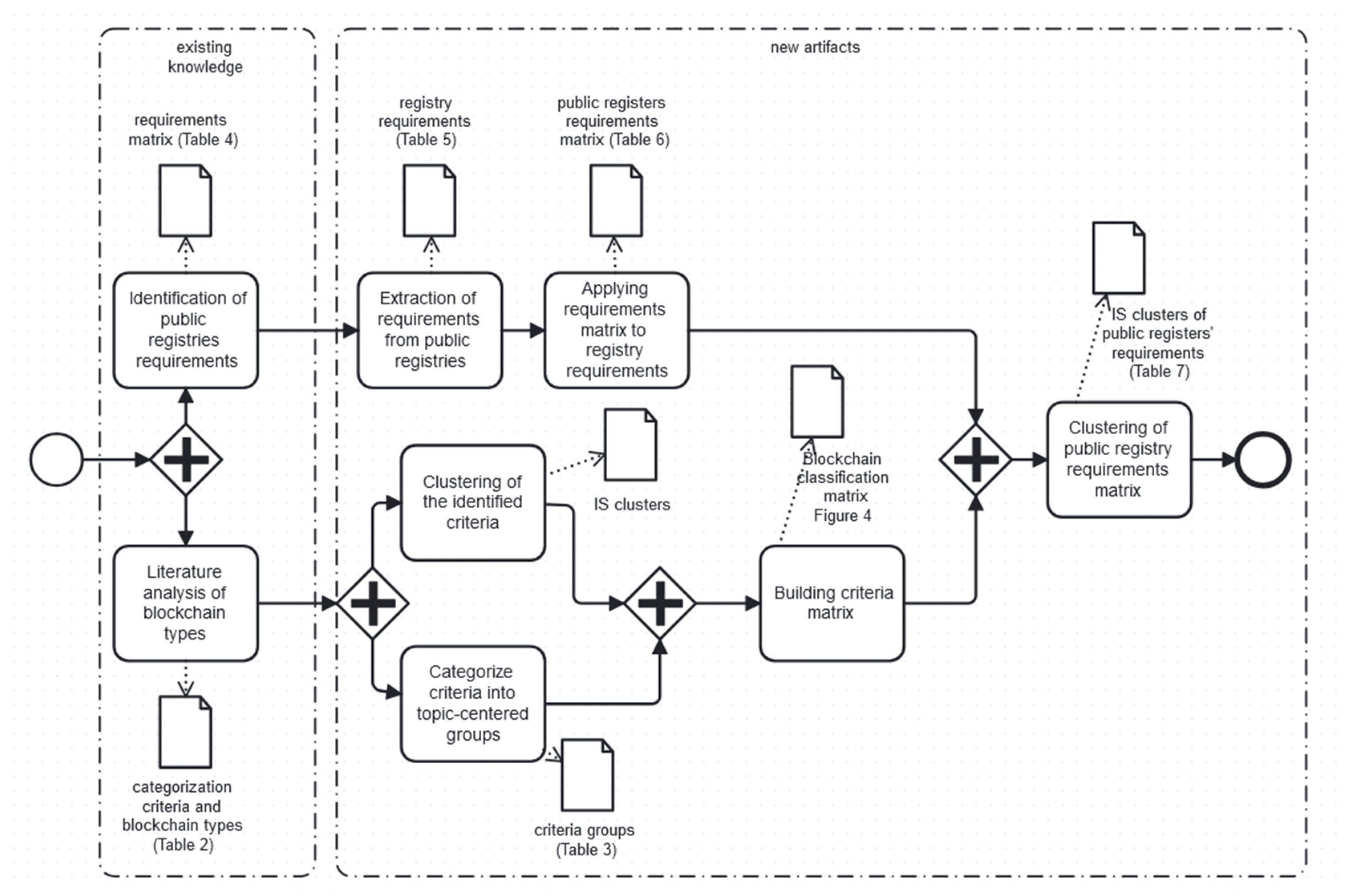
4.2. Framework Design
4.3. Blockchain Categorization Application
4.4. Common and Specific Requirements of Registry Groups
- Legal basis—registry must be established and maintained under a specific normative act.
- Legal norms conformance—includes adherence to the founding act, compliance with broader applicable laws, and temporal alignment to reflect amendments in vital regulations.
- Legal binding—registry data are legally guaranteed as trustworthy.
- Admissible as evidence—registry information can be presented in court without additional authentication.
- Legal authority—the existence and administrative powers of the managing or founding entity.
4.5. Observation of Registry Mapping Procedure
4.6. Security Analysis of the Blockchain-Based Approach
5. Discussion and Conclusions
5.1. Addressing the Security Concerns
5.2. Implications for Policy and Practice
5.3. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Questions Hierarchy | Cluster |
|---|---|
| 0. Is the number of parties limited? [T; F] | INF |
| 0.1 True: What is the nature of admission criterion? | INF |
| 0.2 What is the network topology (node number and node types)? | INF |
| 1. What is the number of administrative parties? [One; Many; Unlimited] | INF |
| 1.0 What is the consensus protocol type? [Resource-intensive; Reputation-based] | BEL |
| (1.0.0) Resource-intensive: Is mining necessary? [T; F] | BEL |
| (1.0.0.0) True: Is mining allowed to all parties—see also Q4? [T; F] | BUS |
| (1.0.0.1) True: Is the incentive necessary to uphold the system? [T; F] | BUS |
| (1.0.1) Reputation-based: What is the source of reputation? [Status; History] | BEL |
| 2. What is the form of incentive? [Coins; Tokens; Recognition] | BUS |
| 2.0 What is the source of the economic value of the incentive? [Real resource usage; Uniqueness; Social recognition] | BUS |
| 2.1 What is the expected de(in)flation rate? | BEL |
| 3. Does the system require trusted logic? [T; F] | INF |
| (3.0.0) True: Should the trusted logic be executed in a distributed environment? [T; F] | INF |
| (3.0.0.0) False: What other type of system is used for logic execution? [Private; Cloud] | INF |
| (3.0.1) True: Which nodes should the logic be executed on? [Any; Selected; Centralized] | BEL |
| 4. Are all parties equal? [T; F] | INF |
| (4.0) False: Do all parties have read access? | BEL |
| (4.1) False: Do all parties have write access? | BEL |
| 4.2 What is the level of information availability (publicity)? [Full, Pseudoanonymous, Limited] | BEL |
| 4.3 What is the nature of the write-mine relation? | BUS |
| 5. What party is the verifier? [Everyone; Selected] | BEL |
| (5.0) Selected: What is the mechanism of verifier selection? | INF |
| (5.1) Selected: How often does the selection process take place? | BUS |
| 5.2 Who verifies the verifier’s results? | BEL |
| 6. How is the information stored? | BUS |
| 6.0 Is the information stored in-chain or outside? [In; Out] | INF |
| (6.0.0) Out: What is the outside storage nature? [Cloud; P2P] | INF |
| (6.0.1) Out: How is the outside storage attached to the blockchain? | INF |
| 6.1 What is the storage unit? [Transaction; Contract; Event log] | INF |
| 6.2 What is the storage unit’s purpose? | BUS |
| 7. What is the manner of data item collection? [Contract; Document; Other] | BUS |
| (7.0) Document: What kind of documents are held? [Binary; Textual; Atomic values] | BUS |
| 7.0.0 Should metadata be included? [T; F] | BEL |
| (7.0.0.0) T: Will metadata change over time? [T; F] | BEL |
| 7.0.1 Is built-in logic needed? | INF |
| 7.0.2 Does data access cost? | BUS |
| (7.0.2.0) T: Does data read cost? | BUS |
| (7.0.2.1) T: Does data write cost? | BUS |
| 8. What type of logic is the design capable of? [Constraints; Contracts] | INF |
| (8.0) Constraints: What are the constraints on? | BUS |
| (8.1) Constraints: What is the outcome of constraint failure? | BEL |
| 9. What is the block topology? [Chain; DAG] | INF |
| (9.0) DAG: How are the alternative block paths respected? | BEL |
| 9.1 What is the block structure? | INF |
| 10. What type of consensus protocol is applied? [PoW, PoS, Storage, BFT] | INF |
| (10.0) PoW: Is the difficulty level adaptable? | BEL |
| (10.1) PoS: How is the stake measured? [Nominal; Temporal] | BUS |
| 11. What is the special purpose of using blockchain? [Security; Storage; Logical representation] | BUS |
| (11.0) Security: From what threats does the blockchain protect? [Integrity; Availability] | BEL |
References
- Vigna, P.; Casey, M. The Age of Cryptocurrency: How Bitcoin and Digital Money Are Challenging the Global Economic Order, 1st ed.; St. Martin’s Press: New York, NY, USA, 2015; ISBN 978-1-250-06563-6. [Google Scholar]
- Yang, Q.; Xu, F.; Zhang, Y.; Liu, F.; Hu, W.; Liao, Q. Design and Implementation of a Loan System Based on Smart Contract. In Smart Blockchain; Qiu, M., Ed.; Lecture Notes in Computer Science; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; Volume 11373, pp. 22–31. ISBN 978-3-030-05763-3. [Google Scholar]
- Li, C.; Hu, J.; Zhou, K.; Wang, Y.; Deng, H. Using Blockchain for Data Auditing in Cloud Storage. In Cloud Computing and Security; Sun, X., Pan, Z., Bertino, E., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; Volume 11065, pp. 335–345. ISBN 978-3-030-00011-0. [Google Scholar]
- Tasca, P. Insurance Under the Blockchain Paradigm. In Business Transformation Through Blockchain; Treiblmaier, H., Beck, R., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 273–285. ISBN 978-3-319-98910-5. [Google Scholar]
- Arnold, L.; Brennecke, M.; Camus, P.; Fridgen, G.; Guggenberger, T.; Radszuwill, S.; Rieger, A.; Schweizer, A.; Urbach, N. Blockchain and Initial Coin Offerings: Blockchain’s Implications for Crowdfunding. In Business Transformation Through Blockchain; Treiblmaier, H., Beck, R., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 233–272. ISBN 978-3-319-98910-5. [Google Scholar]
- Clohessy, T.; Acton, T.; Rogers, N. Blockchain Adoption: Technological, Organisational and Environmental Considerations. In Business Transformation Through Blockchain; Treiblmaier, H., Beck, R., Eds.; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 47–76. ISBN 978-3-319-98910-5. [Google Scholar]
- Xu, X.; Weber, I.; Staples, M.; Zhu, L.; Bosch, J.; Bass, L.; Pautasso, C.; Rimba, P. A Taxonomy of Blockchain-Based Systems for Architecture Design. In Proceedings of the 2017 IEEE International Conference on Software Architecture (ICSA), Gothenburg, Sweden, 3–7 April 2017; IEEE: Gothenburg, Sweden, 2017; pp. 243–252. [Google Scholar]
- Anjum, A.; Sporny, M.; Sill, A. Blockchain Standards for Compliance and Trust. IEEE Cloud Comput. 2017, 4, 84–90. [Google Scholar] [CrossRef]
- Moura, T.; Gomes, A. Blockchain Voting and Its Effects on Election Transparency and Voter Confidence. In Proceedings of the 18th Annual International Conference on Digital Government Research, Staten Island, NY, USA, 7–9 June 2017; ACM: New York, NY, USA, 2017; pp. 574–575. [Google Scholar]
- Tsukerman, M. The Block Is Hot: A Survey of the State of Bitcoin Regulation and Suggestions for the Future. Berkeley Technol. Law J. 2015, 30, 1127. [Google Scholar] [CrossRef]
- Hevner, A.R.; March, S.; Park, J.; Ram, S. Design Science in Information Systems Research. MIS Q. 2004, 28, 75–105. [Google Scholar] [CrossRef]
- Alan, R. Hevner A Three Cycle View of Design Science Research. Scand. J. Inf. Syst. 2007, 19, 87–92. [Google Scholar]
- Hevner, A.; Chatterjee, S. Design Science Research in Information Systems. In Design Research in Information Systems; Integrated Series in Information Systems; Springer US: Boston, MA, USA, 2010; Volume 22, pp. 9–22. ISBN 978-1-4419-5652-1. [Google Scholar]
- Thomas, R. Blockchain’s Incompatibility for Use as a Land Registry: Issues of Definition, Feasibility and Risk. Eur. Prop. Law J. 2017, 6, 361–390. [Google Scholar] [CrossRef]
- Vos, J. Blockchain-Based Land Registry: Panacea Illusion or Something in Between? Legal Interference of Registrars in the e-Conveyancing Process. 2016. Available online: https://elra.eu/wp-content/uploads/2017/02/10.-Jacques-Vos-Blockchain-based-Land-Registry.pdf (accessed on 20 November 2024).
- Navadkar, V.H.; Nighot, A.; Wantmure, R. Overview of Blockchain Technology in Government/Public Sectors. Int. Res. J. Eng. Technol. (IRJET) 2018, 5, 2287–2292. [Google Scholar]
- Gabison, G. Policy Considerations for the Blockchain Technology Public and Private Applications. SMU Sci. Technol. Law Rev. 2016, 19, 327–350. [Google Scholar]
- Oprunenco, A.; Akmeemana, C. Using Blockchain to Make Land Registry More Reliable in India. LSE Bus. Rev. 2018. Available online: https://www.undp.org/blog/using-blockchain-make-land-registry-more-reliable-india (accessed on 20 November 2024).
- Kshetri, N.; Voas, J. Blockchain in Developing Countries. IT Prof. 2018, 20, 11–14. [Google Scholar] [CrossRef]
- Shithy, R.I.; Mohammad, N.; Ruhullah, H.N.A.; Oni, S.M.Y.; Amin, M.A. A Blockchain Based Land Registration and Ownership Management System for Bangladesh. In Proceedings of the 2021 4th International Conference on Blockchain Technology and Applications, Xi’an, China, 17–19 December 2021; ACM: New York, NY, USA, 2021; pp. 94–100. [Google Scholar]
- Information and Communication Technology Division; Government of the People’s Republic of Bangladesh. National Blockchain Strategy: Bangladesh. Pathway to Be a Blockchain-Enabled Nation; Information and Communication Technology Division. Government of the People’s Republic of Bangladesh: Dhaka, Bangladesh, 2020. Available online: https://ictd.portal.gov.bd/sites/default/files/files/ictd.portal.gov.bd/policies/bf4c2781_651a_4d43_b994_55546baf0afa/Blockchain%20Strategy%20Bangladesh_4%20March%202020.pdf (accessed on 20 November 2024).
- Tahar, A.; Mendy, G.; Ouya, S. A Proof of Concept of the Integration of Blockchain with an ISO 19152:2012 Based Land Administration System. In Proceedings of the 2022 5th International Conference on Blockchain Technology and Applications, Xi’an, China, 16 December 2022; pp. 88–94. [Google Scholar]
- Tahar, A.; Mendy, G.; Ouya, S. Implementing Multisignature on a Blockchain-Based Land Administration System: Securing Land Rights and Enhancing Transparency. In Proceedings of the 2023 5th Blockchain and Internet of Things Conference, Osaka, Japan, 21 July 2023; pp. 8–14. [Google Scholar]
- Meng, Q. Blockchain-Based Security Governance Framework of Agricultural Product Traceability Data. In Proceedings of the 2022 4th Blockchain and Internet of Things Conference, Tokyo, Japan, 8 July 2022; pp. 16–21. [Google Scholar]
- Bourguignon, M.; Arantes, G.; Almeida, V.; Macadar, M.A. Rede Blockchain Brasil (Brazil Blockchain Network): Government Blockchain Network in Brazil. In Proceedings of the 16th International Conference on Theory and Practice of Electronic Governance, Belo Horizonte, Brazil, 26 September 2023; pp. 407–410. [Google Scholar]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Rosado Da Cruz, A.M.; Lopes, S.I. An Overview of Blockchain for Industry 5.0: Towards Human-Centric, Sustainable and Resilient Applications. IEEE Access 2024, 12, 116162–116201. [Google Scholar] [CrossRef]
- Central Bank Digital Currencies Foundational Principles and Core Features; Bank for International Settlements: Basel, Switzerland, 2020; ISBN 978-92-9259-427-5.
- Dowd, K. So Far, Central Bank Digital Currencies Have Failed. Econ. Aff. 2024, 44, 71–94. [Google Scholar] [CrossRef]
- Chaleenutthawut, Y.; Davydov, V.; Evdokimov, M.; Kasemsuk, S.; Kruglik, S.; Melnikov, G.; Yanovich, Y. Loan Portfolio Dataset From MakerDAO Blockchain Project. IEEE Access 2024, 12, 24843–24854. [Google Scholar] [CrossRef]
- Official Journal of the European Union. Regulation (EU) No 910/2014 of the European Parliament and of the Council of 23 July 2014 on Electronic Identification and Trust Services for Electronic Transactions in the Internal Market and Repealing Directive 1999/93/EC. 2014. Available online: http://data.europa.eu/eli/reg/2014/910/2024-10-18 (accessed on 20 November 2024).
- State of Arizona, House of Representatives. Arizona House Bill 2417; State of Arizona, House of Representatives: Phoenix, AZ, USA, 2017. Available online: https://www.azleg.gov/legtext/53leg/1r/bills/hb2417p.pdf (accessed on 20 November 2024).
- Brinkmann, M.; Heine, M. The Implementation of New Public Governance Through Blockchain: A Delphi-Based Analysis. In Proceedings of the 15th International Conference on Theory and Practice of Electronic Governance, Guimarães, Portugal, 4 October 2022; pp. 1–9. [Google Scholar]
- European Parliament. European Parliament Resolution of 26 May 2016 on Virtual Currencies (2016/2007(INI)); European Parliament: Strasbourg, France; Brussels, Belgium, 2016; Available online: https://www.europarl.europa.eu/doceo/document/TA-8-2016-0228_EN.html (accessed on 20 November 2024).
- Condos, J.; Sorrell, W.H.; Donegan, S.L. Blockchain Technology: Opportunities and Risks; Vermont Office of the Attorney General: Montpelier, VT, USA, 2016. Available online: https://web.archive.org/web/20250115171046/https://legislature.vermont.gov/assets/Legislative-Reports/blockchain-technology-report-final.pdf (accessed on 20 November 2024).
- Dubai, F.D.I. Blockchain Investment Opportunity Brief. 2018. Available online: https://web.archive.org/web/20230304020534/https://thedubaiadvantage.com/wp-content/uploads/2018/10/blockchain_investmentopportunitybrief.pdf (accessed on 20 November 2024).
- UAE. Emirates Blockchain Strategy 2021. 2019. Available online: https://u.ae/en/about-the-uae/strategies-initiatives-and-awards/strategies-plans-and-visions/strategies-plans-and-visions-untill-2021/emirates-blockchain-strategy-2021#:~:text=in%20april%202018%2c%20the%20uae%20government%20launched%20the,government%20transactions%20into%20the%20blockchain%20platform%20by%202021 (accessed on 20 November 2024).
- Ministry of Electronics & Information Technology, Government of India. National Strategy on Blockchain—Towards Enebling Trusted Digital Platforms; Ministry of Electronics & Information Technology, Government of India: New Delhi, India, 2021. Available online: https://www.meity.gov.in/writereaddata/files/National_BCT_Strategy.pdf (accessed on 20 November 2024).
- National Information Technology Development Agency, Nigeria. National Blockchain Policy for Nigeria; National Information Technology Development Agency, Nigeria: Abuja, Nigeria, 2023. Available online: https://nitda.gov.ng/wp-content/uploads/2023/05/National-Blockchain-Policy.pdf (accessed on 20 November 2024).
- Saeedi, M.A. Blockchain Application for Verification of Passports. Ph.D. Thesis, RCMS NUST, Islamabad, Pakistan, 2018. [Google Scholar]
- Lemieux, V.L. A Typology of Blockchain Recordkeeping Solutions and Some Reflections on Their Implications for the Future of Archival Preservation. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2271–2278. [Google Scholar]
- Kravchenko, P. Ok I Need a Blockchain but Which One. 2016. Available online: https://medium.com/@pavelkravchenko/ok-i-need-a-blockchain-but-which-one-ca75c1e2100 (accessed on 20 November 2024).
- Kruglik, S.; Nazirkhanova, K.; Yanovich, Y. Challenges beyond Blockchain: Scaling, Oracles and Privacy Preserving. In Proceedings of the 2019 XVI International Symposium “Problems of Redundancy in Information and Control Systems” (REDUNDANCY), Moscow, Russia, 21–25 October 2019; pp. 155–158. [Google Scholar]
- BRIS: Business Registers—Search for a Company in the EU. 2024. Available online: https://e-justice.europa.eu/content_business_registers_in_member_states-106-en.do (accessed on 20 November 2024).
- Handelsregister. Gemeinsames Registerportal Der Länder. 2020. Available online: https://www.handelsregister.de/rp_web/welcome.xhtml (accessed on 20 November 2024).
- Handelsgesetzbuch (HGB) of 10 Mai 1897’ (RGBl. S. 219) in the Version Published in the Bundesgesetzblatt Part III, Section No. 4100-1, Corrected Version with Amendmends (BGBl. I p. 1002); —‘Handelsregisterverordnung (HRV) of 12 August 1937’ (RMBl 1937, 515), with Amendmends (BGBl. I p. 2745). Available online: https://www.gesetze-im-internet.de/hgb/BJNR002190897.html (accessed on 20 November 2024).
- ‘Registerverfahrenbeschleunigungsgesetz (RegVBG) of 20 December 1993’ (BGBl. I S. 2182) with Amendmends (BGBl. I S. 866). Available online: https://www.bgbl.de/xaver/bgbl/start.xav?start=%2F%2F%2A%5B%40attr_id%3D%27bgbl193s2182.pdf%27%5D#__bgbl__%2F%2F*%5B%40attr_id%3D%27bgbl193s2182.pdf%27%5D__1737985950073 (accessed on 20 November 2024).
- Unternehmensregister. 2024. Available online: https://www.unternehmensregister.de/ureg/?submitaction=language&language=en (accessed on 20 November 2024).
- ‘Unternehmensregisterverordnung (URV) of 26 February 2007’ (BGBl. I S. 217) with Amendments (BGBl. I S. 2745). Available online: https://www.gesetze-im-internet.de/urv/BJNR021700007.html (accessed on 20 November 2024).
- ‘Firmenbuchgesetz (FBG)’ StF: BGBl. Nr. 10/1991 (NR: GP XVIII IA 9/A AB 23 S. 5. BR: AB 4004 S. 535). Available online: https://unternehmensrecht.univie.ac.at/fileadmin/user_upload/i_unternehmensrecht/Wahlfachkorb_Computer_und_Recht/e-Justice/auer/FBG__Fassung_vom_05.06.2023.pdf (accessed on 20 November 2024).
- Justiz. 2019. Available online: http://www.justiz.gv.at/firmenbuch (accessed on 20 November 2024).
- ‘Informationsweiterverwendungsgesetz (IWG)’ StF: BGBl. I Nr. 135/2005 (NR: GP XXII RV 1026 AB 1150 S. 125. BR: AB 7425 S. 727). Available online: https://www.ris.bka.gv.at/eli/bgbl/I/2005/135 (accessed on 20 November 2024).
- Ediktsdatei. 2024. Available online: https://edikte.justiz.gv.at/edikte/edikthome.nsf (accessed on 20 November 2024).
- Monika Kośka Przez Kilka Godzin Nie Dzialal eKRS. Money. 2018. Available online: https://www.money.pl/gospodarka/wiadomosci/artykul/przez-kilka-godzin-nie-dzialal-ekrs-do,77,0,2411085.html (accessed on 20 November 2024).
- European Commission. European Blockchain Services Infrastructure; European Commission: Brussels, Belgium; Luxembourg, 2024; Available online: https://digital-strategy.ec.europa.eu/en/policies/european-blockchain-services-infrastructure (accessed on 20 November 2024).
- European Commission. EBSI Projects; European Commission: Brussels, Belgium; Luxembourg, 2024; Available online: https://ec.europa.eu/digital-building-blocks/sites/display/ebsi/make+information+easy+to+verify+and+almost+impossible+to+fake (accessed on 20 November 2024).
- Tan, E.; Lerouge, E.; Du Caju, J.; Du Seuil, D. Verification of Education Credentials on European Blockchain Services Infrastructure (EBSI): Action Research in a Cross-Border Use Case between Belgium and Italy. BDCC 2023, 7, 79. [Google Scholar] [CrossRef]
- Koens, T.; Poll, E. The Drivers Behind Blockchain Adoption: The Rationality of Irrational Choices. In Euro-Par 2018: Parallel Processing Workshops; Mencagli, G., B. Heras, D., Cardellini, V., Casalicchio, E., Jeannot, E., Wolf, F., Salis, A., Schifanella, C., Manumachu, R.R., Ricci, L., et al., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; Volume 11339, pp. 535–546. ISBN 978-3-030-10548-8. [Google Scholar]
- Wust, K.; Gervais, A. Do You Need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June2018; pp. 45–54. [Google Scholar]
- Risius, M.; Spohrer, K. A Blockchain Research Framework: What We (Don’t) Know, Where We Go from Here, and How We Will Get There. Bus. Inf. Syst. Eng. 2017, 59, 385–409. [Google Scholar] [CrossRef]
- CyberPeace Institute Public Administration and Defence; Compulsory Social Security. Available online: https://cyberconflicts.cyberpeaceinstitute.org/impact/sectors/public-administration (accessed on 20 November 2024).
- Hylender, D.C.; Langlois, P.; Pinto, A.; Widup, S. Verizon 2024 Data Breach Investigations Report. The Verizon DBIR Team. Available online: https://www.verizon.com/business/resources/Tf18/reports/2024-dbir-data-breach-investigations-report.pdf (accessed on 20 November 2024).


| Administration | Outlook | Document |
|---|---|---|
| EU | ‘potential to accelerate, decentralize, automate and standardize data-driven processes at lower cost has the potential to alter fundamentally how assets are transferred, and records are kept’, ‘increase data sharing, transparency, and trust not only between the government and citizens’ | [33] |
| Vermont, USA | ‘the costs and challenges associated with the use of blockchain technology for Vermont’s public recordkeeping outweighs the identifiable benefits.’ The document recognizes twofold effects: the benefits (1) from a direct adoption of blockchain technology for Vermont governmental functions and the benefits (2) from legal recognition of blockchain for private uses, such as the evidentiary recognition | [34] |
| Dubai | ‘[…] stands to unlock 5.5 billion dirhams in savings annually in document processing alone—equal to the one Burj Khalifa’s worth of value every year.’ | [35] |
| UAE | ‘[…] save AED 11 billion in transactions and documents processed routinely, 398 million printed documents annually, 77 million work hours annually.’ | [36] |
| India | ‘[…] Blockchain characteristics such as tamper-evident, consensus-based transaction validations and secured data storage act as key driving forces for its adoption in various sectors’ | [37] |
| Nigeria | ‘[…] can contribute to strengthening Nigeria’s digital economy by expanding financial inclusion and enhancing openness and accountability’ | [38] |
| Bangladesh | ‘Blockchain technology is widely regarded as one of the core and foundational technologies that will be one of the driving forces for the upcoming 4IR’ | [21] |
| Criteria | Literature Item | Comments and Synonyms |
|---|---|---|
| 1. Cardinality of maintaining parties | [15,26,31] | Blockchain scope. |
| - public | Open to any node. | |
| - hybrid | Consortium/community. | |
| - private | Closed/open to particular nodes. | |
| 2. Permission | [7,31] | - |
| - fully centralized | Not a blockchain. | |
| - permissioned (fine-grained operations) | ||
| - permissioned (write, open access read) | ||
| - permissionless | Fully open system. | |
| 3. Cryptocurrency dependency | [31,39] | |
| - cryptocurrency-based | Driven by tokenized crypto economics. | |
| - non-cryptocurrency based | Tokenless. | |
| 4. Smart contracts functionality | [26,39] | - |
| - smart contracts blockchains | Distributed computations. | |
| - non-smart contracts blockchains | Without or with a basic scripting facility. | |
| 5. Verifier | [7] | Actor or node that verifies transactions. |
| - single | ||
| - m-of-n | ||
| - ad hoc | ||
| 6. Consensus Protocol | [7,26] | - |
| - proof-of-work | Most common consensus algorithm. The probability of the right to create a new block is proportional to computational power. | |
| - proof-of-stake | The probability of the right to create a new block is proportional to the stake in the crypto-economy. | |
| - proof-of-authority | ||
| - proof-of-retrievability | The probability of the right to create a new block is proportional to devoted storage resources. | |
| - Byzantine fault tolerance | ||
| - hybrid consensus | e.g., PoW plus PoS | |
| - proof-of-elapsed-time | ||
| 7. Data structure | [7] | - |
| - chain of blocks | Typical blockchain. | |
| - GHOST | ||
| - blocks DAG | Direct Acyclic Graphs allow for parallel transactions. | |
| - segregated witness | Technical improvement within the structure of a block. | |
| - shard chains | ||
| - rollups | e.g., optimistic, ZK rollups | |
| 8. Data item storage | [7] | - |
| - embedded within transaction | ||
| - embedded within smart contract | ||
| - embedded as a log | ||
| - in cloud | ||
| - P2P system | ||
| 9. Item collection | [7] | - |
| - as a smart contract | ||
| - on a parallel blockchain | ||
| 10. Computation | [7] | |
| - transaction constraints only | On-chain, non-Turing complete. | |
| - smart contracts | On-chain, Turing complete. | |
| - private/third-party cloud | Computation outside the blockchain. | |
| - zk-rollup computations | ||
| - machine learning on blockchain | ||
| 11. Mechanisms for data privacy | ||
| - zero-knowledge proofs | e.g., ZK-SNARKs, ZK-STARKs | |
| - ring signatures | ||
| - confidential transactions | ||
| - anonymization mechanisms | e.g., Mixnets, Tornado Cash | |
| 12. Off-chain transaction protocol | ||
| - mini-blockchain | ||
| - leader selection | ||
| - state channels | ||
| - rollup-based transactions | ||
| 13. Integration with other systems | ||
| - no integration | ||
| - API/interfaces to traditional systems | ||
| - cross-chain bridges | ||
| - interoperability protocols | e.g., Polkadot, Cosmos | |
| 14. Governance | ||
| - off-chain governance | ||
| - on-chain governance | e.g., DAO | |
| - hybrid governance models | ||
| 15. Resilience to attacks | ||
| - quantum-resistant | ||
| - Sybil attack protection mechanisms | ||
| - censorship resistance mechanisms | ||
| 16. Energy efficiency and sustainability | ||
| - high energy consumption | e.g., proof-of-work | |
| - low energy consumption | e.g., proof-of-stake, proof-of-space | |
| - carbon neutrality | e.g., CO2 offsetting mechanisms | |
| 17. Design patterns | [40] | - |
| - mirror type | ||
| - digital record type | ||
| - tokenized type | ||
| 18. Layers | ||
| - layer 1 | - | |
| - layer 2 | ||
| 19. Project phase | - | - |
| - testnet | Used for testing purposes. | |
| - mainnet | Working blockchain environment. |
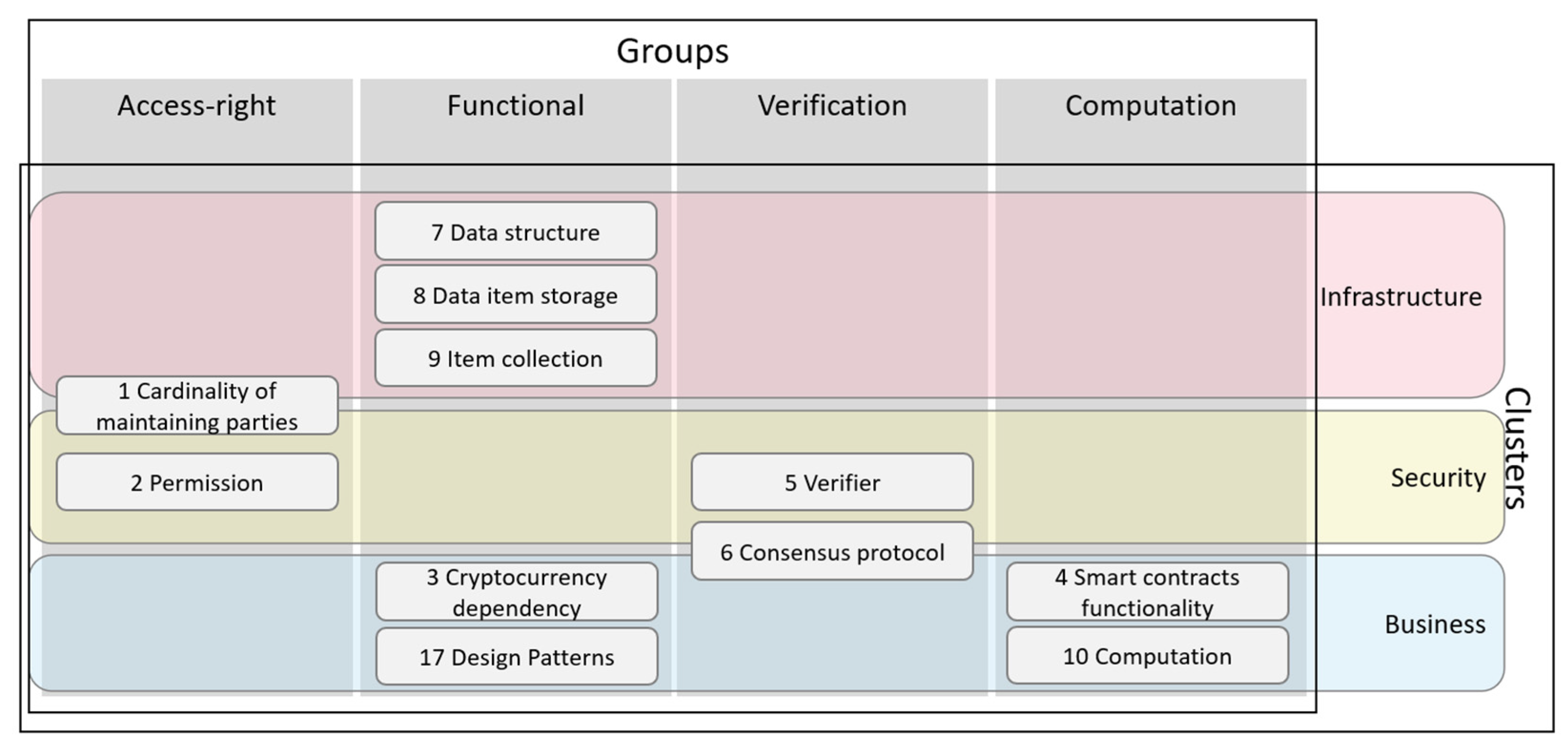
| Group Name | Grouped Criteria |
|---|---|
| Access-right | 1, 2 |
| Functional | 3, 7, 8, 9, 17 |
| Verification | 5, 6 |
| Computation | 4, 10 |
| Legal | Technical | |
|---|---|---|
| Functional | Print-out has legal significance equal to an official document | Search entities by legal form |
| Non-functional | Legal status depends on and reflects entries | Allows storage of information on 2 million objects with full financial documentation |
| Source: normative acts | Source: design/users’ needs |
| # | List of Requirements | Comment |
|---|---|---|
| R1 | Number of nodes | Centralized system with many end-user interfaces. |
| R2 | Read–write permissions | Which actors have the right to access information? |
| R3 | Online access for legal significance/temporal validity | How can the information be accessed? |
| R4 | Print-out has legal significance equal to an official document | What is significance medium dependence? |
| R5 | Availability | The system must be operable in a broad time range. |
| R6 | Accuracy (timelines) | The time needed to change data after the triggering event. |
| R7 | Documents storage | Will the system allow storing additional information? What is the structure of data? |
| R8 | Real-time data presentation | The delay between data alteration and their accessibility by end-user. |
| R9 | Payments | Availability of diverse payable and non-payable services. |
| R10 | External interfaces | Interoperability of the system. |
| R11 | Official acknowledgments (e.g., taxpayer has debt) | Security and flexibility. |
| R12 | Public statistics access | What kind of statistical data are produced? How and by whom can it be traced? |
| R13 | Trusted profile infrastructure interoperability | Is the system aware of security technologies? How efficiently can it cooperate with them? What kind of actors/roles are distinguished? |
| R14 | Number of records | The minimum number of information items a system is capable of persisting and processing. |
| Legal | Technical | |
|---|---|---|
| Functional | R1, R3, R4, R9, R11 | R2, R7, R10, R12 |
| Non-functional | R6, R13 | R5, R8, R14 |
| Cluster | Requirement |
|---|---|
| Security | R2, R6, R13 |
| Infrastructure | R5, R7, R8, R10, R14 |
| Business | R1, R3, R4, R9, R11, R12 |
| Threat Category | Public Entities Only | Private Entities Allowed | ||
|---|---|---|---|---|
| /Susceptibility | Permissioned | Permissionless | Permissioned | Permissionless |
| 1. Data privacy and GDPR compliance | ||||
| - cross-border data sharing | VL | L | VL | VL |
| - right to be forgotten | M | M | H | H |
| 2. Data integrity and fraudulent entries | ||||
| - false (synthetic) data (automated) input | VL | VL | H | VH |
| - varied data quality | VL | L | H | VH |
| - uncontrolled validation | L | M | H | VH |
| 3. Smart contract vulnerabilities | ||||
| - code exploits | VL | L | M | H |
| - upgradability issues | L | M | M | H |
| 4. Consensus mechanism and governance risks | ||||
| - consensus attacks | L | M | L | VL |
| - governance disputes | M | H | L | L |
| - jurisdictional issues | L | M | H | H |
| 5. Other technological threats | ||||
| - breaking encryption (quantum computing) | L | L | L | L |
| - information leakage (side-channel) | M | M | H | H |
| 6. Decentralization and node trustworthiness | ||||
| - node control and trust | L | M | M | M |
| - Byzantine fault tolerance | VL | M | L | L |
| - conflicting business interests | VL | L | H | VH |
| 7. Interoperability issues | ||||
| - differing security standards | H | H | ||
| - cross-chain interoperability risks | L | L | VL | VL |
| 8. Key management and identity verification | ||||
| - compromised private keys | M | H | H | VH |
| - authentication vulnerabilities | H | M | M | H |
| 9. System data overload | ||||
| - data pollution | VL | L | H | VH |
| - spam | VL | L | H | VH |
| 10 Distributed denial of service (DDoS) attacks | ||||
| - network integrity | VL | L | VL | VL |
| - infrastructure | M | L | VL | VL |
| 11. Insider threats and malicious actors | ||||
| - collusion between parties | VL | L | H | VH |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Stolarski, P.; Lewańska, E.; Abramowicz, W.; Schweighofer, E. A Framework for Blockchain Alignment for Implementing Public Business Registers: A European Perspective. Information 2025, 16, 105. https://doi.org/10.3390/info16020105
Stolarski P, Lewańska E, Abramowicz W, Schweighofer E. A Framework for Blockchain Alignment for Implementing Public Business Registers: A European Perspective. Information. 2025; 16(2):105. https://doi.org/10.3390/info16020105
Chicago/Turabian StyleStolarski, Piotr, Elżbieta Lewańska, Witold Abramowicz, and Erich Schweighofer. 2025. "A Framework for Blockchain Alignment for Implementing Public Business Registers: A European Perspective" Information 16, no. 2: 105. https://doi.org/10.3390/info16020105
APA StyleStolarski, P., Lewańska, E., Abramowicz, W., & Schweighofer, E. (2025). A Framework for Blockchain Alignment for Implementing Public Business Registers: A European Perspective. Information, 16(2), 105. https://doi.org/10.3390/info16020105







